5. Ethernet Virtual Private Networks (EVPNs)
5.1. In This Chapter
This chapter provides information about Ethernet Virtual Private Networks (EVPNs), process overview, and implementation notes.
Topics in this chapter include:
5.2. Overview
EVPN is an IETF technology per RFC 7432, BGP MPLS-Based Ethernet VPN, that uses a new BGP address family and allows VPLS services to be operated as IP-VPNs, where the MAC addresses and the information to set up the flooding trees are distributed by BGP.
EVPN is defined to fill the gaps of other L2VPN technologies such as VPLS. The main objective of the EVPN is to build ELAN services in a similar way to RFC 4364 IP-VPNs, while supporting MAC learning within the control plane (distributed by MP-BGP), efficient multi-destination traffic delivery, and active-active multi-homing.
EVPN can be used as the control plane for different data plane encapsulations. Nokia’s implementation supports the following data planes:
- EVPN for VXLAN overlay tunnels (EVPN-VXLAN)EVPN for VXLAN overlay tunnels (EVPN-VXLAN), being the Data Center Gateway (DC GW) function the main application for this feature. In such application VXLAN is expected within the Data Center and VPLS sdp-bindings or SAPs are expected for the connectivity to the WAN. R-VPLS and VPRN connectivity to the WAN is also supported.The EVPN-VXLAN functionality is standardized in draft-ietf-bess-evpn-overlay.
- EVPN for MPLS tunnels (EVPN-MPLS)EVPN for MPLS tunnels (EVPN-MPLS), where PEs are connected by any type of MPLS tunnel. EVPN-MPLS is generally used as an evolution for VPLS services in the WAN, being Data Center Interconnect one of the main applications.The EVPN-MPLS functionality is standardized in RFC 7432.
- EVPN for PBB over MPLS tunnels (PBB-EVPN),PEs are connected by PBB over MPLS tunnels in this data plane. It is usually used for large scale ELAN and ELINE services in the WAN.The PBB-EVPN functionality is standardized in RFC 7623.
The 7750 SR, 7450 ESS, or 7950 XRS EVPN VXLAN implementation is integrated in the Nuage Data Center architecture, where the router serves as the DC GW.
Refer to the Nuage Networks Virtualized Service Platform Guide for more information about the Nuage Networks architecture and products. The following sections describe the applications supported by EVPN in the 7750 SR, 7450 ESS, or 7950 XRS implementation.
5.3. EVPN for VXLAN Tunnels in a Layer-2 DC GW (EVPN-VXLAN)
Figure 135 shows the use of EVPN for VXLAN overlay tunnels on the 7750 SR, 7450 ESS, or 7950 XRS when it is used as a Layer-2 DC GW.
Figure 135: Layer-2 DC PE with VPLS to the WAN
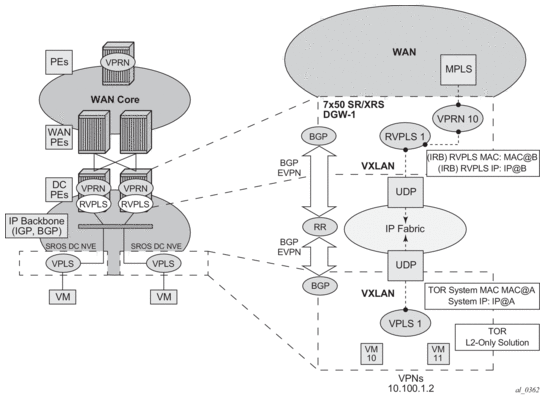
DC providers require a DC GW solution that can extend tenant subnets to the WAN. Customers can deploy the NVO3-based solutions in the DC, where EVPN is the standard control plane and VXLAN is a predominant data plane encapsulation. The Nokia DC architecture (Nuage) uses EVPN and VXLAN as the control and data plane solutions for Layer-2 connectivity within the DC and so does the SR OS.
While EVPN VXLAN will be used within the DC, most service providers use VPLS and H-VPLS as the solution to extend Layer-2 VPN connectivity. Figure 135 shows the Layer-2 DC GW function on the 7750 SR, 7450 ESS, and 7950 XRS routers, providing VXLAN connectivity to the DC and regular VPLS connectivity to the WAN.
The WAN connectivity will be based on VPLS where SAPs (null, dot1q, and qinq), spoke-SDPs (FEC type 128 and 129), and mesh-SDPs are supported.
The DC GWs can provide multi-homing resiliency through the use of BGP multi-homing.
5.4. EVPN for VXLAN Tunnels in a Layer-2 DC with Integrated Routing Bridging Connectivity on the DC GW
Figure 136 shows the use of EVPN for VXLAN overlay tunnels on the 7750 SR, 7450 ESS, or 7950 XRS when the DC provides LAYER-2 connectivity and the DC GW can route the traffic to the WAN through an R-VPLS and linked VPRN.
Figure 136: GW IRB on the DC PE for an L2 EVPN/VXLAN DC

In some cases, the DC GW must provide a Layer 3 default gateway function to all the hosts in a specified tenant subnet. In this case, the VXLAN data plane will be terminated in an R-VPLS on the DC GW, and connectivity to the WAN will be accomplished through regular VPRN connectivity. The 7750 SR, 7450 ESS, and 7950 XRS support IPv4 and IPv6 interfaces as default gateways in this scenario.
5.5. EVPN for VXLAN Tunnels in a Layer 3 DC with Integrated Routing Bridging Connectivity among VPRNs
Figure 137 shows the use of EVPN for VXLAN tunnels on the 7750 SR, 7450 ESS, or 7950 XRS when the DC provides distributed layer-3 connectivity to the DC tenants.
Figure 137: GW IRB on the DC PE for an L3 EVPN/VXLAN DC

Each tenant will have several subnets for which each DC Network Virtualization Edge (NVE) provides intra-subnet forwarding. An NVE may be a Nuage VSG, VSC/VRS, or any other NVE in the market supporting the same constructs, and each subnet normally corresponds to an R-VPLS. For example, in Figure 137, subnet 10.20.0.0 corresponds to R-VPLS 2001 and subnet 10.10.0.0 corresponds to R-VPLS 2000. In this example, the NVE provides inter-subnet forwarding too, by connecting all the local subnets to a VPRN instance. When the tenant requires L3 connectivity to the IP-VPN in the WAN, a VPRN is defined in the DC GWs, which connects the tenant to the WAN. That VPRN instance will be connected to the VPRNs in the NVEs by means of an IRB (Integrated Routing and Bridging) backhaul R-VPLS. This IRB backhaul R-VPLS provides a scalable solution because it allows L3 connectivity to the WAN without the need for defining all of the subnets in the DC GW.
The 7750 SR, 7450 ESS (in mixed mode), and 7950 XRS DC GW support the IRB backhaul R-VPLS model, where the R-VPLS runs EVPN-VXLAN and the VPRN instances exchange IP prefixes (IPv4 and IPv6) through the use of EVPN. Interoperability between the EVPN and IP-VPN for IP prefixes is also fully supported.
5.6. EVPN for VXLAN Tunnels in a Layer 3 DC with EVPN-Tunnel Connectivity among VPRNs
Figure 138 shows the use of EVPN for VXLAN tunnels on the 7750 SR, 7450 ESS (in mixed mode), or 7950 XRS, when the DC provides distributed layer-3 connectivity to the DC tenants and the VPRN instances are connected through EVPN tunnels.
Figure 138: EVPN-Tunnel GW IRB on the DC PE for an L3 EVPN/VXLAN DC
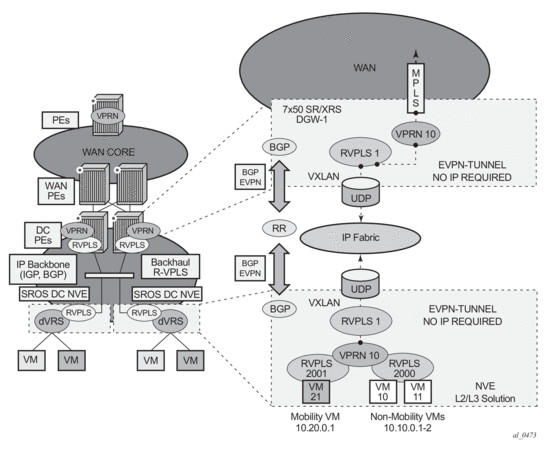
The solution described in section EVPN for VXLAN Tunnels in a Layer 3 DC with Integrated Routing Bridging Connectivity among VPRNs provides a scalable IRB backhaul R-VPLS service where all the VPRN instances for a specified tenant can be connected by using IRB interfaces. When this IRB backhaul R-VPLS is exclusively used as a backhaul and does not have any SAPs or SDP-bindings directly attached, the solution can be optimized by using EVPN tunnels.
EVPN tunnels are enabled using the evpn-tunnel command under the R-VPLS interface configured on the VPRN. EVPN tunnels provide the following benefits to EVPN-VXLAN IRB backhaul R-VPLS services:
- Easier provisioning of the tenant service. If an EVPN tunnel is configured in an IRB backhaul R-VPLS, there is no need to provision the IRB IPv4 addresses on the VPRN. This makes the provisioning easier to automate and saves IP addresses from the tenant space.

Note: IPv6 interfaces do not require the provisioning of an IPv6 Global Address; a Link Local Address is automatically assigned to the IRB interface.
- Higher scalability of the IRB backhaul R-VPLS. If EVPN tunnels are enabled, multicast traffic is suppressed in the EVPN-VXLAN IRB backhaul R-VPLS service (it is not required). As a result, the number of VXLAN binds in IRB backhaul R-VPLS services with EVPN-tunnels can be much higher.
This optimization is fully supported by the 7750 SR, 7450 ESS (in mixed mode), and 7950 XRS.
5.7. EVPN for MPLS Tunnels in ELAN Services
Figure 139 shows the use of EVPN for MPLS tunnels on the 7750 SR, 7450 ESS, and 7950 XRS. In this case, EVPN is used as the control plane for ELAN services in the WAN.
Figure 139: EVPN for MPLS in VPLS Services
EVPN-MPLS is standardized in RFC 7432 as an L2VPN technology that can fill the gaps in VPLS for ELAN services. A significant number of service providers offering ELAN services today are requesting EVPN for their multi-homing capabilities, in addition to the optimization EVPN provides. EVPN supports all-active multi-homing (per-flow load-balancing multi-homing) in addition to single-active multi-homing (per-service load-balancing multi-homing).
EVPN is a standard-based technology that supports all-active multi-homing, and although VPLS already supports single-active multi-homing, EVPN's single-active multi-homing is perceived as a superior technology due to its mass-withdrawal capabilities to speed up convergence in scaled environments.
EVPN technology provides a number of significant benefits, including:
- superior multi-homing capabilities
- an IP-VPN-like operation and control for ELAN services
- reduction and (in some cases) suppression of the BUM (broadcast, Unknown unicast, and Multicast) traffic in the network
- simple provision and management
- new set of tools to control the distribution of MAC addresses and ARP entries in the network
The SR OS EVPN-MPLS implementation is compliant with RFC 7432.
EVPN-MPLS can also be enabled in R-VPLS services with the same feature-set that is described for VXLAN tunnels in sections EVPN for VXLAN Tunnels in a Layer 3 DC with Integrated Routing Bridging Connectivity among VPRNs and EVPN for VXLAN Tunnels in a Layer 3 DC with EVPN-Tunnel Connectivity among VPRNs.
5.8. EVPN for MPLS Tunnels in ELINE Services
The MPLS network used by EVPN for ELAN services can also be shared by ELINE services using EVPN in the control plane. EVPN for ELINE services (EVPN-VPWS) is a simplification of the RFC 7432 procedures, and is supported on the 7750 SR, 7450 ESS, and 7950 XRS in compliance with draft-ietf-bess-evpn-vpws.
5.9. EVPN for PBB over MPLS Tunnels (PBB-EVPN)
Figure 140 shows the use of EVPN for MPLS tunnels on the 7750 SR, 7450 ESS, and 7950 XRS. In this case, EVPN is used as the control plane for ELAN services in the WAN.
Figure 140: EVPN for PBB over MPLS
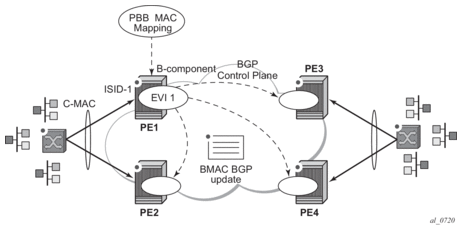
EVPN for PBB over MPLS (hereafter called PBB-EVPN) is specified in RFC 7623. It provides a simplified version of EVPN for cases where the network requires very high scalability and does not need all the advanced features supported by EVPN-MPLS (but still requires single-active and all-active multi-homing capabilities).
PBB-EVPN is a combination of 802.1ah PBB and RFC 7432 EVPN and reuses the PBB-VPLS service model, where BGP-EVPN is enabled in the B-VPLS domain. EVPN is used as the control plane in the B-VPLS domain to control the distribution of BMACs and setup per-ISID flooding trees for I-VPLS services. The learning of the CMACs, either on local SAPs/SDP-bindings or associated with remote BMACs, is still performed in the data plane. Only the learning of BMACs in the B-VPLS is performed through BGP.
The SR OS PBB-EVPN implementation supports PBB-EVPN for I-VPLS and PBB-Epipe services, including single-active and all-active multi-homing.
5.10. VXLAN
The SR OS and Nuage solution for DC supports VXLAN (Virtual eXtensible Local Area Network) overlay tunnels as per RFC 7348.
VXLAN addresses the data plane needs for overlay networks within virtualized data centers accommodating multiple tenants. The main attributes of the VXLAN encapsulation are:
- VXLAN is an overlay network encapsulation used to carry MAC traffic between VMs over a logical Layer 3 tunnel.
- Avoids the Layer 2 MAC explosion, because VM MACs are only learned at the edge of the network. Core nodes simply route the traffic based on the destination IP (which is the system IP address of the remote PE or VTEP-VXLAN Tunnel End Point).
- Supports multi-path scalability through ECMP (to a remote VTEP address, based on source UDP port entropy) while preserving the Layer 2 connectivity between VMs. xSTP is no longer needed in the network.
- Supports multiple tenants, each with their own isolated Layer 2 domain. The tenant identifier is encoded in the VNI field (VXLAN Network Identifier) and allows up to 16M values, as opposed to the 4k values provided by the 802.1q VLAN space.
Figure 141 shows an example of the VXLAN encapsulation supported by Nokia’s implementation.
Figure 141: VXLAN Frame Format
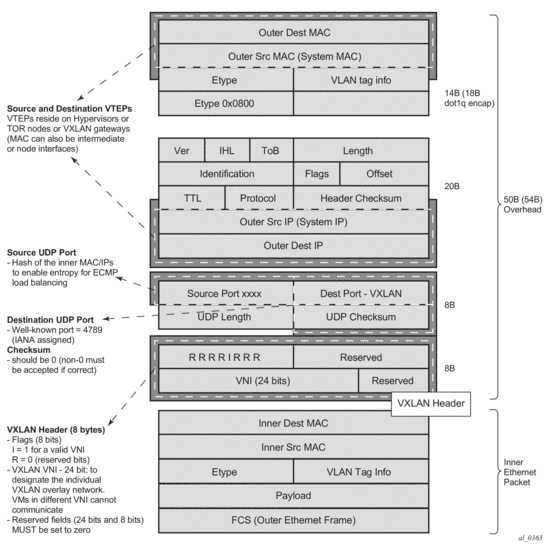
As shown in Figure 141, VXLAN encapsulates the inner Ethernet frames into VXLAN + UDP/IP packets. The main pieces of information encoded in this encapsulation are:
- VXLAN header (8 bytes)
- Flags (8 bits) where the I flag is set to 1 to indicate that the VNI is present and valid. The rest of the flags (“Reserved” bits) are set to 0.
- Includes the VNI field (24-bit value) or VXLAN network identifier. It identifies an isolated Layer-2 domain within the DC network.
- The rest of the fields are reserved for future use.
- UDP header (8 bytes)
- Where the destination port is a well-known UDP port assigned by IANA (4789).
- The source port is derived from a hashing of the inner source and destination MAC/IP addresses that the 7750 SR, 7450 ESS, or 7950 XRS does at ingress. This will create an “entropy” value that can be used by the core DC nodes for load balancing on ECMP paths.
- The checksum will be set to zero.
- Outer IP and Ethernet headers (34 or 38 bytes)
- The source IP and source MAC will identify the source VTEP. That is, these fields will be populated with the PE’s system IP and chassis MAC address.

Note: The source MAC address will be changed on all the IP hops along the path, as is usual in regular IP routing.
- The destination IP will identify the remote VTEP (remote system IP) and will be the result of the destination MAC lookup in the service Forwarding Database (FDB).

Note: All remote MACs will be learned by the EVPN BGP and associated with a remote VTEP address and VNI.
Some considerations related to the support of VXLAN on the 7750 SR, 7450 ESS, and 7950 XRS are:
- VXLAN is only supported on network or hybrid ports with null or dot1q encapsulation.
- VXLAN is supported on Ethernet/LAG and POS/APS.
- IPv4 and IPv6 unicast addresses are supported as VTEPs.
- By default, system IP addresses are supported, as VTEPs, for originating and terminating VXLAN tunnels. Non-system IPv4 and IPv6 addresses are supported by using a Forwarding Path Extension (FPE).
5.10.1. VXLAN ECMP and LAG
The DC GW supports ECMP load balancing to reach the destination VTEP. Also, any intermediate core node in the Data Center should be able to provide further load balancing across ECMP paths because the source UDP port of each tunneled packet is derived from a hash of the customer inner packet. The following must be considered:
- ECMP for VXLAN is supported on VPLS services, but not for BUM traffic. Unicast spraying will be based on the packet contents.
- ECMP for VXLAN is not supported on R-VPLS services.
- In both cases where ECMP is not supported, each VXLAN binding is tied to a single (different) ECMP path, so in a normal deployment with a reasonable number of remote VTEPs, there should be a fair distribution of the traffic across the paths. In other words, only per-VTEP load-balancing is supported, instead of per-flow load-balancing.
- LAG spraying based on the packet hash is supported in all the cases (VPLS unicast, VPLS BUM, and R-VPLS).
5.10.2. VXLAN VPLS Tag Handling
The following describes the behavior on the 7750 SR, 7450 ESS, and 7950 XRS with respect to VLAN tag handling for VXLAN VPLS services:
- Dot1q, QinQ, and null SAPs, as well as regular VLAN handling procedures at the WAN side, are supported on VXLAN VPLS services.
- No “vc-type vlan” like VXLAN VNI bindings are supported. Therefore, at the egress of the VXLAN network port, the router will not add any inner VLAN tag on top of the VXLAN encapsulation, and at the ingress network port, the router will ignore any VLAN tag received and will consider it as part of the payload.
5.10.3. VXLAN MTU Considerations
For VXLAN VPLS services, the network port MTU must be at least 50 Bytes (54 Bytes if dot1q) greater than the Service-MTU to allow enough room for the VXLAN encapsulation.
The Service-MTU is only enforced on SAPs, (any SAP ingress packet with MTU greater than the service-mtu will be discarded) and not on VXLAN termination (any VXLAN ingress packet will make it to the egress SAP regardless of the configured service-mtu).
| Note: The router will never fragment or reassemble VXLAN packets. In addition, the router always sets the DF (Do not Fragment) flag in the VXLAN outer IP header. |
5.10.4. VXLAN QoS
VXLAN is a network port encapsulation; therefore, the QoS settings for VXLAN are controlled from the network QoS policies.
5.10.4.1. Ingress
The network ingress QoS policy can be applied either to the network interface over which the VXLAN traffic arrives or under vxlan/network/ingress within the EVPN service.
Regardless of where the network QoS policy is applied, the ingress network QoS policy is used to classify the VXLAN packets based on the outer dot1p (if present), then the outer DSCP, to yield an FC/profile.
If the ingress network QoS policy is applied to the network interface over which the VXLAN traffic arrives then the VXLAN unicast traffic uses the network ingress queues configured on FP where the network interface resides. QoS control of BUM traffic received on the VXLAN tunnels is possible by separately redirecting these traffic types to policers within an FP ingress network queue group. This QoS control uses the per forwarding class fp-redirect-group parameter together with broadcast-policer, unknown-policer, and mcast-policer within the ingress section of a network QoS policy. This QoS control applies to all BUM traffic received for that forwarding class on the network IP interface on which the network QoS policy is applied.
The ingress network QoS policy can also be applied within the EVPN service by referencing an FP queue group instance, as follows:
In this case, the redirection to a specific ingress FP queue group applies as a single entity (per forwarding class) to all VXLAN traffic received only by this service. This overrides the QoS applied to the related network interfaces for traffic arriving on VXLAN tunnels in that service but does not affect traffic received on a spoke SDP in the same service. It is possible to also redirect unicast traffic to a policer using the per forwarding class fp-redirect-group policer parameter, in addition to the BUM traffic as above, within the ingress section of a network QoS policy. The use of ler-use-dscp, ip-criteria and ipv6-criteria statements are ignored if configured in the ingress section of the referenced network QoS policy. If the instance of the named queue group template referenced in the qos command is not configured on an FP receiving the VXLAN traffic, then the traffic uses the ingress network queues or queue group related to the network interface.
5.10.4.2. Egress
On egress, there is no need to specify “remarking” in the policy to mark the DSCP. This is because the VXLAN adds a new IPv4 header, and the DSCP will be always marked based on the egress network qos policy.
5.10.5. VXLAN Ping
A new VXLAN troubleshooting tool, VXLAN Ping, is available to verify VXLAN VTEP connectivity. The VXLAN Ping command is available from interactive CLI and SNMP.
This tool allows the operator to specify a wide range of variables to influence how the packet is forwarded from the VTEP source to VTEP termination. The ping function requires the operator to specify a different test-id (equates to originator handle) for each active and outstanding test. The required local service identifier from which the test is launched will determine the source IP (the system IP address) to use in the outer IP header of the packet. This IP address is encoded into the VXLAN header Source IP TLV. The service identifier will also encode the local VNI. The outer-ip-destination must equal the VTEP termination point on the remote node, and the dest-vni must be a valid VNI within the associated service on the remote node. The outer source IP address is automatically detected and inserted in the IP header of the packet. The outer source IP address uses the IPv4 system address by default.
If the VTEP is created using a non-system source IP address via the vxlan-src-vtep command, the outer source IP address uses the address specified by vxlan-src-vtep. The remainder of the variables are optional.
The VXLAN PDU will be encapsulated in the appropriate transport header and forwarded within the overlay to the appropriate VTEP termination. The VXLAN router alert (RA) bit will be set to prevent forwarding OAM PDU beyond the terminating VTEP. Since handling of the router alert bit was not defined in some early releases of VXLAN implementations, the VNI Informational bit (I-bit) is set to “0” for OAM packets. This indicates that the VNI is invalid, and the packet should not be forwarded. This safeguard can be overridden by including the i-flag-on option that sets the bit to “1”, valid VNI. Ensure that OAM frames meant to be contained to the VTEP are not forwarded beyond its endpoints.
The supporting VXLAN OAM ping draft includes a requirement to encode a reserved IEEE MAC address as the inner destination value. However, at the time of implementation, that IEEE MAC address had not been assigned. The inner IEEE MAC address will default to 00:00:00:00:00:00, but may be changed using the inner-l2 option. Inner IEEE MAC addresses that are included with OAM packets will not be learned in the local layer 2 forwarding databases.
The echo responder will terminate the VXLAN OAM frame, and will take the appropriate response action, and include relevant return codes. By default, the response is sent back using the IP network as an IPv4 UDP response. The operator can chose to override this default by changing the reply-mode to overlay. The overlay return mode will force the responder to use the VTEP connection representing the source IP and source VTEP. If a return overlay is not available, the echo response will be dropped by the responder.
Support is included for:
- IPv4 VTEP
- Optional specification of the outer UDP Source, which helps downstream network elements along the path with ECMP to hash to flow to the same path
- Optional configuration of the inner IP information, which helps the operator test different equal paths where ECMP is deployed on the source. A test will only validate a single path where ECMP functions are deployed. The inner IP information is processed by a hash function, and there is no guarantee that changing the IP information between tests will select different paths.
- Optional end system validation for a single L2 IEEE MAC address per test. This function checks the remote FDB for the configured IEEE MAC Address. Only one end system IEEE MAC Address can be configured per test.
- Reply mode UDP (default) or Overlay
- Optional additional padding can be added to each packet. There is an option that indicates how the responder should handle the pad TLV. By default, the padding will not be reflected to the source. The operator can change this behavior by including reflect-pad option. The reflect-pad option is not supported when the reply mode is set to UDP.
- Configurable send counts, intervals, times outs, and forwarding class
The VXLAN OAM PDU includes two timestamps. These timestamps are used to report forward direction delay. Unidirectional delay metrics require accurate time of day clock synchronization. Negative unidirectional delay values will be reported as “0.000”. The round trip value includes the entire round trip time including the time that the remote peer takes to process that packet. These reported values may not be representative of network delay.
The following example commands and outputs show how the VXLAN Ping function can be used to validate connectivity. The echo output includes a new header to better describe the VxLAN ping packet headers and the various levels.
5.10.6. IGMP Snooping on VXLAN
The delivery of IP Multicast in VXLAN services can be optimized with IGMP snooping. IGMP snooping is supported in EVPN-VXLAN VPLS services. When enabled, IGMP reports will be snooped on SAPs/SDP-bindings, but also on VXLAN bindings, to create/modify entries in the MFIB for the VPLS service.
The following must be considered when configuring IGMP snooping in EVPN-VXLAN VPLS services:
- There is an additional configuration command to enable IGMP snooping on VXLAN: config>service>vpls>igmp-snooping no shutdown will enable the feature in the VPLS service.
- The VXLAN bindings only support basic IGMP snooping functionality. Features configurable under SAPs or SDP-bindings are not available for VXLAN. Since there is no specific IGMP snooping settings for VXLAN bindings (static mrouters or send-queries, and so on.), a specified VXLAN binding will only become a dynamic mrouter when it receives IGMP queries and will add a specified multicast group to the MFIB when it receives an IGMP report for that group.
- The corresponding show service id igmp-snooping and clear service id igmp-snooping commands are also available for VXLAN bindings. The following CLI commands show how the system displays IGMP snooping information and statistics on VXLAN bindings:
5.10.7. Non-System IPv4 and IPv6 VXLAN Termination in VPLS and R-VPLS Services
By default, only VXLAN packets with the same IP destination address as the system IPv4 address of the router can be terminated and processed for a subsequent MAC lookup. A router can simultaneously terminate VXLAN tunnels destined for its system IP address and three additional non-system IPv4 or IPv6 addresses. This section describes the configuration requirements for services to terminate VXLAN packets destined for a non-system loopback IPv4 or IPv6 address.
Perform the following steps to configure a service with non-system IPv4 or IPv6 VXLAN termination.
Step 1 – FPE Creation
A Forwarding Path Extension (FPE) is required to terminate non-system IPv4 or IPv6 VXLAN tunnels.
In a non-system IPv4 VXLAN termination, the FPE function is used for additional processing required at ingress (VXLAN tunnel termination) only, and not at egress (VXLAN tunnel origination).
If the IPv6 VXLAN terminates on a VPLS service, the FPE function is used at ingress only, and not at egress.
For R-VPLS services terminating IPv6 VXLAN tunnels, in addition to the VXLAN termination function, the FPE is also used for the egress; an internal static SDP is created to allow the required extra processing.
See section “Forwarding Path Extension” of the 7450 ESS, 7750 SR, and 7950 XRS Interface Configuration Guide for information about FPE configuration and functions.
Step 2 – Associate FPE with VXLAN Termination
Next, associate the FPE with the vxlan termination application. The following sample configuration shows two FPEs and their corresponding association.
Step 3 – Configure Router Loopback Interface
Create the interface that will terminate and originate the VXLAN packets. The interface is created as a router interface, which is added to the Interior Gateway Protocol (IGP) and used by the BGP as the EVPN NLRI next hop.
Because the system cannot terminate the VXLAN on a local interface address, a subnet must be assigned to the loopback interface and not a host IP address that is /32 or /128. In the following example, all the addresses in subnet 11.11.11.0/24 (except 11.11.11.1, which is the interface IP) can be used for tunnel termination. The subnet is advertised using the IGP.
Configuring a local interface address as a VXLAN tunnel-termination IP address is not allowed by the CLI, as shown in the following example.
The subnet can be up to 31 bits. For example, to use 11.11.11.1 as the VXLAN termination address, the subnet should be configured and advertised as shown in the following sample configuration.
It is not a requirement for the remote PEs and NVEs to have the specific /32 or /128 IP address in their RTM to resolve the BGP EVPN NLRI next hop or forward the VXLAN packets. An RTM with a subnet that contains the remote VTEP can also perform these tasks.
| Note: The system does not check for a pre-existing local base router loopback interface with a subnet corresponding to the VXLAN tunnel termination address. If a tunnel termination address is configured and the FPE is UP, the system starts terminating VXLAN traffic and responding ICMP messages for that address. The following conditions are ignored in this scenario:
|
The following sample output includes an IPv6 address.
Step 4 – Configure VXLAN Termination (Non-System) VTEP Addresses
The service>system>vxlan>tunnel-termination context allows the user to configure non-system IP addresses that can terminate the VXLAN and their corresponding FPEs.
As shown in the following example, an IP address may be associated with a new or existing FPE already terminating the VXLAN. The list of addresses that can terminate the VXLAN can include IPv4 and IPv6 addresses.
The tunnel-termination command creates internal loopback interfaces that can respond to ICMP requests. In the following sample output, an internal loopback is created when the tunnel-termination address is added (for 11.11.11.1 and 200::1). The internal FPE router interfaces created by the VXLAN termination function are also shown in the output.
Step 5– Add the Service Configuration
By default, the EVPN-VXLAN services use the system IP address as the source VTEP of the VXLAN encapsulated frames. The vxlan-src-vtep command in the service>vpls context enables the system to use a non-system IPv4 or IPv6 address as the source VTEP for the VXLAN tunnels in that service. A different vxlan-src-vtep can be used for different services, as shown in the following example where two different services use different non-system IP addresses as source VTEPs.
In addition, if a vxlan-src-vtep is configured, the IP address is also used to set the BGP NLRI next hop in EVPN route advertisements for the service.
| Note: The BGP EVPN next hop can be overridden by the use of export policies based on the following rules.
|
After the preceding steps are used to configure a VXLAN termination, the VPLS or R-VPLS service can be used normally, except that the service will terminate VXLAN tunnels with a non-system IPv4 or IPv6 destination address instead of the system IP address only.
The FPE vxlan-termination function creates internal router interfaces and loopbacks that are displayed by the show commands. When configuring IPv6 VXLAN termination on an R-VPLS service, in addition to the internal router interfaces and loopbacks, the system will create internal SDP bindings for the required egress processing. The following output shows an example of an internal FPE-type SDP binding created for IPv6 R-VPLS egress processing.
5.11. BGP-EVPN Control Plane for VXLAN Overlay Tunnels
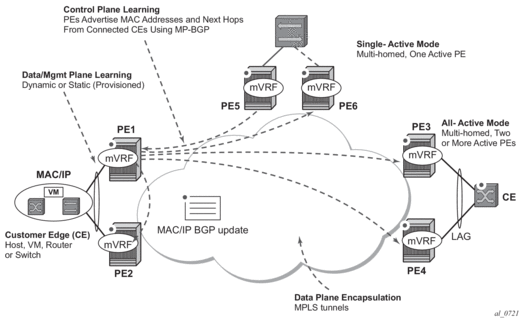
The draft-ietf-bess-evpn-overlay describes EVPN as the control plane for overlay-based networks. The 7750 SR, 7450 ESS, and 7950 XRS support a subset of the routes and features described in RFC 7432 that are required for the DC GW function. In particular, EVPN-specific multi-homing capabilities are not supported for VXLAN. However, multi-homing can be supported by using regular BGP multi-homing based on the L2VPN BGP address family.
Figure 142 shows the EVPN MP-BGP NLRI, required attributes and extended communities, and two route types supported for the DC GW Layer 2 applications:
- route type 3 – Inclusive Multicast Ethernet Tag route
- route type 2 – MAC/IP advertisement route
Figure 142: EVPN-VXLAN Required Routes and Communities
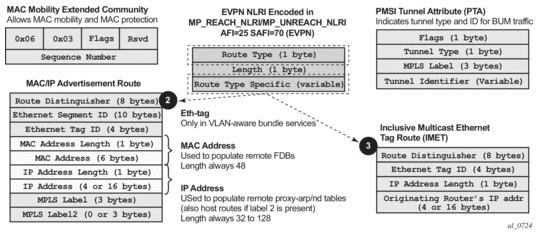
EVPN Route Type 3 – Inclusive Multicast Ethernet Tag Route
Route type 3 is used to set up the flooding tree (BUM flooding) for a specified VPLS service in the data center. The received inclusive multicast routes add entries to the VPLS flood list in the 7750 SR, 7450 ESS, and 7950 XRS. The tunnel types supported in an EVPN route type 3 when BGP-EVPN MPLS is enabled are ingress replication, P2MP MLDP, and composite tunnels.
Ingress Replication (IR) and Assisted Replication (AR) are supported for VXLAN tunnels. See section 5.18, Layer 2 Multicast Optimization for VXLAN (Assisted-Replication) for more information about the AR.
If ingress-repl-inc-mcast-advertisement is enabled, a route type 3 is generated by the router per VPLS service as soon as the service is in an operationally up state. The following fields and values are used:
- Route Distinguisher: taken from the RD of the VPLS service within the BGP contextNote: The RD can be configured or derived from the bgp-evpn evi value.
- Ethernet Tag ID: 0
- IP address length: always 32
- Originating router’s IP address: carries the system address (IPv4 only)Note: By default, the IP address of the Originating router is derived from the system IP address. However, this can be overridden by the config>service>vpls>bgp-evpn>incl-mcast-orig-ip <ip-address> command for the Ingress Replication (and mLDP if MPLS is used) tunnel type.
- PMSI Tunnel Attribute (PTA):
- Tunnel type = Ingress replication (6) or Assisted Replication (10)
- Flags—Leaf not required.
- MPLS label—Carries the VNI configured in the VPLS service. Only one VNI can be configured per VPLS service.
- Tunnel end-point—Equal to the system IP address.
As shown in Figure 143, additional flags are used in the PTA when the service is configured for AR.Figure 143: PMSI Attribute Flags Field for AR
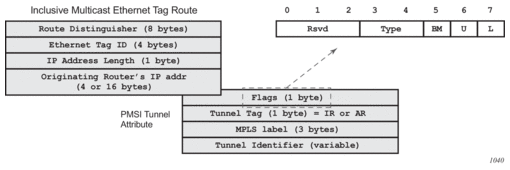 The Flags field is defined as a Type field (for AR) with two new flags that are defined as follows:
The Flags field is defined as a Type field (for AR) with two new flags that are defined as follows:- T is the AR Type field (2 bits):— 00 (decimal 0) = RNVE (non-AR support)— 01 (decimal 1) = AR REPLICATOR— 10 (decimal 2) = AR LEAF
- The U and BM flags defined in draft-ietf-bess-evpn-optimized-ir are not used in the SR OS.
Table 80 describes the inclusive multicast route information sent per VPLS service when the router is configured as assisted-replication replicator (AR-R) or assisted-replication leaf (AR-L). A Regular Network Virtualization Edge device (RNVE) is defined as an EVPN-VXLAN router that does not support (or is not configured for) Assisted-Replication.Note: For AR-R, two inclusive multicast routes may be advertised if ingress-repl-inc-mcast-advertisement is enabled: a route with tunnel-type IR, tunnel-id = IR IP (generally system-ip) and a route with tunnel-type AR, tunnel-id = AR IP (the address configured in the assisted-replication-ip command).Table 80: AR-R AND AR-L Routes and Usage
AR Role
Function
Inclusive Mcast Routes Advertisement
AR-R
Assists AR-LEAFs
- IR included in the Mcast route (uses IR IP) if ingress-repl-inc-mcast-advertisement is enabled
- AR included in the Mcast route (uses AR IP, tunnel type=AR, T=1)
AR-LEAF
Sends BM only to AR-Rs
IR inclusive multicast route (IR IP, T=2) if ingress-repl-inc-mcast-advertisement is enabled
RNVE
Non-AR support
IR inclusive multicast route (IR IP) if ingress-repl-inc-mcast-advertisement is enabled
EVPN Route Type 2 – MAC/IP Advertisement Route
The 7750 SR, 7450 ESS, and 7950 XRS will generate this route type for advertising MAC addresses. The router will generate MAC advertisement routes for the following:
- Learned MACs on SAPs or sdp-bindings – if mac-advertisement is enabled
- Conditional static MACs – if mac-advertisement is enabled
- unknown-mac-routes – if unknown-mac-route is enabled, there is no bgp-mh site in the service or there is a (single) DF site
The route type 2 generated by a router uses the following fields and values:
- Route Distinguisher: taken from the RD of the VPLS service within the BGP context

Note: The RD can be configured or derived from the bgp-evpn evi value.
- Ethernet Segment Identifier (ESI): Value = 0:0:0:0:0:0:0:0:0:0.
- Ethernet Tag ID: 0.
- MAC address length: always 48
- MAC Address:
- is 00:00:00:00:00:00 for the Unknown MAC route address.
- is different from 00:…:00 for the rest of the advertised MACs.
- IP address and IP address length:
- is the IP address associated with the MAC being advertised with a length of 32 (or 128 for IPv6).
- if the MAC address is the Unknown MAC route, the IP address length is zero and the IP omitted.
- in general, any MAC route without IP has IPL=0 (IP length) and the IP is omitted.
- when received, any IPL value not equal to zero, 32, or 128 will make discard the route.
- MPLS Label 1: carries the VNI configured in the VPLS service. Only one VNI can be configured per VPLS.
- MPLS Label 2: 0
- MAC Mobility extended community: used for signaling the sequence number in case of mac moves and the sticky bit in case of advertising conditional static MACs. If a MAC route is received with a MAC mobility ext-community, the sequence number and the sticky bit are considered for the route selection.
When EVPN is used in an IRB backhaul R-VPLS that connects all the VPRN instances for a specified tenant and there is a need to advertise IP prefixes in EVPN, a separate route type is used: route-type 5 IP prefix route.
EVPN Route Type 5 – IP Prefix Route
Figure 144 shows the IP prefix route or route-type 5.
Figure 144: EVPN Route-Type 5
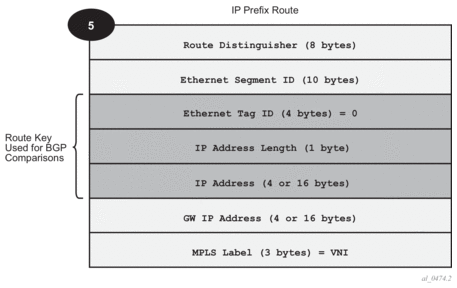
The router will generate this route type for advertising IP prefixes in EVPN. The router will generate IP Prefix advertisement routes for:
- IP prefixes existing in a VPRN linked to the IRB backhaul R-VPLS service.
The route-type 5 generated by a router uses the following fields and values:
- Route Distinguisher: taken from the RD configured in the IRB backhaul R-VPLS service within the BGP context
- Ethernet Segment Identifier (ESI): Value = 0:0:0:0:0:0:0:0:0:0
- Ethernet Tag ID: 0
- IP address length: Any value in the 0 to 128 range
- IP address: any valid IPv4 or IPv6 address
- GW IP address: can carry two different values:
- if different from zero, the route-type 5 carries the primary IP interface address of the VPRN behind which the IP prefix is known. This is the case for the regular IRB backhaul R-VPLS model.
- if 0.0.0.0, the route-type 5 is sent with a MAC next-hop extended community that will carry the VPRN interface MAC address. This is the case for the EVPN tunnel R-VPLS model.
- MPLS Label: carries the VNI configured in the VPLS service. Only one VNI can be configured per VPLS service.
All the routes in EVPN-VXLAN will be sent with the RFC 5512 tunnel encapsulation extended community, with the tunnel type value set to VXLAN.
5.12. EVPN for VXLAN in VPLS Services
The EVPN-VXLAN service is designed around the current VPLS objects and the additional VXLAN construct.
Figure 135 shows a DC with a Layer-2 service that carries the traffic for a tenant who wants to extend a subnet beyond the DC. The DC PE function is carried out by the 7750 SR, 7450 ESS, and 7950 XRS where a VPLS instance exists for that particular tenant. Within the DC, the tenant will have VPLS instances in all the Network Virtualization Edge (NVE) devices where they require connectivity (such VPLS instances can be instantiated in TORs, Nuage VRS, VSG, and so on). The VPLS instances in the redundant DC GW and the DC NVEs will be connected by VXLAN bindings. BGP-EVPN will provide the required control plane for such VXLAN connectivity.
The DC GW routers will be configured with a VPLS per tenant that will provide the VXLAN connectivity to the Nuage VPLS instances. On the router, each tenant VPLS instance will be configured with:
- The WAN-related parameters (saps, spoke-sdps, mesh-sdps, bgp-ad, and so on).
- The BGP-EVPN and VXLAN (VNI) parameters. The following CLI output shows an example for an EVPN-VXLAN VPLS service.
The bgp-evpn context specifies the encapsulation type (only vxlan is supported) to be used by EVPN and other parameters like the unknown-mac-route and mac-advertisement commands. These commands are typically configured in three different ways:
- no unknown-mac-route and mac-advertisement (default option) — The router will advertise new learned MACs (on the SAPs or sdp-bindings) or new conditional static MACs.
- unknown-mac-route and no mac-advertisement — The router will only advertise an unknown-mac-route as long as the service is operationally UP (if no BGP-MH site is configured in the service) or the router is the DF (if BGP-MH is configured in the service).
- unknown-mac-route and mac-advertisement — The router will advertise new learned MACs, conditional static MACs, and the unknown-mac-route. The unknown-mac-route will only be advertised under the preceding described conditions.
Other parameters related to EVPN or VXLAN are:
- Mac duplication parameters
- vxlan vni: Defines the VNI that the router will use in the EVPN routes generated for the VPLS service.
After the VPLS is configured and operationally UP, the router will send/receive inclusive multicast Ethernet Tag routes, and a full-mesh of VXLAN connections will be automatically created. These VXLAN “auto-bindings” can be characterized as follows:
- The VXLAN auto-bindings model is based on an IP-VPN-like design, where no SDPs or SDP-binding objects are created by or visible to the user. The VXLAN auto-binds are composed of remote VTEPs and egress VNIs, and can be displayed with the following command:
- The VXLAN bindings observe the VPLS split-horizon rule. This is performed automatically without the need for any split-horizon configuration.
- BGP Next-Hop Tracking for EVPN is fully supported. If the BGP next-hop for a specified received BGP EVPN route disappears from the routing table, the BGP route will not be marked as “used” and the respective entry in show service id vxlan will be removed.
After the flooding domain is setup, the routers and DC NVEs start advertising MAC addresses, and the routers can learn MACs and install them in the FDB. Some considerations are the following:
- All the MAC addresses associated with remote VTEP/VNIs are always learned in the control plane by EVPN. Data plane learning on VXLAN auto-bindings is not supported.
- When unknown-mac-route is configured, it will be generated when no (BGP-MH) site is configured, or a site is configured AND the site is DF in the PE.

Note: The unknown-mac-route will not be installed in the FDB (therefore, will not show up in the show service id x fdb detail command).
- While the router can be configured with only one VNI (and signals a single VNI per VPLS), it can accept any VNI in the received EVPN routes as long as the route-target is properly imported. The VTEPs and VNIs will show up in the FDB associated with MAC addresses:
5.12.1. Resiliency and BGP Multi-Homing
The DC overlay infrastructure relies on IP tunneling, that is, VXLAN; therefore, the underlay IP layer resolves failure in the DC core. The IGP should be optimized to get the fastest convergence.
From a service perspective, resilient connectivity to the WAN is provided by BGP-Multi-homing.
5.12.2. Use of bgp-evpn, bgp-ad, and Sites in the Same VPLS Service
All bgp-evpn (control plane for a VXLAN DC), bgp-ad (control plane for MPLS-based spoke-sdps connected to the WAN), and ONE site for BGP multi-homing (control plane for the multi-homed connection to the WAN) can be configured in one service in a specified system. If that is the case, the following considerations apply:
- The configured BGP route-distinguisher and route-target are used by BGP for the two families, that is, evpn and l2vpn. If different import/export route targets are to be used per family, vsi-import/export policies must be used.
- The pw-template-binding command under BGP, does not have any effect on evpn or bgp-mh. It is only used for the instantiation of the bgp-ad spoke-sdps.
- If the same import/export route-targets are used in the two redundant DC GWs, VXLAN binding as well as a fec129 spoke-sdp binding will be established between the two DGWs, creating a loop. To avoid creating a loop, the router will allow the establishment of an EVPN VXLAN binding and an sdp-binding to the same far-end, but the sdp-binding will be kept operationally down. Only the VXLAN binding will be operationally up.
5.12.3. Use of the unknown-mac-route
This section describes the behavior of the EVPN-VXLAN service in the router when the unknown-mac-route and BGP-MH are configured at the same time.
The use of E-VPN, as the control plane of NVO networks in the DC, provides a significant number of benefits as described in draft-ietf-bess-evpn-overlay.
However, there is a potential issue that must be addressed when a VPLS DCI is used for an NVO3-based DC: all the MAC addresses learned from the WAN side of the VPLS must be advertised by BGP E-VPN updates. Even if optimized BGP techniques like RT-constraint are used, the number of MAC addresses to advertise or withdraw (in case of failure) from the DC GWs can be difficult to control and overwhelming for the DC network, especially when the NVEs reside in the hypervisors.
The 7750 SR, 7450 ESS, and 7950 XRS solution to this issue is based on the use of an unknown-mac-route address that is advertised by the DC PEs. By using this unknown-mac-route advertisement, the DC tenant may decide to optionally turn off the advertisement of WAN MAC addresses in the DC GW, therefore, reducing the control plane overhead and the size of the FDB tables in the NVEs.
The use of the unknown-mac-route is optional and helps to reduce the amount of unknown-unicast traffic within the data center. All the receiving NVEs supporting this concept will send any unknown-unicast packet to the owner of the unknown-mac-route, as opposed to flooding the unknown-unicast traffic to all other NVEs that are part of the same VPLS.
| Note: Although the router can be configured to generate and advertise the unknown-mac-route, the router will never honor the unknown-mac-route and will flood to the TLS-flood list when an unknown-unicast packet arrives at an ingress SAP/sdp-binding. |
The use of the unknown-mac-route assumes the following:
- A fully virtualized DC where all the MACs are control-plane learned, and learned previous to any communication (no legacy TORs or VLAN connected servers).
- The only exception is MACs learned over the SAPs/SDP-bindings that are part of the BGP-MH WAN site-id. Only one site-id is supported in this case.
- No other SAPs/SDP-bindings out of the WAN site-id are supported, unless ONLY static MACs are used on those SAPs/SDP-bindings.
Therefore, when unknown-mac-route is configured, it will only be generated when one of the following applies:
- No site is configured and the service is operationally UP.
- A BGP-MH site is configured AND the DC GW is Designated Forwarder (DF) for the site. In case of BGP-MH failover, the unknown-mac-route will be withdrawn by the former DF and advertised by the new DF.
5.13. EVPN for VXLAN in R-VPLS Services
Figure 136 shows a DC with a Layer-2 service that carries the traffic for a tenant who extends a subnet within the DC, while the DC GW is the default gateway for all the hosts in the subnet. The DC GW function is carried out by the 7750 SR, 7450 ESS, and 7950 XRS where an R-VPLS instance exists for that particular tenant. Within the DC, the tenant will have VPLS instances in all the NVE devices where they require connectivity (such VPLS instances can be instantiated in TORs, Nuage VRS, VSG, and so on). The WAN connectivity will be based on existing IP-VPN features.
In this model, the DC GW routers will be configured with a R-VPLS (bound to the VPRN that provides the WAN connectivity) per tenant that will provide the VXLAN connectivity to the Nuage VPLS instances. This model provides inter-subnet forwarding for L2-only TORs and other L2 DC NVEs.
On the router:
- The VPRN will be configured with an interface bound to the backhaul R-VPLS. That interface will be a regular IP interface (IP address configured or possibly a Link Local Address if IPv6 is added).
- The VPRN can support other numbered interfaces to the WAN or even to the DC.
- The R-VPLS will be configured with the BGP, BGP-EVPN and VXLAN (VNI) parameters.
On the Nuage VSGs and NVEs:
- Regular VPLS service model with BGP EVPN and VXLAN parameters.
Other considerations:
- Route-type 2 routes with MACs and IPs will be advertised. Some considerations about MAC+IP and ARP/ND entries are:
- The 7750 SR will advertise its IRB MAC+IP in a route type 2 route and possibly the VRRP vMAC+vIP if it runs VRRP and the 7750 SR is the master. In both cases, the MACs will be advertised as static MACs, therefore, protected by the receiving PEs.
- If the 7750 SR VPRN interface is configured with one or more additional secondary IP addresses, they will all be advertised in routes type 2, as static MACs.
- The 7750 SR will process route-type 2 routes as usual, populating the FDB with the received MACs and the VPRN ARP/ND table with the MAC and IPs respectively.

Note: ND entries received from the EVPN are installed as "Router" entries. The ARP/ND entries coming from the EVPN will be tagged as “EVPN”:
- When a VPLS containing proxy-ARP/proxy-ND entries is bound to a VPRN (allow-ip-int-bind) all the proxy-ARP/proxy-ND entries are moved to the VPRN ARP/ND table. ARP/ND entries will be also moved to proxy-ARP/proxy-ND entries if the VPLS is unbound.
- EVPN will not program EVPN-received ARP/ND entries if the receiving VPRN has no IP addresses for the same subnet. The entries will be added when the IP address for the same subnet is added.
- Static ARP/ND entries have precedence over dynamic and EVPN ARP/ND entries.
- VPRN interface binding to VPLS service will bring down the VPRN interface operational status, if the VPRN interface mac or the VRRP mac matches a static-mac or OAM mac configured in the associated VPLS service. If that is the case, a trap will be generated.
- Redundancy will be handled by VRRP. The 7750 SR master will advertise vMAC and vIP, as discussed, including the mac mobility extended community and the sticky bit.
5.14. EVPN for VXLAN in IRB Backhaul R-VPLS Services and IP Prefixes
Figure 137 shows a Layer 3 DC model, where a VPRN is defined in the DC GWs, connecting the tenant to the WAN. That VPRN instance will be connected to the VPRNs in the NVEs by means of an IRB backhaul R-VPLS. Since the IRB backhaul R-VPLS provides connectivity only to all the IRB interfaces and the DC GW VPRN is not directly connected to all the tenant subnets, the WAN ip-prefixes in the VPRN routing table must be advertised in EVPN. In the same way, the NVEs will send IP prefixes in EVPN that will be received by the DC GW and imported in the VPRN routing table.
| Note: To generate or process IP prefixes sent or received in EVPN route type 5, the support for IP route advertisement must be enabled in BGP-EVPN. This is performed through the bgp-evpn>ip-route-advertisement command. This command s disabled by default and must be explicitly enabled. The command is tied to the allow-ip-int-bind command required for R-VPLS. |
Note that local router interface host addresses are not advertised in EVPN by default. To advertise them, the ip-route-advertisement incl-host command must be enabled. For example:
For the case displayed by the output above, the behavior is the following:
- ip-route-advertisement only local subnet (default) - 10.1.1.0/24 is advertised
- ip-route-advertisement incl-host local subnet, host - 10.1.1.0/24 and 10.1.1.100/32 are advertised
Below is an example of VPRN (500) with two IRB interfaces connected to backhaul R-VPLS services 501 and 502 where EVPN-VXLAN runs:
When the above commands are enabled, the router will:
- Receive route-type 5 routes and import the IP prefixes and associated IP next-hops into the VPRN routing table.
- If the route-type 5 is successfully imported by the router, the prefix included in the route-type 5 (for example, 10.0.0.0/24), will be added to the VPRN routing table with a next-hop equal to the GW IP included in the route (for example, 192.0.0.1. that refers to the IRB IP address of the remote VPRN behind which the IP prefix sits).
- When the router receives a packet from the WAN to the 10.0.0.0/24 subnet, the IP lookup on the VPRN routing table will yield 192.0.0.1 as the next-hop. That next-hop will be resolved to a MAC in the ARP table and the MAC resolved to a VXLAN tunnel in the FDB table

Note: IRB MAC and IP addresses are advertised in the IRB backhaul R-VPLS in routes type 2.
- Generate route-type 5 routes for the IP prefixes in the associated VPRN routing table.
- For example, if VPRN-1 is attached to EVPN R-VPLS 1 and EVPN R-VPLS 2, and R-VPLS 2 has bgp-evpn ip-route-advertisement configured, the 7750 SR will advertise the R-VPLS 1 interface subnet in one route-type 5.
- Routing policies can filter the imported and exported IP prefix routes accordingly.
The VPRN routing table can receive routes from all the supported protocols (BGP-VPN, OSPF, IS-IS, RIP, static routing) as well as from IP prefixes from EVPN, as shown below:
The following considerations apply:
- The route Preference for EVPN IP prefixes is 169.
- BGP IP-VPN routes have a preference of 170 by default, therefore, if the same route is received from the WAN over BGP-VPRN and from BGP-EVPN, then the EVPN route will be preferred.
- When the same route-type 5 prefix is received from different GW IPs, ECMP is supported if configured in the VPRN.
- All routes in the VPRN routing table (as long as they do not point back to the EVPN R-VPLS interface) are advertised via EVPN.
Although the description above is focused on IPv4 interfaces and prefixes, it applies to IPv6 interfaces too. The following considerations are specific to IPv6 VPRN R-VPLS interfaces:
- IPv4 and IPv6 interfaces can be defined on R-VPLS IP interfaces at the same time (dual-stack).
- The user may configure specific IPv6 Global Addresses on the VPRN R-VPLS interfaces. If a specific Global IPv6 Address is not configured on the interface, the Link Local Address interface MAC/IP will be advertised in a route type 2 as soon as IPv6 is enabled on the VPRN R-VPLS interface.
- Routes type 5 for IPv6 prefixes will be advertised using either the configured Global Address or the implicit Link Local Address (if no Global Address is configured).If more than one Global Address is configured, normally the first IPv6 address will be used as GW IP. The "first IPv6 address" refers to the first one on the list of IPv6 addresses shown via show router <id> interface <interface> IPv6 or via SNMP.The rest of the addresses will be advertised only in MAC-IP routes (Route Type 2) but not used as GW IP for IPv6 prefix routes.
5.15. EVPN for VXLAN in EVPN Tunnel R-VPLS Services
Figure 138 shows an L3 connectivity model that optimizes the solution described in EVPN for VXLAN in IRB Backhaul R-VPLS Services and IP Prefixes. Instead of regular IRB backhaul R-VPLS services for the connectivity of all the VPRN IRB interfaces, EVPN tunnels can be configured. The main advantage of using EVPN tunnels is that they don't need the configuration of IP addresses, as regular IRB R-VPLS interfaces do.
In addition to the ip-route-advertisement command, this model requires the configuration of the config>service>vprn>if>vpls <name> evpn-tunnel.
| Note: The evpn-tunnel can be enabled independently of ip-route-advertisement, however, no route-type 5 advertisements will be sent or processed in that case. |
The example below shows a VPRN (500) with an EVPN-tunnel R-VPLS (504):
A specified VPRN supports regular IRB backhaul R-VPLS services as well as EVPN tunnel R-VPLS services.
| Note: EVPN tunnel R-VPLS services do not support SAPs or SDP-binds. |
The process followed upon receiving a route-type 5 on a regular IRB R-VPLS interface differs from the one for an EVPN-tunnel type:
- IRB backhaul R-VPLS VPRN interface:
- When a route-type 2 that includes an IP prefix is received and it becomes active, the MAC/IP information is added to the FDB and ARP tables. This can be checked with the show>router>arp command and the show>service>id>fdb detail command.
- When route -type 5 is received and becomes active for the R-VPLS service, the IP prefix is added to the VPRN routing table, regardless of the existence of a route-type 2 that can resolve the GW IP address. If a packet is received from the WAN side and the IP lookup hits an entry for which the GW IP (IP next-hop) does not have an active ARP entry, the system will use ARP to get a MAC. If ARP is resolved but the MAC is unknown in the FDB table, the system will flood into the TLS multicast list. Routes type 5 can be checked in the routing table with the show>router>route-table command and the show>router>fib command.
- EVPN tunnel R-VPLS VPRN interface:
- When route -type 2 is received and becomes active, the MAC address is added to the FDB (only).
- When a route-type 5 is received and active, the IP prefix is added to the VPRN routing table with next-hop equal to EVPN tunnel: GW-MAC.For example, ET-d8:45:ff:00:01:35, where the GW-MAC is added from the GW-MAC extended community sent along with the route-type 5.If a packet is received from the WAN side, and the IP lookup hits an entry for which the next-hop is a EVPN tunnel: GW-MAC, the system will look up the GW-MAC in the FDB. Usually a route-type 2 with the GW-MAC is previously received so that the GW-MAC can be added to the FDB. If the GW-MAC is not present in the FDB, the packet will be dropped.
- IP prefixes with GW-MACs as next-hops are displayed by the show router command, as shown below:
The GW-MAC as well as the rest of the IP prefix BGP attributes are displayed by the show>router>bgp>routes>evpn>ip-prefix command.
EVPN tunneling is also supported on IPv6 VPRN interfaces. When sending IPv6 prefixes from IPv6 interfaces, the GW-MAC in the route type 5 (IP-prefix route) is always zero. If no specific Global Address is configured on the IPv6 interface, the routes type 5 for IPv6 prefixes will always be sent using the Link Local Address as GW-IP. The following example output shows an IPv6 prefix received via BGP EVPN.
5.16. DC GW integration with the Nuage Virtual Services Directory (VSD)
The Nuage VSD (Virtual Services Directory) provides automation in the Nuage DC. The VSD is a programmable policy and analytics engine. It provides a flexible and hierarchical network policy framework that enables IT administrators to define and enforce resource policies.
The VSD contains a multi-tenant service directory that supports role-based administration of users, computing, and network resources. The VSD also manages network resource assignments such as IP addresses and ACLs.
To communicate with the Nuage controllers and gateways (including the 7750 SR, 7450 ESS, or 7950 XRS DC GW), VSD uses an XMPP (eXtensible Messaging and Presence Protocol) communication channel. The router can receive service parameters from the Nuage VSD through XMPP and add them to the existing VPRN/VPLS service configuration.
| Note: The service must be pre-provisioned in the router using the CLI, SNMP, or other supported interfaces. The VSD will only push a limited number of parameters into the configuration. This router – VSD integration model is known as a Static-Dynamic provisioning model, because only a few parameters are dynamically pushed by VSD, as opposed to a Fully Dynamic model, where the entire service can be created dynamically by VSD. |
The router – VSD integration comprises the following building blocks:
- An XMPP interface to the DC XMPP server, through which the router can discover the Data Center Nuage VSDs and select a specified VSD for each VPLS/VPRN service.
- The configuration of vsd-domains on those services where VSD will dynamically provision parameters. As part of the static provisioning of a service, the user will configure a domain name (that will be used between VSD and 7750 SR) using a new CLI command vsd-domain name. Any parameters sent by the VSD for an existing service will contain the vsd-domain. Based on that tag, the router will add the required configuration changes to the correct service.
- The dynamic provisioning of parameters in the following four use-cases:
- L2-DOMAIN: To attach a service at the gateway to a Layer-2 (Ethernet) domain in the data center with no routing at the gateway, a VPLS service should be associated with a vsd-domain of type l2-domain. When the appropriate configuration for the domain is present/added at the VSD, the VSD will dynamically add the VXLAN VNI and BGP export and import route-targets to exchange DC EVPN routes with the VPLS service.
- L2-DOMAIN-IRB: To attach a service at the gateway to a Layer-2 (Ethernet) domain in the data center with routing at the gateway, an R-VPLS service should be associated with a vsd-domain of type l2-domain-irb. When the appropriate configuration for the domain is present/added at the VSD, the VSD will dynamically add the VXLAN VNI and BGP export and import route-targets to exchange DC EVPN routes with the R-VPLS service.
- VRF-GRE: To attach a service at the gateway to a layer 3 domain (with GRE transport) in the data center, a VPRN service should be associated with a vsd-domain of type vrf-gre. When the appropriate configuration for the domain is present/added at the VSD, the VSD will dynamically add the BGP export and import route-targets to exchange DC IP VPN routes with the VPRN service.
- VRF-VXLAN: To attach a service at the gateway to a layer 3 domain (with VXLAN transport) in the data center, an R-VPLS service (linked to an EVPN-tunnel with ip-route-advertisement enabled) should be associated with a vsd-domain of type vrf-vxlan. When the appropriate configuration for the domain is present/added at the VSD, the VSD will dynamically add the VXLAN VNI and BGP export and import route-targets to exchange DC EVPN routes with the backhaul R-VPLS connected to the data center VPRN service.
These building blocks are described in more detail in the following subsections.
5.16.1. XMPP Interface on the DC GW
The Extensible Messaging and Presence Protocol is an open technology for real-time communication using XML (Extensible Markup Language) as the base format for exchanging information. The XMPP provides a way to send small pieces of XML from one entity to another in close to real time.
In a Nuage DC, an XMPP ejabberd server will have an interface to the Nuage VSD as well as the Nuage VSC/VSG and the 7750 SR, 7450 ESS, or 7950 XRS DC GW.
Figure 145 shows the basic XMPP architecture in the data center. While a single XMPP server is represented in the diagram, XMPP allows for easy server clustering and performs message replication to the cluster. It is similar to how BGP can scale and replicate the messages through the use of route reflectors.
Also the VSD is represented as a single server, but a cluster of VSD servers (using the same data base) will be a very common configuration in a DC.
Figure 145: Basic XMPP Architecture
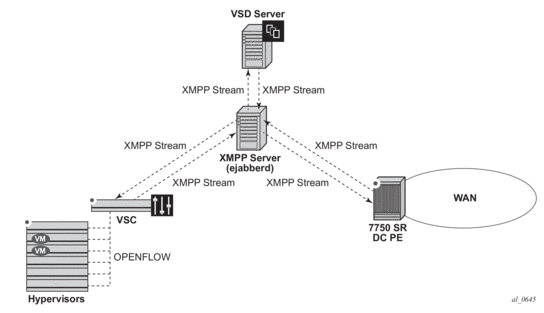
In the Nuage solution, each XMPP client, including the 7750 SR, 7450 ESS, and 7950 XRS, is referred to with a JID (JabberID) in the following format: username@xmppserver.domain. The xmppserver.domain points to the XMPP Server.
To enable the XMPP interface on the 7750 SR, 7450 ESS, or 7950 XRS, the following command must be added to indicate to which XMPP server address the DC GW has to register, as well as the router’s JID:
Where:
- [domain-name <fqdn>] is the domain portion of the JID.
- <user-name> and <password> is the username:password portion of the JID of the router acting as an XMPP client. Plain/MD5/anonymous authentication is supported.
- The user can choose not to configure the username portion of the JID. In that case, an in-band registration will be attempted, using the chassis MAC as username.
- When the xmpp server is properly configured and no shutdown, the 7750 SR will try to establish a TCP session with the XMPP server through the management interface first. If it fails to establish communication, the 7750 SR will use an in-band communication and will use its system IP as source IP address. Shutdown will not remove the dynamic configs in all the services. No server will remove all the dynamic configs in all the services.
- Only one xmpp server can be configured.
| Note: The DNS must be configured on the router so that the XMPP server name can be resolved. XMPP relies on the Domain Name System (DNS) to provide the underlying structure for addressing, instead of using raw IP addresses. The DNS is configured using the following bof commands: bof primary-dns, bof secondary-dns, bof dns-domain. |
After the XMPP server is properly configured, the router can generate or receive XMPP stanza elements, such as presence and IQ (Information/Query) messages. IQ messages are used between the VSD and the router to request and receive configuration parameters. The status of the XMPP communication channel can be checked with the following command:
In addition to the XMPP server, the router must be configured with a VSD system-id that uniquely identifies the router in the VSD:
After the above configuration is complete, the router will subscribe to a VSD XMPP PubSub node to discover the available VSD servers. Then, the router will be discovered in the VSD UIs. On the router, the available VSD servers can be shown with the following command.
5.16.2. Overview of the Static-Dynamic VSD Integration Model
In the Static-Dynamic integration model, the DC and DC GW management entities can be the same or different. The DC GW operator will provision the required VPRN and VPLS services with all the parameters needed for the connectivity to the WAN. VSD will only push the required parameters so that those WAN services can be attached to the existing DC domains.
Figure 146 shows the workflow for the attachment of the WAN services defined on the DC GW to the DC domains.
Figure 146: WAN Services Attachment Workflow
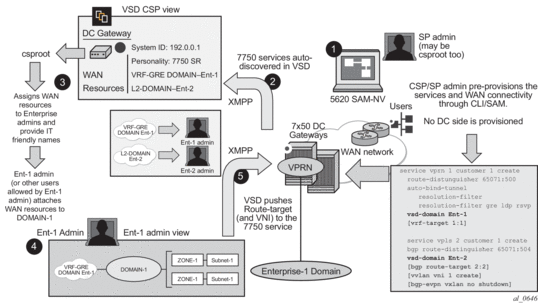
The Static-Dynamic VSD integration model can be summarized in the steps shown in Figure 146 and described as follows:
5.16.2.1. Step 1
The WAN or SP (Service Provider) administrator (which can be also the DC or Cloud Service Provider administrator) provisions the WAN services with all the parameters required for the connectivity to the WAN. This configuration is performed through the regular management interfaces, for example, CLI or SNMP. In the example above, there are two services created by the SP:
- VPRN 1 – associated with vsd-domain Ent-1, which is a VRF-GRE domain.
- VPLS 2 – associated with vsd-domain Ent-2, which is an L2-DOMAIN
| Note: The parameters between brackets “[..]” are not configured at this step. They will be pushed by the VSD through XMPP. |
5.16.2.2. Step 2
The router communicates with the VSD through the XMPP channel and lets VSD know about its presence and available domains: Ent-1 and Ent-2. In the VSD’s User Interface (UI), the router will show up as DC GW with its System ID, personality (for example, router) and the available WAN resources, that is, vsd-domains Ent-1 and Ent-2.
5.16.2.3. Step 3
At VSD, the Cloud Service Provider administrator will assign the available WAN resources to Enterprises defined in VSD. In this example, VRF-GRE Ent-1 will be assigned to Enterprise-1 and L2-DOMAIN Ent-2 to Enterprise-2.
5.16.2.4. Step 4
Each Enterprise administrator will have visibility of their own assigned WAN resource and will attach it to an existing DC Domain, assuming that both the DC domain and WAN resource are compatible. For instance, a VRF-GRE domain can only be attached to an L3 domain in the DC that uses GRE as transport.
5.16.2.5. Step 5
When the Enterprise administrator attaches the WAN resource to the DC domain, VSD will send the required configuration parameters to the DC GW through the XMPP channel:
- In the case of the VRF-GRE domain, VSD will only send the vrf-target required for the service attachment to the DC domain.
- In the case of the L2-DOMAIN, VSD will send the route-target (in the service>bgp or vsi-import/export contexts) as well as the vxlan vni and the bgp-evpn vxlan no shutdown commands.
WAN resources can also be detached from the DC domains.
5.16.3. VSD-Domains and Association to Static-Dynamic Services
In the Static-Dynamic integration model, VSD can only provision certain parameters in VPLS and/or VPRN services. When VSD and the DC GW exchange XMPP messages for a specified service, they use vsd-domains to identify those services. A vsd-domain is a tag that will be used by the 7750 SR, 7450 ESS, or 7950 XRS router and the VSD to correlate a configuration to a service. When redundant DC GWs are available, the vsd-domain for the same service can have the same or a different name in the two redundant DC GWs.
There are four different types of vsd-domains that can be configured in the router:
- L2-DOMAIN – it will be associated with a VPLS service in the router and, in VSD, it will be attached to an existing Nuage L2-DOMAIN. This type of domain will be used for extending Layer-2 subnets to the WAN connected to the DC GW.
- L2-DOMAIN-IRB – it will be associated with a R-VPLS service in the router and, in VSD, it will be attached to an existing Nuage L2-DOMAIN. In this case, the DC GW will be the default gateway for all the VMs and hosts in the Nuage L2-DOMAIN.
- VRF-GRE – this domain type will be associated with a VPRN service in the router that uses GRE tunnels and MP-BGP VPN-IPv4 to provide connectivity to the DC. In VSD, it will be attached to an existing Nuage L3-DOMAIN, when GRE is configured as tunnel-type for L3-DOMAINs.
- VRF-VXLAN – this domain type will be associated with a router R-VPLS service (connected to a VPRN with an evpn-tunnel VPLS interface) that uses VXLAN tunnels and EVPN to provide connectivity to the DC. In VSD, it will be attached to an existing Nuage L3-DOMAIN, when VXLAN is configured as the tunnel-type for L3-DOMAINs.
The domains will be configured in the config>service# context and assigned to each service.
5.16.3.1. VSD-Domain Type L2-DOMAIN
L2-DOMAIN VSD-domains will be associated with VPLS services configured without a route-target and vxlan VNI. VSD will configure the route-target and VNI in the router VPLS service. Some considerations related to L2-DOMAINs are:
- ip-route-advertisement and allow-ip-int-bind commands are not allowed in this type of domain. An example of configuration for an L2-DOMAIN association is shown below:
- The VSD will push a dynamic vxlan vni and route-target that the router will add to the VPLS service. For the route-target, the system will check whether the VPLS service has a configured policy:
- If there is no vsi-import/export policy, the received dynamic route-target will be added in the vpls>bgp> context, and will be used for all the BGP families in the service.
- If there is a vsi-import/export policy, the dynamic route-target will be added to the policy, in an auto-created community that will be shown with the following format: “_VSD_svc-id”. That community will be added to dynamically created entries 1000 and 2000 in the first policy configured in the service vsi-import and vsi-export commands. This allows the user to allocate entries before entries 1000 and 2000 in case other modifications have to be made (user entries would have an action next-entry). An example of the auto-generated entries is shown below:
5.16.3.2. VSD-Domain Type L2-DOMAIN-IRB
L2-DOMAIN-IRB VSD-domains will be associated with R-VPLS services configured without a static route-target and vxlan VNI. VSD will configure the dynamic route-target and VNI in the router VPLS service. The same considerations described for L2-DOMAINs apply to L2-DOMAIN-IRB domains with one exception: allow-ip-int-bind is now allowed.
5.16.3.3. VSD-Domain Type VRF-GRE
VRF-GRE VSD-domains will be associated with VPRN services configured without a static route-target. In this case, the VSD will push a route-target that the router will add to the VPRN service. The system will check whether the VPRN service has a configured policy:
- If there is no vrf-import policy, the received dynamic route-target will be added in the vprn> context.
- If there is a vrf-import policy, the dynamic route-target will be added to the policy, in an auto-created community that will be shown with the following format: “VSD_svc-id” in a similar way as in L2-DOMAINs.

Note: In cases where a vrf-import policy is used, the user will provision the WAN route-target statically in a vrf-export policy. This route-target will also be used for the routes advertised to the DC.
An example of the auto-generated entry is shown below:
5.16.3.4. VSD-Domain Type VRF-VXLAN
VRF-VXLAN VSD-domains will be associated with R-VPLS services configured without a static route-target and vxlan VNI. VSD will configure the dynamic route-target and VNI in the router VPLS service. Some considerations related to VRF-VXLAN domains are:
- ip-route-advertisement, allow-ip-int-bind, as well as the VPRN evpn-tunnel commands are now required for this type of VSD-domain. An example of configuration for a VRF-VXLAN association is shown below:
- The VSD will push a dynamic vxlan VNI and route-target that the router will add to the VPLS service. For the route-target, the system will check whether the VPLS service has a configured policy and will push the route-target either in the service context or the vsi-import/export policies, as described in the section for L2-DOMAINs.
The following commands help show the association between the 7750 SR, 7450 ESS, and 7950 XRS router services and VSD-domains, as well as statistics and configuration errors sent/received to/from VSD.
5.17. Fully-Dynamic VSD Integration Model
In the Static-Dynamic VSD integration model, the VPLS/VPRN service, as well as most of the parameters, must be provisioned "statically" through usual procedures (CLI, SNMP, and so on). VSD will "dynamically" send the parameters that are required for the attachment of the VPLS/VPRN service to the L2/L3 domain in the Data Center. In the Fully-Dynamic VSD integration model, the entire VPLS/VPRN service configuration will be dynamically driven from VSD and no static configuration is required. Through the existing XMPP interface, the VSD will provide the 7750 SR, 7450 ESS, and 7950 XRS routers with a handful of parameters that will be translated into a service configuration by a python-script. This python-script provides an intermediate abstraction layer between VSD and the router, translating the VSD data model into a 7750 SR, 7450 ESS, or 7950 XRS CLI data model.
In this Fully-Dynamic integration model, the DC and DC GW management entities are usually the same. The DC GW operator will provision the required VPRN and VPLS services with all the parameters needed for the connectivity to the WAN and the DC. VSD will push the required parameters so that the router can create the service completely and get it attached to an existing DC domain.
The workflow of the Fully-Dynamic integration model is shown in Figure 147.
Figure 147: Fully-Dynamic VSD Integration Model Workflow
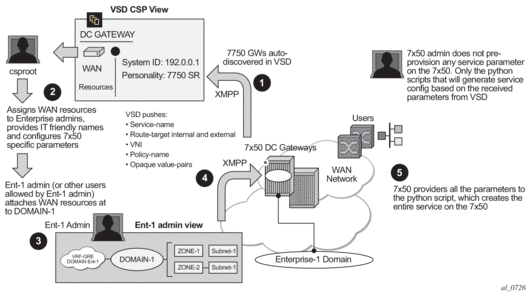
The Fully-Dynamic VSD integration model can be summarized in the steps shown in Figure 147 and described as follows:
5.17.1. Step 1
The 7750 SR, 7450 ESS, or 7950 XRS administrator only needs to provision parameters required for connectivity to the VSD, a service-range, and configure the python script/policy in the system. Provisioning of service parameters is not required.
The service-range defines the service identifiers to include for VSD provisioned services and, once configured, they are protected from CLI changes. The vsd-policy defines the script to be used:
When the router boots up or the gateway configuration is changed, the router sends a message to the VSD indicating its capabilities:
- System-ID
- Name and gateway type
The VSD uses this information to register the router on its list of router GWs.
Once registered, the VSD and router exchange messages where the VSD communicates its list of service-names and their domain-type to the router. Based on this list, the router sends an XMPP IQ message to request the configuration of a specified service.
The 7750 SR, 7450 ESS, or 7950 XRS router will periodically audit the VSD and request a “DIFF” list of Full-Dynamic VSD domains. The VSD keeps a “DIFF” list of domains, that contains the Fully-Dynamic domain names for which the VSD has not received an IQ request from the router for a long time.
The 7750 SR, 7450 ESS, or 7950 XRS CLI user can also audit the VSD to get the DIFF list, or even the “FULL” list of all the domains in the VSD. The following command triggers this audit: tools perform service vsd fd-domain-sync {full|diff}.
5.17.2. Step 2
Concurrently at the VSD, the Cloud Service Provider administrator will assign WAN resources to Enterprises defined in the VSD. In this example, a VRF-GRE domain will be assigned to Enterprise-1.
5.17.3. Step 3
Each Enterprise administrator will have visibility of their own assigned WAN resource and will attach it to an existing DC Domain, assuming that both the DC domain and WAN resource are compatible. For instance, a VRF-GRE domain can only be attached to an L3 domain in the DC that uses GRE as transport.
5.17.4. Step 4
When the Enterprise administrator attaches the service requested by the 7750 SR, 7450 ESS, or 7950 XRS router to the DC domain, the VSD will send the required configuration parameters for that service to the DC GW through the XMPP channel in an IQ Service message, including the following information:
- Service name and service type, where the type can be:
- L2-DOMAIN
- L2-DOMAIN-IRB
- VRF-GRE
- VRF-VXLAN
- Configuration type— Static (for Static-Dynamic model) or Dynamic (for Fully-Dynamic model).
- Internal route-target (RT-i) — Used to export/import the BGP routes sent/received from/to the DC route-reflector.
- External route-target (RT-e) — Used to export/import the BGP routes sent/received from/to the WAN route-reflector. The value can be the same as the RT-i.
- VNI (VXLAN Network Identifier) — Used to configure the EVPN-VXLAN VPLS service on the router (if the domain type is L2-DOMAIN, L2-DOMAIN-IRB, or VRF-VXLAN).
- Metadata — A collection of 'opaque' <key=value> pairs including the rest of the service parameters required for the service configuration at the router.

Note: The keys or values do not need to follow any specific format. The python script interprets and translates them into the router data model.
- Python-policy— Used by the router to find the Python script that will translate the VSD parameters into configuration.
5.17.5. Step 5
When the 7750 SR, 7450 ESS, or 7950 XRS router receives the IQ Service message, it builds a string with all the parameters and passes it to the Python module. The Python module is responsible for creating and activating the service, and, therefore, provides connectivity between the tenant domain and the WAN.
| Note: The python-script cannot access all the CLI commands and nodes in the system. A white-list of nodes and commands is built and Python will only have access to those nodes/commands. The list can be displayed using the following command: tools dump service vsd-services command-list. |
In addition to the white-list, the user can further restrict the allowed CLI nodes to the VSD by using a separate CLI user for the XMPP interface, and associating that user to a profile where the commands are limited. The CLI user for the XMPP interface is configurable:
When the system executes a python-script for VSD commands, the vsd cli-user profile is checked to allow the resulting commands. A single CLI user is supported for VSD, therefore, the operator can configure a single 'profile' to restrict (even further than the whitelist) the CLI commands that can be executed by the VSD Python scripts.
No cli-user means that the system will not perform any authorization checks and the VSD scripts can access any commands that are supported in the white-list.
5.17.6. Python Script Implementation Details
A python-script provides an intermediate abstraction layer between VSD and the router, translating the VSD data model into the 7750 SR, 7450 ESS, or 7950 XRS router CLI data model. VSD will use metadata key=value parameters to provision service specific attributes on the 7750. The XMPP messages get to the 7750 and are passed transparently to the Python module so that the CLI is generated and the service created.
| Note: The CLI generated by the python-script is not saved in the configuration file; it can be displayed by running the info include-dynamic command on the service contexts. The configuration generated by the python-script is protected and cannot be changed by a CLI user. |
The following example shows how the python-script works for a VSD generated configuration:
- The following configuration is added to the 7750 SR. In this case, py-l2 is the python-policy received from VSD that will call the l2domain_service.py python script:
- VSD will send metadata containing the service parameters. This opaque parameter string will be passed to the python script and is composed of tag=value pairs, with the following format:
- In addition, other information provided by the VSD, (domain, vni, rt-i, rt-e, and service type) is bundled with the metadata string and passed to the python script. For example:
The user should consider the following:
- The python script is solely responsible for generating the configuration; no configuration aspects of the Static-Dynamic model are used. The python script must be written in a manner similar to those used by RADIUS Dynamic Business Services. Currently, RADIUS Dynamic Business Services and the Fully-Dynamic VSD model are mutually exclusive, one or the other can operate on the same system, but not both at the same time.
- The following scripts must be defined in order to set up, modify, revert, and tear down the configuration for a service: setup_script(), modify_script(), revert_script(), and teardown_script(). These names must always be the same in all scripts. The revert_script() is only required if the modify_script() is defined, the latter being optional.
- When the configuration for a new domain name is received from the VSD, the metadata and the VSD parameters are concatenated into a single dictionary and setup_script() is called. Within the python script:
- The VSD UI parameters are referenced as vsdParams['rt'], vsdParams ['domain'], and so on.
- The metadata parameters are referenced as vsdParams['metadata'].
- When the startup script is executed, the config>service>vsd>domain is created outside the script context before running the actual script. The teardown script will remove the vsd domain.
- If a specified setup_script() fails, the teardown_script() is invoked.
- When subsequent configuration messages are received from the VSD, the new parameter list is generated again from the VSD message and compared to the last parameter list that was successfully executed.
- If the two strings are identical, no action is taken.
- If there is a difference between the strings, the modify_script() function is called.
- If the modify_script() fails, the revert_script() is invoked. The teardown_script() is invoked if the revert_script() fails or does not exist.
- The python-policy is always present in the attributes received from VSD; if the VSD user does not include a policy name, VSD will include 'default' as the python-policy. Hence, care must be taken to ensure that the 'default' policy is always configured in the 7750.
- If the scripts are incorrect, teardown and modify procedures could leave orphaned objects. An admin mode (enable-vsd-config) is available to enable an administrator to clean up these objects; it is strictly meant for cleaning orphaned objects only.

Note: The CLI configured services cannot be modified when the user is in enable-vsd-config mode.
- Unless the CLI user enters the enable-vsd-config mode, changes of the dynamic created services are not allowed in the CLI. However, changes through SNMP are allowed.
- The command tools perform service vsd evaluate-script is introduced to allow the user to test their setup and to modify and tear down python scripts in a lab environment without the need to be connected to a VSD. The successful execution of the command for action setup will create a vsd domain and the corresponding configuration, just as the system would do when the parameters are received from VSD.
The following example shows the use of the tools perform service vsd evaluate-script command:
The following example output shows a python-script that can set up or tear down L2-DOMAINs.
For instance, assuming that the VSD sends the following:
The system will execute the setup script as follows:
5.17.7. Provisioning Filters using the VSD Fully Dynamic Model
IP, IPv6, and MAC filters can be configured from the VSD within the context of the Fully Dynamic XMPP provisioning model for VPRN and VPLS services.
The VSD filters or filter entries are intended for use in two DC environments:
- Dedicated DC GW ModelThe DC GW services and filter policies in this DC environment are completely owned and self-managed by the Nuage VSD. In this model, the filter cannot be changed and/or deleted by any management or policy interface other than the VSD; changes are not saved in the configuration file.To enable the VSD to configure a filter, the python setup script must contain a config filter ip/ipv6/mac-filter _tmnx_vsd_<filter_id> create statement. The VSD exclusively manages the removal and change of such filters.The following excerpt shows a sample setup script to create a filter.def setup_script(vsdParams):<snip>filter_id = metadata[' filter']<snip>dyn.add_cli("""config filter ip-filter _tmnx_vsd_%(filter_id)s createentry 10 creatematch protocol tcpdst-port eq 80exitactionforwardexit<snip>
- PE/BNG + DC GW Combination ModelThe filter and point of embedding insertion in this DC environment is owned by a WAN controller. In this model, the entries in the embedded filter are populated by the VSD.The WAN controller creates a filter and the embedding point (through a management interface other than the VSD) by using the config filter ip/ipv6/mac-filter <id> embed-filter vsd _tmnx_vsd_<filter-id> command. When this command is run, a filter with the name _tmnx_vsd_<filter-id> will be auto-generated; the python scripts can use that name to create entries driven by the VSD.
5.18. Layer 2 Multicast Optimization for VXLAN (Assisted-Replication)
The Assisted-Replication feature for IPv4 VXLAN tunnels (both Leaf and Replicator functions) is supported in compliance with the non-selective mode described in draft-ietf-bess-evpn-optimized-ir.
The Assisted-Replication feature is a Layer 2 multicast optimization feature that helps software-based PE and NVEs with low-performance replication capabilities to deliver broadcast and multicast Layer 2 traffic to remote VTEPs in the VPLS service.
The EVPN and proxy-ARP/ND capabilities can reduce the amount of broadcast and unknown unicast in the VPLS service; ingress replication is sufficient for most use cases in this scenario. However, when multicast applications require a significant amount of replication at the ingress node, software-based nodes struggle due to their limited replication performance. By enabling the Assisted-Replication Leaf function on the software-based SR-series router, all the broadcast and multicast packets are sent to a 7x50 router configured as a Replicator, which replicates the traffic to all the VTEPs in the VPLS service on behalf of the Leaf. This guarantees that the broadcast or multicast traffic is delivered to all the VPLS participants without any packet loss caused by performance issues.
The Leaf or Replicator function is enabled per VPLS service by the config>service>vpls>vxlan>assisted-replication {replicator|leaf} command. In addition, the Replicator requires the configuration of an Assisted-Replication IP (AR-IP) address. The AR-IP loopback address indicates whether the received VXLAN packets have to be replicated to the remote VTEPs. The AR-IP address is configured using the config>service>system>vxlan>assisted-replication-ip <ip-address> command.
Based on the assisted-replication {replicator|leaf} configuration, the SR-series router can behave as a Replicator (AR-R), Leaf (AR-L), or Regular Network Virtualization Edge (RNVE) router. An RNVE router does not support the Assisted-Replication feature. Because it is configured with no assisted replication, the RNVE router ignores the AR-R and AR-L information and replicates to its flooding list where VTEPs are added based on the regular ingress replication routes.
5.18.1. Replicator (AR-R) Procedures
An AR-R configuration is shown in the following example.
In this example configuration, the BGP advertises a new inclusive multicast route with tunnel-type = AR, type (T) = AR-R, and tunnel-id = originating-ip = next-hop = assisted-replication-ip (IP address 2.2.2.2 in the preceding example). In addition to the AR route, the AR-R sends a regular IR route if ingress-repl-inc-mcast-advertisement is enabled.
| Note: You should disable the ingress-repl-inc-mcast-advertisement command if the AR-R does not have any SAP/SDP-bindings and is used solely for Assisted-Replication functions. |
The AR-R builds a flooding list composed of ACs (SAPs and SDP-bindings) and VXLAN tunnels to remote nodes in the VPLS. All objects in the flooding list are broadcast/multicast (BM) and unknown unicast (U) capable. The following sample output of the show service id vxlan command shows that the VXLAN destinations in the flooding list are tagged as “BUM”.
When the AR-R receives a BUM packet on an AC, the AR-R forwards the packet to its flooding list (including the local ACs and remote VTEPs).
When the AR-R receives a BM packet on a VXLAN tunnel, it checks the IP DA of the underlay IP header and performs the following BM packet processing.
| Note: The AR-R function is only relevant to BM packets; it does not apply to unknown unicast packets. If the AR-R receives unknown unicast packets, it sends them to the flooding list, skipping the VXLAN tunnels. |
- If the destination IP matches its AR-IP, the AR-R forwards the BM packet to its flooding list (ACs and VXLAN tunnels). The AR-R performs source suppression to ensure that the traffic is not sent back to the originating Leaf.
- If the destination IP matches its regular VXLAN termination IP (IR-IP), the AR-R skips all the VXLAN tunnels from the flooding list and only replicates to the local ACs. This is the default Ingress Replication (IR) behavior.
5.18.2. Leaf (AR-L) procedures
An AR-L is configured as shown in the following example.
In this example configuration, the BGP advertises a new inclusive multicast route with a tunnel-type = IR, type (T) = AR-L and tunnel-id = originating-ip = next-hop = IR-IP (IP address terminating VXLAN normally, either system-ip or vxlan-src-vtep address).
The AR-L builds a single flooding list per service but controlled by the BM and U flags. These flags are displayed in the following show service id vxlan command sample output.
The AR-L creates the following VXLAN destinations when it receives and selects a Replicator-AR route or the Regular-IR routes.
- A VXLAN destination to each remote PE that sent an IR route. These bindings have the U flag set.
- A VXLAN destination to the selected AR-R. These bindings have only the BM flag set; the U flag is not set.
- The non-selected AR-Rs create a binding with flag “-” (in the CPM) that is displayed by the show service id vxlan command. Although the VXLAN destinations to non-selected AR-Rs do not carry any traffic, the destinations count against the total limit and must be considered when accounting for consumed VXLAN destinations in the router.
The BM traffic is only sent to the selected AR-R, whereas the U (unknown unicast) traffic is sent to all the destinations with the U flag.
The AR-L performs per-service load-balancing of the BM traffic when two or more AR-Rs exist in the same service. The AR Leaf creates a list of candidate PEs for each AR-R (ordered by IP and VNI; candidate 0 being the lowest IP and VNI). The replicator is selected out of a modulo function of the service-id and the number of replicators, as shown in the following sample output.
A change in the number of Replicator-AR routes (for example, if a route is withdrawn or a new route appears) affects the result of the hashing, which may cause a different AR-R to be selected.
| Note: An AR-L waits for the configured replicator-activation-time before sending the BM packets to the AR-R. In the interim, the AR-L uses regular ingress replication procedures. This activation time allows the AR-R to program the Leaf VTEP. If the timer is zero, the AR-R may receive packets from a not-yet-programmed source VTEP, in which case it will discard the packets. |
The following list summarizes other aspects of the AR-L behavior.
- When a Leaf receives a BM packet on an AC, it sends the packet to its flood list that includes access SAP/SDP-bindings and VXLAN destinations with BM or BUM flags. If a single AR-R is selected, only a VXLAN destination will include the BM flags.
- Control plane-generated BM packets, such as ARP/ND (when proxy-ARP/ND is enabled) or Eth-CFM, follow the behavior of regular data plane BM packets.
- When a Leaf receives an unknown unicast packet on an AC, it sends the packet to the flood-list, skipping the AR destination because the U flag is set to 0. To avoid packet re-ordering, the unknown unicast packets do not go through the AR-R.
- When a Leaf receives a BUM packet on an overlay tunnel, it forwards the packet to the flood list, skipping the VXLAN tunnels (that is, the packet is sent to the local ACs and never to a VXLAN tunnel). This is the default IR behavior.
- When the last Replicator-AR route is withdrawn, the AR-L removes the AR destination from the flood list and falls back to ingress replication.
Figure 148 shows the expected replication behavior for BM traffic when received at the access on an AR-R, AR-L, or RNVE router. Unknown unicast follows regular ingress replication behavior regardless of the role of the ingress node for the specific service.
Figure 148: AR BM Replication Behavior for a BM Packet
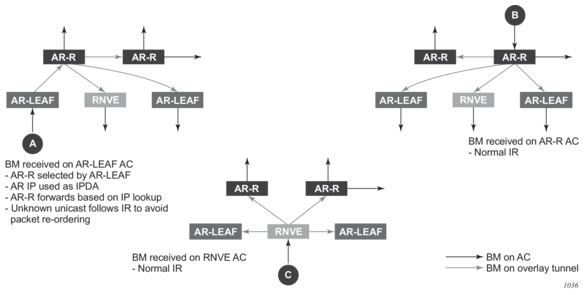
5.18.3. Assisted-Replication Interaction with Other VPLS Features
The Assisted-Replication feature has the following limitations.
- The following features are not supported on the same service where the Assisted-Replication feature is enabled.
- Aggregate QoS per VNI
- VXLAN IPv6 transport
- IGMP-snooping
- Assisted-Replication Leaf and Replicator functions are mutually exclusive within the same VPLS service.
- The Assisted-Replication feature is supported with IPv4 non-system-ip VXLAN termination. However, the configured assisted-replication-ip (AR-IP) must be different from the tunnel termination IP address.
- The AR-IP address must be a /32 loopback interface on the base router.
- The Assisted-Replication feature is only supported in EVPN-VXLAN services (VPLS with bgp-evpn vxlan enabled). Although services with a combination of EVPN-MPLS and EVPN-VXLAN are supported, the Assisted-Replication configuration is only relevant to the VXLAN.
5.19. BGP-EVPN Control Plane for MPLS Tunnels
Table 81 lists all the EVPN routes supported in 7750 SR, 7450 ESS, or 7950 XRS SR OS and their usage in EVPN-VXLAN, EVPN-MPLS, and PBB-EVPN.
| Note: Route type 1 is not required in PBB-EVPN as per RFC 7623. |
Table 81: EVPN Routes and Usage
EVPN Route | Usage | EVPN-VXLAN | EVPN-MPLS | PBB-EVPN |
Type 1 - Ethernet Auto-Discovery route (A-D) | Mass-withdraw, ESI labels, Aliasing | — | Y | — |
Type 2 - MAC/IP Advertisement route | MAC/IP advertisement, IP advertisement for ARP resolution | Y | Y | Y |
Type 3 - Inclusive Multicast Ethernet Tag route | Flooding tree setup (BUM flooding) | Y | Y | Y |
Type 4 - Ethernet Segment route | ES discovery and DF election | — | Y | Y |
Type 5 - IP Prefix advertisement route | IP Routing | Y | Y | — |
RFC 7432 describes the BGP-EVPN control plane for MPLS tunnels. If EVPN multi-homing is not required, two route types are needed to set up a basic EVI (EVPN Instance): MAC/IP Advertisement and the Inclusive Multicast Ethernet Tag routes. If multi-homing is required, the Ethernet Segment and the Auto-Discovery routes are also needed.
The route fields and extended communities for route types 2 and 3 are shown in Figure 142. BGP-EVPN Control Plane for VXLAN Overlay Tunnels The changes compared to their use in EVPN-VXLAN are described below.
EVPN Route Type 3 – Inclusive Multicast Ethernet Tag Route
As in EVPN-VXLAN, route type 3 is used for setting up the flooding tree (BUM flooding) for a specified VPLS service. The received inclusive multicast routes add entries to the VPLS flood list in the 7750 SR, 7450 ESS, and 7950 XRS. Ingress replication, p2mp mLDP and composite tunnels are supported as tunnel types in route type 3 when bgp-evn mpls is enabled
The following route values are used for EVPN-MPLS services:
- Route Distinguisher: taken from the RD of the VPLS service within the BGP context. The RD can be configured or derived from the bgp-evpn evi value.
- Ethernet Tag ID: 0.
- IP address length: always 32.
- Originating router's IP address: carries the system address (IPv4 only).
- PMSI attribute: the PMSI attribute can have different formats depending on the tunnel type enabled in the service.
- Tunnel type = Ingress replication (6)The route is referred to as an Inclusive Multicast Ethernet Tag IR (IMET-IR) route and the PMSI Tunnel Attribute (PTA) fields are populated as follows:
- Flags—Leaf not required.
- MPLS label—Carries the MPLS label allocated for the service in the high-order 20 bits of the label field.Unless bgp-evpn mpls ingress-replication-bum-label is configured in the service, the MPLS label used will be the same as that used in the MAC/IP routes for the service.
- Tunnel end-point—Equal to the originating IP address.
- Tunnel type=p2mp mLDP (2)The route is referred to as an IMET-P2MP route and its PTA fields are populated as follows.
- Flags—Leaf not required.
- MPLS label—0.
- Tunnel end-point—Includes the route node address and an opaque number. This is the tunnel identifier that the leaf-nodes will use to join the mLDP P2MP tree.
- Tunnel type=Composite tunnel (130)The route is referred to as an IMET-P2MP-IR route and its PTA fields are populated as follows.
- Flags—Leaf not required.
- MPLS label 1— 0.
- Tunnel end-point identifier will include the following:MPLS label2—Non-zero, downstream allocated label (like any other IR label). The leaf-nodes will use the label to set up an EVPN-MPLS destination to the root and add it to the default-multicast list.mLDP tunnel identifier—The route node address and an opaque number. This is the tunnel identifier that the leaf-nodes will use to join the mLDP P2MP tree.
IMET-P2MP-IR routes are used in EVIs with a few root nodes and a significant number of leaf-only PEs. In this scenario, a combination of P2MP and IR tunnels can be used in the network, such that the root nodes use P2MP tunnels to send broadcast, Unknown Unicast, and Multicast traffic but the leaf-PE nodes use IR to send traffic to the roots. This use-case is documented in draft-ietf-bess-evpn-etree and the main advantage it offers is the significant savings in P2MP tunnels that the PE/P routers in the EVI need to handle (as opposed to a full mesh of P2MP tunnels among all the PEs in an EVI).
In this case, the root PEs will signal a special tunnel type in the PTA, indicating that they intend to transmit BUM traffic using an mLDP P2MP tunnel but they can also receive traffic over an IR evpn-mpls binding. An IMET route with this special "composite" tunnel type in the PTA is called an IMET-P2MP-IR route and the encoding of its PTA is shown in Figure 149.
Figure 149: Composite p2mp mLDP and IR Tunnels—PTA
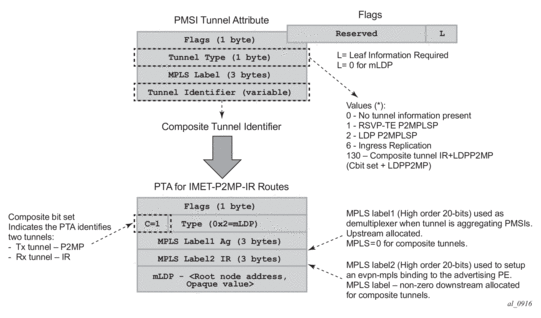
EVPN Route Type 2 - MAC/IP Advertisement Route
The 7750 SR, 7450 ESS, or 7950 XRS router generates this route type for advertising MAC addresses (and IP addresses if proxy-ARP/proxy-ND is enabled). The router generates MAC advertisement routes for the following:
- Learned MACs on SAPs or sdp-bindings—if mac-advertisement is enabled.
- Conditional static MACs—if mac-advertisement is enabled.

Note: The unknown-mac-route is not supported for EVPN-MPLS services.
The route type 2 generated by a router uses the following fields and values:
- Route Distinguisher: Taken from the RD of the VPLS service within the BGP context. The RD can be configured or derived from the bgp-evpn evi value.
- Ethernet Segment Identifier (ESI): Zero for MACs learned from single-homed CEs and different from zero for MACs learned from multi-homed CEs.
- Ethernet Tag ID: 0.
- MAC address length: Always 48.
- MAC Address learned or statically configured.
- IP address and IP address length:
- It will be the IP address associated with the MAC being advertised with a length of 32 (or 128 for IPv6).
- In general, any MAC route without IP will have IPL=0 (IP length) and the IP will be omitted.
- When received, any IPL value not equal to zero, 32, or 128 will discard the route.
- MPLS Label 1: Carries the MPLS label allocated by the system to the VPLS service. The label value is encoded in the high-order 20 bits of the field and will be the same label used in the routes type 3 for the same service unless bgp-evpn mpls ingress-replication-bum-label is configured in the service.
- MPLS Label 2: 0.
- The MAC Mobility extended community: Used for signaling the sequence number in case of mac moves and the sticky bit in case of advertising conditional static MACs. If a MAC route is received with a MAC mobility ext-community, the sequence number and the 'sticky' bit are considered for the route selection.
When EVPN multi-homing is enabled in the system, two more routes are required. Figure 150 shows the fields in routes type 1 and 4 and their associated extended communities.
Figure 150: EVPN Routes Type 1 and 4
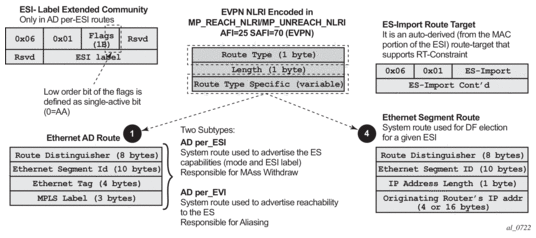
EVPN Route Type 1 - Ethernet Auto-discovery Route (AD route)
The 7750 SR, 7450 ESS, or 7950 XRS router generates this route type for advertising for multi-homing functions. The system can generate two types of AD routes:
- Ethernet AD route per-ESI (Ethernet Segment ID)
- Ethernet AD route per-EVI (EVPN Instance)
The Ethernet AD per-ESI route generated by a router uses the following fields and values:
- Route Distinguisher: Taken from the system level RD or service level RD.
- Ethernet Segment Identifier (ESI): Will contain a 10-byte identifier as configured in the system for a specified ethernet-segment.
- Ethernet Tag ID: MAX-ET (0xFFFFFFFF). This value is reserved and used only for AD routes per ESI.
- MPLS label: 0.
- ESI Label Extended community: Includes the single-active bit (0 for all-active and 1 for single-active) and ESI label for all-active multi-homing split-horizon.
- Route-target extended community: Taken from the service level RT or an RT-set for the services defined on the ethernet-segment.
The system can either send a separate Ethernet AD per-ESI route per service, or a few Ethernet AD per-ESI routes aggregating the route-targets for multiple services. While both alternatives will inter-operate, RFC 7432 states that the EVPN Auto-Discovery per-ES route must be sent with a set of route-targets corresponding to all the EVIs defined on the ethernet-segment. Either option can be enabled using the command: config>service>system>bgp-evpn#ad-per-es-route-target <[evi-rt] | [evi-rt-set route-distinguisher <ip-address>]>
The default option ad-per-es-route-target evi-rt configures the system to send a separate AD per-ES route per service. When enabled, the evi-rt-set option allows the aggregation of routes: A single AD per-ES route with the associated RD (ip-address:1) and a set of EVI route-targets will be advertised (to a maximum of 128). When the number of EVIs defined in the ethernet-segment is significant (hence the number of route-targets), the system will send more than one route. For example:
- AD per-ES route for evi-rt-set 1 will be sent with RD ip-address:1
- AD per-ES route for evi-rt-set 2 will be sent with RD ip-address:2
| Note: When evi-rt-set is configured, no vsi-export policies are possible on the services defined on the ethernet-segment. If vsi-export policies are configured for a service, the system will send an individual AD per-ES route for that service. The maximum standard BGP update size is 4KB, with a maximum of 2KB for the route-target extended community attribute. |
The Ethernet AD per-EVI route generated by a router uses the following fields and values:
- Route Distinguisher: Taken from the service level RD.
- Ethernet Segment Identifier (ESI): Will contain a 10-byte identifier as configured in the system for a specified ethernet-segment.
- Ethernet Tag ID: 0.
- MPLS label: Encodes the unicast label allocated for the service (high-order 20 bits).
- Route-target extended community: Taken from the service level RT.
| Note: The AD per-EVI route is not sent with the ESI label Extended Community. |
EVPN Route Type 4 - Ethernet Segment Route (ES route)
The router generates this route type for multi-homing ES discovery and DF (Designated Forwarder) election.
- Route Distinguisher: Taken from the service level RD.
- Ethernet Segment Identifier (ESI): Will contain a 10-byte identifier as configured in the system for a specified ethernet-segment.
- ES-import route-target community: The value is automatically derived from the MAC address portion of the ESI. This extended community is treated as a route-target and is supported by RT-constraint (route-target BGP family).
EVPN Route Type 5 - IP Prefix Route
IP Prefix Routes are also supported for MPLS tunnels. The route fields for route type 5 are shown in Figure 144. The 7750 SR, 7450 ESS (mixed mode), or 7950 XRS router will generate this route type for advertising IP prefixes in EVPN using the same fields that are described in section BGP-EVPN Control Plane for VXLAN Overlay Tunnels, with the following exceptions:
- MPLS Label—Carries the MPLS label allocated for the service
- This route will be sent with the RFC 5512 tunnel encapsulation extended community with the tunnel type value set to MPLS
RFC 5512 - BGP Tunnel Encapsulation Extended Community
The following routes are sent with the RFC 5512 BGP Encapsulation Extended Community: MAC/IP, Inclusive Multicast Ethernet Tag, and AD per-EVI routes. ES and AD per-ESI routes are not sent with this Extended Community.
The router processes the following BGP Tunnel Encapsulation tunnel values registered by IANA for RFC 5512:
- VXLAN encapsulation: 8.
- MPLS encapsulation: 10.
Any other tunnel value will make the route 'treat-as-withdraw'.
If the encapsulation value is MPLS, the BGP will validate the high-order 20-bits of the label field, ignoring the low-order 4 bits. If the encapsulation is VXLAN, the BGP will take the entire 24-bit value encoded in the MPLS label field as the VNI.
If the encapsulation extended community (as defined in RFC 5512) is not present in a received route, BGP will treat the route as an MPLS or VXLAN-based configuration of the config>router>bgp>neighbor# def-recv-evpn-encap [mpls|vxlan] command. The command is also available at the bgp and group levels.
5.20. EVPN for MPLS Tunnels in VPLS Services (EVPN-MPLS)
EVPN can be used in MPLS networks where PEs are interconnected through any type of tunnel, including RSVP-TE, LDP, RFC 3107 BGP, Segment Routing IS-IS, or Segment Routing OSPF. As with VPRN services, the selection of the tunnel to be used in a VPLS service (with BGP-EVPN MPLS enabled) is based on the auto-bind-tunnel command.
EVPN-MPLS is modeled similar to EVPN-VXLAN, that is, using a VPLS service where EVPN-MPLS 'bindings' can coexist with SAPs and SDP-bindings. The following shows an example of a VPLS service with EVPN-MPLS.
The user will configure a bgp-evpn context where vxlan must be shutdown and mpls no shutdown. In addition to the mpls no shutdown command, the minimum set of commands to be configured to set up the EVPN-MPLS instance are the evi and the auto-bind-tunnel resolution commands. However, the user can configure some other options. The most relevant configuration options are described below.
evi {1..65535} — This EVPN identifier is unique in the system and will be used for the service-carving algorithm used for multi-homing (if configured) and auto-deriving route-target and route-distinguishers in the service. It can be used for EVPN-MPLS and EVPN-VXLAN services.
If this EVPN identifier is not specified, the value will be zero and no route-distinguisher or route-targets will be auto-derived from it. If specified and no other route-distinguisher/route-target are configured in the service:, then the following applies:
- The route-distinguisher is derived from: <system_ip>:evi
- The route-target is derived from: <autonomous-system>:evi
| Note: When the vsi-import/export polices are configured, the route-target must be configured in the policies and those values take preference over the auto-derived route-targets. The operational route-target for a service will be displayed by the show service id x bgp command. |
When the evi is configured, a config>service>vpls>bgp node (even empty) is required to allow the user to see the correct information on the show service id 1 bgp and show service system bgp-route-distinguisher commands.
Although not mandatory, if no multi-homing is configured, the configuration of an evi is enforced for EVPN services with SAPs/SDP-bindings in an ethernet-segment. See the 'EVPN multi-homing' section for more information about ethernet-segments.
The following options are specific to EVPN-MPLS (and defined on bgp-evpn>mpls):
- control-word: Required as per RFC 7432 to avoid frame disordering. The user can enable/disable it so that interoperability to other vendors can be guaranteed.
- auto-bind-tunnel: Allows the user to decide what type of MPLS transport tunnels will be used for a particular instance. The command will be used in the same way as it is used in VPRN services.For bgp-evpn mpls, ‘bgp’ is explicitly added to the resolution-filter in EVPN (‘bgp’ is implicit in VPRNs).
- force-vlan-vc-forwarding: This command will allow the system to preserve the vlan-id and pbits of the service-delimiting qtag in a new tag added in the customer frame before sending it to the EVPN core.

Note: This command may be used in conjunction with the sap ingress vlan-translation command. If so, the configured translated vlan-id will be the vlan-id sent to the EVPN binds as opposed to the service-delimiting tag vlan-id. If the ingress SAP/binding is ‘null’-encapsulated, the output vlan-id and pbits will be zero.
- split-horizon-group: This command allows the association of a user-created split-horizon-group to all the EVPN-MPLS destinations. See the EVPN and VPLS integration section for more information.
- ecmp: When this command is set to a value greater than 1, aliasing is activated to the remote PEs that are defined in the same all-active multi-homing ethernet-segment. See the EVPN multi-homing section for more information.
- ingress-replication-bum-label: This command is only enabled when the user wants the PE to advertise a label for BUM traffic (Inclusive Multicast routes) that is different from the label advertised for unicast traffic (with the MAC/IP routes). This is useful to avoid potential transient packet duplication in all-active multi-homing.
In addition to these options, the following bgp-evpn commands are also available for EVPN-MPLS services:
- [no] mac-advertisement
- mac-duplication and settings
When EVPN-MPLS is established among some PEs in the network, EVPN unicast and multicast 'bindings' are created on each PE to the remote EVPN destinations. A specified ingress PE will create:
- A unicast EVPN-MPLS destination binding to a remote egress PE as soon as a MAC/IP route is received from that egress PE.
- A multicast EVPN-MPLS destination binding to a remote egress PE, if and only if the egress PE advertises an Inclusive Multicast Ethernet Tag Route with a BUM label. That is only possible if the egress PE is configured with ingress-replication-bum-label.
Those bindings, as well as the MACs learned on them, can be checked through the following show commands. In the following example, the remote PE(192.0.2.69) is configured with no ingress-replication-bum-label and PE(192.0.2.70) is configured with ingress-replication-bum-label. Hence, Dut has a single EVPN-MPLS destination binding to PE(192.0.2.69) and two bindings (unicast and multicast) to PE(192.0.2.70).
5.20.1. EVPN and VPLS Integration
The 7750 SR, 7450 ESS, or 7950 XRS router SR OS EVPN implementation supports draft-ietf-bess-evpn-vpls-seamless-integ so that EVPN-MPLS and VPLS can be integrated into the same network and within the same service. Since EVPN will not be deployed in green-field networks, this feature is useful for the integration between both technologies and even for the migration of VPLS services to EVPN-MPLS.
The following behavior enables the integration of EVPN and sdp-bindings in the same VPLS network:
a) Systems with EVPN endpoints and sdp-bindings to the same far-end bring down the sdp-bindings.
- The router will allow the establishment of an EVPN endpoint and a sdp-binding to the same far-end but the sdp-binding will be kept operationally down. Only the EVPN endpoint will be operationally up. This is true for spoke-sdps (manual and BGP-AD) and mesh-sdps. It is also possible between VXLAN and SDP-bindings.
- If there is an existing EVPN endpoint to a specified far-end and a spoke-sdp establishment is attempted, the spoke-sdp will be setup but kept down with an operational flag indicating that there is an EVPN route to the same far-end.
- If there is an existing spoke-sdp and a valid/used EVPN route arrives, the EVPN endpoint will be setup and the spoke-sdp will be brought down with an operational flag indicating that there is an EVPN route to the same far-end.
- In the case of an sdp-binding and EVPN endpoint to different far-end IPs on the same remote PE, both links will be up. This can happen if the sdp-binding is terminated in an IPv6 address or IPv4 address different from the system address where the EVPN endpoint is terminated.
b) The user can add spoke-sdps and all the EVPN-MPLS endpoints in the same split-horizon-group (SHG).
- A CLI command is added under the bgp-evpn>mpls> context so that the EVPN-MPLS endpoints can be added to a split-horizon-group:
- bgp-evpn>mpls> [no] split-horizon-group <group-name>
- The bgp-evpn mpls split-horizon-group must reference a user-configured split-horizon-group. User-configured split-horizon-groups can be configured within the service context. The same group-name can be associated with SAPs, spoke-sdps, pw-templates, pw-template-bindings, and EVPN-MPLS endpoints.
- If the split-horizon-group command in bgp-evpn>mpls> is not used, the default split-horizon-group (that contains all the EVPN endpoints) is still used, but it will not be possible to refer to it on saps/spoke-sdps.
- SAPs and SDP-bindings that share the same split-horizon-group of the EVPN-MPLS provider-tunnel will be brought operationally DOWN if the point-to-multipoint tunnel is operationally UP.
c) The system disables the advertisement of MACs learned on spoke-sdps/saps that are part of an EVPN split-horizon-group.
- When the saps and/or spoke-sdps (manual or BGP-AD-discovered) are configured within the same split-horizon-group as the EVPN endpoints, MAC addresses will still be learned on them, but they will not be advertised in EVPN.
- The preceding statement is also true if proxy-ARP/proxy-ND is enabled and an IP->MAC pair is learned on a SAP or SDP-binding that belongs to the EVPN split-horizon-group.
- The SAPs and/or spoke-SDPs added to an EVPN split-horizon-group should not be part of any EVPN multi-homed ES. If that happened, the PE would still advertise the AD per-EVI route for the SAP and/or spoke-SDP, attracting EVPN traffic that could not possibly be forwarded to that SAP and/or sdp-binding.
- Similar to the preceding statement, a split-horizon-group composed of SAPs/sdp-bindings used in a BGP-MH site should not be configured under bgp-evpn>mpls>split-horizon-group. This misconfiguration would prevent traffic being forwarded from the EVPN to the BGP-MH site, regardless of the DF/NDF state.Figure 151 shows an example of EVPN-VPLS integration.
Figure 151: EVPN-VPLS Integration
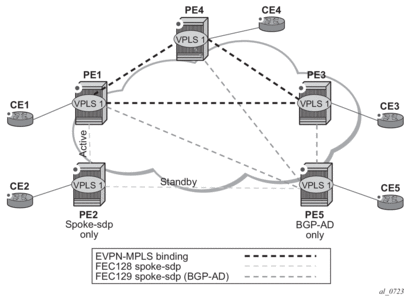 An example CLI configuration for PE1, PE5, and PE2 is provided below.
An example CLI configuration for PE1, PE5, and PE2 is provided below.
- PE1, PE3, and PE4 have BGP-EVPN and BGP-AD enabled in VPLS-1. PE5 has BGP-AD enabled and PE2 has active/standby spoke-sdps to PE1 and PE5.In this configuration:
- PE1, PE3, and PE4 will attempt to establish BGP-AD spoke-sdps, but they will be kept operationally DOWN as long as there are EVPN endpoints active among them.
- BGP-AD spoke-sdps and EVPN endpoints are instantiated within the same split-horizon-group, for example, SHG-1.
- Manual spoke-sdps from PE1 and PE5 to PE2 are not part of SHG-1.
- EVPN MAC advertisements:
- MACs learned on FEC128 spoke-sdps are advertised normally in EVPN.
- MACs learned on FEC129 spoke-sdps are not advertised in EVPN (because they are part of SHG-1, which is the split-horizon-group used for bgp-evpn>mpls). This prevents any data plane MACs learned on the SHG from being advertised in EVPN.
- BUM operation on PE1:
- When CE1 sends BUM, PE1 will flood to all the active bindings.
- When CE2 sends BUM, PE2 will send it to PE1 (active spoke-sdp) and PE1 will flood to all the bindings and saps.
- When CE5 sends BUM, PE5 will flood to the three EVPN PEs. PE1 will flood to the active spoke-sdp and saps, never to the EVPN PEs because they are part of the same SHG.
5.20.2. Auto-Derived Route-Distinguisher (RD) in Services with Multiple BGP Families
In a VPLS service, multiple BGP families and protocols can be enabled at the same time. When bgp-evpn is enabled, bgp-ad and bgp-mh are supported as well (not bgp-vpls in 13.0.R4). Note that a single RD is used per service and not per BGP family/protocol.
The following rules apply:
- The VPLS RD is selected based on the following precedence:
- Manual RD or auto-rd always take precedence when configured.
- If no manual/auto-rd configuration, the RD is derived from the bgp-ad>vpls-id.
- If no manual/auto-rd/vpls-id configuration, the RD is derived from the bgp-evpn>evi.
- If no manual/auto-rd/vpls-id/evi configuration, there will not be RD and the service will fail.
- The selected RD (see above rules) will be displayed by the Oper Route Dist field of the show service id bgp command.
- The service supports dynamic RD changes, for instance, the CLI allows the vpls-id be changed dynamically, even if it is used to auto-derive the service RD for bgp-ad, bgp-vpls, or bgp-mh.

Note: When the RD changes, the active routes for that VPLS will be withdrawn and re-advertised with the new RD.
- If one of the mechanisms to derive the RD for a specified service is removed from the configuration, the system will select a new RD based on the above rules. For example, if the vpls-id is removed from the configuration, the routes will be withdrawn, the new RD selected from the evi, and the routes re-advertised with the new RD.

Note: This reconfiguration will fail if the new RD already exists in a different VPLS/epipe.
- Because the vpls-id takes precedence over the evi when deriving the RD automatically, adding evpn to an existing bgp-ad service will not impact the existing RD - this is important to support bgp-ad to evpn migration.
5.20.3. EVPN Multi-Homing in VPLS Services
EVPN multi-homing implementation is based on the concept of the ethernet-segment. An ethernet-segment is a logical structure that can be defined in one or more PEs and identifies the CE (or access network) multi-homed to the EVPN PEs. An ethernet-segment is associated with port, LAG, or SDP objects and is shared by all the services defined on those objects.
Each ethernet-segment has a unique identifier called esi (Ethernet Segment Identifier) that is 10 bytes long and is manually configured in the router.
| Note: The esi is advertised in the control plane to all the PEs in an EVPN network; therefore, it is very important to ensure that the 10-byte esi value is unique throughout the entire network. Single-homed CEs are assumed to be connected to an ethernet-segment with esi = 0 (single-homed ethernet-segments are not explicitly configured). |
This section describes the behavior of the EVPN multi-homing implementation in an EVPN-MPLS service.
5.20.4. EVPN All-Active Multi-Homing
As described in RFC 7432, all-active multi-homing is only supported on access LAG SAPs and it is mandatory that the CE is configured with a LAG to avoid duplicated packets to the network. LACP is optional.
Three different procedures are implemented in 7750 SR, 7450 ESS, and 7950 XRS SR OS to provide all-active multi-homing for a specified ethernet-segment:
- DF (Designated Forwarder) election
- Split-horizon
- Aliasing
Figure 152 shows the need for DF election in all-active multi-homing.
Figure 152: DF Election
The DF election in EVPN all-active multi-homing avoids duplicate packets on the multi-homed CE. The DF election procedure is responsible for electing one DF PE per ESI per service; the rest of the PEs being non-DF for the ESI and service. Only the DF will forward BUM traffic from the EVPN network toward the ES SAPs (the multi-homed CE). The non-DF PEs will not forward BUM traffic to the local ethernet-segment SAPs.
| Note: BUM traffic from the CE to the network and known unicast traffic in any direction is allowed on both the DF and non-DF PEs. |
Figure 153 shows the EVPN split-horizon concept for all-active multi-homing.
Figure 153: Split-Horizon
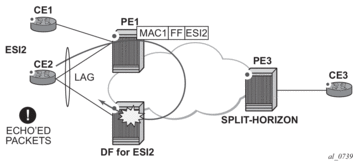
The EVPN split-horizon procedure ensures that the BUM traffic originated by the multi-homed PE and sent from the non-DF to the DF, is not replicated back to the CE (echoed packets on the CE). To avoid these echoed packets, the non-DF (PE1) will send all the BUM packets to the DF (PE2) with an indication of the source ethernet-segment. That indication is the ESI Label (ESI2 in the example), previously signaled by PE2 in the AD per-ESI route for the ethernet-segment. When PE2 receives an EVPN packet (after the EVPN label lookup), the PE2 will find the ESI label that will identify its local ethernet-segment ESI2. The BUM packet will be replicated to other local CEs but not to the ESI2 SAP.
Figure 154 shows the EVPN aliasing concept for all-active multi-homing.
Figure 154: Aliasing
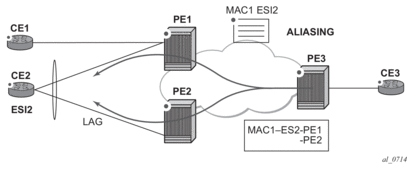
Because CE2 is multi-homed to PE1 and PE2 using an all-active ethernet-segment, 'aliasing' is the procedure by which PE3 can load-balance the known unicast traffic between PE1 and PE2, even if the destination MAC address was only advertised by PE1 as in the example. When PE3 installs MAC1 in the FDB, it will associate MAC1 not only with the advertising PE (PE1) but also with all the PEs advertising the same esi (ESI2) for the service. In this example, PE1 and PE2 advertise an AD per-EVI route for ESI2, therefore, the PE3 installs the two next-hops associated with MAC1.
Aliasing is enabled by configuring ECMP greater than 1 in the bgp-evpn mpls context.
5.20.5. All-Active Multi-Homing Service Model
The following shows an example PE1 configuration that provides all-active multi-homing to the CE2 described in Figure 154.
In the same way, PE2 is configured as follows:
The preceding configuration will enable the all-active multi-homing procedures. The following must be considered:
- The ethernet-segment must be configured with a name and a 10-byte esi:
- config>service>system>bgp-evpn#ethernet-segment <es_name> create
- config>service> system>bgp-evpn>ethernet-segment# esi <value>
- When configuring the esi, the system enforces the 6 high-order octets after the type to be different from zero (so that the auto-derived route-target for the ES route is different from zero). Other than that, the entire esi value must be unique in the system.
- Only a LAG can be associated with the ethernet-segment. This LAG will be exclusively used for EVPN multi-homing. Other LAG ports in the system can be still used for MC-LAG and other services.
- When the LAG is configured on PE1 and PE2, the same admin-key, system-priority, and system-id must be configured on both PEs, so that CE2 responds as though it is connected to the same system.
- The same ethernet-segment may be used for EVPN-MPLS and PBB-EVPN services.

Note: The source-bmac-lsb attribute must be defined for PBB-EVPN (so that it will only be used in PBB-EVPN, and ignored by EVPN). Other than EVPN-MPLS and PBB-EVPN I-VPLS/Epipe services, no other Layer-2 services are allowed in the same ethernet-segment (regular VPLS or EVPN-VXLAN SAPs defined on the ethernet-segment will be kept operationally down).
- Only one sap per service can be part of the same ethernet-segment.
5.20.6. ES Discovery and DF Election Procedures
The ES (Ethernet Segment) discovery and DF election is implemented in three logical steps, as shown in Figure 155.
Figure 155: ES Discovery and DF Election
df_election.gif)
Step 1 - ES Advertisement and Discovery
Ethernet-segment ESI-1 is configured as per the previous section, with all the required parameters. When ethernet-segment no shutdown is executed, PE1 and PE2 will advertise an ES route for ESI-1. They will both include the route-target auto-derived from the MAC portion of the configured ESI. If the route-target address family is configured in the network, this will allow the RR to keep the dissemination of the ES routes under control.
In addition to the ES route, PE1 and PE2 will advertise AD per-ESI routes and AD per-EVI routes.
- AD per-ESI routes will announce the ethernet-segment capabilities, including the mode (single-active or all-active) as well as the ESI label for split-horizon.
- AD per-EVI routes are advertised so that PE3 knows what services (EVIs) are associated with the ESI. These routes are used by PE3 for its aliasing procedures.
Step 2 - DF Election
Once ES routes exchange between PE1 and PE2 is complete, both run the DF election for all the services in the ethernet-segment.
PE1 and PE2 elect a Designated Forwarder (DF) per <ESI, service>. The default DF election mechanism in 7750 SR, 7450 ESS, and 7950 XRS SR OS is service-carving (as per RFC 7432). The following applies when enabled on a specified PE:
- An ordered list of PE IPs where ESI-1 resides is built. The IPs are gotten from the Origin IP fields of all the ES routes received for ESI-1, as well as the local system address. The lowest IP will be considered ordinal '0' in the list.
- The local IP can only be considered a "candidate" after successful ethernet-segment no shutdown for a specified service.

Note: The remote PE IPs must be present in the local PE's RTM so that they can participate in the DF election.
- A PE will only consider a specified remote IP address as candidate for the DF election algorithm for a specified service if, in addition to the ES route, the corresponding AD routes per-ESI and per-EVI for that PE have been received and properly activated.
- All the remote PEs receiving the AD per-ES routes (for example, PE3), will interpret that ESI-1 is all-active if all the PEs send their AD per-ES routes with the single-active bit = 0. Otherwise, if at least one PE sends an AD route per-ESI with the single-active flag set or the local ESI configuration is single-active, the ESI will behave as single-active.
- An es-activation-timer can be configured at the redundancy>bgp-evpn-multi-homing>es-activation-timer level or at the service>system>bgp-evpn>eth-seg>es-activation-timer level. This timer, which is 3 seconds by default, delays the transition from non-DF to DF for a specified service, after the DF election has run.
- This use of the es-activation-timer is different from zero and minimizes the risks of loops and packet duplication due to "transient" multiple DFs.
- The same es-activation-timer should be configured in all the PEs that are part of the same ESI. It is up to the user to configure either a long timer to minimize the risks of loops/duplication or even es-activation-timer=0 to speed up the convergence for non-DF to DF transitions. When the user configures a specific value, the value configured at ES level supersedes the configured global value.
- The DF election is triggered by the following events:
- config>service>system>bgp-evpn>eth-seg# no shutdown triggers the DF election for all the services in the ESI.
- Reception of a new update/withdrawal of an ES route (containing an ESI configured locally) triggers the DF election for all the services in the ESI.
- Reception of a new update/withdrawal of an AD per-ES route (containing an ESI configured locally) triggers the DF election for all the services associated with the list of route-targets received along with the route.
- Reception of a new update of an AD per-ES route with a change in the ESI-label extended community (single-active bit or MPLS label) triggers the DF election for all the services associated with the list of route-targets received along with the route.
- Reception of a new update/withdrawal of an AD route per-EVI (containing an ESI configured locally) triggers the DF election for that service.
- When the PE boots up, the boot-timer will allow the necessary time for the control plane protocols to come up before bringing up the ethernet-segment and running the DF algorithm. The boot-timer is configured at system level - config>redundancy>bgp-evpn-multi-homing# boot-timer - and should use a value long enough to allow the IOMs and BGP sessions to come up before exchanging ES routes and running the DF election for each EVI/ISID.
- The system will NOT advertise ES routes until the boot timer expires. This will guarantee that the peer ES PEs don't run the DF election either until the PE is ready to become the DF if it needs to.
- The following show command displays the configured boot-timer as well as the remaining timer if the system is still in boot-stage.
- When service-carving mode auto is configured (default mode), the DF election algorithm will run the function [V(evi) mod N(peers) = i(ordinal)] to identify the DF for a specified service and ESI, as described in the following example:
- As shown in Figure 155, PE1 and PE2 are configured with ESI-1. Given that V(10) mod N(2) = 0, PE1 will be elected DF for VPLS-10 (because its IP address is lower than PE2's and it is the first PE in the candidate list).

Note: The algorithm takes the configured evi in the service as opposed to the service-id itself. The evi for a service must match in all the PEs that are part of the ESI. This guarantees that the election algorithm is consistent across all the PEs of the ESI. The evi must be always configured in a service with saps/sdp-bindings that are created in an ES.
- A manual service-carving option is allowed so that the user can manually configure for which evi identifiers the PE is primary: service-carving mode manual / manual service <evi> to <evi> primary.
- The system will be the PE forwarding/multicasting traffic for the evi identifiers included as primary. The PE will be secondary (non-DF) for the non-specified evis.
- If a range is configured but the service-carving is not mode manual, then the range has no effect.
- Only two PEs are supported when service-carving mode manual is configured. If a third PE is configured with service-carving mode manual for an ESI, the two non-primary PEs will remain non-DF regardless of the primary status.
- For example, as shown in Figure 155: if PE1 is configured with service-carving manual evi 1 to 100 primary and PE2 with service-carving manual evi 101 to 200 primary, then PE1 will be the primary PE for service VPLS 10 and PE2 the secondary PE.
- When service-carving is disabled, the lowest originator IP will win the election for a specified service and ESI:
config>service>system>bgp-evpn>ethernet-segment> mode off
The following show command displays the ethernet-segment configuration and DF status for all the EVIs and ISIDs (if PBB-EVPN is enabled) configured in the ethernet-segment.
Step 3 - DF and Non-DF Service Behavior
Based on the result of the DF election or the manual service-carving, the control plane on the non-DF (PE1) will instruct the data path to remove the LAG SAP (associated with the ESI) from the default flooding list for BUM traffic. On PE1 and PE2, both LAG SAPs will learn the same MAC address (coming from the CE). For instance, in the following show commands, 00:ca:ca:ba:ce:03 is learned on both PE1 and PE2 access LAG (on ESI-1). However, PE1 learns the MAC as 'Learned' whereas PE2 learns it as 'Evpn'. This is due to the CE2 hashing the traffic for that source MAC to PE1. PE2 learns the MAC through EVPN but it associates the MAC to the ESI SAP, because the MAC belongs to the ESI.
When PE1 (non-DF) and PE2 (DF) exchange BUM packets for evi 1, all those packets will be sent including the ESI label at the bottom of the stack (in both directions). The ESI label being used by each PE for ESI-1 can be displayed by the following command:
5.20.7. Aliasing
Following the example in Figure 155, if the service configuration on PE3 has ECMP > 1, PE3 will add PE1 and PE2 to the list of next-hops for ESI-1. As soon as PE3 receives a MAC for ESI-1, it will start load-balancing between PE1 and PE2 the flows to the remote ESI CE. The following command shows the FDB in PE3.
| Note: mac 00:ca:ca:ba:ce:03 is associated with the ethernet-segment eES:01:00:00:00:00:71:00:00:00:01 (esi configured on PE1 and PE2 for ESI-1). |
The following command shows all the EVPN-MPLS destination bindings on PE3, including the ES destination bindings.
The ethernet-segment eES:01:00:00:00:00:71:00:00:00:01 is resolved to PE1 and PE2 addresses:
PE3 will perform aliasing for all the MACs associated with that ESI. This is possible because PE1 is configured with ecmp parameter >1:
5.20.8. Network Failures and Convergence for All-Active Multi-Homing
Figure 156 shows the behavior on the remote PEs (PE3) when there is an ethernet-segment failure.
Figure 156: All-Active Multi-Homing ES Failure
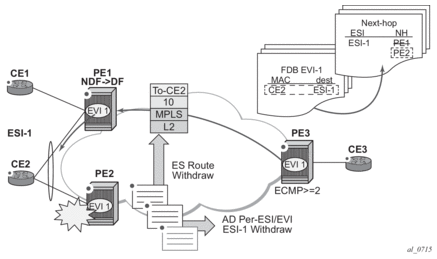
The unicast traffic behavior on PE3 is as follows:
- PE3 can only forward MAC DA = CE2 to both PE1 and PE2 when the MAC advertisement route from PE1 (or PE2) and the set of Ethernet AD per-ES routes and Ethernet AD per-EVI routes from PE1 and PE2 are active at PE3.
- If there was a failure between CE2 and PE2, PE2 would withdraw its set of Ethernet AD and ES routes, then PE3 would forward traffic destined to CE2 to PE1 only. PE3 does not need to wait for the withdrawal of the individual MAC.
- The same behavior would be followed if the failure had been at PE1.
- If after (2), PE2 withdraws its MAC advertisement route, then PE3 treats traffic to MAC DA = CE2 as unknown unicast, unless the MAC had been previously advertised by PE1.
For BUM traffic, the following events would trigger a DF election on a PE and only the DF would forward BUM traffic after the esi-activation-timer expiration (if there was a transition from non-DF to DF).
- Reception of ES route update (local ES shutdown/no shutdown or remote route)
- New AD-ES route update/withdraw
- New AD-EVI route update/withdraw
- Local ES port/SAP/service shutdown
- Service carving range change (affecting the evi)
- Multi-homing mode change (single/all active to all/single-active)
5.20.8.1. Logical Failures on Ethernet Segments and Black-Holes
Be aware of the effects triggered by certain 'failure scenarios'; some of these scenarios are shown in Figure 157:
Figure 157: Black-hole Caused by SAP/SVC Shutdown
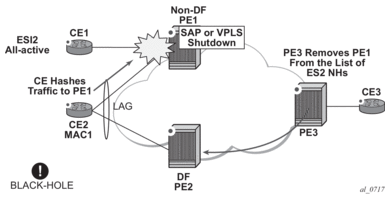
If an individual VPLS service is shutdown in PE1 (the example is also valid for PE2), the corresponding LAG SAP will go oper-down. This event will trigger the withdrawal of the AD per-EVI route for that particular SAP. PE3 will remove PE1 of its list of aliased next-hops and PE2 will take over as DF (if it was not the DF already). However, this will not prevent the network from black-holing the traffic that CE2 'hashes' to the link to PE1. Traffic sent from CE2 to PE2 or traffic from the rest of the CEs to CE2 will be unaffected, so this situation is not easily detected on the CE.
The same result occurs if the ES SAP is administratively shutdown instead of the service.
| Note: When bgp-evpn mpls shutdown is executed, the sap associated with the ES will be brought operationally down (StandbyforMHprotocol) and so will the entire service if there are no other saps or sdp-bindings in the service. However, if there are other saps/sdp-bindings, the service will remain operationally up. |
5.20.8.2. Transient Issues Due to MAC Route Delays
Some situations may cause potential transient issues to occur. These are shown in Figure 158 and explained below.
Figure 158: Transient Issues Caused by “slow” MAC Learning
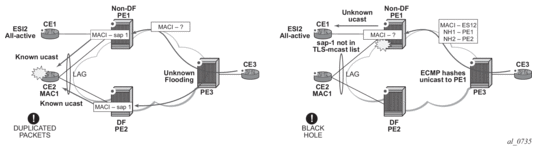
Transient packet duplication caused by delay in PE3 to learn MAC1:
This scenario is illustrated by the diagram on the left in Figure 158. In an all-active multi-homing scenario, if a specified MAC address is not yet learned in a remote PE, but is known in the two PEs of the ES, for example, PE1 and PE2, the latter PEs might send duplicated packets to the CE.
In an all-active multi-homing scenario, if a specified MAC address (for example, MAC1), is not learned yet in a remote PE (for example, PE3), but it is known in the two PEs of the ES (for example, PE1 and PE2), the latter PEs might send duplicated packets to the CE.
This issue is solved by the use of ingress-replication-bum-label in PE1 and PE2. If configured, PE1/PE2 will know that the received packet is an unknown unicast packet, therefore, the NDF (PE1) will not send the packets to the CE and there will not be duplication.
| Note: Even without the ingress-replication-bum-label, this is only a transient situation that would be solved as soon as MAC1 is learned in PE3. |
Transient black-hole caused by delay in PE1 to learn MAC1:
This case is illustrated by the diagram on the right in Figure 158. In an all-active multi-homing scenario, MAC1 is known in PE3 and aliasing is applied to MAC1. However, MAC1 is not known yet in PE1, the NDF for the ES. If PE3 hashing picks up PE1 as the destination of the aliased MAC1, the packets will be black-holed.
As soon as PE1 learns MAC1, the black-hole will be resolved.
5.20.9. EVPN Single-Active Multi-Homing
The 7750 SR, 7450 ESS, and 7950 XRS SR OS supports single-active multi-homing on access LAG SAPs, regular SAPs, and spoke-SDPs for a specified VPLS service. For LAG SAPs, the CE will be configured with a different LAG to each PE in the ethernet-segment (as opposed to a single LAG in an all-active multi-homing).
The following SR OS procedures support EVPN single-active multi-homing for a specified ethernet-segment:
- DF (Designated Forwarder) electionAs in all-active multi-homing, DF election in single-active multi-homing determines the forwarding for BUM traffic from the EVPN network to the ethernet-segment CE. Also, in single-active multi-homing, DF election also determines the forwarding of any traffic (unicast/BUM) and in any direction (to/from the CE).
- Backup PEIn single-active multi-homing, the remote PEs do not perform aliasing to the PEs in the ethernet-segment. The remote PEs identify the DF based on the MAC routes and send the unicast flows for the ethernet-segment to the PE in the DF and program a backup PE as an alternative next-hop for the remote ESI in case of failure.This RFC 7432 procedure is known as 'Backup PE' and is shown in Figure 159 for PE3.
Figure 159: Backup PE
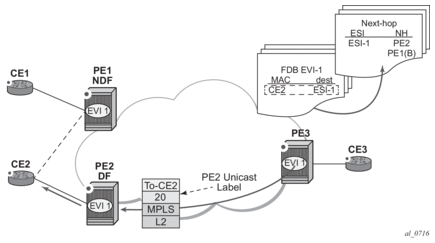
5.20.9.1. Single-Active Multi-Homing Service Model
The following shows an example of PE1 configuration that provides single-active multi-homing to CE2, as shown in Figure 159.
The PE2 example configuration for this scenario is as follows:
In single-active multi-homing, the non-DF PEs for a specified ESI will block unicast and BUM traffic in both directions (upstream and downstream) on the object associated with the ESI. Other than that, single-active multi-homing is similar to all-active multi-homing with the following differences:
- The ethernet-segment will be configured for single-active: service>system>bgp-evpn>ethernet-segment>multi-homing single-active.
- The advertisement of the ESI-label in a per-ESI AD route is optional for single-active ethernet-segments. The user can control the no advertisement of the ESI label by using the following command: service>system>bgp-evpn>ethernet-segment>multi-homing single-active no-esi-label. By default, the ESI label is used for single-active ESs too.
- For single-active multi-homing, the ethernet-segment can be associated with a port and sdp, as well as a lag-id, as shown in Figure 159, where:
- port would be used for single-active sap redundancy without the need for lag.
- sdp would be used for single-active spoke-sdp redundancy.
- lag would be used for single-active LAG redundancy

Note: In this case, key, system-id, and system-priority must be different on the PEs that are part of the ethernet-segment).
- For single-active multi-homing, when the PE is non-DF for the service, the saps/spoke-sdps on the ethernet-segment will be down and show StandByForMHProtocol as the reason.
- From a service perspective, single-active multi-homing can provide redundancy to CEs (MHD, Multi-Homed Devices) or networks (MHN, Multi-Homed Networks) with the following setup:
- LAG with or without LACPIn this case, the multi-homed ports on the CE will be part of the different LAGs (a LAG per multi-homed PE will be used in the CE). The non-DF PE for each service can signal that the sap is oper-down if eth-cfm fault-propagation-enable {use-if-tlv|suspend-ccm} is configured.
- Regular Ethernet 802.1q/ad portsIn this case, the multi-homed ports on the CE/network will not be part of any LAG. Eth-cfm can also be used for non-DF indication to the multi-homed device/network.
- Active-standby PWsIn this case, the multi-homed CE/network is connected to the PEs through an MPLS network and an active/standby spoke-sdp per service. The non-DF PE for each service will make use of the LDP PW status bits to signal that the spoke-sdp is oper-down on the PE side.
5.20.9.2. ES and DF Election Procedures
In all-active multi-homing, the non-DF keeps the SAP up, although it removes it from the default flooding list. In the single-active multi-homing implementation the non-DF will bring the SAP/SDP-binding operationally down. Refer to the ES Discovery and DF Election Procedures for more information.
The following show commands display the status of the single-active ESI-7413 in the non-DF. Note that the associated spoke-SDP is operationally down and it signals PW Status standby to the multi-homed CE:
5.20.9.3. Backup PE Function
A remote PE (PE3 in Figure 159) will import the AD routes per ESI, where the single-active flag is set. PE3 will interpret that the ethernet-segment is single-active if at least one PE sends an AD route per-ESI with the single-active flag set. MACs for a specified service and ESI will be learned from a single PE, that is, the DF for that <ESI, EVI>.
The remote PE will install a single EVPN-MPLS destination (TEP, label) for a received MAC address and a backup next-hop to the PE for which the AD routes per-ESI and per-EVI are received. For instance, in the following command, 00:ca:ca:ba:ca:06 is associated with the remote ethernet-segment eES 01:74:13:00:74:13:00:00:74:13. That eES is resolved to PE(192.0.2.73), which is the DF on the ES.
If PE3 sees only two single-active PEs in the same ESI, the second PE will be the backup PE. Upon receiving an AD per-ES/per-EVI route withdrawal for the ESI from the primary PE, the PE3 will start sending the unicast traffic to the backup PE immediately.
If PE3 receives AD routes for the same ESI and EVI from more than two PEs, the PE will not install any backup route in the data path. Upon receiving an AD per-ES/per-EVI route withdrawal for the ESI, it will flush the MACs associated with the ESI.
5.20.9.4. Network Failures and Convergence for Single-Active Multi-Homing
Figure 160 shows the remote PE (PE3) behavior when there is an ethernet-segment failure.
Figure 160: Single-Active Multi-Homing ES Failure
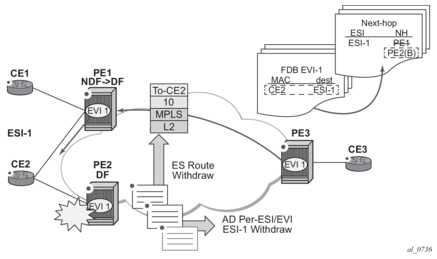
The PE3 behavior for unicast traffic is as follows:
- PE3 forwards MAC DA = CE2 to PE2 when the MAC Advertisement Route came from PE2 and the set of Ethernet AD per-ES routes and Ethernet AD per-EVI routes from PE1 and PE2 are active at PE3.
- If there was a failure between CE2 and PE2, PE2 would withdraw its set of Ethernet AD and ES routes, then PE3 would immediately forward the traffic destined to CE2 to PE1 only (the backup PE). PE3 does not need to wait for the withdrawal of the individual MAC.
- After the (2) PE2 withdraws its MAC advertisement route, PE3 will treat traffic to MAC DA = CE2 as unknown unicast, unless the MAC has been previously advertised by PE1.
Also, a DF election on PE1 is triggered. In general, a DF election is triggered by the same events as for all-active multi-homing. In this case, the DF will forward traffic to CE2 once the esi-activation-timer expiration occurs (the timer kicks in when there is a transition from non-DF to DF).
5.20.9.4.1. Logical Failures on Ethernet Segments and Black-Holes
Be aware of the effects triggered by certain 'failure scenarios'; some of these scenarios are shown in Figure 161:
Figure 161: Single-Active Multi-Homing SAP/SDP/Service Shutdown
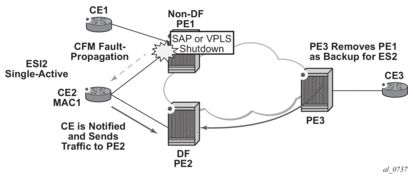
Common effects to consider are:
- If an individual VPLS service is administrative shutdown in PE1, the corresponding SAP/SDP-binding will go oper-down. This event will trigger the withdrawal of the AD per-EVI route for that particular SAP/SDP-binding. PE3 will apply its backup mechanisms and PE2 will take over as DF (if it was not the DF already). To signal the fault to CE2:
- Eth-cfm must be used between the PEs and the multi-homed CE - if the connectivity is based on SAPs. A down MEP on the SAP going down will propagate the fault to a MEP on the CE. This network event will not produce any black-holing (in the all-active multi-homing case, this would partially black-hole the traffic).
- PW status bits must be used between the PEs and the multi-homed CE - if the connectivity is based on pseudowires.
- The same result occurs if the ES SAP/SDP-binding is administrative shutdown instead of the service.
5.21. BGP-EVPN Control Plane for EVPN-VPWS
EVPN-VPWS uses route-type 1 and route-type 4; it does not use route-types 2, 3 or 5. Figure 162 shows the encoding of the required extensions for the Ethernet A-D per-EVI routes. The encoding follows the guidelines described in draft-ief-bess-evpn-vpws.
Figure 162: EVPN-VPWS BGP Extensions
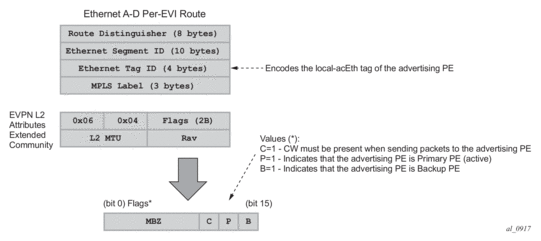
Assuming that the advertising PE has an access SAP-SDP or Spoke-SDP that is not part of an Ethernet Segment (ES), the PE populates the fields of the AD per-EVI route with the following values.
- Ethernet Tag ID field is encoded with the value configured by the user in the service>bgp-evpn>local-ac-name>eth-tag <value> command.
- RD and MPLS label values are encoded as specified in RFC 7432.
- ESI is 0.
- The route is sent along an EVPN L2 attributes extended community, as specified in draft-ietf-bess-evpn-vpws, where:
- type and subtype are 0x06 and 0x04 as allocated by IANA
- flag C is set if control-word is configured in the service
- P and B flags are zero
- L2 MTU is encoded with service-mtu configured in the Epipe service
If the advertising PE has an access SAP-SDP or Spoke-SDP that is part of an ES, the AD per-EVI route is sent with the information described in the preceding list, with the following minor differences.
- The ESI encodes the corresponding non-zero value.
- The P and B flags are set in the following cases.
- All-active multi-homing
- All PEs that are part of the ES always set the P flag.
- The B flag is never set in the all-active multi-homing ES case.
- Single-active multi-homing
- Only the DF PE sets the P bit for an EVI and the remaining PEs send it as P=0.
- Only the backup DF PE sets the B bit.If more than two PEs are present in the same single-active ES, the backup PE is the winner of a second DF election (excluding the DF). The remaining non-DF PEs send B=0.
Also, ES and AD per-ES routes are advertised and processed for the Ethernet-Segment, as described in RFC7432 Ethernet Segments. The ESI label sent with the AD per-ES route is used by BUM traffic on VPLS services; it is not used for Epipe traffic.
5.22. EVPN for MPLS Tunnels in Epipe Services (EVPN-VPWS)
BGP-EVPN can be enabled in Epipe services with either SAPs or spoke-SDPs at the access, as shown in Figure 163.
Figure 163: EVPN-MPLS VPWS
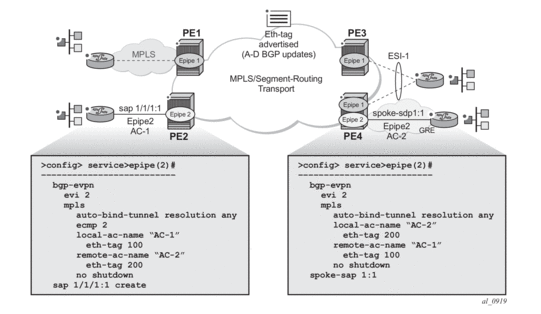
EVPN-VPWS is supported in MPLS networks that also run EVPN-MPLS in VPLS services. From a control plane perspective, EVPN-VPWS is a simplified point-to-point version of RFC 7432 for ELINE services for the following reasons.
- EVPN-VPWS does not use inclusive multicast, MAC/IP routes or IP-Prefix routes.
- A-D Ethernet per EVI routes are used to advertise the local attachment circuit identifiers at each side of the VPWS instance. The attachment circuit identifiers are configured as local and remote ethernet tags. When an AD per EVI route is imported and the ethernet-tag matches the configured remote ethernet-tag, an EVPN destination is created for the Epipe.
In the following configuration example, Epipe 2 is an EVPN-VPWS service between PE2 and PE4 (as shown in Figure 163):
The following considerations apply to the example configuration.
- The evi is used to auto-derive the route-target/route-distinguisher of the service. The evi values must be unique in the system no matter, irrespecitve of the type of service they are assigned (EPIPE or VPLS).
- Support for the following bgp-evpn commands in Epipe services is the same as in VPLS services:
- mpls auto-bind-tunnel
- mpls control-word
- mpls entropy-label
- mpls force-vlan-vc-forwarding
- mpls shutdown
- The following bgp-evpn commands identify the local and remote attachment circuits, with the configured eth-tags encoded in the advertised and received A-D Ethernet per-EVI routes:
- local-ac-name <name>
- local-ac-name <name> eth-tag <tag-value>; where tag-value [1.. 16777215]
- remote-ac-name <name>
- remote-ac-name <name> eth-tag <tag-value>; where tag-value [1.. 16777215]
- Changes on remote eth-tags are allowed without shutting down bgp-evpn mpls or the Epipe service. The local-ac eth-tag value cannot be changed without bgp-evpn mpls shutdown.
- Both local and remote eth-tags are mandatory to bring up the Epipe service.
EVPN-VPWS Epipes can also be configured with the following characteristics.
- Access attachment circuits can be SAPs or spoke-SDPs. Only manually configured spoke-SDPs are supported; BGP-VPWS and endpoints are not supported. The vc-switching configuration is not supported on bgp-evpn enabled pipes.
- EVPN-VPWS Epipes support control-word and entropy-label.When bgp-evpn>mpls>control-word is configured, the PE will set the C bit in its AD per-EVI advertisement and send the control-word in the data path. In this case, the PE will also expect the control-word to be received. If there is a mismatch between the received control-word and the configured control-word, the system will not setup the EVPN destination; as a result, the service will not come up.
- EVPN-VPWS Epipes can advertise the Layer-2 (service) MTU and check its consistency as follows:
- The advertised MTU value will be taken from the configured service-mtu in the Epipe service.
- The received L2 MTU will be checked and compared with the local value. In case of a mismatch between the received MTU and the configured service-mtu, the system will not setup the EVPN destination; as a result, the service will not come up.
- The system will not check the network port MTU value.
- If the received L2 MTU value is 0, the MTU will be ignored.
5.22.1. Using A/S PW and MC-LAG with EVPN-VPWS Epipes
The use of A/S PW (for access spoke-SDPs) and MC-LAG (for access SAPs) provides an alternative redundant solution for EVPN-VPWS that do not use the EVPN multi-homing procedures described in draft-ietf-bess-evpn-vpws. Figure 164 shows the use of both mechanisms in a single Epipe.
Figure 164: A/S PW and MC-LAG Support on EVPN-VPWS
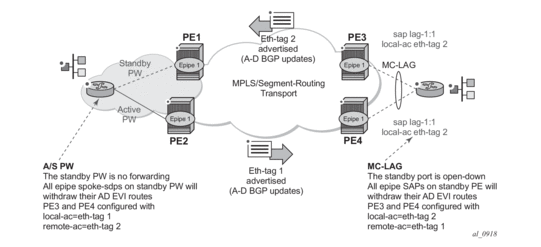
In Figure 164, an A/S PW connects the CE to PE1 and PE2 (left-hand side of the diagram), and an MC-LAG connects the CE to PE3 and PE4 (right-hand side of the diagram). As EVPN multi-homing is not used, there are no AD per-ES routes or ES routes in this example. The redundancy is handled as follows:
- PE1 and PE2 are configured with EPIPE-1, where a spoke-SDP connects the service in each PE to the access CE. The local-ac eth-tag is 1 and the remote-ac eth-tag is 2 (in PE1/PE2).
- PE3 and PE4 are configured with EPIPE-1, where each PE has a lag SAP that belongs to a previously configured MC-LAG construct. The local-ac eth-tag is 2 and the remote-ac eth-tag is 1.
- An endpoint and A/S PW is configured on the CE on the left-hand side of the diagram. PE1/PE2 are able to advertise eth-tag 1 based on the oper-status or the forwarding status of the spoke-SDP.For example, if PE1 receives a standby PW status indication from the CE and the previous status was forward, it will withdraw the AD EVI route for eth-tag 1. If PE2 receives a forward PW status indication and the previous status was standby or down, it will advertise the AD EVI route for eth-tag 1.
- The user can configure MC-LAG for access SAPs using the example configuration of PE3 and PE4 shown in Figure 164. In this case, the MC-LAG will determine which of the two chassis is active or standby.If PE4 becomes the standby chassis, the entire LAG port will be brought down. As a result, the SAP will go oper-down and PE4 will withdraw any previous AD EVI route for eth-tag 2.If PE3 becomes the active chassis, the LAG port will go UP. As a result, the SAP and the PE3 will advertise the AD per-EVI route for eth-tag 2.
5.23. EVPN Multi-homing for EVPN-VPWS Services
EVPN multi-homing is supported for EVPN-VPWS Epipe services with the following considerations.
- Single-active and all-active multi-homing is supported for SAPs and spoke-SDPs.
- Ethernet Segments (ES) can be shared between the Epipe and VPLS services for LAGs, ports, and SDPs.
- A split-horizon function is not required because there is no traffic between the Designated Forwarder (DF) and the non-DF for Epipe services. As a result the ESI label is never used. For this reason, the ethernet-segment multi-homing single-active no-esi-label and ethernet-segment source-bmac-lsb commands do not affect Epipe services.
- The local Ethernet Tag values must match on all PEs that are part of the same ES, regardless of the multi-homing mode. The PEs in the ES use the AD per-EVI routes from the peer PEs to validate the PEs as DF election candidates for a specific EVI.
The DF election for Epipes that is defined in an all-active multi-homing ES is not relevant because all PEs in the ES behave in the same way as follows:
- All PEs send P=1 on the AD per-EVI routes.
- All PEs can send upstream and downstream traffic, regardless of whether the traffic is unicast, multicast, or broadcast (all traffic is treated as unicast in the Epipe services).
Therefore, the following tools command shows “N/A” when all-active multi-homing is configured.
Aliasing is supported for traffic sent to an Ethernet-Segment destination. If ecmp is enabled on the ingress PE, per-flow load-balancing is performed to all PEs that advertise P=1. The PEs that advertise P=0 are not considered as next hops for an ES destination.
| Note: The ingress PE will load-balance the traffic if shared-queuing or ingress policing is enabled on the access SAPs. |
Although DF election is not relevant for Epipes in an all-active multi-homing ES, it is essential for the following forwarding and backup functions in a single-active multi-homing ES.
- The PE elected as DF is the primary PE for the Ethernet Segment in the Epipe. The primary PE unblocks the SAP or Spoke-SDP for upstream and downstream traffic; the remaining PEs in the ES bring their ES SAPs or Spoke-SDPs operationally down.
- The DF candidate list is built from the PEs sending ES routes for the same ES and is pruned for a specific service, depending on the availability of the AD per-ES and per-EVI routes.
- When the SAP/Spoke-SDPs (part of the ES) come up, the AD per-EVI routes are sent with P=B=0. The remote PEs do not send traffic at this stage.The remote PEs do not start sending traffic until the DF election process is completed and the es-activation-timer has expired, and the PEs advertise AD per-EVI routes with P and B bits different from zero.
- The backup PE function is supported as defined in draft-ietf-bess-evpn-vpws. The primary PE, backup, or none status is signaled by the PEs (part of the same single-active MH ES) in the P or B flags of the EVPN L2 attributes extended community. Figure 165 shows the advertisement and use of the primary, backup, or none indication by the PEs in the ES.
Figure 165: VPWS Single-active Multi-homing
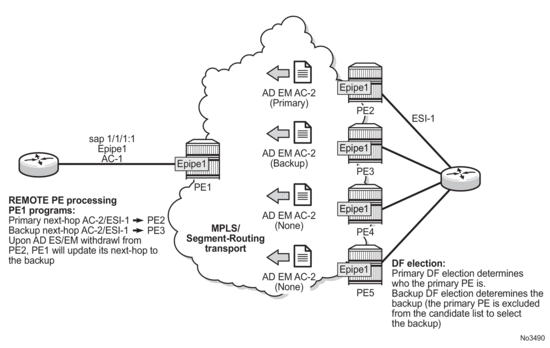
As specified in RFC7432, the remote PEs in VPLS services have knowledge of the primary PE in the remote single-active ES, based on the advertisement of the MAC/IP routes (because only the DF will learn and advertise MAC/IP routes).
Because there are no MAC or IP routes in EVPN-VPWS, the remote PEs can forward the traffic based on the P/B bits. The process is described in the following list; all PE references used refer to the example shown in Figure 165.
- The DF PE for an EVI (PE2 in Figure 165) sends P=1 and B=0.
- For each ES or EVI, a second DF election is run among the PEs in the backup candidate list to elect the backup PE. The backup PE sends P=0 and B=1 (PE3 in Figure 165).
- All remaining multi-homing PEs send P=B=0 (PE4 and PE5).
- At the remote PEs (PE1 in Figure 165), the P and B flags are used to identify the primary and backup PEs within the ES destination. The traffic is then sent to the primary PE, provided that it is active.
- When a remote PE receives the withdrawal of an Ethernet A-D per ES (or EVI) route from the primary PE, the remote PE immediately switches the traffic to the backup PE for the affected EVIs.
- The backup PE takes over immediately without waiting for the es-activation-timer to bring up its SAP or spoke-SDP.
- The bgp-evpn mpls ecmp setting also governs the forwarding in single-active multi-homing, regardless of the single-active multi-homing bit in the AD per-ES route received at the remote PE (PE1 in Figure 165).
- PE1 always sends the traffic to the primary remote PE (the owner of the P=1 bit). In case of multiple primary PEs and ecmp>1, PE1 will load-balance the traffic to all the primary PEs, regardless of the multi-homing mode.
- If the last primary PE withdraws its AD per-EVI or ES route, PE1 sends the traffic to the backup PE or PEs. In case of multiple backup PEs and ecmp>1, PE1 load-balances the traffic to the backup PEs.
5.24. EVPN for MPLS Tunnels in Routed VPLS Services
EVPN-MPLS and IP-prefix advertisement (enabled by the ip-route-advertisement command) are fully supported in routed VPLS services and provide the same feature-set as EVPN-VXLAN. The following capabilities are supported in a service where bgp-evpn mpls is enabled:
- R-VPLS with VRRP support on the VPRN interfaces
- R-VPLS support including ip-route-advertisement with regular interfacesThis includes the advertisement and process of ip-prefix routes as per draft-ietf-bess-evpn-prefix-advertisement with the appropriate encoding for EVPN-MPLS.
- R-VPLS support including ip-route-advertisement with evpn-tunnel interfaces
- R-VPLS with IPv6 support on the VPRN IP interface
5.24.1. EVPN-MPLS Multi-Homing and Passive VRRP
SAP and spoke-SDP based Ethernet Segments are supported on R-VPLS services where bgp-evpn mpls is enabled.
Figure 166 shows an example of EVPN-MPLS multi-homing in R-VPLS services, with the following assumptions.
- There are two subnets for a given customer (for example, EVI1 and EVI2 in Figure 166), and a VPRN is instantiated in all the PEs for efficient inter-subnet forwarding.
- A “backhaul” R-VPLS with evpn-tunnel mode enabled is used in the core to interconnect all the VPRNs. EVPN IP-prefix routes are used to exchange the prefixes corresponding to the two subnets.
- An all-active ES is configured for EVI1 on PE1 and PE2.
- A single-active ES is configured for EVI2 on PE3 and PE4.
Figure 166: EVPN-MPLS Multi-Homing in R-VPLS Services
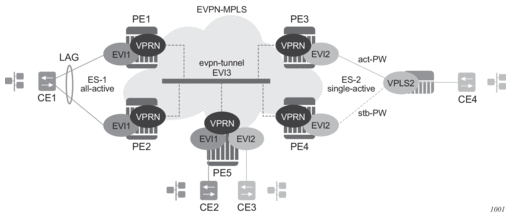
In the example in Figure 166, the hosts connected to CE1 and CE4 could use regular VRRP for default gateway redundancy; however, this may not be the most efficient way to provide upstream routing.
For example, if PE1 and PE2 are using regular VRRP, the upstream traffic from CE1 may be hashed to the backup IRB VRRP interface, instead of being hashed to the master. The same thing may occur for single-active multi-homing for PE3 and PE4. In both cases, unnecessary bandwidth between the PEs is used to get to the master IRB interface. In addition, VRRP scaling is limited if aggressive keepalive timers are used.
Because of these issues, passive VRRP is recommended as the best method when EVPN-MPLS multi-homing is used in combination with R-VPLS redundant interfaces.
Passive VRRP is a VRRP setting in which the transmission and reception of keepalive messages is completely suppressed, and therefore the VPRN interface always behaves as the master. Passive VRRP is enabled by adding the passive keyword to the VRRP instance at creation, as shown in the following examples:
config service vprn 1 interface int-1 vrrp 1 passive
config service vprn 1 interface int-1 ipv6 vrrp 1 passive
For example, if PE1, PE2, and PE5 in Figure 166 use passive VRRP, even if each individual R-VPLS interface has a different MAC/IP address, because they share the same VRRP instance 1 and the same backup IP, the three PEs will own the same virtual MAC and virtual IP address (for example, 00-00-5E-00-00-01 and 10.0.0.254). The virtual MAC is auto-derived from 00-00-5E-00-00-VRID per RFC 3768. The following is the expected behavior when passive VRRP is used in this example.
- All R-VPLS IRB interfaces for EVI1 have their own physical MAC/IP address; they will also own the same default gateway virtual MAC and IP address.
- All EVI1 hosts have a unique configured default gateway; for example, 10.0.0.254.
- When CE1 or CE2 send upstream traffic to a remote subnet, the packets are routed by the closest PE because the virtual MAC is always local to the PE.For example, the packets from CE1 hashed to PE1 will be routed at PE1. The packets from CE1 hashed to PE2 will be routed directly at PE2.
- Downstream packets (for example, packets from CE3 to CE1), are routed directly by the PE to CE1, regardless of the PE to which PE5 routed the packets.For example, the packets from CE3 sent to PE1 will be routed at PE1. The packets from CE3 sent to PE2 will be routed at PE2.
- In case of ES failure in one of the PEs, the traffic will be forwarded by the available PE.For example, if the packets routed by PE5 arrive at PE1 and the link to CE1 is down, then PE1 will send the packets to PE2. PE2 will forward the packets to CE1 even if the MAC source address of the packets matches PE2's virtual MAC address. Virtual MACs bypass the R-VPLS interface MAC protection.
The following list summarizes the advantages of using passive VRRP mode versus regular VRRP for EVPN-MPLS multi-homing in R-VPLS services.
- Passive VRRP does not require multiple VRRP instances to achieve default gateway load-balancing. Only one instance per R-VPLS, hence only one default gateway, is needed for all the hosts.
- The convergence time for link/node failures is not impacted by the VRRP convergence, as all the nodes in the VRRP instance are master routers.
- Passive VRRP scales better than VRRP, as it does not use keepalive or BFD messages to detect failures and allow the backup to take over.
5.25. P2MP mLDP tunnels for BUM traffic in EVPN-MPLS Services
P2MP mLDP tunnels for BUM traffic in EVPN-MPLS services are supported and enabled through the use of the provider-tunnel context. If EVPN-MPLS takes ownership over the provider-tunnel, bgp-ad is still supported in the service but it will not generate BGP updates, including the PMSI Tunnel Attribute. The following CLI example shows an EVPN-MPLS service that uses P2MP mLDP LSPs for BUM traffic.
When provider-tunnel inclusive is used in EVPN-MPLS services, the following commands can be used in the same way as for BGP-AD or BGP-VPLS services:
- data-delay-interval
- root-and-leaf
- mldp
- shutdown
The following commands are used by provider-tunnel in BGP-EVPN MPLS services:
- [no] ingress-replication-incl-mcast-advertisementThis command allows you to control the advertisement of IMET-IR and IMET-P2MP-IR routes for the service. See BGP-EVPN Control Plane for MPLS Tunnels for a description of the IMET routes. The following considerations apply:
- If configured as no ingress-replication-incl-mcast-advertisement, the system will not send the IMET-IR or IMET-P2MP-IR routes, regardless of the service being enabled for bgp-evpn mpls or bgp-evpn vxlan.
- If configured as ingress-replication-incl-mcast-advertisement and the PE is root-and-leaf, the system will send an IMET-P2MP-IR route.
- If configured as ingress-replication-incl-mcast-advertisement and the PE is no root-and-leaf, the system will send an IMET-IR route.
- Default value is ingress-replication-incl-mcast-advertisement.
- [no] owner {bgp-ad|bgp-vpls|bgp-evpn-mpls}The owner of the provider tunnel must be configured. The default value is no owner. The following considerations apply:
- Only one of the protocols will support a provider tunnel in the service and it must be explicitly configured.
- bgp-vpls and bgp-evpn are mutually-exclusive.
- While bgp-ad and bgp-evpn can coexist in the same service, only bgp-evpn can be the provider-tunnel owner in such cases.
Figure 167 shows the use of P2MP mLDP tunnels in an EVI with a root node and a few leaf-only nodes.
Figure 167: EVPN Services with p2mp mLDP—Control Plane
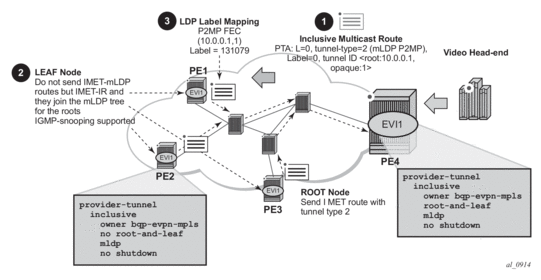
Consider the use-case of a root-and-leaf PE4 where the other nodes are configured as leaf-only nodes (no root-and-leaf). This scenario is handled as follows:
- If ingress-replication-incl-mcast-advertisement is configured, then as soon as the bgp-evpn mpls option is enabled, the PE4 sends an IMET-P2MP route (tunnel type mLDP), or optionally, an IMET-P2MP-IR route (tunnel type composite). IMET-P2MP-IR routes allow leaf-only nodes to create EVPN-MPLS multicast destinations and send BUM traffic to the root.
- If ingress-replication-incl-mcast-advertisement is configured, PE1/2/3 will not send IMET-P2MP routes; only IMET-IR routes will be sent.
- The root-and-leaf node will import the IMET-IR routes from the leaf nodes but it will only send BUM traffic to the P2MP tunnel as long as it is active.
- If the P2MP tunnel goes operationally down, the root-and-leaf node will start sending BUM traffic to the evpn-mpls multicast destinations
- When PE1/2/3 receive and import the IMET-P2MP or IMET-P2MP-IR from PE4, they will join the mLDP P2MP tree signaled by PE4. They will issue an LDP label-mapping message including the corresponding P2MP FEC.
As described in draft-ietf-bess-evpn-etree, mLDP and Ingress Replication (IR) can work in the same network for the same service; that is, EVI1 can have some nodes using mLDP (for example, PE1) and others using IR (for example, PE2). For scaling, this is significantly important in services that consist of a pair of root nodes sending BUM in P2MP tunnels and hundreds of leaf-nodes that only need to send BUM traffic to the roots. By using IMET-P2MP-IR routes from the roots, the operator makes sure the leaf-only nodes can send BUM traffic to the root nodes without the need to set up P2MP tunnels from the leaf nodes.
When both static and dynamic P2MP mLDP tunnels are used on the same router, it is recommended that the static tunnels use a tunnel ID lower than 8193. If a tunnel ID is statically configured with a value equal to or greater than 8193, BGP-EVPN may attempt to use the same tunnel ID for services with enabled provider-tunnel, and fail to set up an mLDP tunnel.
5.26. BGP-EVPN Control Plane for PBB-EVPN
PBB-EVPN uses a reduced subset of the routes and procedures described in RFC 7432. The supported routes are:
- ES routes
- MAC/IP routes
- Inclusive Multicast Ethernet Tag routes.
5.26.1. EVPN Route Type 3 - Inclusive Multicast Ethernet Tag Route
This route is used to advertise the ISIDs that belong to I-VPLS services as well as the default multicast tree. PBB-epipe ISIDs are not advertised in Inclusive Multicast routes. The following fields are used:
- Route Distinguisher: Taken from the RD of the B-VPLS service within the BGP context. Note that the RD can be configured or derived from the bgp-evpn evi value.
- Ethernet Tag ID: Encodes the ISID for a specified I-VPLS.
- IP address length: Always 32.
- Originating router's IP address: Carries the system address (IPv4 only).
- PMSI attribute:
- Tunnel type = Ingress replication (6).
- Flags = Leaf no required.
- MPLS label: Carries the MPLS label allocated for the service in the high-order 20 bits of the label field.

Note: This label will be the same label used in the BMAC routes for the same B-VPLS service unless bgp-evpn mpls ingress-replication-bum-label is configured in the B-VPLS service.
- Tunnel end-point = equal to the originating IP address.
5.26.2. EVPN Route Type 2 - MAC/IP Advertisement Route (or BMAC Routes)
The 7750 SR, 7450 ESS, or 7950 XRS will generate this route type for advertising BMAC addresses for the following:
- Learned MACs on B-SAPs or B-SDP-bindings - if mac-advertisement is enabled.
- Conditional static MACs - if mac-advertisement is enabled.
- B-VPLS shared-BMACs (source-bmacs) and dedicated-BMACs (es-bmacs).
The route type 2 generated by the router uses the following fields and values:
- Route Distinguisher—Taken from the RD of the VPLS service within the BGP context. Note that the RD can be configured or derived from the bgp-evpn evi value.
- Ethernet Segment Identifier (ESI):
- ESI = 0 for the advertisement of source-bmac, es-bmacs, sap-bmacs, or sdp-bmacs if no multi-homing or single-active multi-homing is used.
- ESI=MAX-ESI (0xFF..FF) in the advertisement of es-bmacs used for all-active multi-homing.
- ESI different from zero or MAX-ESI for learned BMACs on B-SAPs/SDP-bindings if EVPN multi-homing is used on B-VPLS SAPs and SDP-bindings.
- Ethernet Tag ID: 0.Note: A different Ethernet Tag value may be used only when send-bvpls-evpn-flush is enabled.
- MAC address length: Always 48.
- BMAC Address learned, configured, or system-generated.
- IP address length zero and IP address omitted.
- MPLS Label 1: carries the MPLS label allocated by the system to the B-VPLS service. The label value is encoded in the high-order 20 bits of the field and will be the same label used in the routes type 3 for the same service unless bgp-evpn mpls ingress-replication-bum-label is configured in the service.
- The MAC Mobility extended community:
- The mac mobility extended community is used in PBB-EVPN for CMAC flush purposes if per ISID load balancing (single-active multi-homing) is used and a source-bmac is used for traffic coming from the ESI.If there is a failure in one of the ES links, CMAC flush through the withdrawal of the BMAC CANNOT be done (other ESIs are still working); therefore, the mac mobility extended community is used to signal CMAC flush to the remote PEs.
- When a dedicated es-bmac per ESI is used, the mac flush can be based on the withdrawal of the BMAC from the failing node.
- es-bmacs will be advertised as static (sticky bit set).
- Source-bmacs will be advertised as static MACs (sticky bit set). In the case of an update, if advertised to indicate that CMAC flush is needed, the mac mobility extended community will be added to the BMAC route including a higher sequence number (than the one previously advertised) in addition to the sticky bit.
5.26.3. EVPN Route Type 4 - Ethernet Segment Route
This route type is used for DF election as described in section BGP-EVPN Control Plane for MPLS Tunnels.
| Note: The EVPN route type 1—Ethernet Auto Discovery route is not used in PBB-EVPN. |
5.27. PBB-EVPN for I-VPLS and PBB Epipe Services
The 7750 SR, 7450 ESS, and 7950 XRS SR OS implementation of PBB-EVPN reuses the existing PBB-VPLS model, where N I-VPLS (or Epipe) services can be linked to a B-VPLS service. BGP-EVPN is enabled in the B-VPLS and the B-VPLS becomes an EVI (EVPN Instance). Figure 168 shows the PBB-EVPN model in the SR OS.
Figure 168: PBB-EVPN for I-VPLS and PFF Epipe Services
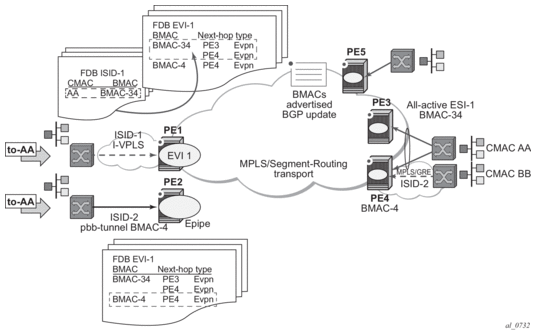
Each PE in the B-VPLS domain will advertise its source-bmac as either configured in (b)vpls>pbb>source-bmac or auto-derived from the chassis mac. The remote PEs will install the advertised BMACs in the B-VPLS FDB. If a specified PE is configured with an ethernet-segment associated with an I-VPLS or PBB Epipe, it may also advertise an es-bmac for the ethernet-segment.
In the example shown in Figure 168, when a frame with MAC DA = AA gets to PE1, a mac lookup is performed on the I-VPLS FDB and BMAC-34 is found. A BMAC lookup on the B-VPLS FDB will yield the next-hop (or next-hops if the destination is in an all-active ethernet-segment) to which the frame is sent. As in PBB-VPLS, the frame will be encapsulated with the corresponding PBB header. A label specified by EVPN for the B-VPLS and the MPLS transport label are also added.
If the lookup on the I-VPLS FDB fails, the system will send the frame encapsulated into a PBB packet with BMAC DA = Group BMAC for the ISID. That packet will be distributed to all the PEs where the ISID is defined and will contain the EVPN label distributed by the Inclusive Multicast routes for that ISID, in addition to the transport label.
For PBB-Epipes, all the traffic is sent in a unicast PBB packet to the BMAC configured in the pbb-tunnel.
The following CLI output shows an example of the configuration of an I-VPLS, PBB-Epipe, and their corresponding B-VPLS.
Configure the bgp-evpn context as described in section EVPN for MPLS Tunnels in VPLS Services (EVPN-MPLS).
Some EVPN configuration options are not relevant to PBB-EVPN and are not supported when bgp-evpn is configured in a B-VPLS; these are as follows:
- bgp-evpn> [no] ip-route-advertisement
- bgp-evpn> [no] unknown-mac-route
- bgp-evpn> vxlan [no] shutdown
- bgp-evpn>mpls>force-vlan-vc-forwarding
When bgp-evpn>mpls no shutdown is added to a specified B-VPLS instance, the following considerations apply:
- BGP-AD is supported along with EVPN in the same B-VPLS instance.
- The following B-VPLS and BGP-EVPN commands are fully supported:
- vpls>backbone-vpls
- vpls>backbone-vpls>send-flush-on-bvpls-failure
- vpls>backbone-vpls>source-bmac
- vpls>backbone-vpls>use-sap-bmac
- vpls>backbone-vpls>use-es-bmac (See PBB-EVPN Multi-Homing in I-VPLS and PBB Epipe Services for more information)
- vpls>isid-policies
- vpls>static-mac
- vpls>sap/sdp-binding>static-isid
- bgp-evpn>mac-advertisement - this command will only have affect on the 'learned' BMACs on saps or sdp-bindings and not on the system BMAC or sap/es-bmacs being advertised.
- bgp-evpn>mac-duplication and settings.
- bgp-evpn>mpls>auto-bind-tunnel and options.
- bgp-evpn>mpls>ecmp
- bgp-evpn>mpls>control-word
- bgp-evpn>evi
- bgp-evpn>mpls>ingress-replication-bum-label
5.27.1. Flood Containment for I-VPLS Services
In general, PBB technologies in the 7750 SR, 7450 ESS, or 7950 XRS SR OS support a way to contain the flooding for a specified I-VPLS ISID, so that BUM traffic for that ISID only reaches the PEs where the ISID is locally defined. Each PE will create an MFIB per I-VPLS ISID on the B-VPLS instance. That MFIB supports SAP/SDP-bindings endpoints that can be populated by:
- MMRP in regular PBB-VPLS
- IS-IS in SPBM
In PBB-EVPN, B-VPLS EVPN endpoints can be added to the MFIBs using EVPN Inclusive Multicast Ethernet Tag routes.
The example in Figure 169 shows how the MFIBs are populated in PBB-EVPN.
Figure 169: PBB-EVPN and I-VPLS Flooding Containment
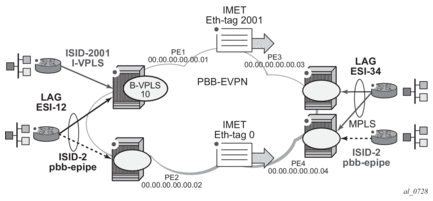
When the B-VPLS 10 is enabled, PE1 will advertise as follows:
- A BMAC route containing PE1's system BMAC (00:01 as configured in pbb>source-bmac) along with an MPLS label.
- An Inclusive Multicast Ethernet Tag route (IMET route) with Ethernet-tag = 0 that will allow the remote B-VPLS 10 instances to add an entry for PE1 in the default multicast list.
| Note: The MPLS label that will be advertised for the MAC routes and the inclusive multicast routes for a specified B-VPLS can be the same label or a different label. As in regular EVPN-MPLS, this will depend on the [no] ingress-replication-bum-label command. |
When I-VPLS 2001 (ISID 2001) is enabled as per the CLI in the preceding section, PE1 will advertise as follows:
- An additional inclusive multicast route with Ethernet-tag = 2001. This will allow the remote PEs to create an MFIB for the corresponding ISID 2001 and add the corresponding EVPN binding entry to the MFIB.This default behavior can be modified by the configured isid-policy. For instance, for ISIDs 1-2000, configure as follows:
This configuration has the following effect for the ISID range:
- no advertise-local instructs the system to not advertise the local active ISIDs contained in the 1 to 2001 range.
- use-def-mcast instructs the system to use the default flooding list as opposed to the MFIB.
The ISID flooding behavior on B-VPLS saps and sdp-bindings is as follows:
- B-VPLS saps and sdp-bindings are only added to the TLS-multicast list and not to the MFIB list (unless static-isids are configured, which is only possible for saps/sdp-bindings and not BGP-AD spoke-sdps).As a result, if the system needs to flood ISID BUM traffic and the ISID is also defined in remote PEs connected through saps or spoke-sdps without static-isids, then an isid-policy must be configured for the ISID so that the ISID uses the default multicast list.
- When an isid-policy is configured and a range of ISIDs use the default multicast list, the remote PBB-EVPN PEs will be added to the default multicast list as long as they advertise an IMET route with an ISID included in the policy's ISID range. PEs advertising IMET routes with Ethernet-tag = 0 are also added to the default multicast list (7750 SR, 7450 ESS, or 7950 XRS SR OS behavior).
- The B-VPLS 10 also allows the ISID flooding to legacy PBB networks via B-SAPs or B-SDPs. The legacy PBB network BMACs will be dynamically learned on those saps/binds or statically configured through the use of conditional static-macs. The use of static-isids is required so that non-local ISIDs are advertised.
| Note: The configuration of PBB-Epipes does not trigger any IMET advertisement. |
5.27.2. PBB-EVPN and PBB-VPLS Integration
The 7750 SR, 7450 ESS, and 7950 XRS SR OS EVPN implementation supports draft-ietf-bess-evpn-vpls-seamless-integ so that PBB-EVPN and PBB-VPLS can be integrated into the same network and within the same B-VPLS service.
All the concepts described in section PBB-EVPN and PBB-VPLS Integration are also supported in B-VPLS services so that B-VPLS SAP/SDP-bindings can be integrated with PBB-EVPN destination bindings. The features described in that section also facilitate a smooth migration from B-VPLS SDP-bindings to PBB-EVPN destination bindings.
5.27.3. PBB-EVPN Multi-Homing in I-VPLS and PBB Epipe Services
The 7750 SR, 7450 ESS, and 7950 XRS SR OS PBB-EVPN implementation supports all-active and single-active multi-homing for I-VPLS and PBB Epipe services.
PBB-EVPN multi-homing reuses the ethernet-segment concept described in section EVPN Multi-Homing in VPLS Services. However, unlike EVPN-MPLS, PBB-EVPN does not use AD routes; it uses BMACs for split-horizon checks and aliasing.
5.27.3.1. System BMAC Assignment in PBB-EVPN
RFC 7623 describes two types of BMAC assignments that a PE can implement:
- Shared BMAC addresses that can be used for single-homed CEs and a number of multi-homed CEs connected to ethernet-segments.
- Dedicated BMAC addresses per ethernet-segment.
In this document and in 7750 SR, 7450 ESS, and 7950 XRS SR OS terminology:
- A shared-bmac (in IETF) is a source-bmac as configured in service>(b)vpls>pbb>source-bmac
- A dedicated-bmac per ES (in IETF) is an es-bmac as configured in service>pbb>use-es-bmac
BMAC selection and use depends on the multi-homing model; for single-active mode, the type of BMAC will impact the flooding in the network as follows:
- All-active multi-homing requires es-bmacs.
- Single-active multi-homing can use es-bmacs or source-bmacs.
- The use of source-bmacs minimizes the number of BMACs being advertised but has a larger impact on CMAC flush upon ES failures.
- The use of es-bmacs optimizes the CMAC flush upon ES failures at the expense of advertising more BMACs.
5.27.3.2. PBB-EVPN all-active multi-homing service model
Figure 170 shows the use of all-active multi-homing in the 7750 SR, 7450 ESS, and 7950 XRS SR OS PBB-EVPN implementation.
Figure 170: PBB-EVPN All-Active Multi-Homing
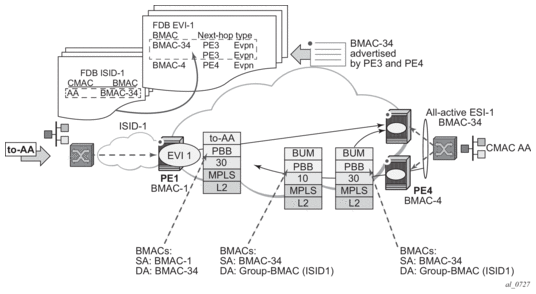
For example, the following shows the ESI-1 and all-active configuration in PE3 and PE4. As in EVPN-MPLS, all-active multi-homing is only possible if a LAG is used at the CE. All-active multi-homing uses es-bmacs, that is, each ESI will be assigned a dedicated BMAC. All the PEs part of the ES will source traffic using the same es-bmac.
In Figure 170 and the following configuration, the es-bmac used by PE3 and PE4 will be BMAC-34, i.e. 00:00:00:00:00:34. The es-bmac for a specified ethernet-segment is configured by the source-bmac-lsb along with the (b-)vpls>pbb>use-es-bmac command.
Configuration in PE3:
Configuration in PE4:
The above configuration will enable the all-active multi-homing procedures for PBB-EVPN.
| Note: The ethernet-segment ESI-1 can also be used for regular VPLS services. |
The following considerations apply when the ESI is used for PBB-EVPN.
- ESI association: Only LAG is supported for all-active multi-homing. The following commands are used for the LAG to ESI association:
- config>service>system>bgp-evpn>ethernet-segment# lag <id>
- config>service>system>bgp-evpn>ethernet-segment# source-bmac-lsb <MAC-lsb> [es-bmac-table-size <size>]
- Where:
- The same ESI may be used for EVPN and PBB-EVPN services.
- For PBB-EVPN services, the source-bmac-lsb attribute is mandatory and ignored for EVPN-MPLS services.
- The source-bmac-lsb attribute must be set to a specific 2-byte value. The value must match on all the PEs part of the same ESI, for example, PE3 and PE4 for ESI-1. This means that the configured pbb>source-bmac on the two PEs for B-VPLS 1 must have the same 4 most significant bytes.
- The es-bmac-table-size parameter modifies the default value (8) for the maximum number of virtual BMACs that can be associated with the ethernet-segment, i.e. es-bmacs. When the source-bmac-lsb is configured, the associated es-bmac-table-size is reserved out of the total FDB space.
- When multi-homing all-active is configured within the ethernet-segment, only a LAG can be associated with it. The association of a port or an sdp will be restricted by the CLI.
- If service-carving is configured in the ESI, the DF election algorithm will be a modulo function of the ISID and the number of PEs part of the ESI, as opposed to a modulo function of evi and number of PEs (used for EVPN-MPLS).
- A service-carving mode manual option is added so that the user can control what PE is DF for a specified ISID. The PE will be DF for the configured ISIDs and non-DF for the non-configured ISIDs.
- DF election: An all-active Designated Forwarder (DF) election is also carried out for PBB-EVPN. In this case, the DF election defines which of the PEs of the ESI for a specified I-VPLS is the one able to send the downstream BUM traffic to the CE. Only one DF per ESI is allowed in the I-VPLS service, and the non-DF will only block BUM traffic and in the downstream direction.
- Split-horizon function: In PBB-EVPN, the split-horizon function to avoid echoed packets on the CE is based on an ingress lookup of the ES BMAC (as opposed to the ESI label in EVPN-MPLS). In Figure 170 PE3 sends packets using BMAC SA = BMAC-34. PE4 does not send those packets back to the CE because BMAC-34 is identified as the es-bmac for ESI-1.
- Aliasing: In PBB-EVPN, aliasing is based on the ES BMAC sent by all the PEs part of the same ESI. See the following section for more information. In Figure 170 PE1 performs load balancing between PE3 and PE4 when sending unicast flows to BMAC-34 (es-bmac for ESI-1).
In the configuration above, a PBB-Epipe is configured in PE3 and PE4, both pointing at the same remote pbb tunnel backbone-dest-mac. On the remote PE, i.e. PE1, the configuration of the PBB-Epipe will point at the es-bmac:
When PBB-Epipes are used in combination with all-active multi-homing, Nokia recommends using bgp-evpn mpls ingress-replication-bum-label in the PEs where the ethernet-segment is created, that is in PE3 and PE4. This guarantees that in case of flooding in the B-VPLS service for the PBB Epipe, only the DF will forward the traffic to the CE.
| Note: PBB-Epipe traffic always uses BMAC DA = unicast; therefore, the DF cannot check whether the inner frame is unknown unicast or not based on the group BMAC. Therefore, the use of an EVPN BUM label is highly recommended. |
Aliasing for PBB-epipes with all-active multi-homing only works if shared-queuing or ingress policing is enabled on the ingress PE epipe. In any other case, the IOM will send the traffic to a single destination (no ECMP will be used in spite of the bgp-evpn mpls ecmp setting).
All-active multi-homed es-bmacs are treated by the remote PEs as eES:MAX-ESI BMACs. The following example shows the FDB in B-VPLS 1 in PE1 as shown in Figure 170:
The show service id evpn-mpls on PE1 shows that the remote es-bmac, i.e. 00:00:00:00:00:34, has two associated next-hops, i.e. PE3 and PE4:
5.27.3.2.1. Network failures and convergence for all-active multi-homing
ES failures are resolved by the PEs withdrawing the es-bmac. The remote PEs will withdraw the route and update their list of next-hops for a specified es-bmac.
No mac-flush of the I-VPLS FDB tables is required as long as the es-bmac is still in the FDB.
When the route corresponding to the last next-hop for a specified es-bmac is withdrawn, the es-bmac will be flushed from the B-VPLS FDB and all the CMACs associated with it will be flushed too.
The following events will trigger a withdrawal of the es-bmac and the corresponding next-hop update in the remote PEs:
- B-VPLS transition to oper-down status.
- Change of pbb>source-bmac.
- Change of es-bmac (or removal of pbb use-es-bmac).
- Ethernet-segment transition to oper-down status.
| Note: Individual saps going oper-down in an ES will not generate any BGP withdrawal or indication so that the remote nodes can flush their CMACs. This is solved in EVPN-MPLS by the use of AD routes per EVI; however, there is nothing similar in PBB-EVPN for indicating a partial failure in an ESI. |
5.27.3.3. PBB-EVPN Single-Active Multi-Homing Service Model
In single-active multi-homing, the non-DF PEs for a specified ESI will block unicast and BUM traffic in both directions (upstream and downstream) on the object associated with the ESI. Other than that, single-active multi-homing will follow the same service model defined in the section 'PBB-EVPN all-active multi-homing service model' with the following differences:
- The ethernet-segment will be configured for single-active: service>system>bgp-evpn>ethernet-segment>multi-homing single-active.
- For single-active multi-homing, the ethernet-segment can be associated with a port and sdp, as well as a lag.
- From a service perspective, single-active multi-homing can provide redundancy to the following services and access types:
- I-VPLS LAG and regular SAPs
- I-VPLS active/standby spoke-sdps
- EVPN single-active multi-homing is supported for PBB-Epipes only in two-node scenarios with local switching.
- While all-active multi-homing only uses es-bmac assignment to the ES, single-active multi-homing can use source-bmac or es-bmac assignment. The system allows the following user choices per B-VPLS and ES:
- A dedicated es-bmac per ES can be used. In that case, the pbb>use-es-bmac command will be configured in the B-VPLS and the same procedures explained in PBB-EVPN all-active multi-homing service model will follow with one difference. While in all-active multi-homing all the PEs part of the ESI will source the PBB packets with the same source es-bmac, single-active multi-homing requires the use of a different es-bmac per PE.
- A non-dedicated source-bmac can be used. In this case, the user will not configure pbb>use-es-bmac and the regular source-bmac will be used for the traffic. A different source-bmac has to be advertised per PE.
- The use of source-bmacs or es-bmacs for single-active multi-homed ESIs has a different impact on CMAC flushing, as shown in Figure 171.
Figure 171: Source-Bmac Versus Es-Bmac CMAC Flushing

- If es-bmacs are used as shown in the representation on the right in Figure 171, a less-impacting CMAC flush is achieved, therefore, minimizing the flooding after ESI failures. In case of ESI failure, PE1 will withdraw the es-bmac 00:12 and the remote PE3 will only flush the CMACs associated with that es-bmac (only the CMACs behind the CE are flushed).
- If source-bmacs are used, as shown on the left-hand side of Figure Figure 171, in case of ES failure, a BGP update with higher sequence number will be issued by PE1 and the remote PE3 will flush all the CMACs associated with the source-bmac. Therefore, all the CMACs behind the PE's B-VPLS will be flushed, as opposed to only the CMACs behind the ESI's CE.
- As in EVPN-MPLS, the non-DF status can be notified to the access CE or network:
- LAG with or without LACP: In this case, the multi-homed ports on the CE will NOT be part of the same LAG. The non-DF PE for each service may signal that the LAG sap is oper-down by using eth-cfm fault-propagation-enable {use-if-tlv|suspend-ccm}.
- Regular Ethernet 802.1q/ad ports: In this case, the multi-homed ports on the CE/network will not be part of any LAG. The non-DF PE for each service will signal that the sap is oper-down by using eth-cfm fault-propagation-enable {use-if-tlv|suspend-ccm}.
- Active-standby PWs: in this case, the multihomed CE/network is connected to the PEs through an MPLS network and an active/standby spoke-sdp per service. The non-DF PE for each service will make use of the LDP PW status bits to signal that the spoke-sdp is standby at the PE side. Nokia recommends that the CE suppresses the signaling of PW status standby.
5.27.3.3.1. Network Failures and Convergence for Single-Active Multihoming
ESI failures are resolved depending on the BMAC address assignment chosen by the user:
- If the BMAC address assignment is based on the use of es-bmacs, DF and non-DFs will send the es-bmac/ESI=0 for a specified ESI. Each PE will have a different es-bmac for the same ESI (as opposed to the same es-bmac on all the PEs for all-active). In case of an ESI failure on a PE:
- The PE will withdraw its es-bmac route triggering a mac-flush of all the CMACs associated with it in the remote PEs.
- If the BMAC address assignment is based on the use of source-bmac, DF and non-DFs will advertise their respective source-bmacs. In case of an ES failure:
- The PE will re-advertise its source-bmac with a higher sequence number (the new DF will not re-advertise its source-bmac).
- The far-end PEs will interpret a source-bmac advertisement with a different sequence number as a flush-all-from-me message from the PE detecting the failure. They will flush all the CMACs associated with that BMAC in all the ISID services.
The following events will trigger a CMAC flush notification. A 'CMAC flush notification' means the withdrawal of a specified BMAC or the update of BMAC with a higher sequence number (SQN). Both BGP messages will make the remote PEs flush all the CMACs associated with the indicated BMAC:
- B-VPLS transition to oper-down status. This will trigger the withdrawal of the associated BMACs, regardless of the use-es-bmac setting.
- Change of pbb>source-bmac. This will trigger the withdrawal and re-advertisement of the source-bmac, causing the corresponding CMAC flush in the remote PEs.
- Change of es-bmac (removal of pbb use-es-bmac). This will trigger the withdrawal of the es-bmac and re-advertisement of the new es-bmac.
- Ethernet-Segment (ES) transition to oper-down or admin-down status. This will trigger an es-bmac withdrawal (if use-es-bmac is used) or an update of the source-bmac with a higher SQN (if no use-es-bmac is used).
- Service Carving Range change for the ES. This will trigger an es-bmac update with higher SQN (if use-es-bmac is used) or an update of the source-bmac with a higher SQN (if no use-es-bmac is used).
- Change in the number of candidate PEs for the ES. This will trigger an es-bmac update with higher SQN (if use-es-bmac is used) or an update of the source-bmac with a higher SQN (if no use-es-bmac is used).
- In an ESI, individual saps/sdp-bindings or individual I-VPLS going oper-down will not generate any BGP withdrawal or indication so that the remote nodes can flush their CMACs. This is solved in EVPN-MPLS by the use of AD routes per EVI; however, there is nothing similar in PBB-EVPN for indicating a partial failure in an ESI.
5.27.3.4. PBB-Epipes and EVPN Multi-Homing
EVPN multi-homing is supported with PBB-EVPN Epipes, but only in a limited number of scenarios. In general, the following applies to PBB-EVPN Epipes:
- PBB-EVPN Epipes don't support spoke-sdps that are associated with EVPN Ethernet Segments (ES).
- PBB-EVPN Epipes support all-active EVPN multi-homing as long as no local-switching is required in the Epipe instance where the ES is defined.
- PBB-EVPN Epipes support single-active EVPN multi-homing only in a two-node case scenario.
Figure 172 shows the EVPN MH support in a three-node scenario.
Figure 172: PBB-EVPN MH in a Three-Node Scenario
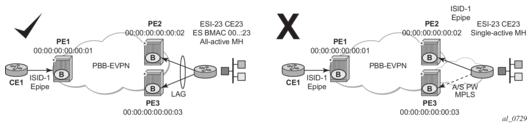
EVPN MH support in a three-node scenario has the following characteristics:
- All-active EVPN multi-homing is fully supported (diagram on the left in Figure 172). CE1 might also be multi-homed to other PEs, as long as those PEs are not PE2 or PE3. In this case, PE1 Epipe's pbb-tunnel would be configured with the remote ES BMAC.
- Single-active EVPN multi-homing is NOT supported in a three (or more)-node scenario (diagram on the right in Figure 172). Since PE1's Epipe pbb-tunnel can only point at a single remote BMAC and single-active multi-homing requires the use of separate BMACs on PE2 and PE3, the scenario is not possible and not supported regardless of the ES association to port/LAG/sdps.
- Regardless of the EVPN multi-homing type, the CLI prevents the user from adding a spoke-sdp to an Epipe, if the corresponding SDP is part of an ES.
Figure 173 shows the EVPN MH support in a two-node scenario.
Figure 173: PBB-EVPN MH in a Two-Node Scenario
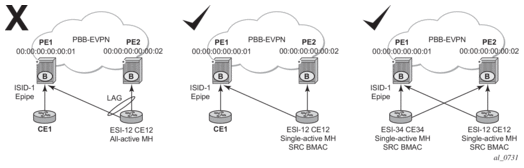
EVPN MH support in a two-node scenario has the following characteristics, as shown in Figure 173:
- All-active multi-homing is not supported for redundancy in this scenario because PE1's pbb-tunnel cannot point at a locally defined ES-BMAC. This is represented in the left-most scenario in Figure 173.
- Single-active multi-homing is supported for redundancy in a two-node three or four SAP scenario, as displayed by the two right-most scenarios in Figure 173).In these two cases, the Epipe pbb-tunnel will be configured with the source BMAC of the remote PE node.When two saps are active in the same Epipe, local-switching is used to exchange frames between the CEs.
5.27.3.5. PBB-EVPN and Use of P2MP mLDP Tunnels for Default Multicast List
P2MP mLDP tunnels can also be used in PBB-EVPN services. The use of provider-tunnel inclusive MLDP is only supported in the B-VPLS default multicast list; that is, no per-ISID IMET-P2MP routes are supported. IMET-P2MP routes in a B-VPLS are always advertised with Eth-tag zero.
B-VPLS supports the use of MFIBs for ISIDs using ingress replication. The following considerations apply when provider-tunnel is enabled in a B-VPLS service.
- Local I-VPLS or static-ISIDs configured on the B-VPLS will generate IMET-IR routes and MFIBs will be created per ISID by default.
- The default IMET-P2MP or IMET-P2MP-IR route sent with ethernet-tag = 0 will be issued depending on the ingress-replication-incl-mcast-advertisement command.
- The following considerations apply if an isid-policy is configured in the B-VPLS.
- A range of ISIDs configured with use-def-mcast will make use of the P2MP tree, assuming the node is configured as root-and-leaf.
- A range of ISIDs configured with advertise-local will make the system advertise IMET-IR routes for the local ISIDs included in the range.
The following example CLI output shows a range of ISIDs (1000-2000) that use the P2MP tree and the system does not advertise the IMET-IR routes for those ISIDs. Other local ISIDs will advertise the IMET-IR and will use the MFIB to forward BUM packets to the EVPN-MPLS destinations created by the IMET-IR routes.
5.27.3.6. PBB-EVPN ISID-Based CMAC Flush
The SR OS supports ISID-based CMAC flush procedures for PBB-EVPN I-VPLS services where no Ethernet segments are used and other redundancy mechanisms, such as BGP-MH, need these procedures to avoid black-holes caused by a SAP failure.
The CMAC flush procedures are enabled on the I-VPLS service using the config>service>vpls>pbb>send-bvpls-evpn-flush CLI command. The feature can be disabled on a per-SAP basis using the config>service>vpls>sap>disable-send-bvpls-evpn-flush command.
With the feature enabled on an I-VPLS service and a SAP, if there is a SAP failure, the router sends a CMAC flush notification for the corresponding BMAC and ISID. The router receiving the notification flushes all the CMACs associated with the indicated BMAC and ISID when the config>service>vpls>bgp-evpn>accept-ivpls-evpn-flush command is enabled for the B-VPLS service.
The CMAC flush notification consists of an EVPN BMAC route that is encoded as follows: the ISID to be flushed is encoded in the Ethernet Tag field and the sequence number is incremented with respect to the previously advertised route.
Ethernet Segment SAPs or spoke SDPs (whether they are associated with an ethernet-segment or not) are not supported on I-VPLS services where the CMAC flush feature is enabled (send-bvpls-evpn-flush).
Figure 174 shows an example where the ISID-based CMAC flush prevents black-hole situations for a CE that is using BGP-MH as the redundancy mechanism in the I-VPLS with an ISID of 3000.
Figure 174: Per-ISID CMAC Flush Following a SAP Failure
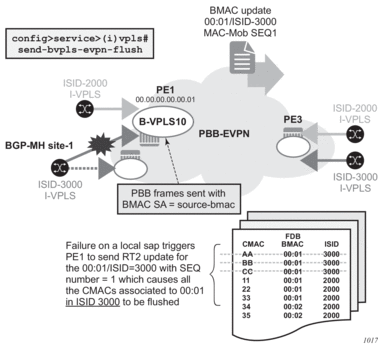
When send-bvpls-evpn-flush is enabled, the I-VPLS service is ready to send per-ISID CMAC flush messages in the form of BMAC/ISID routes. The first BMAC/ISID route for an I-VPLS service is sent with sequence number zero; subsequent updates for the same route increment the sequence number. A BMAC/ISID route for the I-VPLS is advertised or withdrawn in the following cases:
- during I-VPLS send-bvpls-evpn-flush configuration and deconfiguration
- during I-VPLS association and disassociation from the B-VPLS service
- during I-VPLS operational status change (up/down)
- during B-VPLS operational status change (up/down)
- during B-VPLS bgp-evpn mpls status change (no shutdown/shutdown)
- during B-VPLS operational source BMAC change
- if no disable-send-bvpls-evpn-flush is configured for a SAP, upon a failure on that SAP, the system will send a per-ISID CMAC flush message; that is, a BMAC/ISID route update with an incremented sequence number
If the user explicitly configures disable-send-bvpls-evpn-flush for a SAP, the system will not send per-ISID CMAC flush messages for failures on that SAP.
The B-VPLS on the receiving node must be configured with bgp-evpn>accept-ivpls-evpn-flush to accept and process CMAC flush non-zero Ethernet-tag MAC routes. If the accept-ivpls-evpn-flush command is enabled (the command is disabled by default), the node accepts non-zero Ethernet-tag MAC routes (BMAC/ISID routes) and processes them. When a new BMAC/ISID update (with an incremented sequence number) for an existing route is received, the router will flush all the CMACs associated with that BMAC and ISID. The BMAC/ISID route withdrawals will also cause a CMAC flush.
| Note: Only BMAC routes with the Ethernet Tag field set to zero are considered for BMAC installation in the FDB. |
The following CLI example shows the commands that enable the CMAC flush feature on PE1 and PE3.
In the preceding example, with send-bvpls-evpn-flush enabled on the I-VPLS service of PE1, a BMAC/ISID route (for pbb source-bmac address BMAC 00:..:01 and ISID 3000) is advertised. If the SAP goes operationally down, PE1 will send an update of the source BMAC address (00:..:01) for ISID 3000 with a higher sequence number.
With accept-ivpls-evpn-flush enabled on PE3’s B-VPLS service, PE3 flushes all CMACs associated with BMAC 00:01 and ISID 3000. The CMACs associated with other BMACs and/or ISIDs are retained in PE3’s FDB.
5.28. ARP/ND Snooping and Proxy Support
VPLS services support proxy-ARP (Address Resolution Protocol) and proxy-ND (Neighbor Discovery) functions that can be enabled or disabled independently per service. When enabled (proxy-ARP/proxy-ND no shutdown), the system will populate the corresponding proxy-ARP/proxy-ND table with IP->MAC entries learned from the following sources:
- EVPN-received IP->MAC entries
- User-configured static IP->MAC entries
- Snooped dynamic IP->MAC entries (learned from ARP/GARP/NA messages received on local SAPs/SDP-bindings)
In addition, any ingress ARP or ND frame on a SAP or SDP-binding will be intercepted and processed. ARP requests and Neighbor Solicitations will be answered by the system if the requested IP address is present in the proxy table.
Figure 175 shows an example of how proxy-ARP is used in an EVPN network. Proxy-ND would work in a similar way. Note that the MAC address notation in the diagram is shortened for readability.
Figure 175: Proxy-ARP Example Usage in an EVNP Network
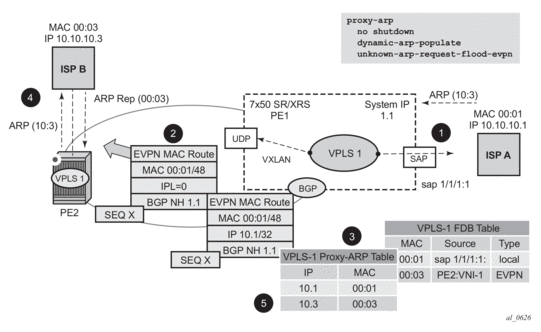
PE1 is configured as follows:
Figure 175 shows the following steps, assuming proxy-ARP is no shutdown on PE1 and PE2, and the tables are empty:
- ISP-A sends ARP-request for (10.10.)10.3.
- PE1 learns the MAC 00:01 in the FDB as usual and advertises it in EVPN without any IP. Optionally, the MAC can be configured as a CStatic mac, in which case it will be advertised as protected. If the MAC is learned on a SAP/SDP-binding where auto-learn-mac-protect is enabled, the MAC will also be advertised as protected.
- The ARP-request is sent to the CPM where:
- An ARP entry (IP 10.1'MAC 00:01) is populated into the proxy-ARP table.
- EVPN advertises MAC 00:01 and IP 10.1 in EVPN with the same SEQ number and Protected bit as the previous route-type 2 for MAC 00:01.
- A GARP is also issued to other SAPs/SDP-bindings (assuming they are not in the same split-horizon-group as the source). If garp-flood-evpn is enabled, the GARP message is also sent to the EVPN network.
- The original ARP-request can still be flooded to the EVPN or not based on the unknown-arp-request-flood-evpn command.
- Assuming PE1 was configured with unknown-arp-request-flood-evpn, the ARP-request is flooded to PE2 and delivered to ISP-B. ISP-B replies with its MAC in the ARP-reply. The ARP-reply is finally delivered to ISP-A.
- PE2 will learn MAC 00:01 in the FDB and the entry 10.1'00:01 in the proxy-ARP table, based on the EVPN advertisements.
- When ISP-B replies with its MAC in the ARP-reply:
- MAC 00:03 is learned in FDB at PE2 and advertised in EVPN.
- MAC 00:03 and IP 10.3 are learned in the proxy-ARP table and advertised in EVPN with the same SEQ number as the previous MAC route.
- ARP-reply is unicasted to MAC 00:01.
- EVPN advertisements are used to populate PE1's FDB (MAC 00:03) and proxy-ARP (IP 10.3—>MAC 00:03) tables as mentioned in 5.
From this point onward, the PEs reply to any ARP-request for 00:01 or 00:03, without the need for flooding the message in the EVPN network. By replying to known ARP-requests / Neighbor Solicitations, the PEs help to significantly reduce the flooding in the network.
Use the following commands to customize proxy-ARP/proxy-ND behavior:
- dynamic-arp-populate and dynamic-nd-populateEnables the addition of dynamic entries to the proxy-ARP or proxy-ND table (disabled by default). When executed, the system will populate proxy-ARP/proxy-ND entries from snooped GARP/ARP/NA messages on SAPs/SDP-bindings in addition to the entries coming from EVPN (if EVPN is enabled). These entries will be shown as dynamic.
- static <IPv4-address> <mac-address> and static <IPv4-address> <mac-address> and static <ipv6-address> <mac-address> {host|router}Configures static entries to be added to the table.

Note: A static IP->MACentry requires the addition of the MAC address to the FDB as either learned or CStatic (conditional static mac) in order to become active (Status —> active).
- age-time <60..86400> (seconds)Specifies the aging timer per proxy-ARP/proxy-ND entry. When the aging expires, the entry is flushed. The age is reset when a new ARP/GARP/NA for the same IP—>MAC is received.
- send-refresh <120..86400> (seconds)If enabled, the system will send ARP-request/Neighbor Solicitation messages at the configured time, so that the owner of the IP can reply and therefore refresh its IP—>MAC (proxy-ARP entry) and MAC (FDB entry).
- table-size [1..16384]Enables the user to limit the number of entries learned on a specified service. By default, the table-size limit is 250.The unknown ARP-requests, NS, or the unsolicited GARPs and NA messages can be configured to be flooded or not in an EVPN network with the following commands:
- proxy-arp [no] unknown-arp-request-flood-evpn
- proxy-arp [no] garp-flood-evpn
- proxy-nd [no] unknown-ns-flood-evpn
- proxy-nd [no] host-unsolicited-na-flood-evpn
- proxy-nd [no] router-unsolicited-na-flood-evpn
- dup-detect [anti-spoof-mac <mac-address>] window <minutes> num-moves <count> hold-down <minutes|max>Enables a mechanism that detects duplicate IPs and ARP/ND spoofing attacks. The working of the dup-detect command can be summarized as follows:
- Attempts (relevant to dynamic and EVPN entry types) to add the same IP (different MAC) are monitored for <window> minutes and when <count> is reached within that window, the proxy-ARP/proxy-ND entry for the IP is suspected and marked as duplicate. An alarm is also triggered.
- The condition is cleared when hold-down time expires (max does not expire) or a clear command is issued.
- If the anti-spoof-mac is configured, the proxy-ARP/proxy-ND offending entry's MAC is replaced by this <mac-address> and advertised in an unsolicited GARP/NA for local SAP/SDP-bindings and in EVPN to remote PEs.
- This mechanism assumes that the same anti-spoof-mac is configured in all the PEs for the same service and that traffic with destination anti-spoof-mac received on SAPs/SDP-bindings will be dropped. An ingress MAC filter has to be configured in order to drop traffic to the anti-spoof-mac.
Table 82 shows the combinations that will produce a Status = Active proxy-arp entry in the table. The system will only reply to proxy-ARP requests for active entries. Any other combination will result in a Status = inActv entry. If the service is not active, the proxy-arp entries will not be active either, regardless of the FDB entries
| Note: A static entry is active in the FDB even when the service is down. |
Table 82: Proxy-arp Entry combinations
Proxy-arp Entry Type | FDB Entry Type (for the same MAC) |
Dynamic | learned |
Static | learned |
Dynamic | CStatic/Static |
Static | CStatic/Static |
EVPN | EVPN |
Duplicate | — |
When proxy-ARP/proxy-ND is enabled on services with all-active multi-homed ethernet-segments, a proxy-arp entry type 'EVPN' might be associated with a 'learned' FDB entry (because the CE can send traffic for the same MAC to all the multi-homed PEs in the ES). If that is the case, the entry will be inactive, as per Table 82.
5.28.1. Proxy-ARP/ND Periodic Refresh, Unsolicited Refresh and Confirm-Messages
When proxy-ARP/proxy-ND is enabled, the system starts populating the proxy table and responding to ARP-requests/NS messages. To keep the active IP->MAC entries alive and ensure that all the host/routers in the service update their ARP/ND caches, the system may generate the following three types of ARP/ND messages for a specified IP->MAC entry:
- Periodic refresh messages (ARP-requests or NS for a specified IP):These messages are activated by the send-refresh command and their objective is to keep the existing FDB and Proxy-ARP/ND entries alive, in order to minimize EVPN withdrawals and re-advertisements.
- Unsolicited refresh messages (unsolicited GARP or NA messages):These messages are sent by the system when a new entry is learned or updated. Their objective is to update the attached host/router caches.
- Confirm messages (unicast ARP-requests or unicast NS messages):These messages are sent by the system when a new MAC is learned for an existing IP. The objective of the confirm messages is to verify that a specified IP has really moved to a different part of the network and is associated with the new MAC. If the IP has not moved, it will force the owners of the duplicate IP to reply and cause dup-detect to kick in.
5.28.2. Proxy-ND and the Router Flag in Neighbor Advertisement messages
RFC 4861 describes the use of the (R) or "Router" flag in NA messages as follows:
- A node capable of routing IPv6 packets must reply to NS messages with NA messages where the R flag is set (R=1).
- Hosts must reply with NA messages where R=0.
The use of the "R" flag in NA messages impacts how the hosts select their default gateways when sending packets "off-link". Therefore, it is important that the proxy-ND function on the 7750 SR, 7450 ESS, or 7950 XRS must meet one of the following criteria:
- Either provide the appropriate R flag information in proxy-ND NA replies
- Flood the received NA messages if it cannot provide the appropriate R flag when replying
Due to the use of the "R" flag, the procedure for learning proxy-ND entries and replying to NS messages differs from the procedures for proxy-ARP in IPv4: the router or host flag will be added to each entry, and that will determine the flag to use when responding to a NS.
5.28.2.1. Procedure to Add the R Flag to a Specified Entry
The procedure to add the R flag to a specified entry is as follows:
- Dynamic entries are learned based on received NA messages. The R flag is also learned and added to the proxy-ND entry so that the appropriate R flag is used in response to NS requests for a specified IP.
- Static entries are configured as host or router as per the command [no] static <ip-address> <ieee-address> {host | router}.
- EVPN entries are learned from BGP and the command evpn-nd-advertise {host | router} determines the R flag added to them.
- In addition, the evpn-nd-advertise {host | router} command will indicate what static and dynamic IP->MAC entries the system will advertise in EVPN. If evpn-nd-advertise router is configured, the system should flood the received unsolicited NA messages for hosts. This is controlled by the [no] host-unsolicited-na-flood-evpn command. The opposite is also recommended so that the evpn-nd-advertise host is configured with the router-unsolicited-na-flood-evpn.
5.29. BGP-EVPN MAC-Mobility
EVPN defines a mechanism to allow the smooth mobility of MAC addresses from an NVE to another NVE. The 7750 SR, 7450 ESS, and 7950 XRS support this procedure as well as the MAC-mobility extended community in MAC advertisement routes as follows:
- The router honors and generates the SEQ (Sequence) number in the mac mobility extended community for mac moves.
- When a MAC is EVPN-learned and it is attempted to be learned locally, a BGP update is sent with SEQ number changed to "previous SEQ"+1 (exception: mac duplication num-moves value is reached).
- SEQ number = zero or no mac mobility ext-community are interpreted as sequence zero.
- In case of mobility, the following MAC selection procedure is followed:
- If a PE has two or more active remote EVPN routes for the same MAC (VNI can be the same or different), the highest SEQ number is selected. The tie-breaker is the lowest IP (BGP NH IP).
- If a PE has two or more active EVPN routes and it is the originator of one of them, the highest SEQ number is selected. The tie-breaker is the lowest IP (BGP NH IP of the remote route is compared to the local system address).
| Note: When EVPN multi-homing is used in EVPN-MPLS, the ESI is compared to determine whether a MAC received from two different PEs has to be processed within the context of MAC mobility or multi-homing. Two MAC routes that are associated with the same remote or local ESI but different PEs are considered reachable through all those PEs. Mobility procedures are not triggered as long as the MAC route still belongs to the same ESI. |
5.30. BGP-EVPN MAC-Duplication
EVPN defines a mechanism to protect the EVPN service from control plane churn as a result of loops or accidental duplicated MAC addresses. The 7750 SR, 7450 ESS, and 7950 XRS support an enhanced version of this procedure as described in this section.
A situation may arise where the same MAC address is learned by different PEs in the same VPLS because of two (or more hosts) being mis-configured with the same (duplicate) MAC address. In such situation, the traffic originating from these hosts would trigger continuous MAC moves among the PEs attached to these hosts. It is important to recognize such situation and avoid incrementing the sequence number (in the MAC Mobility attribute) to infinity.
To remedy such situation, a router that detects a MAC mobility event by way of local learning starts a window <in-minutes> timer (default value of window = 3) and if it detects num-moves <num> before the timer expires (default value of num-moves = 5), it concludes that a duplicate MAC situation has occurred. The router then alerts the operator with a trap message. The offending MAC address can be shown using the show service id x bgp-evpn command:
After detecting the duplicate, the router stops sending and processing any BGP MAC advertisement routes for that MAC address until one of the following occurs:
- The MAC is flushed due to a local event (sap/sdp-binding associated with the MAC fails) or the reception of a remote update with better SEQ number (due to a mac flush at the remote router).
- The retry <in-minutes> timer expires, which will flush the MAC and restart the process.
| Note: The other routers in the VPLS instance will forward the traffic for the duplicate MAC address to the router advertising the best route for the MAC. |
The values of num-moves and window are configurable to allow for the required flexibility in different environments. In scenarios where BGP rapid-update evpn is configured, the operator might want to configure a shorter window timer than in scenarios where BGP updates are sent every (default) min-route-advertisement interval.
Mac-duplication is always enabled in EVPN-VXLAN VPLS services, and the preceding described mac duplication parameters can be configured per VPLS service under the bgp-evpn mac-duplication context:
5.31. Conditional Static MAC and Protection
The draft-ietf-bess-evpn-overlay defines the use of the sticky bit in the mac-mobility extended community to signal static mac addresses. These addresses must be protected in case there is an attempt to dynamically learn them in a different place in the EVPN-VXLAN VPLS service.
In the 7750 SR, 7450 ESS, and 7950 XRS, any conditional static mac defined in an EVPN-VXLAN VPLS service will be advertised by BGP-EVPN as a static address, that is, with the sticky bit set. An example of the configuration of a conditional static mac is shown below:
Local static MACs or remote MACs with sticky bit are considered as 'protected'. A packet entering a SAP / SDP-binding will be discarded if its source MAC address matches one of these 'protected' MACs.
5.32. Auto-Learn MAC Protect and Restricting Protected Source MACs
Auto-learn MAC protect, together with the ability to restrict where the protected source MACs are allowed to enter the service, can be enabled within an EVPN-MPLS and EVPN-VXLAN VPLS and routed VPLS services, but not in PBB-EVPN services. The protection, using the auto-learn-mac-protect command (described in Auto-Learn MAC Protect), and the restrictions, using the restrict-protected-src [discard-frame] command, operate in the same way as in a non-EVPN VPLS service.
- When auto-learn-mac-protect is enabled on an object, source MAC addresses learned on that object are marked as protected within the FDB.
- When restrict-protected-src is enabled on an object and a protected source MAC is received on that object, the object is automatically shutdown (requiring the operator to shutdown then no shutdown the object in order to make it operational again).
- When restrict-protected-src discard-frame is enabled on an object and a frame with a protected source MAC is received on that object, that frame is discarded.
In addition, the following behavioral differences are specific to EVPN services:
- An implicit restrict-protected-src discard-frame command is enabled by default on SAPs, mesh-SDPs and spoke-SDPs. Note that as this is the default, it is not possible to configure this command in an EVPN service. This default state can be seen in the show output for these objects, for example on a SAP:*A:PE# show service id 1 sap 1/1/9:1 detail===============================================================================Service Access Points(SAP)===============================================================================Service Id : 1SAP : 1/1/9:1 Encap : q-tag...RestMacProtSrc Act : none (oper: Discard-frame)
- A restrict-protected-src discard-frame can be optionally enabled on EVPN-MPLS/VXLAN destinations within EVPN services. When enabled, frames that have a protected source MAC address are discarded if received on any EVPN-MPLS/VXLAN destination in this service, unless the MAC address is learned and protected on an EVPN-MPLS/VXLAN destination in this service. This is enabled as follows:configureservicevpls <service id>bgp-evpnmpls[no] restrict-protected-src discard-framevxlan vni <vni-id>[no] restrict-protected-src discard-frame
- Auto-learned protected MACs are advertised to remote PEs in an EVPN MAC/IP advertisement route with the sticky bit set.
- The source MAC protection action relating to the restrict-protected-src [discard-frame] commands also applies to MAC addresses learned by receiving an EVPN MAC/IP advertisement route with the sticky bit set from remote PEs. This causes remotely configured conditional static MACs and auto-learned protected MACs to be protected locally.
- In all-active multi-homing scenarios, if auto-learn-mac-protect is configured on all-active SAPs and restrict-protected-src discard-frame is enabled on EVPN-MPLS/VXLAN destinations, traffic from the CE that enters one multi-homing PE and needs to be switched through the other multi-homing PE will be discarded on the second multi-homing PE. Each multi-homing PE will protect the CE's MAC on its local all-active SAP, which results in any frames with the CE's MAC address as the source MAC being discarded as they are received on the EVPN-MPLS/VXLAN destination from the other multi-homing PE.
Conditional static MACs, EVPN static MACs and locally protected MACs are marked as protected within the FDB, as shown in the example output.
In this output:
- the first MAC is locally protected using the auto-learn-mac-protect command
- the second MAC has been protected using the auto-learn-mac-protect command on a remote PE
- the third MAC is a locally configured conditional static MAC
- the fourth MAC is a remotely configured conditional static MAC
5.33. Black-hole MAC and its Application to Proxy-ARP/Proxy-ND Duplicate Detection
A black-hole MAC is a local FDB record. It is similar to a conditional static MAC; it is associated with a “black-hole” (similar to a VPRN black-hole static-route in VPRNs) instead of a SAP or SDP-binding. A black-hole MAC can be added by using the following command:
The static black-hole MAC can have security applications (for example, replacement of MAC filters) for certain MACs. When used in combination with restrict-protected-src, the static black-hole MAC provides a simple and scalable way to filter MAC DA or SA in the data plane, regardless of how the frame arrived at the system (using SAP/SDP-bindings or EVPN endpoints).
For example, when a given static-mac mac 00:00:ca:fe:ca:fe create black-hole is added to a service, the following behavior occurs:
- The configured MAC is created as a static MAC with a black-hole source identifier.*A:PE1# show service id 1 fdb detail===============================================================================Forwarding Database, Service 1===============================================================================ServId MAC Source-Identifier Type Last ChangeAge-------------------------------------------------------------------------------1 00:ca:ca:ba:ca:01 eES: Evpn 06/29/15 23:21:3401:00:00:00:00:71:00:00:00:011 00:ca:ca:ba:ca:06 eES: Evpn 06/29/15 23:21:3401:74:13:00:74:13:00:00:74:131 00:ca:00:00:00:00 sap:1/1/1:2 CStatic:P 06/29/15 23:20:581 00:ca:fe:ca:fe:00 black-hole CStatic:P 06/29/15 23:20:001 00:ca:fe:ca:fe:69 eMpls: EvpnS:P 06/29/15 20:40:13192.0.2.69:262133-------------------------------------------------------------------------------No. of MAC Entries: 5-------------------------------------------------------------------------------Legend: L=Learned O=Oam P=Protected-MAC C=Conditional S=Static===============================================================================
- After it has been successfully added to the FDB, the black-hole MAC will be treated like any other protected MAC, as follows:
- The black-hole MAC will be added as protected (CStatic:P) and advertised in EVPN as static.
- SAP/SDP-bindings or EVPN endpoints where the restrict-protected-src discard-frame is enabled will discard frames where MAC SA is equal to black-hole MAC.
- SAP/SDP-bindings where restrict-protected-src (no discard-frame) is enabled will go oper-DOWN if a frame with MAC SA is equal to black-hole MAC is received.
- After the black-hole MAC has been successfully added to the FDB, any frame arriving at any SAP/SDP-binding or EVPN endpoint with MAC DA is equal to black-hole MAC will be discarded.
Black-hole MACs can also be used in services with proxy-ARP/proxy-ND enabled to filter traffic with destination to anti-spoof-macs. The anti-spoof-mac provides a way to attract traffic to a given IP when a duplicate condition is detected for that IP address (see section ARP/ND Snooping and Proxy Support for more information); however, the system still needs to drop the traffic addressed to the anti-spoof-mac by using either a MAC filter or a black-hole MAC.
The user does not need to configure MAC filters when configuring a static-black-hole MAC address for the anti-spoof-mac function. To use a black-hole MAC entry for the anti-spoof-mac function in a proxy-ARP/proxy-ND service, the user needs to configure:
- the static-black-hole option for the anti-spoof-mac*A:PE1# config>service>vpls>proxy-arp#dup-detect window 3 num-moves 5 hold-down max anti-spoof-mac 00:66:66:66:66:00 static-black-hole
- a static black-hole MAC using the same MAC address used for the anti-spoof-mac*A:PE1# config>service>vpls#static-mac mac 00:66:66:66:66:00 create black-hole
When this configuration is complete, the behavior of the anti-spoof-mac function changes as follows:
- In the EVPN, the MAC is advertised as Static. Locally, the MAC will be shown in the FDB as “CStatic” and associated with a black-hole.
- The combination of the anti-spoof-mac and the static-black-hole ensures that any frame that arrives at the system with MAC DA = anti-spoof-mac is discarded, regardless of the ingress endpoint type (SAP/SDP-binding or EVPN) and without the need for a filter.
- If, instead of discarding traffic, the user wants to redirect it using MAC DA as the anti-spoof-mac, then redirect filters should be configured on SAPs or SDP-bindings (instead of the static-black-hole option).
When the static-black-hole option is not configured with the anti-spoof-mac, the behavior of the anti-spoof-mac function, as described in ARP/ND Snooping and Proxy Support, remains unchanged. In particular:
- the anti-spoof-mac is not programmed in the FDB
- any attempt to add a Static MAC (or any other MAC) with the anti-spoof-mac value will be rejected by the system
- a MAC filter is needed to discard traffic with MAC DA = anti-spoof-mac.
5.34. CFM Interaction with EVPN Services
Ethernet Connectivity & Fault Management (ETH-CFM) allows the operator to validate and measure Ethernet layer 2 services using standard IEEE 802.1ag and ITU-T Y.1731 protocols. Each tool performs a unique function and adheres to that tool's specific PDU and frame format and the associate rules governing the transmission, interception, and process of the PDU. Detailed information describing the ETH-CFM architecture, the tools, and various functions is located in the various OAM & Diagnostics guides and is not repeated here.
EVPN provides powerful solution architectures. ETH-CFM is supported in the various layer 2 EVPN architectures. Since the destination layer 2 MAC address, unicast or multicast, is ETH-CFM tool dependent (i.e. ETH-CC is sent as a L2 multicast and ETH-DM is sent as an L2 unicast), the ETH-CFM function is allowed to multicast and broadcast to the virtual EVPN connections. The Maintenance Endpoint (MEP) and Maintenance Intermediate Point (MIP) do not populate the local layer 2 MAC Address forwarding database (FDB) with the MAC related to the MEP and MIP. This means that the 48-bit IEEE MAC address is not exchanged with peers and all ETH-CFM frames are broadcast across all virtual connections. To prevent the flooding of unicast packets and allow the remote forwarding databases to learn the remote MEP and MIP layer 2 MAC addresses, the command cfm-mac-advertisement must be configured under the config>service>vpls>bgp-evpn context. This allows the MEP and MIP layer 2 IEEE MAC addresses to be exchanged with peers. This command will track configuration changes and send the required updates via the EVPN notification process related to a change.
Up MEP, Down MEP, and MIP creation is supported on the SAP, spoke, and mesh connections within the EVPN service. There is no support for the creation of ETH-CFM Management Points (MPs) on the virtual connection. VirtualMEP (vMEP) is supported with a VPLS context and the applicable EVPN layer 2 VPLS solution architectures. The vMEP follows the same rules as the general MPs. When a vMEP is configured within the supported EVPN service, the ETH-CFM extraction routines are installed on the SAP, Binding, and EVPN connections within an EVPN VPLS Service. The vMEP extraction within the EVPN-PBB context requires the vmep-extensions parameter to install the extraction on the EVPN connections.
When MPs are used in combination with EVPN multi-homing, the following must be considered:
- Behavior of operationally DOWN MEPs on SAPs/SDP-bindings with EVPN multi-homing:
- All-active multi-homing: no ETH-CFM is expected to be used in this case, since the two (or more) SAPs/SDP-bindings on the PEs will be oper-up and active; however, the CE will have a single LAG and will respond as though it is connected to a single system. In addition to that, cfm-mac-advertisement can lead to traffic loops in all-active multi-homing.
- Single-active multi-homing: DOWN MEPs defined on single-active ethernet-segment SAPs/SDP-bindings will not send any CCMs when the PE is non-DF for the ES and fault-propagation is configured. For single-active multi-homing, the behavior will be equivalent to MEPs defined on BGP-MH saps/binds.
- Behavior for UP MEPs on ES SAPs/SDP-bindings with EVPN multi-homing:
- All-active multi-homing: UP MEPs defined on non-DF ES SAPs can send CFM packets. However, they cannot receive CCMs (the SAP is removed from the default multicast list) or unicast CFM packets (because the MEP MAC is not installed locally in the FDB; unicast CFM packets will be treated as unknown, and not sent to the non-DF SAP MEP).
- Single-active multi-homing: UP MEPs should be able to send or receive CFM packets normally.
- UP MEPs defined on LAG SAPs require the command process_cpm_traffic_on_sap_down so that they can process CFM when the LAG is down and act as regular Ethernet ports.
Due to the above considerations, the use of ETH-CFM in EVPN multi-homed SAPs/SDP-bindings is only recommended on operationally DOWN MEPs and single-active multi-homing. ETH-CFM is used in this case to notify the CE of the DF or non-DF status.
5.35. DC GW Policy Based Forwarding/Routing to an EVPN ESI (Ethernet Segment Identifier)
The Nuage VSP (Virtual Services Platform) supports a service chaining function that ensures traffic traverses a number of services (also known as Service Functions) between application hosts (FW, LB, NAT, IPS/IDS, and so on.) if the operator meeds to do so. In the DC, tenants want the ability to specify these functions and their sequence, so that services can be added or removed without requiring changes to the underlying application.
This service chaining function is built based on a series of policy based routing/forwarding redirecting rules that are automatically coordinated and abstracted by the Nuage VSD (Virtual Services Directory). From a networking perspective, the packets are 'hop-by-hop' redirected based on the location of the corresponding SF (Service Function) in the DC fabric. The location of the SF is specified by its VTEP and VNI and is advertised by BGP-EVPN along with an Ethernet Segment Identifier (ESI) that is uniquely associated with the SF.
Refer to the Nuage VSP documentation for more information about the Nuage Service Chaining solution.
The 7750 SR, 7450 ESS, or 7950 XRS can be integrated as the first hop in the chain in a Nuage DC. This service chaining integration is intended to be used as described in the following three use-cases.
5.35.1. Policy Based Forwarding in VPLS Services for Nuage Service Chaining Integration in L2-Domains
Figure 176 shows the 7750 SR, 7450 ESS, and 7950 XRS Service Chaining integration with the Nuage VSP on VPLS services. In this example, the DC GW, PE1, is connected to an L2-DOMAIN that exists in the DC and must redirect the traffic to the Service Function SF-1. The regular Layer-2 forwarding procedures would have taken the packets to PE2, as opposed to SF-1.
Figure 176: PBF to ESI Function
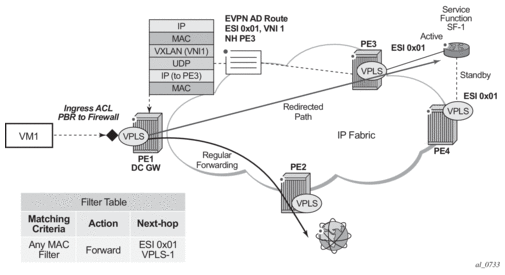
An operator must configure a PBF match/action filter policy entry in an IPv4 or MAC ingress access or network filter deployed on a VPLS interface using CLI/SNMP/NETCONF management interfaces. The PBF target is the first service function in the chain (SF-1) that is identified by an Ethernet Segment Identifier.
In the example shown in Figure 176, the PBF filter will redirect the matching packets to ESI 0x01 in VPLS-1.
| Note: Figure 176 represents ESI as ‘0x01’ for simplicity; in reality, the ESI is a 10-byte number. |
As soon as the redirection target is configured and associated with the vport connected to SF-1, the Nuage VSC (Virtual Services Controller, or the remote PE3 in the example) advertises the location of SF-1 via an Auto-Discovery Ethernet Tag route (route type 1) per-EVI. In this AD route, the ESI associated with SF-1 (ESI 0x01) is advertised along with the VTEP (PE3's IP) and VNI (VNI-1) identifying the vport where SF-1 is connected. PE1 will send all the frames matching the ingress filter to PE3's VTEP and VNI-1.
| Note: When packets get to PE3, VNI-1 (the VNI advertised in the AD route) will indicate that a 'cut-through' switching operation is needed to deliver the packets straight to the SF-1 vport, without the need for a regular MAC lookup. |
The following filter configuration shows an example of PBF rule redirecting all the frames to an ESI.
When the filter is properly applied to the VPLS service (VPLS-301 in this example), it will show 'Active' in the following show commands as long as the Auto-Discovery route for the ESI is received and imported.
Details of the received AD route that resolves the filter forwarding are shown in the following 'show router bgp routes' command.
This AD route, when used for PBF redirection, is added to the list of EVPN-VXLAN bindings for the VPLS service and shown as 'L2 PBR' type:
If the AD route is withdrawn, the binding will disappear and the filter will be inactive again. The user can control whether the matching packets are dropped or forwarded if the PBF target cannot be resolved by BGP.
5.35.2. Policy Based Routing in VPRN Services for Nuage Service Chaining Integration in L2-DOMAIN-IRB Domains
Figure 177 shows the 7750 SR, 7450 ESS, and 7950 XRS Service Chaining integration with the Nuage VSP on L2-DOMAIN-IRB domains. In this example, the DC GW, PE1, is connected to an L2-DOMAIN-IRB that exists in the DC and must redirect the traffic to the Service Function SF-1 with IP address 10.10.10.1. The regular layer-3 forwarding procedures would have taken the packets to PE2, as opposed to SF-1.
Figure 177: PBR to ESI Function
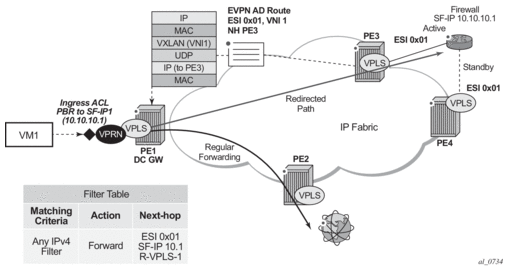
In this case, an operator must configure a PBR match/action filter policy entry in an IPv4 ingress access or network filter deployed on IES/VPRN interface using CLI/SNMP/NETCONF management interfaces. The PBR target identifies first service function in the chain (ESI 0x01 in Figure 177, identifying where the Service Function is connected and the IPv4 address of the SF) and EVPN VXLAN egress interface on the PE (VPRN routing instance and R-VPLS interface name). The BGP control plane together with ESI PBR configuration are used to forward the matching packets to the next-hop in the EVPN-VXLAN data center chain (through resolution to a VNI and VTEP). If the BGP control plane information is not available, the packets matching the ESI PBR entry will be, by default, forwarded using regular routing. Optionally, an operator can select to drop the packets when the ESI PBR target is not reachable.
The following filter configuration shows an example of a PBR rule redirecting all the matching packets to an ESI.
Note that in this use case, the following are required in addition to the ESI: the sf-ip (10.10.10.1 in the example above), router instance (300), and vas-interface.
The sf-ip is used by the system to know which inner MAC DA it has to use when sending the redirected packets to the SF. The SF-IP will be resolved to the SF MAC following regular ARP procedures in EVPN-VXLAN.
The router instance may be the same as the one where the ingress filter is configured or may be different: for instance, the ingress PBR filter can be applied on an IES interface pointing at a VPRN router instances that is connected to the DC fabric.
The vas-interface refers to the R-VPLS interface name through which the SF can be found. The VPRN instance may have more than one R-VPLS interface, therefore, it is required to specify which R-VPLS interface to use.
When the filter is properly applied to the VPRN or IES service (VPRN-300 in this example), it will show 'Active' in the following show commands as long as the Auto-Discovery route for the ESI is received and imported and the SF-IP resolved to a MAC address.
In the FDB for the R-VPLS 301, the MAC address is associated with the VTEP and VNI specified by the AD route, and not by the MAC/IP route anymore. When a PBR filter with a forward action to an ESI and SF-IP (Service Function IP) exists, a MAC route is auto-created by the system and this route has higher priority that the remote MAC/IP routes for the MAC (see section 'BGP and EVPN route selection for EVPN routes').
The following shows that the AD route creates a new EVPN-VXLAN binding and the MAC address associated with the SF-IP uses that 'binding':
As for the Layer-2 case, if the AD route is withdrawn or the SF-IP ARP not resolved, the filter will be inactive again. The user can control whether the matching packets are dropped or forwarded if the PBF target cannot be resolved by BGP.
5.36. IGMP Snooping in EVPN-MPLS Services
IGMP snooping is supported in EVPN-MPLS VPLS and I-VPLS services. It is required in scenarios where the operator does not want to flood all the IP multicast traffic to the access nodes or CEs, and only wants to deliver the IP multicast traffic for which IGMP reports have been received.
The following points apply when IGMP snooping is configured in EVPN-MPLS VPLS or I-VPLS services.
- IGMP snooping is enabled using the config>service>vpls>igmp-snooping no shutdown command.
- Queries and reports received on SAP/SDP bindings are snooped and properly handled; they are sent to SAP/SDP bindings as expected.
- Queries and reports on EVPN-MPLS are handled as follows.
- If received from SAP/SDP bindings, the queries and reports are sent to EVPN-MPLS, regardless of whether the service is using an ingress replication or mLDP provider tunnel.
- If received on EVPN-MPLS, the queries and reports are processed and propagated to access SAP/SDP bindings, regardless of whether the service is using an ingress replication or mLDP provider tunnel.
- EVPN-MPLS is treated as a single IGMP snooping interface and is always added as an mrouter.

Note: The preceding information is also applicable for I-VPLS services when bgp-evpn is running on the associated B-VPLS.
In the following show command output, the EVPN-MPLS destinations are shown as part of the MFIB (when igmp-snooping is in a no shutdown state), and the EVPN-MPLS logical interface is shown as an mrouter.
5.37. Configuring EVPN-VXLAN and EVPN-MPLS in the Same VPLS Service
When two BGP instances are added to a VPLS service, both BGP-EVPN MPLS and BGP-EVPN VXLAN can be configured at the same time in the service. A maximum of two BGP instances are supported in the same VPLS, such that BGP-EVPN MPLS can use BGP instance 1 or 2, and BGP-EVPN VXLAN can use BGP instance 1 only.
In a service where EVPN-VXLAN and EVPN-MPLS are configured together, the config>service>vpls>bgp-evpn>mpls>bgp-instance 2 command allows the user to associate the BGP-EVPN MPLS to an instance different from BGP-EVPN VXLAN, and have both encapsulations simultaneously enabled in the same service. At the control plane level, MAC/IP routes received in one instance are consumed and re-advertised in the other instance as long as the route is the best route for a specific MAC or MAC/IP. Inclusive multicast routes are independently generated for each BGP instance. From a data plane perspective, the EVPN-MPLS and EVPN-VXLAN destinations are instantiated in different implicit Split Horizon Groups (SHGs) so that traffic can be forwarded between them.
The following example shows a VPLS service with two BGP instances and both VXLAN and MPLS encapsulations configured for the same BGP-EVPN service.
The following list describe the preceding example:
- bgp 1 or bgp is the default BGP instance
- bgp 2 is the additional instance required when both bgp-evpn vxlan and bgp-evpn mpls are enabled in the service
- The commands supported in instance 1 are also available for the second instance with the following considerations.
- pw-template-binding: the pw-template-binding can only exist in instance 1; it is not supported in instance 2.
- route-distinguisher: the operating route-distinguisher in both bgp instances must be different
- route-target: the route-target in both instances can be the same or different
- vsi-import and vsi-export: import and export policies can also be defined for either bgp instance
- The mpls bgp-instance 2 command assigns the second BGP instance to the MPLS; VXLAN always uses instance 1.

Note: The bgp-evpn vxlan no shutdown command is only allowed if bgp-evpn shutdown is configured, or if the bgp-instance associated with the MPLS has a different route distinguisher than the VXLAN instance (and vice versa).
The following features are not supported when two BGP instances are enabled on the same VPLS service:
- SAPs or SDP-bindings
- R-VPLS, M-VPLS, I-VPLS, B-VPLS, or Etree VPLS
- Proxy-ARP and Proxy-ND
- BGP Multi-homing
5.37.1. BGP-EVPN Routes in Services Configured With Two BGP Instances
From a BGP perspective, the two BGP instances configured in the service are independent of each other. The redistribution of routes between the BGP instances is resolved at the EVPN application layer.
By default, if BGP-EVPN VXLAN and BGP-EVPN MPLS are both enabled in the same service, BGP will send the generated EVPN routes twice: once with the RFC 5512 BGP encapsulation extended community set to VXLAN and a second time with the encapsulation type set to MPLS.
Usually, a DC gateway will peer a pair of Route-Reflectors (RRs) in the DC and a pair of RRs in the WAN. For this reason, the user needs to add router policies so that EVPN-MPLS routes are only sent to the WAN RRs and EVPN-VXLAN routes are only sent to the DC RRs. The following examples show how you can configure router policies.
It is recommended to drop all EVPN routes exchanged between the DC gateways so that no EVPN binding is established between them.
In a BGP instance, the EVPN routes are imported based on the route-targets and regular BGP selection procedures, regardless of their encapsulation.
The BGP-EVPN routes are generated and redistributed between BGP instances based on the following rules.
- Auto-discovery (AD) routes (type 1) are not generated by services with two BGP instances. However, AD routes are received from the EVPN-MPLS peers and processed for aliasing and backup functions as usual.
- MAC/IP routes (type 2) received in one of the two BGP instances are imported and the MACs added to the FDB according to the existing selection rules. If the MAC is installed in the FDB, it is re-advertised in the other BGP instance with the new BGP attributes corresponding to the BGP instance (route-target, route-distinguisher, and so on). The following considerations apply to these routes.
- The mac-advertisement command governs the advertisement of any MACs (even those learned from BGP).
- A MAC route is redistributed only if it is the best route based on the EVPN selection rules.
- If a MAC route is the best route and has to be redistributed, the MAC/IP information, along with the MAC Mobility Extended Community, is propagated in the redistribution.
- The router redistributes any MAC route update for which any attribute has changed. For example, a change in the SEQ or sticky bit in one instance is updated in the other instance for a route that is selected as the best MAC route.
- EVPN inclusive multicast routes are generated independently for each BGP instance with the corresponding BGP encapsulation extended community (VXLAN or MPLS). Also, the following considerations apply to these routes.
- Ingress Replication (IR) and Assisted Replication (AR) routes are supported in the EVPN-VXLAN BGP instance. If AR is configured, the AR IP address must be a loopback address different from the system-ip and the configured originating-ip address.
- The IR, P2MP mLDP, and composite inclusive multicast routes are supported in the EVPN-MPLS BGP instance.
- The modification of the incl-mcast-orig-ip command is supported, subject to the following considerations.
- The configured IP in the incl-mcast-orig-ip command is encoded in the originating-ip field of the inclusive multicast Routes for IR, P2MP, and composite routes.
- The originating-ip field of the AR routes is still derived from the service>system>vxlan>assisted-replication-ip configured value.
- EVPN handles the inclusive multicast routes in a service based on the following rules.
- For IR routes, the EVPN destination is set up based on the NLRI next hop.
- For P2MP mLDP routes, the PMSI Tunnel Attribute tunnel-id is used to join the mLDP tree.
- For composite P2MP-IR routes, the PMSI Tunnel Attribute tunnel-id is used to join the tree and create the P2MP bind. The NLRI next-hop is used to build the IR destination.
- For AR routes, the NLRI next-hop is used to build the destination.
- The following applies if a router receives two inclusive multicast routes in the same instance.- If the routes have the same originating-ip but different route-distinguishers and next-hops, the router processes both routes. In the case of IR routes, it sets up two destinations: one to each next-hop.- If the routes have the same originating-ip, different route distinguishers, but same next hops, the router sets up only one binding for IR routes.- The router ignores inclusive multicast routes received with its own originating-ip, regardless of the route-distinguisher.
- Ethernet Segment routes (type 4) and IP-Prefix routes (type 5) are not generated or imported by a service with two BGP instances.
5.37.2. Anycast Redundant Solution for Dual BGP Instance Services
Figure 178 shows the Anycast mechanism used to support gateway redundancy for dual BGP instance services. The example shows two redundant DC gateways (DC GWs) where the VPLS services contain two BGP instances: one each for EVPN-VXLAN and EVPN-MPLS.
Figure 178: Multi-homed Anycast Solution
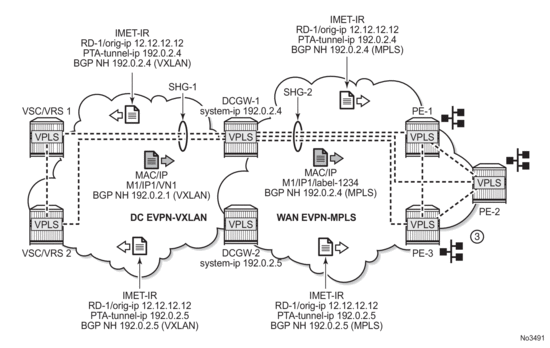
The example shown in Figure 178 depends on the ability of the two DC GWs to send the same inclusive multicast route to the remote PE or NVEs, such that:
- The remote PE or NVEs create a single BUM destination to one of the DC GWs (because the BGP selects only the best route to the DC GWs).
- The DC GWs do not create a destination between each other.
This solution avoids loops for BUM traffic, and known unicast traffic can use either DC GW router, depending on the BGP selection. The following CLI example output shows the configuration of each DC GW.
Based on the preceding configuration example, the DC GWs behavior in this scenario is as follows:
- DCGW-1 and DCGW-2 send inclusive multicast routes to the DC RR and WAN RR with the same route key. For example:
- DCGW-1 and DCGW-2 both send an IR route to DC RR with RD=64501:12, orig-ip=12.12.12.12, and a different next-hop and tunnel ID
- DCGW-1 and DCGW-2 both send an IR route to WAN RR with RD=64502:12, orig-ip=12.12.12.12, and different next-hop and tunnel ID
- DCGW-1 and DCGW-2 both receive MAC/IP routes from DC and WAN that will be redistributed to the other BGP instances, assuming that the route is selected as best route and the MAC is installed in the FDB
- As described in section 5.37.1, router peer policies are required so that only VXLAN or MPLS routes are sent or received for a specific peer
- Configuration of the same incl-mcast-orig-ip address in both DCGWs enables the Anycast solution for BUM traffic due to the following reasons.
- The configured originating-ip is not required to be a reachable IP address and this forces the remote PE/NVEs to select only one of the two DC GWs.
- The BGP next-hops are allowed to be the system-ip or even a loopback address. In both cases, the BGP next-hops are not required to be reachable in their respective networks.
In the example shown in Figure 178, PE-1 will pick up DC GW-1's inclusive multicast route (because of its lower BGP next-hop) and create a BUM destination to 192.0.2.4. When sending BUM traffic for VPLS-1, it will only send the traffic to DC GW-1. In the same way, the DC GWs will not set up BUM destinations between each other as they use the same originating-ip in their inclusive multicast routes.
The remote PE or NVEs perform a similar BGP selection for MAC or IP routes, as a specific MAC is sent by the two DC GWs with the same route-key. A PE or NVE will send known unicast traffic for a specific MAC to only one DC GW.
5.37.3. Using P2MP mLDP in Redundant Anycast DC GWs
Figure 179 shows an example of a common BGP EVPN service configured in redundant Anycast DC GWs and mLDP used in the MPLS instance.
| Note: Packet duplication may occur if the service configuration is not performed carefully. |
Figure 179: Anycast Multi-homing and mLDP
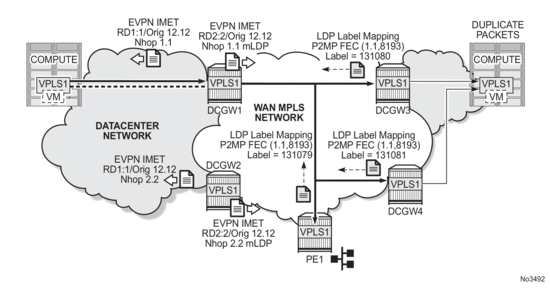
When mLDP is used with multiple Anycast multi-homing DC GWs, the same originating IP address must be used by all the DC GWs. Failure to do so may result in packet duplication.
In the example shown in Figure 179, each pair of DC GWs (DCGW1/DCGW2 and DCGW3/DCGW4) is configured with a different originating IP address, which causes the following behavior.
- DCGW3 and DCGW4 receive the inclusive multicast routes with the same route key from DCGW1 and DCGW2.
- Both DC GWs (DCGW3 and DCGW4) select only one route, which is generally the same, for example, DCGW1's inclusive multicast route.
- As a result, DCGW3 and DCGW4 join the mLDP tree with root in DCGW1, creating packet duplication when DCGW1 sends BUM traffic.
- Remote PE nodes with a single BGP-EVPN instance join the mLDP tree without any problem.
To avoid the packet duplication shown in Figure 179, it is recommended to configure the same originating IP address in all four DC GWs (DCGW1/DCGW2 and DCGW3/DCGW4). However, the route-distinguishers can be different per pair.
The following behavior occurs if the same originating IP address is configured on the DC GW pairs shown in Figure 179.
| Note: This configuration allows the use of mLDP as long as BUM traffic is not required between the two DCs. Ingress Replication must be used if BUM traffic between the DCs is required. |
- DCGW3 and DCGW4 do not join any mLDP tree sourced from DCGW1 or DCGW2, which prevents any packet duplication. This is because a router will ignore inclusive multicast routes received with its own originating-ip, regardless of the route-distinguisher.
- PE1 joins the mLDP trees from the two DCs.
5.38. BGP and EVPN Route Selection for EVPN Routes
When two or more EVPN routes are received at a PE, BGP route selection typically takes place when the route key or the routes are equal. When the route key is different, but the PE has to make a selection (for instance, the same MAC is advertised in two routes with different RDs), BGP will hand over the routes to EVPN and the EVPN application will perform the selection.
EVPN and BGP selection criteria are described below.
- EVPN route selection for MAC routes: when two or more routes with the same mac-length/mac but different route key are received, BGP will hand the routes over to EVPN. EVPN will select the route based on the following tie-break order:
- Conditional static MACs (local protected MACs)
- Auto-learned protected MACs (locally learned MACs on SAPs or mesh/spoke SDPs due to the configuration of auto-learn-mac-protect)
- EVPN ES PBR MACs (see ES PBR MAC routes below)
- EVPN static MACs (remote protected MACs)
- Data plane learned MACs (regular learning on saps/sdp-bindings)
- EVPN MACs with higher SEQ number
- Lowest IP (next-hop IP of the EVPN NLRI)
- Lowest eth-tag (that will be zero for MPLS and might be different from zero for VXLAN)
- Lowest RD
- ES PBR MAC routes: when a PBR filter with a forward action to an ESI and SF-IP (Service Function IP) exists, a MAC route is created by the system. This MAC route will be compared to other MAC routes received from BGP.
- When ARP resolves (it can be static, EVPN, or dynamic) for a SF-IP and the system has an AD EVI route for the ESI, a "MAC route" is created by ES PBR with the <MAC Address = ARPed MAC Address, VTEP = AD EVI VTEP, VNI = AD EVI VNI, RD = ES PBR RD (special RD), Static = 1> and installed in EVPN.
- This MAC route doesn't add anything (back) to ARP; however, it goes through the MAC route selection in EVPN and triggers the FDB addition if it is the best route.
- In terms of priority, this route's priority is lower than local static but higher than remote EVPN static (number 2 in the tie-break order above).
- If there are two competing ES PBR MAC routes, then the selection goes through the rest of checks (Lowest IP > Lowest RD).
- The BGP route selection for MAC routes with the same route-key follows the following priority order:
- EVPN static MACs (remote protected MACs).
- EVPN MACs with higher sequence number.
- Regular BGP selection (local-pref, aigp metric, shortest as-path, …, lowest IP).
- The BGP route selection for the rest of the EVPN routes: regular BGP selection is followed.
| Note: In case BGP has to run an actual selection and a given (otherwise valid) EVPN route 'loses' to another EVPN route, the non-selected route will be displayed by the show router BGP routes evpn x detail command with a 'tie-breaker' reason. |
| Note: Protected MACs do not overwrite EVPN static MACs; in other words, if a MAC is in the FDB and protected due to it being received with the sticky/static bit set in a BGP EVPN update and a frame is received with the source MAC on an object configured with auto-learn-mac-protect, that frame will be dropped due to the implicit restrict-protected-src discard-frame. The reverse is not true; once a MAC is learned and protected using auto-learn-mac-protect, its information is not overwritten with the contents of a BGP update containing the same MAC address. |
5.39. Interaction of EVPN-VXLAN and EVPN-MPLS with Existing VPLS Features
When enabling existing VPLS features in an EVPN-VXLAN or an EVPN-MPLS enabled service, the following must be considered:
- EVPN-VXLAN services are not supported on I-VPLS/B-VPLS. VXLAN cannot be enabled on those services. EVPN-MPLS is only supported in regular VPLS and B-VPLS. Other VPLS types, such as etree or m-vpls, are not supported with either EVPN-VXLAN or EVPN-MPLS.
- In general, no router-generated control packets will be sent to the EVPN destination bindings, except for ARP, VRRP, ping, BFD and Eth-CFM for EVPN-VXLAN, and proxy-ARP/proxy-ND confirm messages and Eth-CFM for EVPN-MPLS.
- xSTP and M-VPLS services:
- xSTP can be configured in bgp-evpn services. BPDUs will not be sent over the EVPN bindings.
- bgp-evpn is blocked in m-vpls services; however, a different m-vpls service can manage a SAP or spoke-sdp in a bgp-evpn enabled service.
- mac-move—in bgp-evpn enabled VPLS services, mac-move can be used in saps/sdp-bindings; however, the MACs being learned through BGP-EVPN will not be considered.

Note: The mac duplication already provides a protection against mac-moves between EVPN and saps/sdp-bindings.
- disable-learning and other fdb-related tools—these will only work for data plane learned mac addresses.
- mac-protect—mac-protect cannot be used in conjunction with EVPN.

Note: EVPN provides its own protection mechanism for static mac addresses.
- MAC OAM—MAC OAM tools are not supported for bgp-evpn services, that is: mac-ping, mac-trace, mac-populate, mac-purge, and cpe-ping.
- EVPN multi-homing and BGP-MH cannot be enabled in the same VPLS service. BGP-MH can still be used for multi-homing as long as no ethernet-segments are configured in the service SAPs/SDP-bindings. There is no limitation in terms of number of BGP-MH sites supported per EVPN-MPLS service.

Note: The number of BGP-MH sites per EVPN-VXLAN service is limited to 1.
- Note that SAPs/SDP-bindings that belong to a specified ES but are configured on non-bgp-evpn-mpls-enabled VPLS or Epipe services will be kept down with the StandByForMHProtocol flag.
- CPE-ping is not supported on EVPN services but it is in PBB-EVPN services (including I-VPLS and PBB-Epipe). CPE-ping packets will not be sent over EVPN destinations. CPE-ping will only work on local active SAP/SDP-bindings in I-VPLS and PBB-Epipe services.
- Other commands not supported in conjunction with bgp-evpn:
- bgp-vpls
- Endpoints and attributes
- Subscriber management commands under service, SAP, and sdp-binding interfaces
- MLD/PIM-snooping and attributes
- BPDU translation
- L2PT termination
- MAC-pinning
- Other commands not supported in conjunction with bgp-evpn mpls are:
- VSD-domains
- SPB configuration and attributes
5.40. Interaction of PBB-EVPN with Existing VPLS Features
In addition to the B-VPLS considerations described in section Interaction of EVPN-VXLAN and EVPN-MPLS with Existing VPLS Features, the following specific interactions for PBB-EVPN should also be considered.
- When bgp-evpn mpls is enabled in a b-vpls service, an i-vpls service linked to that b-vpls cannot be an R-VPLS (the allow-ip-int-bind command is not supported).
- The ISID value of 0 is not allowed for PBB-EVPN services (I-VPLS and Epipes).
- PBB-EVPN multi-homing and BGP-MH cannot be enabled in the same i-vpls service.
- The ethernet-segments can be associated with b-vpls SAPs/SDP-bindings and i-vpls/epipe SAPs/SDP-bindings,; however, the same ES cannot be associated with b-vpls and i-vpls/epipe SAP/SDP-bindings at the same time.
- When PBB-epipes are used with PBB-EVPN multi-homing, spoke-SDPs are not supported on ethernet-segments.
- When bgp-evpn mpls is enabled, eth-tunnels are not supported in the b-vpls instance.
5.41. Interaction of EVPN-VXLAN and EVPN-MPLS with Existing VPRN Features
When enabling existing VPRN features on interfaces linked to EVPN-VXLAN R-VPLS or EVPN-MPLS R-VPLS interfaces, consider that the following are not supported:
- the commands arp-populate and authentication-policy
- dynamic routing protocols such as IS-IS, RIP, and OSPF
- BFD on EVPN tunnel interfaces
5.42. Routing Policies for BGP EVPN IP Prefixes
BGP routing policies are supported for IP prefixes imported or exported through BGP-EVPN.
When applying routing policies to control the distribution of prefixes between EVPN and IP-VPN, the user must consider that both families are completely separate as far as BGP is concerned and that when prefixes are imported in the VPRN routing table, the BGP attributes are lost to the other family. The use of route tags allows the controlled distribution of prefixes across the two families.
Figure 180 shows an example of how VPN-IPv4 routes are imported into the RTM (Routing Table Manager), and then passed to EVPN for its own process.
| Note: VPN-IPv4 routes can be tagged at ingress and that tag is preserved throughout the RTM and EVPN processing, so that the tag can be matched at the egress BGP routing policy. |
Figure 180: IP-VPN Import and EVPN Export BGP Workflow
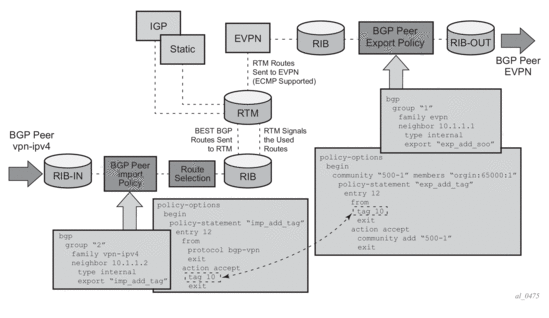
Policy tags can be used to match EVPN IP prefixes that were learned not only from BGP VPN-IPv4 but also from other routing protocols. The tag range supported for each protocol is different:
Figure 181 shows an example of the reverse workflow: routes imported from EVPN and exported from RTM to BGP VPN-IPv4.
Figure 181: IEVPN Import and I-VPN Export BGP Workflow
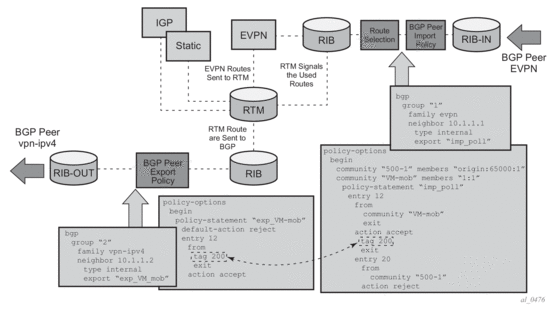
The preceding described behavior and the use of tags is also valid for vsi-import and vsi-export policies in the R-VPLS.
The policy behavior for EVPN ip-prefixes can then be summarized in the following statements.
- For EVPN prefix routes received and imported in RTM:
- Policy entries can match on communities and add tags. This works at the peer level or at the vsi-import level.
- Policy entries can match on family evpn.
- For exporting RTM to EVPN prefix routes:
- Policy entries can match on tags and based on that, add communities, accept, or reject. This works at the peer level or the vsi-export level.
Policy entries can add tags for static-routes, RIP, OSPF, IS-IS, and BGP that can then be matched on the BGP peer export policy or vsi-export policy for EVPN prefix routes.
5.43. MPLS Entropy Label and Hash Label
The router supports the MPLS entropy label (RFC 6790) and the Flow Aware Transport label (known as the hash label) (RFC 6391). These labels allow LSR nodes in a network to load-balance labeled packets in a much more granular fashion than allowed by simply hashing on the standard label stack. The entropy label can be enabled on bgp-evpn services (VPLS and Epipe). See the MPLS Guide for further information.