2. CLI Usage
2.1. CLI Structure
SR OS CLI is a command-driven interface accessible through the console, Telnet and secure shell (SSH). The CLI can be used for the configuration and management of routers.
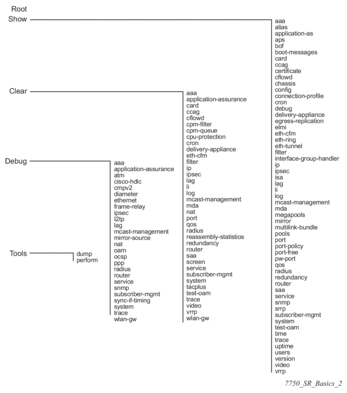
The SR OS CLI command tree is a hierarchical inverted tree. At the highest level is the ROOT level. Below this level are other tree levels with the major command groups; for example, configuration commands and show commands are levels below ROOT.
The CLI is organized so related commands with the same scope are at the same level or in the same context. Sublevels or subcontexts have related commands with a more refined scope.
Figure 1 and Figure 2 are examples displaying the major contexts for router configuration, and are not a definitive list.
| Note: The CLI engine used to execute scripts is the primary CLI engine configured with configure system management-interface cli cli-engine. |
Figure 1: Root Commands

Figure 2: Operational Root Commands
2.2. Navigating in the CLI
The command outputs in the following sections are examples only; actual displays may differ depending on supported functionality and user configuration.
2.2.1. CLI Contexts
Use the CLI to access, configure, and manage Nokia’s routers. CLI commands are entered at the command line prompt. Access to specific CLI commands is controlled by the permissions set by your system administrator. Entering a CLI command makes navigation possible from one command context (or level) to another.
When you initially enter a CLI session, you are in the ROOT context. Navigate to another level by entering the name of successively lower contexts. For example, enter either the configure or show commands at the ROOT context to navigate to the config or show context, respectively. For example, at the command prompt (#), enter config. The active context displays in the command prompt.
In a given CLI context, enter commands at that context level by simply entering the text. It is also possible to include a command in a lower context as long as the command is formatted in the proper command and parameter syntax.
The following example shows two methods to navigate to a service SDP ingress level.
Method 1:
Method 2:
The CLI returns an error message when the syntax is incorrect.
2.2.2. Basic CLI Commands
The console control commands are the commands that are used for navigating within the CLI and displaying information about the console session. Most of these commands are implemented as global commands. They can be entered at any level in the CLI hierarchy with the exception of the password command which must be entered at the ROOT level. The console control commands are listed in Table 3.
Table 3: Console Control Commands
Command | Description |
<Ctrl-c> | Aborts the pending command. |
<Ctrl-z> | Terminates the pending command line and returns to the ROOT context. |
Navigates the user to the parent context. | |
Echoes the text that is typed in. Primary use is to display messages to the screen within an exec file. | |
Executes the contents of a text file as if they were CLI commands entered at the console. | |
Returns the user to the previous higher context. | |
exit all | Returns the user to the ROOT context. |
? | Displays help in the CLI. |
Displays a list of the most recently entered commands. | |
Displays the running configuration for a configuration context. | |
Terminates the CLI session. | |
oam | Provides OAM test suite options. Refer to “OAM” in the 7450 ESS, 7750 SR, 7950 XRS, and VSR OAM and Diagnostics Guide. |
Changes the user CLI login password. The password can only be changed at the ROOT level. | |
Verifies the reachability of a remote host. | |
Displays the present or previous working context of the CLI session. | |
Causes the console session to pause operation (sleep) for one second or for the specified number of seconds. Primary use is to introduce a pause within the execution of an exec file. | |
Opens a secure shell connection to a host. | |
Telnet to a host. | |
Determines the route to a destination address. | |
Displays a list of all commands at the current level and all sublevels. | |
Sends a console message to a specific user or to all users with active console sessions. |
Display the list of all system global commands by entering help globals in the CLI:
Table 4 describes command syntax symbols.
Table 4: Command Syntax Symbols
Symbol | Description |
| | A vertical line indicates that one of the parameters within the brackets or braces is required. tcp-ack {true | false} |
[ ] | Brackets indicate optional parameters. redirects [number seconds] |
{ } | Braces indicate that one of the parameters must be selected. default-action {drop | forward} |
[{ }] | Braces within square brackets indicates that you must choose one of the optional parameters.
|
Bold | Commands in bold indicate commands and keywords. |
Italic | Commands in italics indicate that you must enter text based on the parameter. interface interface-name |
2.2.3. CLI Environment Commands
The CLI environment commands are found in the root>environment context of the CLI tree and control session preferences for a single CLI session. The CLI environment commands are listed in Table 5.
Table 5: CLI Environment Commands
Command | Description |
Enables the substitution of a command line by an alias. | |
Enables or disables the use of a create parameter check. | |
Enables or disables the kernel. | |
Configures whether CLI output should be displayed one screen at a time awaiting user input to continue. | |
Configures the maximum number of higher-level CLI context nodes to display by name in the CLI prompt for the current CLI session. | |
Saves the indicator in the prompt. | |
Enables or disables the shell. | |
Enables the suggestion of internally created objects while auto completing. | |
Configures the terminal screen length for the current CLI session. | |
Specifies whether time should be displayed in local time or UTC. | |
Specifies whether the time-stamp should be displayed before the prompt. |
2.2.4. CLI Monitor Commands
Monitor commands display specified statistical information related to the monitor subject (such as filter, port, QoS, router, service, and VRRP) at a configurable interval until a count is reached. The CLI monitor commands are found in the root>monitor context of the CLI tree.
The monitor command output displays a snapshot of the current statistics. The output display refreshes with subsequent statistical information at each configured interval and is displayed as a delta to the previous display.
The <Ctrl-c> keystroke interrupts a monitoring process. Monitor command configurations cannot be saved. You must enter the command for each monitoring session. If the maximum limits are configured, you can monitor the statistical information for a maximum of 60 * 999 sec ~ 1000 minutes.
The CLI monitor command contexts are listed in Table 6.
Table 6: CLI Monitor Command Contexts
Command | Description |
Enables monitoring of ingress FP queue groups. | |
Enables CCAG port monitoring for traffic statistics. This command is supported on the 7450 ESS and 7750 SR; additional restrictions may apply. | |
Monitor command output for CPM filters. | |
Enables IP and MAC filter monitoring at a configurable interval until that count is reached. | |
Enables Link Aggregation Group (LAG) monitoring to display statistics for individual port members and the LAG. | |
Enables management access filter monitoring. | |
Enables port traffic monitoring. The specified port(s) statistical information displays at the configured interval until the configured count is reached. | |
Enables arbiter and scheduler statistics monitoring. | |
Enables virtual router instance monitoring at a configurable interval until that count is reached. | |
Monitors commands for a particular service. |
2.3. Getting Help in the CLI
The help system commands and the ? key display different types of help in the CLI. Table 7 lists the different help commands.
Table 7: Online Help Commands
Command | Description |
help ? | List all commands in the current context. |
string ? | List all commands available in the current context that start with string. |
command ? | Displays the command’s syntax and associated keywords. |
command keyword ? | List the associated arguments for keyword in command. |
string<Tab> | Complete a partial command name (auto-completion) or list available commands that match string. |
The tree and tree detail system commands are useful when searching for a command in a lower-level context.
The following example shows a partial list of the tree and tree detail command output on a 7750 SR.
2.4. The CLI Command Prompt
By default, the CLI command prompt indicates the device being accessed and the current CLI context. For example, the prompt: A:ALA-1>config>router>if# indicates the active context, and the user is on the device with hostname ALA-1 in the configure>router>interface context. In the prompt, the separator used between contexts is the “>” symbol. The first letter in the prompt indicates the active CPM slot, in this case A. The active CPM can be A or B on 7750 SR, and A, B, C, or D on 7950 XRS.
At the end of the prompt, there is either a pound sign (“#”) or a dollar sign (“$”). A “#” at the end of the prompt indicates the context is an existing context. A “$” at the end of the prompt indicates the context has been newly created. New contexts are newly created for logical entities when the user first navigates into the context.
Since there can be a large number of sublevels in the CLI, the environment command reduced-prompt no of nodes in prompt allows the user to control the number of levels displayed in the prompt.
All special characters (#, $, and so on) must be enclosed within double quotes, otherwise it is seen as a comment character and all characters on the command line following the # are ignored. For example:
When changes are made to the configuration file a “*” appears in the prompt string (*A:ALA-1), indicating that the changes have not been saved. When an admin save command is executed the “*” disappears. This behavior is controlled in the saved-ind-prompt command in the environment context.
2.5. Displaying Configuration Contexts
The info, info detail and objective commands display configuration for the current level. The info command shows non-default configurations. The info detail command shows the entire configuration for the current level, including defaults. The info [objective] command provides an output objective that controls the configuration parameters to be displayed.The following example displays the output from the info command and the info detail command.
2.6. EXEC Files
The exec command allows you to execute a text file of CLI commands as if it were typed at a console device.
The exec command and the associated exec files can be used to conveniently execute a number of commands that are always executed together in the same order. For example, an exec command can be used by a user to define a set of commonly used standard command aliases.
The echo command can be used within an exec command file to display messages on screen while the file executes.
2.7. CLI Script Control
The SR OS provides centralized script management for CLI scripts that are used by CRON and the Event Handling System (EHS). A set of script policies and script objects can be configured to control the following items and more:
- where scripts are located (local compact flash, remote FTP server)
- where to store the output of the results
- how long to keep historical script result records
- how long a script may run
If the scripts are located on local compact flash devices, then the user must ensure that the scripts are on the compact flash devices of both CPMs so that operation of EHS continues as expected if a CPM switchover occurs.
A single script can be executing at one time. A table (SNMP smRunTable in the DISMAN-SCRIPT-MIB) is used as both an input queue of scripts waiting to be executed as well as for storage of records for completed scripts. If the input queue is full, then the script request is discarded.
2.8. Entering CLI Commands
The command outputs in the following sections are examples only; actual displays may differ depending on supported functionality and user configuration.
2.8.1. Command Completion
The CLI supports both command abbreviation and command completion. If the keystrokes entered are enough to match a valid command, the CLI displays the remainder of the command syntax when the <Tab> key or space bar is pressed. When typing a command, the <Tab> key or space bar invokes auto-completion. If the keystrokes entered are definite, auto-completion will complete the command. If the letters are not sufficient to identify a specific command, pressing the <Tab> key or space bar displays commands matching the letters entered.
System commands are available in all CLI context levels.
2.8.2. Unordered and Unnamed Parameters
In a given context, the CLI accepts command parameters in any order as long as the command is formatted in the proper command keyword and parameter syntax. Command completion works as long as enough recognizable characters of the command are entered.
The following output shows the command syntax for static-route-entry.
Some SR OS CLI commands have multiple unnamed parameters. For example, the subrate csu-mode rate-step command has both a csu-mode parameter and a rate-step parameter that do not have leading keywords. SR OS uses a best-match algorithm to select which parts of the user input are intended to be used for each unnamed parameter. This best-match algorithm depends on the specific command.
In some cases, it is not possible for the algorithm to be 100% accurate, and the SR OS may assign a value to an unintended parameter when two unnamed parameters have similar constraints and syntax. For example, the environment alias alias-name alias-command-name command may reverse the alias-name and alias-command-name parameters if the first parameter entered is larger than 80 characters.
2.8.3. Editing Keystrokes
When entering a command, special keystrokes allow for editing of the command. Table 8 lists the command editing keystrokes.
Table 8: Command Editing Keystrokes
Editing Action | Keystrokes |
Delete current character | <Ctrl-d> |
Delete text up to cursor | <Ctrl-u> |
Delete text after cursor | <Ctrl-k> |
Move to beginning of line | <Ctrl-a> |
Move to end of line | <Ctrl-e> |
Get prior command from history | <Ctrl-p> |
Get next command from history | <Ctrl-n> |
Move cursor left | <Ctrl-b> |
Move cursor right | <Ctrl-f> |
Move back one word | <Esc><b> |
Move forward one word | <Esc><f> |
Convert rest of word to uppercase | <Esc><c> |
Convert rest of word to lowercase | <Esc><l> |
Delete remainder of word | <Esc><d> |
Delete word up to cursor | <Ctrl-w> |
Transpose current and previous character | <Ctrl-t> |
Enter command and return to root prompt | <Ctrl-z> |
Refresh input line | <Ctrl-l> |
2.8.4. Absolute Paths
CLI commands can be executed in any context by specifying the full path from the CLI root. To execute an out-of-context command, enter a forward slash “/” or backward slash “\” at the beginning of the command line. The commands are interpreted as an absolute path. The forward slash “/” or backward slash “\” cannot be used as an absolute path at the beginning of the command-string of the environment alias command. Spaces between the slash and the first command will return an error.
The command may change the current context depending on whether or not it is a leaf command. This is the same behavior the CLI performs when CLI commands are entered individually, for example:
or
An absolute path command behaves the same as manually entering a series of command line instructions and parameters.
For example, beginning in an IES context service ID 4 (IES 4):
behaves the same as the following series of commands:
If the command takes you to a different context, the following occurs:
becomes:
2.8.5. History
The CLI maintains a history of the most recently entered commands. The history command shows the most recently entered CLI commands.
2.8.6. Entering Numerical Ranges
The SR OS CLI allows the use of a single numerical range as an argument in the command line. This range can be a set or a sequence of numbers, or a combination of both.
A set is a range of numerical values, from a minimum to a maximum, incremented by 1. For example:
A sequence is a list of discrete integer elements, in any order. For example:
A sequence can contain sets as well as integer elements. For example:
For example, it is possible to shut down ports 1 through 10 in Slot 1 on XMA/MDA 1. A port can be denoted with “slot/mda/port”, where slot is the slot number, mda is the XMA/MDA number and port is the port number. To shut down ports 1 through 10 on Slot 1 and XMA/MDA 1, the command is entered as follows:
<Ctrl-C> can be used to abort the execution of a range command.
CLI commands can contain ranges of hexadecimal values. This allows ranges to be used when working with data normally expressed in hexadecimal instead of decimal, such as IPv6 or MAC addresses. For example:
A range can also be a reference to a previous range in the same command. This reference takes the form "[$x]", where x is an integer between 0 and 5. For example:
This will give vprn 11 the router-id "10.20.11.1", vprn 12 the router-id "10.20.12.1", and so on.
Specifying a range in the CLI does have limitations. These limitations are summarized in Table 9.
Table 9: CLI Range Use Limitations
Limitation | Description |
Up to 6 ranges (including references) may be specified in a single command, and they may not combine to more than 1000 iterations of the command. | It is possible to shut down ports 1 through 10 on XMA/MDA 1 and XMA/MDA 2: configure port 1/[1..2]/[1..10] |
Ranges within quotation marks are interpreted literally. | In the CLI, enclosing a string in quotation marks (“string”) causes the string to be treated literally and as a single parameter. For example, several commands in the CLI allow the configuration of a descriptive string. If the string is more than one word and includes spaces, it must be enclosed in quotation marks. A range that is enclosed in quotes is also treated literally. For example, configure router interface "A[1..10]" no shutdown creates a single router interface with the name “A[1..10]”. However, a command such as: configure router interface A[1..10] no shutdown creates 10 interfaces with names A1, A2 .. A10. |
Command completion will cease to work when entering a range. | After entering a range in a CLI command, command and key completion, which normally occurs by pressing the <Tab> or spacebar, will cease to work. If the command line entered is correct and unambiguous, the command works properly; otherwise, an error is returned. |
2.8.7. Pipe/Match
SR OS supports the pipe feature to search one or more files for a given character string or pattern.
When using the pipe or match command, the variables and attributes must be spelled correctly. The attributes follow the command and must come before the expression or pattern. The following are examples of how to use the pipe/match command to complete different tasks:
- Task: Capture all the lines that include “echo” and redirect the output to a file on the compact flash:admin display-config | match “echo” > cf1:\test\echo_list.txt
- Task: Display all the lines that do not include “echo”:admin display-config | match invert-match “echo”
- Task: Display the first match of “vpls” in the configuration file:admin display-config | match max-count 1 “vpls”
- Task: Display everything in the configuration after finding the first instance of “interface”:admin display-config | match post-lines 999999 interface
- Task: Display a count of the total number of lines of output instead of displaying the output itself.admin display-config | match interface | count
Command syntax:
match pattern context {parents | children | all} [ignore-case] [max-count lines-count] [expression]
match pattern [ignore-case] [invert-match] [pre-lines pre-lines] [post-lines lines-count] [max-count lines-count] [expression]
where:
For example:
Table 10 describes regular expression symbols and their interpretation (similar to what is used for route policy regexp matching). Table 11 describes special characters.
Table 10: Regular Expression Symbols
String | Description |
. | Matches any single character. |
[ ] | Matches a single character that is contained within the brackets. [abc] matches “a”, “b”, or “c”. [a-z] matches any lowercase letter. [A-Z] matches any uppercase letter. [0-9] matches any number. |
[^ ] | Matches a single character that is not contained within the brackets. [^abc] matches any character other than “a”, “b”, or “c”. [^a-z] matches any single character that is not a lowercase letter. |
^ | Matches the start of the line (or any line, when applied in multiline mode) |
$ | Matches the end of the line (or any line, when applied in multiline mode) |
() | Define a “marked subexpression”. Every matched instance will be available to the next command as a variable. |
* | A single character expression followed by “*” matches zero or more copies of the expression. |
{m,n} | Matches least m and at most n repetitions of the term |
{m} | Matches exactly m repetitions of the term |
{m,} | Matches m or more repetitions of the term |
? | The preceding item is optional and matched at most once. |
+ | The preceding item is matched one or more times. |
- | Used between start and end of a range. |
\ | An escape character to indicate that the following character is a match criteria and not a grouping delimiter. |
> | Redirect output |
Table 11: Special Characters
Options | Similar to | Description |
[:upper:] | [A-Z] | uppercase letters |
[:lower:] | [a-z] | lowercase letters |
[:alpha:] | [A-Za-z] | upper- and lowercase letters |
\w | [A-Za-z_] | word characters |
[:alnum:] | [A-Za-z0-9] | digits, upper- and lowercase letters |
[:digit:] | [0-9] | digits |
\d | [0-9] | digits |
[:xdigit:] | [0-9A-Fa-f] | hexadecimal digits |
[:punct:] | [.,!?:...] | punctuation |
[:blank:] | [ \t] | space and TAB |
[:space:] | [ \t\n\r\f\v] | blank characters |
\s | [ \t\n\r\f\v] | blank characters |
2.8.8. Pipe/Count
The SR OS supports a pipe/count command (...| count) that provides a count of the number of lines that would have otherwise been displayed. The pipe/count command is particularly useful when used in conjunction with the pipe/match command in order to count the number of output lines that match a specified pattern.
For example:
2.8.9. Range Operator Support of Regular Expression Match
The user can include a regular expression inside the range operator, of any clear, config, show, or tools CLI command. The beginning and ending of the regular expression must be delimited with the forward slash "/" symbol.
SR OS performs the following steps:
- auto-completes the command to get all the possible names
- performs a match of the regular expression against all the names
- executes the command for the names for which the match was successful
| Note: The order of the execution is the same as the order in which the names are listed in output display of the CLI info command or in the output display when you invoke the auto-complete function using the TAB key. If the execution of the command fails for one of the matching object names, the execution is aborted and the remaining matching object names are not processed. |
For example (assume the following SR-TE LSP names are configured on the router):
The following command displays the subset of all SR-TE LSPs with names that include the expression "LSP":
show router mpls sr-te-lsp [/LSP/]
The SR OS expands this command into the following individual commands:
show router mpls sr-te-lsp RENO194_DET190_LSP1_Profile10
show router mpls sr-te-lsp RENO194_DET190_LSP3
show router mpls sr-te-lsp RENO194_ATL224_LSP1
The output of the three show commands is displayed in the following example:
2.8.9.1. Regular Expression Symbols in a Regular Expression Match Operation
The user can use all the regular expression symbols listed in Table 10 and Table 11 inside the regular expression to match.
For example, the user can list all LSP names that begin with the string "RENO194_" followed by the string "ATL" as follows:
| Note: The following conventions are used in the previous example.
|
Table 12 summarizes special rules governing the use of some of the regular expression symbols inside a regular expression match operation. Any symbol from Table 10 and Table 11 that is not listed in Table 12 can be used directly inside a regular expression match operation.
Table 12: Rules Governing Regular Expression Symbols
String | Description |
? | [/\?/] if using as a regular expression and [/\\\?/] if using to match the character ? |
[ ] | [/\[\]/] if using as a regular expression and [/\\\[\\\]/] if using to match the characters [] |
$ | [/$/] if using as a regular expression and [/\\$/] if using to match the character $ |
\ | [/\\\\/] if using to match the character \ |
/ | [/\//] if using to match the character / |
‘ | [/\'/] if using to match the character ' |
* | [/\\*/] if using to match the character * |
. | [/\./] if using as a regular expression and [/\\\./] if using to match the character . |
+ | [/\\+/] if using to match the character + |
, | [/\,/] if using to match the character , |
^ | [/\\^/] if using to match the character ^ |
( | [/\\(/] if using to match the character ( |
) | [/\\)/] if using to match the character ) |
space | [/\ /] if using to match the character space |
The SR OS does not support a combination of a partial string with a regular expression match operation.
For example, if you want to display the SR-TE LSP names that begin with the string "RENO194_ATL" with part of the string entered directly and the rest of the string entered inside a regular expression, the command will return no match. The following example demonstrates incorrect syntax:
Include the entire string inside the regular expression itself to obtain a match. The following example demonstrates the correct syntax for finding a match:
2.8.10. Redirection
The SR OS supports redirection (“>”) which allows the operator to store the output of a CLI command as a local or remote file. Redirection of output can be used to automatically store results of commands in files (both local and remote).
For example:
In some cases, only part of the output might be applicable. The pipe/match and redirection commands can be combined:
This records only the RTT portion (including the word “time”).
2.9. VI Editor
The “vi”sual editor (vi) is a file editor that can edit any ASCII file. This includes configuration, exec files, BOF, and any other ASCII file on the system.
VT100 terminal mode is supported. However, if a different terminal mode is configured, there is no noticeable negative effect.
When a configuration file is changed, a validation check is executed to see if the user is allowed to view or perform configuration changes. When a user modifies the configuration file using the vi editor, these checks do not occur. Because of this, the vi editor is only available to a user with administrator privileges. Should others require access to the vi editor, their profile must be modified to allow the access. Access permission for the file directory where the file resides must be performed before a user can open, read, or write a file processing command. If a user does not have permission to access the directory, the operation is denied.
When opening a file, a resource check verifies that sufficient resources are available to process the file. If there are insufficient resources, the operation is denied and the operator is informed of that event.
Multiple sessions are allowed and are limited only by the memory resources available on the node.
2.9.1. Summary of vi Commands
The vi editor operates in two modes:
- Command mode — This mode causes actions to be taken on the file.In this mode, each character entered is a command that does something to the text file being edited; a character typed in the command mode may even cause the vi editor to enter the insert mode.
- Insert mode — Entered text is inserted into the file.In the insert mode, every character typed is added to the text in the file. Pressing ESC turns off the insert mode.
2.9.2. Using the vi Commands
Use the following commands to start and end vi edit sessions, move around in a file, enter new text, modify, move, and delete existing text, as well as read from and write to other files. The following tables list vi commands.
Table 13 describes the commands to cut, paste, and delete text.
Table 13: Cutting and Pasting or Deleting Text in vi
vi Command | Description |
" | Specify a buffer to be used with any of the commands using buffers. Follow the " character with a letter or a number, which corresponds to a buffer. |
d | Delete text. The “dd” command deletes the current line. A count specifies the number of lines to delete. Whatever is deleted is placed into the buffer specified with the " command. If no buffer is specified, then the general buffer is used. |
D | Delete to the end of the line from the current cursor position. |
p | Paste the specified buffer after the current cursor position or line. If no buffer is specified (with the " command), then 'p' uses the general buffer. |
P | Paste the specified buffer before the current cursor position or line. If no buffer is specified (with the " command), then “P” uses the general buffer. |
x | Delete the character under the cursor. A count specifies how many characters to delete. The characters will be deleted after the cursor. |
X | Delete the character before the cursor. |
y | Yank text, putting the result into a buffer. The “yy” command yanks the current line. Entering a number yanks that many lines. The buffer can be specified with the " command. If no buffer is specified, then the general buffer is used. |
Y | Yank the current line into the specified buffer. If no buffer is specified, then the general buffer is used. |
Table 14 describes the commands to insert new text.
Table 14: Inserting New Text
vi Command | Description |
A | Append at the end of the current line. |
I | Insert from the beginning of a line. |
O | Enter insert mode in a new line above the current cursor position. |
a | Enter insert mode, the characters typed in will be inserted after the current cursor position. A count inserts all the text that was inserted that many times. |
i | Enter insert mode, the characters typed in will be inserted before the current cursor position. A count inserts all the text that was inserted that many times. |
o | Enter insert mode in a new line below the current cursor position. |
Table 15 describes the commands to move the cursor within the file.
Table 15: Moving the Cursor Within the File
vi Command | Description |
^B | Scroll backwards one page. A count scrolls that many pages. |
^D | Scroll forwards half a window. A count scrolls that many lines. |
^F | Scroll forwards one page. A count scrolls that many pages. |
^H | Move the cursor one space to the left. A count moves that many spaces. |
^J | Move the cursor down one line in the same column. A count moves that many lines down. |
^M | Move to the first character on the next line. |
^N | Move the cursor down one line in the same column. A count moves that many lines down. |
^P | Move the cursor up one line in the same column. A count moves that many lines up. |
^U | Scroll backwards half a window. A count scrolls that many lines. |
$ | Move the cursor to the end of the current line. A count moves to the end of the following lines. |
% | Move the cursor to the matching parenthesis or brace. |
^ | Move the cursor to the first non-whitespace character. |
( | Move the cursor to the beginning of a sentence. |
) | Move the cursor to the beginning of the next sentence. |
{ | Move the cursor to the preceding paragraph. |
} | Move the cursor to the next paragraph. |
| | Move the cursor to the column specified by the count. |
+ | Move the cursor to the first non-whitespace character in the next line. |
- | Move the cursor to the first non-whitespace character in the previous line. |
_ | Move the cursor to the first non-whitespace character in the current line. |
0 | Move the cursor to the first column of the current line. |
B | Move the cursor back one word, skipping over punctuation. |
E | Move forward to the end of a word, skipping over punctuation. |
G | Go to the line number specified as the count. If no count is given, then go to the end of the file. |
H | Move the cursor to the first non-whitespace character on the top of the screen. |
L | Move the cursor to the first non-whitespace character on the bottom of the screen. |
M | Move the cursor to the first non-whitespace character on the middle of the screen. |
W | Move forward to the beginning of a word, skipping over punctuation. |
b | Move the cursor back one word. If the cursor is in the middle of a word, move the cursor to the first character of that word. |
e | Move the cursor forward one word. If the cursor is in the middle of a word, move the cursor to the last character of that word. |
h | Move the cursor one character position to the left. |
j | Move the cursor down one line. |
k | Move the cursor up one line. |
l | Move the cursor one character position to the right. |
w | Move the cursor forward one word. If the cursor is in the middle of a word, move the cursor to the first character of the next word. |
Table 16 describes the commands to move the cursor around the screen.
Table 16: Moving the Cursor Around the Screen
vi Command | Description |
^E | Scroll forwards one line. A count scrolls that many lines. |
^Y | Scroll backwards one line. A count scrolls that many lines. |
z | Redraw the screen with the following options. z<return> puts the current line on the top of the screen; z. puts the current line on the center of the screen; and z- puts the current line on the bottom of the screen. If you specify a count before the z command, it changes the current line to the line specified. For example, 16z. puts line 16 on the center of the screen. |
Table 17 describes the commands to replace text.
Table 17: Replacing Text
vi Command | Description |
C | Change to the end of the line from the current cursor position. |
R | Replace characters on the screen with a set of characters entered, ending with ESC. |
S | Change an entire line. |
c | Change until cc changes the current line. A count changes that many lines. |
r | Replace one character under the cursor. Specify a count to replace a number of characters. |
s | Substitute one character under the cursor, and go into insert mode. Specify a count to substitute a number of characters. A dollar sign ($) is placed at the last character to be substituted. |
Table 18 describes the commands to search for text or characters in the file.
Table 18: Searching for Text or Characters
vi Command | Description |
, | Repeat the last f, F, t or T command in the reverse direction. |
/ | Search the file downwards for the string specified after the /. |
; | Repeat the last f, F, t or T command. |
? | Search the file upwards for the string specified after the ?. |
F | Search the current line backwards for the character specified after the 'F' command. If found, move the cursor to the position. |
N | Repeat the last search given by / or ?, except in the reverse direction. |
T | Search the current line backwards for the character specified after the T command, and move to the column after the if it's found. |
f | Search the current line for the character specified after the f command. If found, move the cursor to the position. |
n | Repeat last search given by / or ?. |
t | Search the current line for the character specified after the t command, and move to the column before the character if it is found. |
Table 19 describes the commands to manipulate character and line formatting.
Table 19: Manipulating Character/Line Formatting
vi Command | Description |
~ | Switch the case of the character under the cursor. |
< | Shift the lines up to where to the left by one shiftwidth. << shifts the current line to the left, and can be specified with a count. |
> | Shift the lines up to where to the right by one shiftwidth. >> shifts the current line to the right, and can be specified with a count. |
J | Join the current line with the next one. A count joins that many lines. |
Table 20 describes the commands to save and quit.
Table 20: Saving and Quitting
vi Command | Description |
ZZ | Exit the editor, saving if any changes were made. |
Table 21 describes miscellaneous commands.
Table 21: Miscellaneous
vi Command | Description |
^G | Show the current filename and the status. |
^L | Clear and redraw the screen. |
^R | Redraw the screen removing false lines. |
^[ | Escape key. Cancels partially formed command. |
^^ | Go back to the last file edited. |
! | Execute a shell. Not supported |
& | Repeat the previous :s command. |
. | Repeat the last command that modified the file. |
: | Begin typing an EX editor command. The command is executed once the user types return. |
@ | Type the command stored in the specified buffer. |
U | Restore the current line to the previous state before the cursor entered the line. |
m | Mark the current position with the character specified after the 'm' command. |
u | Undo the last change to the file. Typing 'u' again will re-do the change. |
2.9.3. EX Commands
The vi editor is built upon another editor, called the EX. The EX editor only edits by line. From the vi editor you use the : command to start entering an EX command. The following list is not complete, however, it includes the most commonly used commands. If more than one line is to be modified by certain commands (such as :s and :w ), the range must be specified before the command. For example, to substitute lines 3 through 15, the command is :3,15s/from/this/g.
Table 22 describes the EX commands.
Table 22: EX commands
vi Command | Description |
:ab string strings | Abbreviation. If a word is typed in vi corresponding to string1, the editor automatically inserts the corresponding words. For example, the abbreviation :ab usa United States of America would insert the words, United States of America whenever the word usa is typed in. |
:map keys new_seq | Mapping. This lets you map a key or a sequence of keys to another key or a sequence of keys. |
:q | Quit vi. If there have been changes made, the editor will issue a warning message. |
:q! | Quit vi without saving changes. |
:s/pattern/to_pattern/options | Substitute. This substitutes the specified pattern with the string in the to_pattern. Without options, it only substitutes the first occurrence of the pattern. If a 'g' is specified, then all occurrences are substituted. |
:set [all] | Sets some customizing options to vi and EX. The :set all command gives all the possible options. |
:una string | Removes the abbreviation previously defined by :ab. |
:unm keys | Removes the remove mapping defined by :map. |
:vi filename | Starts editing a new file. If changes have not been saved, the editor will give you a warning. |
:w | Write out the current file. |
:w filename | Write the buffer to the filename specified. |
:w >> filename | Append the contents of the buffer to the filename. |
:wq | Write the buffer and quit. |
2.10. Configuration Rollback
The Configuration Rollback feature provides the ability to undo configuration and reverts back to previous router configuration states while minimizing impacts to services.
This feature gives the operator better control and visibility over the router configurations and reduces operational risk while increasing flexibility and providing powerful recovery options.
Configuration Rollback is useful in cases where configuration changes are made but the operator later decides not to keep the changes (for example, experimentation or when problems are identified in the configuration during actual network operation).
The advantages of this feature include the following:
- Changes made to router configuration are performed with minimal impact on services being provided by the SR by not being required to reboot the router.
- No impact in areas of configuration that did not change.
With the rollback feature, the operator can smoothly revert to previous configurations.
Configuration parameters that changed (or items that changed configuration have dependencies on) are first removed (revert to default), and the previous values are then restored (can be briefly service impacting in changed areas).
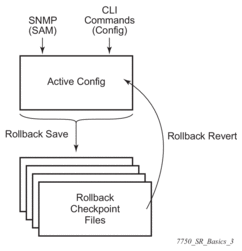
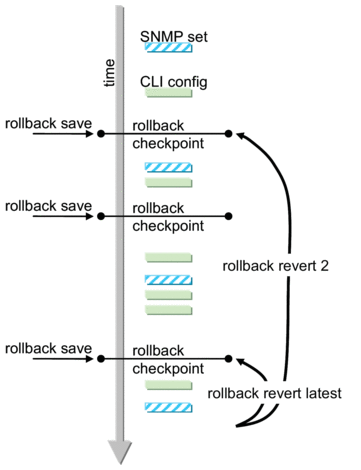
A history of changes is preserved (checkpoint IDs) that allows rollback to different points, as well as examination of changes made, as shown in Figure 3.
Figure 3: Rollback Operation
2.10.1. Feature Behavior
The following list describes detailed behavior and CLI usage of the rollback feature.
- The user can create a rollback checkpoint, and later, revert to this checkpoint with minimal impacts to services.admin>rollback# save [comment comment-string]comment-string: an 255 char comment associated with the checkpoint
- Rollback checkpoints include all current, operationally active configurations:
- Changes from direct CLI commands in the configuration branch.
- SNMP sets
- Rollback checkpoints do not include BOF configurations. The BOF file (and bof config) is not part of a rollback-save or rollback. A rollback does not change any of the BOF configuration. The BOF contains basic information for the node and does not change frequently (mostly during initial commissioning of the node).
- A rollback save feature can be automatically executed (for example, scheduled monthly) using the CRON facility of SR OS.
- The latest rollback checkpoint file uses a suffix of “.rb”. The next latest rollback checkpoint file has a suffix of “.rb.1”, the next oldest has a suffix of “rb.2”, and so on.file-url.rb <--- latest rollback filefile-url.rb.1…file-url.rb.9 <--- oldest rollback file
- When a rollback save is executed, the system shifts the file suffix of all the previous checkpoints by 1 (new id = old id + 1). If there are already as many checkpoint files as the maximum number supported then the last checkpoint file is deleted.
- The maximum number of rollback checkpoints is configurable and defaults to 10 (“latest” and 1 through 9, where checkpoint file 9 is deleted during the next rollback-save).
- The location and name of the rollback checkpoint files is configurable to be local (on compact flash) or remote. The file-url must not contain a suffix (just a path/directory + filename). The suffix for rollback checkpoint files is .rb and is automatically appended to rollback checkpoint files.config>system>rollback# rollback-location file-url
- There is no default rollback-location. If one is not specified (or it is cleared using no rollback-location) and a rollback save is attempted, the rollback save will fail and return an error message.
- The entire set of rollback checkpoint files can be copied from the active CPM CF to the standby CPM CF. This synchronization is done via the following command:admin>redundancy# rollback-sync
- The operator can enable an automatic synchronization of rollback checkpoint files between the active CPM and standby CPM. When this automatic synchronization is enabled, a rollback save will cause the new checkpoint file to be saved to both the active and standby. The suffixes of the old checkpoint files on both active and standby CPMs are incremented.The automatic sync only causes the new checkpoint file to be copied to both CFs (the other 9 checkpoints are not automatically copied from active to standby but that can be done manually with admin redundancy rollback-sync).config>redundancy# [no] rollback-sync
- config>redundancy>synchronize {boot-env | config} and admin>redundancy>synchronize {boot-env | config} do not apply to rollback checkpoint files. These commands do not manually or automatically sync rollback checkpoint files. The dedicated rollback-sync commands must be used to synchronize rollback checkpoint files.
- Rollback files can be deleted using a dedicated rollback checkpoint deletion command.admin>rollback# delete {latest-rb | checkpoint-id}
- Deleting a rollback checkpoint causes the suffixes to be adjusted (decremented) for all checkpoints older that the one that was deleted (to close the “hole” in the list of checkpoint files and create room to create another checkpoint)
- If config>redundancy>rollback-sync is enabled, a rollback delete will also delete the equivalent checkpoint on the standby CF and shuffle the suffixes on the standby CF.
- If an operator manually deletes a rollback checkpoint file (using file delete) then the suffixes of the checkpoint files are not shuffled, nor is the equivalent checkpoint file deleted from the standby CF. This manual deletion creates a “hole” in the checkpoint file list until enough new checkpoints have been created to roll the “hole” off the end of the list.
- As shown in Figure 4, support for rolling back to a previous configuration (a saved rollback checkpoint) with minimal impact on services. The previous configuration will be loaded and take operational effect.admin>rollback# revert [latest-rb | checkpoint-id]
Figure 4: Configuration Rollback
- A rollback revert does not affect the currently stored rollback checkpoint files (no deletions or renumbering). This means that if an operator issues the command rollback revert 3 and then issues the rollback save command, the resulting rollback checkpoint files “file-url.rb” and “file-url.rb.4” will contain the same rollback state/configuration.
- The boot-good-exec or bad-exec are not automatically executed after a rollback.
- Impacts to the running services are minimized during a rollback:
- no impact in areas of configuration that did not change
- configuration parameters that changed (or items that changed config have dependencies on) are first removed (revert to default) and the previous values are then restored (can be briefly service impacting in changed areas). Some examples are the following:
- If the currently active configuration contains configure port 5/1/1 dwdm tdcm dispersion -1000 and the rollback checkpoint contains configure port 5/1/1 dwdm tdcm dispersion -1010, then the operational dispersion will transition from -1000, to 0 and then back to -1010 for port 5/1/1, which will cause a traffic interruption.
- Changing the neighbor of an MC-APS port will start with neighbor 1, then be configured as no neighbor, and then configured with neighbor 2. Moving through the no neighbor intermediate state requires the working and protect circuits to be torn down and rebuilt. This impacts the 7450 ESS and 7750 SR.
- A rollback will undo any SNMP sets or direct CLI configuration commands that occurred since the last checkpoint creation.
- During the period when a node is processing a rollback revert, both CLI commands (from other users) and SNMP commands will continue to be processed. The only commands that are blocked during a rollback revert are other rollback commands including revert, save, and compare (only one rollback command can be executing at a time in one node).
- Commands are available to view and compare the various rollback checkpoints to current operating and candidate configurations.
- Rollback checkpoint files are not guaranteed to be in any particular format. They are not interchangeable with normal configuration files or executable scripts. A normal configuration file (from an admin save) cannot be renamed as a rollback checkpoint and then referenced for a rollback revert operation. Only rollback checkpoint files generated with rollback save can be used to rollback revert.
- If a hardware change is made after a rollback save, then:
- a rollback can be executed as long as the hardware change was an addition of hardware to the node (for example, added a new card or IOM into a previously empty slot).
- a rollback is not guaranteed to work if hardware was removed or changed (for example, XCM/IOM was removed, or XMA/MDA was swapped for a different XMA/MDA type).
- Rollback across a change to the following parameters is not supported:
- chassis-mode
- mixed-mode
- the SR | SS capability of a card (configure card capability sr | ess)
- configure isa application-assurance-group minimum-isa-generation
- Rollback is supported even after an admin reboot is performed (or the primary configuration in the BOF is changed and an admin reboot is performed). Admin reboot does not “break the chain” for rollback.
- Lawful Intercept configuration under the config>li branch is not affected by a rollback or rescue. LI configuration is not saved in the rollback checkpoint or rescue file, and a rollback revert does not affect any configuration under the config>li branch.
- Any configuration or state change performed under the debug branch of CLI is not saved in the rollback checkpoint file or impacted by a rollback.
- Rollbacks to a checkpoint created in a more recent release is not supported (for example, node running in 9.0r5 cannot rollback to a checkpoint created in 9.0r7).
- The following list captures some side effects and specific behaviors of a rollback revert. Some of these side effects are not related purely to configuration (that is, in the CLI configuration branch) and may have interactions with tools commands, RADIUS, and so on.
- SAA jobs that are running when a rollback revert is initiated, and need configuration changes due to the rollback, will be stopped. If the SAA job is a continuous type, then it will be restarted as part of the rollback revert after the configuration changes have been applied (just as if the operator had typed no shutdown for the continuous SAA job). Non-continuous SAA jobs that were modified by the rollback would need to be manually restarted if they need to be run again.
- If max-nbr-mac-addr is reduced as part of the revert and the number of MAC addresses in the forwarding database is greater than the max-nbr-mac-addr, then the rollback is aborted (before any actions are taken) and an informative error message is provided. The operator must take actions to remove the MAC addresses if they wish to proceed with the rollback.
- If active subscribers or subscriber hosts or DHCP lease states are present, some associated configuration changes may be blocked (just as those same changes would be blocked if an operator tried to make them via CLI – trying to delete an SLA profile being used by active subscriber hosts, or trying to change a NAT policy in a subscriber profile). If certain configuration changes associated with the hosts or lease states are required as part of the rollback but those changes are blocked, then for each blocked configuration item, a warning will be printed, that particular configuration item will not be changed and the rollback will continue. This is supported on the 7450 ESS and 7750 SR.
- After multi-chassis peer shutdown or configuration changes have occurred that affect the contents of the distributed database (for example, sync tag creation or deletion), further configuration changes related to that peer may be temporarily refused. The duration of the temporary configuration freeze will depend on the size of the distributed database. A rollback attempting to make those refused configuration changes will fail and an error message will be provided to the CLI user.
- If a force-switchover command (for example, tools perform service id 1 endpoint "x" force-switchover spoke-sdp-fec 1) has been applied to a spoke-sdp-fec of a dynamic multi-segment pseudo wire, and a rollback revert needs to change the admin state of the spoke-sdp-fec (for example, to modify spoke-sdp-fec parameters that may be dependent on the admin state), then the rollback revert will automatically remove the force-switchover and the node will revert to whatever is the best spoke-sdp in the redundant set.
- Rollback impacts the configuration state of the router, and as with normal operator CLI or SNMP configuration changes, additional actions or steps may need to occur before certain configuration changes take operational effect. Some examples include:
- Configuration changes that require a shutdown and then no-shutdown to be done by an operator in order to take operational effect also need this manual shut/no-shut to be performed by the operator in order to take operational effect after a rollback if the rollback changes those configuration items. Some examples include:
- Changes to Autonomous System or Confederation value require a BGP shut/no-shut.
- Changes to VPRN Max-routes require a shut/no-shut on the VPRN service.
- Changes to OSPF or ISIS export-limit require a shut/no-shut on OSPF or ISIS.
- Configuration changes to an MSAP policy that normally require a tools perform subscriber-mgmt eval-msap command to take operational effect on subscribers that are already active. Rollback will change the MSAP policy configuration, but if it is required to have the configuration changes applied to the active subscribers, then the operator will have to run the eval-msap tools command.
- Any uncommitted changes (for example, the begin command was entered, some changes made, but the commit command was never entered) in the following areas will be lost or cleared when a rollback revert is initiated:
- config>app-assure>group policy
- config>router>policy-options
- config>system>sync-if-timing
- Some card and mda commands require a reboot, remove or rebuild of an entire card or XMA/MDA. When these commands need to be executed as part of a rollback, the impacted cards and MDAs will be listed in a warning and the operator will be prompted with a single y/n prompt to decide whether to proceed. This prompting will not occur for a rollback initiated via SNMP, or if the operator uses the now keyword with the rollback revert command. Some examples of card and mda commands that may cause a prompt are:
- configure>card>card-type
- configure>card>named-pool-mode (7450 ESS and 7750 SR)
- configure>card>mda
- configure>card>mda>mda-type
- Although the use of the CTRL-C key combination is not recommended during a rollback revert, it is supported (via CLI or SNMP). Interrupting a rollback revert may leave the router in a state that is not necessarily something between the old active configuration and the rollback checkpoint, as the rollback processing may have been in the middle of tearing things down or rebuilding configurations. A strong warning is issued in this case to indicate that the operator must examine the configuration and potentially issue another rollback revert to return to a known (and coherent) configuration.
- An HA CPM switchover during a rollback revert will cause the rollback operation to abort. The newly active CPM will have an indeterminate configuration. When an HA switchover occurs during a rollback (or within a few seconds of a rollback completing), the operator is advised to repeat the rollback revert operation to the same checkpoint.
- A rollback revert operation does not check authorization of each command that is applied during the revert. Permission to execute the revert operation (authorization for the “admin rollback revert command itself) should only be given to users who are allowed to initiate a rollback revert. It is generally advised to only allow system administrators access to the file system where the rollback files are stored so that they cannot be manually edited.
2.10.2. Rollback and SNMP
The SR OS has SNMP support for rollback status and control. See the TIMETRA-SYSTEM-MIB for details (for example, items such as tmnxSysRollbackStarted).
When the router is doing a rollback revert, SNMP managers will see a tmnxSysRollbackStarted trap, then a rapid set of “config change” traps, and then finally, the tmnxSysRollbackStatusChange trap.
During the period when a router is processing a rollback revert, both CLI commands (from other users) and SNMP commands will continue to be processed.
2.10.3. Rescue Configuration
A special rescue configuration checkpoint can be created that an operator can revert to at any time. The rescue configuration has its own keyword (rescue) and does not use the same rolling suffix indices as the normal rollback checkpoints. This allows the operator to easily return to the rescue configuration state without having to consider a checkpoint index, and ensures that the rescue checkpoint is always available (and does not roll off the bottom of the list of checkpoints).
The operator should define a basic rescue configuration that is known to work and give correct management access to the node.
The location and filename of the rescue file are configurable. The SR OS appends an “.rc” suffix to the specified rescue filename.
2.10.4. Operational Guidelines
The following points offer some operational guidance on the usage of rollback.
- The admin save and admin rollback save commands should be performed periodically:
- The admin save command can be used to backup a complete configuration file that can be used during router reboot, with the following considerations:
- used with a reboot as a last resort
- performed after any major hardware changes or major service changes
- performed after any software upgrade
- The admin rollback save command can be used to create a rollback checkpoint as follows:
- to be used for intermediate checkpoints that can be recovered with minimal impacts to services
- to be performed each time that a moderate amount of configuration changes have been made
- to be performed after any hardware changes
- to be performed after any software upgrade
- to be scheduled with CRON (for example, once every one or two weeks)
- A new admin rollback save rescue must be created when hardware is changed.
- Rollback checkpoint files are not editable, or compatible or interchangeable with configuration files (generated with admin save).
- The repeated use of the admin rollback save, admin rollback delete, and admin rollback revert commands over the course of weeks or months is not recommended without also executing an occasional admin save. In a serious situation, use one of the saved configurations as the primary configuration for an admin reboot.
- For a software upgrade, it is recommended to create a Rollback Checkpoint (admin rollback save), in addition to saving the configuration (admin save), after an upgrade has been performed and the system is operating as expected. This ensures a good checkpoint that is fully compatible with the new release is available at a point shortly after the upgrade.
- An operator could create a set of rollback checkpoints to support busy or quiet days or weekends or weekdays and use CRON to shift between them.
- It is beneficial to create a rollback checkpoint before a rollback revert is initiated (especially if significant configuration changes have been applied since the last checkpoint was created). If the rollback is especially significant (a lot of major changes), it is also a good practice to perform an admin save in case a full reboot is required to recover from an issue.
- A rollback failure may occur in some limited cases where the node needs a long time to complete one of the resulting configuration changes. If a rollback (for example, rollback revert 5) fails during execution, it should be attempted again. The second attempt will typically complete the remaining configuration changes required to fully revert to the desired checkpoint.
- When a new backup CPM is commissioned, the user executes the admin redundancy rollback-sync command to copy the entire set of rollback files from the active CPM CF to the new standby CPM CF. If the operator wants the system to automatically copy new rollback checkpoints to both CFs whenever a new checkpoint is created, then the configure redundancy rollback-sync should be configured.
- An HA CPM switchover during a rollback revert will cause the rollback operation to abort. The newly active CPM will have an indeterminate configuration. A log event is created in this case to warn the operator. When an HA switchover occurs during a rollback (or within a few seconds of a rollback completing), the operator is advised to repeat the rollback revert operation to the same checkpoint.
- A rollback checkpoint stores the rollback location and the local- and remote-max-checkpoint values, and it is possible that a rollback revert operation can change those values. If an operator changes the local- or remote-max-checkpoint values, it is recommended to delete all the existing checkpoints to prevent a subsequent rollback revert from changing the maximum values to any of the previous values..
- If a warning prompt (y/n) is displayed when a rollback revert is initiated, it is highly suggested to respond no to the warning prompt the first time, save a rollback checkpoint before attempting this rollback revert, execute the revert again, and respond yes. If the rollback encounters problems, then a revert to the saved checkpoint can be used to return to the initial configuration state.
2.11. Transactional Configuration
Transactional configuration allows an operator to edit a candidate configuration (a set of configuration changes) without actually causing operational changes in the router (the active or operational configuration). Once the candidate configuration is complete, the operator can explicitly commit the changes and cause the entire new configuration to become active.
Transactional configuration gives the operator better control and visibility over their router configurations and reduce operational risk while increasing flexibility.
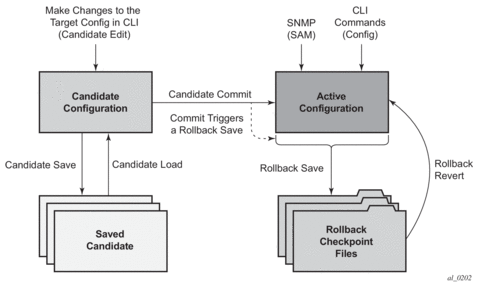
Transactional Configuration and Configuration Rollback support combine to provide the operational model depicted in Figure 5.
Figure 5: Router Configuration with Rollback and Transactions
2.11.1. Basic Operation
In order to edit the candidate configuration, the operator must first enter the candidate edit mode (edit-cfg). The operator can enter and quit the configuration mode as many times as they wish before finally committing the candidate.
In edit-cfg mode, the operator builds a set of candidate configuration changes using the same CLI tree as the standard (line-by-line non-transactional) configuration. Tab completion and keyword syntax checking is available.
Just as there is a single operational active configuration that can be modified simultaneously by multiple users in the SR OS, there is also a single global candidate configuration instance. All users make changes in the same global candidate configuration and a commit operation by any user will commit the changes made by all users.
Users have the ability to exclusively create a candidate configuration by blocking other users (and sessions of the same user) from entering edit-cfg mode.
If a commit operation is successful, then all of the candidate changes will take operational effect and the candidate is cleared. If there is an error in the processing of the commit, or a ‘commit confirmed’ is not confirmed and an auto-revert occurs, then the router will return to a configuration state with none of the candidate changes applied. The operator can then continue editing the candidate and try a commit later.
All commands in the candidate configuration must be in the correct order for a commit to be successful. Configuration that depends on other candidate objects must be placed after those objects in the candidate. A set of candidate editing commands (copy, insert, and so on) are available to correct and reorder the candidate configuration.
The edit-cfg mode is primarily intended for building a candidate configuration while navigating the configure branch of CLI. Many CLI commands in branches other than configure are supported while in edit-cfg mode, but access to some CLI branches and command are blocked including:
- exec command
- enable-admin command
- enable-dynamic-services-config command
- admin branch
- bof branch
- debug branch
- tools branch
The candidate configuration can be saved to a file and subsequently loaded into a candidate configuration. A saved candidate is similar to, but not the same as an SR OS configuration file generated with an admin save command. The saved candidate cannot be used in general as a configuration file and may not exec without failures.
There is no SNMP access to the candidate configuration and no SNMP management of candidates, although any configuration changes done via a transaction are reported via the standard SR OS SNMP change traps and basic candidate status information is available via SNMP.
Failure of a commit may be due to one or more of several reasons including:
- Misordering: The candidate configuration has changes that are not in the correct order (an object is referred to before it is actually created).
- Invalid options and combinations: Although many syntax errors are eliminated during the candidate editing process, the candidate configuration may contain combinations of configuration and options that are not valid and are rejected when the SR OS attempts to have them take operational effect.
- Out of resources: The application of the candidate may exhaust various system resources, such as queue resources.
Error messages that will help the operator to take necessary actions to correct the candidate are provided for commit failures.
Standard line-by-line (immediate operational effect upon pressing Enter) non-transactional CLI and SNMP commands are not blocked during the creation or editing of a candidate or the processing of a commit. These commands take immediate effect as normal.
2.11.2. Transactions and Rollback
By default, the SR OS will automatically create a new rollback checkpoint after a commit operation. The rollback checkpoint will include the new configuration changes made by the commit. An optional no-checkpoint keyword can be used to avoid the auto-creation of a rollback checkpoint after a commit. If the commit fails, then no new rollback checkpoint is created.
When the commit confirmed option is used then a rollback checkpoint is created after the processing of the commit and will exist whether the commit is automatically reverted or not.
Transactional configuration relies on the rollback mechanism to operate. Any commands and configurations that are not supported in a rollback revert are also not supported in edit-cfg mode; for example, changes to chassis-mode.
2.11.3. Authorization
Authorization works transparently in edit-cfg mode and no unique or new local profile or TACACS+ permissions rules are required (other than allowing access to the candidate branch). For example: if an operator has permissions to access the configure filter context, then they will automatically also have access to the configure filter context when in edit-cfg mode.
The candidate load and save operations (if the operator’s profile allows access to these commands) will load and save only those items that the user is authorized to access.
The candidate view will only display the items that the user is authorized to access.
The various candidate editing commands (such as adding lines, removing lines, delete, and so on) only allow operations on items that the user is authorized to access.
The candidate commit and discard operations (along with admin rollback revert) operate on the entire candidate and impact all items (authorization does not apply).