Security
In This Chapter
This chapter provides information to configure security parameters. Topics in this chapter include:
Authentication, Authorization, and Accounting
This chapter describes authentication, authorization, and accounting (AAA) used to monitor and control network access on the 7705 SAR. Network security is based on a multi-step process. The first step, authentication, validates a user’s name and password. The second step is authorization, which allows the user to access and execute commands at various command levels based on profiles assigned to the user.
The third step, accounting, keeps track of the activity of a user who has accessed the network. The type of accounting information recorded can include a history of the commands executed, the amount of time spent in the session, the services accessed, and the data transfer size during the session. The accounting data can then be used to analyze trends, and also for billing and auditing purposes.
You can configure the 7705 SAR to use local, Remote Authentication Dial In User Service (RADIUS), or Terminal Access Controller Access Control System Plus (TACACS+) security to validate users who attempt to access the router by console, Telnet, or FTP. You can select the authentication order that determines the authentication method to try first, second, and third.
The 7705 SAR supports the following security features:
- RADIUS can be used for authentication, authorization, and accounting
- TACACS+ can be used for authentication, authorization, and accounting
- local security can be implemented for authentication and authorization
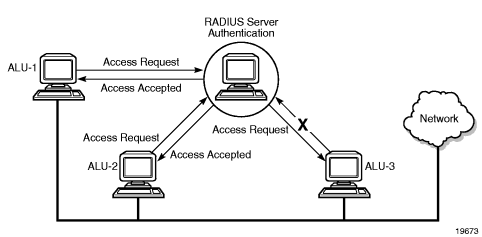
Figure 1 depicts end-user access requests sent to a RADIUS server. After validating the user names and passwords, the RADIUS server returns an access accept message to the users on ALU-1 and ALU-2. The user name and password from ALU-3 could not be authenticated, thus access was denied.
Figure 1: RADIUS Requests and Responses
Authentication
Authentication validates a user name and password combination when a user attempts to log in.
When a user attempts to log in through the console, Telnet, SSH, SCP, or FTP, the 7705 SAR client sends an access request to a RADIUS, TACACS+, or local database.
Transactions between the client and a RADIUS server are authenticated through the use of a shared secret. The secret is never transmitted over the network. User passwords are sent encrypted between the client and RADIUS server, which prevents someone snooping on an insecure network to learn password information.
If the RADIUS server does not respond within a specified time, the router issues the access request to the next configured servers. Each RADIUS server must be configured identically to guarantee consistent results. Up to five RADIUS servers can be configured.
If a server is unreachable, it will not be used again by the RADIUS application until 30 seconds have elapsed, to give the server time to recover from its unreachable state. After 30 seconds, the unreachable server becomes available again for the RADIUS application.
If, within the 30 seconds, the RADIUS server receives a valid response to a previously sent RADIUS packet on that unreachable server, the server immediately becomes available again.
If any RADIUS server rejects the authentication request, it sends an access reject message to the router. In this case, no access request is issued to any other RADIUS servers. However, if other authentication methods such as TACACS+ and/or local are configured, then these methods are attempted. If no other authentication methods are configured, or all methods reject the authentication request, then access is denied.
The user login is successful when the RADIUS server accepts the authentication request and responds to the router with an access accept message.
Implementing authentication without authorization for the 7705 SAR does not require the configuration of VSAs (Vendor Specific Attributes) on the RADIUS server. However, users, user access permissions, and command authorization profiles must be configured on each router.
Any combination of these authentication methods can be configured to control network access from a 7705 SAR router:
Local Authentication
Local authentication uses user names and passwords configured on the router to authenticate login attempts. The user names and passwords are local to each router, not to user profiles.
By default, local authentication is enabled. When one or more of the other security methods are enabled, local authentication is disabled. Local authentication is restored when the other authentication methods are disabled. Local authentication is attempted if the other authentication methods fail and local is included in the authentication order password parameters.
Locally, you can configure user names and password management information. This is referred to as local authentication. Remote security servers such as RADIUS or TACACS+ are not enabled.
RADIUS Authentication
Remote Authentication Dial-In User Service (RADIUS) is a client/server security protocol and software that enables remote access servers to communicate with a central server to authenticate dial-in users and authorize access to the requested system or service.
RADIUS allows you to maintain user profiles in a shared central database and provides better security, allowing a company to set up a policy that can be applied at a single administered network point.
RADIUS Server Selection
Up to five RADIUS servers can be configured. They can be selected to authenticate user requests in two ways, using either the direct method or the round-robin method. The default method is direct.
Direct
In direct mode, the first server, as defined by the server-index command, is the primary server. This server is always used first when authenticating a request.
Round-robin
In round-robin mode, the server used to authenticate a request is the next server in the list, following the last authentication request. For example, if server 1 is used to authenticate the first request, server 2 is used to authenticate the second request, and so on.
TACACS+ Authentication
Terminal Access Controller Access Control System, commonly referred to as TACACS, is an authentication protocol that allows a remote access server to forward a user's login password to an authentication server to determine whether access can be allowed to a given system. TACACS is an encryption protocol and therefore less secure than the later Terminal Access Controller Access Control System Plus (TACACS+) and RADIUS protocols.
TACACS+ and RADIUS have largely replaced earlier protocols in the newer or recently updated networks. TACACS+ uses Transmission Control Protocol (TCP) and RADIUS uses the User Datagram Protocol (UDP). TACACS+ is popular as TCP is thought to be a more reliable protocol. RADIUS combines authentication and authorization. TACACS+ separates these operations.
Authorization
The 7705 SAR supports local, RADIUS, and TACACS+ authorization to control the actions of specific users by applying a profile based on user name and password configurations once network access is granted. The profiles are configured locally as well as on the RADIUS server as VSAs. See Vendor-Specific Attributes (VSAs).
Once a user has been authenticated using RADIUS (or another method), the 7705 SAR router can be configured to perform authorization. The RADIUS server can be used to:
- download the user profile to the 7705 SAR router
- send the profile name that the node should apply to the 7705 SAR router
Profiles consist of a suite of commands that the user is allowed or not allowed to execute. When a user issues a command, the authorization server looks at the command and the user information and compares it with the commands in the profile. If the user is authorized to issue the command, the command is executed. If the user is not authorized to issue the command, then the command is not executed.
Profiles must be created on each 7705 SAR router and should be identical for consistent results. If the profile is not present, then access is denied.
Table 2 displays the following scenarios.
- If the user is authenticated locally (on the 7705 SAR router), local authorization is supported and remote (RADIUS) authorization cannot be performed.
- If the user is authenticated by the RADIUS server, both local authorization and remote (RADIUS) authorization are supported.
- If the user is TACACS+ authenticated, local authorization is supported and remote (RADIUS) authorization cannot be performed.
When authorization is configured and profiles are downloaded to the router from the RADIUS server, the profiles are considered temporary configurations and are not saved when the user session terminates.
Table 2: Supported Authorization Configurations
Local Authorization | RADIUS Authorization | |
7705 SAR configured user | Supported | Not Supported |
RADIUS server configured user | Supported | Supported |
TACACS+ server configured user | Supported | Not Supported |
When using authorization, maintaining a user database on the router is not required. User names can be configured on the RADIUS server. User names and their associated passwords are temporary and are not saved in the configuration database when the user session terminates.
Local Authorization
Local authorization uses user profiles and user access information after a user is authenticated. The profiles and user access information specify the actions the user can and cannot perform.
By default, local authorization is enabled. Local authorization is disabled only when a different remote authorization method is configured (RADIUS authorization or TACACS+). Local authorization is restored when RADIUS authorization is disabled.
You must configure profile and user access information locally.
RADIUS Authorization
RADIUS authorization grants or denies access permissions for a 7705 SAR router. Permissions include the use of FTP, Telnet, SSH (SCP), and console access. When granting Telnet, SSH (SCP) and console access to the 7705 SAR router, authorization can be used to limit what CLI commands the user is allowed to issue and which file systems the user is allowed or denied access to.
TACACS+ Authorization
Like RADIUS authorization, TACACS+ grants or denies access permissions for a 7705 SAR router. The TACACS+ server sends a response based on the user name and password.
TACACS+ separates the authentication and authorization functions. RADIUS combines the authentication and authorization functions.
Accounting
Accounting tracks user activity to a specific host. The 7705 SAR supports RADIUS and TACACS+ accounting.
RADIUS Accounting
When enabled, RADIUS accounting sends command line accounting from the 7705 SAR router to the RADIUS server. The router sends accounting records using UDP packets at port 1813 (decimal).
The router issues an accounting request packet for each event requiring the activity to be recorded by the RADIUS server. The RADIUS server acknowledges each accounting request by sending an accounting response after it has processed the accounting request. If no response is received in the time defined in the timeout parameter, the accounting request must be retransmitted until the configured retry count is exhausted. A trap is issued to alert the NMS (or trap receiver) that the server is unresponsive. The router issues the accounting request to the next configured RADIUS server (up to 5).
User passwords and authentication keys of any type are never transmitted as part of the accounting request.
When RADIUS accounting is enabled, the server is responsible for receiving accounting requests and returning a response to the client indicating that it has successfully received the request. Each command issued on the 7705 SAR router generates a record sent to the RADIUS server. The record identifies the user who issued the command and the timestamp.
Accounting can be configured independently from RADIUS authorization and RADIUS authentication.
TACACS+ Accounting
The 7705 SAR allows you to configure the type of accounting record packet that is to be sent to the TACACS+ server when specified events occur on the device. The accounting record-type parameter indicates whether TACACS+ accounting start and stop packets will be sent or just stop packets will be sent. A start packet is sent to a TACACS+ server when an authenticated user establishes a Telnet or SSH session and a stop packet is sent when the user logs out.
When a user logs in to request access to the network using Telnet or SSH, or a user enters a command for which accounting parameters are configured, or a system event occurs, such as a reboot or a configuration file reload, the 7705 SAR checks the configuration to see if TACACS+ accounting is required for the particular event.
If TACACS+ accounting is required, then, depending on the accounting record type specified, the device sends a start packet to the TACACS+ accounting server that contains information about the event.
The TACACS+ accounting server acknowledges the start packet and records information about the event. When the event ends, the device sends a stop packet. The stop packet is acknowledged by the TACACS+ accounting server.
Security Controls
You can configure the 7705 SAR to use RADIUS, TACACS+, and local authentication to validate users requesting access to the network. The order in which password authentication is processed among RADIUS, TACACS+ and local passwords can be specifically configured. For example, the authentication order can be configured to process authorization via TACACS+ first, then RADIUS for authentication and accounting. Local access can be specified next in the authentication order in the event that the RADIUS and TACACS+ servers are not operational.
When a Server Does Not Respond
A trap is issued if a RADIUS server is unresponsive. An alarm is raised if RADIUS is enabled with at least one RADIUS server and no response is received to either accounting or user access requests from any server.
Periodic checks to determine if the primary server is responsive again are performed. If a server is down, it will not be contacted for 5 minutes. If a login is attempted after 5 minutes, then the server is contacted again. If a server has the health check feature enabled and is unresponsive, the server’s status is checked every 30 seconds. Health check is enabled by default. When a service response is restored from at least one server, the alarm condition is cleared. Alarms are raised and cleared on the Alcatel-Lucent Fault Manager or other third party fault management servers.
The servers are accessed in order from lowest to highest specified index (from 1 to 5) for authentication requests until a response from a server is received. A higher indexed server is only queried if no response is received from a lower indexed server. If a response from the server is received, no other server is queried.
Access Request Flow
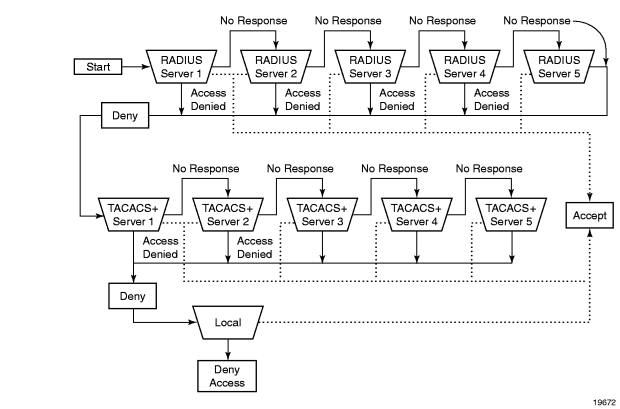
In Figure 2, the authentication process is defined in the config>system>security> password context. The authentication order is determined by specifying the sequence in which password authentication is attempted among RADIUS, TACACS+, and local servers.
This example uses the authentication order of RADIUS, then TACACS+, and finally, local. An access request is sent to RADIUS server 1. One of two scenarios can occur. If there is no response from the server, the request is passed to the next RADIUS server with the next lowest index (RADIUS server 2) and so on, until the last RADIUS server is attempted (RADIUS server 5). If server 5 does not respond, the request is passed to the TACACS+ server 1. If there is no response from that server, the request is passed to the next TACACS+ server with the next lowest index (TACACS+ server 2) and so on.
If a request is sent to an active RADIUS server and the user name and password are not recognized, access is denied and passed on to the next authentication option, in this case, the TACACS+ server. The process continues until the request is either accepted, denied, or each server is queried. Finally, if the request is denied by the active TACACS+ server, the local parameters are checked for user name and password verification. This is the last chance for the access request to be accepted.
Figure 2: Security Flow
Vendor-Specific Attributes (VSAs)
The 7705 SAR software supports the configuration of Alcatel-Lucent-specific RADIUS attributes. These attributes are known as vendor-specific attributes (VSAs) and are discussed in RFC 2138. VSAs must be configured when RADIUS authorization is enabled. It is up to the vendor to specify the format of their VSA. The attribute-specific field is dependent on the vendor's definition of that attribute. The Alcatel-Lucent-defined attributes are encapsulated in a RADIUS vendor-specific attribute with the vendor ID field set to 6527, the vendor ID number.
Note that “PE-Record” should be added as a new standard attribute in the standard RADIUS dictionary file.
The following RADIUS VSAs are supported by Alcatel-Lucent:
- timetra-access <ftp> <console> <both> — this is a mandatory command that must be configured. This command specifies whether the user has FTP and /or console (serial port, Telnet, and SSH) access.
- timetra-profile <profile-name> — when configuring this VSA for a user, it is assumed that the user profiles are configured on the local 7705 SAR router and the following applies for local and remote authentication:
- The authentication-order parameters configured on the router must include the local keyword.
- The user name may or may not be configured on the 7705 SAR router.
- The user must be authenticated by the RADIUS server.
- Up to eight valid profiles can exist on the router for a user. The sequence in which the profiles are specified is relevant. The most explicit matching criteria must be ordered first. The process stops when the first complete match is found.
- If all the above-mentioned conditions are not met, then access to the router is denied and a failed login event/trap is written to the security log.
- timetra-default-action <permit-all | deny-all | none> — this is a mandatory command that must be configured even if the timetra-cmd VSA is not used. This command specifies the default action when the user has entered a command and no entry configured in the timetra-cmd VSA for the user resulted in a match condition.
- timetra-cmd <match-string> — configures a command or command subtree as the scope for the match conditionThe command and all subordinate commands in subordinate command levels are specified.Configure from most specific to least specific. The 7705 SAR exits on the first match; subordinate levels cannot be modified with subsequent action commands. Subordinate level VSAs must be entered prior to this entry to be effective.All commands at and below the hierarchy level of the matched command are subject to the timetra-action VSA.Multiple match-strings can be entered in a single timetra-cmd VSA. Match strings must be semicolon (;) separated (maximum string length is 254 characters).
One or more timetra-cmd VSAs can be entered followed by a single timetra-action VSA:
- timetra-action <deny | permit> — causes the permit or deny action to be applied to all match strings specified since the last timetra-action VSA
- timetra-home-directory <home-directory string> — specifies the home directory that applies for the FTP and CLI user. If this VSA is not configured, the home directory is Compact Flash slot 1 (cf3: on all platforms).
- timetra-restrict-to-home-directory <true | false> — specifies if user access is limited to their home directory (and directories and files subordinate to their home directory). If this VSA is not configured, the user is allowed to access the entire file system.
- timetra-login-exec <login-exec-string> — specifies the login exec file that is executed when the user login is successful. If this VSA is not configured, no login exec file is applied.
If no VSAs are configured for a user, then the following applies.
- The password authentication-order command on the 7705 SAR router must include local.
- The user name must be configured on the 7705 SAR router.
- The user must be successfully authenticated by the RADIUS server.
- A valid profile must exist on the 7705 SAR router for this user.
If all conditions listed above are not met, then access to the 7705 SAR router is denied and a failed login event/trap is written to the security log.
For receiving data from the RADIUS server, the following are supported:
- Juniper (vendor-id 4874) attributes 4 (Primary DNS server) and 5 (Secondary DNS server)
- Redback (vendor-id 2352) attributes 1 (Primary DNS) and 2 (Secondary DNS)
- sending authentication requests: (from the DSL Forum) (vendor-id 3561), attributes 1 (Circuit ID) and 2 (Remote ID)
Sample User (VSA) Configuration
The following example displays a user-specific VSA configuration. This configuration shows attributes for users named ruser1 and ruser2.
The following example shows that user ruser1 is granted console access. ruser1’s home directory is in compact flash slot 3 and is limited to the home directory. The default action permits all packets when matching conditions are not met. The timetra-cmd parameters allow the user to use the tools;telnet;configure system security commands. Matching strings specified in the timetra-action command are denied for this user.
The user ruser2 is granted FTP access. The default action denies all packets when matching conditions are not met. The timetra-cmd parameters allow the user to use the configure, show, and debug commands. Matching strings specified in the timetra-action command are permitted for this user.
Alcatel-Lucent Dictionary
Other Security Features
Secure Shell (SSH)
Secure Shell Version 1 (SSH1) is a protocol that provides a secure, encrypted Telnet-like connection to a router. A connection is always initiated by the client (the user). Authentication takes place by one of the configured authentication methods (local, RADIUS, or TACACS+). With authentication and encryption, SSH allows for a secure connection over an insecure network.
The 7705 SAR allows you to configure SSH1 or Secure Shell Version 2 (SSH2). SSH1 and SSH2 are different protocols and encrypt at different parts of the packets. SSH1 uses the server as well as host keys to authenticate systems, whereas SSH2 only uses host keys. SSH2 does not use the same networking implementation that SSH1 does and is considered a more secure, efficient, and portable version of SSH. Rather than validating identities via passwords, SSH2 can also use public key encryption to authenticate remote hosts. For example, if you were to connect to a remote host also running SSH2, the secure shell would use this system to verify that the remote system is the host and not a computer set up to imitate it.
SSH runs on top of a transport layer (like TCP or IP), and provides authentication and encryption capabilities. SSH supports remote login to another computer over a network, remote command execution, and file relocation from one host to another.
The 7705 SAR has a global SSH server process to support inbound SSH and SCP sessions initiated by external SSH or SCP client applications. The SSH server supports SSH1. Note that this server process is separate from the SSH and SCP client commands on the 7705 SAR, which initiate outbound SSH and SCP sessions.
Inbound SSH sessions are counted as inbound Telnet sessions for the purposes of the maximum number of inbound sessions specified by Login Control. Inbound SCP sessions are counted as inbound FTP sessions by Login Control.
When the SSH server is enabled, an SSH security key is generated. The key is only valid until either the node is restarted or the SSH server is stopped and restarted. The key size is non-configurable and set at 1024 bits. When the server is enabled, both inbound SSH and SCP sessions will be accepted provided the session is properly authenticated.
When the global SSH server process is disabled, no inbound SSH or SCP sessions will be accepted.
When using SCP to copy files from an external device to the file system, the 7705 SAR SCP server will accept either forward slash (“/”) or backslash (“\”) characters to delimit directory and/or filenames. Similarly, the 7705 SAR SCP client application can use either slash or backslash characters, but not all SCP clients treat backslash characters as equivalent to slash characters. In particular, UNIX systems will often interpret the backslash character as an “escape” character, which does not get transmitted to the 7705 SAR SCP server. For example, a destination directory specified as “cf3:\dir1\file1” will be transmitted to the 7705 SAR SCP server as “cf3:dir1file1”, where the backslash escape characters are stripped by the SCP client system before transmission. On systems where the client treats the backslash like an “escape” character, a double backslash “\\” or the forward slash “/” can typically be used to properly delimit directories and the filename.
The 7705 SAR support for SSH and SCP is the same for both IPv4 and IPv6 addressing, including support for:
- SSH1 and SSH2
- in-band and out-of-band management of the 7705 SAR
- key management and authentication types
- encryption types
- simultaneous IPv4 and IPv6 SSH/SCP sessions
CSM Filters and CSM Security
IP forwarding supports CSM filters that are applied to IP packets extracted to the control plane. CSM filters are used to protect the control plane from DoS attacks, unauthorized access to the node, and similar security breaches.
IP filters scan all traffic and take the appropriate (configured) action against matching packets. Packets that are not filtered by the IP filters and are destined for the 7705 SAR are scanned by the configured CSM filter.
For information on IP filters, refer to the 7705 SAR OS Router Configuration Guide.
| Note:
Although the Control and Switching module on the 7705 SAR is called a CSM, the CSM filters are referred to as CPM filters in the CLI in order to maintain consistency with other SR routers. |
Both IPv4 and IPv6 CSM filters are supported.
IPv4 CSM filters drop or accept incoming packets based on the following match criteria:
- DSCP name
- destination IP address
- destination port
- fragmentation
- ICMP code
- ICMP type
- IP option value
- multiple options
- option present
- source IP address
- source port
- TCP ACK
- TCP SYN
IPv6 CSM filters drop or accept incoming packets based on the following match criteria:
- DSCP name
- destination IP address
- destination port
- ICMP code
- ICMP type
- source IP address
- source port
- TCP ACK
- TCP SYN
To avoid DoS-like attacks overwhelming the control plane while ensuring that critical control traffic such as signaling is always serviced in a timely manner, the 7705 SAR has three queues (High, Low, and Ftp) for handling packets addressed to the CSM:
- High – handles all important messaging, such as network management and signaling links
- Low – handles lower-importance messages, such as pings
- Ftp – handles bulk file transfers, such as new software image downloads
These queues are fixed use (each queue handles a certain type of traffic, which is not user-configurable) and fixed configuration (each queue is configured for particular rates and buffering capacity and is not user-configurable).
Exponential Login Backoff
A malicious user can gain CLI access via a dictionary attack: using a script to try “admin” with any password.
The 7705 SAR increases the delay between login attempts exponentially to mitigate attacks. It is applied to the console login. SSH and Telnet sessions terminate after four attempts.
Encryption
Data Encryption Standard (DES) and Triple DES (3DES) are supported for encryption.
- DES is a widely used method of data encryption using a private (secret) key. Both the sender and the receiver must know and use the same private key.
- 3DES is a more secure version of the DES protocol.
802.1x Network Access Control
The 7705 SAR supports network access control of client devices (PCs, STBs, and so on) on an Ethernet network using the IEEE 802.1x standard. 802.1x is known as Extensible Authentication Protocol (EAP) over a LAN network or EAPOL.
Refer to the 7705 SAR OS Interface Configuration Guide for more information about IEEE 802.1x.
Configuration Notes
This section describes security configuration caveats.
- If a RADIUS or a TACACS+ server is not configured, then password, profiles, and user access information must be configured on each router in the domain.
- If RADIUS authorization is enabled, then VSAs must be configured on the RADIUS server.
Reference Sources
For information on supported IEEE standards, IETF drafts and standards as well as standard and proprietary MIBs, refer to Standards and Protocol Support.