4. Filter Policies
4.1. ACL Filter Policy Overview
ACL filter policies, also referred to as Access Control Lists (ACLs) or just “filters”, are sets of ordered rule entries specifying packet match criteria and actions to be performed to a packet upon a match. Filter policies are created with a unique filter ID, but each filter can also have a unique filter name configured after the filter policy has been created. Either filter ID or filter name can be used throughout the system to manage filter policies and assign them to interfaces.
There are three main types of filter policies: IPv4, IPv6, and MAC filter policies. MAC filter policies support three sub-types: configure>filter>mac-filter>type {normal | isid | vid}. These sub-types allow different Layer 2 match criteria for a MAC filter to be configured.
Additionally, nodes that support Network Group Encryption (NGE) can use IP exception filters. IP exception filters scan all outbound traffic entering an NGE domain and allow packets that match the exception filter criteria to transit the NGE domain unencrypted.
There are different kinds of filter policies as defined by the filter policy scope:
- An exclusive filter defines policy rules explicitly for a single interface. An exclusive filter allows the highest level of customization but uses the most resources, because each exclusive filter consumes hardware resources on line cards on which the interface exists.
- A template filter uses an identical set of policy rules across multiple interfaces. Template filters use a single set of resources per line card, regardless of how many interfaces use a specific template filter policy on that line card. Template filter policies used on access interfaces consume resources on line cards only if at least one access interface for a specific template filter policy is configured on a specific line card.
- An embedded filter defines a common set of policy rules that can then be used (embedded) by other exclusive or template filters in the system. This allows optimized management of filter policies.
- A system filter policy defines a common set of policy rules that can then be activated within other exclusive/template filters. A system filter policy is intended mainly for system-level blacklisting rules but can be used for other applications as well. This allows optimized management of common rules (similarly to embedded filters). However, active system filter policy entries are not duplicated inside each policy that activates the system policy (as is the case when embedding is used). The active system policy is downloaded once to line cards, and activated filter policies are chained to it.
Once created, filter policies must then be associated with interfaces/services/subscribers or with other filter policies (if the created policy cannot be directly deployed on an interface/service/subscriber), so the incoming/outgoing traffic can be subjected to filter rules. Filter policies are associated with interfaces/services/subscribers separately in the ingress and egress directions. A policy deployed on ingress and egress direction can be the same or different. In general, Nokia recommends using different filter policies for the ingress and egress directions and to use different filter policies per service type, since filter policies support different match criteria and different actions for different directions/service contexts.
A filter policy is applied to a packet in the ascending rule entry order. When a packet matches all the parameters specified in a filter entry’s match criteria, the system takes the action defined for that entry. If a packet does not match the entry parameters, the packet is compared to the next higher numerical filter entry rule, and so on. If the packet does not match any of the entries, the system executes the default-action specified in the filter policy: drop or forward.
For Layer 2, either an IPv4/IPv6 or MAC filter policy can be applied. For Layer 3 and network interfaces, an IPv4/IPv6 policy can be applied. For R-VPLS service, a Layer 2 filter policy can be applied to Layer 2 forwarded traffic and a Layer 3 filter policy can be applied to Layer 3 routed traffic. For dual-stack interfaces, if both IPv4 and IPv6 filter policies are configured, the policy applied will be based on the outer IP header of the packet. Non-IP packets do not affect an IP filter policy, so the default action in the IP filter policy will not apply to these packets. IPv6 filters do not apply to the 7450 ESS except when it is in mixed mode.
4.1.1. Filter Policy Basics
The following subsections define main functionality supported by filter policies.
4.1.1.1. Filter Policy Packet Match Criteria
This section defines packet match criteria supported on SR OS for IPv4, IPv6, and MAC filters. Supported criteria types depend on the hardware platform and filter direction, see your Nokia representative for more information.
General notes:
- If multiple unique match criteria are specified in a single filter policy entry, all criteria must be met in order for the packet to be considered a match against that filter policy entry (logical AND).
- Any match criteria not explicitly defined is ignored during match.
- An ACL filter policy entry with match criteria defined, but no action configured, is considered incomplete and inactive (an entry is not downloaded to the line card). A filter policy must have at least one entry active for the policy to be considered active.
- An ACL filter entry with no match conditions defined matches all packets.
- Because an ACL filter policy is an ordered list, entries should be configured (numbered) from the most explicit to the least explicit.
4.1.1.2. IPv4/IPv6 Filter Policy Entry Match Criteria
The IPv4 and IPv6 match criteria supported by SR OS are listed below. The criteria are evaluated against the outer IPv4/IPv6 header and a Layer 4 header that follows (if applicable). Support for match criteria may depend on hardware or filter direction, as described below. Nokia recommends not configuring a filter in a direction or on hardware where a match criterion is not supported as this may lead to unwanted behavior. Some match criteria may be grouped in match lists and may be auto-generated based on router configuration. See Filter Policy Advanced Topics for more information.
Basic Layer 3 match criteria:
- dscp — Match for the specified DSCP value against the Differentiated Services Code Point/Traffic Class field in the IPv4 or IPv6 packet header.
- src-ip/dst-ip — Match for the specified source/destination IPv4/IPv6 address prefix against the source/destination IPv4/IPv6 address field in the IPv4/IPv6 packet header. The operator can optionally configure a mask to be used in a match.
- flow-label — Match for the specified flow label against the Flow label field in IPv6 packets. The operator can optionally configure a mask to be used in a match. This operation is supported on ingress filters.
Fragmentation match criteria:
- fragment — Enable fragmentation support in the filter policy match. For IPv4, match against the MF bit or Fragment Offset field to determine whether the packet is a fragment. For IPv6 for the 7750 SR and 7950 XRS, match against the Next Header Field for Fragment Extension Header value to determine whether the packet is a fragment. Up to six extension headers are matched against to find the Fragmentation Extension Header.Additionally, IPv6 filters support mating against initial fragment using first-only or non-initial fragment non-first-only.IPv4 match fragment criteria are supported on both ingress and egress. IPv6 match fragment criteria are supported on ingress only.
IPv4 options match criteria:
- ip-option — Matches the specified option value in the first option of the IPv4 packet. Operator can optionally configure a mask to be used in a match.
- option-present — Matches the presence of IP options in the IPv4 packet. Padding and EOOL are also considered as IP options. Up to six IP options are matched against.
- multiple-option — Matches the presence of multiple IP options in the IPv4 packet.
- src-route-option — Matches the presence of IP Option 3 or 9 (Loose or Strict Source Route) in the first three IP options of the IPv4 packet. A packet will also match this rule if the packet has more than three IP options.
IPv6 next-header match criteria: (see the Upper-layer protocol match next-header description below):
- ah-ext-header — Matches for the presence of the Authentication Header extension header in the IPv6 packet. This match criterion is supported on ingress only. Up to six extension headers are matched against.
- esp-ext-header — Matches for the presence of the Encapsulating Security Payload extension header in the IPv6 packet. This match criterion is supported on ingress only. Up to six extension headers are matched against.
- hop-by-hop-opt — Matches for the presence of Hop-by-hop options extension header in the IPv6 packet. This match criterion is supported on ingress only. Up to six extension headers are matched against.
- routing-type0 — Matches for the presence of Routing extension header type 0 in the IPv6 packet. This match criterion is supported on ingress only. Up to six extension headers are matched against.
Upper-layer protocol match criteria:
- next-header — Matches the specified upper-layer protocol (such as, TCP, UDP, IGMPv6) against the Next Header field of the IPv6 packet header. “*” can be used to specify TCP or UDP upper-layer protocol match (Logical OR). Next-header matching allows also matching on presence of a subset of IPv6 extension headers. See CLI section for details on which extension header match is supported.
- protocol — Matches the specified protocol against the Protocol field in the IPv4 packet header (for example, TCP, UDP, IGMP) of the outer IPv4. “*” can be used to specify TCP or UDP upper-layer protocol match (Logical OR).
- icmp-code — Matches the specified value against the Code field of the ICMP/ICMPv6 header of the packet. This match is supported only for entries that also define protocol/next-header match for “ICMP”/”ICMPv6” protocol.
- icmp-type — Matches the specified value against the Type field of the ICMP/ICMPv6 header of the packet. This match is supported only for entries that also define protocol/next-header match for “ICMP”/”ICMPv6” protocol.
- src-port/dst-port/port — Matches the specified port value, port list, or port range against the Source Port Number/Destination Port Number of the UDP/TCP/SCTP packet header. An option to match either source or destination (Logical OR) using a single filter policy entry is supported by using a directionless “port” command. Source/destination match is supported only for entries that also define protocol/next-header match for “TCP”, “UDP”, “SCTP”, or “TCP or UDP” protocols. A non-initial fragment will never match an entry with non-zero port criteria specified.
- tcp-ack/tcp-syn — Matches the TCP ACK/TCP SYNC flag presence/absence in the TCP header of the packet. This match is supported only for entries that also define protocol/next-header match for “TCP” protocol.
Operational note for fragmented traffic — IP and IPv6 filters defined to match TCP, UDP, ICMP, or SCTP criteria (such as src-port, dst-port, port, tcp-ack, tcp-syn, icmp-type, and icmp-code) with values of zero or false will also match non-first fragment packets if other match criteria within the same filer entry are also met. Non-initial fragment packets do not contain a UDP, TCP, ICMP or SCTP header.
4.1.1.3. MAC Filter Policy Entry Match Criteria
The following list describes the MAC match criteria supported by SR OS or switches for all types of MAC filters (normal, isid, and vid). The criteria are evaluated against the Ethernet header of the Ethernet frame. Support for a match criteria may depend on H/W and/or filter direction as per below description. Match criterion is blocked if it is not supported by a specified frame-type or MAC filter sub-type. Nokia recommends not configuring a filter in a direction or on hardware where a match condition is not supported as this may lead to unwanted behavior.
- frame-type — The filter searches to match a specific type of frame format. For example, configuring frame-type ethernet_II will match only Ethernet-II frames.
- src-mac — The filter searches to match source MAC address frames. Operator can optionally configure a mask to be used in a match.
- dst-mac — The filter searches to match destination MAC address frames. Operator can optionally configure a mask to be used in a match.
- dot1p — The filter searches to match 802.1p frames. The operator can optionally configure a mask to be used in a match.
- etype — The filter searches to match Ethernet II frames. The Ethernet type field is a two-byte field used to identify the protocol carried by the Ethernet frame.
- ssap — The filter searches to match frames with a source access point on the network node designated in the source field of the packet. Operator can optionally configure a mask to be used in a match.
- dsap — The filter searches to match frames with a destination access point on the network node designated in the destination field of the packet. Operator can optionally configure a mask to be used in a match.
- snap-oui — The filter searches to match frames with the specified three-byte OUI field.
- snap-pid — The filter searches to match frames with the specified two-byte protocol ID that follows the three-byte OUI field.
- isid — The filter searches to match for the matching Ethernet frames with the 24-bit ISID value from the PBB I-TAG. This match criterion is mutually exclusive of all the other match criteria under a specific MAC filter policy and is applicable to MAC filters of type isid only. The resulting MAC filter can only be applied on a BVPLS SAP or PW in the egress direction.
- inner-tag/outer-tag — The filter searches to match Ethernet frames with the non-service delimiting tags, as described in the VID MAC Filters section. This match criterion is mutually exclusive with all other match criteria under a specific MAC filter policy and is applicable to MAC filters of type vid only.
4.1.1.4. IP Exception Filters
An NGE node supports IPv4 exception filters. For information on IP exception filters, refer to the “Router Encryption Exceptions using ACLs” section in the 7450 ESS, 7750 SR, 7950 XRS, and VSR Layer 3 Services Guide: IES and VPRN.
4.1.1.5. Filter Policy Actions
The actions are supported by ACL filter policies:
- drop — Allows operators to deny traffic to ingress or egress the system.
- IPv4 packet-length and IPv6 payload-length conditional drop — Traffic can be dropped based on IPv4 packet length or IPv6 payload length by specifying a packet length or payload length value or range within the drop filter action (the IPv6 payload length field does not account for the size of the fixed IP header, which is 40 bytes).This filter action is supported on ingress IPv4 and IPv6 filter policies only, if the filter is configured on an egress interface the packet-length or payload-length match condition is always true.The additional match condition is part of action evaluation, such as, after the packet is determined to match the entry based on other configured match criteria.Packets that match a filter policy entry match criteria and the drop packet-length-value or payload-length-value are dropped. Packets that match only the filter policy entry match criteria and do not match the drop packet-length-value or drop payload-length-value are forwarded with no further match in following filter entries.Interaction with cflowd, log and mirror: The filter entry supports cflowd and log regardless of the outcome of the rate limit while forwarded packets only are mirrored.
- IPv4 TTL and IPv6 hop limit conditional drop — Traffic can be dropped based on IPv4 TTL or IPv6 hop limit by specifying a ttl or hop limit value or range within the rate-limit filter action.This filter action is supported on ingress IPv4 and IPv6 filter policies only. If the filter is configured on an egress interface the packet-length or payload-length match condition is always true.The additional match condition is part of action evaluation, such as, after the packet is determined to match the entry based on other match criteria configured.Packets that match filter policy entry match criteria and the drop ttl or hop-limit-value are dropped. Packets that match only the filter policy entry match criteria and do not match the drop ttl or hop-limit-value are forwarded with no further match in following filter entries.Interaction with cflowd, log and mirror: The filter entry supports cflowd and log regardless of the outcome of the rate limit while forwarded packets only are mirrored.
- drop-extracted-traffic — Traffic extracted to the CPM can be dropped using ingress IPv4 and IPv6 filter policies based on filter match criteria. Any IP traffic extracted to the CPM is subject to this filter action, including routing protocols, snooped traffic, and TTL expired traffic.Packets that match the filter entry match criteria and extracted to the CPM are dropped. Packets that match only the filter entry match criteria and are not extracted to the CPM are forwarded with no further match in the subsequent filter entries.Cflowd, log, mirror, and statistics apply to all traffic matching the filter entry, regardless of drop or forward action.
- forward — Allows operators to permit traffic to ingress or egress the system and be subject to regular processing.
- rate-limit — This action allows operators to rate-limit traffic matching a filter entry match criteria using IPv4, IPv6, or MAC filter policies.If multiple interfaces (including LAG interfaces) use the same rate-limit filter policy on different FPs, then the system allocates a rate limiter resource for each FP; an independent rate limit applies to each FP.If multiple interfaces (including LAG interfaces) use the same rate-limit filter policy on the same FP, then the system allocates a single rate limiter resource to the FP; a common aggregate rate limit is applied to those interfaces.Note that traffic extracted to the CPM is not rate limited by an ingress rate-limit filter policy while any traffic generated by the router can be rate limited by an egress rate-limit filter policy.Interaction with cflowd, log and mirror: rate-limit filter policy entries can coexist with cflowd, log, and mirror regardless of the outcome of the rate limit.Interaction with QoS: Packets matching an ingress rate-limit filter policy entry bypass ingress QoS queuing or policing, and only the filter rate limit policer is applied. Packets matching an egress rate-limit filter policy bypass egress QoS policing, normal egress QoS queuing still applies.
- IPv4 packet-length and IPv6 payload-length rate limit — Traffic can be rate limited based on the IPv4 packet length and IPv6 payload length by specifying a packet-length value or payload-length value or range within the rate-limit filter action. The IPv6 payload-length field does not account for the size of the fixed IP header, which is 40 bytes.This filter action is supported on ingress IPv4 and IPv6 filter policies only and cannot be configured on egress access or network interfaces.This additional rate-limit condition is part of the filter entry action evaluation, it is not part of the filter entry match evaluation. It is performed after the packet is determined to match the entry based on the configured filter entry match criteria.Packets that match a filter policy’s entry match criteria and the rate-limit packet-length-value or rate-limit payload-length-value are rate limited. Packets that match only the filter policy’s entry match criteria and do not match the rate-limit packet-length-value or rate-limit payload-length-value are forwarded with no further match in subsequent filter entries.Cflowd, logging, and mirroring apply to all traffic matching the ACL entry regardless of the outcome of the rate limiter and regardless of the packet-length-value or payload-length-value.
- IPv4 TTL and IPv6 hop-limit rate limit — Traffic can be rate limited based on the IPv4 TTL or IPv6 hop-limit by specifying a TTL or hop limit value or range within the rate-limit filter action using ingress IPv4 or IPv6 filter policies.This additional rate limit condition is part of the filter entry action evaluation. It is not part of the filter entry match evaluation. The evaluation is performed after the packet is determined to match the entry based on the configured filter entry match criteria.The additional match condition is part of action evaluation (for example, after the packet is determined to match the entry based on other match criteria configured). Packets that match a filter policy entry match criteria and the rate-limit ttl or hop-limit value are rate limited. Packets that match only the filter policy entry match criteria and do not match the rate-limit ttl or hop-limit value are forwarded with no further matching in the subsequent filter entries.Cflowd, logging, and mirroring apply to all traffic matching the ACL entry regardless of the outcome of the rate-limit value and the ttl-value or hop-limit-value.
- forward “Policy-based Routing/Forwarding (PBR/PBF) action” — Allows operators to permit ingress traffic but change the regular routing/forwarding that a packet would be a subject to. The PBR/PBF is applicable to unicast traffic only. The following PBR/PBF actions are supported (See CLI section for command details):
- egress-pbr — Enabling egress-pbr activates a PBR action on egress, while disabling egress-pbr activates a PBR action on ingress (default).The following subset of the PBR actions (defined as follows) can be activated on egress: redirect-policy, next-hop router, and esi.Egress PBR is supported in IPv4 and IPv6 filter policies for ESM only. Unicast traffic that is subject to slow-path processing on ingress (for example, IPv4 packets with options or IPv6 packets with hop-by-hop extension header) will not match egress PBR entries. Filter logging, cflowd, and mirror source are mutually exclusive of configuring a filter entry with an egress PBR action. Configuring pbr-down-action-override, if supported with a specific PBR ingress action type, is also supported when the action is an egress PBR action. Processing defined by pbr-down-action-override does not apply if the action is deployed in the wrong direction. If a packet matches a filter PBR entry and the entry is not activated for the direction in which the filter is deployed, action forward is executed. Egress PBR cannot be enabled in system filters.
- esi — Forwards the incoming traffic using VXLAN tunnel resolved using EVPN MP BGP control plane to the first service chain function identified by ESI (Layer 2) or ESI/SF-IP (Layer 3). Supported with VPLS (Layer 2) and IES/VPRN (Layer 3) services. If the service function forwarding cannot be resolved, traffic matches an entry and action forward is executed.For VPLS, no cross-service PBF is supported; that is, the filter specifying ESI PBF entry must be deployed in the VPLS service where BGP EVPN control plane resolution takes place as configured for a specific ESI PBF action. The functionality is supported in filter policies deployed on ingress VPLS interfaces. BUM traffic that matches a filter entry with ESI PBF will be unicast forwarded to the VTEP:VNI resolved through PBF forwarding.For IES/VPRN, the outgoing R-VPLS interface can be in any VPRN service. The outgoing interface and VPRN service for BGP EVPN control plane resolution must again be configured as part of ESI PBR entry configuration. The functionality is supported in filter policies deployed on ingress IES/VPRN interfaces and in filter policies deployed on ingress and egress for ESM subscribers. Only unicast traffic is subject to ESI PBR; any other traffic matching a filter entry with Layer 3 ESI action will be subject to action forward.When deployed in unsupported direction, traffic matching a filter policy ESI PBR/PBF entry will be subject to action forward.
- lsp — Forwards the incoming traffic onto the specified LSP. Supports RSVP-TE LSPs (type static or dynamic only), MPLS-TP LSPs, or SR-TE LSPs. Supported for ingress IPv4/IPv6 filter policies and only deployed on IES SAPs or network interfaces. If the configured LSP is down, traffic matches the entry and action forward is executed.
- next-hop — Changes the IP destination address used in routing from the address in the packet to the address configured in this PBR action. The operator can configure whether the next-hop IP address must be direct (local subnet only) or indirect (any IP). This functionality is supported for ingress IPv4/IPv6 filter policies only, and is deployed on Layer 3 interfaces. If the configured next-hop is not reachable, traffic is dropped and a “ICMP destination unreachable” message is sent. If the indirect keyword is not specified but the IP address is a remote IP address, traffic will be dropped.
- interface — Forwards the incoming traffic onto the specified IPv4 interface. Supported for ingress IPv4 filter policies in global routing table instance. If the configured interface is down or not of the supported type, traffic is dropped.
- redirect-policy — Implements PBR next-hop or PBR next-hop router action with ability to select and prioritize multiple redirect targets and monitor the specified redirect targets so PBR action can be changed if the selected destination goes down. Supported for ingress IPv4 and IPv6 filter policies deployed on Layer 3 interfaces only. See section Redirect Policies for further details.
- remark dscp — Allows an operator to remark the DiffServ Code Points of packets matching filter policy entry criteria. Packets are remarked regardless of QoS-based in-/out-of- profile classification and QoS-based DSCP remarking is overridden. DSCP remarking is supported both as a main action and as an extended action. As a main action, this functionality applies to IPv4 and IPv6 filter policies of any scope and can only be applied at ingress on either access or network interfaces of Layer 3 services only. As an extended action, this functionality applies to IPv4 and IPv6 filter policies of any scope and can be applied at ingress on either access or network interfaces of Layer 3 services, or at egress on Layer 3 subscriber interfaces. The functionality requires IOM3 or above.
- router — Changes the routing instance a packet is routed in from the upcoming interface’s instance to the routing instance specified in the PBR action (supports both GRT and VPRN redirect). It is supported for ingress IPv4/IPv6 filter policies deployed on Layer 3 interfaces. The action can be combined with the next-hop action specifying direct/indirect IPv4/IPv6 next hop. Packets are dropped if they cannot be routed in the configured routing instance. For further details, see section “Traffic Leaking to GRT” in the 7450 ESS, 7750 SR, 7950 XRS, and VSR Layer 3 Services Guide: IES and VPRN.
- sap — Forwards the incoming traffic onto the specified VPLS SAP. Supported for ingress IPv4/IPv6 and MAC filter policies deployed in VPLS service. The SAP that the traffic is to egress on must be in the same VPLS service as the incoming interface. If the configured SAP is down, traffic is dropped.
- sdp — Forwards the incoming traffic onto the specified VPLS SDP. Supported for ingress IPv4/IPv6 and MAC filter policies deployed in VPLS service. The SDP that the traffic is to egress on must be in the same VPLS service as the incoming interface. If the configured SDP is down, traffic is dropped.
- vprn-target — Redirects the incoming traffic in a similar manner to combined next-hop and LSP redirection actions, but with greater control and slightly different behavior. This action is supported for both IPv4 and IPv6 filter policies and is applicable on ingress of access interfaces of IES/VPRN services. See Filter Policy Advanced Topics for further details.
- forward “isa action” — ISA processing actions allow operator to permit ingress traffic and send it for ISA processing as per specified ISA action. The following ISA actions are supported (see CLI section for command details):
- gtp-local-breakout — Forwards matching traffic to NAT instead of being GTP tunneled to the mobile operator’s PGW or GGSN. The action applies to GTP-subscriber-hosts. If filter is deployed on other entities, action forward is applied. Supported for IPv4 ingress filter policies only. If ISAs performing NAT are down, traffic is dropped.
- nat — Forwards matching traffic for NAT. Supported for IPv4/IPv6 filter policies for Layer 3 services in GRT or VPRN. If ISAs performing NAT are down, traffic is dropped. (see CLI for options)
- reassemble — Forwards matching packets to the reassembly function. Supported for IPv4 ingress filter policies only. If ISAs performing reassemble are down, traffic is dropped.
- tcp-mss-adjust — Forwards matching packets (TCP Syn) to an ISA BB Group for MSS adjustment. In addition to the IP filter, the operator also needs to configure the mss-adjust-group command under the Layer 3 service to specify the bb-group-id and the new segment-size.
- http-redirect — Implements the HTTP redirect captive portal. HTTP GET is forwarded to CPM card for captive portal processing by router. See the HTTP-redirect (Captive Portal) section for more information.
In addition to the above actions:
- An operator can select a default-action for a filter policy. The default action is executed on packets subjected to an active filter when none of the filter’s active entries matches the packet. By default, filter policies have default action set to drop but operator can select a default action to be forward instead.
- An operator can override default action applied to packets matching a PBR/PBF entry when the PBR/PBF target is down using pbr-down-action-override. Supported options are to drop the packet, forward the packet, or apply the same action as configured for the filter policy's default-action. The override is supported for the following PBR/PBF actions. For the last three actions, the override is supported whether in redundancy mode or not.
- forward esi (Layer 2 or Layer 3)
- forward sap
- forward sdp
- forward next-hop [indirect] router
Table 46 defines default behavior for packets matching a PBR/PBF filter entry when a target is down.Table 46: Default behavior when a PBR/PBF target is down
PBR/PBF action
Default behavior when down
forward esi (any type)
Forward
forward lsp
Forward
forward next-hop (any type)
Drop
forward redirect-policy
Forward when redirect policy is shutdown
forward redirect-policy
Forward when destination tests are enabled and the best destination is not reachable
forward redirect-policy
Drop when destination tests are not enabled and the best destination is not reachable
forward sap
Drop
forward sdp
Drop
forward router
Drop
forward vprn-target
Forward
4.1.1.6. Viewing Filter Policy Actions
A number of parameters determine the behavior of a packet after it has been matched to a defined criterion or set of criteria:
- the action configured by the user
- the context in which a filter policy is applied. For example, applying a filter policy in an unsupported context can result in simply forwarding the packet rather than applying the configured action.
- external factors, such as the reachability (according to a given test criteria) of a target
Because of this, SR OS provides the following commands that enable the user to capture this context globally and identify how a packet will be handled by the system:
- show>filter>ip
- show>filter>ipv6
- show>filter>mac
This section describes the key information displayed as part of the output for the show commands listed above, and explains how to interpret it.
From a configuration point of view, the show command output displays the main action (primary and secondary), as well as the extended action.
The “PBR Target Status” field shows the basic information that the system has of the target based on simple verification methods. This information is only shown for the filter entries which are configured in redundancy mode (that is, with both primary and secondary main actions configured), and for ESI redirections. Specifically, the target status in the case of redundancy depends on several factors; for example, on a match in the routing table for next-hop redirects, or on VXLAN tunnel resolution for ESI redirects.
The “Downloaded Action” field specifically describes the action that the system will perform on the packets that match the criterion (or criteria). This typically depends on the context in which the filter has been applied (whether it is supported or not), but in the case of redundancy, it also depends on the target status. For example, the downloaded action will be the secondary main action when the target associated to the primary action is down. In the nominal (for example, non-failure condition) case the “Downloaded Action” will reflect the behavior a packet will be subject to. However, in transient cases (for example, in the case of a failure) it may not be able to capture what will effectively happen to the packet.
The output also displays relevant information such as the default action when the target is down (see Table 46) as well as the overridden default action when pbr-down-action-override has been configured.
There are situations where, collectively, this information does not capture what will effectively happen to the packet throughout the system. To that end, the effective-action keyword of the show>filter>[ip | ipv6 | mac] commands enables advanced checks to be performed and accurate packet fates to be displayed.
The criteria for determining when a target is down. While there is little ambiguity on that aspect when the target is local to the system performing the steering action, ambiguity is much more prominent when the target is distant. Therefore, because the use of effective-action triggers advanced tests, a discrepancy is introduced compared to the action when effective-action keyword is not used. This will, for example, be the case for redundant actions.
4.1.1.7. Filter Policy Statistics
Filter policies support per-entry, packet/byte match statistics. The cumulative matched packet/Byte counters are available per ingress and per egress direction. Every packet arriving on an interface/service/subscriber using a filter policy increments ingress or egress (as applicable) matched packet/Byte count for a filter entry the packet matches (if any) on the line card the packet ingresses/egresses. For each policy, the counters for all entries are collected from all line cards, summarized and made available to an operator.
Starting with SR OS Release 11.0R4, filter policies applied on access interfaces are downloaded only when active and only to line cards that have interfaces associated with those filter policies. If a filter policy is not downloaded to any line card, the statistics show 0. If a filter policy is being removed from any of the line cards the policy is currently downloaded to (as result of association change or when a filter becomes inactive), the statistics for the filter are reset to 0. Downloading a filter policy to a new line card keeps incrementing existing statistics.
Starting with SR OS Release 13.0R4, filter policies support bulk requests of CPM cache for policy interface-created entries. The cache is periodically refreshed through a background collection of counters from hardware. The counters are also refreshed when the ACL entry corresponding to the cache entry has statistics read from hardware through any direct-read from hardware mechanism. If a cache entry represents an entry for an ACL filter policy not downloaded to any line cards, the cache returns values of 0. If a cache entry represents an ACL filter entry that was removed from a line card since the previous refresh, the current refresh will reload the cache with the most recent values from hardware. The cache has to be rebuilt on a High Availability (HA) switchover, accordingly initial statistics requests after an HA switchover may require reads from hardware.
Operational notes:
- Two consecutive bulk requests for one entry will return the same values if the cache has not been refreshed between the two requests. The refresh interval is platform/release dependent. Contact your Nokia representative for more information.
- The cache is currently used only for Open Flow statistics retrieval. See Hybrid OpenFlow Switch for more details.
- Conditional action match criteria filter entries for ttl, hop-limit, packet-length, and payload-length support logging and statistics when the condition is met, allowing visibility of filter matched and action executed. If the condition is not met, packets are not logged and statistics against the entry are not incremented.
4.1.1.8. Filter Policy Logging
SR OS supports logging of the information from the packets that match a specific filter policy. Logging is configurable per filter policy entry by specifying preconfigured filter log (config>filter>log). A filter log can be applied to ACL filters and CPM hardware filters. Operators can configure multiple filter logs and specify: memory allocated to a filter log destination, syslog ID for filter log destination, filter logging summarization, and wrap-around behavior.
Notes related to filter log summarization:
- The implementation of the feature applies to filter logs with destination syslog.
- Summarization logging is the collection and summarization of log messages for one specific log ID within a period of time.
- The summarization interval is 100 seconds.
- Upon activation of a summary, a mini-table with src/dst-address and count is created for each type (IPv4/IPv6/MAC).
- Every received log packet (due to filter match) is examined for source or destination address.
- If the log packet (source/destination address) matches a source/destination address entry in the mini-table, from a packet received previously, the summary counter of the matching address is incremented.
- If source or destination address of the log messages does not match an entry already present in the table, the source/destination address is stored in a free entry in the mini-table.
- In case the mini-table has no more free entries, only total counter is incremented.
- At expiry of the summarization interval, the mini-table for each type is flushed to the syslog destination.
Operational note:
- Conditional action match criteria filter entries for ttl, hop-limit, packet-length, and payload-length support logging and statistics when the condition is met, allowing visibility of filter matched and action executed. If the condition is not met, packets are not logged and statistics against the entry are not incremented.
4.1.1.9. Filter Policy cflowd Sampling
Filter policies can be used to control how cflowd sampling is performed on an IP interface. If an IP interface has cflowd sampling enabled, an operator can exclude some flows for interface sampling by configuring filter policy rules that match the flows and by disabling interface sampling as part of the filter policy entry configurations (interface-disable-sample). If an IP interface has cflowd sampling disabled, an operator can enable cflowd sampling on a subset of flows by configuring filter policy rules that match the flows and by enabling cflowd sampling as part of the filter policy entry configurations (filter-sample).
The above cflowd filter sampling behavior is exclusively driven by match criteria. The sampling logic applies regardless of whether an action was executed (including evaluation of conditional action match criteria, for example, packet-length or ttl).
4.1.1.10. Filter Policy Management
4.1.1.10.1. Modifying Existing Filter Policy
There are several ways to modify an existing filter policy. A filter policy can be modified through configuration change or can have entries populated through dynamic, policy-controlled dynamic interfaces; for example, RADIUS, OpenFlow, flowspec, or Gx. Although in general, SR OS ensures filter resources exist before a filter can be modified, because of the dynamic nature of the policy-controlled interfaces, a configuration that was accepted may not be applied in H/W due to lack of resources. When that happens, an error is raised.
A filter policy can be modified directly—by changing/adding/deleting the existing entry in that filter policy—or indirectly. Examples of indirect change to filter policy include changing embedded filter entry this policy embeds (see the Embedded Filters section) or changing redirect policy this filter policy uses.
Finally, a filter policy deployed on a specific interface can be changed by changing the policy the interface is associated with.
All of the above changes can be done in service. A filter policy that is associated with service/interface cannot be deleted unless all associations are removed first.
For a large (complex) filter policy change, it may take a few seconds to load and initiate the filter policy configuration. Filter policy changes are downloaded to line cards immediately; therefore, operators should use filter policy copy or transactional CLI to ensure partial policy change is not activated.
4.1.1.10.2. Filter Policy Copy and Renumbering
To assist operators in filter policy management, SR OS supports entry copy and entry renumbering operations.
Filter copy allows operators to perform bulk operations on filter policies by copying one filter’s entries to another filter. Either all entries or a specified entry of the source filter can be selected for copy. When entries are copied, entry order is preserved unless destination filter’s entry ID is selected (applicable to single-entry copy). The filter copy allows overwrite of the existing entries in the destination filter by specifying “overwrite” option during the copy command. Filter copy can be used, for example, when creating new policies from existing policies or when modifying an existing filter policy (an existing source policy is copied to a new destination policy, the new destination policy is modified, then the new destination policy is copied back to the source policy with overwrite specified).
Entry renumbering allows operators to change relative order of a filter policy entry by changing the entry ID. Entry renumbering can also be used to move two entries closer together or further apart, thereby creating additional entry space for new entries.
4.1.2. Filter Policy Advanced Topics
4.1.2.1. Match List for Filter Policies
Figure 26 shows an approach to implement logical OR on a list of matching criteria (IPv4 address prefixes in this example) in one or more filter policies prior to introduction of match list.
Figure 26: IOM/CPM Filter Policy Using Individual Address Prefixes
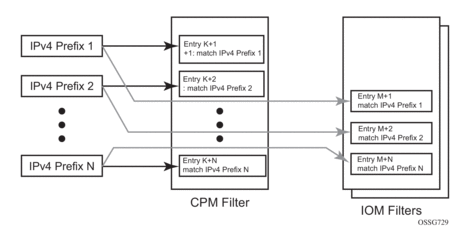
An operator has to create one entry for each address prefix to execute a common action. Each entry defines a match on a unique address prefix from the list plus any other additional match criteria and the common action. If the same set of address prefixes needs to be used in another IOM/line card, or CPM filter policy, an operator again needs to create one entry for each address prefix from the list in those filter policies. Same procedure applies (not shown above) if another action needs to be performed on the list of the addresses within the same filter policy (when, for example, specifying different additional match criteria). This process can introduce large operational overhead, especially when a list contains many elements or needs to be reused multiple times across one or more filter policies.
Match lists for CPM and IOM/FP filter policies eliminate the preceding operational complexity by simplifying the IOM/FP and CPM filter policy management on a list of match criteria. Instead of defining multiple filter entries in any specific filter, an operator can now group the same types of matching criteria into a single filter match list and use that list as a match criterion value, thus requiring only a single filter policy entry per each unique action. The same match list can be used in one or more IOM/line card filter policies as well as CPM filter policies.
The match lists further simplify management and deployment of the policy changes. A change in a match-list content is automatically propagated across all policies employing that list in their match criteria, therefore, only a single configuration change is required to trigger policy changes when a list is used by multiple entries in one or more filter policies.
Figure 27 depicts how the IOM/CPM filter policy changes with a filter match list usage (using IPv4 address prefix list in this example).
Figure 27: IOM/CPM Filter Policy Using an Address Prefix Match List
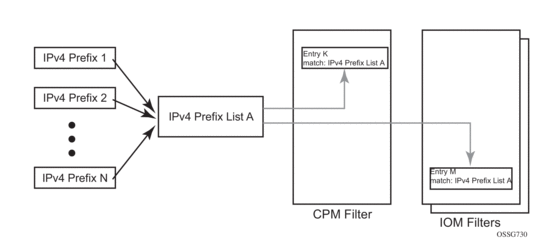
The hardware resource usage does not change whether filter match lists are used or whether operator creates multiple entries (each per one element of the list): however, a careful consideration must be given to how the lists are used to ensure only needed match permutations are created in a filter policy entry (especially when other matching criteria that are also lists or ranges are specified in the same entry). The system verifies that a new list element, for example, an IP address prefix, cannot be added to a specific list or a list cannot be used by a new filter policy unless resources exist in hardware to implement the required filter policy (ies) that reference that list. If that is not the case, addition of a new element to the list or use of the list by another policy will fail.
Some use cases, like those driven by dynamic policy changes, may result in acceptance of filter policy configuration changes that cannot be programmed in hardware because of the resource exhaustion. If that is the case, when attempting to program a filter entry that uses match lists, the operation will fail, the entry will not be programmed, and a notification of that failure will be provided to an operator.
Refer to the Software Release Notes for information about objects that can be grouped into a filter match list for FP and CPM filter policies.
4.1.2.1.1. Apply-Path — Auto-Generation of Prefix List Entries
Using the filter match-list apply-path commands, the router supports the auto-generation of IPv4 and IPv6 prefix list entries from the router configuration for BGP peers configured in the GRT or VPRN. This capability is often required to simplify the management of CPM or line card filters.
Using the filter match-list apply-path capability, the operator can:
- specify one or more regex expression matches against the SR OS configuration per list
- specify wildcard matches by specifying the regex wildcard match expression (“.*”)
- mix auto-generated entries with statically configured entries within a match list
Additional rules followed when using apply-path are:
- Operational and administrative states of a specific router configuration are ignored when auto-generating address prefixes.
- Duplicates are not removed when populated by different auto-generation matches and static configuration.
- A configuration will fail if auto-generation of an address prefix would result in filter policy resource exhaustion on a filter entry, system, or line card level.
4.1.2.2. Embedded Filters
When a large number of standard filter policies are configured in a system, a set of policies will often contain one or more common blocks of entries that define, for example, system-wide and/or service-wide security rules. Before introduction of the embedded filters, such common rules would have to be configured separately in each exclusive/template policy.
To simplify management of such common rules across multiple filter policies, the operator can use embedded filter policies. An embedded filter policy is a special type of a filter policy that cannot be deployed directly but instead is used to define a common filter policy rules that are then included in (embedded into) other filter policies in the system. Thanks to embedding, a common set of rules can now be defined and changed in a single place but deployed across multiple filter policies. The following main rules apply when embedding an embedded filter policy:
- An operator can explicitly define an offset at which to embed a specific embedded filter into a specific embedding filter—the embedded filter entry number X becomes an entry (X + offset) in the embedding filter.
- An exclusive/template filter policy may embed multiple embedded filter policies as long as the embedded entries do not overlap.
- A single embedded filter policy may be embedded in many exclusive/template filter policies.
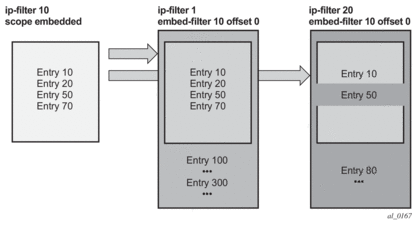
- When embedding an embedded filter, an operator may want to change or deactivate an embedded filter policy entry in the embedding filter, allowing for customization of the common embedded filter policy rules by the embedding filter. This can be achieved by either defining an entry in the embedding filter that will match ahead of the embedded filter entry or by overwriting the embedded filter entry in the embedding filter.For example: If embedded filter 99 has entry 20 that drops packets that match IP source address src_address, and filter 200 embeds filter 99 at offset 100, then to deactivate the embedded entry 20, an operator could define an entry 120 (embedded entry number 20 + offset 100) in filter policy 200 that has the same match criteria and has either:
- no action defined (this will deactivate the embedded entry and allow continued evaluation of filter policy 200)
- action forward defined (packets will match the new entry and will be forwarded instead of dropped, evaluation of filter policy 200 will stop)
- Any embedded policy rule edits are automatically applied to all filter policies that embed that embedded filter policy.
- The system verifies whether system and h/w resources exist when a new embedded filter policy is created, changed or embedded. If resources are not available, the configuration is rejected. In rare cases, filter policy resource check may pass but filter policy can still fail to load due to a resource exhaustion on a line card (for example when other filter policy entries are dynamically configured by applications like RADIUS in parallel). If that is the case, the embedded filter policy configured will be deactivated (configuration will be changed from activate to inactivate).
- An embedded filter is never embedded partially into an exclusive/template filter; that is, resources must exist to embed all embedded filter entries in a specific exclusive/template filter. Although a partial embedding into a single filter will not take place, an embedded filter may be embedded only in a subset of embedding filters (only those where there are sufficient resources available).
Figure 28 shows implementation of embedded filter policy using IPv4 ACL filter policy example with an embedded filter 10 being used to define common filter rules that are then embedded into filter 1 and 20 (with filter 20 overwriting rule at offset 50).
Figure 28: Embedded Filter Policy
| Note: Embedded filter policies are supported for line card IP(v4) and IPv6 filter policies only. |
4.1.2.3. System-level IPv4/IPv6 Line Card Filter Policy
A system filter policy allows the definition of a common set of policy rules that can then be activated within other exclusive/template filters. IPv4/IPv6 system filter policies supports all IPv4/IPv6 filter policy match rules and actions respectively but system policy entries cannot be the sources of mirroring.
System filter policy cannot be used directly; the active system policy is deployed by activating it within any IPv4 or IPv6 exclusive/template filter policy (chaining the system policy and a specific interface policy). When an IPv4/IPv6 filter policy is chained to the active IPv4/IPv6 system filter, system filter rules are evaluated first before any rules of the chaining filter are evaluated (i.e. chaining filter's rules are only matched against if no system filter match took place).
A system filter policy is intended mainly for system-level blacklisting rules, therefore it is recommended to use system policies with drop/forward actions. Other actions like, for example, PBR actions, or redirect to ISAs should not be used unless the system filter policy is activated only in filters used by services that support such action. The “nat” action is not supported and should not be configured. Failure to observe these restrictions can lead to unwanted behavior as system filter actions are not verified against the services the chaining filters are deployed for.
System filter policies can be populated using CLI/SNMP/Netconf management interfaces and Openflow policy interface. System filter policy entries cannot be populated using flowspec, RADIUS, or Gx.
System filter policy scale is identical to a corresponding IPv4 or IPv6 filter policy scale. System filter policy consumes single set of H/W resources on each line card as soon as it is activated, regardless of how many IPv4/IPv6 filters chain to that system policy. This optimizes resource allocation when multiple filter policies activate a specific system policy.
An example (IPv4) configuration is shown below:
4.1.2.4. Primary and Secondary Filter Policy Action for PBR/PBF Redundancy
In some deployments, operators may want to specify a backup PBR/PBF target if the primary target is down. SR OS allows the configuration of a primary action (config>filter>{ip-filter | ipv6-filter | mac-filter}>entry>action) and a secondary action (config>filter>{ip-filter | ipv6-filter | mac-filter}>entry>action secondary) as part of a single filter policy entry. The secondary action can only be configured if the primary action is configured.
For Layer 2 PBF redundancy, the operator can configure the following redundancy options:
- action forward sap AND action secondary forward sap
- action forward sdp AND action secondary forward sdp
- action forward sap AND action secondary forward sdp
- action forward sdp AND action secondary forward sap
For Layer 3 PBR redundancy, an operator can configure any of the following actions as a primary action and any (either same or different than primary) of the following as a secondary action. Furthermore, none of the parameters need to be the same between primary and secondary actions. Although the following commands refer to IPv4 in the ip-address parameter, they also apply to IPv6.
- forward next-hop ip-address router router-instance
- forward next-hop ip-address router service-name service-name
- forward next-hop indirect ip-address router router-instance
- forward next-hop indirect ip-address router service-name service-name
When primary and secondary actions are configured, PBR/PBF uses the primary action if its target is operationally up, or it uses the secondary action if the primary PBR/PBF target is operationally down. If both targets are down, the default action when the target is down (see Table 46), as per the primary action, is used, unless pbr-down-action-override is configured.
When PBR/PBF redundancy is configured, the operator can use sticky destination functionality for a redundant filter entry. When sticky destination is configured (config>filter>{ip-filter | ipv6-filter | mac-filter}>entry>sticky-dest), the functionality mimics that of sticky destination configured for redirect policies. To force a switchover from the secondary to the primary action when sticky destination is enabled and secondary action is selected, the operator can use the tools>perform>filter>{ip-filter | ipv6-filter | mac-filter}>entry>activate-primary-action command. Sticky destination can be configured even if no secondary action is configured.
The control plane monitors whether primary and secondary actions can be performed and programs forwarding filter policy to use either the primary or secondary action as required. More generally, the state of PBR/PBF targets is monitored in the following situations:
- when a secondary action is configured
- when sticky destination is configured
- when a pbr-down-action-override is configured
The show>filter>{ip-filter | ipv6-filter | mac-filter} [entry] command displays which redundant action is activated or downloaded, including when both PBR/PBF targets are down. The following example shows partial output of the command as applicable for PBF redundancy.
4.1.2.5. Extended Action for Performing Two Actions at a Time
In certain deployment scenarios, for example to realize service function chaining, operators may want to perform a second action in addition to a traffic steering action. SR OS allows this behavior by configuring an extended action for a main action. This functionality is supported for Layer 3 traffic steering (that is, PBR) and more specifically for the following main actions:
- forward esi (Layer 3 version)
- forward lsp
- forward next-hop [indirect] [router]
- forward next-hop interface
- forward redirect-policy
- forward router
- forward vprn-target
Furthermore, the capability to specify an extended action is also supported in the case of PBR redundancy, therefore for the following action:
- forward next-hop [indirect] router
The supported extended action is:
- remark dscp dscp-name
The extended action is available in the following contexts: config>filter>ip-filter>entry>action>extended-action and config>filter>ipv6-filter>entry>action>extended-action.
If the status of the target of the main action is tracked, which is the case, amongst others, for PBR/PBF redundancy, the extended action listed above will not be performed when the PBR target is down. Moreover, a filter policy containing an entry with the extended action remark dscp will be blocked in the following cases: if applied on ingress with the egress-pbr flag set, if applied on egress without the egress-pbr flag set. The latter case includes actions that are not supported on egress (and for which egress-pbr cannot be set).
4.1.2.6. Advanced VPRN Redirection
The vprn-target action is a resilient redirection capability which combines both data-path and control plane lookups to achieve the desired redirection. It allows for the following redirection models:
- redirection towards the default PE while selecting a specific LSP to use
- redirection towards an alternative PE while selecting or not a specific LSP to use. If a specific LSP is not selected, then the system will automatically select one based on the BGP next-hop tunnel resolution mechanism
- all of the above within any VPRN
When configuring this action, the user must specify the target BGP next-hop (bgp-nh) towards which the redirection should occur, as well as the routing context (router) in which the necessary lookups will be performed (to derive the service label).
The target BGP next-hop can be configured with any label allocation method (label per VRF, label per next-hop, label per prefix). These methods entail different forwarding behaviors; however, the steering node is not aware of the configuration of the target node. If the user does not specify an advertised route prefix (adv-prefix), the steering node will assume that label per VRF is used by the target node and will select the service label accordingly. If the target node is not operating according to the label per VRF method, the user must specify an appropriate route prefix for which a service label is advertised by the target node, keeping in mind the resulting forwarding behavior at the target node of the redirected packet. This specification will instruct the steering node to use that specific service label.
Be aware that the system will perform and exact match between the specified ip-address/mask (or ipv6-address/prefix-length) and the advertised route.
The user can specify an LSP (RSVP-TE, MPLS-TP, or SR-TE LSP) to use towards the BGP next-hop. If no LSP is specified, the system will automatically select one the same way it would have done when normally forwarding a packet towards the BGP next-hop.
| Note: While the system only performs the redirection when the traffic is effectively able to reach the target BGP next-hop, it does not verify whether the redirected packets will effectively reach their destination after that. |
This action is resilient in that it tracks events affecting the redirection at the service level and reacts to those events. As such, the system will perform the redirection as long as it can reach the target BGP next-hop using the proper service label. If the redirection cannot be performed (for example, if no LSP is available, the peer is down, or there is no more specific labeled route), the system will revert to normal forwarding. This can be overridden and configured to drop. A maximum of 8k of unique (3-tuple {bgp-nh, router, adv-prefix}) redirection targets can be tracked.
4.1.2.7. Destination MAC Rewrite When Deploying Policy-Based Forwarding
For Layer 2 Policy-Based Forwarding (PBF) redirect actions, a far-end router may discard redirected packets when the PBF changes the destination IP interface the packet arrives on. This happens when a far-end IP interface uses a different MAC address than the IP interface reachable via normal forwarding (for example, one of the routers does not support a configurable MAC address per IP interface). To avoid the discards, operators can deploy egress destination MAC rewrite functionality for VPLS SAPs (config>service>vpls>sap>egress>dest-mac-rewrite). Figure 29 shows a sample deployment.
Figure 29: Layer 2 Policy-Based Forwarding (PBF) redirect action
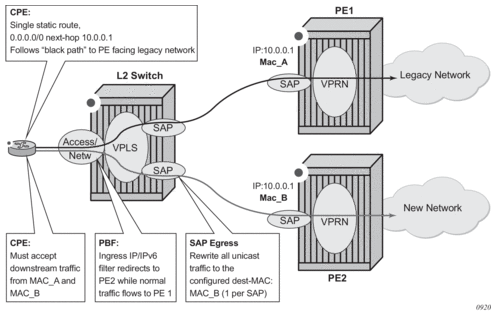
When enabled, all unicast packets have their destination MAC rewritten to operator-configured value on an Layer 2 switch VPLS SAP. Multicast and broadcast packets are unaffected. The feature:
- Is supported for regular and split-horizon group Ethernet SAPs in a regular VPLS Service
- Is expected to be deployed on a SAP that faces far-end IP interface (either a SAP that is the target of PBF action, as shown in Figure 29, or a VPLS SAP of a downstream Layer 2 switch that is connected to a far-end router—not shown).
- Applies to any unicast egress traffic including LI and mirror.
Restrictions:
- Is mutually exclusive with SAP MAC ingress and egress loopback feature: tools perform service id service-id loopback eth sap sap-id {ingress | egress} mac-swap ieee-address
4.1.2.8. Network-port VPRN Filter Policy
Network-port Layer 3 service-aware filter feature allows operators to deploy VPRN service aware ingress filtering on network ports. A single ingress filter of scope template can each be defined for IPv4 and for IPv6 against a VPRN service. The filter applies to all unicast traffic arriving on auto-bind and explicit-spoke network interfaces for that service. The network interface can be either Inter-AS, or Intra-AS. The filter does not apply to traffic arriving on access interfaces (SAP, spoke-sdp, network-ingress (CsC, rVPLS, eVPN).
The same filter can be used on access interfaces of the specific VPRN, can embed other filters (including OpenFlow), can be chained to a system filter, and can be used by other Layer 2 or Layer 3 services.
The filter is deployed on all line cards (chassis network mode D is required). There are no limitations related to filter match/action criteria or embedding. The filter is programmed on line cards against ILM entries for this service. All label-types are supported. If an ILM entry has a filter index programmed, that filter is used when the ILM is used in packet forwarding; otherwise, no filter is used on the service traffic.
Restrictions:
- Network port Layer 3 service-aware filters do not support flowspec and LI (cannot use filter inside LI infrastructure nor have LI sources within the VPRN filter).
4.1.2.9. ISID MAC Filters
ISID filters are a type of MAC filters that allows filtering based on the ISID values rather than Layer 2 criteria used by MAC filters of type "normal" or "vid". ISID filters can be deployed on iVPLS PBB SAPs and ePipe PBB SAPs in the following scenarios:
The MMRP usage of the MRP policy ensures automatically that traffic using Group BMAC is not flooded between domains. However, there could be small transitory periods when traffic originated from PBB BEB with unicast BMAC destination may be flooded in the BVPLS context as unknown unicast in the BVPLS context for both IVPLS and PBB Epipe. To restrict distribution of this traffic for local PBB services, ISID filters can be deployed. The MAC filter configured with ISID match criterion can be applied to the same interconnect endpoints (BVPLS SAP or PW) as the MRP policy to restrict the egress transmission of any type of frames that contains a local ISID. The ISID filters will be applied as required on a per B-SAP or B-PW basis, just in the egress direction.
The ISID match criteria are exclusive with any other criteria under mac-filter. A new mac-filter type attribute is defined to control the use of ISID match criteria and must be set to ISID to allow the use of ISID match criteria.
4.1.2.10. VID MAC Filters
VID filters are a type of MAC filters that extend the capability of current Ethernet ports with null or default SAP tag configuration to match and take action on VID tags. Service delimiting tags (for example, QinQ 1/1/1:10.20 or dot1q 1/1/1:10, where outer tag 10 and inner tags 20 are service delimiting) allow fine granularity control of frame operations based on the VID tag. Service delimiting tags are exact match and are stripped from the frame as shown in Figure 30. Exact match or service delimiting tags do not require VID filters. VID filters can only be used to match on frame tags that are after the service delimiting tags.
With VID filters, operators can choose to match VID tags for up to two tags on ingress, egress, or both.
- The outer tag is the first tag in the packet that is carried transparently through the service.
- The inner tag is the second tag in the packet that is carried transparently through the service.
VID filters add the capability to perform VID value filter policies on default tags (1/1/1:*, or 1/1/1:x.*, or 1/1/1/:*.0) or null tags (1/1/1, 1/1/1:0, or 1/1/1:x.0). The matching is based on the port configuration and the SAP configuration.
At ingress, the system looks for the two outer-most tags in the frame. If present, any service delimiting tags are removed and not visible to VID MAC filtering. For example:
- 1/1/1:x.y SAP has no tag left for VID MAC filter to match on (outer-tag and inner-tag = 0)
- 1/1/1:x.* SAP has potentially one tag in the * position for VID MAC filter to match on
- SAP such as 1/1/1, 1/1/1:*, or 1/1/1:*.* can have as many as two tags for VID MAC filter to match on
- For the remaining tags, the left (outer-most) tag is what is used as the outer tag in the MAC VID filter. The following tag is used as the inner tag in the filter. If any of these positions do not have tags, a value of 0 is used in the filter. At egress, the VID MAC filter is applied to the frame prior to adding the additional service tags.
In the industry, the QinQ tags are often referred to as the C-VID (customer VID) and S-VID (service VID). The terms outer tag and inner tag allow flexibility without having to refer to C-TAG and S-TAG explicitly. The position of inner and outer tags is relative to the port configuration and SAP configuration. Matching of tags is allowed for up to the first two tags on a frame because service delimiting tags may be 0, 1, or 2 tags.
The meaning of inner and outer has been designed to be consistent for egress and ingress when the number of non-service delimiting tags is consistent. Service 1 in Figure 30 shows a conversion from QinQ to a single dot1q example where there is one non-service delimiting tag on ingress and egress. Service 2 shows a symmetric example with two non-service delimiting tags (plus and additional tag for illustration) to two non-service delimiting tags on egress. Service 3 shows a single non-service delimiting tag on ingress and two tags with one non-service delimiting tag on ingress and egress.
SAP-ingress QoS setting allows for MAC-criteria type VID, which uses the VID filter matching capabilities of QoS and VID Filters (see the 7450 ESS, 7750 SR, 7950 XRS, and VSR Quality of Service Guide).
A VID filter entry can also be used as a debug or lawful intercept mirror source entry.
Figure 30: VID Filtering Examples
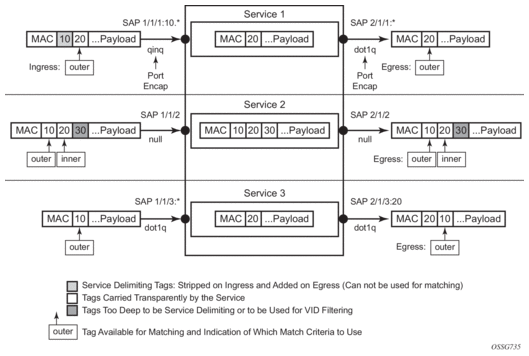
VID filters are available on Ethernet SAPs for Epipe, VPLS, or I-VPLS including eth-tunnel and eth-ring services.
4.1.2.10.1. Arbitrary Bit Matching of VID Filters
In addition to matching an exact value, a VID filter mask allows masking any set of bits. The masking operation is ((value and vid-mask) = = (tag and vid-mask)). For example: A value of 6 and a mask of 7 would match all VIDs with the lower 3 bits set to 6. VID filters allow explicit matching of VIDs and matching of any bit pattern within the VID tag.
When using VID filters on SAPs, only VID filters are allowed on this SAP. Filters of type normal and ISID are not allowed.
An additional check for the “0” VID tag may be required when using certain wild card operations. For example, frames with no tags on null encapsulated ports will match a value of 0 in outer tag and inner tag because there are no tags in the frame for matching. If a zero tag is possible but not wanted, it can be explicitly filtered using exact match on “0” prior to testing other bits for “0”.
config>system>ethernet>new-qinq-untagged-sap is a special QinQ function for single tagged QinQ frames with a null second tag. Using this in combination with VID filters is not recommended. The outer tag is the only tag available for filtering on egress for frames arriving from MPLS SDPs or from PBB services, even though additional tags may be carried transparently.
4.1.2.10.2. Port Group Configuration Example
Figure 31: Port Groups
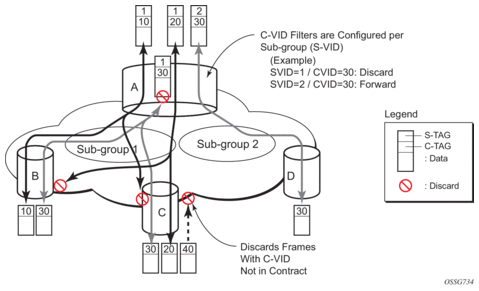
Figure 31 shows a customer use example where some VLANs are prevented from ingressing or egressing certain ports. In the example, port A sap 1/1/1:1.* would have a filter as shown below while port A sap 1/1/1:2.* would not.:
4.1.2.11. IP Exception Filters
IP exception filters scan all outbound traffic entering a Network Group Encryption (NGE) domain and allow packets that match the exception filter criteria to transit the NGE domain unencrypted.
The VSR supports IPv4 exception filters. For information on IP exception filters, refer to the “Router Encryption Exceptions using ACLs” section in the 7450 ESS, 7750 SR, 7950 XRS, and VSR Layer 3 Services Guide: IES and VPRN.
The most basic IP exception filter policy must have the following:
- an exception filter policy ID
- scope, either exclusive or template
- at least one filter entry with a specified matching criteria
4.1.2.12. Redirect Policies
SR OS-based routers support configuring of IPv4 and IPv6 redirect policies. Redirect policies allow specifying multiple redirect target destinations and defining status check test methods used to validate the ability for a destination to receive redirected traffic. This destination monitoring allows routers to react to target destination failures. To specify an IPv4 redirect policy, define all destinations to be IPv4. To specify an IPv6 redirect policy, define all destinations to be IPv6. IPv4 redirect policies can only be deployed in IPv4 filter policies. IPv6 redirect policy can only be deployed in IPv6 filter policies.
Redirect policies support the following destination tests:
- ping test – with configurable interval, drop-count, and time-out
- url-test – with configurable URL, interval, drop-count, timeout, and configurable action (disable destination, lower or raise priority) based upon return error code
- snmp-test – with configurable OID and Community strings, interval, drop-count, timeout, and configurable action (disable destination, lower or raise priority) based upon SNMP return value.
- unicast-rt-test – unicast routing reachability, supported only when router instance is configured for a specific redirect policy. The test yields true if the route to the specified destination exists in RTM for the configured router instance.
Each destination is assigned an initial or base priority describing this destination’s relative importance within the policy. The destination with the highest priority value is selected as most-preferred destination and programmed on line cards in filter policies using this redirect policy as an action. Only destinations that are not disabled by the programmed test (if configured) are considered when selecting the most-preferred destination.
In some deployments, it may not be necessary to switch from a currently active, most-preferred redirect-policy destination when a new more-preferred destination becomes available. To support such deployments, operators can enable the sticky destination functionality (config>filter>redirect-policy>sticky-dest). When enabled, the currently active destination remains active unless it goes down or an operator forces the switch using the tools>perform>filter>redirect-policy>activate-best-dest command. An optional sticky destination hold-time-up is available to delay programming the sticky destination in the redirect policy (transition from action forward to PBR action to the most-preferred destination). When the timer is enabled, the first destination that comes up will not be programmed and instead the timer is started. Once the timer expires, the most-preferred destination at that time will be programmed (which may be a different destination from the one that started the timer). Note the following:
- When the manual switchover to most-preferred destination is executed as described above, the hold-time-up is stopped.
- When the timer value is changed, the new value takes immediate effect and the timer is restarted with the new value (or expired if no-hold-time-up is configured).
| Note: The unicast-rt-test command will fail when performed in the context of a VPRN routing instance when the destination is routable only through grt-leak functionality. ping-test is recommended in such cases. |
Feature restrictions:
- Redirect policy is supported for ingress IPv4 and IPv6 filter policies only.
- SNMP and URL tests are not supported for IPv6.
- Different platforms support different scale for redirect policies. Contact your local Nokia representative to ensure the planned deployment does not exceed recommended scale.
4.1.2.12.1. Router Instance Support for Redirect Policies
There are two modes of deploying redirect policies on VPRN interfaces. The functionality supported depends on the configuration of the redirect-policy router option with config>filter>redirect-policy>router:
- Redirect policy with router option enabled (recommended):
- When a PBR destination is up, the PBR lookup is performed in the redirect policy's configured routing instance. When that instance differs from the incoming interface where the filter policy using the specific redirect policy is deployed, the PBR action is equivalent to forward next-hop router filter policy action.
- When all PBR destinations are down (or a hardware does not support action router), action forward is programmed and the PBR lookup is performed in the routing instance of the incoming interface where the filter policy using the specific redirect policy is deployed.
- Any destination tests configured are executed in the routing context specified by the redirect policy.
- Changing router configuration for a redirect policy brings all destinations with a test configured down. The destinations are brought up once the test confirms reachability based on the new redirect policy router configuration.
- Redirect policy without router option disabled (no router) or with router options not supported (legacy):
- When a PBR destination is up, the PBR lookup is performed in the routing instance of the incoming interface where the filter policy using the specific redirect policy is deployed.
- When all PBR destinations are down, action forward is programmed and the PBR lookup is performed in the routing instance of the incoming interface where the filter policy using the specific redirect policy is deployed.
- Any destination tests configured are always executed in the "Base" router instance regardless of the router instance of the incoming interface where the filter policy using the specific redirect policy is deployed.
Restrictions:
- Only unicast-rt-test and ping-test are supported when the router option is enabled.
4.1.2.13. HTTP-redirect (Captive Portal)
Web redirection policies can be configured on SR OSs/switches. The http redirection action can block a customer’s request from an intended recipient and force the customer to connect to the service’s portal server. 255 unique entries with http-redirect are allowed.
4.1.2.13.1. Traffic Flow
The following example provides a brief scenario of a customer connection with web redirection.
- The customer gets an IP address using DHCP (if the customer is trying to set a static IP he will be blocked by the anti-spoofing filter).
- The customer tries to connect to a website.
- The router intercepts the HTTP GET request and blocks it from the network
- The router then sends the customer an HTTP 302 (service temporarily unavailable/moved). The target URL should then include the customer’s IP and MAC addresses as part of the portal’s URL.
- The customer’s web browser will then close the original connection and open a new connection to the web portal.
- The web portal updates the ACL (directly or through SSC) to remove the redirection policy.
- The customer connects to the original site.
Figure 32: Web Redirect Traffic Flow
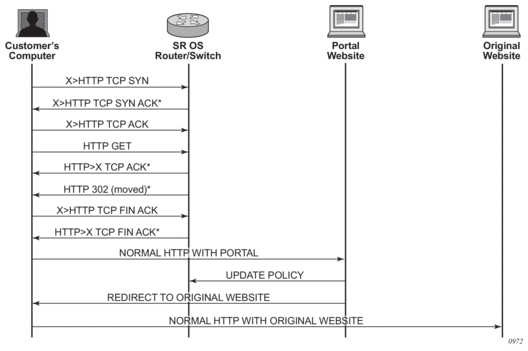
Starred entries (*) are items the router performs masquerading as the destination, regardless of the destination IP address or type of service.
The following displays information that can optionally be added as variables in the portal URL (http-redirect url):
- $IP – The customer’s IP address.
- $MAC – The customer’s MAC address.
- $URL – The original requested URL.
- $SAP – The customer’s SAP.
- $SUB – The customer’s subscriber identification string”.
- $CID — A string that represents the circuit-id or interface-id of the subscriber host (hexadecimal format).
- $RID — A string that represents the remote-id of the subscriber host (hexadecimal format).
- $SAPDESC – A configurable string that represents the configured SAP description.
The subscriber identification string is available only when used with subscriber management. Refer to the subscriber management section of the 7450 ESS, 7750 SR, and VSR Triple Play Service Delivery Architecture Guide and the 7450 ESS, 7750 SR, 7950 XRS, and VSR Router Configuration Guide.
Since most web sites are accessed using the domain name the router allows either DNS queries or responds to DNS with the portal’s IP address.
4.1.2.14. Filter Policies and Dynamic Policy-Driven Interfaces
In addition to configuration interfaces like CLI/SNMP, filter policies can be created and modified by dynamic policy-driven interfaces, such as BGP flowspec, OpenFlow, RADIUS, or XMPP-Python.
For BGP flowspec, routes are learned by a routing instance, and the system auto-creates an embedded filter to contain the rules derived from these routes. The maximum number of rules in the embedded filter of each routing instance can be controlled through configuration. The embedded filter containing the flowspec rules of a routing instance can be inserted into any configured exclusive or template-scope IPv4/IPv6 filter, and the embedding is activated if:
- the filter is applied to the ingress context of an IP interface that supports flowspec
- the IP interfaces to which the filter is applied all belong to the same routing instance, and that routing instance is the one associated with the flowspec routes
The insertion point of the flowspec rules in each embedding filter policy is controlled through offset configuration. For more information, see the BGP flowspec section of the 7450 ESS, 7750 SR, 7950 XRS, and VSR Unicast Routing Protocols Guide.
For RADIUS, operator can assign filter policies to a subscriber, and populate filter policies used by the subscriber within a preconfigured block reserved for RADIUS filter entries. See the 7450 ESS, 7750 SR, and VSR Triple Play Service Delivery Architecture Guide and filter RADIUS-related commands for more details.
VSD filters are created dynamically via XMPP and managed via Python script so rules can be inserted into or removed from the correct VSD template or embedded filters. XMPP messages received by the 7750 SR are passed transparently to the Python module to generate the appropriate CLI. More information about VSD filter provisioning, automation, and Python scripting details are in the 7450 ESS, 7750 SR, 7950 XRS, and VSR Layer 2 Services and EVPN Guide: VLL, VPLS, PBB, and EVPN.
For OpenFlow, embedded filter infrastructure is used to inject OpenFlow rules into an existing filter policy. See Hybrid OpenFlow Switch for more details.
Policy-controlled auto-created filters are re-created on system reboot. Policy-controlled filter-entries are lost on system reboot and need to be reprogrammed.
4.1.2.15. Filter Policy-based ESM Service Chaining
In some deployments, operators may select to redirect ESM subscribers to Value Added Services (VAS). Various deployment models can be used but often subscribers are assigned to a specific residential tier-of-service, which also defines the VAS available to subscribers of the specific tier. The subscribers are redirected to VAS based on tier-of-service rules but such an approach can be hard to manage when many VAS services/tiers of service are desired. Often the only way to identify a subscriber’s traffic with a specific tier-of-service is to preallocate IP/IPv6 address pools to a specific service tier and use those addresses in VAS PBR match criteria. This creates an application-services to network infrastructure dependency that can be hard to overcome, especially if fast and flexible application service delivery is desired.
Filter policy-based ESM service chaining removes ESM VAS steering to network infrastructure inter-dependency. An operator can configure per tier of service or per individual VAS service upstream and downstream service chaining rules without a need to define subscriber or tier-of-service match conditions. Figure 33 shows a possible ACL model (embedded filters are used for VAS service chaining rules).
On the left in Figure 33, the per-tier-of-service ACL model is depicted. Each tier of service (Gold or Silver) has a dedicated embedded VAS filter (“Gold VAS”, “Silver VAS”) that contains all steering rules for all service chains applicable to the specific tier. Each VAS filter is then embedded by the ACL filter used by a specific tier. A subscriber is subject to VAS service chain rules based on the per-tier ACL assigned to that subscriber (for example, via RADIUS). If a new VAS rule needs to be added, an operator must program that rule in all applicable tiers. Upstream and downstream rules can be configured in a single filter (as shown) or can use dedicated ingress and egress filters.
On the right in Figure 33, the per-VAS-service ACL model is depicted. Each VAS has a dedicated embedded filter (“VAS 1”, “VAS 2”, “VAS 3”) that contains all steering rules for all service chains applicable to that VAS service. A tier of service is then created by embedding multiple VAS-specific filters: Gold: VAS 1, VAS 2, VAS 3; Silver: VAS 1 and VAS 3. A subscriber is subject to VAS service chain rules based on the per-tier ACL assigned to that subscriber. If a new VAS rule needs to be added, an operator needs to program that rule in a single VAS-specific filter only. Again, upstream and downstream rules can be configured in a single filter (as shown) or can use dedicated ingress and egress filters.
Figure 33: ACL filter modeling for ESM Service Chaining
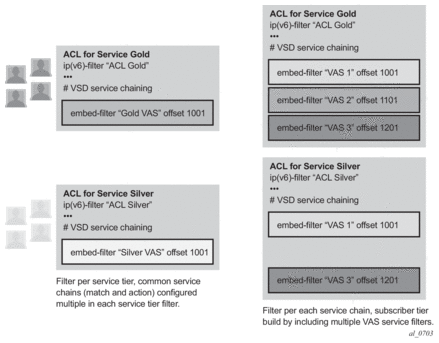
Figure 34 shows upstream VAS service chaining steering using filter policies. Upstream subscriber traffic entering Res-GW is subject to the subscriber's ingress ACL filter assigned to that subscriber by a policy server. If the ACL contains VAS steering rules, the VAS-rule-matching subscriber traffic is steered for VAS processing over a dedicated to-from-access VAS interface in the same or a different routing instance. After the VAS processing, the upstream traffic can be returned to Res-GW by a to-from-network interface (shown in Figure 34) or can be injected to WAN to be routed toward the final destination (not shown).
Figure 34: Upstream ESM ACL-policy based service chaining
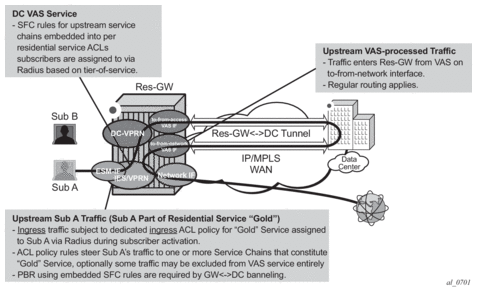
Figure 35 shows downstream VAS service chaining steering using filter policies. Downstream subscriber traffic entering Res-GW is forwarded to a subscriber-facing line card. On that card, the traffic is subject to the subscriber's egress ACL filter policy processing assigned to that subscriber by a policy server. If the ACL contains VAS steering rules, the VAS rule-matching subscriber's traffic is steered for VAS processing over a dedicated to-from-network VAS interface (in the same or a different routing instance). After the VAS processing, the downstream traffic must be returned to Res-GW via a “to-from-network” interface (shown in Figure 35) to ensure the traffic is not redirected to VAS again when the subscriber-facing line card processes that traffic.
Figure 35: Downstream ESM ACL-policy based service chaining
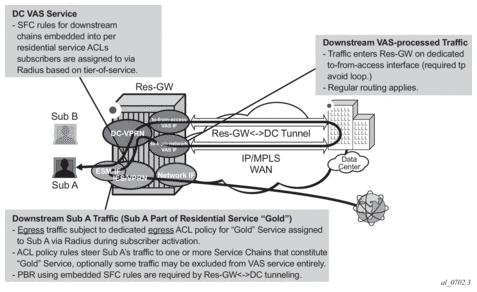
Ensuring the correct settings for the VAS interface type, for upstream and downstream traffic redirected to a VAS and returned after VAS processing, is critical for achieving loop-free network connectivity for VAS services. The available configuration options (config>service>vprn>if>vas-if-type, config>service>ies>if>vas-if-type and config>router>if>vas-if-type) are described below:
- deployments that use two separate interfaces for VAS connectivity (recommended, and required if local subscriber-to-subscriber VAS traffic support is required)
- to-from-access
- upstream traffic arriving from subscribers over access interfaces must be redirected to a VAS PBR target reachable over this interface for upstream VAS processing
- downstream traffic destined for subscribers after VAS processing must arrive on this interface, so that the traffic is subject to regular routing but is not subject to Application Assurance diversion, nor to egress subscriber PBR
- the interface must not be used for downstream pre-VAS traffic; otherwise, routing loops will occur
- to-from-network
- downstream traffic destined for subscribers arriving from network interfaces must be redirected to a VAS PBR target reachable over this interface for downstream VAS processing
- upstream traffic after VAS processing, if returned to the router, must arrive on this interface so that regular routing can be applied
- deployments that use a single interface for VAS connectivity (optional, no local subscriber-to-subscriber VAS traffic support)
- to-from-both
- both upstream traffic arriving from access interfaces and downstream traffic arriving from the network are redirected to a PBR target reachable over this interface for upstream/downstream VAS processing
- after VAS processing, traffic must arrive on this interface (optional for upstream), so that the traffic is subject to regular routing but is not subject to AA diversion, nor to egress subscriber PBR
- the interface must be used for downstream pre-VAS traffic; otherwise, routing loops will occur
The ESM filter policy-based service chaining allows operators to do the following:
- Steer upstream and downstream traffic per-subscriber with full ACL-flow-defined granularity without the need to specify match conditions that identify subscriber or tier-of-service
- Steer both upstream and downstream traffic on a single Res-GW
- Flexibly assign subscribers to tier-of-service by changing the ACL filter policy a specific subscriber uses
- Flexibly add new services to a subscriber or tier-of-service by adding the subscriber-independent filter rules required to achieve steering
- Achieve isolation of VAS steering from other ACL functions like security through the use of embedded filters
- Deploy integrated Application Assurance (AA) as part of a VAS service chain—both upstream and downstream traffic is processed by AA before a VAS redirect
- Select whether to use IP-Src/IP-Dst address hash or IP-Src/IP-Dst address plus TCP/UDP port hash when LAG/ECMP connectivity to DC is used. Layer 4 inputs are not used in hash with IPv6 packets with extension headers present.
ESM filter policy-based traffic steering supports the following:
- IPv4 and IPv6 steering of unicast traffic using IPv4 and IPv6 ACLs
- action forward redirect-policy or action forward next-hop router for IP steering with TCAM-based load-balancing, fail-to-wire, and sticky destination
- action forward esi sf-ip vas-interface router for an integrated service chaining solution
Operational notes:
- Downstream traffic steered toward a VAS on the subscriber-facing IOM is reclassified (FC and profile) based on the subscriber egress QoS policy, and is queued toward the VAS based on the network egress QoS configuration. Packets sent toward VAS will not have DSCP remarked (since they are not yet forwarded to a subscriber). DSCP remarking based on subscriber's egress QoS profile will only apply to traffic ultimately forwarded to the subscriber (after VAS or not subject to VAS).
- If mirroring of subscriber traffic is configured using ACL entry/subscriber/SAP/port mirror, the mirroring will apply to traffic ultimately forwarded to subscriber (after VAS or not subject to VAS). Traffic that is being redirected to VAS cannot be mirrored using an ACL filter implementing PBR action (the same egress ACL filter entry being a mirror source and specifying egress PBR action is not supported).
- Use dedicated ingress and egress filter policies to prevent accidental match of an ingress PBR entry on egress, and vice-versa, that will result in forwarding/dropping of traffic matching the entry (based on the filter's default action configuration).
Restrictions:
- This feature is not supported with HSMDAs on subscriber ingress.
- This feature is not supported when the traffic is subject to non-AA ISA on Res-GW.
- Traffic that matches an egress filter entry with an egress PBR action cannot be mirrored, cannot be sampled using cflowd, and cannot be logged using filter logging while being redirected to VAS on a sub-facing line card.
- This feature is not supported with LAC/LNS ESM (PPPoE subscriber traffic encapsulated into or de-encapsulated from L2TP tunnels).
- This feature is not supported for system filter policies.
4.1.2.16. Policy-Based Forwarding for Deep Packet Inspection in VPLS
The purpose policy-based forwarding is to capture traffic from a customer and perform a deep packet inspection (DPI) and forward traffic, if allowed, by the DPI.
In the following example, the split horizon groups are used to prevent flooding of traffic. Traffic from customers enter at SAP 1/1/5:5. Due to the mac-filter 100 that is applied on ingress, all traffic with dot1p 07 marking will be forwarded to SAP 1/1/22:1, which is the DPI.
DPI performs packet inspection/modification and either drops the traffic or forwards the traffic back into the box through SAP 1/1/21:1. Traffic will then be sent to spoke-sdp 3:5.
SAP 1/1/23:5 is configured to see if the VPLS service is flooding all the traffic. If flooding is performed by the router then traffic would also be sent to SAP 1/1/23:5 (which it should not).
Figure 36 shows an example to configure policy-based forwarding for deep packet inspection on a VPLS service. For information about configuring services, refer to the 7450 ESS, 7750 SR, 7950 XRS, and VSR Layer 2 Services and EVPN Guide: VLL, VPLS, PBB, and EVPN.
Figure 36: Policy-Based Forwarding for Deep Packet Inspection
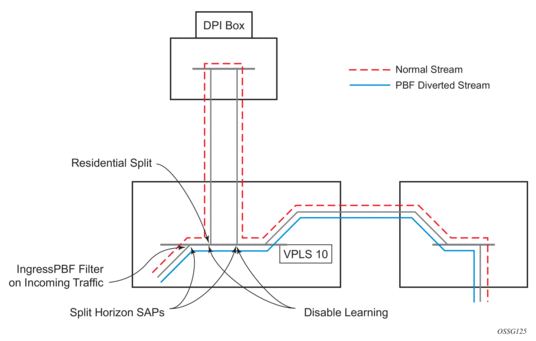
The following displays a VPLS service configuration with DPI example:
The following displays a MAC filter configuration example:
The following displays the MAC filter added to the VPLS service configuration: