2. Mirror Services
2.1. Service Mirroring
When troubleshooting complex operational problems, customer packets can be examined as they traverse the network. Nokia’s service mirroring provides the capability to mirror customer packets to allow for trouble shooting and offline analysis. One way to accomplish this is with an overlay of network analyzers established at multiple PoPs, together with skilled technicians to operate them to decode the data provided. This method of traffic mirroring often requires setting up complex filters in multiple switches and/or routers. These, at best, are only able to mirror from one port to another on the same device.
Nokia’s service mirroring extends and integrates these capabilities into the network and provides significant operational benefits. Each router can mirror packets from a specific service to any destination point in the network, regardless of interface type or speed.
This capability also extends beyond troubleshooting services. Telephone companies have the ability to obtain itemized calling records and wire-taps where legally required by investigating authorities. The process can be very complex and costly to carry out on data networks. Service mirroring greatly simplifies these tasks, as well as reduces costs through centralization of analysis tools and skilled technicians.
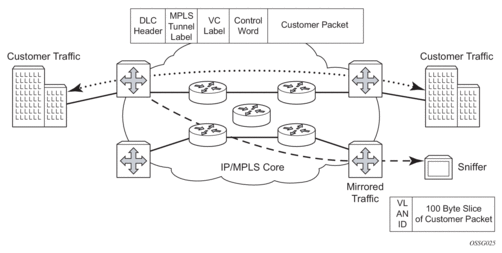
Nokia routers support service-based mirroring. While some Layer 3 switches and routers can mirror on a per-port basis within the device, Nokia routers can mirror on an n-to-1 unidirectional service basis and re-encapsulate the mirrored data for transport through the core network to another location, using either IP or MPLS tunneling as required (Figure 1).
Original packets are forwarded while a copy is sent out the mirrored port to the mirroring (destination) port. Service mirroring allows an operator to see the actual traffic on a customer’s service with a sniffer sitting in a central location. In many cases, this reduces the need for a separate, costly overlay sniffer network.
The mirrored frame size that is to be transmitted to the mirror destination can be explicitly configured by using slicing features. This enables mirroring only the parts needed for analysis. For example, only the headers can be copied for analysis, protecting the integrity and security of customer data, or conversely, copying the full packet, including customer data.
Figure 1: Service Mirroring
2.2. Mirror Implementation
Mirroring can be implemented on service access points (SAPs) or ingress network interfaces. The Flexible Fast Path processing complexes preserve the original packet throughout the forwarding and mirroring process, making any necessary packet changes, such as adding encapsulation, on a separate copy.
Nokia’s implementation of packet mirroring is based on the following assumptions:
- Ingress and egress packets are mirrored as they appear on the wire. This is important for troubleshooting encapsulation and protocol issues.
- When mirroring at ingress, the Flexible Fast Path network processor array (NPA) sends an exact copy of the original ingress packet to the mirror destination while normal forwarding proceeds on the original packet.
- When mirroring is at egress, the system performs normal packet handling on the egress packet, encapsulating it for the destination interface. A copy of the forwarded packet is forwarded to the mirror destination. Because the mirror copy of the packet is created before egress queuing, the mirrored packet stream may include copies of packets that are discarded in egress queues, such as during congestion or rate limiting.
- Mirroring supports tunnel destinations.
- Remote destinations are reached by encapsulating the ingress or egress packet within an SDP, like the traffic for distributed VPN connectivity services. At the remote destination, the tunnel encapsulation is removed and the packet is forwarded out a local SAP.
2.2.1. Mirror Source and Destinations
Mirror sources and destinations have the following characteristics:
- They can be on the same SR OS (local) or on two different routers (remote).
- Mirror destinations can terminate on egress virtual ports which allows multiple mirror destinations to send to the same packet decode device, delimited by IEEE 802.1Q (referred to as Dot1q) tags. This is helpful when troubleshooting a multi-port issue within the network.When multiple mirror destinations terminate on the same egress port, the individual dot1q tags can provide a DTE/DCE separation between the mirror sources.
- Packets ingressing a port can have a mirror destination separate from packets egressing another or the same port (the ports can be on separate nodes).
- Multiple mirror destinations are supported (local and/or remote) on a single chassis.
- The operational state of a mirror destination depends on the state of all the outputs of the mirror. The mirror destination will go operationally down if all the outputs are down (for example, all mirror-dest>sap and mirror-dest>spoke-sdp objects are down, and all gateways configured under mirror-dest>encap do not have a known route by which they can be reached). The state of a mirror destination does not depend on inputs such as SDPs configured under mirror-dest>remote-source, debug>mirror-source entries, or config>li>li-source entries. Some examples of outputs include mirror-dest>sap and mirror-dest>spoke-sdp.
- Both config>mirror-source and debug>mirror-source can reference the same source for mirroring (for example, sap 1/1/1). Instances of config will always take precedence over debug when referencing the same source.
2.2.1.1. Local and Remote Mirroring
Mirrored frames can be copied and sent to a specific local destination or service on the router (local mirroring) or copies can be encapsulated and sent to a different router (remote mirroring). This functionality allows network operators to centralize not only network analyzer (sniffer) resources, but also the technical staff who operate them.
The router allows multiple concurrent mirroring sessions so traffic from more than one ingress mirror source can be mirrored to the same or different egress mirror destinations.
Remote mirroring uses a service distribution path (SDP) which acts as a logical way of directing traffic from one router to another through a uni-directional (one-way) service tunnel. The SDP terminates at the far-end router which directs packets to the correct destination on that device.
The SDP configuration from the mirrored device to a far-end router requires a return path SDP from the far-end router back to the mirrored router. Each device must have an SDP defined for every remote router to which it wants to provide mirroring services. SDPs must be created first, before services can be configured.
2.2.1.2. Slicing
A further service mirroring refinement is “slicing” which copies a specified packet size of each frame. This is useful to monitor network usage without having to copy the actual data. Slicing enables mirroring larger frames than the destination packet decode equipment can handle. It also allows conservation of mirroring resources by limiting the size of the stream of packet through the router and the core network.
When a mirror slice-size is defined, a threshold that truncates a mirrored frame to a specific size is created. For example, if the value of 256 bytes is defined, up to the first 256 bytes of the frame are transmitted to the mirror destination. The original frame is not affected by the truncation. Mirrored frames, most likely, will grow larger as encapsulations are added when packets are transmitted through the network core or out the mirror destination SAP to the packet/protocol decode equipment. Note that slice-size is not supported by CEM encap-types or IP-mirroring (CEM encap-types applies to the 7750 SR and 7950 XRS only).
The transmission of a sliced or non-sliced frame is also dependent on the mirror destination SDP path MTU and/or the mirror destination SAP physical MTU. Packets that require a larger MTU than the mirroring destination supports are discarded if the defined slice size does not truncate the packet to an acceptable size.
2.2.2. Mirroring Performance
Replication of mirrored packets can, typically, affect performance and should be used carefully. Nokia routers minimize the impact of mirroring on performance by taking advantage of its distributed Flexible Fast Path technology. Flexible Fast Path forwarding allows efficient mirror service scaling and, at the same time, allows a large amount of data to be mirrored with minimal performance impact. When a mirror destination is configured, the packet slice option can truncate mirrored packets to the destination, which minimizes replication and tunneling overhead.
2.2.3. Mirroring Configuration
Mirroring can be performed based on the following criteria:
Configuring mirroring is similar to creating a uni-direction service. Mirroring requires the configuration of:
- Mirror source — The traffic on a specific point(s) to mirror.
- Mirror destination — The location to send the mirrored traffic, where the sniffer will be located.
Figure 2 shows a local mirror service configured on ALA-A.
- Port 2/1/2 is specified as the source. Mirrored traffic ingressing and egressing this port will be sent to port 2/1/3.
- SAP 2/1/3 is specified as the destination. The sniffer is physically connected to this port. Mirrored traffic ingressing and egressing port 2/1/2 is sent here. SAP, encapsulation requirements, packet slicing, and mirror classification parameters are configured. SDPs are not used in local mirroring.
Figure 2: Local Mirroring Example
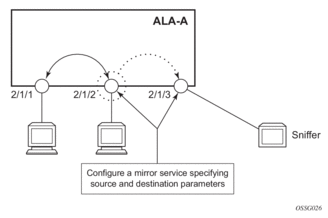
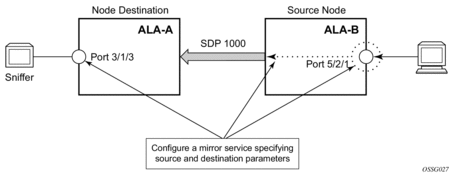
Figure 3 shows a remote mirror service configured as ALA B as the mirror source and ALA A as the mirror destination. Mirrored traffic ingressing and egressing port 5/2/1 (the source) on ALA B is handled the following ways:
- Port 5/2/1 is specified as the mirror source port. Parameters are defined to select specific traffic ingressing and egressing this port.Destination parameters are defined to specify where the mirrored traffic will be sent. In this case, mirrored traffic will be sent to a SAP configured as part of the mirror service on port 3/1/3 on ALA A (the mirror destination).ALA A decodes the service ID and sends the traffic out of port 3/1/3.The sniffer is physically connected to this port (3/1/3). SAP, encapsulation requirements, packet slicing, and mirror classification parameters are configured in the destination parameters.
Figure 3: Remote Mirroring Example
2.2.4. ATM Mirroring
ATM mirror functionality allows 7750 SR users to mirror AAL5 packets from a source ATM SAP to a destination ATM SAP connected locally or remotely. This functionality can be used to monitor the ATM traffic on a particular ATM SAP. In both the local and remote scenarios the source and destination SAPs must be of ATM SAP type.
All ingress and egress AAL5 traffic at the source ATM SAP is duplicated and sent toward the destination ATM SAP. Mirroring the ingress traffic only, egress traffic only, or both, can be configured. ATM OAM traffic is not mirrored toward the destination ATM SAP.
IP filters used as a mirror source are supported on ATM SAPs based on the IP filter applicability for different services.
ATM mirroring is applicable to the following services using an ATM SAP:
- Layer 3: IES and VPRN
- Layer 2: Apipe (sdu-type only), Ipipe, Epipe, VPLS
ATM mirroring on an ATM SAP extends the service mirroring feature to include mirror sources with SAP type of ATM. Mirroring is supported on the following services:
- IES
- VPRN
- VPLS
- Epipe
- Ipipe
- Apipe VLL service with the AAL5 SDU mode (atm-sdu spoke-sdp type)
Characteristics include:
- Supported only ATM MDAs and on the Any Service Any Port (ASAP) MDA.
- Mirror destinations for ATM mirroring must be ATM SAPs and cannot be part of an APS group, an IMA bundle, or an IMA Bundle Protection Group (BPGRP).
- A mirror source can be an ATM SAP component of an IMA bundle but cannot be part of an IMA BPGRP.
- ATM SAPs of an Apipe service with N:1 cell mode (atm-vcc, atm-vpc, and atm-cell spoke-sdp types) cannot be ATM mirror sources.
In Figure 4, CE 3 is connected to PE1 on ATM SAP 2/1/1/:0/100 as part of an IES service. The traffic on ATM SAP 2/1/1/:0/100 is mirrored locally to CE4 device through ATM SAP 1/2/1:1/101. In this scenario, all AAL5 packets arriving at SAP 2/1/1/:0/100 are duplicated and send towards ATM SAP 1/2/1:1/101.
Figure 4: Example of an ATM Mirror Service
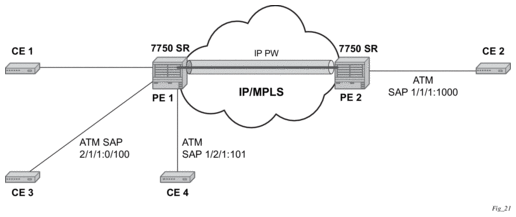
In the case where the destination ATM SAP is on a remote node PE2, then the AAL5 traffic arriving at ATM SAP 2/1/1/:0/100 is duplicated and sent across the IP/MPLS network to PE2. At PE2 the traffic is forwarded to ATM SAP 1/1/1:0/1000 towards the ATM traffic monitoring device.
2.2.5. IP Mirroring
The IP mirroring capability for the 7750 SR and 7950 XRS allows a mirror to be created with a parameter that specifies that only the IP packet is mirrored without the original ATM/FR/POS/Ethernet DLC header. This results in the mirrored IP packet becoming media agnostic on the mirror service egress.
This option is configurable on SAP mirrors for IES, VPRN and VPLS services, Ipipe services, and subscriber mirrors. It is not supported on VLL services such as Apipe, Epipe, Fpipe, and on ports.
2.2.5.1. Remote IP Mirroring
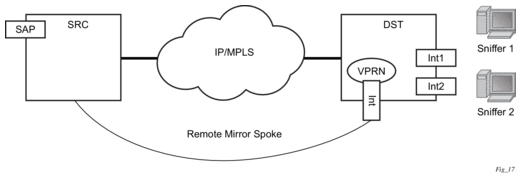
With remote IP mirroring, the mirror destination configuration can allow IP packets to be mirrored from a source router (Figure 5). The packets will be delivered to the destination in a spoke-terminated interface created in a VPRN service. IES interfaces are not supported. The interface can be configured with policy-based routing filters to allow sniffer selection based on incoming mirrored destination IP addresses. The interface cannot send traffic out as it is a destination only feature. Packets arriving at the interface will be routed based on the routing information within the VPRN. Policy-based routing should always be used unless only a sniffer is connected to the VPRN.
Figure 5: Remote IP Mirroring
2.2.5.2. Local IP Mirroring
Local mirroring is similar to remote mirroring but the source and destination of the mirror exist in the same Local IP mirroring node. The configuration must include the source address and destination MAC addresses for the packets going to the sniffer. The destination SAP must be Ethernet.
2.2.5.3. Port-ID Enabled PPP Mirroring
Operators that use mirroring for statistics collection make use of VLANs or DLCIs for customer separation. Since PPP offers no such separation, the maximum number of PPP circuits may be identified (one per destination). This feature provides a proprietary mechanism to allow a single mirror to be used and only applies to the 7450 ESS and 7750 SR.
Port-ID enabled PPP mirroring includes the system’s port ID in the mirrored packet. An operator using this flag in a PPP mirror will be able to identify the end customer circuit by finding the system’s port ID (which is optionally made persistent) and correlating it to the port-id in the mirrored packet.
This mirroring does not change the priority of the mirror order (port, SAP, sub, filter). Lawful intercept mirrors can use the flag and their priority is also maintained.
Since the inclusion of the port ID flag is placed on the mirror destination, all mirrored packets of all sources will include the port ID. For remote mirroring, the mirror destination service at the source node must be configured with this flag.
Note the following restrictions:
- This flag can only be used with a PPP mirror destination.
- This flag is mutually exclusive with a remote-source.
- This flag cannot be enabled on a an IP mirror type.
2.3. Mirrored Traffic Transport using MPLS-TP SDPs
Bidirectional MPLS-TP spoke SDPs with a configured pw-path-id can transport a mirrored service. Mirror services are not supported on static PWs with an MPLS-TP pw-path-id bound to an SDP that uses an RSVP-TE LSP.
Mirror services using MPLS-TP spoke SDPs can be configured using CLI in the context mirror-dest>remote-source. For both the CPM and IOM, this enables reuse of spokes for mirror services and other services such as pipes.
Control channel status signaling is supported with PW redundancy on spoke SDPs in a mirror context.
The following is an example of PW redundancy for a mirror service. In this case, MPLS-TP spoke SDPs are used.
Figure 6: Mirroring with PW Redundancy using MPLS-TP
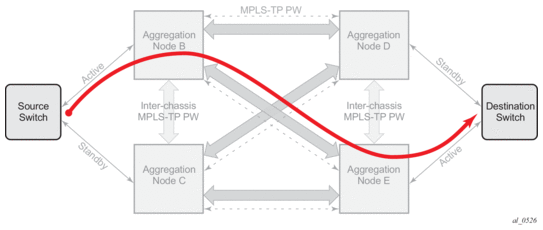
Note that mirroring traffic is usually unidirectional, flowing from “source” nodes (B or C) to “destination” nodes (D or E). However in case of MPLS-TP, the control channel status packets may flow in the reverse direction.
The following is an example of a mirror service configuration using MPLS-TP spoke SDPs:
Source Node B
Destination Node C
Source Node D
Destination Node E
2.4. Subscriber Mirroring
This section describes mirroring based on a subscriber match. Subscriber mirroring applies only to the 7450 ESS and 7750 SR. Enhanced subscriber management provides the mechanism to associate subscriber hosts with queuing and filtering resources in a shared SAP environment. Mirroring used in subscriber aggregation networks for lawful intercept and debugging is required. With this feature, the mirroring capability allows the match criteria to include a subscriber ID.
Subscriber mirroring can also be based on the IP family and host type. The IP family determines if only IPv4 or IPv6 addresses should be mirrored and the host type determines if only IPoE or PPP hosts should be mirrored from the subscriber. To use the IP family and host type, the SAP anti-spoof filter must be set to ip-mac. If subscriber mirroring is performed on the L2TP LAC and the IP family is configured as IPv6, no traffic is mirrored for the PPPoE session, even if the LAC subscriber is dual stack. For L2TP LAC, it is recommended that the IP family is not configured, or configured for IPv4 only.
Subscriber mirroring provides the ability to create a mirror source with subscriber information as match criteria. Specific subscriber packets can be mirrored mirror when using ESM with a shared SAP without prior knowledge of their IP or MAC addresses and without concern that they may change. The subscriber mirroring decision is more specific than a SAP. If a SAP (or port) is placed in a mirror and a subscriber host of which a mirror was configured is mirrored on that SAP packets matching the subscriber host will be mirrored to the subscriber mirror destination.
The mirroring configuration can be limited to specific forwarding classes used by the subscriber. When a forwarding class (FC) map is placed on the mirror only packets that match the specified FCs are mirrored. A subscriber can be referenced in maximum two different mirror-destinations: one for ingress and one for egress.
Subscriber based criteria in a mirror source remains in the mirror/li source configuration even if the subscriber is deleted, removed or logs off. When the subscriber returns (is configured, created or logs in) the mirroring will resume. This also implies that a subscriber can be configured as a mirror or li source before the actual subscriber exists on the node and before the subscriber ID is active (the mirroring will start once the subscriber is actually created or logs in and the subscriber ID becomes active).
2.5. Packet Capture
Packet capture is a troubleshooting tool that uses both mirroring and debugging concepts. It requires only debug privileges (for CLI profile). To enable packet capture there are four steps.
- Setup the mirror destination (in this case, a PCAP). In mirror destination, under a created PCAP ID, specify the file URL for where the packet captures are to be sent. The packet captures are packaged into the libpcap file format.The file URL requires the full path, including both username and password, and the filename. When configured, the system performs a syntax check, but not a FTP or TFTP connection test. The configured file URL is rejected if the syntax check fails.
- Specify the source for packet capture. Using either the debug mirror-source or config mirror mirror-source CLI commands, specify the source to be captured. All mirror sources are supported, including IP-filter, subscriber, SAP, and ports.Similar to debug, the debug mirror-source service ID must match the mirror-dest service ID for the PCAP.
- Begin the capture. To begin the capture, input the debug pcap id capture start CLI command. The following conditions apply:
- Previous captures with the same filename are overwritten. To avoid a file overwrite, create a new capture with a new filename. This can be accomplished by either renaming the file on the FTP or TFTP server or by renaming the filename in the mirror-destination.
- This CLI command also restarts the file transfer session with the remote FTP or TFTP server.
- If the remote FTP or TFTP server is unreachable, the command prompt can pause while attempting to re-establish the remote FTP or TFTP session. The total wait time can be up to 24 seconds (after four attempts of about six seconds each).
- If the debug command pauses, verify the following items:
- the connectivity to the server via the FTP and TFTP port
- the FTP and TFTP user permissions on the FTP or TFTP server
- that the FTP or TFTP server is functional
- The file capture continues indefinitely until the user manually specifies for the packet capture to stop.
- If the file capture fails to start, enter the show pcap id details command to see the status of the capture. The detail prompt notifies the operator of the error, and it may require the operator to stop and re-start the capture again.
- End the capture. To stop the capture, enter the debug pcap id capture stop CLI command. This command also stops the file transfer session and terminates the FTP or TFTP session.
- If the FTP or TFTP server is unreachable, the command prompt rejects further input while it attempts to reestablish the remote FTP/TFTP session. The total wait time can be up to 24s (4 attempts about 6 seconds each, a total of 24s).
- If the debug command pauses, check the following items:
- the connectivity to the server via FTP and TFPT port
- the FTP and TFTP user permissions on the FTP or TFTP server
- that the FTP or TFTP server is functioning
- The file capture will continue indefinitely until the operator specifies the packet capture to stop.
The mirrored packets are placed in a buffer in the CPM before they are transferred over FTP or TFTP. The buffer holds a maximum of 20 Mb. The FTP or TFTP transfer is performed every 0.5 seconds. Each packet that is transferred successfully is flushed from the buffer. Therefore, to ensure all packets are captured successfully, the capture rate must not exceed 20 Mb in 0.5 seconds and the FTP and TFTP transfer must not exceed 320 Mb/s of bandwidth (20 Mb per 0.5 seconds).
In the following show pcap output, the statistics, the session state, write failure, read failures, process time bailouts, and dropped packets are key elements for identifying whether the packet capture on the FTP or TFTP server is reliable.
Packet capture is a troubleshooting tool. Therefore, all CLI commands except for the FTP and TFTP URL destination are located under debug. This allows the administrator to set up CLI profile specifically for packet capture with debug privileges.
The packet capture uses FTP or TFTP for file transfer and can be routed to the destination via the management port or through the IOM port. If the FTP or TFTP server destination is routed via the management port, consider the maximum bandwidth available.
| Caution: Typically, the management port is used for logging, SNMP, SSH/Telnet, AAA, and other management services. A high-throughput packet capture may disrupt these management services. Therefore, use packet capture transfers via the management port with caution. |
Mechanisms are built in to prevent mirroring or packet captures that result in loops or daisy-chains. However, it is possible to form loop or daisy-chain if routing re-routes or configuration changes. When a packet capture becomes looped or daisy-chained, the packet capture stops.
| Note: When executing an admin rollback for a configuration under the config mirror mirror-dest pcap CLI context, the pcap must first be stopped by executing the debug pcap id capture stop command. If the pcap is not stopped, the rollback will fail. |
2.6. Lawful Intercept
Lawful Intercept (LI) describes a process to intercept telecommunications by which law enforcement authorities can un-obtrusively monitor voice and data communications to combat crime and terrorism with higher security standards of lawful intercept capabilities in accordance with local law and after following due process and receiving proper authorization from competent authorities. The interception capabilities are sought by various telecommunications providers.
As lawful interception is subject to national regulation, requirements vary from one country to another. -Nokia’s implementation satisfies most national standard’s requirements. LI capability is configurable for all Nokia service types.
LI mirroring is configured by an operator that has LI permission. LI mirroring is hidden from anyone who does not have the right permission.
2.6.1. LI Activation Through RADIUS
In addition to CLI and SNMP control, RADIUS messages also activate LI sessions for subscriber-host targets. Activation through RADIUS is equivalent to adding or removing a set of subscriber-host entries in an LI source.
| Note: The term “activation” in this section represents both “activation and de-activation”. |
The activation of an LI session via RADIUS applies to the 7450 ESS and 7750 SR and can occur in one of two ways:
- when the RADIUS Access-Accept message is received by the 7450 ESS or 7750 SRThe target (either a host or a set of hosts) is implicit. The target acts as the same host (or set of hosts) that is within the scope of the Access-Accept and interception occurs for this entire set of hosts (or a single host).
- through RADIUS CoA messagesThe target (set of hosts) is identified through one of the following methods:
- Acct-Session-Id (which can represent a single host or a collection of hosts)
- a sap-id;ip-addr carried in the NAS-Port-Id (attr 87) and the Framed-Ip-Address (attr 8).” for IPv4 hosts
- a sap-id;IPv6_addr carried in the NAS-Port-ID (attr 87) and one of Alc-Ipv6-Address, Framed-Ipv6-Prefix, or Delegated-Ipv6-Prefix for IPv6 hosts
- Alc-Subsc-ID-Str
The following set of VSAs is used to activate LI sessions via RADIUS:
- Alc-LI-Action – ON/OFF/NONE
- Alc-LI-Destination - <string> and has two options:
- the mirror destination service ID
- at real time, specify the IP destination, the UDP port, and the router instance of the LI mediation deviceThe format for the VSA is ip-address [:port] [router instance]. The IP address must be of type IPv4 and is the only mandatory parameter.
- Alc-LI-Direction – INGRESS/EGRESS
- Alc-LI-FC – be/l1/l2/af/ef
- (optional) Alc-LI-Use-Outside-IPUse this VSA when the subscriber is an L2-aware NAT subscriber and uses the outside IP address instead of the private IP address for packet mirroring. Refer to L2-Aware NAT for more details.
The Alc-LI-FC VSA can be present several times if more than one forwarding class (FC) is subject to LI.
The VSAs Alc-LI-Direction and Alc-LI-FC are optional. If either is not included, both directions (ingress and egress) as well as all FCs will be mirrored.
The Alc-LI-Destination VSA can be used in one of the following ways.
- A mirror destination must first be provisioned on SR. To use the mirror destination, the VSA specifies the mirror destination service ID in the Access-Accept message or a CoA.
- The VSA specifies the IP address of the mirror destination through the Access-Accept message or a CoA. The reserved range of service IDs and the mirror destination template must be configured first. This VSA provisions the mirror destination using a combination of parameters from the LI template and RADIUS VSAs. The following should be considered when using this VSA.
- Only Layer 3 encapsulation is supported as the mirror destination.
- The VSA has the format ipv4-address [:port] [router {Base | svc-id}]. The VSA must include the LI destination IPv4 address, while the port and the routing instance are optional. If the destination port and routing instance are not specified in the VSA, the configuration from the LI mirror destination template is used.
- With the LI mirror destination reservation, a list of service IDs is reserved for configuring the mirror destination via RADIUS. The LI mirror destination is shared with the mirror destination used for debugging purposes. Therefore, it is suggested to reserve enough for LI purposes, and leave a sufficient amount for debugging and configuration. The VSA triggers the creation of a mirror destination automatically and uses one of the service IDs in the reservation range. An LI source that matches the IP source, IP destination, UDP destination, UDP source, and direction bit, reuses the same LI mirror destination service ID. The LI mirror destination reservation range can be expanded or reduced in real time. The range can be changed completely when there are no LI sources referenced in the mirror reservation range.
- The LI mirror destination template specifies the parameters for the Layer 3 encapsulation. It is mandatory to provision the IP source, IP destination, UDP source, and UDP destination parameters.
- It is possible to configure up to eight LI mirror destination templates. The mirror destination template can be switched in real time, if, for example, a parameter such as the source IP address is to be updated.
- The system can block RADIUS from generating the mirror destination by removing a template reference under the config>li>radius context.
VSAs in the Access-Accept message will also activate LI for a newly-created host. In this case, the LI activation is not addressed by the Acct-Session-Id, as this is not yet known during session authorization.
Different attributes can be used in a CoA to identify one or more subscriber hosts.Typically, only a single attribute or set of attributes is used to target a host or a number of hosts: NAS-Port-Id + IP, Acct-Session-Id, or Alc-Subsc-ID-Str. In the case where “NAS-Port-Id + IP” is used in a Wholesale or Retail model, the Alc-Retail-Serv-Id VSA must be included in the CoA.
The ability to delete all li-source entries from a particular mirror service is also available via RADIUS. This function may be useful when an LI mediation device loses synchronization with the SR OS state and needs to reset a mirror service to a known state with no LI sessions. This clear function is performed by sending the following attributes in a RADIUS CoA. If the CoA does not contain exactly the following three VSAs (each with a valid value matching the configuration on SR OS), the CoA will be silently dropped without a NAK:
- Alc-LI-ActionAlc-LI-Action = ‘clear-dest-service’
- Alc-LI-DestinationThe destination can specify the service ID of the mirror destination or it can pass the VSA in the mirror destination IP, where the mirror destination IP was automatically created by RADIUS.
- Alc-LI-Destination = service-id, if a mirror destination service ID was used for LI
- Alc-LI-Destination = ip-address [:port] [router instance]. The system deletes RADIUS auto-generated mirror destinations based on three parameters: the IP destination, the UDP destination port, and the router instance. These parameters can be passed in from the Alc-LI-Destination VSA. If the VSA provides only some of the parameters, for example, only the destination IP, the parameters from the mirror destination template is used (from config>li>mirror-dest-template). The three parameters determine the mirror service ID to delete and any combination of the IP source, UDP source port, and direction bit can be deleted. It is possible that a template change can prevent the VSA from deleting the mirror destination service. To manually delete a mirror destination, a CLI command is provided under clear li radius mirror-dest svc-id. To determine the service ID to delete, a manual login is required.
- Alc-Authentication-Policy-NameThis VSA is only required in a certain configuration. The VSA is not required when a RADIUS server policy is configured under configure subscriber-mgmt authentication-policy and the RADIUS server policy servers are used as CoA servers.This VSA is required in the configuration where the servers configured inside the authentication policy are used as CoA servers, with the following:
- a list of servers is configured under config>subscr-mgmt>auth-plcy>radius-auth-server
- accept-authorization-change is enabled under config>subscr-mgmt>auth-plcy
- the authentication policy does not reference the RADIUS server policy
When the above conditions are met, the Alc-Authentication-Policy-Name VSA is required and must reference the authentication policy that contains the IP address of the LI CoA client.
The LI-related VSAs cannot be combined in one CoA message with other action-related VSAs (force renew, change of SLA profile, and so on). The only exception to this rule is for the CoA used to create a new subscriber host. In this case, LI-related VSAs can be included, along with other VSAs.
If LI is activated through CLI or SNMP, the activation through RADIUS takes precedence. The precedence in this context means that RADIUS activation of LI fully overrides whatever was configured at CLI or SNMP level for this particular host. If the RADIUS LI is de-activated, the CLI or SNMP configuration will become active again.
The LI-related VSAs are not shown in debug messages. The show li li-source command shows all sub-hosts for which LI was activated using RADIUS VSAs. This command is only accessible to CLI users with LI privileges.
2.6.2. Routable Lawful Intercept Encapsulation
The Routable LI encapsulation feature allows LI mirrored packets to be placed into a routable (for example, IP/UDP) header and then forwarded in a routing context (base or VPRN). An LI-shim inserted before the customer packet allows correlation of packets to LI sessions at the downstream LI Mediation device (LIG).
Figure 7: Routable Lawful Intercept Encapsulation
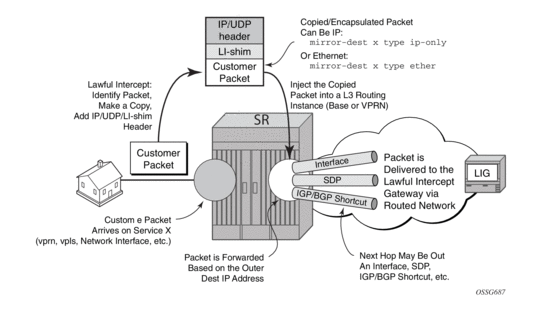
Figure 8: Routable Encapsulation Format
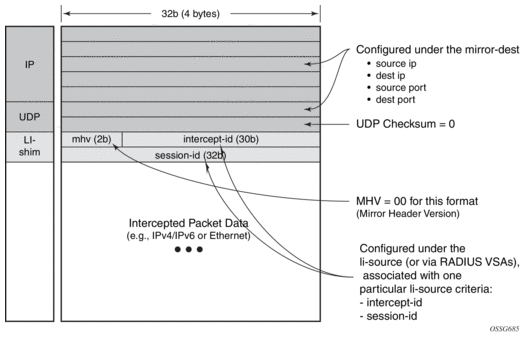
Some of the supported attributes and scenarios for the routable LI encapsulation feature include the following:
- The part of the customer packet that is copied and placed into the routable encapsulation can be either the IP packet (with none of the original Layer2 encap) or an Ethernet packet by selecting either ip-only or ether as the mirror-dest type.
- The ability to inject into the Base routing instance (for forwarding out network interfaces or IES SAPs for example) or a VPRN service.
- The ability to forward the encapsulated packets out VPRN SDPs, IGP/BGP shortcuts and SDP spoke interfaces.
- Options to use ip, udp, li-shim or ip, gre routable encapsulation (applies to the 7450 ESS and 7750 SR).
- An optional direction bit in the li-shim.
- If the use of the direction bit is configured, then a bit from the intercept-id (config under the mirror-dest) is “stolen”. Only a 29b intercept-id is allowed for li-source entries if the mirror destination is configured to use a direction bit.
Figure 9: LI-Shim version 01 with a direction bit
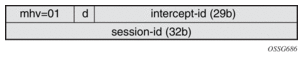
- The encoding of the direction (d) bit is as follows:
- 0 = ingress
- 1 = egress
- For NAT based LI, ingress means the traffic arriving at the node from the subscriber host (applies to the 7450 ESS and 7750 SR).
- User configurable intercept-id and session-id per li-source entry that is placed into the li-shim (a total max of 62 configurable bits).
- Configuration via CLI/SNMP or RADIUS (applies to the 7450 ESS and 7750 SR). For RADIUS configuration the following VSAs are used:
- Alc-LI-Action, Alc-LI-Direction, Alc-LI-Destination, Alc-LI-FC (See LI Activation Through RADIUS).
- Alc-LI-Intercept-Id: specifies the intercept-id to place in the LI shim. Only applicable if the mirror-dest (as specified by the Alc-LI-Destination) is configured with routable encap that contains the LI-Shim. A value of 0 is used if this VSA is not present.
- Alc-LI-Session-Id: specifies the session-id to place in the LI-Shim. Only applicable if the mirror-dest (as specified by the Alc-LI-Destination) is configured with routable encap that contains the LI shim. A value of 0 is used if this VSA is not present.
- A LI session configured via RADIUS takes precedence over a session configured via CLI, but the CLI mirror is re-instated if the RADIUS mirror request is later removed (applies to the 7450 ESS and 7750 SR)
- ip, udp and li-shim encap is available for ether and LI shim mirror-dest types (note that ip-only supports, amongst other formats, packets that are reassembled from ATM cells.)
- ip | udp | li-shim encap is available for all li-source entry types: sap, filter, subscriber and nat.
- Note that for NAT based Lawful Intercept, routable LI encap is available, as well as the MAC or Layer 2-based encapsulation for NAT LI as configured under config>li>li-source>nat>ethernet-encap (applies to the 7450 ESS and 7750 SR)
- Fragmentation of the resulting mirror packet is supported. Note that fragmentation is supported for NAT LI with the routable encapsulation, but fragmentation is not supported for NAT LI with Ethernet encapsulation (applies to the 7450 ESS and 7750 SR).
The following restrictions apply to the routable LI encapsulation feature:
- Only applicable to Lawful Intercept and is not available for debug or MS-ISA based Application Assurance mirrors. MS-ISA based Application Assurance is applicable to the 7450 ESS and 7750 SR.
- Not applicable to frame-relay, PPP, ATM-SDU, SAToP, or CESoPSN mirror-dest types.
- IPv4 transport only (the routable encapsulation cannot be IPv6).
- On the mirror source node, forwarding of routable encapsulated LI packets out of an R-VPLS interface is not supported. A mirror destination configured with routable encapsulation can be bound to a routing instance that also has an R-VPLS bound to it, but the operator must ensure that the destination of the LI packets is not reachable via any R-VPLS interfaces. Any routable encapsulated LI packets that arrive at the egress of an R-VPLS interface are discarded. Parallel use of routable LI encapsulation and R-VPLS in the same routing instance is supported as long as the mirrored packets do not egress out of the R-VPLS interface.
- ip | gre encap is supported for the ip-only mirror destination type only, and only for subscriber li-source entries (CLI, SNMP, or RADIUS based). Subscriber management is not supported on the 7950 XRS.
- The contents of the GRE header are all zeros (all optional bits zero, no optional headers/fields like checksum, offset, key, seq, and so on) except for the Protocol field which will contain 0x0800 for IPv4 packets or 0x86DD for IPv6 packets. The far end receiver of the intercepted packets must be configured to expect no GRE options (that is, no key, no checksum, and so on).
- On the source node where LI mirroring occurs, the operator must configure the mirror-dest to inject into the routing instance (that is, base or VPRN) in which the actual destination address is reachable without having to hop into a different instance using GRT leaking. In other words the interface out which the packet will end up traveling must exist in the routing instance that is configured in the mirror-dest.
- For example, if the LIG is at 110.120.130.140 and is in the base instance, but VPRN-1 has a default route to the GRT (for example, 0.0.0.0->GRT) then the operator must configure the mirror destination to inject into the base (even though theoretically address 110.120.130.140 is reachable from VPRN-1). If the operator attempts to configure the mirror destination to inject into VPRN-1, and VPRN-1 itself does not have reachability to 110.120.130.140 out an interface that is part of the VPRN, then the mirror destination will be operationally down.
- Platforms: Not supported on the 7450 ESS-1.
Care must be taken in the configuration of LI mirrors and the destination IP address for the routable LI encapsulation. Incorrect selection of the destination IP could send packets to unintended destinations (for example, configuring the encapsulation with a subscriber's IP address), and combinations of mirrors and routable encapsulation can create loops in the network.
2.7. Pseudowire Redundant Mirror Services
This section describes the implementation and configuration of redundant Mirror/Lawful Intercept services using redundant pseudowires.
Regardless of the protection mechanism (MC-LAG, STP, or APS) the source switch will only transmit on the active link and not simultaneously on the standby link. As a result when configuring a redundant mirror or LI service or a mirror service where the customer has a redundant service but the mirror or LI service is not redundant the mirror source must be configured on both (A and B) PE nodes. In either case the PE with a mirror source will establish a pseudo wire to each eligible PE where the mirror / LI service terminates.
Figure 10: State Engine for Redundant Service to a Redundant Mirror Service
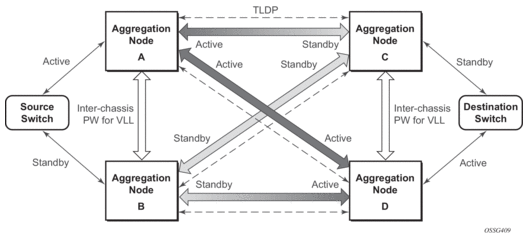
It is important to note that in order to provide protection in case the active SDP between node A and D fails and the need to limit the number of lost data for LI the ICB between node A and B must be supported. As a result when the SDP connecting nodes A and D fails the data on its way from the source switch to node A and the data in node A must be directed by the ICB to node B and from there to node D.
This functionality is already supported in when providing pseudo wire redundancy for VLLs and must be extended to mirror or LI service redundancy.
Figure 11: State Engine for Redundant Service to a Non-Redundant Mirror Service
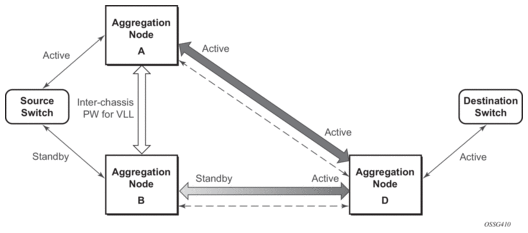
The notable difference with scenarios standard pseudo wire redundancy scenarios is that provided the customer service is redundant on nodes A and B (Figure 10 and Figure 11) both aggregation node A and Aggregation node B maintain an active Pseudo wire to Node D who in turn has an active link to the destination switch. If in the sample in Figure 10, the link between D and the destination switch is disconnected then both aggregation A and B must switch to use pseudowire connection to Node C.
Figure 12: State Engine for a Non-Redundant Service to a Redundant Mirror Service
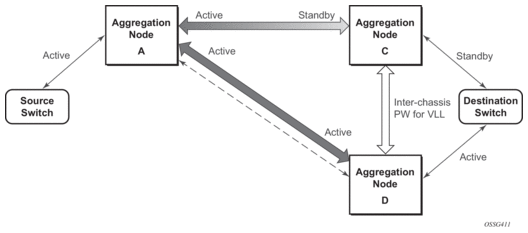
In the case where a non-redundant service is being mirrored to a redundant mirror service (Figure 12) the source aggregation node (A) can only maintain a pseudo wire to the active destination aggregation node (D). Should the link between aggregation node D and the destination switch fail then the pseudo wire must switch to the new active aggregation node (C).
2.7.1. Redundant Mirror Source Notes
A redundant remote mirror service destination is not supported for IP mirrors (a set of remote IP mirror destinations). The remote destination of an IP mirror is a VPRN instance, and an “endpoint” cannot be configured in a VPRN service.
A redundant mirror source is supported for IP mirrors, but the remote destination must be a single node (a set of mirror source nodes, each with a mirror destination that points to the same destination node). In this case the destination node would have a VPRN instance with multiple ip-mirror-interfaces.
Multi Chassis APS (MC-APS) groups can not be used as the SAP for a redundant remote mirror destination service. APS can not be used to connect the remote mirror destination SR nodes to a destination switch.
Multi Chassis APS (MC-APS) groups can be used as the SAP for a redundant mirror service source. APS can be used to redundantly connect the source of the mirrored traffic to the SR nodes that are behaving as the mirror-sources.
2.8. Lawful Intercept and NAT
2.8.1. Carrier Grade NAT
Lawful intercept (LI) for NAT is supported to mirror configured subscriber’s traffic to a mirror destination. When active, packets are mirrored from the perspective of the NAT outside interface (after NAT translations have occurred). All traffic for the specified subscriber, including traffic associated with static port-forwards, is mirrored. This feature is supported for 7450 ESS and 7750 SR only.
A simplified Ethernet encapsulation (with an optional Intercept ID) is used for all NAT traffic. When mirroring NAT traffic, the mirror destination must be of type ether. The customer packet from the (outside) IP header onwards (including the IP header) is mirrored. The operator has the configuration option of embedding the intercept ID into the LI packet through the use of an explicit intercept-id command. Both packet formats are described below:
Figure 13: Ethernet Mirror Examples

The contents of the highlighted fields are configurable using the following CLI:
The default Ethernet-header is to use etype 0x600 and system MAC address for both the source and destination addresses. The configurable Ethertype and Intercept ID is only added when an intercept ID is present for the subscriber in the NAT configuration.
2.8.2. L2-Aware NAT
When Layer 3 encapsulation is configured as the mirror destination for an L2-Aware NAT subscriber, the mirror destination must be of type ip-only and the encapsulation must be of type ip-udp-shim. For L2-Aware NAT, it is possible to assign the same inside IPv4 private IP address to all subscribers. It is preferable to intercept the L2-Aware NAT subscriber using the outside IP address instead. This can be accomplished from both RADIUS and CLI as described in the following table.
Table 3: Use of Inside and Outside IPs for LI
Lawful Intercept to use host inside IP address | Lawful Intercept to use host outside IP address | |
CLI access |
The command config>li>use-outside-ip-address does not apply to CLI configured LI targets. | Configure the subscriber ID under config>li>li-source>nat>l2-aware-sub. The command config>li>use-outside-ip-address does not apply to CLI configured LI targets. |
RADIUS access |
|
|
When the RADIUS VSA Alc-LI-Use-Outside-IP is used, the configuration config>li>use-outside-ip-address is ignored.
Alc-Use-Outside-IP is only supported when the mirror destination service is configured with Layer 3 encapsulation.
L2-Aware subscribers do not support the LI RADIUS VSAs Alc-LI-FC and Alc-LI-Direction. When an L2-Aware subscriber is subjected to LI via CLI or RADIUS, dual stack traffic is mirrored.
2.9. Configuration Process Overview
Figure 14 shows the process to provision basic mirroring parameters.
Figure 14: Mirror Configuration and Implementation Flow
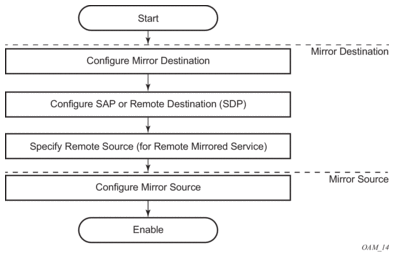
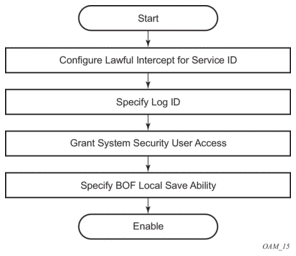
Figure 15 shows the process to provision LI parameters.
Figure 15: Lawful Intercept Configuration and Implementation Flow
2.10. Configuration Notes
This section describes mirroring configuration caveats.
- Multiple mirroring service IDs (mirror destinations) may be created within a single system.
- A mirrored source can only have one destination.
- Both destination mirroring service IDs (including service parameters) and config mirror source (defined in config>mirror>mirror-source) are persistent between router (re)boots and are included in the configuration savesDebug mirror source (defined debug>mirror>mirror-source) and lawful intercept source (defined in config>li>li-source) criteria configurations are not preserved in a configuration save (admin save). Debug mirror source configuration can be saved using admin>debug-save. Lawful intercept source configuration can be saved using config>li>save.
- Subscriber based lawful intercept source criteria is persistent across creation/existence of the subscriber. Filter or SAP-based lawful intercept (LI) source criteria is removed from the LI source configuration if the filter entry or SAP is deleted. Applies to the 7450 ESS and 7950 SR.
- Physical layer problems such as collisions, jabbers, and so on, are not mirrored. Typically, only complete packets are mirrored.
- Starting and shutting down mirroring:Mirror destinations:
- The default state for a mirror destination service ID is shutdown. Execute a no shutdown command to enable the feature.
- When a mirror destination service ID is shutdown, mirrored packets associated with the service ID are not accepted from its mirror source or remote source. The associated mirror source is put into an operationally down mode. Mirrored packets are not transmitted out the SAP or SDP. Each mirrored packet is silently discarded. If the mirror destination is a SAP, the SAP’s discard counters are incremented.
- Issuing the shutdown command causes the mirror destination service or its mirror source to be put into an administratively down state. Mirror destination service IDs must be shut down first in order to delete a service ID, or SAP, or SDP association from the system.
Mirror sources:- The default state for a mirror source for a given mirror-dest service ID is no shutdown. Enter a shutdown command to deactivate (disable) mirroring from that mirror-source.
- Mirror sources do not need to be shutdown to remove them from the system. When a mirror source is shutdown, mirroring is terminated for all sources defined locally for the mirror destination service ID.
The following are lawful intercept configuration caveats.
Network management — Operators without LI permission cannot view or manage the LI data on the node nor can they view or manage the data on the Network Management platform.
LI mirroring does not allow the configuration of ports and ingress labels as a source parameter.