Configuration Note Internet Protocol Security (IPSec) Last
Updated: 2014-08-08 Version
1.2

Introduction:
The IP Security (IPSec) architecture consists of a suite of protocols developed to ensure integrity, confidentiality and authentication of data communications over an IP network. IPSec operates at the network layer (OSI layer 3). IPSec can be used for protecting layer 4 protocols, including both TCP and UDP. An application does not need to be specifically designed to use IPSec.
The primary function of IPSec includes:
· Encryption
o A security mechanism used to transform data from an intelligible form (plaintext) into an unintelligible form (cipher text) using an algorithm, to provide confidentiality.
o The inverse transformation process is called "decryption".
· Authentication
o Authentication is the act of establishing or confirming something (or someone) as authentic. IPSec also includes protocols for cryptographic key establishment.
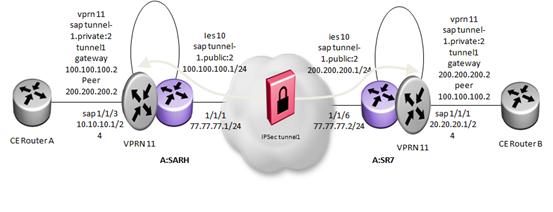
Setup 1: Static LAN-to-LAN tunnels
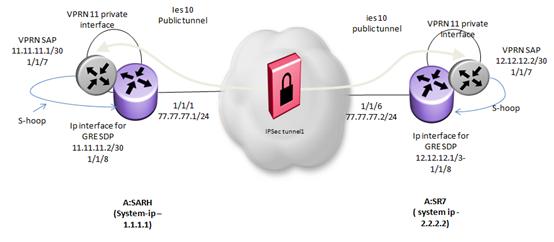
Setup 2: GRE SDP over IPSec tunnel
Prerequisites:
This Configuration Note assumes that the following base configuration has been implemented on the PEs:
- Cards, MDAs and ports configured
- Interfaces configured
Static LAN-to-LAN tunnels
The 7705 SAR supports only Static LAN-to-LAN tunnels and below is the step-by-step procedure to configure and verify.
1. Configure an Internet interface or IES interface that provides IP reachability to the tunnel peers in the Global Routing Table (GRT).
*A:SAR-H>config>router# interface to-SR
*A:SAR-H>config>router>if# info
----------------------------------------------
address 77.77.77.1/24
port 1/1/1
dhcp
shutdown
exit
----------------------------------------------
*A:SR7>config>router# interface "to-SAR"
*A:SR7>config>router>if# info
----------------------------------------------
address 77.77.77.2/24
port 1/1/6
no shutdown
----------------------------------------------
2. Tunnel group configuration – the 7705 SAR supports only 1 tunnel group and multiple IPSec tunnels can be configured with the same tunnel group.
*A:SAR-H# configure isa
*A:SAR-H>config>isa# info
----------------------------------------------
tunnel-group 1 create
no shutdown
exit
----------------------------------------------
A:SR7# configure card 1 mda 2
A:SR7>config>card>mda# info
----------------------------------------------
mda-type isa-tunnel
no shutdown
----------------------------------------------
A:SR7>config>isa# info
----------------------------------------------
tunnel-group 1 create
primary 1/2
no shutdown
exit
----------------------------------------------
3. IPSec public interface configuration - IPSec public interface represents the public side of the IPSec encryption engine. Only IES can be configured as a public interface.
*A:SAR-H>config>service>ies 10
A:SAR-H>config>service>ies# info
----------------------------------------------
interface "Public-to-SR" create
address 100.100.100.1/24
sap tunnel-1.public:2 create
exit
exit
no shutdown
----------------------------------------------
A:SR7# configure service ies 10
A:SR7>config>service>ies# info
----------------------------------------------
interface "Public-to-SAR" create
address 200.200.200.1/24
tos-marking-state untrusted
sap tunnel-1.public:2 create
exit
exit
no shutdown
4. IPSec private interface and tunnel configuration –
Below are the mandatory policy configurations required to create an IPSec private interface.
a. Security policy: the tunnel cannot be enabled without security policy.
Security policy can be used to allow traffic only from certain IP address ranges by configuring a local and remote IP address.
*A:SAR-H>config>service>vprn# info
----------------------------------------------
ipsec
security-policy 1 create
entry 1 create
local-ip any
remote-ip any
exit
exit
exit
A:SR7# configure service vprn 11
A:SR7>config>service>vprn# info
----------------------------------------------
ipsec
security-policy 1 create
entry 1 create
local-ip any
remote-ip any
exit
exit
exit
b. Transform policy: this policy defines the authentication and encryption algorithm used by ESP. This policy is also required to enable the tunnel .
*A:SAR-H>config>ipsec# ipsec-transform 1
*A:SAR-H>config>ipsec>transform# info detail
----------------------------------------------
esp-auth-algorithm sha1
esp-encryption-algorithm aes128
----------------------------------------------
A:SR7>config>ipsec# ipsec-transform 1 create
A:SR7>config>ipsec>transform# info detail
----------------------------------------------
esp-auth-algorithm sha1
esp-encryption-algorithm aes128
----------------------------------------------
c. IKE policy: this policy defines the parameters describing the IKE session itself. Only 1 IKE policy per tunnel is required and the 7705 SAR supports only IKEv2.
*A:SAR-H>config>ipsec# ike-policy 1 create
*A:SAR-H>config>ipsec>ike-policy# info detail
----------------------------------------------
no description
no auth-method
no own-auth-method
no dh-group
no ipsec-lifetime
no isakmp-lifetime
no pfs
auth-algorithm sha1
encryption-algorithm aes128
no nat-traversal
no dpd
----------------------------------------------
On the SR, the default IKE version is 1 and has to be changed to version 2.
A:SR7>config>ipsec>ike-policy# info detail
----------------------------------------------
no description
ike-version 2
no ike-mode
no auth-method
no own-auth-method
no dh-group
no ipsec-lifetime
no isakmp-lifetime
no pfs
auth-algorithm sha1
encryption-algorithm aes128
no nat-traversal
no dpd
no match-peer-id-to-cert
----------------------------------------------
Tunnel configuration:
The private IPSec interface represents the private/protected side of the encryption engine. Only VPRN can be configured as a private interface. The private VPRN SAP configuration is similar to the public IES SAP configuration, except that the keyword “private” replaces “public”.
- Local gateway and public IES addresses must be in the same subnet.
- Delivery service ID must be the public IES service ID.
- Peer Gateway address is the remote peer’s gateway IP address.
- Pre-shared-key must match the remote peer’s configuration.
*A:SAR-H# configure service vprn 11
*A:SAR-H>config>service>vprn# info
interface "Private-ipsec" tunnel create
no ip-mtu
sap tunnel-1.private:2 create
ipsec-tunnel "toSR" create
security-policy 1
local-gateway-address 100.100.100.2 peer 200.200.200.2 delivery-service 10
dynamic-keying
ike-policy 1
pre-shared-key "alcatel"
transform 1
exit
no shutdown
exit
exit
exit
A:SR7# configure service vprn 11
A:SR7>config>service>vprn# info
----------------------------------------------
interface "Private-to-SAR" tunnel create
sap tunnel-1.private:2 create
ipsec-tunnel "toSAR" create
security-policy 1
local-gateway-address 200.200.200.2 peer 100.100.100.2 delivery-service 10
dynamic-keying
ike-policy 1
pre-shared-key "alcatel"
transform 1
exit
no shutdown
exit
exit
exit
----------------------------------------------
Complete VPRN configuration:
A static route is required to route CE traffic through the IPSec tunnel.
*A:SAR-H# configure service vprn 11
*A:SAR-H>config>service>vprn# info
----------------------------------------------
ipsec
security-policy 1 create
entry 1 create
local-ip any
remote-ip any
exit
exit
exit
route-distinguisher 65001:105
vrf-target target:65001:105
interface "towards-CE" create
address 10.10.10.1/24
sap 1/1/3 create
exit
exit
interface "Private-ipsec" tunnel create
no ip-mtu
sap tunnel-1.private:2 create
ipsec-tunnel "toSR" create
security-policy 1
local-gateway-address 100.100.100.2 peer 200.200.200.2 delivery-service 10
dynamic-keying
ike-policy 1
pre-shared-key "alcatel"
transform 1
exit
no shutdown
exit
exit
exit
static-route 20.20.20.0/24 ipsec-tunnel "toSR"
no shutdown
----------------------------------------------
*A:SR7#configure service vprn 11 customer 1 create
*A:SR7>config>service>vprn# info
----------------------------------------------
ipsec
security-policy 1 create
entry 1 create
local-ip any
remote-ip any
exit
exit
exit
route-distinguisher 65001:105
vrf-target target:65001:105
interface "Private-to-SAR" tunnel create
sap tunnel-1.private:2 create
ipsec-tunnel "toSAR" create
security-policy 1
local-gateway-address 200.200.200.2 peer 100.100.100.2 delivery-service 10
dynamic-keying
ike-policy 1
pre-shared-key "alcatel"
transform 1
exit
no shutdown
exit
exit
exit
interface "to-CE" create
address 20.20.20.1/24
sap 1/1/1 create
exit
exit
static-route 10.10.10.0/24 ipsec-tunnel "toSAR"
no shutdown
exit
The local gateway address must be routable through the network using either static routes or dynamic routing protocol. Below is the static route configuration in this setup.
*A:SAR-H# configure router
*A:SAR-H>config>router# info
----------------------------------------------
<SNIP>
#--------------------------------------------------
echo "Static Route Configuration"
#--------------------------------------------------
static-route 200.200.200.0/24 next-hop 77.77.77.2
#--------------------------------------------------
*A:SR7#configure service vprn 11 customer 1 create
*A:SR7>
config>router# info
----------------------------------------------
<SNIP>
#--------------------------------------------------
echo "Static Route Configuration"
#--------------------------------------------------
static-route 100.100.100.0/24 next-hop 77.77.77.1
Triggering tunnel setup:
By default, the tunnel negotiation does not happen automatically unless “auto-established” is configured under the tunnel. A data packet could trigger the tunnel setup .
This can be done with a ping from a private address reachable in the local VPRN to a private address reachable at the other side of the tunnel.
*A:CE-A# ping 20.20.20.2
PING 20.20.20.2 56 data bytes
64 bytes from 20.20.20.2: icmp_seq=2 ttl=62 time=0.906ms.
64 bytes from 20.20.20.2: icmp_seq=3 ttl=62 time=0.918ms.
64 bytes from 20.20.20.2: icmp_seq=4 ttl=62 time=0.910ms.
64 bytes from 20.20.20.2: icmp_seq=5 ttl=62 time=0.911ms.
Request timed out. icmp_seq=1.
---- 20.20.20.2 PING Statistics ----
5 packets transmitted, 4 packets received, 20.00% packet loss
round-trip min = 0.906ms, avg = 0.911ms, max = 0.918ms, stddev = 0.015ms
*A:CE-A#
Verification:
Use <show ipsec tunnel> to display tunnel name, status, peer IP addresses, etc.
*A:SAR-H# show ipsec tunnel
==============================================================================
IPsec Tunnels
==============================================================================
TunnelName LocalAddress SvcId Admn Keying
SapId RemoteAddress DlvrySvcId Oper Sec
Plcy
------------------------------------------------------------------------------
toSR 100.100.100.2 11 Up Dynamic
tunnel-1.private:2 200.200.200.2 10 Up 1
------------------------------------------------------------------------------
IPsec Tunnels: 1
==============================================================================
Use <show ipsec tunnel <ipsec-tunnel-name>> to display the IPSec tunnel configuration.
*A:SAR-H# show ipsec tunnel toSR
===============================================================================
IPsec Tunnel Configuration Detail
===============================================================================
Service Id : 11 Sap Id : tunnel-1.private:2
Tunnel Name : toSR
Description : None
Local Address : 100.100.100.2 Remote Address : 200.200.200.2
Delivery Service : 10 Security Policy : 1
Admin State : Up Oper State : Up
Keying Type : Dynamic Replay Window : None
Clear DF Bit : false IP MTU : max
Oper Flags : None
-------------------------------------------------------------------------------
BFD Interface
-------------------------------------------------------------------------------
BFD Designate : no
-------------------------------------------------------------------------------
Dynamic Keying Parameters
-------------------------------------------------------------------------------
Transform Id1 : 1 Transform Id2 : None
Transform Id3 : None Transform Id4 : None
Ike Policy Id : 1 Auto Establish : disabled
PreShared Key:alcatel
-------------------------------------------------------------------------------
ISAKMP-SA
-------------------------------------------------------------------------------
State : Up
Established : 01/23/2000 13:13:45 Lifetime : 86400
Expires : 01/24/2000 13:13:44
ISAKMP Statistics
--------------------
Tx Packets : 1 Rx Packets : 1
Tx Errors : 0 Rx Errors : 0
Tx DPD : 0 Rx DPD : 0
Tx DPD ACK : 0 Rx DPD ACK : 0
DPD Timeouts : 0 Rx DPD Errors : 0
-------------------------------------------------------------------------------
IPsec-SA : 1, Inbound (index 1)
-------------------------------------------------------------------------------
Type : Dynamic
SPI : 20172
Auth Algorithm : Sha1 Encr Algorithm : Aes128
Installed : 01/23/2000 20:56:37 Lifetime : 3600
Aggregate Statistics
--------------------
Bytes Processed : 336 Packets Processed: 4
Crypto Errors : 0 Replay Errors : 0
SA Errors : 0 Policy Errors : 0
-------------------------------------------------------------------------------
IPsec-SA : 1, Outbound (index 1)
-------------------------------------------------------------------------------
Type : Dynamic
SPI : 523424
Auth Algorithm : Sha1 Encr Algorithm : Aes128
Installed : 01/23/2000 20:56:37 Lifetime : 3600
Aggregate Statistics
--------------------
Bytes Processed : 336 Packets Processed: 4
Crypto Errors : 0 Replay Errors : 0
SA Errors : 0 Policy Errors : 0
Use <show ipsec ike-policy> to display the configured IKE policy parameters such as encryption and authentication algorithms.
*A:SAR-H# show ipsec ike-policy
===============================================================================
IPsec IKE Policies
===============================================================================
Id Ike Ike DH Pfs Pfs Auth Encr Isakmp IPsec Auth DPD NAT
Mode Ver DH Alg Alg Life- Life- Method
time time
-------------------------------------------------------------------------------
1 Main 2 2 False 2 Sha1 Aes128 86400 3600 psk disable disable
-------------------------------------------------------------------------------
No. of IPsec IKE Policies: 1
===============================================================================
Use <show ipsec security-policy <service-id> <security-policy-id>> to display the local/remote IP addresses configured.
*A:SAR-H# show ipsec security-policy 11 1
========================================================================
Security Policy Param Entries
========================================================================
SvcId Security Policy LocalIp RemoteIp
PlcyId ParamsId
------------------------------------------------------------------------
11 1 1 any any
------------------------------------------------------------------------
No. of IPsec Security Policy Param Entries: 1
========================================================================
Use <show ipsec transform> to display the configured ESP encryption and authentication algorithms.
*A:SAR-H# show ipsec transform
================================================================
IPsec Transforms
================================================================
TransformId EspAuthAlgorithm EspEncryptionAlgorithm
----------------------------------------------------------------
1 Sha1 Aes128
----------------------------------------------------------------
No. of IPsec Transforms: 1
================================================================
Use <show mda <slot/mda> statistics <security> <encryption>> to display the queue statistics on the encryption engine.
*A:SAR-H# show mda 1/1 statistics security encryption
===============================================================================
MDA 1/1 Security Statistics
===============================================================================
-------------------------------------------------------------------------------
IPsec Datapath Statistics
-------------------------------------------------------------------------------
Encrypted packets : 31
Encrypted bytes : 2604
Outbound dropped packets : 18
Outbound SA misses : 18
Outbound policy entry misses : 0
Decrypted packets : 80
Decrypted bytes : 6720
Inbound dropped packets : 0
Inbound SA misses : 0
Inbound IP dst/src mismatches : 0
Transmit packet errors : 0
Drop Too Big/Df-set Pkts : 0
-------------------------------------------------------------------------------
IPsec Control Statistics (System Wide)
-------------------------------------------------------------------------------
Static IPsec Tunnels : 1
Dynamic IPsec Tunnels : 0
-------------------------------------------------------------------------------
IPsec Queue Statistics
-------------------------------------------------------------------------------
Decryption Queue Best-effort Packets Bytes
Hi Priority forwarded : 0 0
Hi Priority dropped : 0 0
Low Priority forwarded : 80 10560
Low Priority dropped : 0 0
Decryption Queue Expedited Packets Bytes
Hi Priority forwarded : 0 0
Hi Priority dropped : 0 0
Low Priority forwarded : 0 0
Low Priority dropped : 0 0
Encryption Queue Best-effort Packets Bytes
In Profile forwarded : 0 0
In Profile dropped : 0 0
Out Profile forwarded : 26 2184
Out Profile dropped : 0 0
Encryption Queue Expedited Packets Bytes
In Profile forwarded : 0 0
In Profile dropped : 0 0
Out Profile forwarded : 0 0
Out Profile dropped : 0 0
Encryption Queue CTL Packets Bytes
Forwarded : 5 420
Dropped : 0 0
===============================================================================
Use <show pools mda <slot/mda> detail> to display the encryption/decryption queue utilization.
*A:SAR-H# show pools mda 1/1 detail
===============================================================================
Buffer Pool Information (Shared among all ports in the system)
Pool Total : 524287 buffers Buffer Size : 512 bytes
Pool Shared : 434007 buffers Pool Resv : 90280 buffers
Pool Total In Use : 75 buffers
Pool Exhaustion Drop : 0
ß--SNIP--->
=============================================================
IPsec Queues
=============================================================
-------------------------------------------------------------
Queue Name O.MBS(buf) Depth(buf)
O.CBS(buf)
-------------------------------------------------------------
Decryption Best-effort 131072 0
1024
Decryption Expedited 20480 0
1024
Encryption Best-effort 131072 0
1024
Encryption Expedited 20480 0
1024
=============================================================
GRE SDP over IPSec tunnel
Refer to the Figure shown in Setup 2.
Configure the VPRN SAP that is s-hooked to the IP interface for creating the GRE SDP.
*A:SAR-H>config>service>vprn# info
<SNIP>
interface "GRE-interface" create
address 11.11.11.1/30
sap 1/1/7 create
exit
exit
*A:SR7>config>service>vprn# info
<SNIP>
interface "GRE-interface" create
address 12.12.12.1/30
sap 1/1/7 create
exit
exit
Configure the IP interface that is physically s-hooked to the VPRN SAP.
*A:SAR-H# configure router interface Interface-GRE-S-hook
*A:SAR-H>config>router>if# info
----------------------------------------------
address 11.11.11.2/30
port 1/1/8
dhcp
shutdown
exit
----------------------------------------------
*A:SR7# configure router interface "Interface-GRE-Shook"
*A:SR7>config>router>if# info
----------------------------------------------
address 12.12.12.2/30
port 1/1/8
no shutdown
----------------------------------------------
Configure the static route to remote system address in the GRT to route via VPRN.
*A:SAR-H# configure router
*A:SAR-H>config>router# info
<SNIP>
#--------------------------------------------------
echo "Static Route Configuration"
#--------------------------------------------------
static-route 2.2.2.2/32 next-hop 11.11.11.1 static-route 200.200.200.0/24 next-hop 77.77.77.2
*A:SR7>config>router# info
----------------------------------------------
<SNIP>
#--------------------------------------------------
echo "Static Route Configuration"
#--------------------------------------------------
static-route 1.1.1.1/32 next-hop 12.12.12.1
static-route 100.100.100.0/24 next-hop 77.77.77.1
Configure the static route in VPRN for both system interface IP addresses.
*A:SAR-H# configure service vprn 11
*A:SAR-H>config>service>vprn# info
<SNIP>
static-route 1.1.1.1/32 next-hop 11.11.11.2
static-route 2.2.2.2/32 ipsec-tunnel "toSR"
*A:SR7# configure service vprn 11
*A:SR7>config>service>vprn# info
<SNIP>
static-route 1.1.1.1/32 ipsec-tunnel "toSAR"
static-route 2.2.2.2/32 next-hop 12.12.12.2
Configuring GRE SDP
*A:SAR-H# configure service sdp 100 gre create
*A:SAR-H>config>service>sdp# info
----------------------------------------------
far-end 2.2.2.2
keep-alive
shutdown
exit
no shutdown
*A:SR7# configure service sdp 100 gre create
*A:SR7>config>service>sdp# info
----------------------------------------------
far-end 1.1.1.1
keep-alive
shutdown
exit
no shutdown
Enabling Targeted LDP session
*A:SAR-H# configure router ldp
*A:SAR-H>config>router>ldp# info
----------------------------------------------
interface-parameters
exit
targeted-session
peer 2.2.2.2
exit
exit
*A:SR7>config>router>ldp# info
----------------------------------------------
interface-parameters
exit
targeted-session
peer 1.1.1.1
exit
exit
no shutdown
Verification:
*A:SAR-H# show service sdp
===============================================================================
Services: Service Destination Points
===============================================================================
SdpId Adm MTU Opr MTU IP address Adm Opr Deliver Signal
-------------------------------------------------------------------------------
100 0 1472 2.2.2.2 Up Up GRE TLDP
-------------------------------------------------------------------------------
Number of SDPs : 1
-------------------------------------------------------------------------------
*A:SR7# show service sdp
=============================================================================
Services: Service Destination Points
=============================================================================
SdpId Adm MTU Opr MTU IP address Adm Opr Del LSP Sig
-----------------------------------------------------------------------------
100 0 1472 1.1.1.1 Up Up GRE n/a TLDP
-----------------------------------------------------------------------------
Number of SDPs : 1
-----------------------------------------------------------------------------
Legend: R = RSVP, L = LDP, B = BGP, n/a = Not Applicable
=============================================================================