IS-IS
In This Chapter
This chapter provides information about configuring the Intermediate System-to-Intermediate System (IS-IS) protocol.
Topics in this chapter include:
Overview of IS-IS
IS-IS is an interior gateway protocol (IGP), similar to OSPF, that is used within large autonomous systems (ASs). IS-IS is a link-state protocol. Each IS-IS router maintains an identical database (called the link-state database, topological database, or routing information database [RIB]) of the AS, including information about the local state of each router (for example, its usable interfaces and reachable neighbors).
IS-IS-TE (IS-IS with traffic engineering extensions) is used to advertise reachability information and traffic engineering information such as available bandwidth.
The 7705 SAR also supports multiple instances of IS-IS (MI-IS-IS).
Entities within IS-IS include networks, intermediate systems, and end systems. In IS-IS, a network is an autonomous system (AS), or routing domain, with intermediate systems and end systems. A router, such as the 7705 SAR, is an intermediate system. Intermediate systems send, receive, and forward protocol data units (PDUs). End systems are network devices (or hosts) that send and receive PDUs but do not forward them.
Intermediate system and end system protocols allow routers and nodes to identify each other. IS-IS sends out link-state updates (called link-state PDUs, or LSPs) periodically throughout the network so that each router can maintain current network topology information.
IS-IS uses a cost metric that represents the status of a link, and (optionally) the bandwidth of the interface, in an algorithm that determines the best route to a destination. This algorithm is called the Shortest Path First (SPF), or Dijkstra, algorithm. Routing decisions are made using the link-state information. IS-IS evaluates topology changes and, if necessary, performs SPF recalculations.
When the best route to a particular destination is determined, the route information is sent to the routing table manager (RTM). The RTM may contain more than one best route to a destination from multiple protocols. Because metrics from different protocols are not comparable, the RTM uses the concept of preference to select the best route. The route with the lowest preference value is selected.
The best routes from the RTM are then added to the forwarding table (also known as the forwarding information base [or FIB]). All forwarding decisions are based on the information in the forwarding database.
The forwarding (or dropping) of packets is controlled by filters applied to the interface and route policies applied to the IS-IS protocol. Refer to the 7705 SAR OS Router Configuration Guide for information on filters and route policies.
The following major IS-IS features are supported:
IS-IS Areas (Two-level Hierarchy)
IS-IS can subdivide an autonomous system into areas to simplify the calculation of routes and minimize the size of IP routing tables. When an AS is divided into areas, each IS-IS router in an area must maintain an identical link-state database of the area topology, but routes from other areas can be summarized. Sometimes one “default” route can be used to represent many different routes. The topology is hidden from routing devices in other areas, which minimizes the size of the link-state database and reduces IS-IS link-state PDUs (LSPs). See Route Redistribution and Summarization.
IS-IS uses a two-level hierarchy when dividing an AS into smaller areas. A system logically belongs to one area. Level 1 routing is performed within an area. Level 2 routing is performed between areas. A 7705 SAR can be configured as a level 1 router, level 2 router, or level 1/2 router.
Figure 5 shows an example of an IS-IS topology.
Level 1 routers know the topology in their area, including all routers and end systems in their area, but do not know the identity of routers or destinations outside of their area. Level 1 routers forward traffic with destinations outside of their area to a level 1/2 router in their area.
Sometimes, the shortest path to an outside destination is not through the closest level 1/2 router, or the only level 1/2 router to forward packets out of an area is not operational. In order to avoid such cases, route leaking provides a mechanism to leak level 2 routes to level 1 routers to provide routing information regarding inter-area routes. Therefore, a level 1 router has more options to forward packets. For more information about route leaking, see Configuring Leaking.
Figure 5: IS-IS Topology
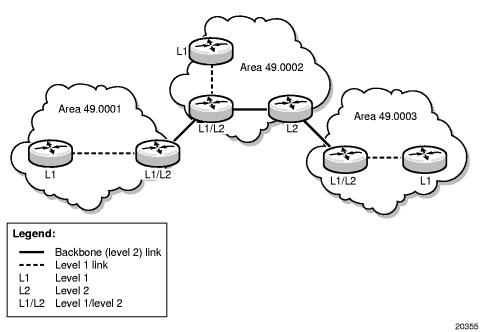
Level 2 routers know the level 2 topology and know which addresses are reachable by each level 2 router. Level 2 routers do not need to know the topology within any level 1 area, except if the level 2 router is also a level 1 router within a single area. By default, only level 2 routers can exchange PDUs or routing information directly with external routers located outside the routing domain.
Table 34 describes the router types (or intermediate systems) within IS-IS.
Table 34: IS-IS Intermediate Systems
Intermediate System | Description |
Level 1 | Maintains a link-state database of other routers that reside in the same area (i.e., local area) Exchanges topology information for the local area Routing is performed within the area, based on the area ID portion of the ISO address (see ISO Network Addressing) If the destination address is in the area (area ID is equal), routers forward the packets to the level 1 router that is advertising the destination address, based on the system ID If the destination address is not in the area (area ID is not equal), routers forward the packet to the nearest level 1/2 router in the local area |
Level 2 | Resides within an area but connects to other level 2 routers in multiple areas in a backbone mesh Maintains a link-state database of other level 2 routers and of the level 1/2 routers in each local area Exchanges topology information between areas Routing is performed between areas based on the area address |
Level 1/2 | Acts as an area border router with links to the level 2 backbone as well as to the level 1 routers within its area Maintains two link-state databases – a level 1 link-state database of the routers in the local area and a level 2 link-state database of the backbone and any level 1/2 routers Exchanges topology information within the local area and between areas Routing is performed within and between areas If the destination address is in the area (area ID is equal), routers use the level 1 database to forward the packets to the level 1 router that is advertising the destination address, based on the system ID If the destination address is not in the area (area ID is not equal), routers use the level 2 database to forward the packet based on the area ID |
ISO Network Addressing
IS-IS uses ISO network addresses. There are two types of network addresses:
- Network Service Access Point (NSAP)NSAP addresses identify a point of connection to the network, such as a router interface. Each NSAP represents a service that is available at that node. An end system can have multiple NSAP addresses; the addresses differ only by the last byte (called the n-selector). In addition to having multiple services, a single node can belong to multiple areas.
- Network Entity Title (NET)NET addresses identify network layer entities or processes instead of services. Structurally, an NET is identical to an NSAP address but has an n-selector of 00. Most end systems have one NET. Intermediate systems (routers) can have up to three NETs, differentiated by the area ID.
NSAP addresses are divided into three parts. Only the area ID portion is configurable:
- area ID – a variable-length field between 1 and 13 bytes that identifies the area to which the router belongs. This field includes the Authority and Format Identifier (AFI) as the first (most significant byte) and the area identifier.
- system ID – A 6-byte system identifier. This value is not configurable. The system ID is derived from the system or router ID and uniquely identifies the router.
- selector ID – A 1-byte selector identifier that is always 00 for an NET. This value is not configurable.
The area ID portion of the NET can be manually configured with 1 to 13 bytes. If fewer than 13 bytes are entered, the rest of the field is padded with zeros.
Neighbors and Adjacencies
IS-IS routers discover their neighbors by exchanging Hello PDUs. Neighbors are routers that have an interface to a common network/area. In a broadcast-supported topology, one router sends Hello packets to a multicast address and receives Hello packets in return. In non-broadcast topologies, unicast Hello packets are used.
Because all routing devices on a common network must agree on certain parameters, these parameters are included in Hello packets. Differences in these parameters can prevent neighbor relationships from forming.
A level 1 router will not become a neighbor with a node that does not have a common area address. However, if a level 1 router has area addresses A, B, and C, and a neighbor has area addresses B and D, the level 1 router will accept the other node as a neighbor because address B is common to both routers.
When Hello packets have been successfully exchanged, the neighbors are considered to be adjacent.
Within an area, level 1 routers exchange link-state PDUs (LSPs) that identify the IP addresses reachable by each router. Each router has one LSP that contains information about that router; included in each LSP can be zero or more IP addresses, subnet masks, and metric combinations. Each level 1 router is manually configured with the IP address, subnet mask, and metric combinations that are reachable on each interface.
Level 2 routers exchange LSPs that include a complete list of IP addresses, subnet masks, and metrics specifying all the IP addresses that are reachable in their area. Level 2 routers can also report external reachability information, corresponding to addresses reachable by routers in other routing domains or autonomous systems.
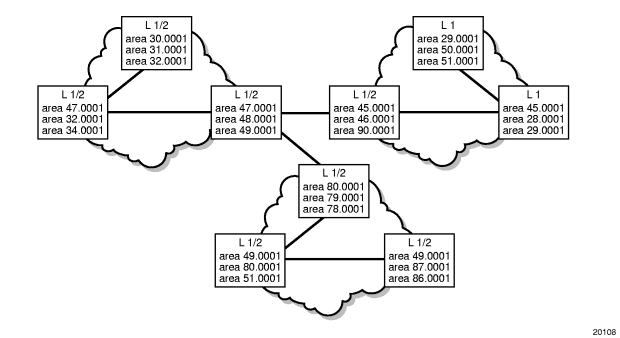
Routers with common area addresses form level 1 adjacencies. Routers with no common NET addresses form level 2 adjacencies, if they are capable. See Figure 6.
Level 2 adjacencies are formed with other level 2 nodes whose area addresses do not overlap. If the area addresses do not overlap, the link is considered by both routers to be level 2 and only level 2 LSPs flow on the link.
Figure 6: Using Area Addresses to Form Adjacencies
Designated Routers
In multi-access broadcast networks, such as Ethernet networks, with at least two attached routers, a designated router can be elected. The IS-IS protocol refers to the designated router as the designated intermediate system (DIS).
The concept of a designated router was developed in order to avoid the formation of adjacencies between all attached routers. Without a designated router, the area would be flooded with link-state PDUs (LSPs)—a router would send LSPs to all its adjacent neighbors, and each in turn would send LSPs to all their neighbors, and so on. This would create multiple copies of the same LSP on the same link.
The designated router reduces the number of adjacencies required because each router forms an adjacency only with the designated router. Only the designated router sends LSPs in multicast format to the rest of the network, reducing the amount of routing protocol traffic.
In IS-IS, a broadcast subnetwork with multiple connected routers is considered to be a pseudonode. The pseudonode has links to each of the routers and each of the routers has a single link to the pseudonode (rather than links to each of the other routers). LSPs are generated on behalf of the pseudonode by the DIS.
The DIS has two tasks:
- create and update the pseudonode LSP
- flood the LSP over the LAN
The DIS is automatically elected based on the interface priority of the router and/or if it has the highest MAC address of all routers in the LAN. If all interface priorities are the same, the router with the highest subnetwork point of attachment (SNPA) is selected. The SNPA is the MAC address on a LAN.
Every IS-IS router interface is assigned both a level 1 priority and a level 2 priority. If a new router starts up in the LAN and has a higher interface priority, the new router preempts the original DIS and becomes the new DIS. The new DIS purges the old pseudonode LSP and floods a new set of LSPs.
Because different priorities can be set according to level 1 or level 2 routing, there can be two different routers in an Ethernet LAN that are DIS-designated. One DIS supports all level 1 routers, and the other DIS supports all level 2 routers on that segment.
The DIS generates the pseudonode LSP. The DIS reports all LAN neighbors (including itself) in the pseudonode link-state PDU (LSP). All LAN routers communicate with the pseudonode via their LSPs. The pseudonode reduces the number of adjacencies by having all physical devices exchange information only with the pseudonode. Each router listens for updates to the pseudonode and updates its individual topology according to those updates.
Note:
|
IS-IS Packet Types
Table 35 describes the packet types used by IS-IS to exchange protocol information.
Table 35: IS-IS Packet Types
Packet Type | Description |
Hello PDUs | Routers with IS-IS enabled send Hello PDUs to IS-IS-enabled interfaces to discover neighbors and establish adjacencies. |
Link-state PDUs (LSPs) | LSPs contain information about the state of adjacencies to neighboring IS-IS systems and are used to build the link-state database. LSPs are flooded periodically throughout an area. Level 1 and level 2 LSPs are supported. |
Complete sequence number PDUs (CSNPs) | In order for all routers to maintain the same information (synchronize), CSNPs inform other routers that some LSPs might be outdated or missing from their database. CSNPs contain a complete list of all LSPs in the current IS-IS database. Level 1 and level 2 CSNPs are supported. |
Partial sequence number PDUs (PSNPs) | PSNPs are used to request missing LSPs and acknowledge that an LSP was received. Level 1 and level 2 PSNPs are supported. |
When a change takes place, IS-IS sends only the changed information, not the whole topology information or whole link-state database. From the topological database, each router constructs a tree of shortest paths with itself as root (that is, runs the Dijkstra algorithm). IS-IS distributes routing information between routers belonging to a single AS.
To summarize:
- Hello PDUs are sent over the IS-IS-enabled interfaces to discover neighbors and establish adjacencies.
- IS-IS neighbor relationships are formed if the Hello PDUs contain information that meets the criteria for forming an adjacency.
- Routers can build a link-state PDU based upon their local interfaces that are configured for IS-IS and prefixes learned from other adjacent routers.
- Routers flood LSPs to the adjacent neighbors except the neighbor from which they received the same LSP. The link-state database is constructed from these LSPs.
- A Shortest Path Tree (SPT) is calculated by each router, and from this SPT the routing table is built.
Metrics
IS-IS uses a cost metric that represents the status of a link in an algorithm to determine the best route to a destination. This algorithm is called the Shortest Path First (SPF), or Dijkstra, algorithm. Routing decisions are made using the link-state information. IS-IS evaluates topology changes and, if necessary, performs SPF recalculations.
To calculate the lowest cost to reach a destination, each configured level on each interface must have a cost. The costs for each level on an interface may be different.
In IS-IS, if the metric is not configured, the default cost 10 is used, regardless of the actual capacity of the link. By default, IS-IS does not use reference bandwidth in the calculation, unlike OSPF.
Authentication
All IS-IS protocol exchanges can be authenticated. This guarantees that only trusted routers can participate in autonomous system routing. The Alcatel-Lucent implementation of IS-IS supports plain text (simple password) and Message Digest 5 (MD5) authentication.
When authentication is enabled on a link, a text string password must be configured. Neighbor IS-IS routers must supply the password in all IS-IS packets they send to an interface.
Plain text authentication includes the password in each IS-IS packet sent on a link.
MD5 authentication is more secure than plain text authentication. MD5 authentication uses the password as an encryption key. Routers in the same routing domain must be configured with the same key. When the MD5 hashing algorithm is used for authentication, MD5 is used to verify data integrity by creating a 128-bit message digest from the data input that is included in each packet. The packet is transmitted to the router neighbor and can only be decrypted if the neighbor has the correct password.
By default, authentication is not enabled on an interface.
Route Redistribution and Summarization
This section contains information on the following topics:
Redistribution
Route redistribution is the taking of routes from one protocol and sending them to another protocol. The 7705 SAR supports the redistribution of static routes into OSPF and IS-IS and the redistribution of routes between IS-IS levels. The routes can be redistributed as level 1, level 2, or level 1/2 routes, depending on the level capability of the IS-IS router.
Multi-instance IS-IS (MI-IS-IS) supports route redistribution:
- to and from any other routing protocol
- to and from any other IS-IS instance
Route redistribution involves the use of routing policies. For information on routing policies, refer to the 7705 SAR OS Router Configuration Guide, “Route Policies”. To configure route redistribution, see Redistributing External IS-IS Routers.
Summarization
IS-IS IPv4 route summarization allows users to create aggregate IPv4 addresses that include multiple groups of IPv4 addresses for a given IS-IS level. Routes redistributed from other routing protocols can also be summarized.
IS-IS route summarization helps to reduce the size of the link-state database and the routing table. It also helps to reduce the chance of route flapping, which may occur when a router alternately advertises a destination network via one route then another route in quick sequence (or advertises a route as unavailable then available again).
IS-IS-TE Extensions
IS-IS traffic engineering (TE) extensions enable the 7705 SAR to include traffic engineering information in the algorithm in order to calculate the best route to a destination. IS-IS-TE extensions are used by MPLS traffic engineering; that is, RSVP-TE. The traffic information includes:
- maximum reservable bandwidth
- unreserved bandwidth
- available bandwidth
- link administration groups (or link colors)
- SRLGs
- TE metrics
Bidirectional Forwarding Detection (BFD) for IS-IS
BFD is a simple protocol for detecting failures in a network. BFD uses a “hello” mechanism that sends control messages periodically to the far end and receives periodic control messages from the far end. BFD can detect device, link, and protocol failures.
When BFD is enabled on an IS-IS interface, the state of the interface is tied to the state of the BFD session between the local node and remote (far-end) node. BFD is implemented in asynchronous mode only (similar to a heartbeat message), meaning that neither end responds to control messages; rather, the messages are sent in the interval configured at each end.
If the configured number of consecutive BFD missed messages is reached, the link is declared down and IS-IS takes the appropriate action (for example, generates a link-state PDU (LSP) against the failed link or reroutes around the failed link).
Due to the lightweight nature of BFD, the frequency of BFD packets can be relatively high (up to 10 per second); therefore, it can detect failures faster than other detection protocols, making it ideal for use in applications such as mobile transport.
Multi-Instance IS-IS (MI-IS-IS)
The 7705 SAR routers support multiple IS-IS instances. There is one default (base) instance. The remaining (non-default) instances must be specified with an isis-instance value.
The default (base) and non-default MI-IS-IS instances use the following MAC addresses:
- default instance, as per the ISO 10589 standard:
- 01-80-C2-00-00-14 for all level 1 routers (AllL1IS)
- 01-80-C2-00-00-15 for all level 2 routers (AllL2IS)
- non-default instances, as per the RFC 6822 standard:
- 01-00-5E-90-00-02 for all level 1 routers (AllL1MI-ISs)
- 01-00-5E-90-00-03 for all level 2 routers (AllL2MI-ISs)

Note: On the 7705 SAR, all non-default instances use the same MAC address for routers at the same level, which is different multicast MAC address from the base instance. The non-default MAC address is not user-configurable and is permanently set.
All IS-IS instances on a 7705 SAR populate the same router information base (RIB).
To use the same router interface in more than one IS-IS instance, use the iid-tlv-enable command. When the iid-tlv-enable command is issued, the instance ID (IID) is included in all IS-IS PDUs so that the far-end router knows which instance will receive the packet.
IS-IS Configuration Process Overview
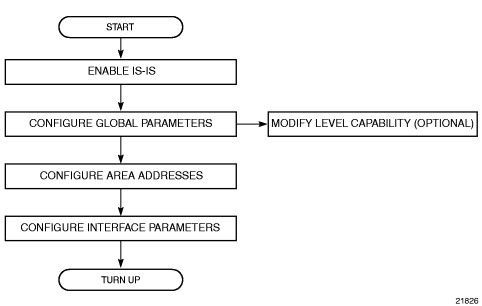
Figure 7 shows the process to provision basic IS-IS parameters.
Figure 7: IS-IS Configuration Process
Configuration Notes
General
- IS-IS must be enabled on each participating 7705 SAR.
- There are no default network entity titles.
- There are no default interfaces.
- By default, 7705 SAR routers are assigned a level 1/2 capability.
Reference Sources
For information on supported IETF drafts and standards, as well as standard and proprietary MIBs, refer to Standards and Protocol Support.