7705 SAR R7.0 Configuration Note


Introduction:
• A firewall is a system designed to provide access control, traffic filtering, and other security functions between network segments.
• A firewall can also provide audit, alarm, and log notifications of traffic access attempts to and from the network.
• Firewalls are commonly deployed to protect entities in one network segment from threats and attacks originating from another network segment.
Firewall configuration:
• To enable firewall/NAT:
• Security configurations must be defined.
• Includes Policy, Profile, etc.
• Zone configurations must be defined.
• Includes assigning an IP interface to a zone and a security policy.
• A zone can be created within a base router context (GRT) and/or within an IES or VPRN service context. This configuration note covers the VPRN and IES scenarios.
Prerequisites:
This Configuration Note assumes that following base configuration has been implemented on the PEs:
- Cards, MDAs and ports configured
- Interfaces configured
- Purchase the RTU license for the firewall
Setup 1: Firewall in VPRN context
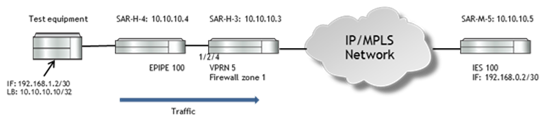
In this example, the SAR-H-4 has an EPIPE configured terminating to the VPRN in SAR-H-3.
Configuration on SAR-H-4:
A:SAR-H-4>config>service# info
----------------------------------------------
epipe 100 customer 1 create
endpoint "end1" create
revert-time 300
standby-signaling-master
exit
sap 1/2/1 create
exit
spoke-sdp 3:100 endpoint "end1" create
precedence primary
no shutdown
exit
spoke-sdp 7:100 endpoint "end1" create
precedence 2
no shutdown
exit
no shutdown
exit
----------------------------------------------
Configuration on SAR-M-5:
A:SAR-M-5# configure service ies 100
A:SAR-M-5>config>service>ies# info
----------------------------------------------
interface "to-SAR8-8-vprn" create
address 192.168.0.2/30
sap 1/1/3 create
exit
exit
no shutdown
----------------------------------------------
Firewall configuration on SAR-H-3:
1. Security policy:
A:SARHC-66>config>router>ospf# info
*A:SAR-H-3>config>security# info
----------------------------------------------
logging
log-id 10 create
destination memory 1024
no shutdown
exit
log-id 20 create
destination memory 1024
no shutdown
exit
exit
profile 2 create
application
assurance
ip
exit
icmp
request-limit 15
exit
tcp
exit
dns
exit
exit
exit
timeouts
exit
exit
policy 1 create
entry 10 create
match
direction zone-outbound #forwarding to NAT, direction can be either inbound or outbound (here is outbound because it’s leaving the zone to fabric)
src-ip 10.10.10.10 to 10.10.10.20
exit
limit
exit
action nat
profile "2"
logging to zone
exit
entry 20 create
match
exit
limit
exit
action forward
exit
exit
----------------------------------------------
2. Zone configuration in VPRN:
A:SAR-H-3>config>service>vprn# info
----------------------------------------------
route-distinguisher 65100:50
auto-bind ldp
vrf-target target:65100:50
interface "to-eNodeB" create
address 192.168.1.1/30
ip-mtu 1500
spoke-sdp 4:100 create
no shutdown
exit
exit
static-route 10.10.10.10/32 next-hop 192.168.1.2
spoke-sdp 2 create
exit
spoke-sdp 7 create
exit
spoke-sdp 8 create
exit
zone 1 create
interface "to-eNodeB"
exit
nat
pool 10 create
direction zone-outbound
entry 10 create
ip-addr interface "to-eNodeB"
port 2000 to 3000
exit
exit
exit
policy "1"
inbound
limit
exit
exit
outbound
limit
exit
exit
log "10"
commit
exit
no shutdown
----------------------------------------------
Verification:
Use <show security profile <profile-id> detail> to display the security profile information
*A:SAR-H-3# show security profile 2 detail
===============================================================================
Security Profile
===============================================================================
Profile Id : 2 Applied : Yes
Name : (Not Specified)
Description : (Not Specified)
Packet :
Fragmentation : Allowed
Application : Inspection-Enabled ALG : Auto
IP Options : Permit-All
TCP Layer : Non-Strict
ICMP Request : 15 packets ICMP Type 3 : Restrict
DNS Request : Reply-Only
Timeouts :
TCP Syn-Rcvd : strict 15 sec
TCP Transitory : strict 4 min
TCP Established: idle 2 hrs 4 min
TCP Time-Wait : none
UDP Initial : strict 15 sec
UDP Established: idle 5 min
UDP DNS : strict 15 sec
ICMP Request : strict 1 min
OTHER Sessions : idle 10 min
================================================================================
Use <show security zone <zone-id> policy detail> to display the zone security policy information.
*A:SAR-H-3# show security zone 1 policy detail
===============================================================================
Security Zone
===============================================================================
Zone Id : 1 State : Committed
Name : (Not Specified)
===============================================================================
===============================================================================
Policy
===============================================================================
Policy Id : 1 Applied : Yes
Name : (Not Specified)
Scope : Template Def. Action : Reject
Entries : 2
Description : (Not Specified)
-------------------------------------------------------------------------------
Policy Match Criteria : IP
-------------------------------------------------------------------------------
Entry : 10 Active : yes
Description : (Not Specified)
Oper. Flags : (Not Specified)
NAT Pool Id : 10
Match : OUTBOUND
Src. IP : 10.10.10.10-10.10.10.20 Src. Port : -
Dest. IP : Any Dst. Port : -
Protocol : Any
ICMP Type : - ICMP Code :
Profile : 2 Session : Bi-Direct*
Action : nat
Logging : To-Zone
Active Matches : 0 Session Limit : None
Total Matches : 6
Entry : 20 Active : yes
Description : (Not Specified)
Oper. Flags : (Not Specified)
NAT Pool Id : None
Match : INBOUND/OUTBOUND
Src. IP : Any Src. Port : -
Dest. IP : Any Dst. Port : -
Protocol : Any
ICMP Type : - ICMP Code :
Profile : DEFAULT Session : Bi-Direct*
Action : forward
Logging : Suppressed
Active Matches : 0 Session Limit : None
Total Matches : 0
-------------------------------------------------------------------------------
Num of Entries: 2
================================================================================
On the test equipment, ping 192.168.0.2 :
A:Tester# ping 192.168.0.2 source 10.10.10.10 count 20
PING 192.168.0.2 56 data bytes
64 bytes from 192.168.0.2: icmp_seq=1 ttl=62 time=61.8ms.
64 bytes from 192.168.0.2: icmp_seq=2 ttl=62 time=0.000ms.
64 bytes from 192.168.0.2: icmp_seq=3 ttl=62 time=0.000ms.
64 bytes from 192.168.0.2: icmp_seq=4 ttl=62 time=9.85ms.
64 bytes from 192.168.0.2: icmp_seq=5 ttl=62 time=1.50ms.
64 bytes from 192.168.0.2: icmp_seq=6 ttl=62 time=11.0ms.
64 bytes from 192.168.0.2: icmp_seq=7 ttl=62 time=10.7ms.
64 bytes from 192.168.0.2: icmp_seq=8 ttl=62 time=10.6ms.
64 bytes from 192.168.0.2: icmp_seq=9 ttl=62 time=10.7ms.
64 bytes from 192.168.0.2: icmp_seq=10 ttl=62 time=10.7ms.
64 bytes from 192.168.0.2: icmp_seq=11 ttl=62 time=10.7ms.
64 bytes from 192.168.0.2: icmp_seq=12 ttl=62 time=1.26ms.
64 bytes from 192.168.0.2: icmp_seq=13 ttl=62 time=0.926ms.
64 bytes from 192.168.0.2: icmp_seq=14 ttl=62 time=0.926ms.
64 bytes from 192.168.0.2: icmp_seq=15 ttl=62 time=0.927ms.
Request timed out. icmp_seq=16. # This is expected. In the policy profile, we limited the ICMP request to 15
Request timed out. icmp_seq=17.
Request timed out. icmp_seq=18.
Request timed out. icmp_seq=19.
Request timed out. icmp_seq=20.
Use <show security zone <zone-id> session> to display the zone session information.
*A:SAR-H-3# show security zone 1 session
===============================================================================
Security Zone
===============================================================================
Zone Id : 1 State : Committed
Name : (Not Specified)
===============================================================================
===============================================================================
Inbound Sessions
===============================================================================
Sess-Id Action From Source NAT Mapping
Proto ALG Rev Destination
-------------------------------------------------------------------------------
No Inbound Sessions
===============================================================================
===============================================================================
Outbound Sessions
===============================================================================
Sess-Id Action To Source NAT Mapping
Proto ALG Rev Destination
-------------------------------------------------------------------------------
00000036 NAT <Base> 10.10.10.10 -> 192.168.1.1
ICMP Y 192.168.0.2
-------------------------------------------------------------------------------
Num of Sessions: 1
===============================================================================
Use <show security zone <zone-id> session <session-id> detail> to display the session details.
*A:SAR-H-3# show security zone 1 session 36 detail
===============================================================================
Security Zone
===============================================================================
Zone Id : 1 State : Committed
Name : (Not Specified)
===============================================================================
===============================================================================
Security Session Details
===============================================================================
Session Id : 36 Action : NAT
Created : 09/24/2015 17:20:49
Protocol : ICMP ALG : None
State : ICMP-ESTABLISHED
Source : Destination :
Zone : 1 Zone : <BASE>
Ip-Address : 10.10.10.10 Ip-Address : 192.168.0.2
ICMP :
Type : 8 (echo-request)
Code : 0 (network-unreachable)
Id : 49237
Profile :
Bidirection*: Yes
CSM Inspect*: No
Timeouts :
ICMP-Requ*: strict 1 min
-------------------------------------------------------------------------------
Session Security Trace
-------------------------------------------------------------------------------
[INGRESS] VPRN-5:to-eNodeB <ZONE-1>
[ZONE-1] OUTBOUND-PLCY:1-10 Profile:2 Action:nat
[ACTION] SRC-NAT: 10.10.10.10 -> 192.168.1.1
===============================================================================
Use <show security zone <zone-id> session <session-id> statistics> to display statistics for the session
*A:SAR-H-3# show security zone 1 session 36 statistics
===============================================================================
Security Zone
===============================================================================
Zone Id : 1 State : Committed
Name : (Not Specified)
===============================================================================
===============================================================================
Session 36 Traffic Statistics
===============================================================================
Forward Reverse
-------------------------------------------------------------------------------
Passed
Packets 15 15
Octets 1260 1260
Dropped Packets
Drop Action 0
Prohibited IP Option 0 0
Max Pkts Exceeded 5 0
Max ICMP Errors Exceeded 0 0
Application Error 0 0
===============================================================================
Use <show mda aggregate-statistics> to display the firewall queue statistics.
*A:SAR-H-3# show mda aggregate-statistics
===============================================================================
Aggregated Statistics
===============================================================================
...output omitted...
Firewall Queue Statistics
-------------------------------------------------------------------------------
Network Queue 1 Best-effort Packets Bytes
In Profile forwarded : 0 0
In Profile dropped : 0 0
Out Profile forwarded : 29 3998
Out Profile dropped : 0 0
Network Queue 2 Expedited Packets Bytes
In Profile forwarded : 0 0
In Profile dropped : 0 0
Out Profile forwarded : 0 0
Out Profile dropped : 0 0
Access Queue 1 Best-effort Packets Bytes
Hi Priority forwarded : 0 0
Hi Priority dropped : 0 0
Low Priority forwarded : 0 0
Low Priority dropped : 0 0
Access Queue 2 Expedited Packets Bytes
Hi Priority forwarded : 0 0
Hi Priority dropped : 0 0
Low Priority forwarded : 0 0
Low Priority dropped : 0 0
===============================================================================
Use <show security log <log-id>> to display the log.
*A:SAR-H-3# show security log 10
7 09/25/2015 11:38:25 SECURITY:Packet vprn5 IF:to-eNodeB
" Outbound : 1 (Rule:10)
Inbound : <None>
Session : 4-FWD
Report : SessionBegin
IP header :
ver:4 hlen:20 tos:0x00 len:84 hxsum:0xdad5
id:0x1e80 frag:000 (offset:0)
192.168.1.1->192.168.0.2 proto:ICMP
ICMP header:
type:8 code:0 xsum:0x42a7 (echo-request)"
8 09/25/2015 11:39:24 SECURITY:Audit SESSION:4
" Outbound : 1
Inbound : <None>
Session : 4-FWD
Report : SessionEnd (TIMER-EXPIRED)
"
Setup 2: Firewall in IES context
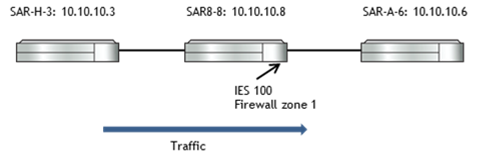
Firewall Configuration on SAR-8-8:
A:SAR8-8>config>security# info
----------------------------------------------
logging
log-id 10 create
destination memory 1024
exit
exit
policy 1 create
entry 10 create
match protocol icmp
src-ip 10.10.10.3
exit
limit
exit
action forward
exit
exit
commit
----------------------------------------------
A:SAR8-8>config>service>ies# info
----------------------------------------------
interface "to-SAR-A-6" create
address 172.10.10.1/30
sap 1/1/6 create
exit
exit
zone 1 create
interface "to-SAR-A-6"
exit
nat
exit
policy "1"
inbound
limit
exit
exit
outbound
limit
exit
exit
log "10"
commit
exit
no shutdown
----------------------------------------------
Verification:
PING SAR-A-6’s system IP in SAR-H-3:
A:SAR-H-3# ping 10.10.10.6 count 20
PING 10.10.10.6 56 data bytes
64 bytes from 10.10.10.6: icmp_seq=1 ttl=63 time=77.8ms.
64 bytes from 10.10.10.6: icmp_seq=2 ttl=63 time=0.902ms.
64 bytes from 10.10.10.6: icmp_seq=3 ttl=63 time=0.906ms.
... output omitted ...
Use <show security zone <zone-id> session> to display the zone session information.
A:SAR8-8#show security zone 1 session
===============================================================================
Security Zone
===============================================================================
Zone Id : 1 State : Committed
Name : (Not Specified)
===============================================================================
===============================================================================
Inbound Sessions
===============================================================================
Sess-Id Action From Source NAT Mapping
Proto ALG Rev Destination
-------------------------------------------------------------------------------
00000002 FWD <Base> 10.10.10.3
ICMP Y 10.10.10.6
-------------------------------------------------------------------------------
Num of Sessions: 1
===============================================================================
===============================================================================
Outbound Sessions
===============================================================================
Sess-Id Action To Source NAT Mapping
Proto ALG Rev Destination
-------------------------------------------------------------------------------
No Outbound Sessions
===============================================================================
Use <show security zone <zone-id> session <session-id> detail> to display the session details.
A:SAR8-8#show security zone 1 session 2 detail
===============================================================================
Security Zone
===============================================================================
Zone Id : 1 State : Committed
Name : (Not Specified)
===============================================================================
===============================================================================
Security Session Details
===============================================================================
Session Id : 2 Action : Forward
Created : 09/28/2015 10:12:52
Protocol : ICMP ALG : None
State : ICMP-ESTABLISHED
Source : Destination :
Zone : <BASE> Zone : 1
Ip-Address : 10.10.10.3 Ip-Address : 10.10.10.6
ICMP :
Type : 8 (echo-request)
Code : 0 (network-unreachable)
Id : 49156
Profile :
Bidirection*: Yes
CSM Inspect*: No
Timeouts :
ICMP-Requ*: strict 1 min
-------------------------------------------------------------------------------
Session Security Trace
-------------------------------------------------------------------------------
[INGRESS] Base:to-SAR-H-3
[ZONE-1] INBOUND-PLCY:1-10 Profile:1 Action:forward
======================================================================================