Configuring IS-IS with CLI
This section provides information to configure intermediate-system-to-intermediate-system (IS-IS) using the command line interface.
Topics in this section include:
IS-IS Configuration Overview
Router Levels
The router’s level capability can be configured globally and on a per-interface basis. The interface-level parameters specify the interface’s routing level. The neighbor capability and parameters define the adjacencies that are established.
IS-IS is not enabled by default. When IS-IS is enabled, the global default level capability is Level 1/2 which enables the router to operate as either a Level 1 and/or a Level 2 router with the associated databases. The router runs separate shortest path first (SPF) calculations for the Level 1 area routing and for the Level 2 multi-area routing to create the IS-IS routing table.
The level value can be modified on both or either of the global and interface levels to be only Level 1-capable, only Level 2-capable or Level 1 and Level 2-capable.
If the default value is not modified on any routers in the area, then the routers try to form both Level 1 and Level 2 adjacencies on all IS-IS interfaces. If the default values are modified to Level 1 or Level 2, then the number of adjacencies formed are limited to that level only.
Area Address Attributes
The area-id command specifies the area address portion of the NET which is used to define the IS-IS area to which the router will belong. At least one area-id command should be configured on each router participating in IS-IS. A maximum of three area-id commands can be configured per router.
The area address identifies a point of connection to the network, such as a router interface, and is called a network service access point (NSAP). The routers in an area manage routing tables about destinations within the area. The Network Entity Title (NET) value is used to identify the IS-IS area to which the router belongs.
NSAP addresses are divided into three parts. Only the Area ID portion is configurable.
- Area ID — A variable length field between 1 and 13 bytes long. This includes the Authority and Format Identifier (AFI) as the most significant byte and the area ID.
- System ID — A six-byte system identification. This value is not configurable. The system ID is derived from the system or router ID.
- Selector ID — A one-byte selector identification that must contain zeros when configuring a NET. This value is not configurable. The selector ID is always 00.
The following example displays ISO addresses in IS-IS address format:
MAC address 00:a5:c7:6b:c4:90 49.0011.00a5.c76b.c490.00 IP address: 218.112.14.5 49.0011.2181.1201.4005.00
Interface Level Capability
The level capability value configured on the interface level is compared to the level capability value configured on the global level to determine the type of adjacencies that can be established. The default level capability for routers and interfaces is Level 1/2.
Table 30 displays configuration combinations and the potential adjacencies that can be formed.
Table 30: Potential Adjacency
Global Level | Interface Level | Potential Adjacency |
L 1/2 | L 1/2 | Level 1 and/or Level 2 |
L 1/2 | L 1 | Level 1 only |
L 1/2 | L 2 | Level 2 only |
L 2 | L 1/2 | Level 2 only |
L 2 | L 2 | Level 2 only |
L 2 | L 1 | none |
L 1 | L 1/2 | Level 1 only |
L 1 | L 2 | none |
L 1 | L 1 | Level 1 only |
Route Leaking
Nokia’s implementation of IS-IS route leaking is performed in compliance with RFC 2966, Domain-wide Prefix Distribution with Two-Level IS-IS. As previously stated, IS-IS is a routing domain (an autonomous system running IS-IS) which can be divided into Level 1 areas with a Level 2-connected subset (backbone) of the topology that interconnects all of the Level 1 areas. Within each Level 1 area, the routers exchange link state information. Level 2 routers also exchange Level 2 link state information to compute routes between areas.
Routers in a Level 1 area typically only exchange information within the Level 1 area. For IP destinations not found in the prefixes in the Level 1 database, the Level 1 router forwards PDUs to the nearest router that is in both Level 1/Level 2 with the attached bit set in its Level 1 link-state PDU.
There are many reasons to implement domain-wide prefix distribution. The goal of domain-wide prefix distribution is to increase the granularity of the routing information within the domain. The routing mechanisms specified in RFC 1195 are appropriate in many situations and account for excellent scalability properties. However, in certain circumstances, the amount of scalability can be adjusted which can distribute more specific information than described by RFC 1195.
Distributing more prefix information can improve the quality of the resulting routes. A well known property of default routing is that loss of information can occur. This loss of information affects the computation of a route based upon less information which can result in sub-optimal routes.
Basic IS-IS Configuration
For IS-IS to operate on the routers, IS-IS must be explicitly enabled, and at least one area address and interface must be configured. If IS-IS is enabled but no area address or interface is defined, the protocol is enabled but no routes are exchanged. When at least one area address and interface are configured, then adjacencies can be formed and routes exchanged.
To configure IS-IS, perform the following tasks:
- Enable IS-IS (specifying the instance ID of multi-instance IS-IS is to be enabled).
- If necessary, modify the level capability on the global level (default is level-1/2).
- Define area addresses
- Configure IS-IS interfaces.
The following output displays IS-IS default values.
Common Configuration Tasks
To implement IS-IS in your network, you must enable IS-IS on each participating router.
To assign different level to the routers and organize your network into areas, modify the level capability defaults on end systems from Level 1/2 to Level 1. Routers communicating to other areas can retain the Level 1/2 default.
On each router, at least one area ID also called the area address should be configured as well as at least one IS-IS interface.
- Enable IS-IS.
- Configure global IS-IS parameters.
- Configure area addresses.
- Configure IS-IS interface-specific parameters.
Configuring IS-IS Components
Use the CLI syntax displayed below for:
Enabling IS-IS
IS-IS must be enabled in order for the protocol to be active.
| Caution: Careful planning is essential to implement commands that can affect the behavior of global and interface levels. |
To configure IS-IS on a router, enter the following command:
IS-IS also supports the concept of multi-instance IS-IS which allows separate instances of the IS-IS protocol to run independently of the SR-OS router.
Separate instances are created by adding a different instance ID as the optional parameter to the config>router>isis command.
Modifying Router-Level Parameters
When IS-IS is enabled, the default level-capability is Level 1/2. This means that the router operates with both Level 1 and Level 2 routing. To change the default value in order for the router to operate as a Level 1 router or a Level 2 router, you must explicitly modify the level value.
If the level is modified, the protocol shuts down and restarts. Doing this can affect adjacencies and routes.
The level-capability value can be configured on the global level and also on the interface level. The level-capability value determines which level values can be assigned on the router level or on an interface-basis.
In order for the router to operate as a Level 1 only router or as a Level 2 only router, you must explicitly specify the level-number value.
- Select level-1 to route only within an area.
- Select level-2 to route to destinations outside an area, toward other eligible Level 2 routers.
To configure the router level, enter the following commands:
The following example displays the configuration:
Configuring ISO Area Addresses
Use the following CLI syntax to configure an area ID also called an address. A maximum of 3 area-id can be configured.
The following example configures the router’s area ID:
The following example displays the area ID configuration:
Configuring Global IS-IS Parameters
Commands and parameters configured on the global level are inherited to the interface levels. Parameters specified in the interface and interface-level configurations take precedence over global configurations.
The following example displays global-level IS-IS configuration command usage:
The following example displays the modified global-level configuration.
Migration to IS-IS Multi-Topology
To migrate to IS-IS multi-topology for IPv6, perform the following tasks:
Enable the sending/receiving of IPv6 unicast reachability information in IS-IS MT TLVs on all the routers that support MT.
Ensure that all MT routers have the IPv6 reachability information required by MT TLVs:
Configure MT TLVs for IPv6 SPF:
Verify IPv6 routes:
Configuring Interface Parameters
There are no interfaces associated with IS-IS by default. An interface belongs to all areas configured on a router. Interfaces cannot belong to separate areas. There are no default interfaces applied to the router’s IS-IS instance. You must configure at least one IS-IS interface in order for IS-IS to work.
To enable IS-IS on an interface, first configure an IP interface in the config>router> interface context. Then, apply the interface in the config>router>isis>interface context.
You can configure both the Level 1 parameters and the Level 2 parameters on an interface. The level-capability value determines which level values are used.
| Note: For point-to-point interfaces, only the values configured under Level 1 are used regardless of the operational level of the interface. |
The following example displays the modified interface parameters:
The following example displays the global and interface-level configurations.
Example: Configuring a Level 1 Area
Interfaces are configured in the config>router>interface context.
Figure 23: Configuring a Level 1 Area
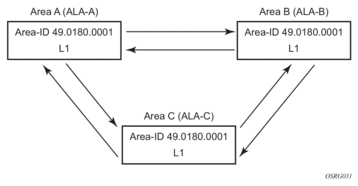
The following example displays the command usage to configure a Level 1 area.
Example: Modifying a Router’s Level Capability
In the previous example, ALA-A, ALA-B, and ALA-C are configured as Level 1 systems. Level 1 systems communicate with other Level 1 systems in the same area. In this example, ALA-A is modified to set the level capability to Level 1/2. Now, the Level 1 systems in the area with NET 47.0001 forward PDUs to ALA-A for destinations that are not in the local area.
Figure 24: Configuring a Level 1/2 Area
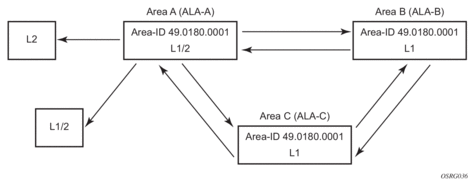
The following example displays the command usage to configure a Level 1/2 system.
Configuring IS-IS Link Groups
IS-IS Link-Groups allows the creation of an administrative grouping of multiple IS-IS member interfaces that should be treated as a common group for ECMP purposes. If the number of operational links in the link-group drops below the operational-member value then all links associated with that IS-IS link group will have their interface metric increased by the configured offset amounts. As a result, IS-IS will then try to reroute traffic over lower cost paths.
Once triggered, the higher metric will not be reset to the originally configured IS-IS interface metric values until the number of active interfaces in the link bundle reaches the configured revertive threshold (revert-members).
Prerequisite are the following:
- 1 or more interface members.
- A configured operational-member (oper-members) value.
- A configured revertive-member (revert-members) value.
- Configured offset values for the appropriate address families.
IS-IS Configuration Management Tasks
This section discusses the following IS-IS configuration management tasks:
Disabling IS-IS
The shutdown command disables the IS-IS protocol instance on the router. The configuration settings are not changed, reset, or removed.
To disable IS-IS on a router, enter the following commands:
Removing IS-IS
The no isis command deletes the IS-IS protocol instance. The IS-IS configuration reverts to the default settings.
To remove the IS-IS configuration enter the following commands:
Modifying Global IS-IS Parameters
You can modify, disable, or remove global IS-IS parameters without shutting down entities. Changes take effect immediately. Modifying the level capability on the global level causes the IS-IS protocol to restart.
The following example displays command usage to modify various parameters:
The following example displays the global modifications
Modifying IS-IS Interface Parameters
You can modify, disable, or remove interface-level IS-IS parameters without shutting down entities. Changes take effect immediately. Modifying the level capability on the interface causes the IS-IS protocol on the interface to restart.
To remove an interface, issue the no interface ip-int-name command. To disable an interface, issue the shutdown command in the interface context.
The following example displays interface IS-IS modification command usage. For specific interface configuration and modification examples also see, Example: Configuring a Level 1 Area and Example: Modifying a Router’s Level Capability.
The following example displays the modified interface parameters.
Configuring Authentication using Keychains
The use of authentication mechanism is recommended to protect against malicious attack on the communications between routing protocol neighbors. These attacks could aim to either disrupt communications or to inject incorrect routing information into the systems routing table. The use of authentication keys can help to protect the routing protocols from these types of attacks. In addition, the use of authentication keychains provides the ability to configure authentication keys and make changes to them without affecting the state of the routing protocol adjacencies.
To configure the use of an authentication keychain within IS-IS, use the following steps:
- Configure an authentication keychain within the config>system>security context. The configured keychain must include at least on valid key entry, using a valid authentication algorithm for the IS-IS protocol.
- Associate the configure authentication keychain with IS-IS. Authentication keychains can be used to specify the authentication at the IS-IS global, and level context as well as for hello authentication at the interface and interface-level context.
The association of the authentication keychain is established through the auth-keychain keychain-name command at the global and level context. The hello authentication association is established through the hello-auth-keychain keychain-name command.
For a key entry to be valid, it must include a valid key, the current system clock value must be within the begin and end time of the key entry, and the algorithm specified in the key entry must be supported by the IS-IS protocol.
The IS-IS protocol supports the following algorithms:
- Clear text password (RFC 5304 and RFC 5310 formats)
- HMAC-MD5 (RFC 5304 and RFC 5310 formats)
- HMAC-SHA-1 (RFC 5310 format)
- HMAC-SHA-256 (RFC 5310 format)
The IS-IS key entry may also include the option parameter to determine how the IS-IS protocol encodes the authentication signature. The value of basic results in the use of RFC 5304 format. The default or a value of isis-enhanced results in using the RFC 5310 format.
Error handling:
- If a keychain exists but there are no active key entries with an authentication type that is valid for the associated protocol then inbound protocol packets will not be authenticated and discarded and no outbound protocol packets should be sent.
- If keychain exists, but the last key entry has expired, a log entry will be raised indicating that all keychain entries have expired. The IS-IS protocol requires that the protocol not revert to an unauthenticated state and requires that the old key is not to be used, therefore, once the last key has expired, all traffic will be discarded.
Configuring Leaking
IS-IS allows a two-level hierarchy to route PDUs. Level 1 areas can be interconnected by a contiguous Level 2 backbone. The Level 1 link-state database contains information only about that area. The Level 2 link-state database contains information about the Level 2 system and each of the Level 1 systems in the area. A Level 1/2 router contains information about both Level 1 and Level 2 databases. A Level 1/2 router advertises information about its Level 1 area toward the other Level 1/2 or Level 2 (only) routers.
Packets with destinations outside the Level 1 area are forwarded toward the closest Level 1/2 router which, in turn, forwards the packets to the destination area.
Sometimes, the shortest path to an outside destination is not through the closest Level 1/2 router, or, the only Level 1/2 system to forward packets out of an area is not operational. Route leaking provides a mechanism to leak Level 2 information to Level 1 systems to provide routing information regarding inter-area routes. Then, a Level 1 router has more options to forward packets.
Configure a route policy to leak routers from Level 2 into Level 1 areas in the config>router>policy-options>policy-statement context.
The following example shows the command usage to configure prefix list and policy statement parameters in the config>router context.
Next, apply the policy to leak routes from Level 2 info Level 1 systems on ALA-A.
After the policy is applied, create a policy to redistribute external IS-IS routes from Level 1 systems into the Level 2 backbone (see Redistributing External IS-IS Routers). In the config>router context, configure the following policy statement parameters:
Redistributing External IS-IS Routers
IS-IS does not redistribute Level 1 external routes into Level 2 by default. You must explicitly apply the policy to redistribute external IS-IS routes. Policies are created in the config>router>policy-options context. See 6 for more information.
The following example displays the policy statement configuration.
Specifying MAC Addresses for All IS-IS Routers
Specify the MAC address to use for all L1 or L2 IS-IS routers. The following example shows how to specify all L1 routers:
You can also specify the MAC address for all L2 IS-IS routers by using the all-l2isis command.