5. System Management
This chapter provides information about configuring basic system management parameters.
5.1. System Management Parameters
System management commands allow you to configure basic system management functions such as the system name, the router’s location and coordinates, and Common Language Location Identifer (CLLI) code, as well as time zones, Network Time Protocol (NTP), Simple Network Time Protocol (SNTP) properties, CRON and synchronization properties.
5.1.1. System Information
System information components include the following:
5.1.1.1. System Name
The system name is the MIB II (RFC 1907, Management Information Base for Version 2 of the Simple Network Management Protocol (SNMPv2)) sysName object. By convention, this text string is the fully-qualified domain name of the node. The system name can be any ASCII printable text string up to 32 characters.
5.1.1.2. System Contact
The system contact is the MIB II sysContact object. By convention, this text string is a textual identification of the contact person for this managed node, together with information about how to contact this person.The system contact can be any ASCII printable text string up to 80 characters.
5.1.1.3. System Location
The system location is the MIB II sysLocation object, which is a text string conventionally used to describe the physical location of the node; for example, Bldg MV-11, 1st Floor, Room 101. The system location can be any ASCII printable text string up to 80 characters.
5.1.1.4. System Coordinates
The Nokia Chassis MIB tmnxChassisCoordinates object defines the system coordinates. This text string indicates the Global Positioning System (GPS) coordinates of the location of the chassis.
Two-dimensional GPS positioning offers latitude and longitude information as a four dimensional vector:
<direction, hours, minutes, seconds>
where:
direction is one of the four basic values: N, S, W, E
hours ranges from 0 to 180 (for latitude) and 0 to 90 for longitude
minutes and seconds range from 0 to 60.
<W, 122, 56, 89> is an example of longitude and <N, 85, 66, 43> is an example of latitude.
System coordinates can be expressed in different notations; for example:
- N 45 58 23, W 34 56 12
- N37 37' 00 latitude, W122 22' 00 longitude
- N36*39.246' W121*40.121
The system coordinates can be any ASCII printable text string up to 80 characters.
5.1.1.5. Naming Objects
It is discouraged to configure named objects with a name that starts with “_tmnx_” and with the “_” symbol.
5.1.1.6. CLLI
A CLLI code string for the device is an 11-character standardized geographic identifier that uniquely identifies the geographic location of places and certain functional categories of equipment unique to the telecommunications industry. The CLLI code is stored in the Nokia Chassis MIB tmnxChassisCLLICode object.
The CLLI code can be any ASCII printable text string of up to 11 characters.
5.1.2. System Time
The 7210 SAS routers are equipped with a real-time system clock for time-keeping purposes. When set, the system clock always operates on Coordinated Universal Time (UTC), but the software has options for local time translation and system clock synchronization.
System time parameters include the following:
5.1.2.1. Time Zones
Setting a time zone allows for times to be displayed in the local time rather than in UTC. The 7210 SAS supports both user-defined and system-defined time zones.
A user-defined time zone has a user-assigned name of up to four printable ASCII characters that is different from the system-defined time zones. For user-defined time zones, the offset from UTC is configured, as well as any summer time adjustment for the time zone.
Table 22 describes the system-defined time zones, including time zones with and without summer time correction.
Table 22: System-defined Time Zones
Acronym | Time Zone Name | UTC Offset |
Europe | ||
GMT | Greenwich Mean Time | UTC |
BST | British Summer Time | UTC +1 |
IST | Irish Summer Time | UTC +1* |
WET | Western Europe Time | UTC |
WEST | Western Europe Summer Time | UTC +1 |
CET | Central Europe Time | UTC +1 |
CEST | Central Europe Summer Time | UTC +2 |
EET | Eastern Europe Time | UTC +2 |
EEST | Eastern Europe Summer Time | UTC +3 |
MSK | Moscow Time | UTC +3 |
MSD | Moscow Summer Time | UTC +4 |
US and Canada | ||
AST | Atlantic Standard Time | UTC -4 |
ADT | Atlantic Daylight Time | UTC -3 |
EST | Eastern Standard Time | UTC -5 |
EDT | Eastern Daylight Saving Time | UTC -4 |
ET | Eastern Time | Either as EST or EDT, depending on place and time of year |
CST | Central Standard Time | UTC -6 |
CDT | Central Daylight Saving Time | UTC -5 |
CT | Central Time | Either as CST or CDT, depending on place and time of year |
MST | Mountain Standard Time | UTC -7 |
MDT | Mountain Daylight Saving Time | UTC -6 |
MT | Mountain Time | Either as MST or MDT, depending on place and time of year |
PST | Pacific Standard Time | UTC -8 |
PDT | Pacific Daylight Saving Time | UTC -7 |
PT | Pacific Time | Either as PST or PDT, depending on place and time of year |
HST | Hawaiian Standard Time | UTC -10 |
AKST | Alaska Standard Time | UTC -9 |
AKDT | Alaska Standard Daylight Saving Time | UTC -8 |
Australia | ||
AWST | Western Standard Time (e.g., Perth) | UTC +8 |
ACST | Central Standard Time (e.g., Darwin) | UTC +9.5 |
AEST | Eastern Standard/Summer Time (e.g., Canberra) | UTC +10 |
5.1.2.2. Network Time Protocol (NTP)
The Network Time Protocol (NTP) is defined in RFC 1305, Network Time Protocol (Version 3) Specification, Implementation and Analysis. It allows participating network nodes to keep time more accurately and maintain time in a more synchronized manner between the participating network nodes.
NTP uses stratum levels to define the number of hops from a reference clock. The reference clock is treated as a stratum-0 device that is assumed to be accurate with little or no delay. Stratum-0 servers cannot be used in a network. However, they can be directly connected to devices that operate as stratum-1 servers. A stratum-1 server is an NTP server with a directly-connected device that provides Coordinated Universal Time (UTC), such as a GPS or atomic clock.
The 7210 SAS devices cannot act as stratum-1 servers but can act as stratum-2 devices because a network connection to an NTP server is required.
The higher stratum levels are separated from the stratum-1 server over a network path, thus a stratum-2 server receives its time over a network link from a stratum-1 server. A stratum-3 server receives its time over a network link from a stratum-2 server.
If the internal PTP process is used as a time source for System Time and OAM, it must be specified as a server for NTP. If PTP is specified, the prefer parameter must also be specified. After PTP has established a UTC traceable time from an external grandmaster source, that clock will always be the time source into NTP, even if PTP goes into time holdover.
| Note: Use of the internal PTP time source for NTP will promote the internal NTP server to stratum-1 level. This may impact the NTP network topology. |
The following NTP elements are supported:
- server modeIn this mode, the node advertises the ability to act as a clock source for other network elements. By default, the node will, by default, transmits NTP packets in NTP version 4 mode.
- authentication keysThese keys implement increased security support in carrier and other networks. Both DES and MD5 authentication are supported, as well as multiple keys.
- symmetric active modeIn this mode, the NTP is synchronized with a specific node that is considered more trustworthy or accurate than other nodes carrying NTP in the system. This mode requires that a specific peer is set.
- broadcastIn this mode, the node receives or sends using a broadcast address.
- alert when NTP server is not availableWhen none of the configured servers are reachable on the node, the system reverts to manual timekeeping and issues a critical alarm. When a server becomes available, a trap is issued indicating that standard operation has resumed.
- NTP and SNTPIf both NTP and SNTP are enabled on the node, SNTP transitions to an operationally down state. If NTP is removed from the configuration or shut down, SNTP resumes an operationally up state.
- gradual clock adjustmentBecause several applications (such as Service Assurance Agent (SAA)) can use the clock, if a major adjustment (128 ms or more) is needed, it is performed by programmatically stepping the clock. If a minor (less than 128 ms) adjustment is needed, it is performed by either speeding up or slowing down the clock.
- rate limit events and trapsTo avoid the generation of excessive events and traps the NTP module rate limits the generation of events and traps to three per second. At that point, a single trap is generated to indicate that event and trap squashing is taking place.
5.1.2.3. SNTP Time Synchronization
To synchronize the system clock with outside time sources, the 7210 SAS devices include a Simple Network Time Protocol (SNTP) client. As defined in RFC 2030, SNTP Version 4 is an adaptation of NTP. SNTP typically provides time accuracy within 100 ms of the time source. SNTP can only receive the time from NTP servers; it cannot be used to provide time services to other systems. SNTP is a compact, client-only version of NTP. SNTP does not authenticate traffic.
In the 7210 SAS software, the SNTP client can be configured in both unicast client modes (point-to-point) and broadcast client modes (point-to-multipoint). SNTP should be used only at the extremities of the synchronization subnet. SNTP clients should operate only at the highest stratum (leaves) of the subnet and in configurations where no NTP or SNTP client is dependent on another SNTP client for synchronization. SNTP time servers should operate only at the root (stratum 1) of the subnet and then only in configurations where no other source of synchronization other than a reliable radio clock is available.
5.1.2.4. CRON
The CRON feature supports the SAA functions and time-based policy scheduling to meet time of day requirements. CRON functionality includes the ability to specify the commands to be run, their scheduling, including one-time only functionality (oneshot), interval and calendar functions, and the storage location for the script output. CRON can also specify the relationship between input, output, and schedule. Scheduled reboots, peer turn ups, service assurance agent tests, and OAM events, such as connectivity checks or troubleshooting runs, can also be scheduled.
CRON features are saved to the configuration file.
CRON features run serially with at least 255 separate schedules and scripts. Each instance can support a schedule where the event is repeatedly executed.
The following CRON elements are supported:
- actionThis configures parameters for a script including the maximum amount of time to keep the results from a script run, the maximum amount of time a script may run, the maximum number of script runs to store and the location to store the results.
- scheduleThe schedule function configures the type of schedule to run, including one-time only (oneshot), periodic, or calendar-based runs. All runs are determined by month, day of month or weekday, hour, minute and interval (seconds).
- scriptThe script command opens a new nodal context that contains information about a script.
- time rangeACLs and QoS policy configurations may be enhanced to support time-based matching. CRON configuration includes time-matching with the schedule sub-command. Schedules are based on events; time-range defines an end-time used as a match criteria.
- time of dayTime of Day (TOD) suites are useful when configuring many types of time-based policies or when a large number of SAPs require the same type of TOD changes. The TOD suite may be configured while using specific ingress or egress ACLs or QoS policies, and is an enhancement of the ingress and egress CLI trees.
5.2. High Availability
This section describes the high availability (HA) routing options and features that service providers can use to reduce vulnerability at the network or service provider edge and alleviate the effect of a lengthy outage on IP networks.
HA is an important feature in service provider routing systems. The unprecedented growth of IP services and applications in service provider networks is driven by the demand from the enterprise and residential communities. Downtime can be very costly, and, in addition to lost revenue, customer information and business-critical communications can be lost. HA is the combination of continuous uptime over long periods (Mean Time Between Failures (MTBF)) and the speed at which failover or recovery occurs (Mean Time To Repair (MTTR)).
The advantage of HA routing is evident at the network or service provider edge, where thousands of connections are hosted. Rerouting options around a failed piece of equipment are often limited, or, a single access link exists to a customer because of the additional cost of redundant links. As service providers converge business-critical services, such as real-time voice (VoIP), video, and VPN applications over their IP networks, the requirements for HA become more stringent compared to the requirements for best-effort data.
Network and service availability become critical aspects in advanced IP service offerings, which dictate that the IP routers used to build the foundations of these networks must be resilient to component and software outages.
5.2.1. HA Features
This section describes high availability features for devices.
5.2.1.1. Redundancy
Redundancy features enable duplication of data elements to maintain service continuation in case of outages or component failure.
5.2.1.1.1. Component Redundancy
7210 SAS component redundancy is critical to reducing MTTR for the routing system.
The following component redundancy features are supported on the 7210 SAS-D and 7210 SAS-Dxp:
- AC or DC power supplyThe 7210 SAS-D and 7210 SAS-Dxp each have an integrated AC or DC power supply. A redundant external backup power supply is available only on the 7210 SAS-D ETR variant and 7210 SAS-Dxp ETR variant. Use of redundant external backup power is optional. The external backup power supply cannot be used with the 7210 SAS-D standard variant and 7210 SAS-Dxp standard variant.
- chassis cooling7210 SAS-D 128 MB devices support passive cooling. The device also has a fan to allow air circulation (and not cooling). By default, the fan mode is set to auto mode. In auto mode, by default, the software determines when to turn the fan on and when to switch it off. This can be changed by the operator using the CLI command config>system>fan. Operators have an option to switch off the fan permanently or turn it on permanently.7210 SAS-Dxp supports passive cooling; it does not have any fans.
- hot swapThe power supply is integrated into the chassis. Hot swapping is not supported. The external power supply backup connection can be added or removed at any time on the 7210 SAS-D ETR variant and 7210 SAS-Dxp ETR variant.
- replaceable storage mediaThe 7210 SAS-D internal flash device (cf1:\) cannot be replaced.The 7210 SAS-Dxp (all variants) supports a single, field-replaceable, SD card-based storage medium.
The following component redundancy features are supported on the 7210 SAS-K 2F1C2T:
- The 7210 SAS-K 2F1C2T non-ETR (standard) unit supports a single external AC power supply.
- The 7210 SAS-K 2F1C2T ETR unit supports power redundancy and provides two power input pins on the rear of the unit. The user has the option to use AC, -48V DC, or +24V DC power.
- There are no fans in either of the 7210 SAS-K 2F1C2T non-ETR or ETR variants; these units are passively cooled.
- The 7210 SAS-K 2F1C2T (all variants) supports a single, field-replaceable, SD card-based storage medium.
The following component redundancy features are supported on the 7210 SAS-K 2F6C4T:
- The 7210 SAS-K 2F6C4T non-ETR (standard) unit supports a single external AC power supply.
- The 7210 SAS-K 2F6C4T ETR unit supports power redundancy and provides two power input connectors on the front panel of the unit. The unit currently only supports an external AC power supply.
- There are no fans in either of the 7210 SAS-K 2F6C4T non-ETR or ETR variants; these units are passively cooled.
- The 7210 SAS-K 2F6C4T (all variants) supports a single, field-replaceable, SD card-based storage medium.
The following component redundancy features are supported on the 7210 SAS-K 3SFP+ 8C:
- The 7210 SAS-K 3SFP+ 8C AC and DC variants support power redundancy and provide two power input connectors on the front panel of the unit. The AC variant has two integrated AC power supplies. The DC variant has one integrated DC power supply.
- There are no fans in the 7210 SAS-K 3SFP+ 8C; the unit is passively cooled.
- The 7210 SAS-K 3SFP+ 8C (all variants) supports a single, field-replaceable, SD card-based storage medium.
5.3. Temperature Threshold Alarm and Fan Speed
Table 23 describes the over-temperature thresholds for 7210 SAS devices:
Table 23: Over-Temperature Threshold for 7210 SAS Devices
Device Variants | Minimum Temperature (in degree centigrade) | Maximum Temperature (in degree centigrade) |
7210 SAS-D | 0 | 45 |
7210 SAS-D ETR | -40 | 60 |
7210 SAS-Dxp | 0 | 45 |
7210 SAS-Dxp ETR | -40 | 60 |
7210 SAS-K 2F1C2T | 0 | 65 |
7210 SAS-K 2F1C2T ETR | -25 | 85 |
7210 SAS-K 2F6C4T | 0 | 76 |
7210 SAS-K 2F6C4T ETR | -25 | 85 |
7210 SAS-K 3SFP+ 8C | -25 | 90 |
The 7210 SAS system software controls the fans by monitoring the internal temperature of the chassis. The software manages the fan speed to maintain the internal temperature within the operational limits.
The 7210 SAS-D and 7210 SAS-D ETR platforms support fanless operation. The platforms have a fan for air circulation only, and not for cooling. The fan operates in automatic mode by default, and can be disabled by the operator.
The 7210 SAS-Dxp and 7210 SAS-Dxp ETR platforms are passively cooled and do not have fans.
5.4. Network Synchronization
This section describes the network synchronization capabilities available on 7210 SAS platforms. These capabilities involve multiple approaches to network timing, including synchronous Ethernet, PTP/1588v2, adaptive timing, and others. These features address barriers to entry as follows:
- provide synchronization quality required by mobile networks, such as radio operations and circuit emulation services (CES) transport
- augment and potentially replace the existing (SONET/SDH) timing infrastructure and deliver high quality network timing for time-sensitive wireline applications
| Note: Network synchronization is only supported on the 7210 SAS-D ETR, 7210 SAS-Dxp ETR, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C. |
Figure 22 shows how network synchronization is commonly distributed in a hierarchical master-slave topology at the physical layer.
Figure 22: Conventional Network Timing Architecture (North American Nomenclature)
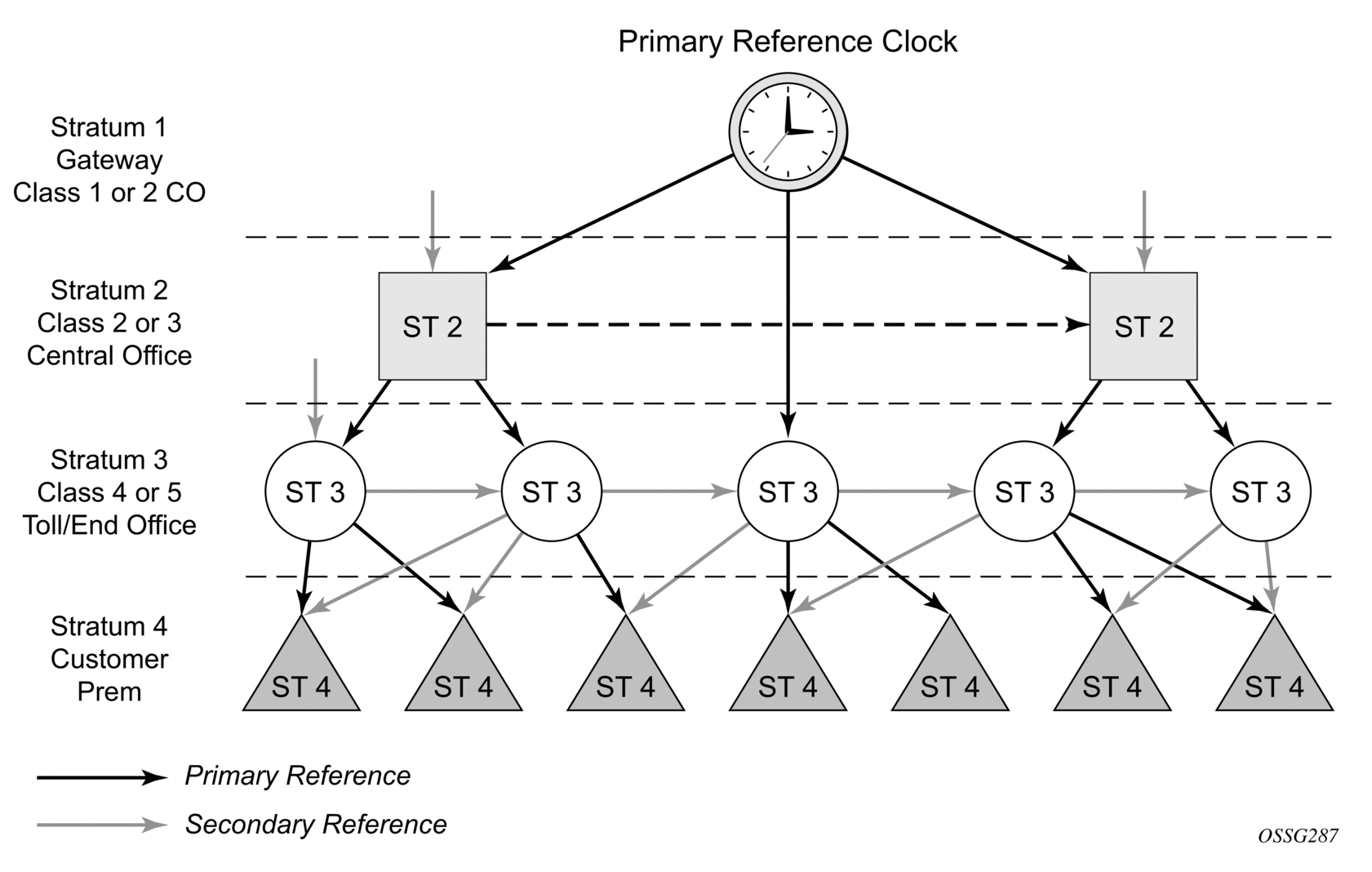
The architecture shown in Figure 22 provides the following benefits.
- It limits the need for high quality clocks at each network element and only requires that they reliably replicate input to remain traceable to its reference.
- It uses reliable physical media to provide transport of the timing signal. It does not consume any bandwidth and requires limited additional processing.
The synchronization network is designed so a clock always receives timing from a clock of equal or higher stratum or quality level. This ensures that if an upstream clock has a fault condition (for example, loses its reference and enters a holdover or free-run state) and begins to drift in frequency, the downstream clock will be able to follow it. For greater reliability and robustness, most offices and nodes have at least two synchronization references that can be selected in priority order (such as primary and secondary).
Further levels of resiliency can be provided by designing a capability in the node clock that will operate within prescribed network performance specifications without any reference for a specified timeframe. A clock operating in this mode is said to hold the last known state over (or holdover) until the reference lock is once again achieved. Each level in the timing hierarchy is associated with minimum levels of network performance.
Each synchronization-capable port can be independently configured to transmit data using the node reference timing. In addition, some TDM channels can use adaptive timing or loop timing.
Transmission of a reference clock through a chain of Ethernet equipment requires that all equipment supports Synchronous Ethernet. A single piece of equipment that is not capable of performing Synchronous Ethernet breaks the chain. Ethernet frames will still get through but downstream devices should not use the recovered line timing because it will not be traceable to an acceptable stratum source.
5.4.1. Central Synchronization Subsystem
The timing subsystem has a central clock located on the CPM. The timing subsystem performs several functions of the network element clock as defined by Telcordia (GR-1244-CORE) and ITU-T G.781 standards.
The central clock uses the available timing inputs to train its local oscillator. The number of timing inputs available to train the local oscillator varies per platform. The priority order of these references must be specified. This is an ordered list of inputs: (ref1, ref2). The CPM clock output can drive the clocking for all line cards in the system. The routers support selection of the node reference using Quality Level (QL) indications. The recovered clock will be able to derive its timing from one of the references available on that platform.
Figure 23 shows how on 7210 SAS devices, the recovered clock is able to derive the timing from any of the following references:
- synchronous Ethernet ports
- 1588v2/PTP slave port
See Synchronization Options Available on 7210 SAS Platforms for information about the synchronization options supported by each 7210 SAS platform.
Figure 23 shows the synchronization reference selection available for the 7210 SAS platforms.
Figure 23: A Logical Model of the Synchronization Reference Selection on 7210 SAS Platforms
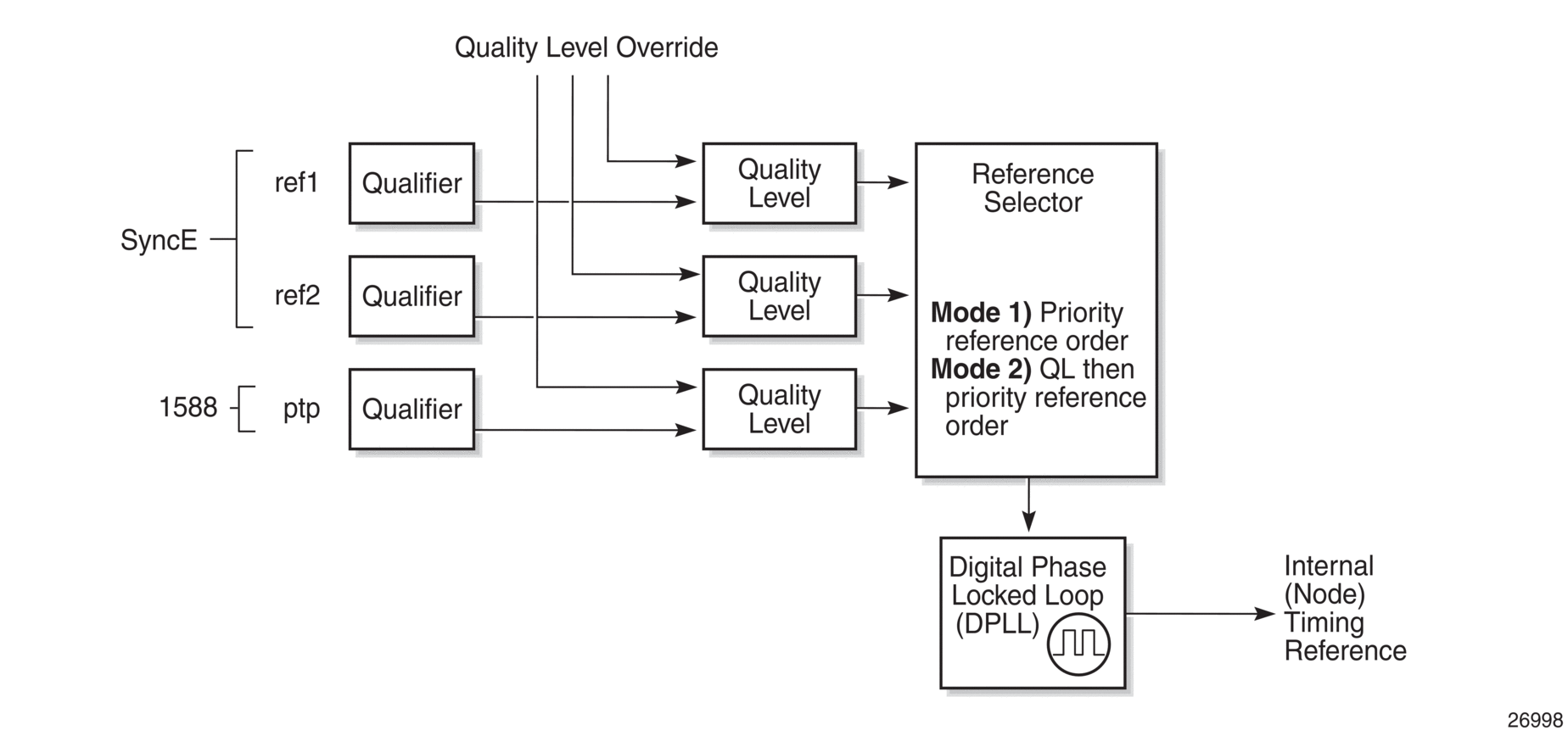
When Quality Level (QL) selection mode is disabled, the reversion setting controls when the central clock can reselect a previously failed reference.
Table 24 describes the selection followed for two references in both revertive and non-revertive modes.
Table 24: Revertive, Non-Revertive Timing Reference Switching Operation
Status of Reference A | Status of Reference B | Active Reference Non-revertive Case | Active Reference Revertive Case |
OK | OK | A | A |
Failed | OK | B | B |
OK | OK | B | A |
OK | Failed | A | A |
OK | OK | A | A |
Failed | Failed | Holdover | Holdover |
OK | Failed | A | A |
Failed | Failed | Holdover | Holdover |
Failed | OK | B | B |
Failed | Failed | Holdover | Holdover |
OK | OK | A or B | A |
5.4.2. Synchronization Options Available on 7210 SAS Platforms
Table 25 lists the supported synchronization options supported on 7210 SAS platforms.
Table 25: Synchronization Options on 7210 SAS-D ETR, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C
Synchronization Options | 7210 SAS Platforms | ||||
7210 SAS-D ETR | 7210 SAS-Dxp ETR | 7210 SAS-K 2F1C2T | 7210 SAS-K 2F6C4T | 7210 SAS-K 3SFP+ 8C | |
SyncE with SSM (SFP, SFP+, and 10G/XFP ports) | ✓ | ✓ | ✓ 1 | ✓ 1 | ✓ |
SyncE with fixed copper ports (master/slave support) | ✓ 2 | ✓ | ✓ 1 | ✓ 1 | ✓ |
1588v2/PTP with port-based timestamps (both for frequency and time, also known as PTP pure mode) | — 3 | ✓ 4 | ✓ 4 | ✓ 5 | |
1588v2/PTP with port-based timestamps (time only with SyncE used for frequency recovery, also known as PTP hybrid mode) | ✓ | ✓ | ✓ | ✓ | |
- Supported on non-ETR and ETR variants
- Only supported on fixed copper ports
- Not recommended for use
- Ordinary clock (slave) and boundary clock are supported on all variants (non-ETR and ETR)
- Ordinary clock (slave) and boundary clock are supported
Notes:
5.4.3. Synchronization Status Messages (SSM)
| Note: Synchronous status messages are supported on devices that support Synchronous Ethernet. |
SSM allows the synchronization distribution network to determine the quality level of the clock sourcing a specific synchronization trail and also allows a network element to select the best of multiple input synchronization trails. SSMs are defined for various transport protocols (including SONET/SDH, T1/E1, and Synchronous Ethernet), for interaction with office clocks (such as BITS or SSUs) and embedded network element clocks.
SSM allows equipment to autonomously provision and reconfigure (by reference switching) their synchronization references, while helping to avoid the creation of timing loops. These messages are particularly useful for synchronization re-configurations when timing is distributed in both directions around a ring.
5.4.4. Synchronous Ethernet
Traditionally, Ethernet-based networks employ a physical layer transmitter clock derived from an inexpensive +/-100ppm crystal oscillator and the receiver locks onto it. Because data is packetized and can be buffered, there is no need for long-term frequency stability or for consistency between frequencies of different links.
Synchronous Ethernet is a variant of the line timing that derives the physical layer transmitter clock from a high-quality frequency reference, replacing the crystal oscillator with a frequency source traceable to a primary reference clock. This change is transparent to the other Ethernet layers and does not affect their operation. The receiver at the far end of the link is locked to the physical layer clock of the received signal, and ensures access to a highly accurate and stable frequency reference. In a manner analogous to conventional hierarchical master-slave network synchronization, this receiver can lock the transmission clock of other ports to this frequency reference, and establish a fully time-synchronous network.
Unlike methods that rely on sending timing information in packets over an unclocked physical layer, Synchronous Ethernet is not affected by impairments introduced by higher levels of networking technology (packet loss, packet delay variation). The frequency accuracy and stability in Synchronous Ethernet typically exceeds networks with unsynchronized physical layers.
Synchronous Ethernet allows operators to gracefully integrate existing systems and future deployments into a conventional industry-standard synchronization hierarchy. The concept is analogous to SONET/SDH system timing capabilities. The operator can select any (optical) Ethernet port as a candidate timing reference. The recovered timing from this port is used to time the system (for example, the CPM will lock to this provisioned reference selection). The operator then can ensure that all system output is locked to a stable traceable frequency source.
The use of synchronous Ethernet as a candidate reference and for distribution of recovered reference is supported on the 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-D ETR platforms. It is not supported on the 7210 SAS-D.
Synchronous Ethernet using fiber Ethernet ports, including 10G ports (if available), is supported on the 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, 7210 SAS-K 3SFP+ 8C, and 7210 SAS-D ETR platforms.
| Note:
|
Fixed copper ports using Synchronous Ethernet can be used as a candidate reference (Master) or for distribution of recovered reference (Slave). If the port is a fixed copper Ethernet port and in 1000BASE-T mode of operation, there is a dependency on the 802.3 link timing for the synchronous Ethernet functionality (refer to ITU-T G.8262). The 802.3 standard link master-slave timing states must align with the desired direction of synchronous Ethernet timing flow. When a fixed copper Ethernet port is specified as an input reference for the node or when it is removed as an input reference for the node, 802.3 link autonegotiation is triggered to ensure that the link timing aligns correctly.
The SSM of synchronous Ethernet uses an Ethernet OAM PDU that uses the slow protocol subtype. For a complete description of the format and processing, refer to ITU-T G.8264.
5.4.4.1. Clock Source Quality Level Definitions
This section describes the clock source quality levels identified for tracking network timing flow in accordance with the network deployment options defined in Recommendation G.803 and G.781. The Option I network is developed on the original European SDH model; Option II network is a network developed on the North American SONET model.
In addition to the QL values received over SSM of an interface, the standards define the following additional codes for internal use.
- QL INVx is generated internally by the system if and when an unallocated SSM value is received, where x represents the binary value of this SSM. Within the SR OS, these independent values are assigned as the single value QL-INVALID.
- QL FAILED is generated internally by the system if and when the terminated network synchronization distribution trail is in the signal fail state.
The internal quality level of QL-UNKNOWN is used to differentiate from a received QL-STU code, but is equivalent for the purposes of QL selection.
Table 26 and Table 27 list the synchronization message coding and source priorities for SSM values received and transmitted on the port.
Table 26: Synchronization Message Coding and Source Priorities – SSM Received
SSM Value Received on Port | Internal Relative Quality Level | |||
SDH Interface SyncE Interface in SDH Mode | SONET Interface SyncE Interface in SONET Mode | E1 Interface | T1 Interface (ESF) | |
0010 (prc) | 0001 (prs) | 0010 (prc) | 00000100 11111111 (prs) | 1. Best quality |
0000 (stu) | 00001000 11111111 (stu) | 2. | ||
0111 (st2) | 00001100 11111111 (ST2) | 3. | ||
0100 (ssua) | 0100 (tnc) | 0100 (ssua) | 01111000 11111111 (TNC) | 4. |
1101 (st3e) | 01111100 11111111 (ST3E) | 5. | ||
1000 (ssub) | 1000 (ssub) | 6. | ||
1010 (st3/eec2) | 00010000 11111111 (ST3) | 7. | ||
1011 (sec/eec1) | 1011 (sec) | 8. Lowest quality qualified in QL-enabled mode | ||
1100 (smc) | 00100010 11111111 (smc) | 9. | ||
00101000 11111111 (st4) | 10. | |||
1110 (pno) | 01000000 11111111 (pno) | 11. | ||
1111 (dnu) | 1111 (dus) | 1111 (dnu) | 00110000 11111111 (dus) | 12. |
Any other | Any other | Any other | N/A | 13. QL_INVALID |
14. QL-FAILED | ||||
15. QL-UNC | ||||
Table 27: Synchronization Message Coding and Source Priorities – SSM Transmitted
Internal Relative Quality Level | SSM Values to be Transmitted by Interface of Type | |||
SDH Interface SyncE Interface in SDH Mode | SONET Interface SyncE Interface in SONET Mode | E1 Interface | T1 Interface (ESF) | |
1. Best quality | 0010 (prc) | 0001 (PRS) | 0010 (prc) | 00000100 11111111 (PRS) |
2. | 0100 (ssua) | 0000 (stu) | 0100 (ssua) | 00001000 11111111 (stu) |
3. | 0100 (ssua) | 0111 (st2) | 0100 (ssua) | 00001100 11111111 (st2) |
4. | 0100 (ssua) | 0100 (tnc) | 0100 (ssua) | 01111000 11111111 (tnc) |
5. | 1000 (ssub) | 1101 (st3e) | 1000 (ssub) | 01111100 11111111 (st3e) |
6. | 1000 (ssub) | 1010 (st3/eec2) | 1000 (ssub) | 00010000 11111111 (st3) |
7. | 1011 (sec/eec1) | 1010 (st3/eec2) | 1011 (sec) | 00010000 11111111 (st3) |
8. Lowest quality qualified in QL-enabled mode | 1011 (sec/ eec1) | 1100 (smc) | 1011 (sec) | 00100010 11111111 (smc) |
9. | 1111 (dnu) | 1100 (smc) | 1111 (dnu) | 00100010 11111111 (smc) |
10. | 1111 (dnu) | 1111 (dus) | 1111 dnu | 00101000 11111111 (st4) |
11. | 1111 (dnu) | 1110 (pno) | 1111 (dnu) | 01000000 11111111 (pno) |
12. | 1111 (dnu) | 1111 (dus) | 1111 (dnu) | 00110000 11111111 (dus) |
13. QL_INVALID | 1111 (dnu) | 1111 (dus) | 1111 (dnu) | 00110000 11111111 (dus) |
14. QL-FAILED | 1111 (dnu) | 1111 (dus) | 1111 (dnu) | 00110000 11111111 (dus) |
15. QL-UNC | 1011 (sec/eec1) | 1010 (st3/eec2) | 1011 (sec) | 00010000 11111111 (st3) |
5.4.5. IEEE 1588v2 PTP
Note:
|
PTP is a timing-over-packet protocol defined in the IEEE 1588v2 standard 1588 PTP 2008.
PTP may be deployed as an alternative timing-over-packet option to ACR. PTP provides the capability to synchronize network elements to a Stratum-1 clock or primary reference clock (PRC) traceable source over a network that may or may not be PTP-aware. PTP has several advantages over ACR. It is a standards-based protocol, has lower bandwidth requirements, can transport both frequency and time, and can potentially provide better performance.
The following is a list of the four basic types of PTP devices:
- ordinary clock
- boundary clock
- end-to-end transparent clock
- peer-to-peer transparent clock
The 7210 SAS supports the ordinary clock in slave mode and the boundary clock. The boundary clock and ordinary clock slave can be used for both frequency and time distribution. The 7210 SAS does not support ordinary clock in master mode, end-to-end transparent clock, or peer-to-peer transparent clock.
Figure 24 shows how the 7210 SAS communicates with peer 1588v2 clocks.These peers can be ordinary clock slaves or boundary clocks. The communication can be based on either unicast IPv4 sessions transported through IP interfaces or Ethernet multicast PTP packets transported through an Ethernet port.
Table 28 describes IP/UDP unicast and multicast support for the 7210 SAS platforms.
Table 28: IP/UDP Unicast and Ethernet Multicast Support
Protocol | IP/UDP Unicast | Ethernet Multicast |
7210 SAS-D | Yes 1 | No |
7210 SAS-Dxp | No | No |
7210 SAS-K 2F1C2T | Yes | No |
7210 SAS-K 2F6C4T | Yes | Yes |
7210 SAS-K 3SFP+ 8C | Yes | Yes |
- Supported on ETR variant only
Note:
For unicast IP sessions, there are two types of peers: configured and discovered. The 7210 SAS operating as an ordinary clock slave or as a boundary clock must have configured peers for each PTP neighbor clock from which it might accept synchronization information. The 7210 SAS initiates unicast sessions with all configured peers. A 7210 SAS operating as a boundary clock will accept unicast session requests from external peers. If the peer is not a configured peer, it is considered a discovered peer. The 7210 SAS can deliver synchronization information toward discovered peers (that is, slaves).
For Ethernet multicast operation, the node listens for and transmits PTP messages using the configured multicast MAC address. Neighbor clocks are discovered via the reception of messages through an enabled Ethernet port. Figure 25 shows how the 7210 SAS supports only one neighbor PTP clock connecting into a single port.
The 7210 SAS does not allow for simultaneous PTP operations using both unicast IPv4 and Ethernet multicast. A change of profile to G.8275.1 or from G.8275.1 to another profile requires a reboot of the node.
Figure 24 shows the relationship of various neighbor clocks using unicast IP sessions to communicate with a 7210 SAS configured as a boundary clock with two configured peers.
Figure 24: Peer Clocks
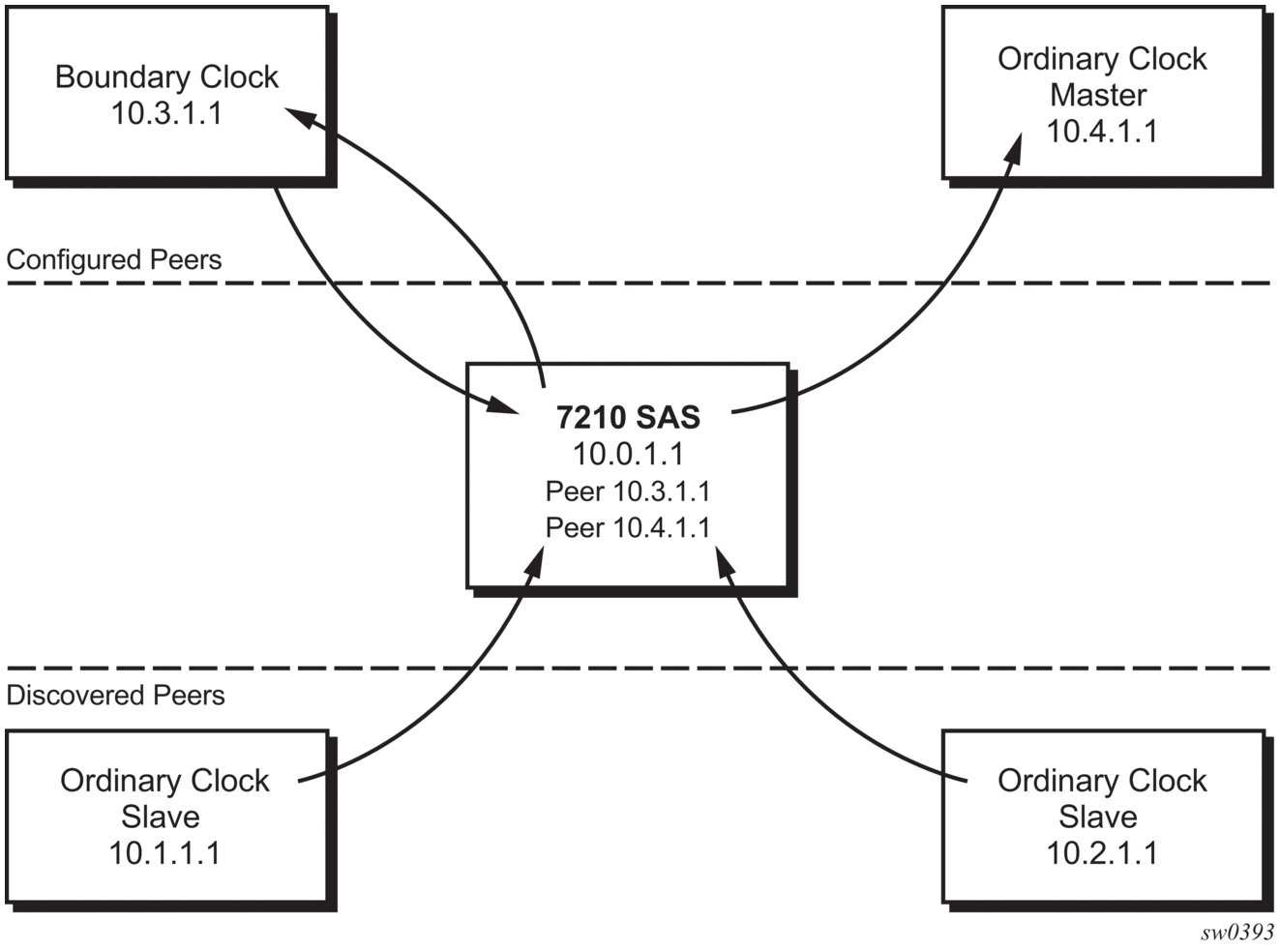
Figure 25 shows the relationship of various neighbor clocks using multicast Ethernet sessions to a 7210 SAS configured as a boundary clock.
Figure 25: Ethernet Multicast Ports
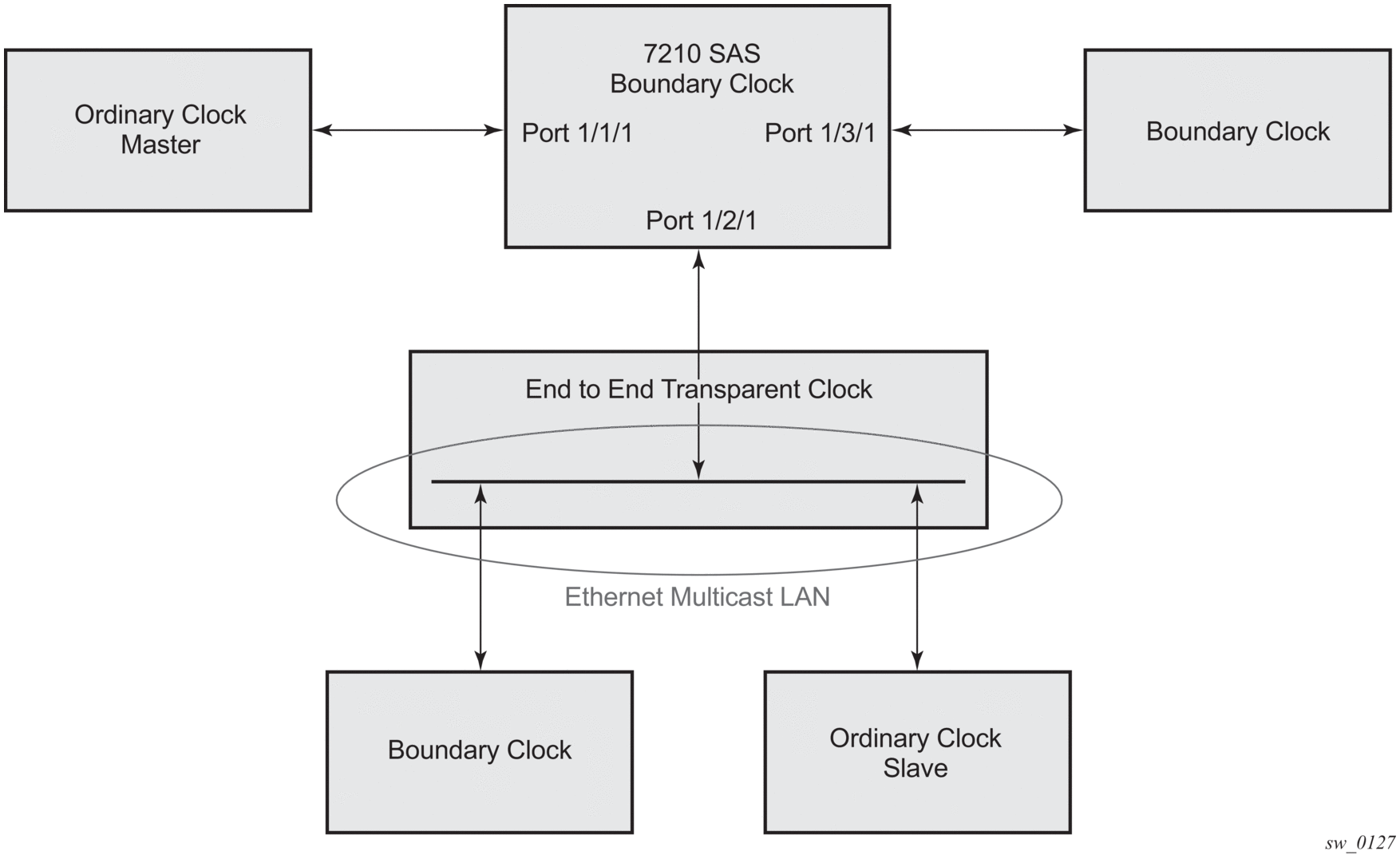
| Note: 7210 SAS platforms do not support the ordinary clock master configuration. |
The IEEE 1588v2 standard includes the concept of PTP profiles. These profiles are defined by industry groups or standards bodies that define the use of IEEE 1588v2 for specific applications.
The 7210 SAS currently supports three profiles:
- IEEE 1588v2 (default profile)
- ITU-T Telecom profile (G.8265.1)
- ITU-T Telecom profile for time with full timing support (G.8275.1), on 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C devices only
When a 7210 SAS receives Announce messages from one or more configured peers or multicast neighbors, it executes a Best Master Clock Algorithm (BMCA) to determine the state of communication between itself and the peers. The system uses the BMCA to create a hierarchical topology, allowing the flow of synchronization information from the best source (the grandmaster clock) out through the network to all boundary and slave clocks. Each profile has a dedicated BMCA.
If the profile setting for the clock is ieee1588-2008, the precedence order for the best master selection algorithm is as follows:
- priority1
- clock class
- clock accuracy
- PTP variance (offsetScaledLogVariance)
- priority2
- clock identity
- steps removed from the grandmaster
Table 29 describes how the 7210 SAS sets its local parameters.
Table 29: Local Clock Parameters When Profile is Set to ieee1588-2008
Parameter | Value |
clockClass | 248 — the 7210 SAS is configured as a boundary clock 255 — the 7210 SAS is configured as an ordinary clock slave |
clockAccuracy | FE — unknown |
offsetScaledLogVariance | FFFF — not computed |
clockIdentity | Chassis MAC address following the guidelines of section 7.5.2.2.2 of IEEE 1588-2008 |
If the profile setting for the clock is itu-telecom-freq (ITU G.8265.1 profile), the precedence order for the best master selection algorithm is the following:
- clock class
- PTSF (Packet Timing Signal Fail) - Announce Loss (miss 3 Announce messages or do not get an Announce message for 6 seconds)
- priority
Table 30 describes how the 7210 SAS sets its local parameters.
Table 30: Local Clock Parameters When Profile is Set to itu-telecom-freq
Parameter | Value |
clockClass | 80-110 — value corresponding to the QL out of the central clock of the 7210 SAS as per Table 1/G.8265.1 255 — the 7210 SAS is configured as an ordinary clock slave |
The ITU-T profile is for use in environments with only ordinary clock masters and slaves for frequency distribution. The default profile should be used for all other cases.
If the profile setting for the clock is g8275dot1-2014, the precedence order for the best master selection algorithm is very similar to that used for the default profile. It ignores the priority1 parameter, includes a localPriority parameter, and includes the ability to force a port to never enter the slave state (master-only). The precedence is as follows:
- clock class
- clock accuracy
- PTP variance (offsetScaledLogVariance)
- priority2
- localPriority
- clock identity
- steps removed from the grandmaster
Table 31 describes how the 7210 SAS sets its local parameters.
Table 31: Local Clock Parameters When Profile is Set to g8275dot1-2014
Parameter | Value |
clockClass | 165 — the 7210 SAS is configured as a boundary clock and the boundary clock was previously locked to a grandmaster with a clock class of 6 248 — the 7210 SAS is configured as a boundary clock 255 — the 7210 SAS is configured as an ordinary clock slave |
clockAccuracy | FE — unknown |
offsetScaledLogVariance | FFFF — not computed |
clockIdentity | Chassis MAC address following the guidelines of section 7.5.2.2.2 of IEEE 1588-2008 |
The 7210 SAS can support a limited number of configured peers (possible master or neighbor boundary clocks) and a limited number of discovered peers (slaves).These peers use the unicast negotiation procedures to request service from the 7210 SAS clock. A neighbor boundary clock counts for two peers (both a configured and a discovered peer) toward the maximum limit.
On the 7210 SAS-D ETR, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C there are limits on the number of slaves enforced in the implementation for unicast and multicast PTP slaves. Contact your Nokia technical support representative for information about the specific unicast message limits related to PTP.
When PTP is configured, the PTP load must be monitored to ensure that the load does not exceed the capabilities (configured values) to ensure that sufficient CPU processing cycles are available for PTP. There are several commands that can be used for this monitoring, including:
- show system cpu identifies the load of the PTP software process. If the “capacity usage” reaches 100%, the PTP software process on the 7210 SAS is at its limit of transmitting and/or receiving PTP packets.
Because the user cannot control the number of PTP messages received by the 7210 SAS over its Ethernet ports, the following statistics commands can be used to identify the source of the message load:
- show system ptp statistics displays aggregate packet rates
- show system ptp port and show system ptp port port-id [detail] display received packet rates
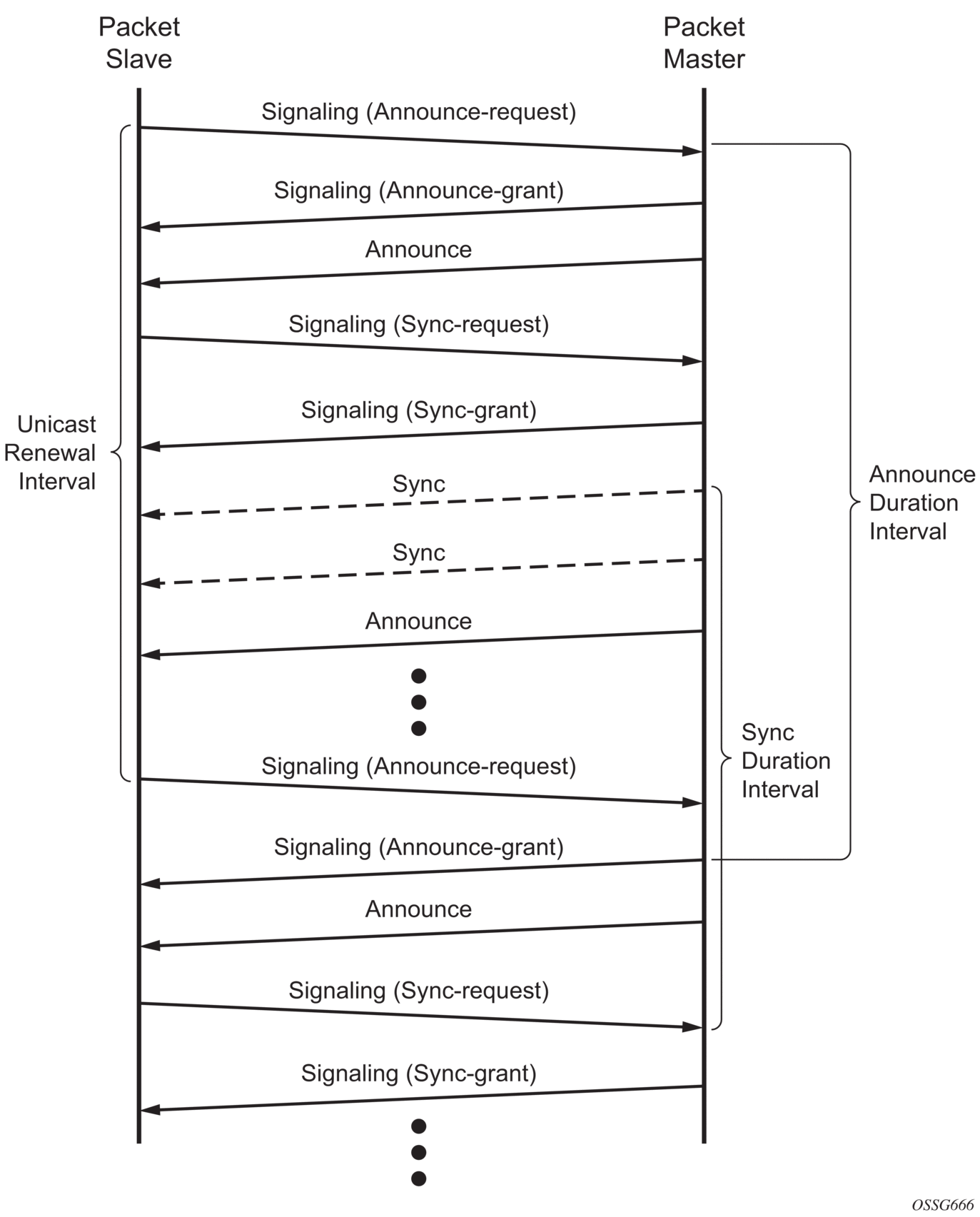
Figure 26 shows the unicast negotiation procedure performed between a slave and a peer clock that is selected to be the master clock. The slave clock will request Announce messages from all peer clocks but only request Sync and Delay_Resp messages from the clock selected to be the master clock.
Figure 26: Messaging Sequence Between the PTP Slave Clock and PTP Master Clocks
5.4.5.1. PTP Clock Synchronization
The IEEE 1588v2 standard synchronizes the frequency and time from a master clock to one or more slave clocks over a packet stream. This packet-based synchronization can be over unicast IP/UDP unicast or Ethernet multicast.
As part of the basic synchronization timing computation, event messages are defined for synchronization messaging between the PTP slave clock and PTP master clock. A one-step or two-step synchronization operation can be used; the two-step operation requires a follow-up message after each synchronization message.
| Note: The 7210 SAS-D ETR supports only two-step master port operation. All platforms can operate slave ports that receive from a one-step or two-step master port. |
During startup, the PTP slave clock receives synchronization messages from the PTP master clock before a network delay calculation is made. Prior to any delay calculation, the delay is assumed to be zero. A drift compensation is activated after a number of synchronization message intervals occur. The expected interval between the reception of synchronization messages is user-configurable.
Figure 27 shows the basic synchronization timing computation between the PTP slave clock and PTP best master, as well as the offset of the slave clock referenced to the best master signal during startup.
Figure 27: PTP Slave Clock and Master Clock Synchronization Timing Computation
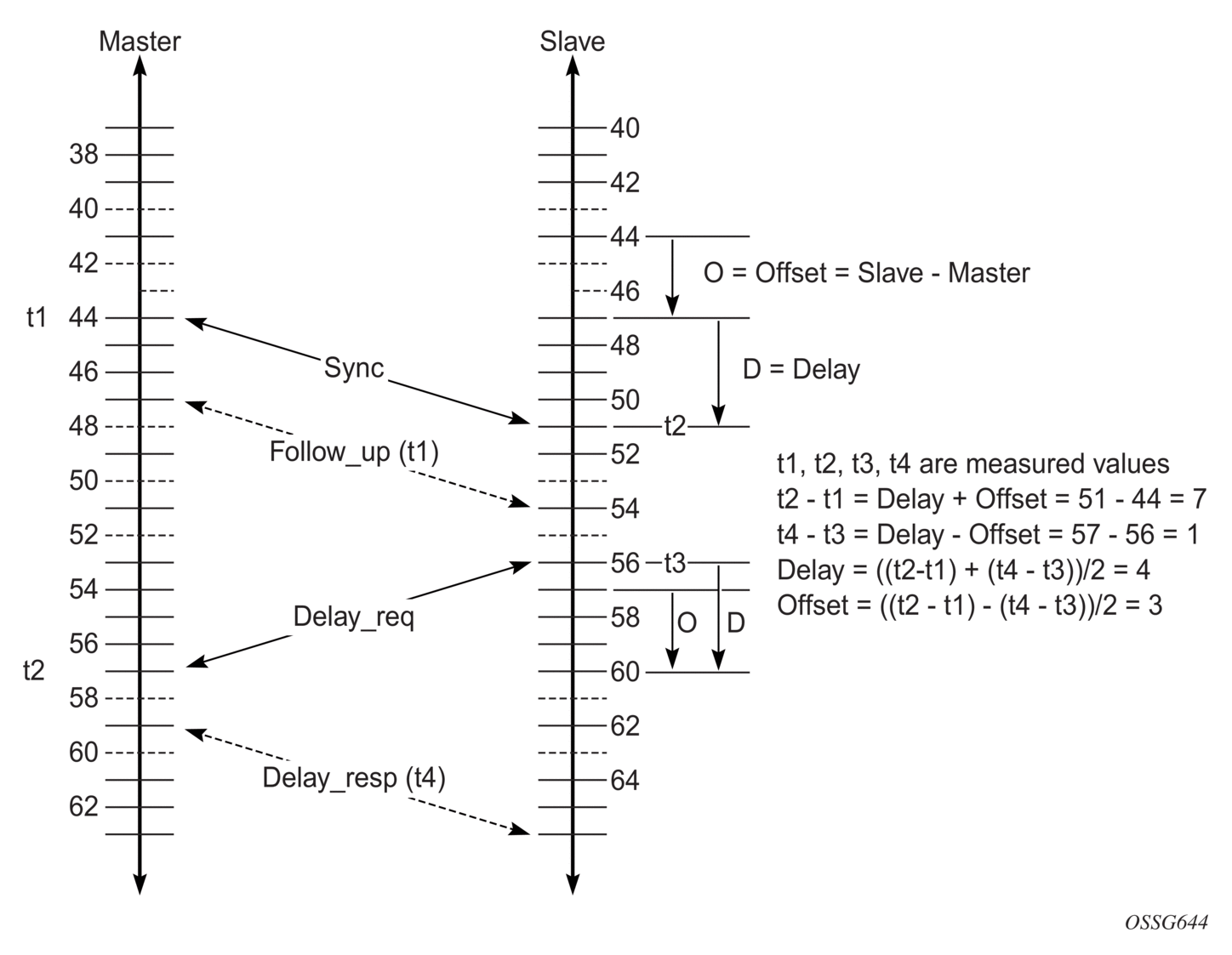
When the IEEE 1588v2 standard is used for distribution of a frequency reference, the slave calculates a message delay from the master to the slave based on the timestamps exchanged. A sequence of these calculated delays contains information about the relative frequencies of the master clock and slave clock, but also includes a noise component related to the PDV experienced across the network. The slave must filter the PDV effects to extract the relative frequency data and then adjust the slave frequency to align with the master frequency.
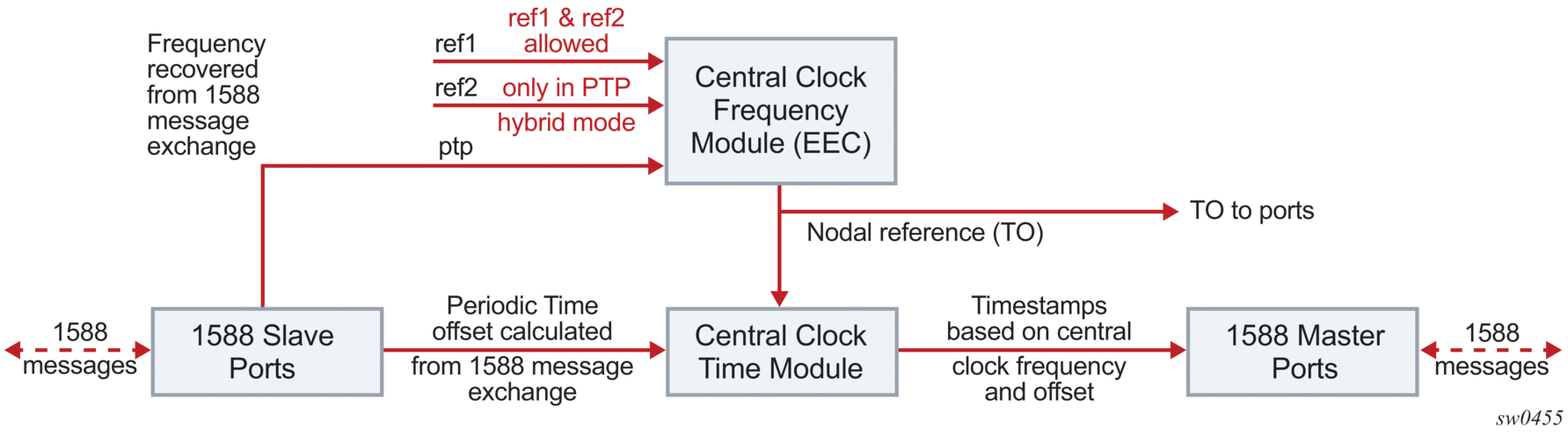
When the IEEE 1588v2 standard is used for distribution of time, the 7210 SAS calculates the offset between the 7210 SAS time base and the external master clock time base based on the four timestamps exchanged. The 7210 SAS determines the offset adjustment, and between these adjustments, it maintains the progression of time using the frequency from the central clock of the node. This allows time to be maintained using a Synchronous Ethernet input source even if the IEEE 1588v2 communications fail. When using IEEE 1588v2 for time distribution, the central clock should, at a minimum, have the PTP input reference enabled.
Figure 28 shows the logical model for using PTP/1588 for network synchronization.
Figure 28: Logical Model for Using PTP/1588 for Network Synchronization on 7210 SAS Platforms
5.4.5.2. Performance Considerations
Although IEEE 1588v2 can be used on a network that is not PTP-aware, the use of PTP-aware network elements (boundary clocks) within the packet-switched network improves synchronization performance by reducing the impact of PDV between the grand master clock and the slave clock. In particular, when IEEE 1588v2 is used to distribute high-accuracy time, such as for mobile base station phase requirements, the network architecture requires the deployment of PTP awareness in every device between the grandmaster and the mobile base station slave.
In addition, performance is also improved by the removal of any PDV caused by internal queuing within the boundary clock or slave clock. This is accomplished with hardware that is capable of port-based timestamping, which detects and timestamps the IEEE 1588v2 packets at the Ethernet interface.
5.4.5.3. PTP Capabilities
PTP messages are supported through IPv4 unicast with a fixed IP header size. Table 32 describes the supported message rates for slave and master states. The ordinary clock can only be used in the slave state. The boundary clock can be in both of these states.
Table 32: Support Message Rates for Slave and Master Clock States
Support Message | Slave Clock | Master Clock | |
Request Rate | Grant Rate | ||
Min | Max | ||
Announce | 1 packet every 2 seconds | 1 packet every 2 seconds | 1 packet every 2 seconds |
Sync | User-configurable with an option to configure 8/16 packets per second | 8 packets/second | 16 packets/second |
Delay_Resp | User-configurable with an option to configure 8/16 packets per second | 8 packets/second | 16 packets/second |
Duration | 300 seconds | 1 second | 1000 seconds |
State and statistics data for each master clock are available to assist in the detection of failures or unusual situations.
5.4.5.4. PTP Ordinary Slave Clock for Frequency
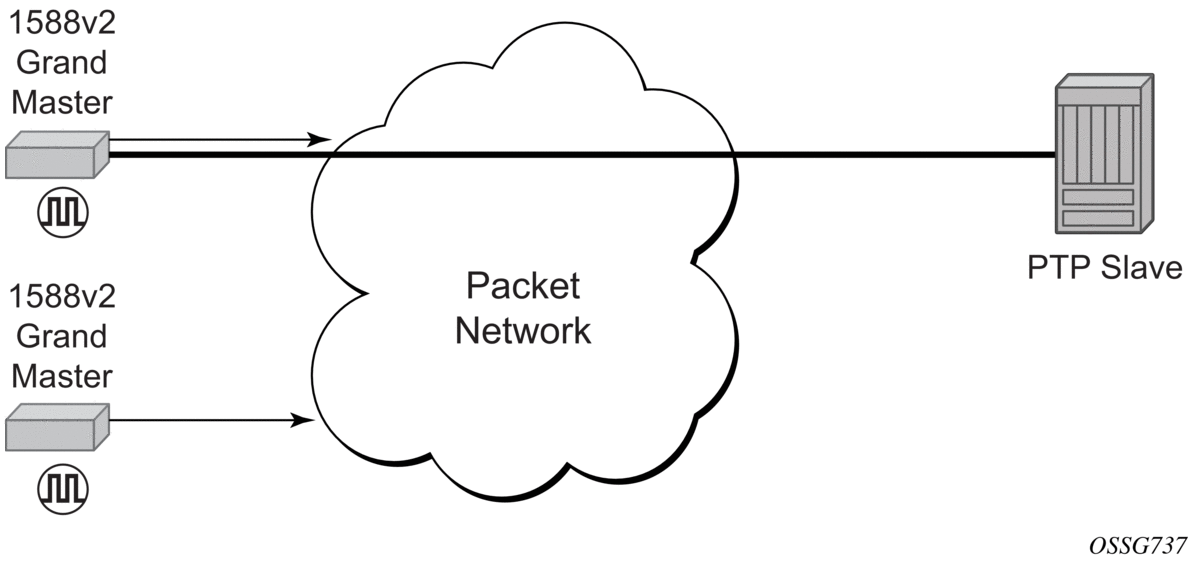
Traditionally, only clock frequency is required to ensure smooth transmission in a synchronous network. The PTP ordinary clock with slave capability on the 7210 SAS provides another option to reference a Stratum-1 traceable clock across a packet switched network. The recovered clock can be referenced by the internal SSU and distributed to all slots and ports.
Figure 29 shows a PTP ordinary slave clock network configuration.
Figure 29: Slave Clock
5.4.6. PTP Boundary Clock for Frequency and Time
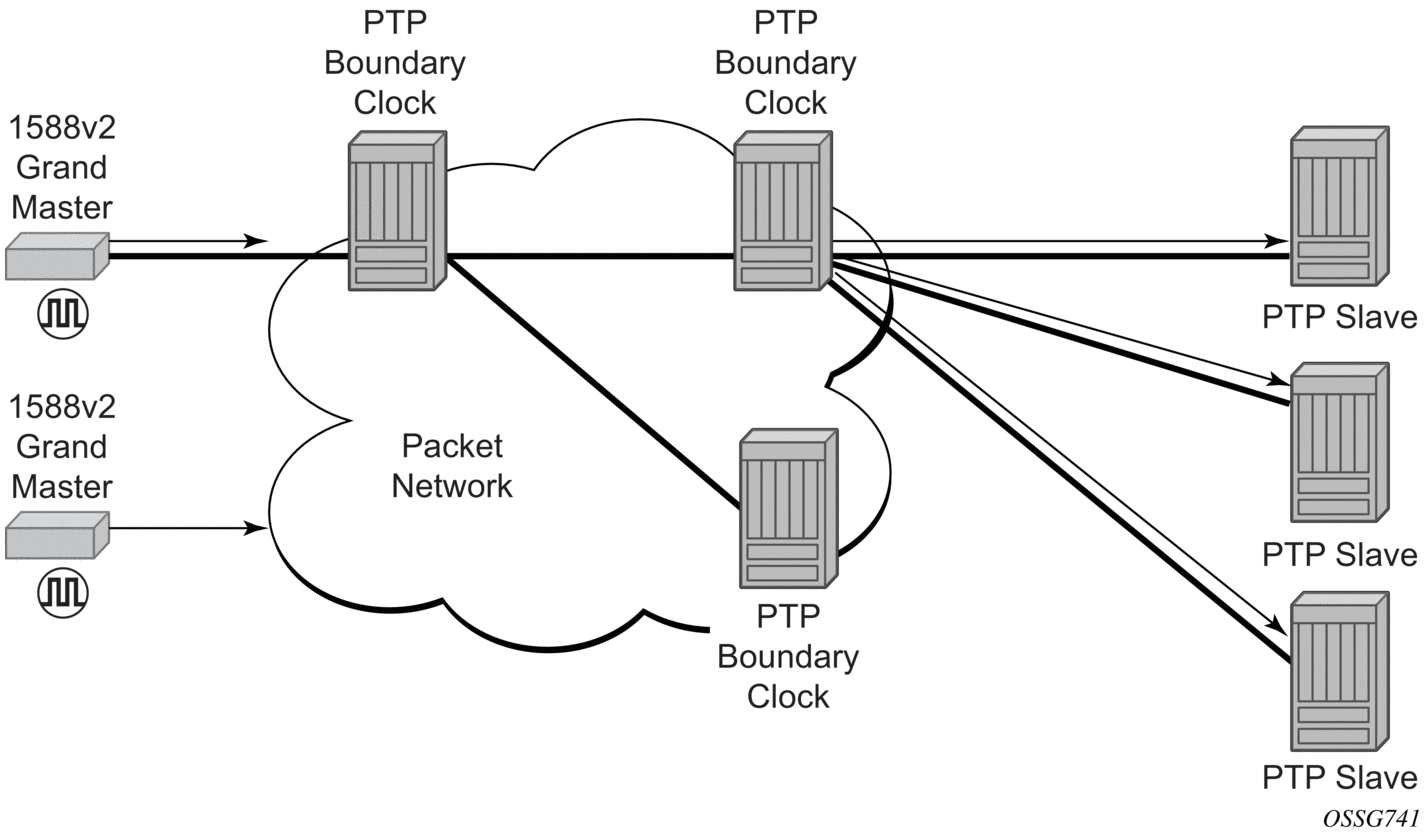
Although IEEE 1588v2 can function across a packet network that is not PTP-aware, performance may be unsatisfactory and unpredictable. PDV across the packet network varies with the number of hops, link speeds, utilization rates, and the inherent behavior of routers. By using routers with boundary clock functionality in the path between the grandmaster clock and the slave clock, one long path over many hops is split into multiple shorter segments, allowing better PDV control and improved slave performance. This allows PTP to function as a valid timing option in more network deployments and allows for better scalability and increased robustness in certain topologies, such as rings.
Boundary clocks can simultaneously function as a PTP slave of an upstream grandmaster (ordinary clock) or boundary clock, and as a PTP master of downstream slaves (ordinary clock) and/or boundary clocks. The time scale recovered in the slave side of the boundary clock is used by the master side of the boundary clock. This allows time across the boundary clock.
Figure 30 shows routers with boundary clock functionality in the path between grandmaster and the slave clock.
Figure 30: Boundary Clock
5.4.7. Configuration Guidelines and Restrictions for PTP
- The PTP slave capability is available on all the ports on the 7210 SAS-D ETR.
- The 7210 SAS-D ETR, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C use CPU processing cycles for frequency and time recovery.
- On the 7210 SAS-D ETR, Nokia highly recommends that PTP be used only in hybrid mode. Hybrid mode allows users to use reduced PTP packet rates and to scale better.
- On the 7210 SAS-D ETR, use of both PTP and SyncE as a reference simultaneously is not allowed. Either PTP or SyncE can be configured as a reference but not both at the same time.
- On 7210 SAS devices, only a single profile (IEEE 1588v2, G.8265.1, or G.8275.1) can be enabled for all PTP communications (both toward its master and slaves connected to it) at a time.
- The PTP G.8275.1 profile is only supported on the 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C. When using the profile, the following restrictions apply.
- The delay and sync requests are set to 16 pps by default and are not configurable.
- The announce rate is set to 8 pps by default and is not configurable.
- A change of profile to G.8275.1 or from G.8275.1 to another profile requires a reboot of the node.
- Only a single multicast slave is supported per port.
- PTP with Ethernet encapsulation is only supported with the G.8275.1 profile.
- PTP over IP encapsulation is not supported with the G.8275.1 profile. It is only supported with the IEEE 1588v2 and G.8265.1 profiles.
- PTP slave capability is available on all ports on the 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C.
- When changing the clock-type to or from a boundary clock on the 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C, the node must be rebooted for the change to take effect. Ensure that measures are taken to minimize service disruption during the reboot process.
- On the 7210 SAS-K 2F6C4T and 7210 SAS-K 3SFP+ 8C, to enable PTP hybrid mode, the user must execute the command config>system>ptp>clock>freq-source ssu. To enable pure PTP mode, the user must execute the command config>system>ptp>clock>freq-source ptp. A change of value from ssu to ptp, or vice-versa, requires a reboot of the node after the configuration changes are saved in order for the change to take effect.
- On the 7210 SAS-D ETR, 7210 SAS-K 2F1C2T, 7210 SAS-K 2F6C4T, and 7210 SAS-K 3SFP+ 8C, port-based time-stamping is enabled for all PTP packets by default when PTP is enabled. When PTP is enabled, PTP packets are not forwarded transparently through the node, regardless of the service used and whether PTP is configured as a system clock reference. If PTP is enabled, to enable transparent PTP forwarding again, disable PTP, save the configuration, and reboot the node.
5.4.8. Configuration to Change Reference from SyncE to PTP on 7210 SAS-D ETR
The following are the configuration steps to change reference from SyncE to PTP. This procedure is required only on 7210 SAS-D ETR nodes.
- To configure standalone PTP as a reference, run the following commands:configure >system >ptp >no shutdownconfig> system> sync-if-timing> beginptpno shutdownexitref-order ptp [Must be configured]config> system> sync-if-timing> commitAfter the preceding commands are run, the frequency and time are provided by PTP only.
- To change the reference to syncE, run the following commands:config> system> sync-if-timing> beginptpshutdownexitconfig> system> sync-if-timing> commitconfig> system> sync-if-timing> beginref1source-port 1/1/10no shutdownexitref2source-port 1/1/11no shutdownexitref-order ref1 ref2 --------> Or, the ref-order you want [But Must be configured]revert ---------------------> If you want ref-order you have setup to takeeffectql-selection -------------------> Optional, if we need Quality to be considered.config> system> sync-if-timing> commitAfter the preceding commands are run, the frequency is provided by SyncE and TOD is provided by PTP [configure>system>ptp>no shutdown]. This is called PTP Hybrid mode.
- To revert to standalone PTP from SyncE, run the following commands:config> system> sync-if-timing> beginref1source-port 1/1/10 --------------------> Not Required if port is alreadyconfigured, but in admin down stateshutdownexitref2source-port 1/1/11 --------------------> Not Required if port is alreadyconfigured, but in admin down stateshutdownexitconfig> system> sync-if-timing> commitconfig> system> sync-if-timing> beginptpno shutdownexitref-order ptp [Must be configured]config> system> sync-if-timing> commitNow the frequency and time are provide by PTP (config>system>ptp>no shutdown) only. This is standalone PTP mode.
5.5. Link Layer Discovery Protocol (LLDP)
The IEEE 802.1ab Link Layer Discovery Protocol (LLDP) is a unidirectional protocol that uses the MAC layer to transmit specific information about the capabilities and status of the local device. The LLDP can send as well as receive information from a remote device stored in the related MIB (or MIBs).
The LLDP does not contain a mechanism to solicit information received from other LLDP agents or to confirm the receipt of information. However, LLDP provides the flexibility to enable a transmitter and receiver separately, and the following LLDP agent configurations are allowed:
- only transmit information
- only receive information
- transmit and receive information
The information fields in each LLDP frame are contained in an LLDP Data Unit (LLDPDU) as a sequence of variable length information elements. Each information element includes Type, Length, and Value fields (TLVs).
- Type indicates the nature of information being transmitted.
- Length indicates the length of the information string in octets.
- Value is the actual information that is transmitted. (For example, a binary bit map or an alphanumeric string that can contain one or more fields).
Each LLDPDU contains four mandatory TLVs and optional TLVs selected by the Network Management. The following is the format of an LLDPDU:
- Chassis ID TLV
- Port ID TLV
- Time To Live (TTL) TLV
- zero or more optional TLVs, depending on the maximum size of the LLDPDU allowed
- End of LLDPDU TLV
A concatenated string formed by the Chassis ID TLV and the Port ID TLV is used by a recipient to identify an LLDP port or agent. The combination of the Port ID and Chassis ID TLVs remains unchanged until the port or agent is operational.
The TTL field of a Time-To-Live TLV can be a zero or non-zero value. A zero TTL field value notifies the receiving LLDP agent to immediately discard all information related to sending LLDP agent. A non-zero TTL field value indicates the time duration for which the receiving LLDP agent should retain the information of the sending LLDP agent. The receiving LLDP agent discards all information related to the sending LLDP agent after the time interval indicated in the TTL field is complete.
| Note: A TTL zero value is used to signal that the sending LLDP port has initiated a port shutdown procedure. |
The End Of LLDPDU TLV indicates the end of the LLDPDU.
The following information is included in the protocol as defined by the IEEE 802.1ab standard.
- Connectivity and management information about the local station to adjacent stations on the same IEEE 802 LAN is advertised.
- Network management information from adjacent stations on the same IEEE 802 LAN is received.
- It operates with all IEEE 802 access protocols and network media.
- Network management information schema and object definitions suitable for storing connection information about adjacent stations is established.
- It supports compatibility with a number of MIBs.
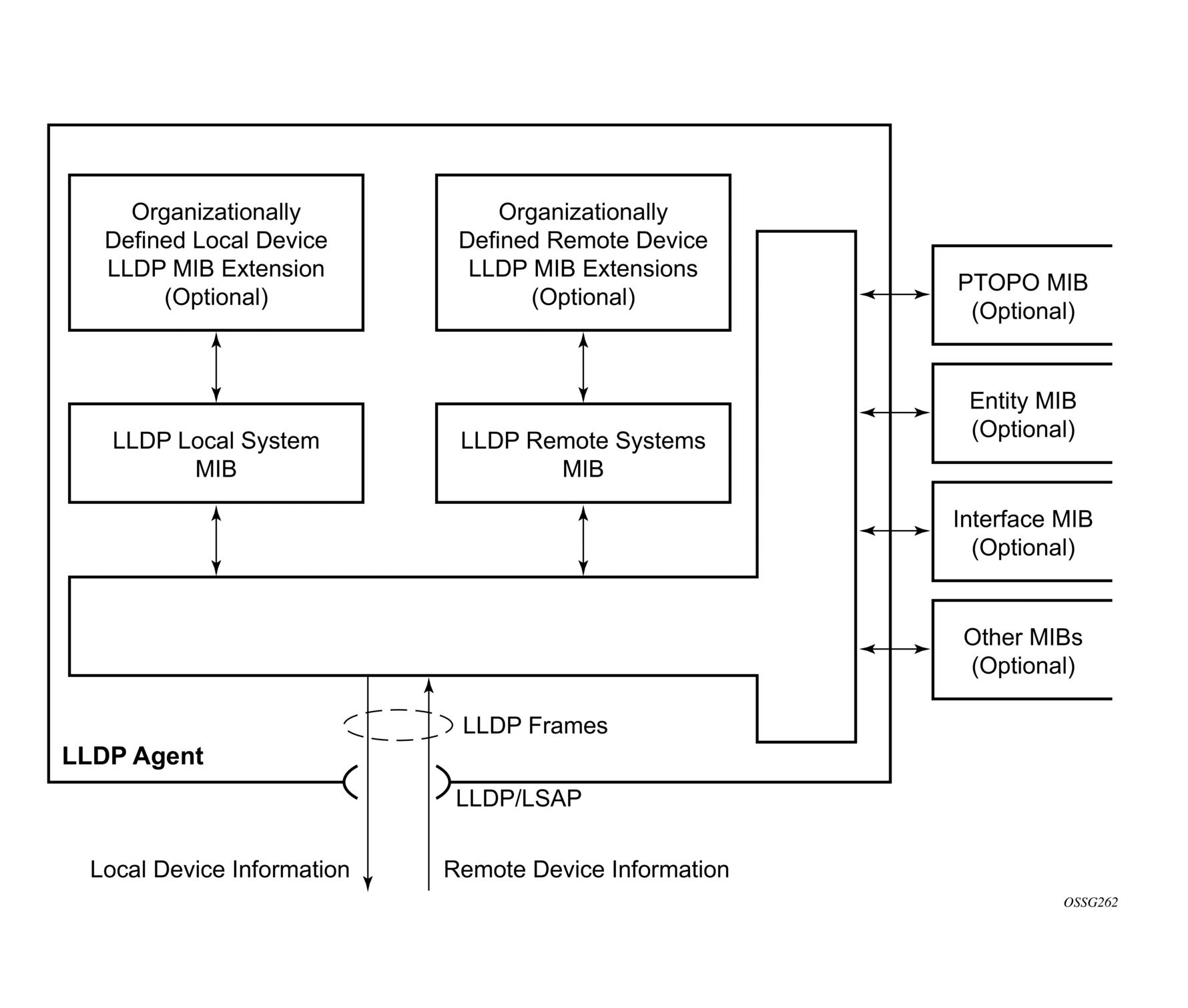
Figure 31 shows the LLDP internal architecture for a network node.
Figure 31: LLDP Internal Architecture for a Network Node
To detect and address network problems and inconsistencies in the configuration, the network operators can discover the topology information using LLDP. The standard-based tools address the complex network scenarios where multiple devices from different vendors are interconnected using Ethernet interfaces.
Figure 32 shows an MPLS network that uses Ethernet interfaces in the core, or as an access or handoff interface to connect to different kinds of Ethernet-enabled devices such as service gateway and routers, QinQ switches, DSLAMs, or customer equipment.
The topology information of the network in Figure 32 can be discovered if IEEE 802.1ab LLDP is running on each of the Ethernet interfaces in the network.
Figure 32: Customer Use Example For LLDP

5.6. System Resource Allocation
5.6.1. Allocation of Ingress Internal TCAM resources
The system statically allocates ingress TCAM resources for use by SAP ingress QoS classification, SAP ingress access control lists (ACLs), identifying and sending CFM OAM packets to CPU for local processing, and so on. The resource allocation is not user-configurable. With the introduction of new capabilities such as IPv6 classification, UP MEP support, and G8032-fast-flood, the static allocation of resources by software does not meet requirements of customer who need to use different features.
The user can allocate a fixed amount of resources per system for QoS, ACLs, CFM/Y.1731 MEPs, and other features. Of these, some parameters are boot-time and others are run-time. A change in the current value of the parameter that is designated boot-time needs a reboot of the node before the new value takes effect. Change in the current value of the parameter that is designated run-time takes effect immediately if the software determines resources are available for use to accommodate the change.
During bootup, the system reads the resource profile parameters and allocates resources to features in the order they appear in the configuration file.
Because resources are shared, the user must ensure that the sum total of such resources does not exceed the limit supported by the IMM or node. If the system determines that it cannot allocate the requested resources, the feature is disabled. For example, if the system determines that it cannot allocate resources for g8032-fast-flood, it disables the feature from use and G8032 eth-rings will not be able to use fast-flood mechanisms). Another example is the case where the system determines that it cannot allocate resources for IPv4-based SAP Ingress ACL classification, the system will not allow users to use IPv4-based SAP ingress ACL classification feature and fails the configuration when it comes upon the first SAP in the configuration file that uses an IPv4-based SAP ingress ACL policy.
For boot-time parameters, such as g8032-fast-flood-enable, the user must ensure that the configured services match the resources allocated. If the system determines that it cannot allocate resources to services, it fails the configuration file at the first instance where it encounters a command to which resources cannot be allocated. The available resources can be allocated to different features.
For ACL and QoS resources, the user has the option to allocate resources to limit usage per feature, regardless of the match criteria used. The sum of all resources used for different SAP ingress classification match-criteria is limited by the amount of resources allocated for SAP ingress classification. The user can also allocate resources by specific match criteria. The user can enable any supported match criteria and associate a fixed amount of resources with each match criteria in fixed sizes; the chunk size is dependent on the platform.
The system allocates resources based on the order of appearance in the configuration file, and fails any match criteria if the system does not have any more resources to allocate. In addition, the max keyword can be used to indicate that the system needs to allocate resources when they are first required, as long as the maximum amount of resources allocated for that feature is not exceeded or the maximum amount of resources available in the system is not exceeded. The 7210 SAS platforms allocate resources to each feature and match-criteria in fixed-size chunks.
The no form of the command disables the use of corresponding match criteria. During runtime, the command succeeds, if no SAPs are currently using the criteria. Similarly, reduction of resources from the current value to a lower value succeeds, if no SAPs are currently using the criteria.
If the system successfully runs the no command, it frees up resources used by the chunk or slice and make the resources, or the entire chunk/slice, available for use by other features. Before deallocating resources, the software checks if a service object is using the resource and fails the command if the object is in use. If resources are in use, they can be freed up by deleting a SAP, removing a policy association with a SAP, deleting a MEP, and so on. Some commands under the system resource-profile context do not take effect immediately and require a system reboot before the change occurs and resources are freed. The following is the handling of freed resources.
- If some entries in a slice are freed, they are made available for use by other SAPs using the same feature to which the chunk is allocated.
- If an entire chunk is freed, it is returned to the system free pool for possible use by other features.
The no form of the commands that are designated as boot-time does not take effect immediately. It takes effect after the reboot. Before reboot, it is the user’s responsibility to free up resources required for use by the feature that has been enabled to take effect after the reboot. Not doing so results in failure when the configuration file is executed on boot up.
Refer to the CLI and feature description chapters in the appropriate 7210 SAS platform user guide for more information about CLI commands and features that use system resource allocation.
5.6.2. Allocation of Egress Internal TCAM Resources
Before the introduction of new capabilities, such as IPv6 match criteria, the system allocated egress TCAM resources on bootup for use by different criteria in SAP egress access control lists (ACLs) and other purposes; the resource allocation was not user configurable. With the introduction of new capabilities, such as IPv6 match criteria in egress, the static allocation of resources by software may not meet customer requirements if they want to use different features. Therefore, to facilitate user configuration and resource allocation in accordance with user needs, the ingress internal TCAM resource allocation capabilities have been extended to include the egress internal TCAM resources.
For information about specific CLI commands and features that use system resource allocation, refer to the CLI command and feature descriptions in the appropriate 7210 SAS software user manuals.
| Note: The commands in the config>system>resource-profile context, which require a reboot to take effect, are read and implemented by the system only during bootup. These commands do not take effect if the exec command is used to run the configuration file. |
5.6.2.1. System Resource Allocation Examples
Note:
|
Example one:
In the preceding CLI example, the system performs the following actions.
- 3 chunks are allocated for use by the SAP ingress ACL entries.
- 1 chunk is allocated for use by SAP ingress ACL entries that use ipv4-criteria. The system fails the configuration when the number of ACL entries using ipv4-criteria exceeds the configured limit (that is, the system does not allocate in excess of the configured limit of 1 chunk).
- A chunk is allocated for use by SAP ingress ACL entries that use mac-criteria. After the max keyword is specified, the system allocates 1 chunk for use when an ingress ACL policy (with mac-criteria entries defined) is associated with a SAP. The system can allocate up to 2 chunks because the max keyword is used. More chunks are allocated when the user configures a SAP that uses mac-criteria and all entries in the allocated chunks are used up. The system fails the configuration if the number of ACL entries with mac-criteria exceeds the limit of 2 chunks allocated to SAP ingress ACL match (that is, the system does not allocate in excess of the configured limit of 3; up to 2 chunks of the configured 3 chunk limit are allocated to mac-criteria and 1 chunk is allocated to ipv4-criteria).
- The system fails a user attempt to use SAP ingress ACLs with IPv6 match criteria (and other combinations listed in the preceding list items), because the user has disabled these criteria.
Example 2:
In the preceding CLI example, the system performs the following actions.
- 3 chunks are allocated for use by the SAP ingress ACL entries. These resources are available for use with mac-criteria, ipv4-criteria and ipv6-64-bit match criteria.
- 1 chunk is allocated for use by SAP ingress ACL entries that use ipv4-criteria. The system fails the configuration if the number of ACL entries using ipv4-criteria exceeds the configured limit (that is, the system does not allocate more than the configured limit of 1 chunk).
- 1 chunk is allocated for use by SAP ingress ACL entries that use mac-criteria when the user associates an ingress ACL policy (with mac-criteria entries defined) with a SAP. Because the max keyword is used, the system can allocate more chunks, if a chunk is available for use.In this example, (assuming a SAP with an ingress ACL policy that uses ipv6-64-bit criteria is configured), as no additional chunks are available, mac-criteria cannot allocate more than 1 chunk (even if the max keyword is specified). The system fails the configuration if the number of ACL entries with mac-criteria exceeds the limit of 1 chunk allocated to SAP ingress ACL mac-criteria (that is, the system does not allocate more than the configured limit of 3 chunks = 1 for mac-criteria + for ipv4-criteria + 1 for ipv6-criteria).
- A chunk is allocated for use by SAP ingress ACL entries that use ipv6-64-bit criteria when the user associates an ingress ACL policy (with ipv6-64-bit-criteria entries defined) with a SAP. Because the max keyword is specified, the system can allocate more chunks, if a chunk is available for use.In this example, as there are no more chunks available, ipv6-64-bit criteria cannot allocate more than 1 chunk (even if the max keyword is specified). The system fails the configuration when the number of ACL entries with ipv6-64-bit criteria exceeds the limit of one chunk allocated to SAP ingress ACL match (that is, the system does not allocate more than the configured limit of 3 chunks = 1 for mac-criteria + 1 for ipv4-criteria + 1 for ipv6-64-bit criteria).
- The system fails any attempt to use SAP ingress ACLs with ipv6-128 bit match criteria (and the other combinations listed above), because the user has disabled these criteria.
In Example 2, the user can run no ipv4-match-enable command to disable the use of ipv4-criteria. The system checks for SAPs that use ipv4-criteria and if found, fails the command; otherwise, the chunk freed for use with either mac-criteria or ipv6-64-bit criteria. The entire chunk is allocated to mac-criteria if the first SAP that needs resources requests for mac-criteria and no entries in the chunk are already allocated to mac-criteria, which leaves no resources for use by ipv6-64-bit criteria. In the same way, the entire chunk is allocated to ipv6-64-bit criteria, if the first SAP that needs resources requests for ipv6-64-bit criteria and no entries in the chunk are already allocated to ipv6-64-bit criteria, which leaves no resources for use by mac-criteria.
5.7. System Configuration Process Overview
Figure 33 shows the process to provision basic system parameters.
Figure 33: System Configuration and Implementation Flow
5.8. Configuration Notes
This section describes system configuration caveats.
5.8.1. General
To access the CLI, ensure that the 7210 SAS device is correctly initialized and the boot loader and BOFs have successfully executed.