4.5. Basic Configuration
The most basic IP and MAC filter policies must have the following:
A filter ID
Template scope, either exclusive or template
Default action, either drop or forward
At least one filter entry
Specified action, either drop or forward
Specified matching criteria
Allocates the required amount of resources for ingress and egress filter policies
The following is a sample configuration output of allocation of ingress internal CAM resources for ingress policy for 7210 SAS-M.
*A:7210SAS>config>system>res-prof>ing-internal-tcam>acl-sap-ing# info detail
----------------------------------------------
ipv4-match-enable max
ipv6-64-only-match-enable 1
no ipv4-ipv6-128-match-enable
----------------------------------------------
*A:7210SAS>config>system>res-prof>ing-internal-tcam>acl-sap-ing# back
The following is a sample configuration output of allocation of egress internal CAM resources for egress policy for 7210 SAS-M and 7210 SAS-Sx/S 1/10GE.
A:7210SAS>config>system>res-prof>egr-internal-tcam# info detail
----------------------------------------------
acl-sap-egress 2
mac-ipv4-match-enable 2
ipv6-128bit-match-enable 0
mac-ipv6-64bit-match-enable 0
mac-match-enable 0
exit
----------------------------------------------
*A:7210SAS>config>system>res-prof>egr-internal-tcam# acl-sap-egress
The following is a sample configuration output of allocation of egress internal CAM resources for egress policy for 7210 SAS-Sx 10/100GE.
*A:7210SAS>config>system>res-prof>egr-internal-tcam# info detail
----------------------------------------------
acl-sap-egress 2
mac-ipv4-match-enable 2
ipv6-128bit-match-enable 0
ipv6-64bit-match-enable 0
mac-match-enable 0
exit
no egress-sap-aggregate-meter
----------------------------------------------
*A:7210SAS>config>system>res-prof>egr-internal-tcam# acl-sap-egress
The following is a sample configuration output of allocation of egress internal CAM resources for egress policy for 7210 SAS-Mxp.
*A:sim_dutc>config>system>res-prof>egr-internal-tcam>acl-sap-egr# info detail
----------------------------------------------
mac-ipv4-match-enable 2
ipv6-128bit-match-enable 0
mac-ipv6-64bit-match-enable 0
mac-match-enable 0
----------------------------------------------
*A:sim_dutc>config>system>res-prof>egr-internal-tcam>acl-sap-egr#
The following is a sample configuration output of an IP filter policy. The configuration blocks all incoming TCP session except Telnet and allows all outgoing TCP sessions from IP net 10.67.132.0/24. CAM resources must be allocated to IPv4 criteria before associating the filter with a SAP. Figure 11 shows the interface to apply the filter.
A:ALA-1>config>filter# info
----------------------------------------------
ip-filter 3 create
entry 10 create
match protocol 6
dst-port eq 23
src-ip 10.67.132.0/24
exit
action
forward
exit
entry 20 create
match protocol 6
tcp-syn true
tcp-ack false
exit
action
drop
exit
exit
----------------------------------------------
A:ALA-1>config>filter#
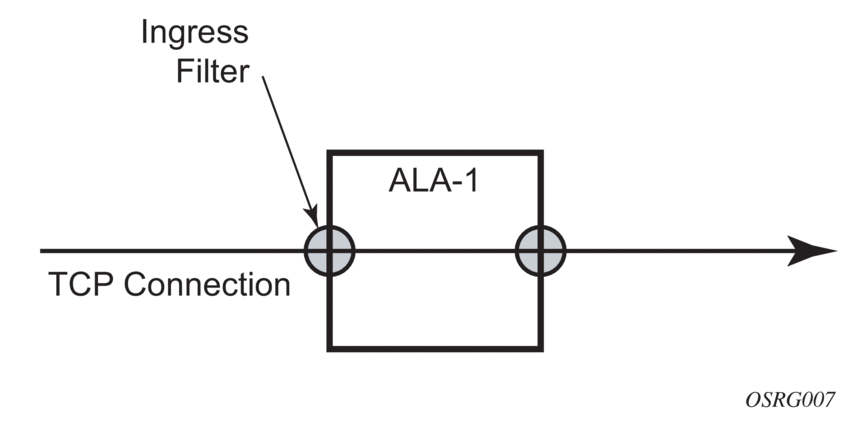
Figure 11 shows the IP filter applied to an ingress interface.
Figure 11:
Applying an IP Filter to an Ingress Interface
4.6. Common Configuration Tasks
This section provides a brief overview of the tasks that must be performed for both IP and MAC filter configurations and provides the CLI commands.
4.6.1. Allocating Resources for Filter policies (Ingress and Egress)
The following provides an example of allocation of CAM hardware resources for use with filter policies that use IPv4 and MAC criteria:
4.6.2. Creating an IP Filter Policy
Configuring and applying filter policies is optional. Each filter policy must have the following:
The filter type specified (IP)
A filter policy ID
A default action, either drop or forward
Filter policy scope specified, either exclusive or template
At least one filter entry with matching criteria specified
Configure CAM hardware resource for use by the filter policy match-criteria
4.6.2.1. IP Filter Policy
The following is a sample exclusive filter policy configuration output.
A:ALA-7>config>filter# info
----------------------------------------------
...
ip-filter 12 create
description "IP-filter"
scope exclusive
exit
...
----------------------------------------------
A:ALA-7>config>filter#
4.6.2.2. IP Filter Entry
Within a filter policy, configure filter entries which contain criteria against which ingress, egress, or network traffic is matched. The action specified in the entry determine how the packets are handled, either dropped or forwarded.
Enter a filter entry ID. The system does not dynamically assign a value.
Assign an action, either drop or forward.
Specify matching criteria.
Use the following syntax to create an IP filter entry.
config>filter# ip-filter filter-id [create]
entry entry-id [time-range time-range-name] [create]
description description-string
The following is a sample IP filter entry configuration output.
A:ALA-7>config>filter>ip-filter# info
----------------------------------------------
description "filter-main"
scope exclusive
entry 10 create
description "no-91"
match
exit
no action
exit
exit
----------------------------------------------
A:ALA-7>config>filter>ip-filter#
4.6.2.3. IP Entry Matching Criteria
Use the following syntax to configure IP filter matching criteria.
The following is a sample IP filter matching configuration output.
*A:ALA-48>config>filter>ip-filter# info
----------------------------------------------
description "filter-mail"
scope exclusive
entry 10 create
description "no-91"
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.103/24
exit
action
forward
exit
----------------------------------------------
*A:ALA-48>config>filter>ip-filter#
4.6.3. Creating an IPv6 Filter Policy
Configuring and applying IPv6 filter policies is optional. Each filter policy must have the following:
The IPv6 filter type specified.
An IPv6 filter policy ID.
A default action, either drop or forward.
Template scope specified, either exclusive or template.
At least one filter entry with matching criteria specified.
4.6.3.1. IPv6 Filter Policy
Use the following syntax to create an IPv6 filter policy.
To create an IPv6 filter using 64-bit-address, the user can use the command config> filter>ipv6-filter filter-id ipv6-64bit-address create.
By default, the IPv6 filters are configured using 128-bit-address, the output is as follows.
*A:7210SAS>config>filter>ipv6-filter# info detail
----------------------------------------------
default-action drop
no description
scope template
exit
*A:7210SAS>config>filter>ipv6-filter#
4.6.3.2. IPv6 Filter Entry
Within an IPv6 filter policy, configure filter entries which contain criteria against which ingress, egress, or network traffic is matched. The action specified in the entry determine how the packets are handled, either dropped or forwarded.
Enter an IPv6 filter entry ID. The system does not dynamically assign a value.
Assign an action, either drop or forward.
Specify matching criteria.
The following is a sample IPv6 filter entry configuration output.
*A:7210SAS>config>filter>ipv6-filter# info detail
----------------------------------------------
default-action drop
no description
scope template
entry 1 create
no description
match next-header none
no dscp
no dst-ip
no dst-port
src-ip 2001:db8::1/128
no src-port
no tcp-syn
no tcp-ack
no icmp-type
no icmp-code
exit
action
forward
exit
*A:7210SAS>config>filter>ipv6-filter#
4.6.4. Creating a MAC Filter Policy
Configuring and applying filter policies is optional. Each filter policy must have the following:
The filter type specified (MAC).
A filter policy ID.
A default action, either drop or forward.
Filter policy scope, either exclusive or template.
At least one filter entry.
Matching criteria specified.
4.6.4.1. MAC Filter Policy
The following is a sample MAC filter policy configuration output.
A:ALA-7>config>filter# info
----------------------------------------------
...
mac-filter 90 create
description "filter-west"
scope exclusive
exit
----------------------------------------------
A:ALA-7>config>filter#
4.6.4.2. MAC Filter Entry
Within a filter policy, configure filter entries which contain criteria against which ingress, egress, or network traffic is matched. The action specified in the entry determine how the packets are handled, either dropped or forwarded.
Enter a filter entry ID. The system does not dynamically assign a value.
Assign an action, either drop or forward.
Specify matching criteria.
The following is a sample MAC filter entry configuration output.
A:sim1>config>filter# info
----------------------------------------------
mac-filter 90 create
entry 1 create
description "allow-104"
match
exit
action
drop
exit
exit
----------------------------------------------
A:sim1>config>filter#
4.6.4.3. MAC Entry Matching Criteria
The following is a sample filter matching configuration output.
A;ALA-7>config>filter>mac-filter# info
----------------------------------------------
description "filter-west"
scope exclusive
entry 1 create
description "allow-104"
match
src-mac 00:dc:98:1d:00:00 ff:ff:ff:ff:ff:ff
dst-mac 02:dc:98:1d:00:01 ff:ff:ff:ff:ff:ff
exit
action
drop
exit
----------------------------------------------
4.6.4.4. Apply IP and MAC Filter Policies
Use the following syntax to apply an IP and a MAC filter policy to an Epipe service.
config>service# epipe service-id
sap sap-id
egress
filter {ip ip-filter-id | mac mac-filter-id}
ingress
filter {ip ip-filter-id | mac mac-filter-id}
The following is a sample of IP and MAC filters assigned to an ingress and egress SAP output.
A:ALA-48>config>service>epipe# info
----------------------------------------------
sap 1/1/1.1.1 create
ingress
filter ip 10
exit
egress
filter mac 92
exit
exit
no shutdown
----------------------------------------------
A:ALA-48>config>service>epipe#
4.6.4.5. Apply an IPv6 Filter Policy to VPLS
The following is a sample of IPv6 filters assigned to VPLS service interface output.
*A:7210SAS>config>service#vpls#sap info detail
----------------------------------------------
......
ingress
counter-mode in-out-profile-count
no drop-count-extra-vlan-tag-pkts
exit
exit
ingress
qos 1
no aggregate-meter-rate
filter ipv6 1
exit
egress
no filter
exit
no collect-stats
no accounting-policy
no shutdown
exit
*A:7210SAS>config>service#vpls#sap info detail
4.6.5. Applying Filter Policies to a Network IP Interface
IP filter policies can be applied to network IP interfaces. MAC filters cannot be applied to network IP interfaces or to routable IES services.
4.6.5.1. Applying a Filter Policy to an IP Interface
config>router# interface ip-int-name
The following is a sample IP filter applied to an interface at ingress output.
A:ALA-48>config>router# info
#------------------------------------------
# IP Configuration
#------------------------------------------
...
interface "to-104"
address 10.0.0.103/24
port 1/1/1
ingress
filter ip 10
exit
egress
filter ip 10
exit
exit
...
#------------------------------------------
A:ALA-48>config>router#
4.7. Filter Management Tasks
This section describes the filter policy management tasks.
4.7.1. Renumbering Filter Policy Entries
The system exits the matching process when the first match is found and then executes the actions in accordance with the specified action. Because the ordering of entries is important, the numbering sequence can be rearranged. Entries should be numbered from the most explicit to the least explicit.
Use the following syntax to renumber existing MAC or IP filter entries to re-sequence filter entries.
config>filter
ip-filter filter-id
renum old-entry-number new-entry-number
mac-filter filter-id
renum old-entry-number new-entry-number
config>filter>ip-filter# renum 10 15
config>filter>ip-filter# renum 20 10
config>filter>ip-filter# renum 40 1
The following is a sample of the original filter entry order output.
A:ALA-7>config>filter# info
----------------------------------------------
...
ip-filter 11 create
description "filter-main"
scope exclusive
entry 10 create
description "no-91"
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.103/24
exit
action forward
exit
entry 20 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.0.100/24
exit
action drop
exit
entry 30 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.0.200/24
exit
action forward
exit
entry 40 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.106/24
exit
action drop
exit
exit
...
----------------------------------------------
A:ALA-7>config>filter#
The following is a sample of the reordered filter entries output.
A:ALA-7>config>filter# info
----------------------------------------------
...
ip-filter 11 create
description "filter-main"
scope exclusive
entry 1 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.106/24
exit
action drop
exit
entry 10 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.0.100/24
exit
action drop
exit
entry 15 create
description "no-91"
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.103/24
exit
action forward
exit
entry 30 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.0.200/24
exit
action forward
exit
exit
...
----------------------------------------------
A:ALA-7>config>filter#
4.7.2. Modifying an IP Filter Policy
To access a specific IP filter, you must specify the filter ID. Use the no form of this command to remove the command parameters or return the parameter to the default setting.
config>filter>ip-filter# description "New IP filter info"
config>filter>ip-filter# entry 2 create
config>filter>ip-filter>entry$ description "new entry"
config>filter>ip-filter>entry# action drop
config>filter>ip-filter>entry# match dst-ip 10.10.10.104/32
config>filter>ip-filter>entry# exit
config>filter>ip-filter#
The following is a sample of the modified IP filter output.
A:ALA-7>config>filter# info
----------------------------------------------
...
ip-filter 11 create
description "New IP filter info"
scope exclusive
entry 1 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.106/24
exit
action
drop
exit
entry 2 create
description "new entry"
match
dst-ip 10.10.10.104/32
exit
action
drop
exit
entry 10 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.0.100/24
exit
action
drop
exit
entry 15 create
description "no-91"
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.103/24
exit
action
forward
exit
entry 30 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.0.200/24
exit
action
forward
exit
exit
..
----------------------------------------------
A:ALA-7>config>filter#
4.7.3. Modifying an IPv6 Filter Policy
To access a specific IPv6 filter, you must specify the filter ID. Use the no form of this command to remove the command parameters or return the parameter to the default setting.
config>filter# ipv6-filter 11
config>filter>ipv6-filter# description "IPv6 filter for Customer 1"
config>filter>ipv6-filter# scope exclusive
config>filter>ipv6-filter# entry 1
config>filter>ipv6-filter>entry# description "Fwds matching packets"
config>filter>ipv6-filter>entry# action forward
config>filter>ipv6-filter>entry# exit
The following is a sample output of the modified IPv6 filter output.
A:7210SAS>config>filter>ipv6-filter# info detail
----------------------------------------------
default-action drop
no description
scope template
entry 1 create
description "Test"
match next-header none
no dscp
no dst-ip
no dst-port
src-ip 2001:db8::1/128
no src-port
no tcp-syn
no tcp-ack
no icmp-type
no icmp-code
exit
action
forward
exit
...
A:7210SAS>config>filter>ipv6-filter
4.7.4. Modifying a MAC Filter Policy
To access a specific MAC filter, you must specify the filter ID. Use the no form of this command to remove the command parameters or return the parameter to the default setting.
config>filter# mac-filter 90
config>filter>mac-filter# description "New filter info"
config>filter>mac-filter# entry 1
config>filter>mac-filter>entry# description "New entry info"
config>filter>mac-filter>entry# action forward
config>filter>mac-filter>entry# exit
config>filter>mac-filter# entry 2 create
config>filter>mac-filter>entry$ action drop
config>filter>mac-filter>entry# match
config>filter>mac-filter>entry>match# dot1p 7 7
The following is a sample of the modified MAC filter output.
A:ALA-7>config>filter# info
----------------------------------------------
...
mac-filter 90 create
description "New filter info"
scope exclusive
entry 1 create
description "New entry info"
match
src-mac 00:dc:98:1d:00:00 ff:ff:ff:ff:ff:ff
dst-mac 02:dc:98:1d:00:01 ff:ff:ff:ff:ff:ff
exit
action
forward
exit
entry 2 create
match
dot1p 7 7
exit
action
drop
exit
exit
...
----------------------------------------------
A:ALA-7>config>filter#
4.7.5. Detaching/Deleting a Filter Policy
Before you can delete a filter, you must remove the filter association from the applied ingress and egress SAPs and network interfaces.
4.7.5.1. From an Ingress SAP
The following shows the command usage to remove a filter from an ingress SAP.
config>service# [epipe | vpls] service-id
sap port-id[:encap-val]
ingress
no filter
config>service# epipe 5
config>service>epipe# sap 1/1/2:3
config>service>epipe>sap# ingress
config>service>epipe>sap>ingress# no filter
4.7.5.2. From an Egress SAP
The following shows the command usage to remove a filter from an egress SAP.
config>service# [epipe | vpls] service-id
sap port-id[:encap-val]
egress
no filter
config>service# epipe 5
config>service>epipe# sap 1/1/2:3
config>service>epipe>sap# egress
config>service>epipe>sap>egress# no filter
4.7.5.3. From a Network Interface
The following shows the command usage to delete a filter from a network interface.
config>router# interface ip-int-name
ingress
config>router>if>ingress# no filter ip 2
config>router>if>ingress# exit
4.7.5.4. From the Filter Configuration
Use the following syntax to delete the filter after you have removed the filter from the SAP.
config>filter# no ip-filter filter-id
config>filter# no mac-filter filter-id
config>filter# no ip-filter 11
config>filter# no mac-filter 13
4.7.6. Copying Filter Policies
When changes are made to an existing filter policy, they are applied immediately to all services where the policy is applied. If numerous changes are required, the policy can be copied so you can edit the “work in progress” version without affecting the filtering process. When the changes are completed, you can overwrite the work in progress version with the original version.
New filter policies can also be created by copying an existing policy and renaming the new filter.
config>filter# copy filter-type src-filter-id [src-entry src-entry-id] to dst-filter-id [dst-entry dst-entry-id] [overwrite]
The following shows the command usage to copy an existing IP filter (11) to create a new filter policy (12).
config>filter# copy ip-filter 11 to 12
A:ALA-7>config>filter# info
----------------------------------------------
...
ip-filter 11 create
description "This is new"
scope exclusive
entry 1 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.106/24
exit
action
drop
exit
entry 2 create
...
ip-filter 12 create
description "This is new"
scope exclusive
entry 1 create
match
dst-ip 10.10.10.91/24
src-ip 10.10.10.106/24
exit
action
drop
exit
entry 2 create
...
----------------------------------------------
A:ALA-7>config>filter#
