Configuring Logging with CLI
This section provides information to configure logging using the command line interface.
Topics in this section include:
Log Configuration Overview
Configure logging parameters to save information in a log file or direct the messages to other devices. Logging does the following:
- Provides you with logging information for monitoring and troubleshooting.
- Allows you to select the types of logging information to be recorded.
- Allows you to assign a severity to the log messages.
- Allows you to select the source and target of logging information.
Log Types
Logs can be configured in the following contexts:
- Log file — Log files can contain log event message streams or accounting/billing information. Log file IDs are used to direct events, alarms/traps and debug information to their respective targets.
- SNMP trap groups — SNMP trap groups contain an IP address and community names which identify targets to send traps following specified events.
- Syslog — Information can be sent to a syslog host that is capable of receiving selected syslog messages from a network element.
- Event control — Configures a particular event or all events associated with an application to be generated or suppressed.
- Event filters — An event filter defines whether to forward or drop an event or trap based on match criteria.
- Accounting policies — An accounting policy defines the accounting records that will be created. Accounting policies can be applied to one or more service access points (SAPs).
- Event logs — An event log defines the types of events to be delivered to its associated destination.
- Event throttling rate — Defines the rate of throttling events.
Basic Event Log Configuration
The most basic log configuration must have the following:
- Log ID or accounting policy ID
- A log source
- A log destination
The following displays a log configuration example for the 7750 SR.
Common Configuration Tasks
The following sections describe basic system tasks that must be performed.
Configuring an Event Log
A event log file contains information used to direct events, alarms, traps, and debug information to their respective destinations. One or more event sources can be specified. File IDs, SNMP trap groups, or syslog IDs must be configured before they can be applied to an event log ID.
Use the following CLI syntax to configure a log file:
The following displays a log file configuration example:
Configuring a File ID
To create a log file a file ID is defined, specifies the target CF drive, and the rollover and retention interval period for the file. The rollover interval is defined in minutes and determines how long a file will be used before it is closed and a new log file is created. The retention interval determines how long the file will be stored on the CF before it is deleted.
When creating new log files in a compact flash disk card, the minimum amount of free space is the MINIMUM of 10% of Compact Flash disk capacity OR 5Mb (5,242,880 = 5 * 1024 * 1024).
The following displays a log file configuration example:
Configuring an Accounting Policy
Before an accounting policy can be created a target log file must be created to collect the accounting records. The files are stored in system memory of compact flash (cf1: or cf2:) in a compressed (tar) XML format and can be retrieved using FTP or SCP. See Configuring an Event Log on page 447 and Configuring a File ID on page 448.
Accounting policies must be configured in the config>log context before they can be applied to a service SAP or service interface, or applied to a network port.
The default accounting policy statement cannot be applied to LDP nor RSVP statistics collection records.
An accounting policy must define a record type and collection interval. Only one record type can be configured per accounting policy.
When creating accounting policies, one service accounting policy and one network accounting policy can be defined as default. If statistics collection is enabled on a SAP or network port and no accounting policy is applied, then the respective default policy is used. If no default policy is defined, then no statistics are collected unless a specifically defined accounting policy is applied.
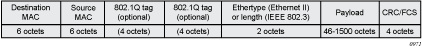
By default, the subscriber host volume accounting data are based on the 14-byte Ethernet DLC header, 4-byte or 8-byte VLAN Tag (optional), 20-byte IP header, IP payload, and the 4-byte CRC (everything except the preamble and inter-frame gap). See Figure 14. This default can be altered by the packet-byte-offset configuration option.
Figure 14: Subscriber Host Volume Accounting Data
The following displays an accounting policy configuration example:
Configuring Event Control
The following displays an example of an event control configuration:
Configuring a Log Filter
The following displays a log filter configuration example:
Configuring an SNMP Trap Group
The associated log-id does not have to configured before a snmp-trap-group can be created, however, the snmp-trap-group must exist before the log-id can be configured to use it.
The following displays a basic SNMP trap group configuration example:
The following displays a SNMP trap group, log, and interface configuration examples:
Setting the Replay Parameter
For this example the replay parameter was set by a SNMP SET request for the trap-target address 10.10.10.3 which is bound to port-id 1/1/1.
In the following output, the Replay field changed from disabled to enabled.
Since no events are waiting to be replayed, the log displays as before.
Shutdown In-Band Port
A shutdown on the in-band port that the trap-target address is bound to causes the route to that particular trap target to be removed from the route table. When the SNMP module is notified of this event, it marks the trap-target as inaccessible and saves the sequence-id of the first SNMP notification that will be missed by the trap-target.
Example: config>log>snmp-trap-group# exit all #configure port 1/1/1 shutdown # # tools perform log test-event #
The Replay from field is updated with the sequence-id of the first event that will be replayed when the trap-target address is added back to the route table.
A display of the event log indicates which trap targets are not accessible and waiting for notification replay and the sequence ID of the first notification that will be replayed.
| Note:
If there are more missed events than the log size, the replay will actually start from the first available missed event. |
No Shutdown Port
A no shutdown command executed on the in-band port to which the trap-target address is bound will cause the route to that trap target to be re-added to the route table. When the SNMP trap module is notified of this event, it resends the notifications that were missed while there was no route to the trap-target address.
Example: configure# port 1/1/1 no shutdown # # tools perform log test-event
After the notifications have been replayed the Replay from field indicates n/a because there are no more notifications waiting to be replayed and the Last replay field timestamp has been updated.
A display of the event log shows that it is no longer waiting to replay notifications to one or more of its trap target addresses. An event message has been written to the logger that indicates the replay to the trap-target address has happened and displays the notification sequence ID of the first and last replayed notifications.
Configuring a Syslog Target
Log events cannot be sent to a syslog target host until a valid syslog ID exists.
The following displays a syslog configuration example:
Configuring an Accounting Custom Record
The following is an example custom record configuration.
Log Management Tasks
This section discusses the following logging tasks:
Modifying a Log File
The following displays the current log configuration:
The following displays an example to modify log file parameters:
The following displays the modified log file configuration:
Deleting a Log File
The log ID must be shutdown first before it can be deleted. In a previous example, file 1 is associated with log-id 2.
The following displays an example to delete a log file:
Modifying a File ID
The following displays the current log configuration:
The following displays an example to modify log file parameters:
The following displays the file modifications:
The following displays an example to modify log file parameters:
The following displays the file modifications:
Modifying a Syslog ID
The following displays an example of the syslog ID modifications:
The following displays the syslog configuration:
Modifying an SNMP Trap Group
The following displays the current SNMP trap group configuration:
The following displays an example of the command usage to modify an SNMP trap group:
The following displays the SNMP trap group configuration:
Deleting an SNMP Trap Group
The following displays the SNMP trap group configuration:
The following displays an example to delete a trap target and an SNMP trap group.
Modifying a Log Filter
The following output displays the current log filter configuration:
The following displays an example of the log filter modifications:
The following displays the log filter configuration:
Modifying Event Control Parameters
The following displays the current event control configuration:
The following displays an example of an event control modification:
The following displays the log filter configuration:
The following displays the current event control configuration:
The following displays an example of an event control modification:
The following displays the log filter configuration:
Returning to the Default Event Control Configuration
The no form of the event-control command returns modified values back to the default values.
Use the following CLI syntax to modify event control parameters:
The following displays an example of the command usage to return to the default values: