5. Event and accounting logs
This chapter provides information about configuring event and accounting logs on the 7210 SAS.
5.1. Logging overview
The two primary types of logging supported on the 7210 SAS are event logging and accounting logs.
Event logging controls the generation, dissemination and recording of system events for monitoring status and troubleshooting faults within the system. The 7210 SAS groups events into four major categories or event sources:
- security events - events that pertain to attempts to breach system security
- change events - events that pertain to the configuration and operation of the node
- main events - events that pertain to applications that are not assigned to other event categories/sources
- debug events - events that pertain to trace or other debugging information
The following are events within the 7210 SAS and have the following characteristics:
- a time stamp in UTC or local time
- the generating application
- a unique event ID within the application
- the VRF-ID
- a subject identifying the affected object
- a short text description
Event control assigns the severity for each application event and whether the event should be generated or suppressed. The severity numbers and severity names supported on the 7210 SAS conform to ITU standards M.3100 X.733 and X.21 and are listed in the following table.
Table 40: Event severity levels
Severity number | Severity name |
1 | cleared |
2 | indeterminate (info) |
3 | critical |
4 | major |
5 | minor |
6 | warning |
Events that are suppressed by event control will not generate any event log entries. Event control maintains a count of the number of events generated (logged) and dropped (suppressed) for each application event. The severity of an application event can be configured in event control.
An event log on the 7210 SAS associates the event sources with logging destinations. Examples of logging destinations include, the console session, a specific telnet or SSH session, memory logs, file destinations, SNMP trap groups and syslog destinations. A log filter policy can be associated with the event log to control which events will be logged in the event log based on combinations of application, severity, event ID range, VRF ID, and the subject of the event.
The 7210 SAS accounting logs collect comprehensive accounting statistics to support a variety of billing models. The routers collect accounting data on services and network ports on a per-service class basis. In addition to gathering information critical for service billing, accounting records can be analyzed to provide insight about customer service trends for potential service revenue opportunities. Accounting statistics on network ports can be used to track link utilization and network traffic pattern trends. This information is valuable for traffic engineering and capacity planning within the network core.
Accounting statistics are collected according to the parameters defined within the context of an accounting policy. Accounting policies are applied to access objects (such as access ports and SAPs) or network objects (such as SDPs, network ports, network IP interface). Accounting statistics are collected by counters for individual services defined on the customer’s SAP or by the counters within forwarding class (FC) queues defined on the network ports.
The type of record defined within the accounting policy determines where a policy is applied, what statistics are collected and time interval at which to collect statistics.
The “location” field of the file-id lets the user configure the device and store it in any directory. The default value is cf1:, but it can also be uf1: (for devices supporting USB).
5.2. Log destinations
Both event logs and accounting logs use a common mechanism for referencing a log destination.
Only a single log destination can be associated with an event log or with an accounting log. An event log can be associated with multiple event sources, but it can only have a single log destination.
A file destination is the only type of log destination that can be configured for an accounting log.
5.2.1. Console
Sending events to a console destination means the message will be sent to the system console The console device can be used as an event log destination.
5.2.2. Session
A session destination is a temporary log destination which directs entries to the active telnet or SSH session for the duration of the session. When the session is terminated, for example, when the user logs out, the event log is removed. Event logs configured with a session destination are not stored in the configuration file. Event logs can direct log entries to the session destination.
5.2.3. Memory logs
A memory log is a circular buffer. When the log is full, the oldest entry in the log is replaced with the new entry. When a memory log is created, the specific number of entries it can hold can be specified, otherwise it will assume a default size. An event log can send entries to a memory log destination.
5.2.4. Log files
Log files can be used by both event logs and accounting logs and are stored on the compact flash devices (specifically cf1:) in the file system.
A log file is identified with a single log file ID, but a log file will generally be composed of a number individual files in the file system. A log file is configured with a rollover parameter, expressed in minutes, which represents the length of time an individual log file should be written to before a new file is created for the relevant log file ID. The rollover time is checked only when an update to the log is performed. Therefore, complying to this rule is subject to the incoming rate of the data being logged. For example, if the rate is very low, the actual rollover time may be longer than the configured value.
The retention time for a log file specifies the amount of time the file should be retained on the system based on the creation date and time of the file.
When a log file is created, only the compact flash device for the log file is specified. Log files are created in specific subdirectories with standardized names depending on the type of information stored in the log file.
Event log files are always created in the \log directory on the specified compact flash device. The naming convention for event log files is:
log eeff-timestamp
where:
- ee is the event log ID
- ff is the log file destination ID
- timestamp is the timestamp when the file is created in the form of yyyymmdd-hhmmss where:
- yyyy is the four-digit year (for example, 2007)
- mm is the two digit number representing the month (for example, 12 for December)
- dd is the two digit number representing the day of the month (for example, 03 for the 3rd of the month)
- hh is the two digit hour in a 24-hour clock (for example, 04 for 4 a.m.)
- mm is the two digit minute (for example, 30 for 30 minutes past the hour)
- ss is the two digit second (for example, 14 for 14 seconds)
Accounting log files are created in the \act-collect directory on a compact flash device (cf1). The naming convention for accounting log files is nearly the same as for log files except the prefix act is used instead of the prefix log. The naming convention for accounting logs is:
act aaff-timestamp.xml.gz
where:
- aa is the accounting policy ID
- ff is the log file destination ID
- timestamp is the timestamp when the file is created in the form of yyyymmdd-hhmmss where:
- yyyy is the four-digit year (for example, 2007)
- mm is the two digit number representing the month (for example, 12 for December)
- dd is the two digit number representing the day of the month (for example, 03 for the 3rd of the month)
- hh is the two digit hour in a 24-hour clock (for example, 04 for 4 a.m.)
- mm is the two digit minute (for example, 30 for 30 minutes past the hour)
- ss is the two digit second (for example, 14 for 14 seconds)
Accounting logs are .xml files created in a compressed format and have a .gz extension.
The \act-collect directory is where active accounting logs are written. When an accounting log is rolled over, the active file is closed and archived in the \act directory before a new active accounting log file created in \act-collect.
5.2.5. SNMP trap group
An event log can be configured to send events to SNMP trap receivers by specifying an SNMP trap group destination.
An SNMP trap group can have multiple trap targets. Each trap target can have different operational parameters.
A trap destination has the following properties:
- the IP address of the trap receiver
- the UDP port used to send the SNMP trap
- SNMP version (v1, v2c, or v3) used to format the SNMP notification
- SNMP community name for SNMPv1 and SNMPv2c receivers
- security name and level for SNMPv3 trap receivers
For SNMP traps that will be sent in-band, the source IP address of the trap is the system IP address of the 7210 SAS.
Each trap target destination of a trap group receives the identical sequence of events as defined by the log ID and the associated sources and log filter applied.
5.2.6. Syslog
An event log can be configured to send events to one syslog destination. Syslog destinations have the following properties:
- syslog server IP address
- the UDP port used to send the syslog message
- the Syslog Facility Code (0 - 23) (default 23 - local 7)
- the Syslog Severity Threshold (0 - 7) - events exceeding the configured level will be sent
Because syslog uses eight severity levels whereas the 7210 SAS uses six internal severity levels, the severity levels are mapped to syslog severities. The following table lists the severity level mappings to syslog severities.
Table 41: 7210 SAS to syslog severity level mappings
Severity level | Numerical severity (highest to lowest) | Syslog configured severity | Definition |
0 | emergency | System is unusable | |
3 | 1 | alert | Action must be taken immediately |
4 | 2 | critical | Critical conditions |
5 | 3 | error | Error conditions |
6 | 4 | warning | Warning conditions |
5 | notice | Normal but significant condition | |
1 cleared 2 indeterminate | 6 | info | Informational messages |
7 | debug | Debug-level messages |
5.3. Event logs
Event logs are the means of recording system generated events for later analysis. Events are messages generated by the system by applications or processes within the 7210 SAS.
The following figure shows a function block diagram of event logging.
Figure 7: Event logging block diagram
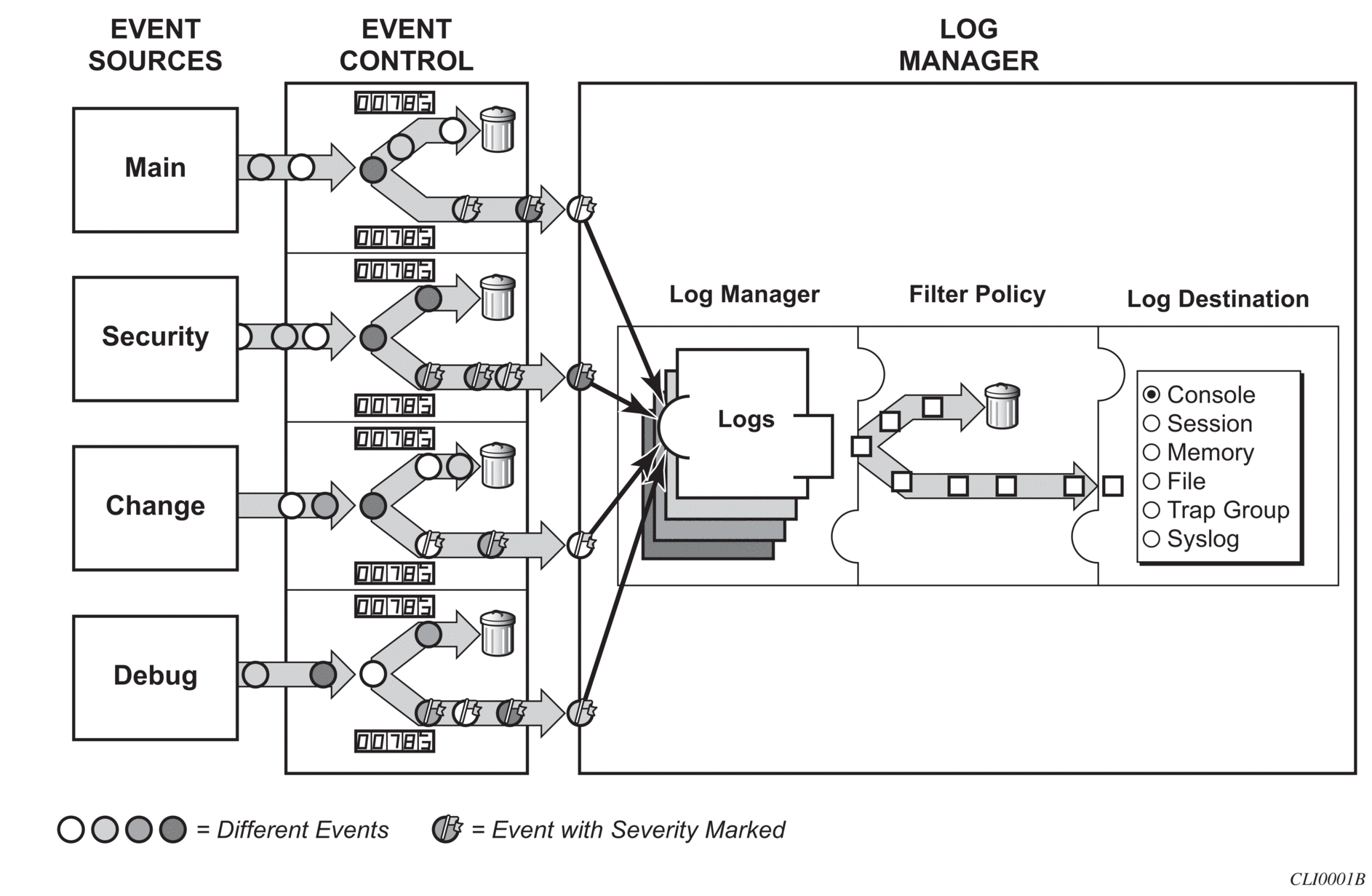
5.3.1. Event sources
In Figure 7, the event sources are the main categories of events that feed the log manager:
- securityThe security event source is all events that affect attempts to breach system security such as failed login attempts, attempts to access MIB tables to which the user is not granted access or attempts to enter a branch of the CLI to which access has not been granted. Security events are generated by the SECURITY application and the authenticationFailure event in the SNMP application.
- changeThe change activity event source is all events that directly affect the configuration or operation of the node. Change events are generated by the USER application. The Change event stream also includes the tmnxConfigModify(#2006), tmnxConfigCreate (#2007), tmnxConfigDelete (#2008) and tmnxStateChange (#2009) change events from the SYSTEM application.
- debugThe debug event source is the debugging configuration that has been enabled on the system. Debug events are generated by the DEBUG application.
- mainThe main event source receives events from all other applications within the 7210 SAS.
Examples of applications within 7210 SAS include IP, MPLS, OSPF, CLI, and services. The following output displays an example of the show log applications command output which displays all applications.
5.3.2. Event control
Event control preprocesses the events generated by applications before the event is passed into the main event stream. Event control assigns a severity to application events and can either forward the event to the main event source or suppress the event. Suppressed events are counted in event control, but these events will not generate log entries as it never reaches the log manager.
Simple event throttling is another method of event control and is configured similarly to the generation and suppression options. See Simple logger event throttling.
Events are assigned a default severity level in the system, but the application event severities can be changed by the user.
Application events contain an event number and description that describe why the event is generated. The event number is unique within an application, but the number can be duplicated in other applications.
The following example, generated by querying event control for application generated events, displays a partial list of event numbers and names.
5.3.3. Log manager and event logs
Events that are forwarded by event control are sent to the log manager. The log manager manages the event logs in the system and the relationships between the log sources, event logs and log destinations, and log filter policies.
An event log has the following properties:
- a unique log ID
- the log ID is a short, numeric identifier for the event log (a maximum of ten logs can be configured at a time)
- one or more log sources
- the source stream or streams to be sent to log destinations can be specified. The source must be identified before the destination can be specified. The events can be from the main event stream, events in the security event stream, or events in the user activity stream
- one event log destination
- a log can only have a single destination *the destination for the log ID destination can be one of console, session, syslog, snmp-trap-group, memory, or a file on the local file system)
- an optional event filter policy
- an event filter policy defines whether to forward or drop an event or trap-based on match criteria
5.3.4. Event filter policies
The log manager uses event filter policies to allow fine control over which events are forwarded or dropped based on various criteria. Like other policies with the 7210 SAS, filter policies have a default action. The default actions are either:
- Forward
- Drop
Filter policies also include a number of filter policy entries that are identified with an entry ID and define specific match criteria and a forward or drop action for the match criteria.
Each entry contains a combination of matching criteria that define the application, event number, router, severity, and subject conditions. The entry’s action determines how the packets should be treated if they have met the match criteria.
Entries are evaluated in order from the lowest to the highest entry ID. The first matching event is subject to the forward or drop action for that entry.
Valid operators are listed in the following table.
Table 42: Valid filter policy operators
Operator | Description |
eq | equal to |
neq | not equal to |
lt | less than |
lte | less than or equal to |
gt | greater than |
gte | greater than or equal to |
A match criteria entry can include combinations of:
- equal to or not equal to a specific system application
- equal to, not equal to, less than, less than or equal to, greater than or greater than or equal to an event number within the application
- equal to, not equal to, less than, less than or equal to, greater than or greater than or equal to a severity level
- equal to or not equal to a router name string or regular expression match
- equal to or not equal to an event subject string or regular expression match
5.3.5. Event log entries
Log entries that are forwarded to a destination are formatted in a way appropriate for the specific destination whether it be recorded to a file or sent as an SNMP trap, but log event entries have common elements or properties. All application generated events have the following properties:
- a time stamp in UTC or local time
- the generating application
- a unique event ID within the application
- a router name identifying the VRF-ID that generated the event
- a subject identifying the affected object
- a short text description
The general format for an event in an event log with either a memory, console or file destination is as follows.
The following is an event log example:
The specific elements that compose the general format are described in the following table.
Table 43: Log entry field descriptions
Label | Description |
nnnn | The log entry sequence number. |
YYYY/MM/DD | The UTC date stamp for the log entry. YYYY - year MM - month DD - date |
HH:MM:SS.SS | The UTC time stamp for the event. HH - hours (24 hour format) MM - minutes SS.SS - seconds |
<severity> | The severity level name of the event. CLEARED - a cleared event (severity number 1) INFO - an indeterminate/informational severity event (severity level 2) CRITICAL - a critical severity event (severity level 3) MAJOR - a major severity event (severity level 4) MINOR - a minor severity event (severity level 5) WARNING - a warning severity event (severity 6) |
<application> | The application generating the log message. |
<event_id> | The application’s event ID number for the event. |
<router> | The router name representing the VRF-ID that generated the event. |
<subject> | The subject/affected object for the event. |
<description> | A text description of the event. |
5.3.6. Simple logger event throttling
Simple event throttling provides a mechanism to protect event receivers from being overloaded when a scenario causes many events to be generated in a very short period of time. A throttling rate, # events/# seconds, can be configured. Specific event types can be configured to be throttled. After the throttling event limit is exceeded in a throttling interval, any further events of that type cause the dropped events counter to be incremented. Dropped events counts are displayed by the show>log>event-control context. Events are dropped before being sent to one of the logger event collector tasks. There is no record of the details of the dropped events and therefore no way to retrieve event history data lost by this throttling method.
A particular event type can be generated by multiple managed objects within the system. At the point this throttling method is applied the logger application has no information about the managed object that generated the event and cannot distinguish between events generated by object “A” from events generated by object “B”. If the events have the same event-id, they are throttled regardless of the managed object that generated them. It also does not know which events may eventually be logged to destination log-id <n> from events that will be logged to destination log-id <m>.
Throttle rate applies commonly to all event types. It is not configurable for a specific event-type. A timer task checks for events dropped by throttling when the throttle interval expires. If any events have been dropped, a TIMETRA-SYSTEM-MIB::tmnxTrapDropped notification is sent.
5.3.7. Default system log
Log 99 is a preconfigured memory-based log that logs events from the main event source (not security, debug, and so on). Log 99 exists by default.
The following example displays the log 99 configuration.
5.4. Accounting logs
Before an accounting policy can be created, a target log file must be created to collect the accounting records. The files are stored in system memory on compact flash (cf1:) in a compressed (tar) XML format and can be retrieved using FTP or SCP.
A file ID can only be assigned to either one event log ID or one accounting log.
5.4.1. Accounting records
An accounting policy must define a record name and collection interval. Only one record name can be configured per accounting policy. Also, a record name can only be used in one accounting policy.
When creating accounting policies, one service accounting policy and one network accounting policy can be defined as default. If statistics collection is enabled on a SAP, access-uplink, or network port and no accounting policy is applied, then the respective default policy is used. If no default policy is defined, then no statistics are collected unless a specifically defined accounting policy is applied.
The record name, sub-record types, and default collection period for service and network accounting policies are listed in Table 44, Table 45, Table 46, Table 47, and Table 48.
5.4.2. Accounting record names and collection periods
Table 44: Accounting record names and collection periods for 7210 SAS-D
Record name | Sub-record types | Accounting object | Default collection period (minutes) |
service-ingress-octets | sio | Access SAP | 5 |
service-egress-octets | seo | Access SAP | 5 |
service-ingress-packets | sip | Access SAP | 5 |
service-egress-packets | sep | Access SAP | 5 |
combined-service-ingress | sip, sio | Access SAP | 5 |
combined-service-egress | seo, sep | Access SAP | 5 |
complete-service-ingress-egress | sip, sio, seo, sep | Access SAP | 5 |
access-egress-packets | aep | Access-port | 5 |
access-egress-octets | aeo | Access-port | 5 |
combined-access-egress | cmAeo, cmAep | Access-port | 5 |
network-ingress-octets | nio | Access-uplink-port | 15 |
network-ingress-packets | nip | Access-uplink-port | 15 |
network-egress-octets | neo | Access-uplink-port | 15 |
network-egress-packets | neo | Access-uplink-port | 15 |
combined-network-egress | cmNeo, cmNep | Access-uplink-port | 15 |
combined-network-ingress-egress-octets | cmNio, cmNeo | Access-uplink-port | 15 |
saa | 5 |
Table 45: Accounting record names and collection periods for 7210 SAS-Dxp
Record name | Sub-record types | Accounting object | Default collection period (minutes) |
service-ingress-octets | sio | Access SAP | 5 |
service-egress-octets | seo | Access SAP | 5 |
service-ingress-packets | sip | Access SAP | 5 |
service-egress-packets | sep | Access SAP | 5 |
combined-service-ingress | sip, sio | Access SAP | 5 |
combined-service-egress | seo, sep | Access SAP | 5 |
complete-service-ingress-egress | sip, sio, seo, sep | Access SAP | 5 |
access-egress-packets | aep | Access-port | 5 |
access-egress-octets | aeo | Access-port | 5 |
combined-access-egress | cmAeo, cmAep | Access-port | 5 |
network-ingress-octets | nio | Access-uplink-port | 15 |
network-ingress-packets | nip | Access-uplink-port | 15 |
network-egress-octets | neo | Access-uplink-port | 15 |
network-egress-packets | nep | Access-uplink-port | 15 |
combined-network-egress | cmNeo, cmNep | Access-uplink-port | 15 |
combined-network-ingress-egress-octets | cmNio, cmNeo | Access-uplink-port | 15 |
saa | 5 | ||
complete-pm | 5 |
Table 46: Accounting record names and collection periods for 7210 SAS-K 2F1C2T
Record name | Sub-record types | Accounting object | Default collection period (minutes) |
service-ingress-octets | sio | Access SAP | 5 |
service-egress-octets | seo | Access SAP | 5 |
service-ingress-packets | sip | Access SAP | 5 |
service-egress-packets | sep | Access SAP | 5 |
combined-service-ingress | sip, sio | Access SAP | 5 |
combined-service-egress | seo, sep | Access SAP | 5 |
complete-service-ingress-egress | sip, sio, seo, sep | Access SAP | 5 |
network-ingress-octets | nio | Access-uplink-port | 15 |
network-ingress-packets | nip | Access-uplink-port | 15 |
network-egress-octets | neo | Access-uplink-port | 15 |
network-egress-packets | neo | Access-uplink-port | 15 |
combined-network-egress | cmNeo, cmNep | Access-uplink-port | 15 |
combined-network-ingress-egress-octets | cmNio, cmNeo | Access-uplink-port | 15 |
saa | 5 | ||
y1564 | 5 | ||
complete-pm | 5 |
Table 47: Accounting record names and collection periods for 7210 SAS-K 2F6C4T
Record name | Sub-record types | Accounting object | Default collection period (minutes) |
service-ingress-octets | sio | Access SAP | 5 |
service-egress-octets | seo | Access SAP | 5 |
service-ingress-packets | sip | Access SAP | 5 |
service-egress-packets | sep | Access SAP | 5 |
combined-service-ingress | sip, sio | Access SAP | 5 |
combined-service-egress | seo, sep | Access SAP | 5 |
complete-service-ingress-egress | sip, sio, seo, sep | Access SAP | 5 |
combined-access-egress | cmAeo, cmAep | Access-port | 5 |
network-ingress-octets | nio | Access-uplink-port and Network port | 15 |
network-ingress-packets | nip | Access-uplink-port and Network port | 15 |
network-egress-octets | neo | Access-uplink-port and Network port | 15 |
network-egress-packets | neo | Access-uplink-port and Network port | 15 |
combined-network-egress | cmNeo, cmNep | Access-uplink-port and Network port | 15 |
combined-network-ingress-egress-octets | cmNio, cmNeo | Access-uplink-port and Network port | 15 |
saa | 5 | ||
y1564 | 5 | ||
complete-pm | 5 |
Table 48: Accounting record names and collection periods for 7210 SAS-K 3SFP+ 8C
Record name | Sub-record types | Accounting object | Default collection period (minutes) |
service-ingress-octets | sio | Access SAP | 5 |
service-egress-octets | seo | Access SAP | 5 |
service-ingress-packets | sip | Access SAP | 5 |
service-egress-packets | sep | Access SAP | 5 |
combined-service-ingress | sip, sio | Access SAP | 5 |
combined-service-egress | seo, sep | Access SAP | 5 |
complete-service-ingress-egress | sip, sio, seo, sep | Access SAP | 5 |
combined-access-egress | cmAeo, cmAep | Access-port | 5 |
network-ingress-octets | nio | Access-uplink-port and Network port | 15 |
network-ingress-packets | nip | Access-uplink-port and Network port | 15 |
network-egress-octets | neo | Access-uplink-port and Network port | 15 |
network-egress-packets | neo | Access-uplink-port and Network port | 15 |
combined-network-egress | cmNeo, cmNep | Access-uplink-port and Network port | 15 |
combined-network-ingress-egress-octets | cmNio, cmNeo | Access-uplink-port and Network port | 15 |
saa | 5 | ||
y1564 | 5 | ||
complete-pm | 5 |
5.4.3. Accounting record details
Each accounting record name is composed of one or more sub-records, which are in turn composed of multiple fields.
See Appendix: accounting record name details for 7210 SAS platforms for more information about accounting records and statistics for the 7210 SAS platforms.
5.4.4. Configuration guidelines
The following information describes configuration guidelines:
- On the 7210 SAS-D and 7210 SAS-Dxp, the ingress SAP counter counts both octets and packets simultaneously.
- On the 7210 SAS-D, the egress SAP counter is disabled by default.
- Ensure that egress SAP counters are enabled on 7210 SAS-D devices before associating accounting records of type service-egress-octets, service-egress-packets, combined-service-egress and complete-service-ingress-egress.
- Before modifying the counter mode, disable account log generation. Execute the no collect-stats command. Changing the mode of the counter results in loss of previously collected counts and resets the counter.
- Egress SAP statistics are not available on any of the SAPs of a port on which a dot1q SAP and dot1q default SAP configuration are present at the same time.
- On the 7210 SAS-D and 7210 SAS-Dxp for VLL and VPLS services, the counter-mode of counters associated with SAP ingress meters/policers can be changed by executing the following command:
- for 7210 SAS-D and 7210 SAS-Dxp devices — config>service>epipe/vpls>sap>statistics>ingress>counter-mode {in-out-profile-count | forward-drop-count}
For more information about the counter-mode command, refer to the 7210 SAS-D, Dxp, K 2F1C2T, K 2F6C4T, K 3SFP+ 8C Services Guide.
The statistics collected for the following accounting records vary based on the counter-mode selected:
- Service-ingress-octets
- Service-ingress-packets
- Combined-service-ingress
- Complete-service-ingress-egress
5.4.5. Reporting and time-based accounting
Node support for volume and time-based accounting concept provides an extra level of intelligence at the network element level to provide service models such as “prepaid access” in a scalable manner. This means that the network element gathers and stores per-subscriber accounting information and compare it with predefined quotas. After a quota is exceeded, the predefined action (such as redirection to a web portal or disconnect) is applied.
5.5. Configuration notes
This following information describes logging configuration caveats:
- A file or filter cannot be deleted if it has been applied to a log.
- File IDs, syslog IDs, or SNMP trap groups must be configured before they can be applied to a log ID.
- A file ID can only be assigned to either one log ID or one accounting policy.
- Accounting policies must be configured in the config>log context before they can be applied to a service SAP or service interface, or applied to a network port.
- The snmp-trap-id must be the same as the log-id.