5. Filter Policies
This chapter provides information about filter policies and management.
Topics in this chapter include:
5.1. Configuring Filter Policies
Topics in this section include:
5.1.1. Overview of Filter Policies
Filter policies (or filters), also referred to as Access Control Lists (ACLs), are sets of rules that can be applied to network interfaces and services (VLL (Ethernet and IP), VPLS, VPRN and IES, and IES in-band management). Filter policies constrain network or user traffic based on match criteria and determine the action that will be invoked against the subject packet (that is, the default action can be either “drop” or “forward”).
The 7705 SAR supports five types of filter policies:
- IP filters
- MAC filters
- VLAN filters
- CSM filters
- IP exception filters
The 7705 SAR also supports policy-based routing (PBR), which is based on IP filters, and multi-field classification (MFC).
IP, MAC, and VLAN filters scan all traffic and take the appropriate (configured) action against matching packets. Packets that are not filtered by one of these filters and are destined for the 7705 SAR are then scanned by the CSM filter, if configured.
IP exception filters scan all outbound traffic entering a Network Group Encryption (NGE) domain and allow packets that match the exception filter criteria to transit the NGE domain unencrypted.
IP and MAC filter support for SAP and SDP is described in the following sections and is summarized in Table 67 and Table 68. Ingress filter override support for routed VPLS on IES and VPRN services is summarized in Table 69. IPv4 and IPv6 filter support (ingress and egress) for network interfaces is described in the lists following Table 69. MAC filters do not support network interfaces.
Configuring an entity for a filter policy is optional. If a network or service interface is not configured with filter policies, all traffic is allowed on the interface. By default, there are no filters associated with interfaces or services. The filters must be explicitly created and associated. When you create a new filter, you must specify a unique filter ID value for each new filter policy, as well as each new filter entry and associated actions. The filter entries specify the filter matching criteria. See Filter Policy Entries. After creating a filter policy you can also, optionally, assign filters a unique name. Filter IDs or filter names can be used throughout the system to manage filter policies and assign them to interfaces.
Table 67: IP and MAC Filter Support on SAPs
Service SAP | Ingress Filter | Egress Filter | ||||
IPv4 | IPv6 | MAC | IPv4 | IPv6 | MAC | |
Epipe | Yes | No | No | No | No | No |
IES | Yes | Yes | No | Yes | Yes | No |
Ipipe | Yes | No | No | No | No | No |
VPLS | Yes | Yes | Yes | Yes | Yes | No |
VPRN | Yes | Yes | No | Yes | Yes | No |
Table 68: IP and MAC Filter Support on SDPs
Service SDP | Ingress Filter | Egress Filter | ||||
IPv4 | IPv6 | MAC | IPv4 | IPv6 | MAC | |
Epipe | No | No | No | No | No | No |
IES | Yes | No | No | No | No | No |
Ipipe | No | No | No | No | No | No |
VPLS | Yes | Yes | Yes | No | No | No |
VPRN | Yes | Yes | No | No | No | No |
Table 69: Routed VPLS Ingress Filter Override Support
Service | Ingress Override IPv4 | Ingress Override IPv6 |
IES | Yes | Yes |
VPRN | Yes | Yes |
IP Filters
IPv4 filters can be applied to the following entities:
- network interfaces
- ingress and egress network interfaces, affecting incoming traffic from the network link and outgoing traffic to the network link
- SAPs
- ingress IES management SAPs, affecting incoming node management traffic
- ingress pseudowire SAPs (Epipe and Ipipe), affecting incoming user traffic
- ingress VPLS SAPs, affecting incoming user traffic
- ingress VPRN SAPs and IES SAPs, affecting incoming user traffic
- egress VPLS SAPs (Ethernet SAPs only), affecting outgoing user traffic
- egress VPRN and IES SAPs, affecting outgoing user traffic
- SDPs
- ingress VPLS SDPs (spoke and mesh), affecting incoming traffic from the remote end of the service
- ingress IES and VPRN interface spoke SDPs, affecting incoming traffic from the remote end of the service
Ingress filters affect only incoming packets regardless of whether the packets need to be forwarded to a downstream router or are destined for the 7705 SAR.
IPv6 filters can be applied to the following entities:
- network interfaces
- ingress and egress Ethernet network interfaces (with null or dot1q encapsulation)
- ingress and egress network interfaces on the 4-port OC3/STM1 Clear Channel Adapter card (with POS encapsulation)
- SAPs
- ingress IES SAPs
- ingress and egress VPLS SAPs
- ingress and egress VPRN SAPs
- SDPs
- ingress VPLS SDPs (spoke and mesh), affecting incoming traffic from the remote end of the service
- ingress VPRN interface spoke SDPs, affecting incoming traffic from the remote end of the service
MAC Filters
MAC filters can be applied to the following entities:
- SAPs
- ingress VPLS SAPs, affecting incoming user traffic
- SDPs
- ingress VPLS SDPs (spoke and mesh), affecting outgoing user traffic
VLAN Filters
VLAN filters can be applied to ring ports at the ingress point on the 2-port 10GigE (Ethernet) Adapter card and 2-port 10GigE (Ethernet) module. VLAN filters are blocked on all other adapter cards and modules.
CSM Filters
The 7705 SAR supports IPv4 and IPv6 CSM filters. For information on CSM filters, refer to the 7705 SAR System Management Guide, “CSM Filters and CSM Security”.
IP Exception Filters
The 7705 SAR supports IPv4 exception filters. For information on IP exception filters, refer to the 7705 SAR Services Guide, “Router Encryption Exceptions using ACLs”.
5.1.2. Network and Service (Access) Interface-based Filtering
IP and MAC filter policies specify either a forward or a drop action for packets, based on information specified in the match criteria. Within each filter policy, you can create entries that define matching criteria.
The same IP filter policy can be assigned to any entity (network interfaces, IP pseudowires, Ethernet pseudowires, VPLS services, VPRN services, and IES services), all of which can be configured on the same adapter card. For example, a filter policy with filter-id defined as filter-5 can be assigned to multiple Ipipe SAPs and, simultaneously, to network interfaces on the same adapter card.
A filter policy assigned to an entity on one adapter card can also be assigned to any entity on another adapter card. For example, a filter policy with filter-id defined as filter-2 can be assigned to an Epipe on an Ethernet Adapter card and to a network interface on another Ethernet Adapter card.
Only one type of filter (IP or MAC) can be assigned to an interface at a time, and only one filter of that type can be assigned to an interface at a time. The exception is a dual-stack interface (one that supports both IPv4 and IPv6); the interface can have both an IPv4 and an IPv6 filter assigned to it.
Both IP and MAC filter policies are supported per adapter card, and assigning the same filter policy to different entities on a card counts as using one filter policy.
Filter entry matching criteria can be as general or specific as required, but all conditions in the entry must be met in order for the packet to be considered a match and the specified entry action performed. The process stops when the first complete match is found and the action defined in the entry is executed (that is, packets that match the criteria are either dropped or forwarded).
Configuration and assignment of IP and MAC filter policies is similar for network interfaces, IES management SAPs, Ethernet and IP pseudowire SAPs, VPRN and IES interface SAPs and spoke SDPs, and VPLS SAPs and SDPs (spoke and mesh). This guide describes the assignment of filter policies to network interfaces. For detailed information on assigning filters to a service, refer to the 7705 SAR Services Guide; see “IP Filters” (under “Ethernet VLL (Epipe) Services” and “IP Interworking VLL (Ipipe) Services”) for information on assigning IP filter policies to SAPs and spoke SDPs, and see “MAC Filters” (under VPLS Features), for information on assigning MAC filter policies to VPLS SAPs and SDPs.
5.1.3. Policy-Based Routing
Traditionally, IP routing is done by making routing decisions based on the destination IP address of the incoming packet. PBR expands the routing decision from one based solely on the destination IP address to include any other IP criteria, such as source IP address, DSCP, or source/destination UDP/TCP port.
Using PBR at the iLER node provides filtering needed to route IP traffic over multiple uplink interfaces or tunnels using IP criteria. For example, a service provider can use PBR to separate high-value traffic (signaling) from user data by examining the source IP address and/or DSCP bits of the incoming IP packets, and assign a separate transport tunnel to each traffic flow. The transport tunnels could be engineered by using RSVP-TE throughout the entire mobile backhaul network with specific reservation values. The LSP is signaled throughout the network and reserves the needed resources at each node, ensuring the QoS for the high-value traffic.
PBR can also be used to extract packets from the data path and send them to the CSM for debugging or slow path forwarding.
Figure 12 illustrates a PBR implementation for VPRN services in an LTE network, and includes CLI command syntax. The 7705 SAR-8 at the cell site makes routing decisions based on the incoming packet DSCP only, as follows:
- BE packets are forwarded to 7750 SR_1 over SDP1
- AF11 packets are forwarded to 7750 SR_2 over SDP2
- each SDP (SDP1 and SDP2) is signaled throughout the network using RSVP-TE protocol with its own separate TE criteria
Figure 12: PBR Filtering Based on the DSCP of Incoming Packets

PBR is supported at ingress for the following services and interfaces:
- IES and VPRN service
- SAP
- Layer 3 spoke SDP
- routed VPLS
- router network interface (Global Routing Table (GRT))
| Note: A PBR filter action can be assigned to an Epipe or Ipipe, or to VPLS (SAP, spoke SDP, or mesh SDP); however, the PBR action is ignored (not performed). |
PBR is supported on the private IPSec service (VPRN). For more information on IPSec and PBR, refer to the “PBR” section in the 7705 SAR Services Guide.
5.1.4. Multi-field Classification (MFC)
Multi-field classification (MFC) allows untrusted traffic arriving on the access ports of the 7705 SAR to be reclassified and queued according to a forwarding class assigned to the traffic.
Traffic is classified based on IP criteria. Arriving traffic has an ACL (also known as filter policies) applied to it. If the ACL action is forward fc, a match results in the assignment of the corresponding configured Forwarding Class (FC). This FC is used for queuing of the packet through the 7705 SAR. The match can be based on any IP criteria currently supported by the 7705 SAR IP filter policies.
When MFC is configured and a match is made on an arriving packet, the FC is based only on the MFC configuration. The access ingress policy is no longer active for this packet.
Both PBR and MFC are configured under the IP filter configuration and the action of the filter policy can include both PBR (next-hop ip-address) and MFC (fc fc-name).
If MFC is assigned to a Layer 3 spoke-SDP termination interface, MFC classification is based on the traffic’s customer-assigned inner IP packet. The filter policy rules are applied to the IP criteria of the inner packet after the VC label and transport tunnel label have been removed from the packet. Based on the matching criteria, the appropriate FC is assigned to the packet. This functionality allows the customer packet to be marked with the correct DSCP before it egresses the 7705 SAR. This applies only to an untrusted SAP configuration that has a SAP egress QoS policy assigned to it.
MFC is supported at ingress for the following services and interfaces:
- IES and VPRN service
- SAP
- Layer 3 spoke SDP
- routed VPLS
- router network interface (Global Routing Table (GRT))
- VLLs
- Epipe
- Ipipe
- VPLS
- SAP
- spoke or mesh SDP
Multi-field classification (MFC) is also supported on the private IPSec service (VPRN). MFC functions in the same manner as the VPRN configuration of traditional services.
5.1.5. VLAN-based Filtering
VLAN filter policies specify either a forward or a drop action for packets, based on VLAN ID information specified in the policy match criteria.
Only one VLAN filter is allowed per ring port on the 2-port 10GigE (Ethernet) Adapter card or 2-port 10GigE (Ethernet) module. The same VLAN filter can be applied to both ring ports. Each VLAN filter supports up to 64 matching criteria entries. The filter acts on ingress traffic and the forwarding action sends packets to the other ring port or to the v-port, depending on the packet’s destination.
The number of VLAN filters that can be created depends on the memory available on the 2-port 10GigE (Ethernet) Adapter card or 2-port 10GigE (Ethernet) module.
The 7705 SAR does not support filter logging or statistics collection for VLAN filters.
5.1.6. Filter Policy Entries
Topics in this section include:
A filter policy compares the match criteria specified within a filter entry to packets coming into the system, in the order the entries are numbered in the policy. When a packet matches all the parameters specified in the entry, the system takes the specified action to either drop or forward the packet. If a packet does not match the entry parameters, the packet continues through the filter process and is compared to the next filter entry, and so on.
If the packet does not match any of the entries, the system executes the default action specified in the filter policy, which is to either drop or forward the packet. Each filter policy is assigned a unique filter ID. Each filter policy is defined with:
- scope (exclusive or template) (except VLAN filter policies, which always have a template scope)
- default action (drop or forward)
- description
- at least one filter entry
Each filter entry contains:
- match criteria
- an action
5.1.6.1. Applying Filter Policies
IPv4 filter policies can be applied at:
- network interfaces
- ingress and egress of network IP interfaces
- SAPs
- ingress of Ethernet and IP pseudowire SAPs (Epipe and Ipipe), VPLS SAPs, VPRN SAPs, and IES SAPs
- ingress of IES in-band management SAPs
- egress of VPRN and IES SAPs
- egress of VPLS SAPs (Ethernet only)
- SDPs
- ingress of VPLS SDPs (spoke and mesh)
- ingress of VPRN and IES spoke SDPs
IPv6 filters can be applied at:
- network interfaces
- ingress and egress of Ethernet network interfaces (with null or dot1q encapsulation)
- ingress and egress of network interfaces on the 4-port OC3/STM1 Clear Channel Adapter card (with POS encapsulation)
- SAPs
- ingress and egress of IES SAPs
- ingress and egress of VPRN SAPs
- ingress and egress of VPLS SAPs
- SDPs
- ingress of VPRN spoke SDPs
- ingress of VPLS SDPs
MAC filter policies can be applied at the ingress of VPLS SAPs (Ethernet, and ATM on clear channel OC3 adapter cards) and SDPs (spoke and mesh).
VLAN filters can only be applied to ring ports on the 2-port 10GigE (Ethernet) Adapter card and 2-port 10GigE (Ethernet) module.
| Note: By default, all created filters have a default action of drop (implicit drop). That is, if none of the entries in the filter match the packet, and a default action is not explicitly configured by the user, the packet is dropped. |
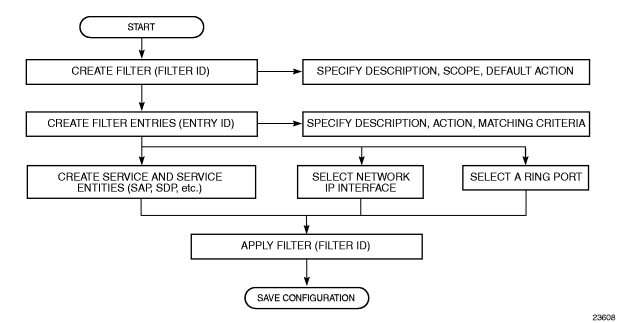
Figure 13 shows the process to create filter policies and apply them to a network interface.
Figure 13: Creating and Applying Filter Policies
5.1.6.2. Packet Matching Criteria
IPv4 filter entries can specify one or more matching criteria, with one caveat. In order to support the maximum 256 entries for IPv4 filters, any entry that uses source port (src-port) and/or destination port (dst-port) ranges (lt, gt, or range keywords) as match criteria must be within the first 64 entries.
For IPv6 filters, the combined number of fields for all entries in a filter must not exceed 16 fields (or 256 bits), where a field contains the bit representation of the matching criteria.
All conditions must be met in order for the packet to be considered a match and the specified action performed. The process stops when the first complete match is found and the action defined in the entry is executed (that is, packets that match the criteria are either dropped or forwarded). If no match is found, the default action is to drop the packet.
Matching criteria for IP filters, MAC filters, and VLAN filters are described in Table 70, Table 71, and Table 72, respectively.
IP Filter Matching Criteria
IPv4 and IPv6 filter policies compare the matching criteria to traffic at a network interface. Matching criteria to drop or forward IP traffic are described in Table 70.
Table 70: IP Filter Policy Criteria
Criteria | Description |
Protocol identifier/next header | For IPv4, entering a protocol identifier allows the filter to match the IP protocol. Common protocol numbers include ICMP(1), TCP(6), and UDP(17). For a full list of protocol numbers, see the config>filter>ip-filter>entry>match command in the Filter Command Reference. For IPv6, entering a next header allows the filter to match the first next header following the IPv6 header. |
DSCP name | Entering a DSP name allows the filter to match DiffServ Code Point (DSCP) names |
Destination IP address and mask | Entering a destination IP address and mask allows the filter to match destination IP address and mask values (for IPv4) and matching destination IP address and prefix length (for IPv6). The IPv4 address scheme consists of 32 bits expressed in dotted-decimal notation. The IPv6 address scheme consists of 128 bits expressed in colon-hexadecimal format. |
Destination port/range | Entering a destination port/range allows the filter to match TCP or UDP values |
Fragmentation | Entering a fragment allows the filter to match the fragmentation state of packets (fragmented or non-fragmented) (not applicable to IPv6) |
ICMP code | Entering an ICMP code allows the filter to match an ICMP code in the ICMP header |
ICMP type | Entering an ICMP type allows the filter to match an ICMP type in the ICMP header |
IP option | Entering an IP option allows the filter to match an option or range of options in the IP header (not applicable to IPv6) |
Multiple IP options | Entering multiple IP options allows the filter to match the state of multiple option fields in the IP header (true or false) (not applicable to IPv6) |
Option present | Entering option present allows the filter to match the state of the option field in the IP header (present or absent) (not applicable to IPv6) |
Source IP address and mask | Entering a source IP address and mask allows the filter to match a source IP address and mask values (for IPv4) or a source IP address and prefix length (for IPv6). The IPv4 address scheme consists of 32 bits expressed in dotted-decimal notation. The IPv6 address scheme consists of 128 bits expressed in colon-hexadecimal format. |
Source port/range | Entering a source port/range allows the filter to match a TCP or UDP port and range values |
TCP ACK | Entering TCP ACK allows the filter to match the state of the ACK bit set in the control bits of the TCP header of an IP packet (set or not set) |
TCP SYN | Entering a TCP SYN allows the filter to match the state of the SYN bit set in the control bits of the TCP header of an IP packet (set or not set) |
MAC Filter Matching Criteria
MAC filter policies compare the matching criteria to traffic at the ingress of a VPLS SAP or SDP (spoke or mesh). Matching criteria to drop or forward MAC traffic are described in Table 71.
Table 71: MAC Filter Policy Criteria
Criteria | Description |
Frame type | Entering the frame type allows the filter to match a specific type of frame format; for example, Ethernet-II will match only Ethernet-II frames |
Source MAC address | Entering the source MAC address allows the filter to search for a matching source MAC address. Enter the source MAC address in the form xx:xx:xx:xx:xx:xx or xx-xx-xx-xx-xx-xx; for example, 00:dc:98:1d:00:00. |
Destination MAC address | Entering the destination MAC address allows the filter to search for a matching destination MAC address. Enter the destination MAC address in the form xx:xx:xx:xx:xx:xx or xx-xx-xx-xx-xx-xx; for example, 02:dc:98:1d:00:01. |
Ethertype | Entering an Ethernet type II Ethertype value allows the value to be used as a filter match criterion. The Ethernet type field is a 2-byte field used to identify the protocol carried by the Ethernet frame. The Ethertype accepts decimal, hex, or binary in the range of 1536 to 65535. |
VLAN Filter Matching Criteria
VLAN filter policies compare the matching criteria to traffic at the ingress of a ring port on the 2-port 10GigE (Ethernet) Adapter card and 2-port 10GigE (Ethernet) module. Matching criteria to drop or forward traffic are described in Table 72.
Table 72: VLAN Filter Policy Criteria
Criteria | Description |
VLAN ID or VLAN range | Entering a VLAN identifier or range allows the filter to match VLAN ID values |
Untagged | Selecting untagged allows the filter to match on Ethernet frames with no tag or dot1q header. Having no tag or dot1q header is also referred to as null encapsulation. |
5.1.6.3. Ordering Filter Entries
When entries are created, they should be arranged sequentially from the most explicit entry to the least explicit. Filter matching ceases when a packet matches an entry. The entry action is performed on the packet, either drop or forward. To be considered a match, the packet must meet all the conditions defined in the entry.
Packets are compared to entries in a filter policy in ascending entry ID order. To reorder entries in a filter policy, for example, to reposition entry ID 6 as entry ID 2, use the renum command (renum 6 2).
When a filter policy consists of a single entry, the filter executes actions as follows.
- If a packet matches all the entry criteria, the entry’s specified action is performed (drop or forward).
- If a packet does not match all of the entry criteria, the policy’s default action is performed (drop or forward).
If a filter policy contains two or more entries, packets are compared in ascending entry ID order (for example, 1, 2, 3 or 10, 20, 30).
- Packets are compared with the criteria in the first entry ID.
- If a packet matches all the properties defined in the entry, the entry’s specified action is executed.
- If a packet does not completely match, the packet continues to the next entry, and then subsequent entries.
- If a packet does not completely match any subsequent entries, the default action is performed (drop or forward).

Note: By default, all created filters have a default action of drop (implicit drop). That is, if none of the entries in the filter match the packet, and a default action is not explicitly configured by the user, the packet is dropped.
Figure 14 displays an example of several packets forwarded upon matching the filter criteria and several packets traversing through the filter entries and then dropped.
Figure 14: Filtering Process Example

5.1.7. Filter Log Files
Filter entries can be configured to be written to a filter log file. The log file must exist before any entries can be logged. To create a log file, use the config>filter>log log-id create command. Filter logs can be sent to either memory or to an existing syslog server. See Filter Logs for more information.
The 7705 SAR supports filter logging for the following filters:
- ingress spoke SDP IPv4, IPv6, or MAC filters (VPLS only)
- ingress mesh SDP IPv4, IPv6, or MAC filters (VPLS only)
- ingress spoke SDP IPv4 or IPv6 filters (VPRN)
The 7705 SAR does not support filter logging for VLAN filters.
Refer to the 7705 SAR System Management Guide, “Syslog”, for information on syslogs.
5.2. Configuration Notes
The following information describes the conditions for filter policy implementation.
- Creating a filter policy is optional.
- Using a filter policy is optional.
- A filter policy must be created before it can be applied to a service.
- When a filter policy is configured, it must be defined as having either an exclusive scope (for use with one interface), or a template scope (meaning that the filter can be applied to multiple interfaces). VLAN filter policies always have a template scope.
- A specific filter must be explicitly associated with a specific interface in order for packets to be matched.
- Each filter policy must consist of at least one filter entry. Each entry represents a collection of filter match criteria. When packets enter an ingress port or SAP or SDP, or exit an egress SAP, the packets are compared to the criteria specified within the entry or entries.
- When you configure a large (complex) filter, it may take a few seconds to load the filter policy configuration.
- The action keyword must be entered for the entry to be active. Any filter entry without the action keyword is considered incomplete and will be inactive.
See the following sections for specific notes on:
5.2.1. IP Filters
- Define filter entry packet matching criteria — if a filter policy is created with an entry and an entry action specified, but the packet matching criteria is not defined, then all packets processed through this filter policy entry will pass and take the action specified. There are no default parameters defined for matching criteria.
- Action — an action keyword must be specified for the entry to be active. Any filter entry without an action keyword specified is considered incomplete and will be inactive.
5.2.2. IPv6 Filters
IPv6 packets with extension headers can be filtered with an IPv6 filter, but are subject to some restrictions:
- if the packet contains the Hop-by-Hop Options header, slow path extraction will occur and the packet will be processed by the CSM's CPM filter (if present); however, the main (fast path) IPv6 filter (service or network filter) will filter packets with the Hop-by-Hop Options header
- if the authentication header is present in the packet and the target fields for the filter are offset by the presence of the authentication header, the filter will not detect the target header fields and no filter action will occur
No alarms, logs, or statistics will be reported in the above cases.
5.2.3. MAC Filters
- If a MAC filter policy is created with an entry and entry action specified but the packet matching criteria is not defined, then all packets processed through this filter policy entry will pass and take the action specified. There are no default parameters defined for matching criteria.
- MAC filters cannot be applied to network interfaces, routable VPRN or IES services.
- Some of the MAC match criteria fields are exclusive to each other, based on the type of Ethernet frame. Use Table 73 to determine the exclusivity of fields.
Table 73: MAC Match Criteria Exclusivity Rules
Frame Format
Ethertype
Ethernet – II
Yes
802.3
No
802.3 – snap
No
5.2.4. VLAN Filters
- VLAN filters are applied to physical ring ports on the 2-port 10GigE (Ethernet) Adapter card and 2-port 10GigE (Ethernet) module. VLAN filters are exclusive to the ring adapter card and module.
- Only one VLAN filter is allowed per ingress ring port.
- The same VLAN filter can be applied to both ring ports.
- The forwarding action sends packets to the other ring port or to the v-port, depending on the packet’s destination.
- The 7705 SAR does not support filter logging or statistics collection for VLAN filters.
5.2.5. Filter Logs
- Summarization logging is the collection and summarization of log messages for one specific log ID within a period of time.
- The summarization interval is 100 s.
- The filter log can be applied to IP filters, MAC filters, or CPM filters.
- For VPLS scenarios, both Layer 2 and Layer 3 are applicable.
- Layer 2: source MAC or (optionally) destination MAC
- Layer 3: source IPv6 or (optionally) destination IPv6 for Layer 3 filters
- Upon activation of a fixed summarization interval, a mini-table with source/destination address and count is created for each filter type (IP, MAC, or CPM).
- Every received log packet is examined for the source or destination address.
- If the log packet (source/destination address) matches a source/destination address entry in the mini-table (meaning that a packet was received previously), the summary counter of the matching address is incremented.
5.2.6. Reference Sources
For information on supported IETF drafts and standards, as well as standard and proprietary MIBs, refer to Standards and Protocol Support.