3. OAM and SAA
This chapter provides information about the Operations, Administration and Maintenance (OAM) and Service Assurance Agent (SAA) commands available in the CLI for troubleshooting services.
Topics in this chapter include:
3.1. OAM Overview
Delivery of services requires that a number of operations occur properly and at different levels in the service delivery model. For example, operations—such as the association of packets to a service, VC-labels to a service, and each service to a service tunnel—must be performed properly in the forwarding plane for the service to function properly. In order to verify that a service is operational, a set of in-band, packet-based OAM tools is provided, with the ability to test each of the individual packet operations.
For in-band testing, the OAM packets closely resemble customer packets in order to effectively test the customer's forwarding path, but they are distinguishable from customer packets so that they can be kept within the service provider's network and not get forwarded to the customer.
The suite of OAM diagnostics supplements the basic IP ping and traceroute operations with diagnostics specialized for the different levels in the service delivery model. In addition, there are diagnostics for MPLS LSPs, SDPs, and Services within a service.
This section describes the following topics:
3.1.1. ICMP and ICMPv6 Diagnostics
Internet Control Message Protocol (ICMP) is part of the IP suite as defined in RFC 792, Internet Control Message Protocol, for IPv4 and RFC 4443, Internet Control Message Protocol (ICMPv6) for the Internet Protocol Version 6 (IPv6) Specification.
ICMP and ICMPv6 send and receive control and error messages used to manage the behavior of the TCP/IP stack. ICMP and ICMPv6 provide:
- debugging tools and error reporting mechanisms to assist in troubleshooting an IP network
- the ability to send and receive error and control messages to far-end IP entities
3.1.1.1. Ping
Ping is used to determine if there is IP layer connectivity between the 7705 SAR and another node in the network.
The 7705 SAR supports redirection of SGT to egress data queues rather than the default control queue. To redirect ping to a data queue, the ping command includes the fc-queue option, which specifies the queue to be used for servicing the ping packets in the egress direction. All other SGT applications are redirected using the config>router>sgt-qos>application>fc-queue or config>service>vprn>sgt-qos>application>fc-queue command. For more information on SGT redirection, refer to the 7705 SAR Quality of Service Guide, “SGT Redirection”.
3.1.1.2. Traceroute
Traceroute is used to determine the path that an IP packet takes from the 7705 SAR to a specified router.
3.1.2. Two-Way Active Measurement Protocol
The Two-way active measurement protocol (TWAMP) provides a standards-based method to measure the round-trip performance (including the packet loss, delay, and jitter) of IP packets that are transmitted between two devices. TWAMP, which is described in RFC 5357, uses the methodology and architecture of the One-way active measurement protocol (OWAMP) to assess the two-way transmission of IP packets.
TWAMP offers advantages for performance monitoring at L3/IP layer because it provides functions that other performance monitoring methods, such as ICMP, lack:
- timestamping for delay and jitter measurements
- high-accuracy timestamping at TX and RX on 7705 SAR nodes for error-free results
- intelligent control plane
There are four logical entities in TWAMP:
- control client—initiates the TWAMP control session and negotiates the security protocols to be used and the tests to be performed with the server
- server—negotiates with the control client request to establish the control session
- session sender—transmits test packets to the session reflector
- session reflector—transmits a packet to the session sender in response to each packet it receives
The TWAMP control and data (test) protocol operate on separate planes, as shown in Figure 1. The TWAMP control protocol initiates test sessions and starts and stops the tests. The TWAMP test protocol exchanges test packets between TWAMP entities.
Figure 1: TWAMP Logical Entities (RFC 5357)
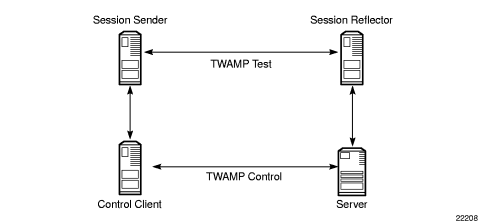
The control client and session sender are typically implemented in one physical device (also known as the client device) and the server and session reflector are typically implemented in a second physical device (also known as the server device), as shown in Figure 2.
Figure 2: Typical TWAMP Implementation

The control client and server establish a TCP connection and exchange TWAMP control messages over the connection. To start the test, the client communicates the test parameters to the server. If the server agrees to conduct the test, the test begins as soon as the client sends a start-sessions message. As part of a test, the session sender sends a stream of UDP-based test packets to the session reflector. The session reflector responds to each received packet with a UDP-based packet response. When the session sender receives the response packets from the session reflector, the information is used to calculate two-way delay, packet loss, and packet delay variation between the two devices.
The following ports are assigned for the TWAMP control protocol, as defined in RFC 5357:
- 862/tcp
- 862/udp
3.1.2.1. 7705 SAR Support for TWAMP Server
The 7705 SAR supports the TWAMP server and the session reflector functions, as shown in Figure 3.
Figure 3: 7705 SAR as TWAMP Server and Session Reflector
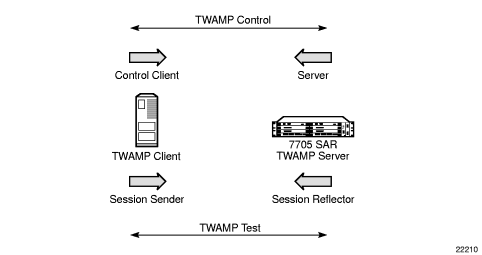
The 7705 SAR plays a passive role: the TWAMP control client initiates the control session with the 7705 SAR in order to negotiate the following:
- the tests to be executed
- the security protocol to be used
- the port to be used
The 7705 SAR responds, and when the negotiation is complete, the 7705 SAR performs the following:
- timestamps the TWAMP packets upon reception
- processes the TWAMP packets and generates a response
- timestamps the packets again before transmitting the response packets
TWAMP is supported on all IPv4 interfaces and on the base router of any interface address, including the system and loopback IP addresses. Any IP address can be used to terminate TWAMP control and test packets.
Datapath timestamping in both ingress and egress directions for TWAMP frames is supported on all datapath Ethernet ports on the following adapter cards, modules, and standalone nodes:
- adapter cards
- 2-port 10GigE (Ethernet) Adapter card
- 8-port Ethernet Adapter card, version 2 (high accuracy when using IEEE 1588v2 PTP time source)
- 6-port Ethernet 10Gbps Adapter card (high accuracy when using IEEE 1588v2 PTP time source)
- 8-port Gigabit Ethernet Adapter card (high accuracy when using IEEE 1588v2 PTP time source)
- 10-port 1GigE/1-port 10GigE X-Adapter card (high accuracy when using IEEE 1588v2 PTP time source)
- Packet Microwave Adapter card (high accuracy when using IEEE 1588v2 PTP time source)
- modules
- 2-port 10GigE (Ethernet) module
- 4-port SAR-H Fast Ethernet module
- 6-port SAR-M Ethernet module
- standalone nodes
- 7705 SAR-A (high accuracy when using IEEE 1588v2 PTP time source)
- 7705 SAR-Ax (high accuracy when using IEEE 1588v2 PTP time source)
- 7705 SAR-H (high accuracy when using IEEE 1588v2 PTP time source)
- 7705 SAR-Hc (high accuracy when using IEEE 1588v2 PTP time source)
- 7705 SAR-M (high accuracy when using IEEE 1588v2 PTP time source)
- 7705 SAR-W (high accuracy when using IEEE 1588v2 PTP time source)
- 7705 SAR-Wx (high accuracy when using IEEE 1588v2 PTP time source)
- 7705 SAR-X (high accuracy when using IEEE 1588v2 PTP time source)
| Note: A 7705 SAR node using GNSS or IEEE 1588v2 PTP for time of day/phase recovery can perform high-accuracy timestamping for TWAMP packets. Refer to the 7705 SAR Basic System Configuration Guide for information about node timing sources. |
CSM-based egress timestamping for TWAMP is supported on:
- all TDM cards
- 2-port OC3/STM1 Channelized Adapter card
- 4-port DS3/E3 Adapter card
- 4-port OC3/STM1 Clear Channel Adapter card
- 16-port T1/E1 ASAP Adapter card
- 32-port T1/E1 ASAP Adapter card
- Ethernet ports bound to a routed VPLS interface, where the frames are processed via the VPLS instance before reaching the IP interface
For information about how to configure the TWAMP server and the TWAMP command hierarchy, see the OAM commands for TWAMP.
The 7705 SAR supports a show>test-oam>twamp>server command that displays information about the TWAMP server configuration and statistics, and the clients associated with each server address prefix. See the Show Commands for more information. The 7705 SAR also supports a dump command that displays statistics for dropped connections, dropped connection states, rejected sessions, and dropped test packets. See Dump Test-OAM Commands for more information.
3.1.2.1.1. Interactions with Ethernet Loopback
Ethernet line loopbacks, being the lower layer functionality, take precedence over TWAMP operations. If an Ethernet port loopback is enabled, all frames including TWAMP frames are looped back. TWAMP frames cannot be processed on the interface until the loopback is released.
3.1.2.1.2. Limitations
The following limitations apply:
- only the unauthenticated mode of TWAMP is supported. Authenticated and encrypted modes are excluded.
- TWAMP does not support redundant HA configurations. During a CSM activity switch, all TWAMP control sessions are dropped and all tests that are in progress are terminated.
3.1.2.2. Two-Way Active Measurement Protocol Light (TWAMP Light)
TWAMP Light is an optional model included in the TWAMP standard RFC 5357, A Two-Way Active Measurement Protocol (TWAMP). TWAMP Light uses the standard TWAMP packet format but provides a simpler approach to gathering ongoing IP delay and synthetic loss performance data for the base router and per-VPRN statistics. Full details are described in Appendix I of RFC 5357.
With TWAMP Light, the TWAMP client/server model is replaced with a session controller/responder model. The server, control-client and session-sender role is combined in one host called the controller, and the session-reflector role is in another host called the responder. In general terms, the session controller is the launch point for the TWAMP test packets and the responder reflects the packets.
TWAMP Light maintains the TWAMP test packet exchange but eliminates the TWAMP TCP control connection with local configurations; however, not all negotiated control parameters are replaced with local configurations. The DSCP value in an incoming TWAMP test packet is reflected back to the originator. The incoming TWAMP test packet is classified to a specific FC based on the ingress QoS policy and the dot1p in the reflected packet is determined by the FC to dot1p mapping in the egress QoS policy.
The reflector function is configured under the config>router>twamp-light command hierarchy for base router reflection, and under the config>service>vprn>twamp-light command hierarchy for per-VPRN reflection. The TWAMP Light reflector function is configured per context and must be activated before reflection can occur; the function is not enabled by default for any context. The reflector requires the operator to define the TWAMP Light UDP listening port that identifies the TWAMP Light protocol and to define the prefixes that the reflector will accept as valid sources for a TWAMP Light request.
If the source IP address in the TWAMP Light packet arriving on the responder does not match a configured IP address prefix, the packet is dropped. Multiple prefix entries may be configured per context on the responder. Configured prefixes can be modified without shutting down the reflector function. An inactivity timeout under the config>oam-test>twamp>twamp-light command hierarchy defines the amount of time the reflector will keep the individual reflector sessions active in the absence of test packets.
TWAMP uses a single packet to gather both delay and loss metrics. This means there is special consideration over those approaches that utilize a specific tool per metric type.
TWAMP Light is supported for deployments that use IPv4 or IPv6 addressing, which may each have their own hardware requirements. All IP addressing must be unicast. IPv6 addresses cannot be reserved or link local addresses. Multiple test sessions may be configured between the same source and destination IP endpoints. The 4-tuple lookup (source IP, destination IP, source UDP, destination UDP provides a unique index for each test point.
| Note: A 7705 SAR node using GNSS or IEEE 1588v2 PTP for time of day/phase recovery can perform high-accuracy timestamping for TWAMP Light packets. |
3.1.2.2.1. 7705 SAR Support for TWAMP Light Responder
TWAMP Light is supported on the same hardware as TWAMP. See 7705 SAR Support for TWAMP Server.
For information about how to configure the TWAMP Light reflector see the OAM commands for TWAMP Light.
3.1.2.2.2. Interactions with Ethernet Loopback
Ethernet line loopbacks, being the lower layer functionality, take precedence over TWAMP Light operations. If an Ethernet port loopback is enabled, all frames are looped back. Frames cannot be processed on the interface until the loopback is released.
3.1.2.2.3. Limitations
The following limitations apply:
- only the unauthenticated mode of TWAMP is supported
3.1.2.2.4. TWAMP Light Configuration Example
The following example shows a basic configuration using TWAMP Light to monitor two IP endpoints in a VPRN, including the default TWAMP Light values that were not overridden with configuration entries.
3.1.3. LSP Diagnostics
The 7705 SAR LSP diagnostics are implementations of LSP ping and LSP traceroute based on RFC 4379, Detecting Multi-Protocol Label Switched (MPLS) Data Plane Failures. LSP ping and LSP traceroute are modeled after the ICMP echo request/reply used by ping and traceroute to detect and localize faults in IP networks.
The downstream mapping TLV is used in LSP ping and LSP trace to allow the sender and responder nodes to exchange and validate interface and label stack information for each downstream hop of an LDP FEC or an RSVP LSP and at each hop in an LDP FEC path, RSVP LSP, or BGP-labeled IPv4 route. The 7705 SAR supports two downstream mapping TLVs: the original Downstream Mapping (DSMAP) TLV defined in RFC 4379 and the Downstream Detailed Mapping (DDMAP) TLV defined in RFC 6424.
This section describes the following topics:
3.1.3.1. LSP Ping
LSP ping, as described in RFC 4379, provides a mechanism to detect data plane failures in MPLS LSPs. For a given FEC, LSP ping verifies whether the packet reaches the egress label edge router (eLER).
A 7705 SAR node using GNSS or IEEE 1588v2 PTP for time of day/phase recovery can perform LSP ping tests with high-accuracy timestamping. Refer to the 7705 SAR Basic System Configuration Guide, “Node Timing”, for information about node timing sources.
3.1.3.2. LSP Traceroute
LSP traceroute sends a packet to each transit LSR along a communications path until the far-end router is reached. The path is traced one LSR at a time, where each LSR that receives a traceroute packet replies to the initiating 7705 SAR with a packet that identifies itself. Once the final LSR is identified, the initiating LSR has a list of all LSRs on the path. Like IP traceroute, LSP traceroute is a hop-by-hop operation (that is, LSR by LSR).
Use LSP traceroute to determine the exact litigation of LSP failures.
3.1.3.3. LSP Ping and LSP Traceroute for BGP Route Tunnels
LSP ping and LSP traceroute are supported on BGP route tunnels using existing LSP ping and traceroute commands with the bgp-label prefix option. The system uses the DSMAP TLV target FEC stack TLV for BGP-labeled IPv4 /32 prefix as defined in RFC 4379, Detecting Multi-Protocol Label Switched (MPLS) Data Plane Failures. Figure 4 shows the new TLV structure.
Figure 4: Target FEC Stack TLV for BGP-Labeled IPv4 Prefix

The following process is used when sending or responding to an LSP ping or LSP traceroute packet on BGP route tunnels.
- The next hop of a BGP-labeled route for a core IPv4 /32 prefix is always resolved to an LDP FEC or an RSVP-TE LSP. The transmitting node encapsulates the packet containing the echo request message with a label stack that consists of the LDP/RSVP-TE outer label and the BGP inner label.
- If the packet expires on an RSVP-TE or LDP LSR node that does not have context for the BGP-labeled IPv4 /32 prefix, the system must validate the outer label in the stack, and if the validation is successful, it must reply with return code 8 <Label switched at stack-depth <RSC>>.
- An LSR node that is the next hop for the BGP-labeled IPv4 /32 prefix, as well as the LER node that originated the BGP-labeled IPv4 prefix, have full context for the BGP IPv4 target FEC stack and can thus perform full validation of it.
| Note: The 7705 SAR supports only BGP-labeled IPv4 /32 prefixes in LSP ping and LSP trace. |
For more information on BGP route tunnels, refer to the 7705 SAR Routing Protocols Guide, “BGP Route Tunnels”.
3.1.3.3.1. TC Handling on BGP Route Tunnels
A 7705 SAR that process BGP 3107 labels always re-marks the TC bits. Ingress classification is based on the received TC/DSCP bits to FC. Egress re-marking is based on the QoS queue policy.
A 7705 SAR that does not process labels on a BGP route tunnel such as a 7705 SAR acting as an LSR, does not re-mark the TC bits.
3.1.3.3.2. BGP Route Tunnel Traceroute
Labeled-BGP route tunnels pose a challenge to traceroute capability because there are two labels used in the transport layer: an inner BGP label identifying the far-end node and the regular label identifying the next hop for that far end.
Traceroute and TTL monitoring on the 7705 SAR have been enhanced to be able to identify and report every PE, ABR, ASBR, and P node along the path of a Layer 2 or Layer 3 service built partially or wholly over labeled-BGP route tunnels.
Both the MPLS tunnel TTL and the labeled-BGP route tunnel TTL are monitored for TTL expiry, which causes an ICMP TTL expired message to be sourced. Depending on the role of the intermediate nodes along the path, monitoring both TTL values is the most comprehensive way to ensure proper TTL handling.
3.1.3.3.3. Traceroute TTL for Self-generated Traffic
Depending on how the network is built on elements in the topology, a node along the path might be operating based on the outer MPLS tunnel label or the inner BGP label. In order to ensure that all the nodes along the path are displayed correctly, the 7705 SAR sets the TTL of the outer MPLS transport tunnel and the inner labeled-BGP route tunnel to identical values. The next node is therefore identified and displayed correctly in a traceroute regardless of which label it is operating on.
For a self-generated traffic traceroute, both the MPLS and the labeled-BGP TTLs are set to 1 in order to identify the first node. At the next hop, both TTL values are incremented to 2. This pattern continues at each hop in the path.
3.1.3.4. Downstream Detailed Mapping (DDMAP) TLV
The DDMAP TLV, as defined in RFC 6424, provides users with the same features as the existing DSMAP TLV along with enhancements that allow LSP diagnostics to trace the details of LSP hierarchy. With the DDMAP TLV, all intermediate routers will appear in the LSP ping and traceroute lists, and intermediate nodes can append additional data with details about their relative functionality. The DDMAP TLV format is derived from the DSMAP TLV format with variable length and optional fields converted into sub-TLVs. Figure 5 shows the DDMAP TLV format.
Figure 5: DDMAP TLV
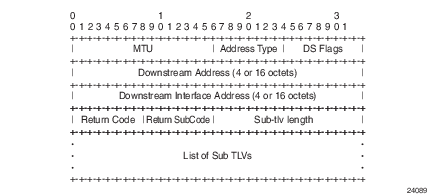
The following process is used when sending or responding to an LSP ping or LSP traceroute packet using the DSMAP or DDMAP TLV.
- When either the DSMAP TLV or the DDMAP TLV is received in an echo request message, the responder node includes the same type of TLV in the echo reply message with the proper downstream interface information and label stack information.
- If an echo request message without a DSMAP or DDMAP TLV expires at a node that is not the egress for the target FEC stack, the responder node always includes the DSMAP TLV in the echo reply message. This can occur in the following cases:
- The user issues an LSP trace from a sender node with a min-ttl value higher than 1 and a max-ttl value lower than the number of hops required to reach the egress of the target FEC stack. This is the sender node behavior when the global configuration or the per-test setting of the DSMAP/DDMAP is set to DSMAP.
- The user issues an LSP ping from a sender node with a TTL value lower than the number of hops required to reach the egress of the target FEC stack. This is the sender node behavior when the global configuration of the DSMAP/DDMAP is set to DSMAP.
- If the global configuration or the per-test setting of the DSMAP TLV is set to DDMAP, the sender node includes the DDMAP TLV with the downstream IP address field set to the all-routers multicast address as per Section 3.3 of RFC 4379. The responder node then bypasses the interface and label stack validation and replies with a DDMAP TLV with the correct downstream information for the target FEC stack.
- A sender node never includes the DSMAP or DDMAP TLV in an lsp-ping message.
The user can globally configure the downstream mapping TLV to be used for all LSP trace and LDP treetrace packets with the configure test-oam mpls-echo-request-downstream-map command. The configured global value becomes the default downstream mapping TLV for all newly created LSP trace and LDP treetrace tests. It has no effect on existing tests and can be overridden on a specific test by setting the downstream-map-tlv parameter in the lsp-trace or ldp-treetrace context.
3.1.3.4.1. Using The DDMAP TLV in LSP Stitching and LSP Hierarchy
The DDMAP TLV provides full validation for a BGP IPv4 label route tunneled over an RSVP LSP or an LDP FEC.
| Note: The 7705 SAR does not support LSP stitching. |
In order to properly check a target FEC that is stitched to another FEC (stitching FEC) of the same or a different type, or that is tunneled over another FEC (tunneling FEC), it is necessary for the responding nodes to provide details about the FEC manipulation to the sender node. The system collects this detailed information with the DDMAP TLV FEC stack change sub-TLV, shown in Figure 6. The field definitions match those of the DSMAP TLV and are described in RFC 4379.
Figure 6: FEC Stack Change Sub-TLV
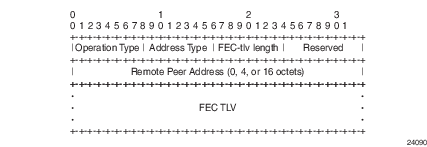
The operation type specifies the action associated with the FEC stack change. Table 2 defines the operation types for the FEC stack change sub-TLV.
Table 2: FEC Stack Change Sub-TLV Operation Types
Type # | Operation |
1 | Push |
2 | Pop |
When DDMAP TLV is configured on an LSP trace that does not undergo stitching or tunneling operation in the network, the procedures at the sender and responder nodes are the same as in the case of the existing DSMAP TLV.
When DDMAP TLV is configured on an LSP trace that does undergo stitching or tunneling operation in the network, there are changes to the target FEC stack validation procedures at the sender and responder nodes. The following procedure represent a superset of the rules described in Section 4 of RFC 6424 to allow greater scope of interoperability with other vendor implementations.
Responder Node Procedures:
- As a responder node, the 7705 SAR always inserts the global return code, 3 Replying router is an egress for the FEC at stack-depth <RSC> or the code, 14 See DDMAP TLV for Return Code and Return Subcode.
- When the responder node inserts a global return code of 3, it does not include a DDMAP TLV.
- When the responder node includes the DDMAP TLV, it inserts the global return code, 14 See DDMAP TLV for Return Code and Return Subcode. Additionally, the responder node will:
- on a success response, include a return code of 15 in the DDMAP TLV for each downstream hop that has a FEC stack change sub-TLV
- on a success response, include a return code, 8 Label switched at stackdepth <RSC> in the DDMAP TLV for each downstream hop if no FEC stack change sub-TLV is present
- on a failure response, include an appropriate error return code in the DDMAP TLV for each downstream hop
- A tunneling node indicates that it is pushing a FEC (the tunneling FEC) on top of the target FEC stack TLV by including a FEC stack change sub-TLV in the DDMAP TLV with a FEC operation type value of PUSH. It also includes a return code, 15 Label switched with FEC change. The downstream interface address and downstream IP address fields of the DDMAP TLV are populated for the pushed FEC. The remote peer address field in the FEC stack change sub-TLV is populated with the address of the control plane peer for the pushed FEC. The Label stack sub-TLV provides the full label stack over the downstream interface.
- A node that is stitching a FEC indicates that it is performing a POP operation for the stitched FEC followed by a PUSH operation for the stitching FEC and potentially one PUSH operation for the transport tunnel FEC. The echo reply message will include two or more FEC stack change sub-TLVs in the DDMAP TLV. It also includes a return code 15 Label switched with FEC change. The downstream interface address and downstream address fields of the DDMAP TLV are populated for the stitching FEC. The remote peer address field in the FEC stack change sub-TLV of type POP is populated with a null value (0.0.0.0). The remote peer address field in the FEC stack change sub-TLV of type PUSH is populated with the address of the control plane peer for the tunneling FEC. The Label stack sub-TLV provides the full label stack over the downstream interface.
- If the responder node is the egress for one or more FECs in the target FEC Stack, then it must reply with no DDMAP TLV and with a return code 3 Replying router is an egress for the FEC at stack-depth <RSC>. RSC must be set to the depth of the topmost FEC. This operation is iterative.The receipt of the echo reply message the sender node will pop the topmost FEC from the target stack FEC TLV and resend the echo request message with the same TTL value as explained in step 5. The responder node performs the same operation until all FECs are popped or until the topmost FEC in the target FEC stack TLV matches the tunneled or stitched FEC. In the latter case, processing of the target FEC stack TLV follows again steps 1 or 2.
Sender Node Procedures:
- If the echo reply message contains the return code 14 See DDMAP TLV for Return Code and Return Subcode and the DDMAP TLV has a return code 15 Label switched with FEC change, the sender node adjusts the target FEC Stack TLV in the echo request message for the next value of the TTL to reflect the operation on the current target FEC stack as indicated in the FEC stack change sub-TLV received in the DDMAP TLV of the last echo reply message. This results in one FEC being popped at most and one or more FECs being pushed as indicated.
- If the echo reply message contains the return code 3 Replying router is an egress for the FEC at stack-depth <RSC>, then:
- If the value for the label stack depth specified in the Return Sub-Code (RSC) field is the same as the depth of current target FEC Stack TLV, then the sender node considers the trace operation complete and terminates it. A 7705 SAR responder node will cause this case to occur as per Step 6 of the Responder Node Procedures.
- If the value for the label stack depth specified in the Return Sub-Code (RSC) field is different from the depth of the current target FEC Stack TLV, the sender node must continue the LSP trace with the same TTL value after adjusting the target FEC stack TLV by removing the top FEC.This step continues iteratively until the value for the label stack depth specified in the Return Sub Code (RSC) field is the same as the depth of current target FEC Stack TLV, at which point step a is performed. A 7705 SAR responder node causes this case to occur as per Step 6 of the responder node procedures.
- If a DDMAP TLV with or without a FEC stack change sub-TLV is included, then the sender node ignores it and processing is performed as per steps (a) or (b) above. A 7705 SAR responder node does not cause this case to occur but a third party implementation may.
- As a sender node, the 7705 SAR can accept an echo-reply message with the global return code of either 14 (with DDMAP TLV return code of 15 or 8), or 15 and process the FEC stack change TLV as per Step 1 of the Sender Node Procedures.
- If an LSP ping is performed directly to the egress LER of the stitched FEC, there is no DDMAP TLV included in the echo request message and the responder node, which is the egress node, still replies with return code 4 Replying router has no mapping for the FEC at stack- depth <RSC>. This case cannot be resolved with this feature.
Figure 7 and the following LSP trace examples illustrate how the 7705 SAR provides validation for a BGP IPv4 label route tunneled over an RSVP LSP or an LDP FEC.
Figure 7: BGP 3107 Tunnel Through LDP FEC

LSP trace launched from ALU-A (AS 100) to ALU-D (AS 300) with the DSMAP option:
LSP trace launched from ALU-A (AS 100) to ALU-D (AS 300) with the DDMAP option:
LSP trace launched from ALU-B (AS 300) to ALU-F (AS 100) with the DSMAP option:
LSP trace launched from ALU-B (AS 300) to ALU-F (AS 100) with the DDMAP option:
3.1.4. SDP Diagnostics
The 7705 SAR SDP diagnostics include:
3.1.4.1. SDP Ping
SDP ping performs in-band unidirectional or round-trip connectivity tests on SDPs. The SDP ping OAM packets are sent in-band, in the tunnel encapsulation, so it will follow the same path as traffic within the service. The SDP ping response can be received out-of-band in the control plane, or in-band using the data plane for a round-trip test.
For a unidirectional test, SDP ping tests:
- the egress SDP ID encapsulation
- the ability to reach the far-end IP address of the SDP ID within the SDP encapsulation
- the path MTU to the far-end IP address over the SDP ID
- the forwarding class mapping between the near-end SDP ID encapsulation and the far-end tunnel termination
For a round-trip test, SDP ping uses a local egress SDP ID and an expected remote SDP ID. Since SDPs are unidirectional tunnels, the remote SDP ID must be specified and must exist as a configured SDP ID on the far-end 7705 SAR.
SDP round-trip testing is an extension of SDP connectivity testing with the additional ability to test:
- the remote SDP ID encapsulation
- the potential service round-trip time
- the round-trip path MTU
- the round-trip forwarding class mapping
3.1.4.2. SDP MTU Path Discovery
In a large network, network devices can support a variety of packet sizes that are transmitted across their interfaces. The largest packet (including headers) can be as large as the Maximum Transmission Unit (MTU). An MTU specifies the largest packet size, measured in octets, that can be transmitted through a network entity. It is important to understand the MTU of the entire path (end-to-end) when provisioning services, especially for VLL services where the service must support the ability to transmit the extra large customer packets.
The Path MTU Discovery tool is a powerful tool that enables service providers to get the exact MTU supported between the service ingress and service termination points, accurate to 1 byte.
| Note: The sdp-mtu command probes the far-end port using the configured MTU of the near-end port, not the configured MTU of the far-end port. For example, a far-end port that is physically capable of receiving jumbo frames would respond to sdp-mtu probes up to the jumbo frame size, regardless of the configured MTU of the far-end port. This assumes that the intermediate transport network can switch frames of this size. |
3.1.5. Service Diagnostics
The Nokia Service ping feature provides end-to-end connectivity testing for an individual service. Service ping operates at a higher level than the SDP diagnostics in that it verifies an individual service and not the collection of services carried within an SDP.
3.1.5.1. Service Ping
Service (SVC) ping is initiated from a 7705 SAR router to verify round-trip connectivity and delay to the far end of the service. Service ping applies to GRE, IP, and MPLS tunnels and tests the following from edge-to-edge:
- tunnel connectivity
- VC label mapping verification
- service existence
- service provisioned parameter verification
- round-trip path verification
- service dynamic configuration verification

Note: By default, service ping uses GRE encapsulation.
3.1.6. VLL Diagnostics
This section describes VCCV (Virtual Circuit Connectivity Verification) ping and VCCV trace, the VLL diagnostic capabilities for the 7705 SAR.
3.1.6.1. VCCV Ping
VCCV ping is used to check the connectivity (in-band) of a VLL. It checks that the destination (target) PE is the egress point for the Layer 2 FEC. It provides a cross-check between the data plane and the control plane. It is in-band, meaning that the VCCV ping message is sent using the same encapsulation and along the same path as user packets in that VLL. This is equivalent to the LSP ping for a VLL service. VCCV ping reuses an LSP ping message format and can be used to test a VLL configured over an MPLS, GRE, or IP SDP.
A 7705 SAR node using GNSS or IEEE 1588v2 PTP for time of day/phase recovery can perform VCCV ping tests with high-accuracy timestamping. Refer to the 7705 SAR Basic System Configuration Guide, “Node Timing”, for information about node timing sources.
3.1.6.1.1. VCCV Ping Application
VCCV creates an IP control channel within the pseudowire between PE1 and PE2 (see Figure 8). PE2 should be able to distinguish, on the receive side, VCCV control messages from user packets on that VLL.
Figure 8: VCCV Ping Application
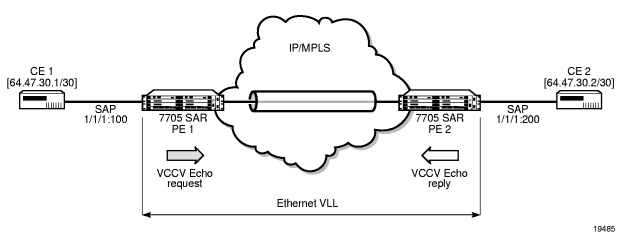
VCCV-based pseudowire (PW) tests are only supported on dynamically signaled PWs (not on statically signaled PWs).
There are three methods of encapsulating a VCCV message in a VLL, which translates into three types of control channels, as follows:
- Type 1 — in-band VCCV (special control word)Type 1 uses the OAM control word, which is shown in Figure 9.
Figure 9: OAM Control Word Format
 In Figure 9, the first nibble is set to 0x1. The Format ID and the Reserved fields are set to 0 and the Channel Type is the code point associated with the VCCV IP control channel, as specified in the PWE3 IANA registry [RFC 4446]. The channel type value of 0x21 indicates that the Associated Channel carries an IPv4 packet.The use of the OAM control word assumes that the draft-martini control word is also used for the user packets. This means that if the control word is optional for a VLL and is not configured, the 7705 SAR PE node will only advertise the router alert label as the CC capability in the Label Mapping message.This method is supported by the 7705 SAR.
In Figure 9, the first nibble is set to 0x1. The Format ID and the Reserved fields are set to 0 and the Channel Type is the code point associated with the VCCV IP control channel, as specified in the PWE3 IANA registry [RFC 4446]. The channel type value of 0x21 indicates that the Associated Channel carries an IPv4 packet.The use of the OAM control word assumes that the draft-martini control word is also used for the user packets. This means that if the control word is optional for a VLL and is not configured, the 7705 SAR PE node will only advertise the router alert label as the CC capability in the Label Mapping message.This method is supported by the 7705 SAR. - Type 2 — out-of-band VCCV (router alert above the service label)The 7705 SAR uses the router alert label immediately above the VC label to identify the VCCV ping message. This method has a drawback in that if ECMP is applied to the outer LSP label, such as the transport label, the VCCV message will not follow the same path as the user packets. This effectively means it will not troubleshoot the appropriate path.This method is supported by the 7705 SAR when a 7750 SR node acts as an LSR in the core of the network. If a 7705 SAR acts as an LSR in the core of the network, the VCCV type 2 message will instead follow the data path.
- Type 3 — TTL expiry VCCV (service label TTL = 1 and special control word)This method is not supported by the 7705 SAR.
When sending the label mapping message for the VLL, PE1 and PE2 must indicate which of the above OAM packet encapsulation methods (that is, which control channel type) they support. This is accomplished by including an optional VCCV TLV in the PW FEC interface parameter field. The format of the VCCV TLV is shown in Figure 10.
The absence of the optional VCCV TLV in the Interface parameters field of the pseudowire FEC indicates that the PE has no VCCV capability.
Figure 10: VCCV TLV
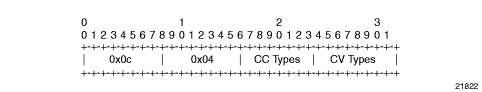
In Figure 10, the Control Channel (CC) Type field is a bit mask used to indicate if the PE supports none, one, or many control channel types:
- 0x00 — none of the following VCCV control channel types (Type 1, Type 2, or Type 3) are supported
- 0x01 — (Type 1, in-band) PWE3 OAM control word (see Figure 9)
- 0x02 — (Type 2, out-of-band) MPLS router alert label
- 0x04 — (Type 3, not supported on the 7705 SAR) MPLS inner label TTL = 1
If both PE nodes support more than one of the CC types, then a 7705 SAR PE will make use of the CC type with the lowest type value. For instance, OAM control word (0x01) will be used in preference to the MPLS router alert label (0x02).
The Connectivity Verification (CV) Type field is a bit mask used to indicate the specific type of VCCV packets to be sent over the VCCV control channel. The possible values supported on the 7705 SAR are:
- 0x00 — none of the following VCCV packet types are supported
- 0x02 — LSP pingThis value (0x02) is used in the VCCV ping application and applies to a VLL over an MPLS, GRE, or IP SDP.
A VCCV ping is an LSP echo request message as defined in RFC 4379. It contains a Layer 2 FEC stack TLV in which it must include the sub-TLV type 10 FEC 128 pseudowire. It also contains a field that indicates to the destination PE which reply mode to use:
- do not replyThis mode is supported by the 7705 SAR.
- reply by an IPv4 UDP packetThis mode is supported by the 7705 SAR.
- reply via an IPv4 UDP packet with router alertThis mode is not supported by the 7705 SAR.

Note: Do not confuse this mode, which sets the router alert bit in the IP header, with the CC type that makes use of the router alert label.
- reply by application-level control channelThis mode sends the reply message in-band over the pseudowire from PE2 to PE1. PE2 will encapsulate the echo reply message using the CC type negotiated with PE1.This mode is supported by the 7705 SAR.
The VCCV ping reply has the same format as an LSP echo reply message as defined in RFC 4379. The message is sent via the reply mode requested by PE1. The return codes supported are the same as those currently supported in the 7705 SAR LSP ping capability.
The VCCV ping feature is in addition to the service ping OAM feature that can be used to test a service between 7705 SAR nodes. The VCCV ping feature can test connectivity of a VLL with any third-party node that is compliant with RFC 5085.
3.1.6.1.2. VCCV Ping in a Multi-Segment Pseudowire
Figure 11 displays an example of an application of VCCV ping over a multi-segment pseudowire (MS-PW). Pseudowire switching provides the user with the ability to create a VLL service by cross-connecting two spoke SDPs.
Figure 11: VCCV Ping Over a Multi-Segment Pseudowire
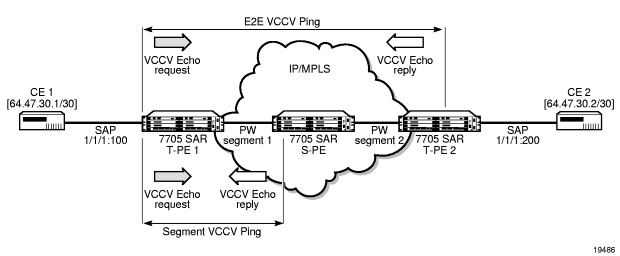
In the network, a Termination PE (T-PE) is where the pseudowire originates and terminates. The Switching PE (S-PE) is the node that performs pseudowire switching by cross-connecting two spoke SDPs.
VCCV ping on the 7705 SAR is capable of performing VCCV ping to a destination PE. A VLL FEC ping is a message sent by T-PE1 to test the FEC at T-PE2. The operation at T-PE1 and T-PE2 is the same as in the case of a single-segment pseudowire. The 7705 SAR pseudowire switching node, S-PE1, pops the outer label, swaps the inner (VC) label, decrements the TTL of the VC label, and pushes a new outer label. The 7705 SAR S-PE1 node does not process the VCCV OAM control word unless the VC label TTL expires. If the VC label TTL expires, the message is sent to the CSM for further validation and processing. This is the method described in draft-hart-pwe3-segmented-pw-vccv.
The originator of the VCCV ping message does not need to be a T-PE node; it can be an S-PE node. The destination of the VCCV ping message can also be an S-PE node. When an S-PE node receives a VCCV ping echo request destined for itself, it sends an IP-routed reply. VCCV trace can trace the entire path of a pseudowire with a single command issued at the T-PE. This is equivalent to LSP trace and is an iterative process, where T-PE1 sends successive VCCV ping messages while incrementing the TTL value, starting from TTL=1. The procedure for each iteration is the same. Each node in which the VC label TTL expires checks the FEC and replies with the FEC to the downstream S-PE or T-PE node. The process is terminated when the reply is sent from the T-PE2 node or when a timeout occurs.
3.1.6.1.3. Automated VCCV Trace Capability for Multi-Segment Pseudowire
Although tracing of the MS-PW path is possible using the methods explained in the VCCV Ping section, these require multiple manual iterations and that require the FEC of the last pseudowire segment to the target T-PE/S-PE already be known at the node originating the echo request message for each iteration. This mode of operation is referred to as a “ping” mode.
The automated VCCV trace can trace the entire path of a pseudowire with a single command issued at the T-PE or at an S-PE. This is equivalent to LSP trace and is an iterative process by which the ingress T-PE or T-PE sends successive VCCV ping messages with incrementing TTL values, starting from TTL=1.
The method is described in draft-hart-pwe3-segmented-pw-vccv, VCCV Extensions for Segmented Pseudo-Wire, and is pending acceptance by the PWE3 working group. In each iteration, the source T-PE or S-PE builds the MPLS echo request message in a way similar to VCCV Ping. The first message with TTL=1 will have the next-hop S-PE T-LDP session source address in the Remote PE Address field in the pseudowire FEC TLV. Each S-PE that terminates and processes the message will include the FEC 128 TLV corresponding to the pseudowire segment to its downstream node, in the MPLS echo reply message. The inclusion of the FEC TLV in the echo reply message is allowed according to RFC 4379, Detecting Multi-Protocol Label Switched (MPLS) Data Plane Failures.
The source T-PE or S-PE then sends the next echo reply message with TTL=2 to test the next-next hop for the MS-PW. It copies the FEC TLV it received in the echo reply message into the new echo request message. The process is terminated when the reply is sent from the egress T-PE node or when a timeout occurs. If specified, the max-ttl parameter in the vccv-trace command will stop on SPE before reaching T-PE.
The results of VCCV trace can be displayed for a fewer number of pseudowire segments of the end-to-end MS-PW path. In this case, the min-ttl and max-ttl parameters are configured accordingly. However, the T-PE/S-PE node will still probe all hops up to the min-ttl value in order to correctly build the FEC of the desired subset of segments.
This method does not require the use of the downstream mapping TLV in the echo request and echo reply messages.
3.1.6.1.4. VCCV for Static Pseudowire Segments
MS-PW is supported with a mix of static and signaled pseudowire segments. However, VCCV ping and VCCV trace are not allowed if any segment of the MS-PW is static. Users cannot test a static segment or contiguous signaled segments of the MS-PW. VCCV ping and VCCV trace are not supported in static-to-dynamic configurations.
3.1.6.1.5. VCCV for MS-PW and Pseudowire Redundancy
VCCV is supported on S-PE nodes configured for MS-PW and PW redundancy. In this case, S-PE terminates the in-band or out-of-band (IP-routed) VCCV ping (echo reply) and can generate VCCV ping (echo request) toward the dynamic section of the PW segment.
To configure an S-PE for MS-PW and pseudowire redundancy, an explicit endpoint is required to configure the service. Only one explicit endpoint is supported. The first PW segment must be configured with a static inner label under an implicit endpoint. The second PW segment can be created as either a redundant or non-redundant PW using the explicit endpoint.
| Note: A VLL service is in MS-PW and PW redundancy mode as long as there is one PW segment with an explicit endpoint configured. |
On S-PE nodes configured for MS-PW and PW redundancy, each segment of the PW can be configured with its own independent control word. The control word of the dynamic segment does not have to match the control word of the static segment for traffic to flow. The control word is automatically inserted or removed from the packets as they are switched from one segment to the other based on the control word configuration for each segment.
From an OAM diagnostic perspective, only Type-1 VCCV is supported for the dynamic MS-PW segment, which means that the PW segment must be configured with the control word option. In this mode, the ability to support VCCVs is signaled through the label message and the optional VCCV TLV toward the dynamic segment on the S-PE. The S-PE terminates all VCCV packets arriving on the dynamic segment, then extracts them towards the CSM.
3.1.6.1.6. Detailed VCCV Trace Operation
In Figure 11, a trace can be performed on the MS-PW originating from T-PE1 by a single operational command. The following process occurs:
- T-PE 1 sends a VCCV echo request with TTL set to 1 and a FEC 128 containing the pseudowire information of the first segment (pseudowire1 between T-PE 1 and S-PE) to S-PE for validation.
- S-PE validates the echo request with the FEC 128. Since it is a switching point between the first and second segment, it builds an echo reply with a return code of 8 and includes the FEC 128 of the second segment (pseudowire2 between S-PE and T-PE 2) and sends the echo reply back to T-PE 1.
- T-PE 1 builds a second VCCV echo request based on the FEC 128 in the echo reply from the S-PE. It increments the TTL and sends the next echo request out to T-PE 2. The VCCV echo request packet is switched at the S-PE datapath and forwarded to the next downstream segment without any involvement from the control plane.
- T-PE 2 receives and validates the echo request with the FEC 128 of the pseudowire2 from TPE 1. Since T-PE 2 is the destination node or the egress node of the MS-PW, it replies to T-PE1 with an echo reply with a return code of 3 (egress router) and no FEC 128 is included.
- T-PE 1 receives the echo reply from T-PE 2. T-PE 1 is made aware that T-PE 2 is the destination of the MS-PW because the echo reply does not contain the FEC 128 and because its return code is 3. The trace process is completed.
3.1.6.2. VCCV Trace
VCCV trace is similar to LSP trace. VCCV trace is used to trace the entire path of a pseudowire (PW) with a single command.
VCCV trace is useful in multi-segment PW (MS-PW) applications where a single PW traverses one or more switched PEs (S-PEs). VCCV trace is an iterative process by which the initiating terminating PE (T-PE) sends successive VCCV ping messages, each message having an incrementing TTL value, starting from TTL=1. The procedure for each iteration is the same as that for VCCV-ping, where each node in which the VC label TTL expires will check the FEC and reply with the FEC to the downstream S-PE or far-end T-PE. The process is terminated when the reply is from the far-end T-PE or when a timeout occurs.
The results of a VCCV trace can be displayed for a fewer number of pseudowire segments of the end-to-end MS-PW path. In this case, the min-ttl and max-ttl parameters should be configured accordingly. However, the T-PE or S-PE will still probe all hops up to the min-ttl value in order to correctly build the FEC of the desired subset of segments.
3.1.7. ITU-T Y.1564 Diagnostics
The 7705 SAR supports the ITU-T Y.1564 feature for throughput and bandwidth testing of Ethernet point-to-point virtual circuits. ITU-T Y.1564 includes, but also improves and standardizes, the RFC 2544 testing process.
ITU-T Y.1564 is supported on second-generation Ethernet ports in access mode in conjunction with 16-priority scheduling, on the following:
- 7705 SAR-A
- 7705 SAR-Ax
- 7705 SAR-H (not supported on the 4-port SAR-H Fast Ethernet module)
- 7705 SAR-Hc
- 7705 SAR-M
- 7705 SAR-W
- 7705 SAR-Wx
- 8-port Gigabit Ethernet Adapter card
- 10-port 1GigE X-Adapter card (in 10-port 1GigE mode)
- Packet Microwave Adapter card
ITU-T Y.1564 is supported on third-generation Ethernet ports in access mode in conjunction with 4-priority scheduling, on the following:
- 7705 SAR-X
- 6-port Ethernet 10Gbps Adapter card
For information on card and platform generations, refer to the 7705 SAR Interface Configuration Guide, “Evolution of Ethernet Adapter Cards, Modules, and Platforms”.
In a traditional hub and spoke network model, traffic is terminated on edge routers and aggregation hubs, which also perform bandwidth and throughput tests. In a flat, seamless, MPLS network, edge routers and aggregation hubs provide only forwarding and switching and cannot be used for service testing as they do not terminate traffic. ITU-T Y.1564 is crucial in these types of networks because it provides the 7705 SAR edge nodes with the ability to run a complete validation of Ethernet SLAs. The 7705 SAR generates RFC 2544 test frames, up to the desired rate, and sends them through the SAP of the service to test its performance. The far-end nodes must also offer per-service loopback capabilities, with the epipe>sap>loopback command, to return the traffic to the source node for test analysis and reporting.
Figure 12 shows a network with service endpoints where throughput tests are required.
Figure 12: ITU-T Y.1564 End-to-End Throughput Test
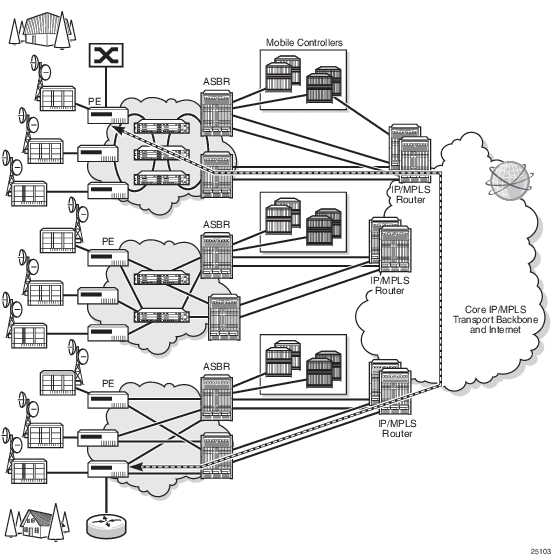
During an ITU-T Y.1564 test, marker frames are used to measure delay and jitter. Packet loss is reported directly by counting transmitted and received frames. Delay, jitter, and loss support two profile states: conforming traffic (configured as in-profile) and non-conforming traffic (configured as out-of-profile).
The 7705 SAR relies on the SAP ingress and SAP egress QoS profile queuing points for generated test traffic bandwidth. The assigned CIR and PIR dictate the potential test frame coloring when a Y.1564 test is run with color-aware enabled. The following colors are assigned to packets:
- green — traffic is equivalent to the CIR
- yellow — traffic received, up to the SAP PIR provisioned value
- red — traffic exceeding the PIR provisioned value
Figure 13 shows all of the queuing and policing points, in addition to the SAP ingress QoS profile, that can have an effect on the throughput test results. Each of these queuing points can contribute to traffic policing or shaping, which can impact delay, jitter, and loss measurements.
Figure 13: Queuing and Policing Points That Impact Throughput
A | Test head access/SAP ingress QoS profile | H | Far-end/responder access/SAP ingress QoS profile |
B | Test head access ingress fabric shaper | I | Far-end/responder access ingress fabric shaper |
C | Test head network egress QoS profile | J | Far-end/responder network egress QoS profile |
D | Any QoS enforcement via intermediate LSR nodes | K | Any QoS enforcement via intermediate LSR nodes |
E | Far-end/responder network ingress QoS profile | L | Test head network ingress QoS profile |
F | Far-end/responder network ingress fabric shaper | M | Test head network ingress fabric shaper |
G | Far-end/responder access/SAP egress QOS profile | N | Test head access/SAP egress QoS profile |
3.1.7.1. ITU-T Y.1564 Functionality
The 7705 SAR supports the test heads, as defined in RFC 2544, for ITU-T Y.1564. Test heads allow users to configure a set of trusted procedures to use during testing.
An ITU-T Y.1564 test head cannot survive activity switches (on platforms supporting HA), or any maintenance operation at the port, SAP, service level. The user must restart the test from the newly active CSM. If an activity switch occurs during an active test, all statistics and measurement data are lost.
An Ethernet SAP loopback can survive a CSM activity switch if it is enabled with the persistent keyword. Otherwise, the loopback is also reset during an activity switch. Ethernet SAP loopbacks are supported on LAG and MC-LAG ports on second-generation and third-generation Ethernet cards.
ITU-T Y.1564 test heads rely on delay and delay variation when calculating jitter. For more details, refer to RFC 3550, section A.8.
Users can configure the following frame type using the frame-payload command: Layer 2 payload, IPv4 payload, and IP/TCP/UDP payload. The test head uses the configured values for the IP header fields and TCP header fields based on the payload type configured.
The test head implementation on the 7705 SAR allows users to run tests with up to four parallel flows by specifying up to four frame payload IDs in the oam>testhead command. This allows users to test a service with IMIX-type traffic patterns.
3.1.7.2. ITU-T Y.1564 Protocol Interaction
CFM OAM must be explicitly disabled in order for an ITU-T Y.1564 test or Ethernet SAP loopback to be operational. You can enable a Y.1564 test head or Ethernet SAP loopback, or enable CFM OAM, but not both simultaneously (see Table 3).
Table 3: ITU-T Y.1564 Protocol Interaction
Feature | Y.1564 Test Head | Ethernet SAP Loopback | ||
Line | Internal | Line | Internal | |
All Layer 1 peering functionality (EFM (excluding tunneling), LLDP, SSM, EAP, and down-when-looped) | Maintained | — | Maintained | — |
EFM tunneling | Dropped | — | Dropped | — |
802.1ag Y.1731 CFM | — | Must be explicitly disabled | — | Must be explicitly disabled |
BFD | — | — | — | — |
3.1.8. VPLS MAC Diagnostics
Although the LSP ping, SDP ping, and service ping tools enable transport tunnel testing and verify that the correct transport tunnel is used, they do not provide the means to test the learning and forwarding functions on a per-VPLS-service basis.
It is possible that even though tunnels are operational and correctly bound to a service, an incorrect Forwarding Information Base (FIB) table for a service could cause connectivity issues in the service and not be detected by the ping tools. The 7705 SAR provides VPLS OAM functionality to specifically test all the critical functions on a per-service basis. These tools are based primarily on the IETF document draft-stokes-vkompella-ppvpn-hvpls-oam-xx.txt, Testing Hierarchical Virtual Private LAN Services.
The VPLS OAM tools are:
- MAC Ping — an end-to-end test to identify the egress customer-facing port where a customer MAC was learned. MAC ping can also be used with a broadcast MAC address to identify all egress points of a service for the specified broadcast MAC.
- MAC Trace — the ability to trace a specified MAC address hop-by-hop until the last node in the service domain. An SAA test with MAC trace is considered a successful OAM and SAA test when there is a reply from a far-end node indicating the destination MAC address on an egress SAP or the CSM.
- CPE Ping — the ability to check network connectivity to the specified client device within the VPLS. CPE ping will return the MAC address of the client, as well as the SAP and PE from which it was learned.
- MAC Populate — allows specified MAC addresses to be injected in the VPLS service domain. This triggers learning of the injected MAC address by all participating nodes in the service. This tool is generally followed by MAC ping or MAC trace to verify if correct learning occurred.
- MAC Purge — allows MAC addresses to be flushed from all nodes in a service domain
3.1.8.1. MAC Ping
For a MAC ping test, the destination MAC address (unicast or multicast) to be tested must be specified. A MAC ping packet can be sent through the control plane or the data plane. When sent by the control plane, the ping packet goes directly to the destination IP in a UDP/IP OAM packet. When it is sent by the data plane, the ping packet goes out with the data plane format.
In the control plane, a MAC ping is forwarded along the flooding domain if no MAC address bindings exist. If MAC address bindings exist, then the packet is forwarded along those paths (if they are active). Finally, a response is generated only when there is an egress SAP binding to that MAC address. A control plane request is responded to via a control reply only.
In the data plane, a MAC ping is sent with a VC label TTL of 255. This packet traverses each hop using forwarding plane information for next hop, VC label, and so on. The VC label is swapped at each service-aware hop, and the VC TTL is decremented. If the VC TTL is decremented to 0, the packet is passed up to the management plane for processing. If the packet reaches an egress node, and would be forwarded out a customer-facing port, it is identified by the OAM label below the VC label and passed to the management plane.
MAC pings are flooded when they are unknown at an intermediate node. They are responded to only by the egress nodes that have mappings for that MAC address.
A 7705 SAR node using GNSS or IEEE 1588v2 PTP for time of day/phase recovery can perform MAC ping tests with high-accuracy timestamping. Refer to the 7705 SAR Basic System Configuration Guide, “Node Timing”, for information about node timing sources.
3.1.8.2. MAC Trace
A MAC trace operates like an LSP trace with variations. Operations in a MAC trace are triggered when the VC TTL is decremented to 0.
Like a MAC ping, a MAC trace can be sent either by the control plane or the data plane.
When a MAC trace request is sent by the control plane, the destination IP address is determined from the control plane mapping for the destination MAC. If the destination MAC is known to be at a specific remote site, then the far-end IP address of that SDP is used. If the destination MAC is not known, then the packet is sent as a unicast transmission to all SDPs in the service with the appropriate squelching.
A control plane MAC traceroute request is sent via UDP/IP. The destination UDP port is the LSP ping port. The source UDP port is assigned by the system, where the source UDP port is really the demultiplexer that identifies the particular instance that sent the request, when that demultiplexer correlates the reply. The source IP address is the system IP address of the sender.
When a traceroute request is sent via the data plane, the data plane format is used. The reply can be via the data plane or the control plane.
A data plane MAC traceroute request includes the tunnel encapsulation, the VC label, and the OAM, followed by an Ethernet DLC, a UDP, and IP header. If the mapping for the MAC address is known at the sender, then the data plane request is sent down the known SDP with the appropriate tunnel encapsulation and VC label. If it is not known, then it is sent down every SDP (with the appropriate tunnel encapsulation per SDP and appropriate egress VC label per SDP binding).
The tunnel encapsulation TTL is set to 255. The VC label TTL is initially set to the min-ttl (default is 1). The OAM label TTL is set to 2. The destination IP address is the all-routers multicast address. The source IP address is the system IP address of the sender.
The Reply Mode is either 3 (control plane reply) or 4 (data plane reply), depending on the reply-control option. By default, the data plane request is sent with Reply Mode 3 (control plane reply).
The Ethernet DLC header source MAC address is set to either the system MAC address (if no source MAC is specified) or to the specified source MAC. The destination MAC address is set to the specified destination MAC. The Ethertype is set to IP.
3.1.8.3. CPE Ping
The MAC ping OAM tool makes it possible to detect whether a particular MAC address has been learned in a VPLS.
The cpe-ping command extends this capability and can detect end-station IP addresses inside a VPLS. A CPE ping for a specific destination IP address within a VPLS will be translated to a MAC ping towards a broadcast MAC address. Upon receiving such a MAC ping, each peer PE within the VPLS context will trigger an ARP request for the specific IP address. The PE receiving a response to this ARP request will report back to the requesting 7705 SAR. Operators are encouraged to use the source IP address of 0.0.0.0 in order to prevent the provider’s IP address from being learned by the CE.
3.1.8.4. MAC Populate
MAC populate is used to send a message through the flooding domain to learn a MAC address as if a customer packet with that source MAC address had flooded the domain from that ingress point in the service. This allows the provider to craft a learning history and engineer packets in a particular way to test forwarding plane correctness.
The MAC populate request is sent with a VC TTL of 1, which means that it is received at the forwarding plane at the first hop and passed directly up to the management plane. The packet is then responded to by populating the MAC address in the forwarding plane, like a conventional learn, although the MAC will be an OAM-type MAC in the FIB to distinguish it from customer MAC addresses.
This packet is then taken by the control plane and flooded out the flooding domain (squelching appropriately, the sender and other paths that would be squelched in a typical flood).
This controlled population of the FIB is very important to manage the expected results of an OAM test. The same functions are available by sending the OAM packet as a UDP/IP OAM packet. It is then forwarded to each hop and the management plane has to do the flooding.
Options for MAC populate are to force the MAC in the table to type OAM (in case it already existed as dynamic or static or as an OAM-induced learning with some other binding), to prevent new dynamic learning to over-write the existing OAM MAC entry, or to allow customer packets with this MAC to either ingress or egress the network while still using the OAM MAC entry.
Finally, an option to flood the MAC populate request causes each upstream node to learn the MAC, for example, to populate the local FIB with an OAM MAC entry, and to flood the request along the data plane using the flooding domain.
An age can be provided to age a particular OAM MAC after a different interval than other MACs in a FIB.
3.1.8.5. MAC Purge
MAC purge is used to clear the FIBs of any learned information for a particular MAC address. This allows an operator to perform a controlled OAM test without learning induced by customer packets. In addition to clearing the FIB of a particular MAC address, the purge can also indicate to the control plane not to allow further learning from customer packets. This allows the FIB to be clean and be populated only via a MAC populate request.
MAC purge follows the same flooding mechanism as the MAC populate. A UDP/IP version of this command is also available that does not follow the forwarding notion of the flooding domain, but rather the control plane behavior of it.
3.1.9. Ethernet OAM Capabilities
The 7705 SAR supports Ethernet OAM capabilities, as described in the following sections:
3.1.9.1. Ethernet OAM Overview
The 7705 SAR supports the following Ethernet OAM capabilities:
- Ethernet Connectivity Fault Management (ETH-CFM) — for network layer OAM according to IEEE 802.1ag (dot1ag) and ITU Y.1731 standards, including loopback (LB), linktrace (LT), continuity check (CC), and remote defect indication (RDI). “Network layer” refers to an end-to-end context across a network.ITU-T Y.1731 provides functional enhancements to 802.1ag ETH-CFM, including alarm indication signals (AIS) and Ethernet signal tests (ETH-Test).
- Ethernet Bandwidth Notification (ETH-BN) – when enabled on a port, the egress rate may be dynamically altered based on the available bandwidth indicated by the ETH-BN server.
- Performance Monitoring (PM) — PM according to the ITU-T Y.1731 standard, including delay measurements (DM), delay variation measurements (DV), and loss measurements (LM)
- Ethernet First Mile (EFM) OAM — for the transport layer OAM according to IEEE 802.3ah (dot3ah) standards. “Transport layer” refers to a point-to-point link context or transport hop.See EFM OAM (802.3ah).
Ethernet OAM capabilities on the 7705 SAR are similar to the OAM capabilities offered in SONET/SDH networks and include loopback tests to verify end-to-end connectivity, test pattern generation (and response) to verify error-free operation, and alarm message generation in case of fault conditions to ensure that the far end is notified of the failure.
Ethernet OAM configurations are maintained across Control and Switching module (CSM) switchovers.
3.1.9.1.1. Ethernet OAM Usage Examples
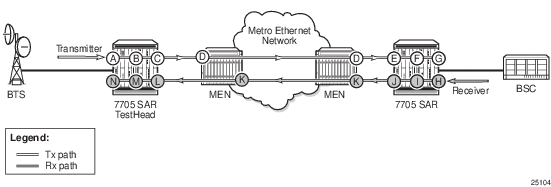
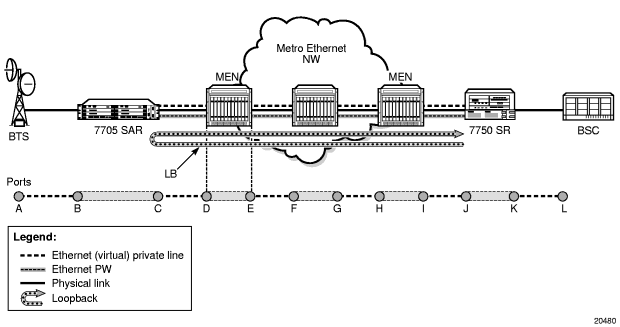
Figure 14 illustrates the complementary use of dot3ah and dot1ag to locate points of failure along a route from BTS to BSC. Since dot1ag and Y.1731 have similar functions, only dot1ag is discussed in order to simplify the explanation.
In Figure 14, from the IP/MPLS (network) layer perspective, the 7705 SAR looks as though it is connected directly to the 7750 SR. From the Ethernet (transport) layer perspective, the route passes through many ports and nodes, where each port or node is a potential point of failure. These failure points cannot be detected using IP/MPLS OAM capabilities (that is, using ETH-CFM (dot1ag)). However, they can be detected using EFM OAM (dot3ah) capabilities.
Figure 14: 7705 SAR Ethernet OAM Endpoints
Dot3ah uses port-level loopbacks to check and verify last-mile Ethernet frame integrity, connectivity verification between ports and nodes, and so on. As shown in Figure 14, dot3ah provides transport (link) layer OAM between the BTS and the 7705 SAR access port facing the BTS (ports A and B), or between the 7705 SAR network port and the MEN switch (ports C and D). Ethernet first mile (EFM) OAM allows users to test frame integrity and detect Ethernet layer failures faster than using associated heartbeat messages.
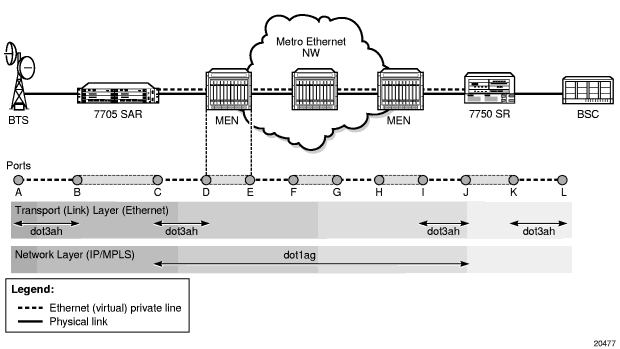
Dot1ag checks end-to-end connectivity across an Ethernet PW (across a network). Since end-to-end connectivity differs depending on the service provided and the span of the network, dot1ag can operate at several MD levels (as defined in the IEEE 802.1ag standard). For example, in Figure 14, ETH-CFM (dot1ag) could be used by a MEN provider at one MD level to ensure connectivity between ports D and I (or possibly all the way to their customer’s Ethernet ports, C and J). Similarly, a mobile backhaul service provider (MBSP) can use dot1ag at another MD level to ensure connectivity between ports B and K (and possibly between ports A and L).
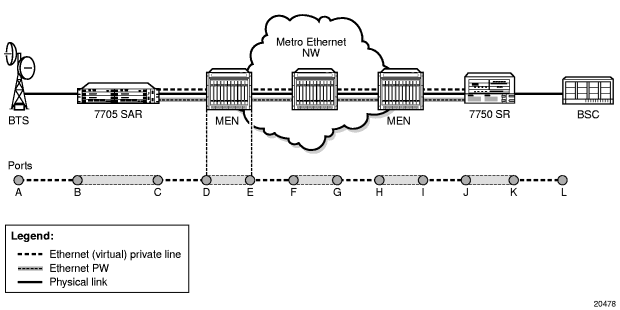
Figure 15 and Figure 16 illustrate the use of ETH-CFM to verify connectivity across an Ethernet PW and EFM OAM to verify transport layer connectivity between two directly connected nodes.
For example, in Figure 15, an MBSP can use dot1ag between the two Ethernet spoke SDP endpoints (ports C and J, which define the Ethernet PW) to ensure connectivity. Similarly, a MEP can use dot1ag between ports D and I to ensure the health status of the Ethernet (virtual) private line.
Figure 15: ETH-CFM (Dot1ag) Capabilities on the 7705 SAR
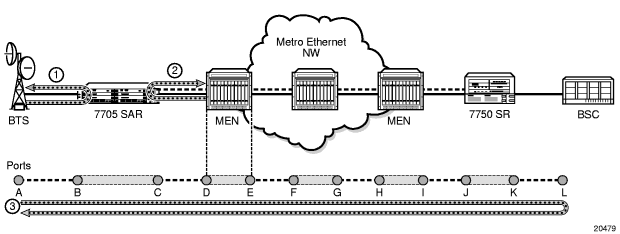
In Figure 16, EFM OAM ensures transport layer connectivity between two directly connected nodes. Figure 16 illustrates three scenarios in which EFM can be used by the MEN provider to ensure error-free connectivity to the 7705 SAR (the cell site) via loopback tests, including:
- scenario 1: EFM termination at the Ethernet access port, which includes loopback tests, heartbeat messages at the Ethernet layer with dying gasp, and termination of customer device-initiated EFM packets at the access port
- scenario 2: EFM termination at the Ethernet network port, which includes network-side loopbacks
- scenario 3: EFM tunneling through an Epipe service
Figure 16: EFM OAM (Dot3ah) Capabilities on the 7705 SAR
3.1.9.2. 802.1ag and Y.1731 Functional Comparison
Table 4 lists the 802.1ag and Y.1731 OAM functions supported on the 7705 SAR. For each function and test, the table identifies the PDU that carries the test data, the test’s target entity, and the standards that the 7705 SAR supports for the test.
For example, the 7705 SAR can run an Ethernet Continuity Check using an ETH-CC test according to the dot1ag and the Y.1731 standards. For either standard, the test data is carried in a Continuity Check message (CCM) and the test target is a MEP.
The Fault Management (FM) capabilities of ITU-T Y.1731 extend the functionality of dot1ag (ETH-CFM) with additional FM functions as well as performance monitoring (PM) capabilities. The generation of AIS and RDI messages are defined under the FM section of the Y.1731 specification, whereas Ethernet layer, delay, jitter, loss, and throughput tests are part of Y.1731 PM capabilities.
Table 4: 802.1ag and Y.1731 OAM Functionality Overview
Test | OAM Function | PDU | Target | Standard |
ETH-LB | Loopback | LBM, LBR | MEP | dot1ag, Y.1731 |
ETH-LT | Linktrace | LTM, LTR | MEP | dot1ag, Y.1731 |
ETH-CC | Continuity Check | CCM | MEP | dot1ag, Y.1731 |
ETH-RDI | Remote Defect Indication | CCM | MEP | dot1ag, Y.1731 |
ETH-AIS | Alarm Indication Signal | AIS | MEP | Y.1731 |
ETH-LM | Frame Loss Measurement (dual-ended) | CCM | MEP | Y.1731 |
ETH-LM | Frame Loss Measurement (single-ended) | LMM, LMR | MEP | Y.1731 |
ETH-DM | Frame Delay Measurement (two-way) | DMM, DMR | MEP | Y.1731 |
ETH-DM | Frame Delay Measurement (one-way) | 1DM | MEP | Y.1731 |
ETH-DV | Frame Delay Variation (one-way) | DMM, DMR | MEP | Y.1731 |
ETH-Test | Test Error Measurements | TST | MEP | Y.1731 |
ETH-SL | Synthetic Loss Measurement | SLM | MEP | Y.1731 |
3.1.9.3. ETH-CFM Ethernet OAM Tests (802.1ag and Y.1731)
Ethernet Connectivity Fault Management (ETH-CFM) is defined in the IEEE 802.1ag and ITU Y.1731 standards. ETH-CFM specifies protocols, procedures, and managed objects to support fault management (including discovery and verification of the path), detection, and isolation of a connectivity fault in an Ethernet network.
IEEE 802.1ag and Y.1731 can detect:
- loss of connectivity
- unidirectional loss
- loops
- merging of services
The implementation of Y.1731 on the 7705 SAR also provides the following enhancements:
- Ethernet Alarm Indication Signal (ETH-AIS)
- Ethernet Test function (ETH-Test)
ETH-CFM uses Ethernet frames and can be distinguished by its Ethertype value (8902). With ETH-CFM, interoperability can be achieved between different vendor equipment in the service provider network, up to and including customer premises bridges.
ETH-CFM is configured at the global level and at the Ethernet service level and/or network interface level. The following entities and their configuration levels are listed below:
- global level
- MA and MEG
- MD
- MD level and MEG level
- Ethernet service level
- MEP
- Ethernet network interface level
- facility MEP
For information on configuring ETH-CFM to set up an Ethernet OAM architecture, refer to the 7705 SAR Services Guide, “ETH-CFM (802.1ag and Y.1731)”. Most of the configuration information applies to Ethernet network interfaces as well; for information on ETH-CFM support specific to network interfaces, refer to the 7705 SAR Router Configuration Guide, “ETH-CFM Support”.
3.1.9.3.1. Hold MEP Up On Failure
The hold MEP up on failure function allows MEP operation that is independent of SAP status. In order to report service–level agreement (SLA) metrics, transport providers run Y.1731 performance monitoring tests periodically. At preset times, transport providers initiate various tests to measure and record one or all required SLA components: jitter, delay, loss and throughput. The ability to hold MEP up allows the MEP to be kept in operation even if the SAP is down or non-operational.
The hold MEP up on failure function is only applicable to Ethernet pseudowire services operating between SAPs or between SAPs and SDPs. The SAP connecting the provider equipment to the customer can be configured to hold the MEP in operation when the customer-facing SAP enters any failed state. Only one SAP per Ethernet pseudowire can be configured in this manner. Pseudowire status will indicate a failed SAP in the LDP status message but as long as the pseudowire is in an operationally up state, it supports receiving frames from the network’s far-end side. Counters are also incremented to accurately represent the number of received packets.
ETH-CFM PM measurements, ETH-CFM troubleshooting tools and connectivity, and ETH-CFM CCM processing and fault propagation are not impacted by this feature and continue to function normally.
3.1.9.3.2. Loopback (LB)
The loopback function is supported by 802.1ag and Y.1731 on the 7705 SAR. A Loopback Message (LBM) is generated by a MEP to its peer MEP. Both dot1ag and dot3ah loopbacks are supported. The loopback function is similar to IP or MPLS ping in that it verifies Ethernet connectivity between the nodes on a per-request basis. That is, it is non-periodic and is only initiated by a user request.
In Figure 17, the line labeled LB represents the dot1ag loopback message between the 7750 SR (source) and 7705 SAR (target) over an Epipe. The 7750 SR-generated LBM is switched to the 7705 SAR, where the LBM message is processed. Once the 7705 SAR generates the Loopback Reply message (LBR), the LBR is switched over the Ethernet PW to the 7750 SR.
Figure 17: Dot1ag Loopback Test
3.1.9.3.3. Linktrace (LT)
The linktrace function is supported by 802.1ag and Y.1731 on the 7705 SAR. A Linktrace Message (LTM) is originated by a MEP and targeted to a peer MEP in the same MA and within the same MD level. Its function is similar to IP traceroute. The peer MEP responds with a Linktrace Reply (LTR) message after successful inspection of the LTM.
3.1.9.3.4. Throughput Measurement
Throughput measurement is performed by sending frames to the far end at an increasing rate (up to wire speed) and measuring the percentage of frames received back. In general, the rate is dependent on frame size; the larger the frame size, the lower the rate.
The Y.1731 specification recommends the use of unicast ETH-LB and ETH-Test frames to measure throughput.
On the 7705 SAR, LBM processing and LBR generation is enhanced and occurs on the datapath, allowing the node to respond to loopback messages at wire speed and making in-service throughput tests possible. Thus, if the 7705 SAR receives LBMs at up to wire speed, it can generate up to an equal number of LBRs. In order to process LBMs at wire speed, there must be either no TLVs or a single TLV (which is a Data TLV) in the LBM frame. The End TLV field (0) must be present and the frame can be padded with data after the End TLV field in order to increase the size of the frame. The MAC address cannot be a multicast MAC address; it must be the MEP MAC destination address (DA).
Datapath processing of LBMs is supported for the following MEPs:
- dot1ag
- SAP Up MEP
- SAP Down MEP
- spoke-SDP Down MEP
- network interface facility Down MEP
- Y.1731
- SAP Up MEP
- SAP Down MEP
- network interface facility Down MEP
For spoke-SDP Down MEPs, fastpath (datapath) LBM processing requires that both interfaces—the LBM receiver and the LBR transmitter—reside on the same adapter card. For example, if the 7705 SAR must perform a reroute operation and needs to move the next hop interface to another adapter card (that is, LBMs are received on one card and LBRs are transmitted on another), then the fastpath processing of LBMs is terminated and LBM processing continues via the CSM.
3.1.9.3.5. Continuity Check (CC)
The continuity check function is supported by 802.1ag and Y.1731 on the 7705 SAR. A Continuity Check Message (CCM) is a multicast frame that is generated by a MEP and sent to its remote MEPs in the same MA. The CCM does not require a reply message. To identify faults, the receiving MEP maintains a MEP database with the MAC addresses of the remote MEPs with which it expects to maintain connectivity checking. The MEP database can be provisioned manually. If there is no CCM from a monitored remote MEP in a preconfigured period, the local MEP raises an alarm.
The following CC capabilities are supported:
- enable and disable CC for a MEP
- automatically put local MEPs into the database when they are created
- manually configure and delete the MEP entries in the CC MEP monitoring database. The only local provisioning required to identify a remote MEP is the remote MEP identifier (using the remote-mepid mep-id command).
- CCM transmit interval: 10ms, 100ms, 1s, 10s, 1m, 10m (default: 10s)
- transmit interval: 10ms, 100ms, 1s, 10s, 1m, 10m (default: 10s)
- CCM declares a fault when it:
- stops hearing from one of the remote MEPs for a period of 3.5 times the CC interval
- hears from a MEP with a lower MD level
- hears from a MEP that is not in the same MA
- hears from a MEP that is in the same MA but is not in the configured MEP list
- hears from a MEP that is in the same MA with the same MEP ID as the receiving MEP
- recognizes that the CC interval of the remote MEP does not match the local configured CC interval
- recognizes that the remote MEP declares a faultAn alarm is raised and a trap is sent if the defect is greater than or equal to the configured low-priority-defect value.
- CC must be enabled in order for RDI information to be carried in the CCM OAMPDU
The optional ccm-tlv-ignore command can be used to ignore the receipt of interface-status and port-status TLVs in the ETH-CCM PDU on a facility MEP. No processing is performed on ignored ETH-CCM TLV values.
Any TLV that is ignored is reported as absent to the relevant remote peer, and the values in the TLV do not have any effect. This is the same behavior as if the received ETH-CCM PDU never included these TLVs in the first place. If the TLV is not properly formed, the ETH-CCM PDU will fail the packet parsing process, which will cause it to be discarded and an alarm to be raised.
3.1.9.3.6. ETH-RDI
The Ethernet Remote Defect Indication function (ETH-RDI) is used by a MEP to communicate to its peer MEPs that a defect condition has been encountered. Defect conditions such as signal fail and AIS may result in the transmission of frames with ETH-RDI information. ETH-RDI is used only when ETH-CC transmission is enabled.
ETH-RDI has the following two applications:
- single-ended fault management — the receiving MEP detects an RDI defect condition, which gets correlated with other defect conditions in this MEP. The absence of received ETH-RDI information in a single MEP indicates the absence of defects in the entire MEG.
- contribution to far-end performance monitoring — the transmitting MEP reflects that there was a defect at the far end, which is used as an input to the performance monitoring process
A MEP that is in a defect condition transmits frames with ETH-RDI information. A MEP, upon receiving frames with ETH-RDI information, determines that its peer MEP has encountered a defect condition.
The specific configuration information required by a MEP to support the ETH-RDI function is as follows:
- MEG level — the MEG level at which the MEP exists
- ETH-RDI transmission period — application-dependent and is the same value as the ETH-CC transmission period
- priority — the priority of frames containing ETH-RDI information and is the same value as the ETH-CC priority
The PDU used to carry ETH-RDI information is the CCM.
| Note: When a port or interface experiences a failure, the Up MEP on the port or interface transmits a Port or Interface Status TLV (or both).
|
3.1.9.3.7. ETH-AIS
The Ethernet Alarm Indication Signal function (ETH-AIS) is a Y.1731 CFM enhancement used to suppress alarms at the client (sub) layer following detection of defect conditions at the server (sub) layer.
Transmission of frames with ETH-AIS information can be enabled or disabled on a Y.1731 MEP.
| Note: ETH-AIS is not supported on network interface facility MEPs. |
Frames with ETH-AIS information can be issued at the client MEG level by a MEP, including a server MEP, upon detecting the following conditions:
- signal failure conditions in the case where ETH-CC is enabled
- AIS condition in the case where ETH-CC is disabled
For a point-to-point Ethernet connection at the client (sub) layer, a client layer MEP can determine that the server (sub) layer entity providing connectivity to its peer MEP has encountered a defect condition upon receiving a frame with ETH-AIS information. Alarm suppression is simplified by the fact that a MEP is expected to suppress only those defect conditions associated with its peer MEP.
Only a MEP, including a server MEP, is configured to issue frames with ETH-AIS information. Upon detecting a defect condition, the MEP can immediately start transmitting periodic frames with ETH-AIS information at a configured client MEG level. A MEP continues to transmit periodic frames with ETH-AIS information until the defect condition is removed. Upon receiving a frame with ETH-AIS information from its server (sub) layer, a client (sub) layer MEP detects the AIS condition and suppresses alarms associated with all its peer MEPs. Once the AIS condition is cleared, a MEP resumes alarm generation upon detecting defect conditions.
The following specific configuration information is required by a MEP to support ETH-AIS:
- client MEG level — the MEG level at which the most immediate client layer MEPs exist
- ETH-AIS transmission period — the transmission period of frames with ETH-AIS information
- priority — the priority of frames with ETH-AIS information
3.1.9.3.8. ETH-Test
The Ethernet Test (signal) function (ETH-Test) is a Y.1731 CFM enhancement used to perform one-way, on-demand, in-service diagnostics tests, which include verifying frame loss, bit errors, and so on.
| Note: The out-of-service diagnostics test is not supported in the 7705 SAR. |
When configured to perform such tests, a MEP inserts frames with ETH-Test information such as frame size and transmission patterns.
When an in-service ETH-Test function is performed, data traffic is not disrupted and the frames with ETH-Test information are transmitted.
To support ETH-Test, a Y.1731 MEP requires the following configuration information:
- MEG level — the MEG level at which the MEP exists
- unicast MAC address — the unicast MAC address of the peer MEP for which the ETH-Test is intended
- data — an optional element with which to configure data length and contents for the MEP. The contents can be a test pattern and an optional checksum.Examples of test patterns include all 0s or all 1s. At the transmitting MEP, this configuration information is required for a test signal generator that is associated with the MEP. At the receiving MEP, this configuration is required for a test signal detector that is associated with the MEP.
- priority — the priority of frames with ETH-Test information
A MEP inserts frames with ETH-Test information towards a targeted peer MEP. The receiving MEP detects the frames with ETH-Test information and performs the requested measurements.
3.1.9.4. ITU-T Y.1731 Ethernet Bandwidth Notification (ETH-BN)
The Ethernet Bandwidth Notification (ETH-BN) function, as defined in ITU-T Rec. G.8013/Y.1731, is used by a server MEP to signal changes in link bandwidth to a client MEP.
One of the best applications of this functionality is for point-to-point microwave radios. When a microwave radio uses adaptive modulation, the capacity of the radio can change based on the condition of the microwave link. For example, in adverse weather conditions that cause link degradation, the radio can change its modulation scheme to a more robust one (which will reduce the link bandwidth) in order to continue transmitting. This change in bandwidth is communicated from the server MEP on the radio, using ETH-BNM (Ethernet Bandwidth Notification Message), to the client MEP on the connected router. The router responds to this information by adjusting the rate of traffic being sent to the radio. The server MEP continues to transmit periodic frames with ETH-BN information with the currently available bandwidth. When full bandwidth is restored, the ETH-BNM will start indicating the full bandwidth.
When the 7705 SAR, Release 8.0, is interoperating with 9500 MPR-e radios, ETH-BN functionality is supported with 9500 MPR-e radios in standalone mode. ETH-BN support with MWA mode will be considered in a future release.
The 7705 SAR supports the client side of ETH-BN, receiving and acting on the ETH-BN information sent by the server MEP.
ETH-BN is supported on Ethernet ports on the following adapter cards, modules, and platforms:
- 8-port Gigabit Ethernet Adapter card
- 10-port 1GigE/1-port 10GigE X-Adapter card
- Packet Microwave Adapter card
- 6-port Ethernet 10Gbps Adapter card
- 2-port 10GigE (Ethernet) Adapter card (v-port)
- 2-port 10GigE (Ethernet) module (v-port)
- 6-port SAR-M Ethernet module
- all fixed platforms, with the exception of Fast Ethernet ports on the 7705 SAR-A (ports 9 to 12)
The ports can be configured for network, access, or hybrid mode. When ETH-BN is enabled on a port with the egress-rate sub-rate allow-eth-bn-rate-changes command, the egress rate, which was configured as a fixed bandwidth, can be dynamically changed based on the available bandwidth indicated by the ETH-BN server.
The maximum egress rate that the port can be set to is the native port rate (for example, 1 Gb/s), and the minimum egress rate is 1 kb/s. If a rate request is outside that range, including 0, it cannot be implemented, and the egress rate is set as close as possible to the requested rate. The egress rate setting has a ±1% accuracy, as rate conversion to the hardware is necessary. Any request for a change less than 1% is ignored.
To reduce the number of bandwidth changes (each change incurs a small data hit), a hold timer can be configured. The range is 1 to 600 s with a default of 5 s. Any ETH-BN message received before the hold timer expires, after the last bandwidth change, is ignored.
The bandwidth indicated by the ETH-BN server includes the FCS; therefore, the include-fcs option must also be selected in the egress-rate command or the bandwidth will not match the intended rate.
For information on the egress-rate command, refer to the “Ethernet Commands” section in the 7705 SAR Interface Configuration Guide, “Configuration Command Reference” chapter.
3.1.9.4.1. Bandwidth Notification Message (BNM)
The PDU used for ETH-BN information is called the Bandwidth Notification Message (BNM).
The BNM PDU format consists of the following fields:
- MEG level – carries the MEG level of the client MEP (0 to 7); this field can be any value
- Version – current version is 0
- OpCode – value for this PDU type is GMN (32)
- Flags – contains one information element:
- period – bits 3 to 1 indicate how often BN messages are transmitted; currently, the only valid values are 100 (1 frame/s), 101 (1 frame/10 s), and 110 (1 frame/min)
- TLV Offset – set to 13
- Sub-OpCode – value for this PDU type is BNM (1)
- Nominal Bandwidth – the nominal full bandwidth of the link, in Mb/s; this information is ignored by the 7705 SAR
- Current Bandwidth – the current bandwidth of the link, in Mb/s
- Port ID – a non-zero unique identifier for the port associated with the ETH-BN information, or zero if not used; this information is ignored by the 7705 SAR
- End TLV – all zeros octet value
Typical behavior for ETH-BN is that if no BNM frames are received within an interval of 3.5 times the BNM transmission period indicated in the last BNM frame received, the MEP signals to the management system that it no longer has any bandwidth information (for example, because the full bandwidth has been restored). For the 7705 SAR implementation, no action is taken if no BNM frame arrives within 3.5 periods.
Upon startup or restart of the system, the configured egress rate is used until a BNM arrives on the port with a new bandwidth request from the ETH-BN server MEP.
Event logs are generated each time the egress bandwidth is changed based on reception of a BNM. If a BNM is received that does not result in a bandwidth change, no event log is generated.
BN messages are transmitted with a source MAC address that cannot be a multicast address or have a value of 0. The destination MAC address can be a Class 1 multicast address (that is, 01-80-C2-00-0x) or the MAC address of the configured port. If these conditions are not satisfied, the message is discarded. The packets are rate-limited to the CSM as are all OAM packets.
BN messages with zero, one, or two VLAN tags are supported.
For LAG bundles, the BNM settings in the primary port are propagated to all the other member links. Each link in the bundle must always have the same value.
3.1.9.5. ITU-T Y.1731 Performance Monitoring (PM)
The Y.1731 Performance Monitoring (PM) functions can be used to measure Ethernet frame delay, delay variation, throughput (including throughput at queue-rates), and frame loss. These performance parameters are defined for point-to-point Ethernet connections.
3.1.9.5.1. Delay and Delay Variation Measurements (DM and DV)
The Y.1731 recommendation covers the following performance parameters, which are based on Metro Ethernet Forum (MEF) 10:
- frame delay — specified as one-way or round-trip delay for a frame, where frame delay is defined as the time elapsed since the start of transmission of the first bit of the frame by a source node until the reception of the frame by the destination node or the same source node
- frame delay variation — a measure of the variations in the frame delay between a pair of service frames, where the service frames belong to the same CoS instance on a point-to-point Ethernet connection
The performance parameters listed above are applicable to Ethernet services frames. Services frames are those frames that conform to an agreed-upon level of bandwidth profile conformance and are associated with a particular CoS identifier. Services frames are admitted at the ingress Ethernet flow point of a point-to-point Ethernet connection and should be delivered to the egress Ethernet flow point.
The 7705 SAR supports one-way and two-way Ethernet Delay Measurement (ETH-DM) tests (section 8.2 of the Y.1731 standard), using the CLI commands oam> eth-cfm>one-way-delay-test and oam>eth-cfm>two-way-delay-test. Ethernet Delay Variation (ETH-DV) tests are run concurrently with the one-way and two-way ETH-DM tests.
For ETH-DM, the accuracy of the measurement is in the microseconds range.
3.1.9.5.2. Y.1731 Delay Measurement (DM)
Y.1731 delay measurement implementation ensures the most accurate results under all circumstances. The implementation ensures that there is minimal delay measurement error between packet generation and packet play-out over the Ethernet link.
In order to isolate delay measurement results from the effects of any queuing, scheduling, and shaping procedures, timestamping of source one-way and two-way delay measurement (1DM and DMM) frames in the transmit direction occurs when the first byte of the DM frame is put on the wire (that is, once the actual serialization starts). Last-minute timestamping ensures that DM tests truly measure the delay between two SAP or port endpoints, and not the delay imposed by the routers. Using these accurate measurements, a network operator can separate the delay introduced by the routers from the transmission delay introduced by the transmission network, such as a Metro Ethernet network (MEN) or Generic Framing Procedure (GFP) over SONET links.
Timestamping of received 1DM and DMM frames is similar to transmitted source 1DM and DMM frames. When a Y.1731 delay measurement frame is identified internally, it is immediately timestamped to ensure reporting of only the network-induced delay and jitter.
With two-way delay measurement, delay measurement reply (DMR) timestamping occurs at the entry point to the egress datapath. DMR frames are then classified according to their configured dot1p setting and experience any scheduling delays experienced by the queue and scheduling priorities that the frames are associated with. Performing DMR timestamping at the entry point to the egress datapath provides the most accurate end-to-end measurement of delay and jitter, as it takes into account the internal delay of the responding node due to other higher-priority packets.
In summary, one-way delay measurement performs timestamping in the transmit direction only when the frame is about to be sent on the wire and in the receive direction when the frame is received, before any queuing at the far end. This provides true transport network-induced delay and jitter measurements. Two-way delay measurement takes into account the delay introduced by queuing and scheduling of the far-end node for true end-to-end measurements.
3.1.9.5.3. Loss Measurement (LM)
The 7705 SAR supports single-ended and dual-ended Ethernet Loss Measurement (ETH-LM) tests. Dual-ended LM tests are enabled under the config>service> epipe>sap>eth-cfm>mep and config>router>if>eth-cfm>mep contexts. When enabled, dual-ended LM tests run continuously in the background. Single-ended LM tests are run from the oam>eth-cfm context and are considered on-demand tests.
Y.1731 loss measurement functionality is implemented to ensure the most accurate results under all circumstances. Each adapter card has a network processor (NP). LM counters are maintained at the NP. The NP is responsible for incrementing and resetting these counters. These counters are accessed by the CSM CPU in order to calculate and display the loss (percentage) to the user.
LM/CCM frames follow the associated QoS path and therefore might inadvertently report loss due to local congestion even before the frame is switched onto the link. In order to reflect the true experience of a particular QoS setting, generated LM/CCM frames follow the egress QoS path. Once generated, these frames are classified in the same manner as the applicable dot1p-to-FC mapping, associated queuing, and scheduling rules. Following the proper path ensures that loss measurements reflect the experience of a given FC all the way through the network, including within the 7705 SAR platform. As is the case for any other frame of the same FC (that is, user or control frame), the LM/CCM frame follows the associated QoS path to reflect the real experience.
For example, newly generated LM/CCM frames that have a higher counter value can be forwarded sooner than LM/CCM frames with a lower counter value that have been generated but are waiting to be serviced (that is, frames with a lower queue, a queue in the out-of-profile state; or a single SAP with multiple FCs). As a result, when under congestion, the LM ratio would increase to reflect local loss if lower-priority frames cannot be serviced in a timely manner.
In addition, congestion, and hence prioritization, can occur anywhere in the transport network, which means that a reordering might take place not only on the ingress point, but anywhere in the network along the entire path.
The loss ratio is calculated based on the aggregate frames being transmitted and received. Thus, in a uncongested network, the loss ratio would be 0%. With congestion, not all frames may be sent out to the network (that is, higher priority traffic, and so on) or any one of the transit nodes or the endpoint node might drop the packet, which would end up with loss.
The above-described behavior for following the QoS path equally applies to both Up and Down MEPs. Loss measurements in both up and down directions for the same MEP can be performed simultaneously.
The counters used for loss measurement in LM and CCM frames are appended as late as possible in the datapath. Appending the counters at the last minute to the LM or CCM frames ensures that a scheduling priority issue or some other queue-delaying event does not delay the OAM frame in a queue. If the counters are updated or generated earlier in the datapath, then the OAM frames could be affected by queuing or scheduling delays, which might cause the frames to be counted as lost frames when the far-end receive timer expires.
The following notes apply to Y.1731 LM tests.
- Single-ended and dual-ended LM tests cannot be enabled on a MEP simultaneously. That is, either a single-ended or a dual-ended LM test can be enabled on a given MEP at any given time.
- The behavior and the interaction between single- and dual-ended LM tests are described in the following list. Error conditions, such as correct domain level and valid destination address (DA) MAC, are not covered in the list:
- if dual-ended loss test is disabled:
- CCM frames are transmitted with LM counters set to 0
- CCM frames being received are not processed for LM
- LMM and LMR frames being received are processed
- single-ended tests can be enabled (not blocked by CLI)
- if dual-ended loss test is enabled:
- single-ended tests cannot be enabled (blocked by CLI)
- LMM and LMR frames being received will be dropped
- Multiple MEPs bound to the same Epipe SAP but belonging to different MEG levels can perform LM tests simultaneously.
- CCM must be enabled before a dual-ended LM test can be enabled.
- When a dual-ended LM test is enabled, the user cannot disable CCM. The dual-ended LM test needs to be disabled before the CCM can be disabled.
- For dual-ended LM tests, an alarm is declared when frame losses are greater than an alarm threshold configured for the MEP. The granularity of the alarm threshold (declaring or clearing) is 0.01%. The default threshold is set to 0.25%.
- On a per-SAP or per-network interface basis, there is one set of Rx and Tx Local LM counters and one set of Rx and Tx Remote LM counters. LM counters are not separated on a per-MAC source address (SA) basis. All MEPs, irrespective of their MD or MEG level, share the same set of Rx and Tx LM counters.
- On the CLI, there are interval counters and accumulated counters. The CCM counters are referred to as Local and FarEnd counters and the accumulated counters are referred to as Near-End and Far-End counters.
- The LM counters are incremented when a user data frame reaches a SAP. Since there is only one set of Tx and Rx Local counters per SAP, each user data frame received by all the MEPs configured on that SAP is counted.
- OAM frames with MEP levels matching or lower than the locally configured MEP level are not counted. They are treated and processed as OAM frames. This functionality applies to both received and transmitted OAM frames. CFM OAM frames at higher MEP levels are counted as user data frames.
- For example, assume a SAP with two MEPs configured on it; one MEP at level 5 and the other at level 6.
- When a level 6 OAM frame is received, it is extracted to the CSM for processing and is not counted by LM counters. It is treated as an OAM frame.
- The same behavior applies in the transmit direction. In the above example, any level 5 or level 6 OAM frames generated by the local SAR would not be counted by the far-end LM counters.
- For dual-ended LM tests, any received CCMs with all LM counters being 0s (zeros) are treated as invalid. In this case, the 7705 SAR resets the LM counters for the current and previous CCMs to 0s (zeros). Accumulated counters are not reset.
- Except for a valid counter rollover scenario, if the value of any CCM/LMR counter is less than the value of the same counter in the previous CCM/LMR frame, then the accumulated values of all counters are not increased; they are kept at the same values as before the last CCM/LMR frame is processed.
- When the first valid CCM/LMR frame — that is, a frame with at least one non-zero LM counter — is received after a dual-ended loss test is enabled or a single-ended loss test is launched, the accumulated values cannot be calculated. In this case, the counters are resaved as current counters. When the next received CCM/LMR frame with valid LM counts is received, it will trigger the update of accumulation counts.Accumulated counts always start at 0 for each launch of a single-ended test. However, the accumulation counts do not change nor do they get reset to all 0s when dual-ended loss tests become disabled. For dual-ended loss tests, accumulated counts can be restarted at 0s by removing the existing LM result of a particular MEP with the CLI command clear>eth-cfm>dual-ended-loss-test>mep mep-id domain md-index association ma-index, or the equivalent SNMP command.
3.1.9.6. CFM OAM QoS
It is important that CFM OAM tools use the relevant FC and the associated queue to report traffic performance issues such as delay, jitter, and loss. When user traffic is mapped to one FC/queue and the OAM traffic is mapped to another FC/queue, data reported by the OAM tools might not be a true reflection of the performance metrics that the user traffic is experiencing, due mainly to different queue depths and scheduling priorities.
In order to ensure that CFM OAM traffic experiences the same treatment as user traffic, the 7705 SAR supports a configurable priority to specify the FC, and therefore the queue, to be used for a given OAM test. The priority keyword in the eth-cfm loopback, one-way-delay-test, single-ended-loss-test, two-way-delay-test and two-way-slm-test commands is used to configure the FC mapping as per the configured priority. The priority value maps to a specific FC; therefore, selecting a priority selects the FC. Table 5 lists the priority-to-FC mapping. This mapping of priority to FC cannot be changed by the user.
Table 5: Y.1731 Priority-to-FC Mapping
Priority | FC-ID | FC Name |
0 | 0 | BE |
1 | 1 | L2 |
2 | 2 | AF |
3 | 3 | L1 |
4 | 4 | H2 |
5 | 5 | EF |
6 | 6 | H1 |
7 | 7 | NC |
The priority-to-FC mapping does change depending on the message type and direction of the MEP. Table 6 summarizes the FC and Dot1p priority mappings based on this criteria.
Table 6: Priority Mapping Based on Message Type and MEP Direction
MEP Type | Message Type | FC | Dot1p |
SAP Down MEP | CCM | Dictated via ccm-ltm-priority value | Dictated via ccm-ltm-priority value |
LMM, DMM, 1DM, LBM | User-defined priority value copied | User-defined priority value copied | |
LMR, DMR, LBR | ccm-ltm-priority value | Incoming dot1p priority preserved | |
SAP Up MEP | CCM | User-defined priority value copied to dot1p and FC as per sap-ingress classification | Dictated via ccm-ltm-priority value |
LMM, DMM, 1DM, LBM | User-defined priority value copied to dot1p and FC as per sap-ingress classification | User-defined priority value copied | |
LMR, DMR, LBR | User-defined priority value copied to dot1p and FC as per sap-ingress classification | Incoming dot1p priority preserved |
For more information, refer to the 7705 SAR Services Guide, “Priority Mapping (802.1ag and Y.1731)”.
3.1.9.7. EFM OAM (802.3ah)
802.3ah Clause 57 defines the Ethernet in the First Mile (EFM) OAM sublayer, which is a link-level Ethernet OAM that is supported on 7705 SAR Ethernet ports configured as network or access ports. It provides mechanisms for monitoring link operations such as remote fault indication and remote loopback control. Ethernet OAM gives network operators the ability to monitor the health of Ethernet links and quickly determine the location of failing CFM links or fault conditions.
Because some of the sites where the 7705 SAR will be deployed will have only Ethernet uplinks, this OAM functionality is mandatory. For example, mobile operators must be able to request remote loopbacks from the peer router at the Ethernet layer in order to debug any connectivity issues. EFM OAM provides this capability.
EFM OAM defines a set of events that may impact link operation. The following events are supported:
- critical link events (defined in 802.3ah clause 57.2.10.1)
- link fault: the PHY has determined that a fault has occurred in the receive direction of the local DTE
- dying gasp: an unrecoverable local failure condition has occurred
- critical event: an unspecified critical event has occurred
These critical link events are signaled to the remote DTE by the flag field in OAMPDUs.
EFM OAM is supported on network and access Ethernet ports, and is configured at the Ethernet port level. The access ports can be configured to tunnel the OAM traffic originated by the far-end devices.
EFM OAM has the following characteristics.
- All EFM OAM, including loopbacks, operate on point-to-point links only.
- EFM loopbacks are always line loopbacks (line Rx to line Tx).
- When a port is in loopback, all frames (except EFM frames) are discarded. If dynamic signaling and routing is used (dynamic LSPs, OSPF, IS-IS, or BGP routing), all services also go down. If all signaling and routing protocols are static (static routes, LSPs, and service labels), the frames are discarded but services stay up.
The following EFM OAM functions are supported:
- OAM capability discovery
- configurable transmit interval with an Information OAMPDU
- active or passive mode
- OAM loopback
- OAMPDU tunneling and termination (for Epipe service)
- dying gasp at network and access ports
For information on Epipe service, refer to the 7705 SAR Services Guide, “Ethernet VLL (Epipe) Services”.
3.1.9.7.1. Unidirectional OAM Operation
Some physical layer devices support unidirectional OAM operation. When a link is operating in unidirectional OAM mode, the OAM sublayer ensures that only information OAMPDUs with the Link Fault critical link event indication set and no Information TLVs are sent across the link.
3.1.9.7.2. Remote Loopback
EFM OAM provides a link-layer frame loopback mode, which can be controlled remotely.
To initiate a remote loopback, the local EFM OAM client enables the OAM remote loopback command to send a loopback control OAMPDU. After receiving the loopback control OAMPDU, the remote OAM client puts the remote port into local loopback mode.
OAMPDUs are slow protocol frames that contain appropriate control and status information used to monitor, test, and troubleshoot OAM-enabled links.
To exit a remote loopback, the local EFM OAM client sends a loopback control OAMPDU by disabling the OAM remote loopback command. After receiving the loopback control OAMPDU, the remote OAM client puts the port back into normal forwarding mode.
When a port is in local loopback mode (the far end requested an Ethernet OAM loopback), any packets received on the port will be looped back, except for EFM OAMPDUs. No data will be transmitted from the node; only data that is received on the node will be sent back out.
When the node is in remote loopback mode, local data from the CSM is transmitted, but any data received on the node is dropped, except for EFM OAMPDUs.
Remote loopbacks should be used with caution; if dynamic signaling and routing protocols are used, all services go down when a remote loopback is initiated. If only static signaling and routing is used, the services stay up. On the 7705 SAR, the Ethernet port can be configured to accept or reject the remote-loopback command.
3.1.9.7.3. 802.3ah OAMPDU Tunneling and Termination for Epipe Services
Customers who subscribe to Epipe service might have customer equipment running 802.3ah at both ends. The 7705 SAR can be configured to tunnel EFM OAMPDUs received from a customer device to the other end through the existing network using MPLS or GRE, or to terminate received OAMPDUs at a network or an access Ethernet port.
| Note: This feature applies only to port-based Epipe SAPs because 802.3ah runs at port level, not at VLAN level. |
While tunneling offers the ability to terminate and process the OAM messages at the head-end, termination on the first access port at the cell site can be used to detect immediate failures or can be used to detect port failures in a timelier manner.
The user can choose either tunneling or termination, but not both at the same time.
In Figure 16, scenario 1 shows the termination of received EFM OAMPDUs from a customer device on an access port, while scenario 2 shows the same thing except for a network port. Scenario 3 shows tunneling of EFM OAMPDUs through the associated Ethernet PW. To configure termination (scenario 1), use the config>port>ethernet>efm-oam>no shutdown command.
3.1.9.7.4. Dying Gasp
Dying gasp is used to notify the far end that EFM-OAM is disabled or shut down on the local port. The dying gasp flag is set on the OAMPDUs that are sent to the peer. The far end can then take immediate action and inform upper layers that EFM-OAM is down on the port.
When a dying gasp is received from a peer, the node logs the event and generates an SNMP trap to notify the operator.
3.1.10. Ethernet Loopbacks
Table 7 lists the loopbacks supported on Ethernet, DSL module (6-port DSL Combination module and 8-port xDSL module), and GPON module ports.
Table 7: Loopbacks Supported on Ethernet, DSL, and GPON Ports
Loopback | |||
Ethernet | DSL | GPON | |
Timed network line loopback | ✓ | ✓ | |
Timed and untimed access line loopbacks | ✓ | ✓ | |
Timed and untimed access internal loopbacks | ✓ | ✓ | ✓ |
Persistent access line loopback | ✓ | ||
Persistent access internal loopback | ✓ | ||
MAC address swapping | ✓ | ||
CFM loopback on network and access ports | ✓ | ✓ | ✓ |
CFM loopback on ring ports and v-port | ✓ | ||
3.1.10.1. Line and Internal Ethernet Loopbacks
A line loopback loops frames received on the corresponding port back towards the transmit direction. Line loopbacks are supported on ports configured for access or network mode.
Similarly, a line loopback with MAC addressing loops frames received on the corresponding port back towards the transmit direction, and swaps the source and destination MAC addresses before transmission. See MAC Swapping for more information.
An internal loopback loops frames from the local router back to the framer. This is usually referred to as an equipment loopback. The transmit signal is looped back and received by the interface. Internal loopbacks are supported on ports configured in access mode.
If a loopback is enabled on a port, the port mode cannot be changed until the loopback has been disabled.
A port can support only one loopback at a time. If a loopback exists on a port, it must be disabled or the timer must expire before another loopback can be configured on the same port. EFM-OAM cannot be enabled on a port that has an Ethernet loopback enabled on it. Similarly, an Ethernet loopback cannot be enabled on a port that has EFM-OAM enabled on it.
When an internal loopback is enabled on an Ethernet port, autonegotiation is turned off silently. This is to allow an internal loopback when the operational status of a port is down. Any user modification to autonegotiation on a port configured with an internal Ethernet loopback will not take effect until the loopback is disabled.
The loopback timer can be configured from 30 s to 86400 s. All non-zero timed loopbacks are turned off automatically under the following conditions: an adapter card reset, DSL module reset, GPON module reset, an activity switch, or timer expiry. Line or internal loopback timers can also be configured as a latched loopback by setting the timer to 0 s, or as a persistent loopback with the persistent keyword. Latched and persistent loopbacks are enabled indefinitely until turned off by the user. Latched loopbacks survive adapter card resets and activity switches, but are lost if there is a system restart. Persistent loopbacks survive adapter card resets and activity switches and can survive a system restart if the admin>save or admin>save>detail command was executed prior to the restart. Latched loopbacks (untimed) and persistent loopbacks can be enabled only on Ethernet access ports.
Persistent loopbacks are the only Ethernet loopbacks saved to the database by the admin>save and admin>save>detail commands.
3.1.10.1.1. MAC Swapping
Typically, an Ethernet port loopback only echoes back received frames. That is, the received source and destination MAC addresses are not swapped. However, not all Ethernet equipment supports echo mode, where the original sender of the frame must support receiving its own port MAC address as the destination MAC address.
The MAC swapping feature on the 7705 SAR is an optional feature that swaps the received destination MAC address with the source MAC address when an Ethernet port is in loopback mode. After the swap, the FCS is recalculated to ensure the validity of the Ethernet frame and to ensure that the frame is not dropped by the original sender due to a CRC error.
MAC swapping is not supported on the GPON module, 6-port DSL Combination module, or 8-port xDSL module.
3.1.10.1.2. Interaction of Ethernet Port Loopback with Other Features
EFM OAM and line loopback are mutually exclusive. If one of these functions is enabled, it must be disabled before the other can be used.
However, a line loopback precedes the dot1x behavior. That is, if the port is already dot1x-authenticated it will remain so. If it is not, EAP authentication will fail.
Ethernet port-layer line loopback and Ethernet port-layer internal loopback can be enabled on the same port with the down-when-looped feature. EFM OAM cannot be enabled on the same port with the down-when-looped feature. For more information, refer to the 7705 SAR Interface Configuration Guide, “Ethernet Port Down-When-Looped”.
3.1.10.2. CFM Loopbacks for OAM on Ethernet Ports
Connectivity fault management (CFM) loopback support for loopback messages (LBMs) on Ethernet ports allows operators to run standards-based Layer 1 and Layer 2 OAM tests on ports receiving unlabeled packets.
The 7705 SAR supports CFM MEPs associated with different endpoints (that is, spoke SDP down MEPs, and SAP up and SAP down MEPs). In addition, for traffic received from an uplink (network ingress), the 7705 SAR supports CFM LBM for both labeled and unlabeled packets. CFM loopbacks are applied to the Ethernet port.
See Ethernet OAM Capabilities for information on CFM MEPs.
Figure 18 shows an application where an operator leases facilities from a transport network provider in order to transport traffic from a cell site to their MTSO. The operator leases a certain amount of bandwidth between the two endpoints (the cell site and the MTSO) from the transport provider, who offers Ethernet Virtual Private Line (EVPL) or Ethernet Private Line (EPL) PTP service. Before the operator offers services on the leased bandwidth, the operator runs OAM tests to verify the SLA. Typically, the transport provider (MEN provider) requires that the OAM tests be run in the direction of (towards) the first Ethernet port that is connected to the transport network. This is done in order to eliminate the potential effect of queuing, delay, and jitter that may be introduced by a spoke SDP or SAP.
Figure 18: CFM Loopback on Ethernet Ports
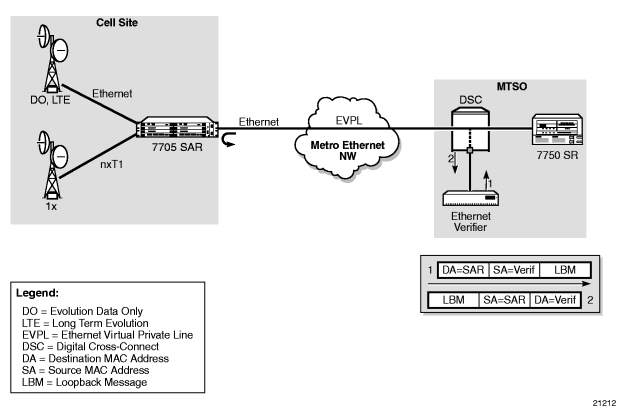
Figure 18 shows an Ethernet verifier at the MTSO that is directly connected to the transport network (in front of the 7750 SR). Thus, the Ethernet OAM frames are not label- encapsulated. Given that Ethernet verifiers do not support label operations and the transport provider mandates that OAM tests be run between the two hand-off Ethernet ports, the verifier cannot be relocated behind the 7750 SR node at the MTSO. Therefore, CFM loopback frames received are not MPLS-encapsulated, but are simple Ethernet frames where the type is set to CFM (dot1ag or Y.1731).
3.1.10.2.1. CFM Loopback Mechanics
The following list contains important facts to consider when working with CFM loopbacks:
- CFM loopbacks can be enabled on a per-port basis, and:
- the port can be in access or network mode
- once enabled on a port, all received LBM frames are processed, regardless of the VLAN and the service that the VLAN or SAP is bound to
- there is no associated MEP creation involved with this feature; therefore, no domain, association, or similar checks are performed on the received frame
- upon finding a destination address MAC match, the LBM frame is sent to the CFM process
- CFM loopback support on a physical ring port on the 2-port 10GigE (Ethernet) Adapter card/module differs from other Ethernet ports. For these ports, cfm-loopback is configured, optionally, using dot1p and match-vlan to create a list of up to 16 VLANs. The null VLAN is always applied. The CFM Loopback Message will be processed if it does not contain a VLAN header, or if it contains a VLAN header with a VLAN ID that matches one in the configured match-vlan list.
- received LBM frames undergo no queuing or scheduling in the ingress direction
- at egress, loopback reply (LBR) frames are stored in their own queue; that is, a separate new queue is added exclusively for LBR frames
- users can configure the way a response frame is treated among other user traffic stored in network queues; the configuration options are high-priority, low-priority, or dot1p, where dot1p applies only to physical ring ports
- for network egress, where profiled scheduling is enabled, the following conditions apply:
- high-priority: either cir = port_speed, which applies to all frames that are scheduled via an in-profile scheduler; or round-robin (RR) for all other (network egress queue) frames that are in-profile
- low-priority: either cir = 0, pir = port_speed, which applies to all frames that are scheduled as out-of-profile, or RR for all other frames that are out-of-profile
- for network egress or access egress, where 4-priority scheduling is enabled:
- high-priority: either cir = port_speed, which applies to all frames that are scheduled via an expedited in-profile scheduler, or RR for all other (network egress queue) frames that reside in expedited queues and are in an in-profile state
- low-priority: either cir = 0, pir = port_speed, which applies to all frames that are scheduled via a best effort out-of-profile scheduler, or RR for all other frames that reside in best-effort queues and are in an out-of-profile state
- for the 6-port Ethernet 10Gbps Adapter card, 8-port Gigabit Ethernet Adapter card, the 10-port 1GigE/1-port 10GigE X-Adapter card, and the v-port on the 2-port 10GigE (Ethernet) Adapter card/module, for network egress, where 16-priority scheduling is enabled:
- high-priority: has higher priority than any user frames
- low-priority: has lower priority than any user frames
- for the physical ring ports on the 2-port 10GigE (Ethernet) Adapter card/module, which can only operate as network egress, the priority of the LBR frame is derived from the dot1p setting of the received LBM frame. Based on the assigned ring-type network queue policy, dot1p-to-queue mapping is handled using the same mapping rule that applies to all other user frames.
- the above queue parameters and scheduler mappings are all preconfigured and cannot be altered. The desired QoS treatment is selected by enabling the CFM loopback and specifying high-priority, low-priority, or dot1p.
3.1.11. OAM Propagation to Attachment Circuits
Typically, T1/E1 equipment at a site relies on the physical availability of the T1/E1 ports to determine the uplink capacity (that is, for ATM IMA or MLPPP groups). When a failure in the access link between the 7705 SAR and the associated T1/E1 equipment is detected, notification of the failure is propagated by the PW status signaling using one of two methods — label withdrawal or TLV (see LDP Status Signaling). In addition, the PW failure must also be propagated to the devices attached to the T1/E1 equipment. The propagation method depends on the type of port used by the access circuit (ATM, T1/E1 TDM, or Ethernet) and is described below.
3.1.11.1. ATM Ports
Propagation of ATM PW failures to the ATM port is achieved through the generation of AIS and RDI alarms.
3.1.11.2. T1/E1 TDM Ports
If a port on a 16-port T1/E1 ASAP Adapter card, 32-port T1/E1 ASAP Adapter card, or 2-port OC3/STM1 Channelized Adapter card is configured for CESoPSN VLL service, failure of the VLL forces a failure of the associated DS0s (timeslots). Since there can be n × DS0s bound to a CESoPSN VLL service as the attachment circuit, an alarm is propagated to the bound DS0s only. In order to emulate the failure, an “all 1s” or an “all 0s” signal is sent through the DS0s. The bit pattern can be configured to be either all 1s or all 0s. This is sometimes called “trunk conditioning”.
3.1.11.3. Ethernet Ports
For an Ethernet port-based Ethernet VLL, failure of the VLL forces a failure of the local Ethernet port. That is, the local attachment port is taken out of service at the physical layer and the Tx is turned off on the associated Ethernet port.
3.1.11.4. Pseudowire Status Signaling OAM Propagation
See the 7705 SAR Services Guide for more information about frame relay and HDLC PW status signaling and OAM propagation.
3.1.12. LDP Status Signaling
The failure of a local circuit needs to be propagated to the far-end PE, which then propagates the failure to its attached circuits. The 7705 SAR can propagate failures over the PW using one of the following methods:
- LDP status via label withdrawal
- LDP status via TLV
3.1.12.1. LDP Status via Label Withdrawal
Label withdrawal is negotiated during the PW status negotiation phase and needs to be supported by both the near-end and the far-end points. If the far end does not support label withdrawal, the 7705 SAR still withdraws the label in case the local attachment circuit is removed or shut down.
Label withdrawal occurs only when the attachment circuit is administratively shut down or deleted. If there is a failure of the attached circuit, the label withdrawal message is not generated.
When the local circuit is re-enabled after shutdown, the VLL must be re-established, which causes some delays and signaling overhead.
3.1.12.2. LDP Status via TLV
Signaling PW status via TLV is supported as per RFC 4447. Signaling PW status via TLV is advertised during the PW capabilities negotiation phase. It is more efficient and is preferred over the label withdrawal method.
For cell mode ATM PWs, when an AIS message is received from the local attachment circuit, the AIS message is propagated to the far-end PE unaltered and PW status TLV is not initiated.
3.1.13. IP Multicast Debugging Tools
This section describes multicast debugging tools for the 7705 SAR.
The debugging tools for multicast consist of three elements, which are accessed from the CLI <global> level:
3.1.13.1. Mtrace
Assessing problems in the distribution of IP multicast traffic can be difficult. The multicast traceroute (mtrace) feature uses a tracing feature implemented in multicast routers that is accessed via an extension to the IGMP protocol. The mtrace feature is used to print the path from the source to a receiver; it does this by passing a trace query hop-by-hop along the reverse path from the receiver to the source. At each hop, information such as the hop address, routing error conditions, and packet statistics are gathered and returned to the requester.
Data added by each hop includes:
- query arrival time
- incoming interface
- outgoing interface
- previous hop router address
- input packet count
- output packet count
- total packets for this source/group
- routing protocol
- TTL threshold
- forwarding/error code
The information enables the network administrator to determine:
- the flow of the multicast stream
- where multicast flows stop
When the trace response packet reaches the first-hop router (the router that is directly connected to the source’s network interface), that router sends the completed response to the response destination (receiver) address specified in the trace query.
If a multicast router along the path does not implement the mtrace feature or if there is an outage, then no response is returned. To solve this problem, the trace query includes a maximum hop count field to limit the number of hops traced before the response is returned. This allows a partial path to be traced.
The reports inserted by each router contain not only the address of the hop, but also the TTL required to forward the packets and flags to indicate routing errors, plus counts of the total number of packets on the incoming and outgoing interfaces and those forwarded for the specified group. Examining the differences in these counts for two separate traces and comparing the output packet counts from one hop with the input packet counts of the next hop allows the calculation of packet rate and packet loss statistics for each hop to isolate congestion problems.
3.1.13.1.1. Finding the Last-Hop Router
The trace query must be sent to the multicast router that is the last hop on the path from the source to the receiver. If the receiver is on the local subnet (as determined by the subnet mask), then the default method is to send the trace query to all-routers.mcast.net (224.0.0.2) with a TTL of 1. Otherwise, the trace query is sent to the group address since the last-hop router will be a member of that group if the receiver is. Therefore, it is necessary to specify a group that the intended receiver has joined. This multicast query is sent with a default TTL of 64, which may not be sufficient for all cases.
When tracing from a multihomed host or router, the default receiver address may not be the desired interface for the path from the source. In that case, the desired interface should be specified explicitly as the receiver.
3.1.13.1.2. Directing the Response
By default, mtrace first attempts to trace the full reverse path, unless the number of hops to trace is explicitly set with the hop option. If there is no response within a 3-s timeout interval, a “*” is displayed and the probing switches to hop-by-hop mode. Trace queries are issued starting with a maximum hop count of one and increasing by one until the full path is traced or no response is received. At each hop, multiple probes are sent. The first attempt is made with the unicast address of the host running mtrace as the destination for the response. Since the unicast route may be blocked, the remainder of attempts request that the response be sent to mtrace.mcast.net (224.0.1.32) with the TTL set to 32 more than what is needed to pass the thresholds seen so far along the path to the receiver. For the last attempts, the TTL is increased by another 32.
Alternatively, the TTL may be set explicitly with the TTL option.
For each attempt, if no response is received within the timeout, a “*” is displayed. After the specified number of attempts have failed, mtrace will try to query the next-hop router with a DVMRP_ASK_NEIGHBORS2 request (as used by the mrinfo feature) to determine the router type.
The output of mtrace is a short listing of the hops in the order they are queried, that is, in the reverse of the order from the source to the receiver. For each hop, a line is displayed showing:
- the hop number (counted negatively to indicate that this is the reverse path)
- the multicast routing protocol
- the threshold required to forward data (to the previous hop in the listing as indicated by the up-arrow character)
- the cumulative delay for the query to reach that hop (valid only if the clocks are synchronized)
The response ends with a line showing the round-trip time which measures the interval from when the query is issued until the response is received, both derived from the local system clock.
Mtrace/mstat packets use special IGMP packets with IGMP type codes of 0x1E and 0x1F.
3.1.13.2. Mstat
The mstat feature adds the capability to show the multicast path in a limited graphic display and indicates drops, duplicates, TTLs, and delays at each node. This information is useful to the network operator because it identifies nodes with high drop and duplicate counts. Duplicate counts are shown as negative drops.
The output of mstat provides a limited pictorial view of the path in the forward direction with data flow indicated by arrows pointing downward and the query path indicated by arrows pointing upward. For each hop, both the entry and exit addresses of the router are shown if different, along with the initial TTL required on the packet in order to be forwarded at this hop and the propagation delay across the hop assuming that the routers at both ends have synchronized clocks. The output consists of two columns, one for the overall multicast packet rate that does not contain lost/sent packets and the other for the (S,G)-specific case. The (S,G) statistics also do not contain lost/sent packets.
3.1.13.3. Mrinfo
The mrinfo feature is a simple mechanism to display the configuration information from the target multicast router. The type of information displayed includes the multicast capabilities of the router, code version, metrics, TTL thresholds, protocols, and status. This information can be used by network operators, for example, to verify if bidirectional adjacencies exist. Once the specified multicast router responds, the configuration is displayed.
3.2. Service Assurance Agent Overview
Broadband service delivery technologies have enabled the introduction of broadband service termination applications such as Voice over IP (VoIP), TV service delivery, and video and high-speed Internet services. These new applications force carriers to produce services where the health and quality of Service Level Agreement (SLA) commitments are verifiable, both to the customer and internally (within the carrier).
SAA is a feature that monitors network operations using statistics for parameters such as latency, jitter, response time, and packet loss. The information can be used to troubleshoot network problems and help in problem prevention and network topology planning. The 7705 SAR also supports the following SAA Ethernet CFM tests: loopback, linktrace, two-way delay measurement, and two-way SLM.
The results are saved in SNMP tables that are queried by either the CLI or a management system. Threshold monitors allow for both rising and falling threshold events to alert the provider if SLA performance statistics deviate from the required parameters. SAA CFM tests can be saved to accounting files that can be accessed by the network management system.
SAA allows two-way timing for several applications. This provides carriers and their customers with data to verify that the SLA agreements are being properly enforced. For SAA ICMP ping, one-way timestamping can be enabled at the system level for all outbound SAA ICMP ping packets.
3.2.1. Traceroute Implementation
For various applications, such as LSP traceroute, packets must pass through the network processor while on their way to the control CPU. When the packets exit the control CPU in the egress direction, the network processor inserts a timestamp inside each packet. Only packets processed by the control CPU will receive a timestamp.
When interpreting these timestamps, care must be taken because some nodes are not capable of providing timestamps, as such timestamps must be associated with the same IP address that is being returned to the originator to indicate which hop is being measured.
3.2.2. SAA Jitter
Mobile operators require millisecond-level granularity when it comes to delay and jitter measurements. This is especially true for synchronization-over-packet based applications.
Two-way jitter tests measure the jitter in each direction separately. The 7705 SAR provides two-way jitter tests with millisecond granularity for all network deployment applications.
3.2.3. SAA Ethernet CFM Test Support
CFM loopback, linktrace, and two-way delay measurement tests (ETH-DM) can be initiated using SAA. Additional timestamping is required for loopback and linktrace tests. An organization-specific TLV is used on both sender and receiver nodes to carry the timestamp information. Currently, timestamps are only applied by the sender node. This means that any time measurements resulting from the loopback and linktrace tests include the packet processing time used by the remote node. Because ETH-DM uses a four timestamp approach to remove the remote processing time, it should be used for accurate delay measurements.
The SAA versions of the CFM loopback, linktrace, and ETH-DM tests support send-count, interval, timeout, and FC. The summary of the test results are stored in an SAA accounting file.
The 7705 SAR now supports SAA-triggered ETH-DM tests for both Y.1731 and 802.1ag SAP MEPs. In previous releases, these tests were only supported for Y.1731 MEPs. The tests are supported on SAP Up and SAP Down Y.1731 and 802.1ag MEPs.
3.2.3.1. Writing SAA Ethernet CFM Test Results to Accounting Files
When each SAA CFM test is completed, the 7705 SAR collects the results in an accounting file that can be accessed by the network management system. In order to write the SAA test results to an accounting file in a compressed XML format, the results must be collected and entered in the appropriate MIB table, and a record must be generated in the appropriate accounting file.
Refer to the 7705 SAR System Management Guide, “Configuring an Accounting Policy” section, for information about creating accounting files and writing to them.
Once an accounting file has been created, accounting information can be specified and collected under the config>log>acct-policy>to file log-file-id context.
3.3. Configuring SAA Test Parameters
Use the following CLI syntax to create an SAA test and set test parameters:
The following example displays the SAA test configuration output:
The following example displays the result after running the test:
3.4. Synthetic Loss Measurement (SLM)
SLM is a single-ended test that can be run on demand or proactively to determine in-loss, out-loss, and unacknowledged packets. The test uses a small amount of synthetic test traffic as a substitute for customer traffic. SLM is used between peer MEPs in point-to-point configurations. Only remote peer MEPs within the association and matching the unicast destination will respond to the SLM packet. SLM uses an optional TLV with a timestamp on the near-end and far-end MEPs for the combined loss and delay measurement.
Various sequence numbers and counters are used to determine loss in each direction. In order to properly use the information that is gathered, the following terms are defined:
- count — number of probes that are sent if the last frame is not lost. If the last frame is lost, the count plus the number of unacknowledged packets equals the number of probes sent.
- out-loss (far end) — packets lost on the way to the remote node from the test initiator
- in-loss (near end) — packets lost on the way back from the remote node to the test initiator
- unacknowledged — number of packets not responded to by the end of the test
An SLM test packet can be generated using the CLI or SNMP for an on-demand test and SAA for a proactive test.The on-demand test provides per-probe-specific loss indicators or individual probe information stored in the MIB. The test does not store data for later processing. An SAA scheduled or continuous test summarizes the per-probe data but does not maintain per-probe information, and any unacknowledged packets are recorded as in-loss packets.
SLM packets originate and terminate on the CSM card. The probe count for SLM has a configurable range of 1 to 100 with probe spacing between 1 s and 10 s. A single test therefore can be up to 1000 s in length. A node may only initiate and maintain a single active on-demand test at any given time. The results table maintains a maximum of one storage entry per remote MEP. Subsequent tests on the same peer overwrite the results for that peer. For this reason, operators should run the on-demand test and check the results before starting another test.
Proactive measurement functions are linked to SAA and provide scheduling, storage, and summarization capabilities. Scheduling can be continuous or periodic. Proactive measurement also allows for the interpretation and representation of data that may enhance the specification. As an example, an optional TLV allows for the measurement of both loss and delay/ jitter with a single test. The optional TLV is ignored by equipment that does not support it. In mixed-vendor environments, loss measurement is tracked but delay and jitter only report round-trip times.
The round-trip times in mixed-vendor environments include the remote node’s processing time because only two timestamps are included in the packet. In an environment where both nodes support the optional TLV to include timestamps, unidirectional and round-trip times are reported. Since all four timestamps are included in the packet, the round-trip time in this case does not include remote node processing time.
The ETH-SL packet format contains a test-id that is internally generated and not configurable. The display summary for the on-demand test shows the test-id. A remote node processing the SLM frames could receive overlapping test-ids due to multiple MEPs measuring the loss at the same remote MEP. For this reason, the uniqueness of the test is based on the remote MEP-ID, test-id, and source MAC address of the packet.
All Ethernet adapter cards and ports in access mode support SLM Down and Up MEPs, and all Ethernet adapter cards and ports in network mode that support spoke SDPs support SLM Down MEPs. SLM Down MEPs are also supported on Ethernet network interfaces. There is no coordination between various fault conditions that could impact loss measurement. This is also true for conditions where MEPs are placed in a shutdown state as a result of linkage to a redundancy scheme such as MC-LAG.
It is possible to have a valid configuration where multiple MEPs on the same remote node have the same MAC address. If this is the case, the first responder is used to measure packet loss. The second responder is dropped.
A configurable inactivity timer determines the length of time that an on-demand test is valid. The test is active as long as packets are received within the timeframe set by the inactivity timer, as defined by the test-id, remote MEP ID, and source MAC address. If there is a gap between the packets that exceeds the inactivity timer value, the responding node responds with a sequence number of 1. For the remote MEP, the previous test has expired and any new probes are now part of a new test. The inactivity timer default is 100 s with a range of 10 to 100 s.
The responding node is limited to 1000 concurrent SLM tests. A node that is already actively processing 1000 SLM tests will show as out-loss or unacknowledged packets on the node that initiated the test because the packets will be silently discarded at the responder. No log entries or alarms will be raised. These packets are ETH-CFM-based and the stated receive rate for ETH-CFM must not be exceeded for the platform.
Only the configuration is supported by the high availability function. There is no synchronization of data between active and standby. Any unwritten or active tests are lost during a switchover and the data cannot be recovered.
3.4.1. Configuration Example
Figure 19 shows the configuration required for a proactive SLM test using SAA.
Figure 19: SLM Example
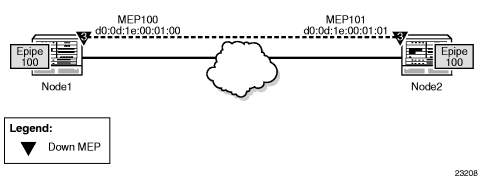
Node1 is tested for this example. The SAA configuration does not include the accounting policy required to collect the statistics before they are overwritten. Node2 does not have an SAA configuration. Node2 includes the configuration to build the MEP in the Epipe service context.
The following example displays the Node1 SAA test configuration:
The following example displays the Node2 configuration:
The following output example shows the different loss conditions that an operator may see. The total number of attempts is ‘99” because the final probe in the test was not acknowledged.
The following is an example of an on-demand test and the associated output. Only single test runs are stored and can be viewed after the fact.
3.5. OAM Timestamping
The following tables provide information on OAM timestamping for OAM tests.
Table 8 lists the locations where each type of OAM timestamping can occur.
Table 8: Location of OAM Timestamping
Timestamping Type | Timestamp Location | |
Tx | Rx | |
A | At the edge after enqueue | At the edge before enqueue |
B | Before enqueuing | At the edge before enqueue |
C | CSM timestamping | |
Table 9 lists the mapping of OAM tests to timestamping.
Table 9: Mapping of OAM Tests to Timestamping
Test Execution | Test | OAM Type | MEP and Direction | Timestamping Type |
SAA | eth-cfm | Loopback | SAP Down MEP | A |
SAA | eth-cfm | Loopback | SAP Up MEP | A |
SAA | eth-cfm | Loopback | Spoke-SDP Down MEP | A |
SAA | eth-cfm | Loopback | Network interface Down MEP | A |
SAA | eth-cfm | Linktrace | SAP Down MEP | A |
SAA | eth-cfm | Linktrace | SAP Up MEP | A |
SAA | eth-cfm | Linktrace | Spoke-SDP Down MEP | A |
SAA | eth-cfm | Linktrace | Network interface Down MEP | A |
SAA | eth-cfm | SLM | SAP Down MEP | A |
SAA | eth-cfm | SLM | SAP Up MEP | A |
SAA | eth-cfm | SLM | Spoke-SDP Down MEP | A |
SAA | eth-cfm | SLM | Network interface Down MEP | A |
SAA | eth-cfm | DM | SAP Down MEP | A |
SAA | eth-cfm | DM | SAP Up MEP | B |
SAA | eth-cfm | DM | Network interface Down MEP | A |
SAA | lsp-ping | — | — | A |
SAA | vccv-ping | — | — | A |
SAA | sdp-ping | — | — | A |
SAA | vprn-ping | — | — | A |
SAA | mac-ping | — | — | A |
SAA | icmp-ping | — | — | C |
SAA | cpe-ping | — | — | A |
On demand | eth-cfm | DM | SAP Down MEP | A |
On demand | eth-cfm | DM | SAP Up MEP | B |
On demand | eth-cfm | DM | Network interface Down MEP | A |
On demand | eth-cfm | 1DM | SAP Down MEP | B |
On demand | eth-cfm | 1DM | SAP Up MEP | A |
On demand | eth-cfm | 1DM | Network interface Down MEP | B |
On demand | twamp/twamp-light | — | Ethernet ports | A |
On demand | twamp/twamp-light | — | Non-Ethernet ports | C |
On demand | lsp-ping | — | — | A |
On demand | vccv-ping | — | — | A |
On demand | sdp-ping | — | — | A |
On demand | vprn-ping | — | — | A |
On demand | mac-ping | — | — | A |
Table 10 lists the timestamps per OAM test.
Table 10: Timestamps per OAM Test
Type | Test | Line Card Timestamp | Timestamp | |||
T1 1 | T2 2 | T3 3 | T4 4 | |||
CFM | loopback | ✓ | ✓ | — | — | ✓ |
linktrace | ✓ | ✓ | — | — | ✓ | |
slm | ✓ | ✓ | ✓ | ✓ | ✓ | |
two-way-delay | ✓ | ✓ | ✓ | ✓ | ✓ | |
Others | lsp-ping | ✓ | ✓ | ✓ | — | ✓ |
vccv-ping | ✓ | ✓ | ✓ | — | ✓ | |
sdp-ping | ✓ | ✓ | ✓ | ✓ | ✓ | |
vprn-ping | ✓ | ✓ | ✓ | ✓ | ✓ | |
mac-ping | ✓ | ✓ | ✓ | ✓ | ✓ | |
icmp-ping (with enable icmp-vse) | ✓ | ✓ | T2 = T3 | T3 = T2 | ✓ | |
- At the Tx of the initiator or test head
- At the Rx of the responder
- At the Tx of the responder
- At the Rx of the initiator or test head
Notes: