8.5. Configuring IPSec with CLI
This section provides information to configure IPSec using the command line interface.
Topics in this section include:
8.6. Basic Configuration Overview
The following list provides a high-level outline for setting up IPSec on the 7705 SAR.
- Create an IPSec tunnel group.
- Configure an IPSec IKE policy.
- Configure an IPSec transform policy.
- Create a private side tunnel interface on the VPRN service.
- Create an interface using the tunnel keyword and private tunnel SAP.
- Create the IPSec tunnel and configure its parameters, which include local and peer gateway IP addresses, IP MTU, keying (manual or dynamic), and so on.
- Create a public side tunnel interface on the IES.
- Create an interface and public tunnel SAP.
- Configure a VPRN static route for the IPSec tunnel.
8.7. Common Configuration Tasks
This section provides a brief overview of the following common configuration tasks that must be performed to configure IPSec:
8.7.1. Configuring an IPSec Tunnel Group
The following output displays an IPSec group configuration in the ISA context. The 7705 SAR supports only one tunnel-group. The tunnel-group-id is always 1.
8.7.2. Configuring Router Interfaces for IPSec
An IPSec tunnel requires the following three interfaces:
- public tunnel interface (under IES)
- private tunnel interface (under VPRN)
- physical untrusted network/Internet-facing interface: either IES or router
The physical interface is the one that must reside on an encryption-capable adapter card.
The following example displays an interface (“internet”) configured using a network port (1/1/1) and an IES interface (“public”) configuration using SAP 1/1/8.
8.7.3. Configuring IPSec Parameters
Under the IPSec context, configure the IKE policy and IPSec transform parameters.
The following example displays the IPSec parameter configuration output.
8.7.4. Configuring IPSec and IPSec Tunnels in Services
IPSec is configured under IES and VPRN services.
Under VPRN service, configure IPSec security policies, and create tunnel interfaces, private tunnel SAPs, and IPSec tunnels along with setting the IPSec tunnel parameters. Use the tunnel keyword when creating an interface for a private tunnel SAP.
Under IES service, create an interface and public tunnel SAP. The tunnel keyword is not used when creating an interface for a public tunnel SAP.
Private and public tunnels function in pairs, where a pair is defined by the tag in the sap-id; for example, SAP tunnel-1.private:22 and SAP tunnel-1.public:22 are a pair.
The local gateway address and delivery service configured under the VPRN ipsec-tunnel>local-gateway-address command correspond to the IES interface address and service ID where the public tunnel interface is defined. In the example below, the local-gateway-address is 10.10.10.11 and the delivery-service is 10.
The following example displays the configuration output when configuring IPSec for VPRN services and for IES.
8.7.5. Configuring IPSec IPv6 Parameters for a VPRN Service
Use the following CLI syntax to configure IPSec IPv6 parameters for a VPRN service:
The following example displays IPSec IPv6 parameters configuration output.
8.7.6. Configuring X.509v3 Certificate Parameters
Perform the following steps to configure certificate enrollment.
- Generate a key:admin certificate gen-keypair cf3:/key_plain_rsa2048 size 2048 type rsa
- Generate a certificate request:admin certificate gen-local-cert-req keypair cf3:/key_plain_rsa2048 subject-dn "C=US,ST=CA,CN=7705" file 7705_req.csr
- Send the certificate request to CA-1 to sign and get the signed certificate.
- Import the key:admin certificate import type key input cf3:/key_plain_rsa2048 output key1_rsa2048 format der
- Import the signed certificate:admin certificate import type cert input cf3:/7705_cert.pem output 7705cert format pem
Perform the following steps to import the CA certificate and CRL.
- Import the CA certificate:admin certificate import type cert input cf3:/CA_1_cert.pem output ca_cert format pem
- Import the CA’s CRL:admin certificate import type crl input cf3:/CA_1_crl.pem output ca_crl format pem
The following example displays a certificate authentication for IKEv2 static LAN-to-LAN tunnel configuration.
The following example displays the syntax to import a certificate from the PEM format.
The following example displays the syntax to export a certificate to the PEM format.
8.7.7. Configuring CMPv2
CMPv2 server information is configured under a corresponding ca-profile by using the following CLI commands:
The url command specifies the HTTP URL of the CMPv2 server and the service-id specifies the routing instance that the system used to access the CMPv2 server (if the service ID is omitted, the system uses the base routing instance).
The service ID is only needed for in-band connections to the server via VPRN services. IES services are not referenced by the service ID, since an IES service routing instance is considered to be a base routing instance.
The response-signing-cert command specifies an imported certificate that is used to verify CMP response messages if they are protected by a signature. If this command is not configured, the CA’s certificate is used.
The key-list command specifies a list of pre-shared-keys used for CMPv2 initial registration message protection.
All CMPv2 operations are invoked by using the admin certificate cmpv2 command.
If there is no key-list defined under the cmpv2 configuration, the system defaults to the cmpv2 transaction that was input for the command line related to authenticating a message without a sender ID. If there is no sender ID in the response message and there is a key-list defined, the system chooses the lexicographical first entry only, and if that fails, there is a fail result for the transaction.
The system supports optional commands (such as always-set-sender-ir) to support inter-operation with CMPv2 servers. Refer to the IPSec Command Reference for details about syntax and usage.
8.7.8. Configuring OCSP
OCSP server information is configured under the corresponding ca-profile:
The responder-url command specifies the HTTP URL of the OCSP responder. The service command specifies the routing instance that the system used to access the OCSP responder.
For a given IPSec tunnel, the user can configure a primary method, a secondary method, and a default result.
8.8. Configuring IPSec over MPLS
On the 7705 SAR, IPSec routes to the secure gateway address can be resolved by using either a BGP 3107 label route or an IGP shortcut. When BGP learns IPv4 addressed as BGP 3107 label routes, BGP resolves the next hops for these routes with an LDP or RSVP-TE tunnel. These BGP routes create BGP tunnels that can be used to resolve an IPSec secure gateway address. When an IGP shortcut is enabled on the 7705 SAR by using the config>router>ospf>rsvp-shortcut command, OSPF installs an OSPF route in the RIB, with an RSVP-TE LSP as the next hop. If this OSPF route is determined as the overall best route, then the next hop is an RSVP-TE tunnel.
The IPSec implementation on the 7705 SAR is VPN-based. In order to configure IPSec, a private VPRN and a public IES must both be configured; the encryption and decryption functions occur between these two services.
This section shows a configuration example of an IPSec route resolved by a BGP 3107 label route and a configuration example of an IPSec route resolved by an IGP shortcut.
8.8.1. IPSec over BGP 3107 Label Route
To route IPSec traffic using BGP 3107 label routes, the following components must be configured:
- a static LAN-to-LAN tunnel for IPSec traffic
- a policy option to advertise the IPSec gateway using BGP
- BGP with a BGP 3107 label route configured
- an LDP or RSVP-TE tunnel to resolve the BGP 3107 label route
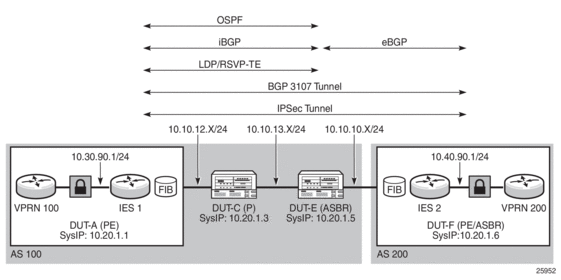
Figure 128 shows a scenario where IPSec traffic is routed over a BGP 3107 label route. In this example, both the BGP 3107 tunnel and the IPSec tunnel are set up between Dut-A and Dut-F. The nature of BGP 3107 requires the LDP or RSVP-TE tunnel to be set up inside the autonomous system between Dut-A and Dut-E.
Figure 128: IPSec over BGP 3107 Label Route
8.8.1.1. Static LAN-to-LAN Tunnel Configuration
Setting up a static LAN-to-LAN tunnel for IPSec traffic involves configuring a number of elements, including:
- VPRN service parameters, including the following: BGP parameters, route distinguisher parameter, auto-bind parameter or VPRN spoke SDP, VRF route-target associations or VRF import/export policies, OSPF parameters, a VPRN interface and its SAP parameters, and spoke-SDP parameters on the VPRN interface
- IES service parameters
- IPSec parameters
The CLI output below is an example of a static LAN-to-LAN tunnel configuration.
8.8.1.2. Policy Option Configuration
The CLI output below is an example of a policy option configuration.
8.8.1.3. BGP Configuration with BGP 3107 Label Route Advertisement
The CLI output below is an example of BGP enabled with label route advertisement.
8.8.1.4. LDP or RSVP-TE Tunnel Configuration
The CLI output below is an example of an LDP tunnel that is configured to resolve the next hop for the BGP 3107 label route. An RSVP-TE tunnel could also be configured to resolve the next hop.
8.8.2. IPSec over IGP Shortcut
To route IPSec traffic over an IGP shortcut, the following must be configured:
- a static LAN-to-LAN tunnel
- an IGP shortcut (by creating an RSVP-TE tunnel in the OSPF context)
- an RSVP-TE LSP to the system IP address or loopback address, with CSPF enabled
8.8.2.1. Static LAN-to-LAN Tunnel Configuration
The CLI output below is an example of a static LAN-to-LAN tunnel configuration.
8.8.2.2. IGP Shortcut Configuration
The CLI output below is an example of an IGP shortcut configuration. An IGP shortcut is created using the rsvp-shortcut command in the ospf context.
8.8.2.3. RSVP-TE LSP Configuration
The CLI output below is an example of an RSVP-TE LSP with CSPF enabled.
8.9. Service Management Tasks
This section provides a brief overview of the following service management tasks:
8.9.1. Deleting an IPSec IKE Policy or an IPSec Transform
An IPSec IKE policy or transform cannot be deleted if it is being used by an IPSec tunnel. To delete an IKE policy or IPSec transform:
8.9.2. Deleting a Public IPSec Tunnel SAP and Interface
A public IPSec tunnel interface and SAP are created under IES. To delete a public IPSec tunnel interface and SAP:
8.9.3. Deleting a Private IPSec Tunnel SAP and Interface
A private IPSec tunnel interface and SAP are created under a VPRN service. To delete a private IPSec tunnel interface and SAP:
8.9.4. Deleting an IPSec Security Policy
Security policies are created under the VPRN service. To delete an IPSec security policy:
8.9.5. Deleting an IPSec Tunnel
IPSec tunnels are created under the VPRN service. To delete an IPSec tunnel: