4. IS-IS
4.1. Configuring IS-IS
Intermediate-system-to-intermediate-system (IS-IS) is a link-state interior gateway protocol (IGP) which uses the Shortest Path First (SPF) algorithm to determine routes. Routing decisions are made using the link-state information. IS-IS evaluates topology changes and, if necessary, performs SPF recalculations.
Entities within IS-IS include networks, intermediate systems, and end systems. In IS-IS, a network is an autonomous system (AS), or routing domain, with end systems and intermediate systems. A router is an intermediate system. End systems are network devices which send and receive protocol data units (PDUs), the OSI term for packets. Intermediate systems send, receive, and forward PDUs.
End system and intermediate system protocols allow routers and nodes to identify each other. IS-IS sends out link-state updates periodically throughout the network, so each router can maintain current network topology information.
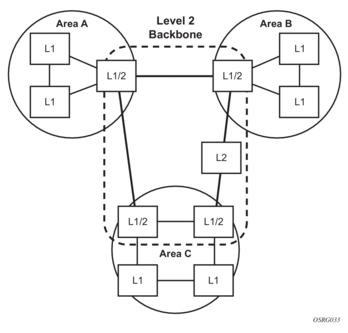
IS-IS supports large ASs by using a two-level hierarchy. A large AS can be administratively divided into smaller, more manageable areas. A system logically belongs to one area. Level 1 routing is performed within an area. Level 2 routing is performed between areas. The routers can be configured as Level 1, Level 2, or both Level 1/2.
Figure 14 displays an example of an IS-IS routing domain.
Figure 14: IS-IS Routing Domain
4.1.1. Routing
OSI IS-IS routing uses two-level hierarchical routing. A routing domain can be partitioned into areas. Level 1 routers know the topology in their area, including all routers and end systems in their area but do not know the identity of routers or destinations outside of their area. Level 1 routers forward traffic with destinations outside of their area to a Level 2 router in their area.
Level 2 routers know the Level 2 topology, and know which addresses are reachable by each Level 2 router. Level 2 routers do not need to know the topology within any Level 1 area, except to the extent that a Level 2 router can also be a Level 1 router within a single area. By default, only Level 2 routers can exchange PDUs or routing information directly with external routers located outside the routing domain.
In IS-IS, there are two types of routers:
- Level 1 intermediate systems — Routing is performed based on the area ID portion of the ISO address called the network entity title (NET). Level 1 systems route within an area. They recognize, based on the destination address, whether the destination is within the area. If so, they route toward the destination. If not, they route to the nearest Level 2 router.
- Level 2 intermediate systems — Routing is performed based on the area address. They route toward other areas, disregarding other area’s internal structure. A Level 2 intermediate system can also be configured as a Level 1 intermediate system in the same area.
Within an area, Level 1 routers exchange LSPs which identify the IP addresses reachable by each router. Specifically, zero or more IP address, subnet mask, and metric combinations can be included in each LSP. Each Level 1 router is manually configured with the IP address, subnet mask, and metric combinations, which are reachable on each interface. A Level 1 router routes as follows:
- If a specified destination address matches an IP address, subnet mask, or metric reachable within the area, the PDU is routed via Level 1 routing.
- If a specified destination address does not match any IP address, subnet mask, or metric combinations listed as reachable within the area, the PDU is routed towards the nearest Level 2 router.
Level 2 routers include in their LSPs, a complete list of IP address, subnet mask, and metrics specifying all the IP addresses which reachable in their area. This information can be obtained from a combination of the Level 1 LSPs (by Level 1 routers in the same area). Level 2 routers can also report external reachability information, corresponding to addresses reachable by routers in other routing domains or autonomous systems.
4.1.2. IS-IS Frequently Used Terms
- Area — An area is a routing sub-domain which maintains detailed routing information about its own internal composition, and also maintains routing information which allows it to reach other routing sub-domains. Areas correspond to the Level 1 sub-domain.
- End system — End systems send NPDUs to other systems and receive NPDUs from other systems, but do not relay NPDUs. This International Standard does not specify any additional end system functions beyond those supplied by ISO 8473 and ISO 9542.
- Neighbor — A neighbor is an adjacent system reachable by traversing a single sub-network by a PDU.
- Adjacency — An adjacency is a portion of the local routing information which pertains to the reachability of a single neighboring end or intermediate system over a single circuit. Adjacencies are used as input to the decision process to form paths through the routing domain. A separate adjacency is created for each neighbor on a circuit and for each level of routing (Level 1 and Level 2) on a broadcast circuit.
- Circuit — The subset of the local routing information base pertinent to a single local Subnetwork Point of Attachments (SNPAs).
- Link — The communication path between two neighbors. A link is up when communication is possible between the two SNPAs.
- Designated IS — The intermediate system on a LAN which is designated to perform additional duties. In particular, the designated IS generates link-state PDUs on behalf of the LAN, treating the LAN as a pseudonode.
- Pseudonode — Where a broadcast sub-network has n connected intermediate systems, the broadcast sub-network itself is considered to be a pseudonode. The pseudonode has links to each of the n intermediate systems and each of the ISs has a single link to the pseudonode (rather than n-1 links to each of the other intermediate systems). Link-state PDUs are generated on behalf of the pseudonode by the designated IS.
- Broadcast sub-network — A multi-access subnetwork that supports the capability of addressing a group of attached systems with a single PDU.
- General topology sub-network — A topology that is modeled as a set of point-to-point links, each of which connects two systems. There are several generic types of general topology subnetworks, multipoint links, permanent point-to-point links, dynamic and static point-to-point links.
- Routing sub-domain — A routing sub-domain consists of a set of intermediate systems and end systems located within the same routing domain.
- Level 2 sub-domain — Level 2 sub-domain is the set of all Level 2 intermediate systems in a routing domain.
4.1.3. ISO Network Addressing
IS-IS uses ISO network addresses. Each address identifies a point of connection to the network, such as a router interface, and is called a Network Service Access Point (NSAP).
An end system can have multiple NSAP addresses, in which case the addresses differ only by the last byte (called the n-selector). Each NSAP represents a service that is available at that node. In addition to having multiple services, a single node can belong to multiple areas.
Each network entity has a special network address called a Network Entity Title (NET). Structurally, a NET is identical to an NSAP address but has an n-selector of 00. Most end systems have one NET. Intermediate systems can have up to three area IDs (area addresses).
NSAP addresses are divided into three parts. Only the area ID portion is configurable.
- Area ID — A variable length field between 1 and 13 bytes long. This includes the Authority and Format Identifier (AFI) as the most significant byte and the area ID.
- System ID — A six-byte system identification. This value is not configurable. The system ID is derived from the system or router ID.
- Selector ID — A one-byte selector identification that must contain zeros when configuring a NET. This value is not configurable. The selector ID is always 00.
Of the total 20 bytes comprising the NET, only the first 13 bytes, the area ID portion, can be manually configured. As few as one byte can be entered or, at most, 13 bytes. If less than 13 bytes are entered, the rest is padded with zeros.
Routers with common area addresses form Level 1 adjacencies. Routers with no common NET addresses form Level 2 adjacencies, if they are capable (Figure 15).
Figure 15: Using Area Addresses to Form Adjacencies

4.1.3.1. IS-IS PDU Configuration
The following PDUs are used by IS-IS to exchange protocol information:
- IS-IS hello PDU — Routers with IS-IS enabled send hello PDUs to IS-IS-enabled interfaces to discover neighbors and establish adjacencies.
- Link-state PDUs — Contain information about the state of adjacencies to neighboring IS-IS systems. LSPs are flooded periodically throughout an area.
- Complete sequence number PDUs — In order for all routers to maintain the same information, CSNPs inform other routers that some LSPs can be outdated or missing from their database. CSNPs contain a complete list of all LSPs in the current IS-IS database.
- Partial sequence number PDUs (PSNPs) — PSNPs are used to request missing LSPs and acknowledge that an LSP was received.
4.1.3.2. IS-IS Operations
The routers perform IS-IS routing as follows:
- Hello PDUs are sent to the IS-IS-enabled interfaces to discover neighbors and establish adjacencies.
- IS-IS neighbor relationships are formed if the hello PDUs contain information that meets the criteria for forming an adjacency.
- The routers can build a link-state PDU based upon their local interfaces that are configured for IS-IS and prefixes learned from other adjacent routers.
- The routers flood LSPs to the adjacent neighbors except the neighbor from which they received the same LSP. The link-state database is constructed from these LSPs.
- A Shortest Path Tree (SPT) is calculated by each IS, and from this SPT the routing table is built.
4.1.4. IS-IS Route Summarization
IS-IS IPv4 route summarization allows users to create aggregate IPv4 addresses that include multiple groups of IPv4 addresses for a given IS-IS level. IPv4 Routes redistributed from other routing protocols also can be summarized. It is similar to the OSPF area-range command. IS-IS IPv4 route summarization helps to reduce the size of the LSDB and the IPv4 routing table, and it also helps to reduce the chance of route flapping.
IPv4 route summarization supports:
- Level 1, Level 1-2, and Level 2
- Route summarization for the IPv4 routes redistributed from other protocols
4.1.4.1. Partial SPF Calculation
4.1.5. IS-IS MT-Topology Support
Multi-Topology IS-IS (MT-ISIS) support within SR OS allows for the creation of different topologies within IS-IS that contribute routes to specific route tables for IPv4 unicast, IPv6 unicast, IPv4 multicast, and IPv6 multicast. This capability allows for non-congruent topologies between these different routing tables. As a result, networks are able to control which links or nodes are to be used for forwarding different types of traffic.
For example, MT-ISIS could allow all links to carry IPv4 traffic, while only a subset of links can also carry IPv6 traffic.
SR OS supports the following Multi-Topologies:
- IPv4 Unicast – MT-ID 0
- IPv6 Unicast – MT-ID 2
- IPv4 Multicast – MT-ID 3
- IPv6 Multicast – MT-ID 4
4.1.5.1. Native IPv6 Support
IS-IS IPv6 TLVs for IPV6 routing is supported in SR OS. This support is considered native IPv6 routing within IS-IS. However, it has limitations in that IPv4 and IPv6 topologies must be congruent, otherwise traffic may be blackholed. Service providers should ensure that the IPv4 topology and IPv6 topologies are the same if native IPv6 routing is used within IS-IS.
4.1.6. IS-IS Administrative Tags
IS-IS admin tags enable a network administrator to configure route tags to tag IS-IS route prefixes. These tags can subsequently be used to control Intermediate System-to-Intermediate System (IS-IS) route redistribution or route leaking.
The IS-IS support for route tags allows the tagging of IP addresses of an interface and use the tag to apply administrative policy with a route map. A network administrator can also tag a summary route and then use a route policy to match the tag and set one or more attributes for the route.
Using these administrative policies allow the operator to control how a router handles the routes it receives from and sends to its IS-IS neighboring routers. Administrative policies are also used to govern the installation of routes in the routing table.
Route tags allow:
- Policies to redistribute routes received from other protocols in the routing table to IS-IS.
- Policies to redistribute routes between levels in an IS-IS routing hierarchy.
- Policies to summarize routes redistributed into IS-IS or within IS-IS by creating aggregate (summary) addresses.
4.1.6.1. Setting Route Tags
IS-IS route tags are configurable in the following ways:
- Setting a route tag for an IS-IS interface.
- Setting a route tag on an IS-IS passive interface.
- Setting a route tag for a route redistributed from another protocol to IS-IS.
- Setting a route tag for a route redistributed from one IS-IS level to another IS-IS level.
- Setting a route tag for an IS-IS default route.
- Setting a route tag for an IS-IS summary address.
4.1.6.2. Using Route Tags
Although an operator on this or on a neighboring IS-IS router has configured setting of the IS-IS administrative tags, it will not have any effect unless policies are configure to instruct how to process the given tag value.
Policies can process tags where IS-IS is either the origin, destination or both origin and destination protocol.
4.1.6.3. Unnumbered Interface Support
IS-IS supports unnumbered point-to-point interface with both Ethernet and PPP encapsulations.
Unnumbered interfaces borrow the address from other interfaces such as system or loopback interfaces and uses it as the source IP address for packets originated from the interface. This feature supports both dynamic and static ARP for unnumbered interfaces to allow interworking with unnumbered interfaces that may not support dynamic ARP.
An unnumbered interface is an IPv4 capability only used in cases where IPv4 is active (IPv4-only and mixed IPv4/IPv6 environments). When configuring an unnumbered interface, the interface specified for the unnumbered interface (system or other) must have an IPv4 address. Also, the interface type for the unnumbered interface will automatically be point-to-point. The unnumbered option can be used in IES and VPRN access interfaces, as well as in a network interface with MPLS support.
4.1.7. Segment Routing in Shortest Path Forwarding
Segment routing adds to IS-IS and OSPF routing protocols the ability to perform shortest path routing and source routing using the concept of abstract segment. A segment can represent a local prefix of a node, a specific adjacency of the node (interface/next-hop), a service context, or a specific explicit path over the network. For each segment, the IGP advertises an identifier referred to as Segment ID (SID).
When segment routing is used together with MPLS data plane, the SID is a standard MPLS label. A router forwarding a packet using segment routing will thus push one or more MPLS labels. This is the scope of the features described in this section.
Segment routing using MPLS labels can be used in both shortest path routing applications and in traffic engineering applications. This section focuses on the shortest path forwarding applications.
When a received IPv4 or IPv6 prefix SID is resolved, the Segment Routing module programs the ILM with a swap operation and also the LTN with a push operation both pointing to the primary/LFA NHLFE. An IPv4 or IPv6 SR tunnel to the prefix destination is also added to the TTM and is available for use by shortcut applications and L2/L3 services.
4.1.7.1. Configuring Segment Routing in Shortest Path
The user enables segment routing in an IGP routing instance using the following sequence of commands.
Next, the user enables the context to configure segment routing parameters within a given IGP instance:
Local Label (Prefix SID) = start-label + {SID index}
The label operation in the network becomes thus very similar to LDP when operating in the independent label distribution mode (RFC 5036) with the difference that the label value used to forward a packet to each downstream router is computed by the upstream router based on advertised prefix SID index using the above formula.
The following is an example of a router advertising its loopback address and the resulting packet label encapsulation throughout the network.
Figure 16: Packet Label Encapsulation using Segment Routing Tunnel

Router N-6 advertises loopback 10.10.10.1/32 with a prefix index of 5.Routers N-1 to N-6 are configured with the same SID index range of [1,100] and an offset label of 100 to 600 respectively. The following are the actual label values programmed by each router for the prefix of PE2:
- N-6 has a start label value of 600 and programs an ILM with label 605.
- N-3 has a start label of 300 and swaps incoming label 305 to label 605.
- N-2 has a start label of 200 and swaps incoming label 205 to label 305.
Similar operations are performed by N-4 and N-5 for the bottom path.
N-1 has an SR tunnel to N-6 with two ECMP paths. It pushes label 205 when forwarding an IP or service packet to N-6 via downstream next-hop N-2 and pushes label 405 when forwarding via downstream next-hop N-4.
The CLI for configuring the prefix SID index range and offset label value for a given IGP instance is as follows:
The user can, however, change the SRGB on the fly as long as it does not reduce the current per-IGP instance SID index/label range defined with the prefix-sid-range. Otherwise, the user must shutdown the segment routing context of the IGP instance and delete and re-configure the prefix-sid-range command.
Finally, the user brings up segment routing on that IGP instances by un-shutting the context:
The IGP segment routing extensions are area-scoped. As a consequence, the user must configure the flooding scope to area in OSPF and to area or as in IS-IS, otherwise performing no shutdown of the segment-routing node fail.
The segment-routing command is mutually exclusive with the igp-shortcut and advertise-tunnel-link options under IGP, because an SR tunnel cannot resolve to an RSVP tunnel next-hop.
Next, the user assigns a node SID index or label to the prefix representing the primary address of an IPv4 or IPv6 network interface of type loopback using one of the following commands:
Only a single node SID can be assigned to an interface. The secondary address of an IPv4 interface cannot be assigned a node SID index and does not inherit the SID of the primary IPv4 address. The same applies to the non-primary IPv6 addresses of an interface.
Above commands should fail if the network interface is not of type loopback or if the interface is defined in an IES or a VPRN context. Also, assigning the same SID index/label value to the same interface in two different IGP instances is not allowed within the same node.
Also, for OSPF the protocol version number and the instance number dictates if the node-SID index/label is for an IPv4 or IPv6 address of the interface. Specifically, the support of address families in OSPF is as follows:
- ospfv2: always IPv4 only
The value of the label or index SID is taken from the range configured for this IGP instance. When using the global mode of operation, a new segment routing module checks that the same index or label value cannot be assigned to more than one loopback interface address. When using the per-instance mode of operation, this check is not required because the index, and thus the label ranges, of the various IGP instances are not allowed to overlap.
4.1.7.2. Segment Routing Operational Procedures
4.1.7.2.1. Prefix Advertisement and Resolution
- Advertise the assigned index for each configured node SID in the new prefix SID sub-TLV with the N-flag (node-SID flag) set. Then the segment routing module programs the incoming label map (ILM) with a pop operation for each local node SID in the data path.
- Assign and advertise automatically an adjacency SID label for each formed adjacency over a network IP interface in the new Adjacency SID sub-TLV. The following points should be considered.
- Adjacency SID is advertised for both numbered and unnumbered network IP interface.
- Adjacency SID for parallel adjacencies between two IGP neighbors is not supported.
The segment routing module programs the incoming label map (ILM) with a swap to an implicit null label operation, for each advertised adjacency SID.
When the user enables segment routing in a given IGP instance, the main SPF and LFA SPF are computed normally and the primary next-hop and LFA backup next-hop for a received prefix are added to RTM without the label information advertised in the prefix SID sub-TLV. In all cases, the segment routing (SR) tunnel is not added into RTM.
4.1.7.2.2. Error and Resource Exhaustion Handling
When the prefix corresponding to a node SID is being resolved, the following procedures are followed.
4.1.7.2.2.1. Procedure 1: Providing support of multiple topologies for the same destination prefix
For example: In two different instances (L2, IS-IS instance 1 and L1, IS-IS instance 2—see Figure 17), Router D has the same prefix destination, with different SIDs (SIDx and SIDy).
Figure 17: Programming multiple tunnels to the same destination
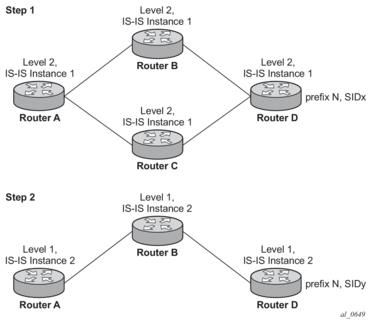
Assume the following route type preference in RTM and tunnel type preference in TTM are configured:
- ROUTE_PREF_ISIS_L1_INTER (RTM) 15
- ROUTE_PREF_ISIS_L2_INTER (RTM) 18
- ROUTE_PREF_ISIS_TTM 10
| Note: |
- Router A performs the following resolution within the single IS-IS instance 1, level 2. All metrics are the same, and ECMP = 2.
- For prefix N, the RTM entry is:
- prefix N
- nhop1 = B
- nhop2 = C
- preference 18
- For prefix N, the SR tunnel TTM entry is:
- tunnel-id 1: prefix N-SIDx
- nhop1 = B
- nhop2 = C
- tunl-pref 10
- Add IS-IS instance 2 (Level 1) in the same setup, but in routers A, B, and C only.
- For prefix N, the RTM entry is:
- prefix N
- nhop1 = B
- preference 15
- For prefix N, there are two SR tunnel entries in TTM:SR entry for L2:
- tunnel-id 1: prefix N-SIDx
- nhop1 = B
- nhop2= C
- tunl-pref 10
SR entry for L1:- tunnel-id 2: prefix N-SIDy
4.1.7.2.2.2. Procedure 2: Resolving received SID indexes or labels to different routes of the same prefix within the same IGP instance
Two variations of this procedure can occur.
4.1.7.2.2.3. Procedure 3: Checking for SID error prior to programming ILM and NHLFE
If any of the following conditions are true, the router logs a trap and generates a syslog error message and will not program the ILM and NHLFE for the prefix SID.
- Received prefix SID index falls outside of the locally configured SID range.
- One or more resolved ECMP next-hops for a received prefix SID did not advertise SR Capability sub-TLV.
- Received prefix SID index falls outside the advertised SID range of one or more resolved ECMP next-hops.
4.1.7.2.2.4. Procedure 4: Programming ILM/NHLFE for duplicate prefix-SID indexes/labels for different prefixes
Two variations of this procedure can occur.
- For received duplicate prefix-SID indexes or labels for different prefixes within the same IGP instance, the router:
- programs ILM/NHLFE for the first one
- logs a trap and a syslog error message
- does not program the subsequent one in data path
- For received duplicate prefix-SID index for different prefixes across IGP instances, there are two options.
- programs ILM/NHLFE for the prefix of the winning IGP instance based on the RTM route type preference
- logs a trap and a syslog error message
- does not program the subsequent prefix SIDs in data path
- In per-instance SID index range mode of operation, the resulting ILM label will have different values across the IGP instances. The router programs ILM/NHLFE for each prefix as expected.
4.1.7.2.2.5. Procedure 5: Programming ILM/NHLFE for the same prefix across IGP instances
The behavior in the case of a global SID index range is illustrated by the IS-IS example in Figure 18.
Figure 18: Handling of Same Prefix and SID in different IS-IS Instances
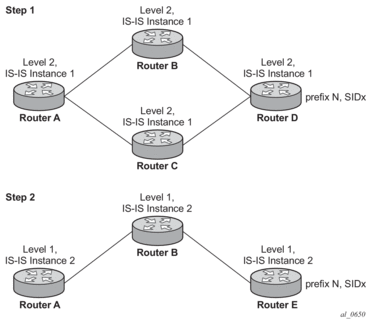
Assume the following route type preference in RTM and tunnel type preference in TTM are configured:
- ROUTE_PREF_ISIS_L1_INTER (RTM) 15
- ROUTE_PREF_ISIS_L2_INTER (RTM) 18
- ROUTE_PREF_ISIS_TTM 10
| Note: |
- Router A performs the following resolution within the single IS-IS instance 1, level 2. All metrics are the same, and ECMP = 2.
- For prefix N, the RTM entry is:
- prefix N
- nhop1 = B
- nhop2 = C
- preference 18
- For prefix N, the SR tunnel TTM entry is:
- tunnel-id 1: prefix N-SIDx
- nhop1 = B
- nhop2 = C
- tunl-pref 10
- Add IS-IS instance 2 (Level 1) in the same setup, but in routers A, B, and E only.
- For prefix N, the RTM entry is:
- prefix N
- nhop1 = B
- preference 15
- For prefix N, there is one SR tunnel entry for L2 in TTM:
- tunnel-id 1: prefix N-SIDx
- nhop1 = B
- nhop2 = C
- tunl-pref 10
4.1.7.2.2.6. Procedure 6: Handling ILM resource exhaustion while assigning an SID index/label
If the system exhausted an ILM resource while assigning an SID index/label to a local loopback interface, then index allocation is failed and an error is returned in CLI. In addition, the router logs a trap and generates a syslog error message.
4.1.7.2.2.7. Procedure 7: Handling ILM/NHLFE/other IOM or CPM resource exhaustion while resolving or programming an SID index/label
- The IGP instance goes into overload and a trap and syslog error message are generated.
- The segment routing module deletes the tunnel.
4.1.7.3. Segment Routing Tunnel Management
With ECMP, a maximum of 32 primary next-hops (NHLFEs) are programmed for the same tunnel destination per IGP instance. ECMP and LFA next-hops are mutually exclusive as per existing implementation.
The default preference for shortest path SR tunnels in the TTM is set lower than LDP tunnels but higher than BGP tunnels to allow controlled migration of customers without disrupting their current deployment when they enable segment routing. The following is the setting of the default preference of the various tunnel types. This includes the preference of both SR tunnels based on shortest path (referred to as SR-ISIS and SR-OSPF).
The global default TTM preference for the tunnel types is as follows:
- ROUTE_PREF_RSVP 7
- ROUTE_PREF_SR_TE 8
- ROUTE_PREF_LDP 9
- ROUTE_PREF_OSPF_TTM 10
- ROUTE_PREF_ISIS_TTM 11
- ROUTE_PREF_BGP_TTM 12
- ROUTE_PREF_GRE 255
For SR-ISIS and SR-OSPF, the user can configure the preference of each specific IGP instance away from the above default values.
| Note: The preference of SR-TE LSP is not configurable and is the second most preferred tunnel type after RSVP-TE. This is independent if the SR-TE LSP was resolved in IS-IS or OSPF. |
4.1.7.3.1. Tunnel MTU Determination
The MTU of an SR tunnel populated into TTM is determined as in the case of an IGP tunnel; for example, LDP LSP, based on the outgoing interface MTU minus the label stack size. Segment routing, however, supports remote LFA which programs an LFA backup next-hop adding another label to the tunnel for a total of two labels.
Based on the above, the user is provided with a CLI to configure the MTU of all SR tunnels within each IGP instance:
The MTU of the SR tunnel, in bytes, is then determined as follows:
SR_Tunnel_MTU = MIN {Cfg_SR_MTU, IGP_Tunnel_MTU- (1+ frr-overhead)*4}
Where:
- IGP_Tunnel_MTU is the minimum of the IS-IS or OSPF interface MTU among all the ECMP paths or among the primary and LFA backup paths of this SR tunnel.
- frr-overhead is set to 1 if segment-routing and remote-lfa options are enabled in the IGP instance. Otherwise, it is set to 0.
The SR tunnel MTU is dynamically updated anytime any of the above parameters used in its calculation changes. This includes when the set of the tunnel next-hops changes or the user changes the configured SR MTU or interface MTU value.
| Note: For the purpose of fragmentation of IP packets forwarded in GRT or in a VPRN over an SR shortest path tunnel, the IOM always deducts the worst case MTU (5 labels or 6 labels if hash label feature is enabled) from the outgoing interface MTU for the decision to fragment or not the packet. In this case, the above formula is not used. |
4.1.7.4. Remote LFA with Segment Routing
The user enables the remote LFA next-hop calculation by the IGP LFA SPF by appending the following new option in the existing command which enables LFA calculation:
SPF performs the remote LFA additional computation following the regular LFA next-hop calculation when both of the following conditions are met:
- The remote-lfa option is enabled in an IGP instance.
- The LFA next hop calculation did not result in protection for one or more prefixes resolved to a given interface.
Remote LFA extends the protection coverage of LFA-FRR to any topology by automatically computing and establishing/tearing-down shortcut tunnels, also referred to as repair tunnels, to a remote LFA node which puts the packets back into the shortest without looping them back to the node which forwarded them over the repair tunnel. A repair tunnel can in theory be an RSVP LSP, an LDP-in-LDP tunnel, or an SR tunnel. In SR OS, this feature is restricted to use an SR repair tunnel to the remote LFA node.
Figure 19: Remote LFA Algorithm
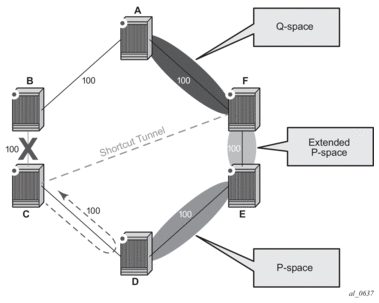
- Compute the extended P space of Node C with respect to link C-B: set of nodes reachable from node C without any path transiting the protected link (link C-B). This yields nodes D, E, and F.The determination of the extended P space by node C uses the same computation as the regular LFA by running SPF on behalf of each of the neighbors of C.

Note: RFC 7490 initially introduced the concept of P space, which would have excluded node F because, from the node C perspective, node C has a couple of ECMP paths, one of which goes via link C-B. However, because the remote LFA next-hop is activated when link C-B fails, this rule can be relaxed and node F can be included, which then yields the extended P space.
The user can limit the search for candidate P nodes to reduce the amount of SPF calculations in topologies where many eligible P nodes can exist. A CLI command is provided to configure the maximum IGP cost from node C for a P node to be eligible:- configure>router>isis>loopfree-alternate remote-lfa max-pq-cost value
- configure>router>ospf>loopfree-alternate remote-lfa max-pq-cost value
- Compute the Q space of node B with respect to link C-B: set of nodes from which the destination proxy (node B) can be reached without any path transiting the protected link (link C-B).The Q space calculation is effectively a reverse SPF on node B. In general, one reverse SPF is run on behalf of each of C neighbors to protect all destinations resolving over the link to the neighbor. This yields nodes F and A in the example of Figure 19.The user can limit the search for candidate Q nodes to reduce the amount of SPF calculations in topologies where many eligible Q nodes can exist. The CLI above is also used to configure the maximum IGP cost from node C for a Q node to be eligible.
- Select the best alternate node: this is the intersection of extended P and Q spaces. The best alternate node or PQ node is node F in the example of Figure 19. From node F onwards, traffic follows the IGP shortest path.If many PQ nodes exist, the lowest IGP cost from node C is used to narrow down the selection and if more than one PQ node remains, the node with lowest router-id is selected.
The details of the label stack encoding when the packet is forwarded over the remote LFA next-hop is shown in Figure 20.
Figure 20: Remote LFA Next-Hop in Segment Routing

If the PQ node is also the advertising router for the resolved prefix, the label stack is compressed in some cases depending on the IGP:
- In IS-IS, the label stack is always reduced to a single label, which is the label of the resolved prefix owned by the PQ node.
- In OSPF, the label stack is reduced to the single label of the resolved prefix when the PQ node advertised a single node SID in this OSPF instance. If the PQ node advertised a node SID for multiple of its loopback interfaces within this same OSPF instance, the label stack is reduced to a single label only in the case where the SID of the resolved prefix is the lowest SID value.
The following rules and limitations apply to the remote LFA implementation:
4.1.7.5. Topology Independent LFA
4.1.7.5.1. TI-LFA Configuration
The FRR overhead is computed by IGP and its value is set as follows:
- 0 if segment-routing is disabled in the IGP instance
- 0 if segment-routing is enabled but remote-lfa is disabled and ti-lfa is disabled
- 1 if segment routing is enabled and remote-lfa is enabled but ti-lfa is disabled, or if segment-routing is enabled and remote-lfa is enabled and ti-lfa is enabled but ti-lfa max-sr-frr-labels labels is set to 0.
4.1.7.5.2. TI-LFA Link-Protect Operation
4.1.7.5.2.1. LFA Protection Option Applicability
- First compute a regular LFA for each node and prefix. In this step, a computed backup next-hop satisfies any applied LFA policy. This backup next-hop protects that specific prefix or node in the context of IP FRR, LDP FRR, SR FRR, and SR-TE FRR.
- Next, always follow with the TI-LFA if the ti-lfa option enabled for all prefixes and nodes regardless of the outcome of the first step.The prefix or node continues the use backup next-hop found in (a) in LDP FRR, if the LDP fast-reroute backup-sr-tunnel option disabled, and in IP FRR.
- adjacency SID of an alternate ECMP next-hop
- TI-LFA backup next-hop
- LFA backup next-hop
4.1.7.5.2.2. TI-LFA Algorithm
Figure 21: Selecting Link-Protect TI-LFA Backup Path
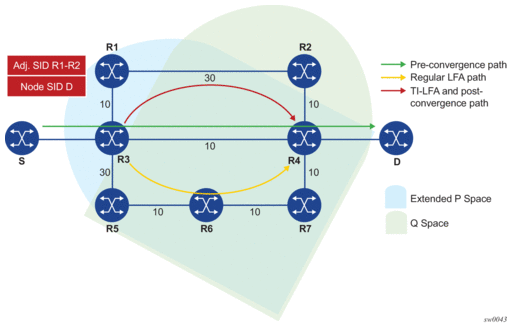
For each destination node D:
- This is the set of nodes Yi in the post-convergence paths which are reachable from R3 neighbors without any path transiting the protected link R3-R4.Distance_opt(R1, Yi) < Distance_opt(R1, R3) + Distance_opt(R3, Yi)
- Compute Q-space of R3 with respect to protected link R3-R4 in the post-convergence paths.This is the set of nodes Zi in the post-convergence paths from which the neighbor node R4 of the protected link, acting as a proxy for all destinations D, can be reached without any path transiting the protected link R3-R4.Distance_opt(Zi, R4) < Distance_opt(Zi, R3) + Distance_opt(R3, R4)The Q-space calculation yields nodes R2 and R4.
- In the topology in Figure 21, there is a single post-convergence path, a single P-node (R1), and the closest of the two found Q-nodes to the P-Node is R2.
4.1.7.5.2.3. TI-LFA Feature Interaction and Limitations
The following are feature interactions and limitations of the TI-LFA link protection.
Figure 22: TI-LFA Backup Path via a Pseudo-Node
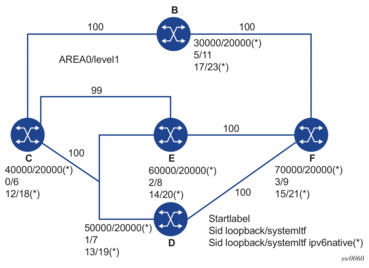
- For example, node A in Figure 23 computes the link-protect TI-LFA backup path for destination node E as path A-C-E, where C is the P node and E is the Q node and destination. C has a pair of adjacency SIDs with the same metric to E. Node A selects the adjacency over the P2P link C-E because it has the lowest SID value but node C may select the interface C-PN in its post-convergence path calculation if that interface has a lower interface index than P2P link C-E.
Figure 23: Parallel Adjacencies between P and Q Nodes
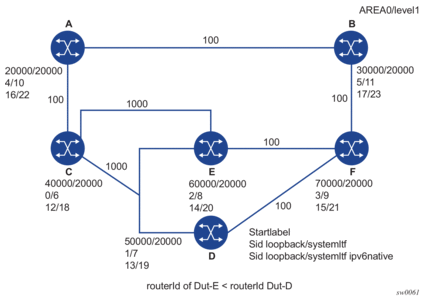
4.1.7.5.3. Data Path Support
The data path models the backup path like a SR-TE LSP and thus uses a super-NHLFE pointing to the NHLFE of the first hop in the repair tunnel. That first hop corresponds to either an adjacency SID or a node SID of the P node.
4.1.7.6. IPv6 Segment Routing using MPLS Encapsulation
This feature implements support for SR IPv6 tunnels in IS-IS MT=0. The user can configure a node SID for the primary IPv6 global address of a loopback interface, which then gets advertised in IS-IS. IS-IS automatically assigns and advertises an adjacency SID for each adjacency with an IPv6 neighbor. After the node SID is resolved, it is used to install an IPv6 SR-ISIS tunnel in the TTM for use by the services.
4.1.7.6.1. IS-IS MT=0 Extensions
4.1.7.6.2. Service and Forwarding Contexts Supported
The service and forwarding contexts supported with the SR-ISIS IPv6 tunnels are:
- SDP of type sr-isis with far-end option using IPv6 address
- VLL, VPLS, IES/VPRN spoke-interface, R-VPLS
- Support of PW redundancy within Epipe/Ipipe VLL, Epipe spoke termination on VPLS and R-VPLS, and Epipe/Ipipe spoke termination on IES/VPRN
- IPv6 static route resolution to indirect next-hop using Segment Routing IPv6 tunnel
- Remote mirroring and L3 encap LI
4.1.7.6.3. Services Using SDP with a SR IPv6 Tunnel
The MPLS SDP of type sr-isis with a far-end option using an IPv6 address is supported. Note the SDP must have the same IPv6 far-end address, used by the control plane for the T-LDP session, as the prefix of the node SID of the SR IPv6 tunnel.
The bgp-tunnel, lsp, sr-te lsp, sr-ospf, and mixed-lsp-mode commands are blocked within the SDP configuration context when the far-end is an IPv6 address.
- the IPv6 PW control word with both data plane packets and VCCV OAM packets
- Hash Label and Entropy Label, with the above services
- network domains in VPLS
The PW switching feature is not supported with LDP IPv6 control planes. As a result, the CLI does not allow the user to enable the vc-switching option whenever one or both spoke SDPs uses an SDP that has the far-end configured as an IPv6 address.
L2 services that use BGP control plane such as dynamic MS-PW, BGP-AD VPLS, BGP-VPLS, BGP-VPWS, and EVPN MPLS cannot bind to an SR IPv6 tunnel because a BGP session to a BGP IPv6 peer does not support advertising an IPv6 next-hop for the L2 NLRI. As a result, these services will not auto-generate SDPs using an SR IPv6 tunnel. In addition, they skip any provisioned SDPs with far-end configured to an IPv6 address when the use-provisioned-sdp option is enabled.
SR OS also supports multi-homing with T-LDP active/standby FEC 128 spoke SDP using SR IPv6 tunnel to a VPLS/B-VPLS instance. BGP multi-homing is not supported because BGP IPv6 does not support signaling an IPv6 next-hop for the L2 NLRI.
The Shortest Path Bridging (SPB) feature works with spoke SDPs bound to an SDP that uses an SR IPv6 tunnel.
4.1.7.7. Data Path Support
Table 29: Data Path Support
Label type | Operation |
Top label is a local node SID | Label is popped and the packet is further processed. If the popped node SID label is the bottom of stack label, the IP packet is looked up and forwarded in the appropriate FIB. |
Top or next label is a remote node SID | Label is swapped to the calculated label value for the next-hop and forwarded according to the primary or backup NHLFE. With ECMP, a maximum of 32 primary next-hops (NHLFEs) are programmed for the same destination prefix and for each IGP instance. ECMP and LFA next-hops are mutually exclusive as per existing implementation. |
Top or next label is an adjacency SID | Label is popped and the packet is forwarded out on the interface to the next-hop associated with this adjacency SID label. In effect, the data path operation is modeled like a swap to an implicit-null label instead of a pop. |
Next label is BGP 3107 label | The packet is further processed according to the ILM operation as in current implementation.
|
Next label is a service label | The packet is looked up and forwarded in the Layer 2 or VPRN FIB as in current implementation. |
Figure 24: Transport Label Stack in Shortest Path Forwarding with Segment Routing

Assume that a VPRN service in node B forwards a packet received on a SAP to a destination VPN-IPv4 prefix X advertised by a remote PE2 via ASBR/ABR node A. Router B is in a segment routing domain while PE2 is in an LDP domain. BGP label routes are used to distribute the PE /32 loopbacks between the two domains.
When the ABR/ASBR node receives the packet from either node B or node Z, it pops the segment routing label which corresponds to a local node SID, then swaps the BGP label and pushes the LDP label of PE2 which is the next-hop of the BGP label route.
4.1.7.7.1. Hash Label and Entropy Label Support
When the hash-label option is enabled in a service context, hash label is always inserted at the bottom of the stack as per RFC 6391.
The LSR adds the capability to check a maximum of 16 labels in a stack. The LSR is able to hash on the IP headers when the payload below the label stack of maximum size of 16 is IPv4 or IPv6, including when a MAC header precedes it (eth-encap-ip option).
The Entropy Label (EL) feature, as specified in RFC 6790, is introduced for RSVP, LDP, and BGP transport tunnels. It uses the Entropy Label Indicator (ELI) to indicate the presence of the entropy label in the label stack. The ELI, followed by the actual entropy label, is inserted immediately below the transport label for which entropy label feature is enabled. If multiple transport tunnels have the entropy label feature enabled, the ELI/EL is inserted below the lowest transport label in the stack.
The EL feature is not supported with an SR tunnel. If, however, a BGP LSP is tunneled over an SR-ISIS or SR-OSPF tunnel and the entropy label is enabled on the BGP LSP, the LSR parses the label stack and detects the ELI below the BGP label.
The LSR hashing operates as follows:
- If the lbl-only hashing option is enabled, or if one of the other LSR hashing options is enabled but a IPv4 or IPv6 header is not detected below the bottom of the label stack, the LSR hashes on the EL only.
- If the lbl-ip option is enabled, the LSR hashes on the EL and the IP headers.
- If the ip-only or eth-encap-ip is enabled, the LSR hashes on the IP headers only.
For more information about the Hash Label and Entropy Label features, see the "MPLS Entropy Label and Hash Label" section of the MPLS Guide.
4.1.7.8. Control Protocol Changes
This section describes both IS-IS Control Protocol Changes and OSPF Control Protocol Changes.
4.1.7.8.1. IS-IS Control Protocol Changes
New TLV/sub-TLVs are defined in draft-ietf-isis-segment-routing-extensions and are supported in the implementation of segment routing in IS-IS. Specifically:
- the prefix SID sub-TLV
- the adjacency SID sub-TLV
- the SID/Label Binding TLV
- SR-Capabilities Sub-TLV
- SR-Algorithm Sub-TLV
This section describes the behaviors and limitations of the IS-IS support of segment routing TLV and sub-TLVs.
SR OS supports advertising the IS router capability TLV (RFC 4971) only for topology MT=0. As a result, the segment routing capability Sub-TLV can only be advertised in MT=0 which restricts the segment routing feature to MT=0.
I and V flags are both set to 1 when originating the SR capability sub-TLV to indicate support for processing both SR MPLS encapsulated IPv4 and IPv6 packets on its network interfaces. These flags are not checked when the sub-TLV is received. Only the SRGB range is processed.
The algorithm field is set to 0, meaning Shortest Path First (SPF) algorithm based on link metric, when originating the SR-Algorithm capability sub-TLV but is not checked when the sub-TLV is received.
Both IPv4 and IPv6 prefix and adjacency SID sub-TLVs originate within MT=0.
SR OS originates a single prefix SID sub-TLV per IS-IS IP reachability TLV and processes the first prefix SID sub-TLV only if multiple are received within the same IS-IS IP reachability TLV.
SR OS encodes the 32 bit index in the prefix SID sub-TLV. The 24 bit label is not supported.
SR OS originates a prefix SID sub-TLV with the following encoding of the flags and the following processing rules:
- The R-flag is set if the prefix SID sub-TLV, along with its corresponding IP reachability TLV, is propagated between levels. See below for more details about prefix propagation.
- The N-flag is always set because SR OS supports prefix SID of type node SID only.
- The V-flag is always set to 0 to indicate an index value for the SID.
- The L-flag is always set to 0 to indicate that the SID index value is not locally significant.
- The algorithm field is always set to zero to indicate Shortest Path First (SPF) algorithm based on link metric and is not checked on a received prefix SID sub-TLV.
- SID received via L1 in a prefix SID sub-TLV part of IP reachability TLV
- SID received via L2 in a prefix SID sub-TLV part of IP reachability TLV
- SR OS propagates the prefix SID sub-TLV when exporting the prefix to another IS-IS instance; however, it does not propagate it if the prefix is exported from a different protocol. Thus, when the corresponding prefix is redistributed from another protocol such as OSPF, the prefix SID is removed.
SR OS originates an adjacency SID sub-TLV with the following encoding of the flags:
- the F-flag is set to zero to indicate the IPv4 family and is set to 1to indicate an IPv6 family for the adjacency encapsulation.
- the B-Flag is set to zero and is not processed on receipt
- the V-flag is always set to 1
- the L-flag is always set to 1
- the weight octet is not supported and is set to all zeros.
SR OS can originate the SID/Label Binding TLV as part of the Mapping Server feature (see 4.1.8 for more information). It can process it properly if received. The following rules and limitations should be considered.
- Only the Mapping Server Prefix-SID Sub-TLV within the TLV is processed and the ILMs installed if the prefixes in the provided range are resolved.
- The range and FEC prefix fields are processed. Each FEC prefix is resolved normally, as for the prefix SID sub-TLV, meaning there must be an IP Reachability TLV received for the exact matching prefix.
- If the same prefix is advertised with both a prefix SID sub-TLV and a mapping server Prefix-SID sub-TLV. The resolution follows the following route preference:
- SID received via L1 in a prefix SID sub-TLV part of IP reachability TLV
- SID received via L2 in a prefix SID sub-TLV part of IP reachability TLV
- SID received via L1 in a mapping server Prefix-SID sub-TLV
- SID received via L2 in a mapping server Prefix-SID sub-TLV
- The mapping server which advertised the SID/Label Binding TLV does not need to be in the shortest path for the FEC prefix.
- No check is performed if the content of the binding TLVs from different mapping servers are consistent or not.
4.1.7.8.2. OSPF Control Protocol Changes
New TLV/sub-TLVs are defined in draft-ietf-ospf-segment-routing-extensions-04 and are required for the implementation of segment routing in OSPF. Specifically:
- the prefix SID sub-TLV part of the OSPFv2 Extended Prefix TLV
- the prefix SID sub-TLVpart of the OSPFv2 Extended Prefix Range TLV
- the adjacency SID sub-TLV part of the OSPFv2 Extended Link TLV
- SID/Label Range Capability TLV
- SR-Algorithm Capability TLV
This section describes the behaviors and limitations of the OSPF support of segment routing TLV and sub-TLVs.
SR OS originates a single prefix SID sub-TLV per OSPFv2 Extended Prefix TLV and processes the first one only if multiple prefix SID sub-TLVs are received within the same OSPFv2 Extended Prefix TLV.
SR OS encodes the 32-bit index in the prefix SID sub-TLV. The 24-bit label or variable IPv6 SID is not supported.
SR OS originates a prefix SID sub-TLV with the following encoding of the flags.
- The M-Flag is always unset because SR OS does not support originating a mapping server prefix-SID sub-TLV.
- The V-flag is always set to 0 to indicate an index value for the SID.
- The L-flag is always set to 0 to indicate that the SID index value is not locally significant.
- The algorithm field is always set to zero to indicate Shortest Path First (SPF) algorithm based on link metric and is not checked on a received prefix SID sub-TLV.
SR OS resolves a prefix SID received within an Extended Prefix TLV based on the following route preference:
- SID received via an intra-area route in a prefix SID sub-TLV part of Extended Prefix TLV
- SID received via an inter-area route in a prefix SID sub-TLV part of Extended Prefix TLV
SR OS originates an adjacency SID sub-TLV with the following encoding of the flags.
- The F-flag is unset to indicate the Adjacency SID refers to an adjacency with outgoing IPv4 encapsulation.
- The B-flag is set to zero and is not processed on receipt.
- The V-flag is always set.
- The L-flag is always set.
- The S-flag is not supported.
- The weight octet is not supported and is set to all zeros.
SR OS does not originate the OSPFv2 Extended Prefix Range TLV but can process it properly if received. The following rules and limitations should be considered.
- Only the prefix SID sub-TLV within the TLV is processed and the ILMs installed if the prefixes are resolved.
- The range and address prefix fields are processed. Each prefix is resolved separately.
- If the same prefix is advertised with both a prefix SID sub-TLV in a IP reachability TLV and a mapping server Prefix-SID sub-TLV, the resolution follows the following route preference:
- the SID received via an intra-area route in a prefix SID sub-TLV part of Extended Prefix TLV
- the SID received via an inter-area route in a prefix SID sub-TLV part of Extended Prefix TLV
- the SID received via intra-area route in a prefix SID sub-TLV part of a OSPFv2 Extended Range Prefix TLV
- the SID received via a inter-area route in a prefix SID sub-TLV part of a OSPFv2 Extended Range Prefix TLV
- No leaking of the entire TLV is performed between areas. Also, an ABR will not propagate the prefix-SID sub-TLV from the Extended Prefix Range TLV (received from a mapping server) into an Extended Prefix TLV if the latter is propagated between areas.
- The mapping server which advertised the OSPFv2 Extended Prefix Range TLV does not need to be in the shortest path for the FEC prefix.
- No check is performed to determine whether or not the contents of the OSPFv2 Extended Prefix Range TLVs received from different mapping servers are consistent.
SR OS supports propagation on ABR of external prefix LSA into other areas with routeType set to 3 as per draft-ietf-ospf-segment-routing-extensions-04.
SR OS supports propagation on ABR of external prefix LSA with route type 7 from NSSA area into other areas with route type set to 5 as per draft-ietf-ospf-segment-routing-extensions-04. SR OS does not support propagating of the prefix SID sub-TLV between OSPF instances.
When the user configures an OSPF import policy, the outcome of the policy applies to prefixes resolved in RTM and the corresponding tunnels in TTM. So, a prefix removed by the policy will not appear as both a route in RTM and as an SR tunnel in TTM.
4.1.7.9. BGP Shortcut Using Segment Routing Tunnel
The user enables the resolution of IPv4 prefixes using SR tunnels to BGP next-hops in TTM with the following command:
When the sr-isis or sr-ospf value is enabled, an SR tunnel to the BGP next-hop is selected in the TTM from the lowest preference IS-IS or OSPF instance. If many instances have the same lowest preference from the lowest numbered IS-IS or OSPF instance
4.1.7.10. BGP Label Route Resolution Using Segment Routing Tunnel
The user enables the resolution of RFC 3107 BGP label route prefixes using SR tunnels to BGP next-hops in TTM with the following command:
The following tunnel types are supported in a BGP label route context and in order of preference: RSVP, LDP, and Segment Routing.
When the sr-isis or sr-ospf is specified using the resolution-filter option, a tunnel to the BGP next-hop is selected in the TTM from the lowest numbered IS-IS or OSPF instance.
4.1.7.11. Service Packet Forwarding with Segment Routing
SDP subtypes of the MPLS type are available to allow service binding to an SR tunnel programmed in TTM by OSPF or IS-IS:
*A:7950 XRS-20# configure service sdp 100 mpls create
*A:7950 XRS-20>config>service>sdp$ sr-ospf
*A:7950 XRS-20>config>service>sdp$ sr-isis
The SDP of type sr-isis or sr-ospf can be used with the far-end option. When the sr-isis or sr-ospf value is enabled, a tunnel to the far-end address is selected in the TTM from the lowest preference IS-IS or OSPF instance. If many instances have the same lowest preference from the lowest numbered IS-IS or OSPF instance. The SR-ISIS or SR-OSPF tunnel is selected at the time of the binding, following the tunnel selection rules. If a more preferred tunnel is subsequently added to the TTM, the SDP will not automatically switch to the new tunnel until the next time the SDP is being re-resolved.
The tunnel-far-end option is not supported. In addition, the mixed-lsp-mode option does not support the sr-isis and sr-ospf tunnel types.
The signaling protocol for the service labels for an SDP using an SR tunnel can be configured to static (off), T-LDP (tldp), or BGP (bgp).
SR tunnels can be used in VPRN and BGP EVPN with the auto-bind-tunnel command. See Next-hop Resolution of BGP Routes Using Tunnels for more information.
Both VPN-IPv4 and VPN-IPv6 (6VPE) are supported in a VPRN or BGP EVPN service using segment routing transport tunnels with the auto-bind-tunnel command.
The following are the service contexts which are supported with SR tunnels:
- VLL, LDP VPLS, IES/VPRN spoke-interface, R-VPLS, BGP EVPN.
- BGP-AD VPLS, BGP-VPLS, BGP VPWS when the use-provisioned-sdp option is enabled in the binding to the PW template.
- Intra-AS BGP VPRN for VPN-IPv4 and VPN-IPv6 prefixes with both auto-bind and explicit SDP.
- Multicast over IES/VPRN spoke interface with spoke-sdp riding an SR tunnel.
The following service contexts are not supported:
- Inter-AS VPRN.
- Dynamic MS-PW, PW-switching.
- BGP-AD VPLS, BGP-VPLS, BGP VPWS with auto-generation of SDP using an SR tunnel when binding to a PW template.
4.1.7.12. Mirror Services and Lawful Intercept
The user can configure a spoke-SDP bound to an SR tunnel to forward mirrored packets from a mirror source to a remote mirror destination. In the configuration of the mirror destination service at the destination node, the remote-source command must use a spoke-sdp with VC-ID which matches the one the user configured in the mirror destination service at the mirror source node. The far-end option is not supported with an SR tunnel.
This also applies to the configuration of the mirror destination for an LI source.
Configuration at mirror source node:
Note:
|
Configuration at mirror destination node:
Note:
|
Mirroring and LI are also supported with the PW redundancy feature when the endpoint spoke-sdp, including the ICB, is using an SR tunnel. Routable Lawful Intercept Encapsulation (config>mirror>mirror-dest>encap# layer-3-encap) when the remote L3 destination is reachable over an SR tunnel is also supported.
4.1.8. Segment Routing Mapping Server Function for IPv4 Prefixes
4.1.8.1. Segment Routing Mapping Server
The mapping server feature allows the configuration and advertisement via IS-IS of the node SID index for prefixes of routers which are in the LDP domain. This is performed in the router acting as a mapping server and using a prefix-SID sub-TLV within the SID/Label binding TLV in IS-IS.
The user configures the SR mapping database in IS-IS using the following CLI command:
The no form of the sid-map command deletes the range of node SIDs beginning with the specified index value. The no form of the mapping-server command deletes all node SID entries in the IS-IS instance.
By setting the S-flag, the user can indicate to the IS-IS routers in the rest of the network that the flooding scope of the SID/Label binding TLV is the entire domain. In that case, a router receiving the TLV advertisement should leak it between IS-IS levels. If leaked from level 2 to level 1, the D-flag must be set and, once set, the TLV cannot be leaked back into level 2. Otherwise, the S-flag is clear by default and the TLV must not be leaked by routers receiving the mapping server advertisement.
| Note: SR OS does not leak this TLV between IS-IS instances and does not support the multi-topology SID/Label Binding TLV format. In addition, the user can specify the mapping server’s flooding scope for the generated SID/Label binding TLV using the level option. This option allows further narrowing of the flooding scope configured under the router IS-IS level-capability for a one or more SID/Label binding TLVs if required. The default flooding scope of the mapping server is L1/L2, which can be narrowed by what is configured under the router IS-IS level-capability. |
The A-flag is used to indicate that a prefix for which the mapping server prefix SID is advertised is directly attached. The M-flag is used to advertise a SID for a mirroring context to provide protection against the failure of a service node. None of these flags are supported on the mapping server; the mapping client ignores them.
Each time a prefix or a range of prefixes is configured in the SR mapping database in any routing instance, the router issues for this prefix, or range of prefixes, a prefix-SID sub-TLV within a IS-IS SID/label binding TLV in that instance. The flooding scope of the TLV from the mapping server is determined as explained above. No further check of the reachability of that prefix in the mapping server route table is performed and no check if the SID index is duplicate with some existing prefix in the local IGP instance database or if the SID index is out of range with the local SRGB.
4.1.8.2. Segment Routing Mapping Server Prefix SID Resolution
An SR-capable router, including the mapping server and its clients, attempts to resolve each received prefix SID to either a SR tunnel endpoint or a LDP tunnel endpoint according to the following preference:
- If a prefix-SID sub-TLV is received within both an IS-IS SID/label binding TLV from the mapping server and an IP reachability TLV for the same prefix in a router prefix advertisement, the latter is preferred in the resolution.
- If the prefix SID is resolved from a router prefix advertisement, the SR ILM is swapped to a SR NHLFE like in regular SR tunnel resolution.
- If the prefix SID is resolved from a mapping server advertisement, then stitching to an LDP FEC is preferred over swapping to a SR next-hop.
- The LDP FEC can be resolved via a static route or an IS-IS instance. The IS-IS instance can be the same or different from the IGP instance that advertised the mapping server prefix SID sub-TLV.
- The SR next-hop in this case is only possible if a route is exported from another IGP instance into the local IGP instance without propagating the prefix SID sub-TLV with the route. Otherwise, when the prefix SID is propagated with the route, the resolution follows preference 2, above.
4.2. FIB Prioritization
The RIB processing of specific routes can be prioritized through the use of the rib-priority command. This command allows specific routes to be prioritized through the protocol processing so that updates are propagated to the FIB as quickly as possible.
The rib-priority command is configured within the global IS-IS routing context, and the administrator has the option to either specify a prefix-list or an IS-IS tag value. If a prefix list is specified than route prefixes matching any of the prefix list criteria will be considered high priority. If instead an IS-IS tag value is specified then any IS-IS route with that tag value will be considered high priority.
4.3. IS-IS Configuration Process Overview
Figure 25 displays the process to provision basic IS-IS parameters.
Figure 25: IS-IS Configuration and Implementation Flow
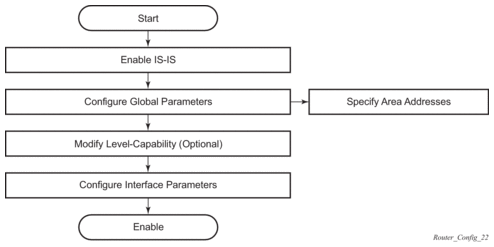
4.4. Configuration Notes
This section describes IS-IS configuration caveats.
4.4.1. General
- IS-IS must be enabled on each participating router.
- There are no default network entity titles.
- There are no default interfaces.
- By default, the routers are assigned a Level 1/Level 2 level capability.