9. gRPC
gRPC is a modern, open-source, high-performance RPC framework that runs in any environment. In SR OS, this framework is used to implement the gRPC server, which can then be used for configuration management or telemetry.
The gRPC transport service uses HTTP/2 bidirectional streaming between the gRPC client (the data collector) and the gRPC server (the SR OS device). A gRPC session is a single connection from the gRPC client to the gRPC server over the TCP/TLS port.
The gRPC service runs on port 57400 by default in SR OS. The service is not configurable.
A single gRPC server supports concurrent gRPC sessions and channels.
- There is a maximum of eight concurrent gRPC sessions for all of the gRPC clients.
- There is a maximum of 225 concurrent gRPC channels for all of the gRPC clients.
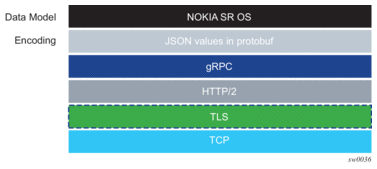
Figure 22 shows the gRPC protocol stack.
Figure 22: Protocol Stack
9.1. Security Aspects
9.1.1. TLS-Based Encryption
The gRPC server on SR OS can operate in two modes:
- without TLS encryption
- with TLS encryption
TLS encryption is used for added security. However, TLS encryption can be disabled in lab environments.
If TLS is not used, gRPC messages are not encrypted and user-names and passwords required in gRPC communication are visible to anyone capturing the packets. Therefore, Nokia recommends disabling TLS encryption only in a closed environment.
Before a gRPC connection will come up without TLS, the following conditions must both be met:
- no TLS server profile is assigned to the gRPC server
- the allow-unsecure-connection flag is set
The following summarizes the process of encryption:
- To use TLS encryption:
- The gRPC session must be in an encrypted state.
- If the gRPC client and gRPC server are unable to negotiate an encrypted gRPC session, the gRPC session fails and the gRPC server sends an error.
- Fallback from an encrypted to an unencrypted gRPC session is not allowed.
For information about how to configure TLS with gRPC, see the TLS chapter.
9.1.2. Authentication
User authentication is based on following principles:
- Each RPC sent by the gRPC client carries a username and password.
- For the first RPC in the gRPC session, the gRPC server tries to authenticate the user using the specified authentication order, such as using the local user database, RADIUS, or TACACS+.For example, if TACACS+ is first in the authentication order, the gRPC server sends a request to the TACACs+ server to authenticate the gRPC user.
- For the subsequent RPCs on that same authenticated gRPC session, the username and password are re-authenticated only if changed.
- When no username and password are provided with the RPC, the gRPC server returns an error.
- If the RPC user is changed, any active subscriber RPCs on that same gRPC session are terminated by the gRPC server.
- If the RPC password is changed, the active gRPC session will continue to exist until a different username and password is sent in a subsequent RPC, or the gRPC session is terminated.
- Each message is carried over a gRPC session that was previously encrypted; the session is not re-encrypted.
- SR OS device authentication
- The gRPC clients do not share gRPC sessions. Each gRPC client starts a separate gRPC session.
- When a gRPC session is established, the gRPC server certificates are verified by the gRPC client to ensure that every gRPC server is authenticated by the gRPC client.
- If gRPC is shut down on the gRPC server and a gRPC client is trying to establish a gRPC session, the gRPC client will get an error for every RPC sent.
- If gRPC is shut down on the gRPC server and a gRPC session is established, all active RPCs are gracefully terminated and an error is returned for every active RPC.
9.2. gNMI Service
gRPC Network Management Interface (gNMI) is a gRPC based protocol for network management functions, such as configuration and retrieval of information from network elements. In addition, it provides functionality necessary for supporting telemetry. gNMI service is specified in the OpenConfig forum.
9.2.1. gNMI Service Definitions
The SR OS gRPC server supports gNMI version 0.7.0, and in particular, the following RPC operations:
- Capability RPC
- Set/Get RPCs
- Subscribe RPC
As in NETCONF RPCs, gNMI RPCs that are sent to the SR OS system are logged in security log and they are marked as authorized, unauthorized, and accompanied including information such as username, time, RPC type, and IP address of the client.
9.2.1.1. Capability Discovery
In gNMI service, the client discovers the capabilities of the gRPC server through a Capability-Discovery RPC, which consists of “CapabiltyRequest” and “CapabilityResponse” messages.
During this message exchange, the gRPC server informs the client about following attributes:
- supported gNMI version
- supported models
- supported encodings
The SR OS server announces the supported models based on the configuration under config>system>management-interface>yang-modules. The supported models includes the NOKIA-YANG or OpenConfig (OC) models.
The advertised module names and organizations are as follows:
- nokia-conf, org = "Nokia"
- nokia-state, org = "Nokia"
- openconfig, org = "OpenConfig working group" (as specified by the 'organization' in the YANG models)
- version - the version number will be defined as follows:
- for NOKIA YANG models, the version number will correspond to an SR OS release number, for example, "16.0r1"
- for OC YANG models, the version number will correspond to a version number defined in "oc-ext:openconfig-version" that is included in the respective YANG models
- for OC-YANG models, including NOKIA deviations, the version number will correspond to an SR OS release number, for example, "16.0r1"
The following is an example of a “Capabilities Response Message”:
9.2.1.2. Get/Set RPC
Information is retrieved from the NE using GET RPC messages, which consists of “GetRequest” and “GetResponse” messages. The client asks for a given information by specifying following:
- A set of paths — all rules to a path definition apply, as specified in the gNMI specification
- Type — configuration, state, or operational data
- Encoding — in accordance to server advertisement during capability discovery
- Use_models — this message will be ignored
There is an upper limit on the size of the “GetResponse” message. This limit cannot exceed 100MB. If the limit is exceeded, the SR OS gRPC server responds with an error message.
In order to modify the information in an NE element, a SET gRPC message is used. This gRPC supports three types of transactions:
- delete
- replace
- update
9.2.1.3. Subscribe RPC
A subscription is initiated from the gRPC client by sending a Subscribe RPC that contains a "SubscribeRequest" message to the gRPC server. A prefix can be specified to be used with all paths specified in the "SubscribeRequest". If a prefix is present, it is appended to the start of every path to provide a full path.
A subscription contains:
- a list of one or more paths. The following conditions apply:
- A path represents the data tree as a series of repeated strings and elements. Each element represents a data tree node name and its associated attributes.
- A path must be syntactically valid within the set of schema modules that the gRPC server supports.
- The path list cannot be modified during the lifetime of the subscription.
- If the subscription path is to a container node, all child leafs of that container node are considered to be subscribed to.
- Any specified path must be unique within the list; paths cannot be repeated within the list. An error is returned if the same path is used more than one time in a single subscription.
- A specified path does not need to pre-exist within the current data tree on the gRPC server. If a path does not exist, the gRPC server continues to monitor for the existence of the path. Assuming that the path exists, the gRPC server transmits telemetry updates.
- The gRPC server does not send any data for a non-existent path; for example, if a path is non-existent at the time of subscription creation or if the path was deleted after the subscription was established.
- The maximum number of paths for all subscriptions on a single SR OS device is 14400. A path using a wildcard is still considered a single path.
- a subscription mode of one of the following types:
- ONCE mode — the server returns only one notification containing all information the client has subscribed to. In general, retrieving large amounts of information from the NE can be done using telemetry: “SubscribeRequest” message with ONCE subscription type.
- ON_CHANGE mode — the server returns notifications only when the value of the subscribed field changes. See ON_CHANGE Subscription Mode for more information.
- SAMPLE mode — the gRPC server sends notifications at the specified sampling interval
- TARGET_DEFINED mode — means ON_CHANGE for all states supporting ON_CHANGE notifications and SAMPLE mode for all other objects in the YANG tree
- a sample interval is supported for each path. If a sample interval of less than 1 s is specified, the gRPC server returns an error. If the sample interval is set to 0, the default value of 10 s is used. A sample interval is specified in nanoseconds (10 000 000 000 by default)
When a subscription is successfully initiated on the gRPC server, “SubscribeReponse” messages are sent from the gRPC server to the gRPC client. The “SubscribeResponse” message contains update notifications about the subscription's path list.
An update notification contains:
- a timestamp of the statistics collection time, represented in nanoseconds
- a prefix:
- If a prefix is present, it is logically appended to the start of every path to provide the full path.
- The presence of a prefix in the “SubscriptionResponse” message is not related to the presence of a prefix in the original “SubscriptionRequest” message. The prefix in the “SubscriptionResponse” message is optimized by the gRPC server.
- a list of updates (path and value pairs):
- A path represents the data tree path as a series of repeated strings or elements, where each element represents a data tree node name and its associated attributes. See Schema Paths for more information.
- The “TypedValue” message represents the data tree node’s value, where the encoding is “JSON” or “Bytes”, depending on the information in the “SubscribeRequest” message.
A sync response notification is sent one time, after the gRPC server sends all of the updates for the subscribed-to paths. The sync response must be set to “true” for the gRPC client to consider that the stream has synced one time. A sync response is used to signal the gRPC client that it has a full view of the subscribed-to data.
The gRPC server sends an error if required. The error contains a description of the problem.
9.2.1.3.1. Bytes Encoding
Bytes encoding is performed by the gRPC server, which encodes the values of the leafs as typed values. Table 117 lists the mapping of the individual YANG types to the typed values defined in the gNMI specification in the GitHub repository.
Table 117: Mapping of YANG Types to gNMI-specified Typed Values
YANG Type | Typed Value |
binary | bytes_val |
bits | string_val |
boolean | bool_val |
decimal64 | decimal_val |
empty | bool_val |
enumeration | string_val |
identityref | string_val |
instance-identifier | string_val |
int8 | int_val |
int16 | int_val |
int32 | int_val |
int64 | int_val |
leafref | type of referenced leaf |
string | string_val |
uint8 | uint_val |
uint16 | uint_val |
uint32 | uint_val |
uint64 | uint_val |
union | type of active union member |
9.2.1.3.2. ON_CHANGE Subscription Mode
SR OS supports ON_CHANGE subscription mode. This subscription mode indicates that Notification messages are sent as follows:
- after the “SubscriptionRequest” message is received
- every time the corresponding leaf value is changed
The notification message, as a response to an ON_CHANGE subscription, always contains the new value of the corresponding leaf, as defined in gNMI specification.
The ON_CHANGE subscription is supported for all configuration events as well as for selected state leafs. The tools command can display all state leafs supporting the ON_CHANGE subscription.
ON_CHANGE subscription is accepted for all valid paths. The server sends ON_CHANGE notifications only for leafs within this path that support ON_CHANGE notifications.
9.2.1.4. Schema Paths
Telemetry subscriptions include a set of schema paths used to identify which data nodes are of interest to the collector.
The paths in Telemetry Subscribe RPC requests follow the basic conventions described in the OpenConfig gnmi-path-conventions.md published on github.com (version 0.2.0 from February 24th, 2017).
A path consists of a set of path segments often shown with a “/” character as a delimiter; for example, /configure/router[router-instance=Base]/interface[interface-name=my-interface1]/description.
These paths are encoded as a set of individual string segments in gnmi.proto (without any “/” characters); for example, ["configure", "router[router-instance=Base]", "interface[interface-name=my-interface1]", "description"].
A path selects an entire subtree of the data model and includes all descendants of the node indicated in the path. Table 118 describes the types of schema paths that are supported in SR OS telemetry.
Table 118: Schema Paths
Path example | Description |
/configure/router[router-instance=Base]/interface[interface-name=abc] | Selects all config leafs of interface abc and all descendants. |
/configure/router[router-instance=Base]/interface[interface-name=abc]/description | Selects only the description leaf of interface abc. |
/state/router[router-instance=Base]/interface[interface-name=*] | Selects all state information for all base router interfaces using a wildcard in a single segment of a path. |
/configure/router[router-instance=Base]/interface[interface-name=*]/description | Selects all state information for all base router interfaces using a wildcard in a single segment of a path. |
/ | The root path. This selects all config and state data from all models (in all namespaces) supported on the router. Encoded as “” in gRPC/gPB. |
The following list describes types of telemetry paths that are not supported in SR OS.
- Wildcards for entire path segments are not supported.For example: /state/service/*/oper-status
- If a wildcard is used for any key of a list, a wildcard must be used for all the keys of that list. In a single path segment, all the keys must either have specific values or all the keys must have wildcards. A mix of wildcards and specific values for different parts of a list key is not supported.For example:Supported:/a/b[key1=*][key2=*]/c[key1=foo]/a/b[key1=foo][key2=bar]/c[key1=*]Not supported:/a/b[key1=foo][key2=*]
- Functions such as “current()”, “last()” and mathematical operators, such as stat<5 or octets>3 are not supported in paths. The “|” (OR operator, used to select multiple paths) is not supported.
- The “//” wildcard pattern is not supported.For example: /state//oper-status
The following list describes types of telemetry paths that are supported in SR OS.
- Wildcards in multiple segments of a path are supported.For example: /state/card[slot-number=*]/mda[mda-slot=*]
9.2.2. gNMI Service Use Cases
The gNMI Service can be used for the following:
- Telemetry
- NE Configuration Management
9.2.2.1. Telemetry
Telemetry is a network monitoring and fault management framework. Telemetry is driven by the need to use fresh data obtained from the network to make fast networking decisions such as traffic optimization and preventative troubleshooting.
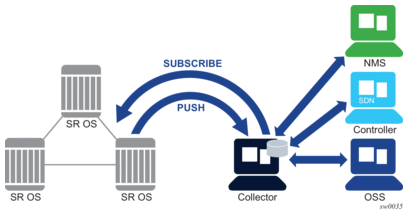
Unlike legacy monitoring platforms such as SNMP, telemetry does not only rely on continuously pulling data from the network devices. Instead, network devices push and stream data (such as statistics) continuously to data collectors based on subscriptions. The data collectors can then filter, analyze, store, and make decisions using the collected data from the network devices. Figure 23 shows a telemetry application.
Figure 23: Telemetry Application
9.2.2.1.1. Telemetry Examples
This section contains examples of Telemetry subscription requests and responses. The following examples are dumps of protobuf messages from a Python API. Formats may vary across different implementations.
Example 1 — Subscribe to a single path
Example 2 — Subscribe to a single path with wildcard
Example 3: Subscribe to more than one path
Example 4: Subscribe to a list with wildcard
Example 5: Subscribe to path where the object did not exist before subscription
Example 6: Subscribe to a path where the object existed before subscription then was deleted after subscription
9.2.2.2. NE Configuration Management
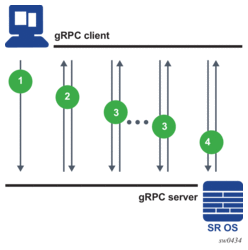
Figure 24 shows NE configuration and information retrieval using the gNMI service.
Figure 24: NE Configuration and Information Retrieval using gNMI Service
In the context of gNMI, every SET RPC appears as an single commit operation, regardless of the number of paths included in the message. Both, NOKIA and OC models are supported by gNMI SET/GET RPC.
An example of the SET RPC command (including the response message from the gRPC server) follows:
An example of the GET RPC command (including the response message from the gRPC server) follows:
9.3. gNOI Services
The gRPC Network Operations Interface (gNOI) defines a set of gRPC-based micro-services for executing operational commands on network devices. This includes the gNOI CERT service, that provides certificate management. The individual RPCs and messages that perform the operations required for certificate management on the node are defined in the Git repository hosting service (GitHub).
9.3.1. Certificate Management for TLS Connections
This section describes the gNOI services certificates that SR OS supports for managing secure TLS connections.
The SR OS supports the following RPCs for managing certificates for secure TLS connections:
- RPC GetCertificates
- RPC CanGenerateCSR
- RPC Rotate
- RPC Install
| Note: The gNOI RPCs, are by default, disabled in the user profile. |
9.3.1.1. RPC GetCertificates
RPC GetCertificates provide information to the controller about all active certificates on the server (SR OS node). Figure 25 shows the message sequence.
Figure 25: RPC GetCertificates Message Flow
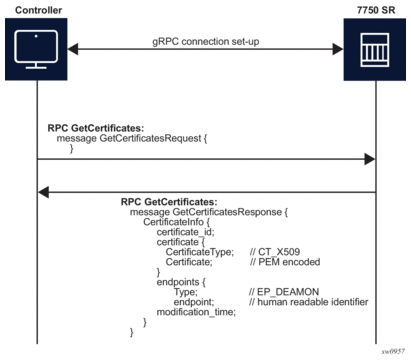
The RPC GetCertificates messages include a GetCertificateRequest and a GetCertificateRespone message. The GetCertificatesResponse message shown in Figure 25 includes the following:
- certificate_id — The SR OS uses a certificate file name as the certificate ID.
- CertificateType — This is always set to X509, because it is the only type that the SR OS supports.
- endpoint — Indicates which of the CERT profiles in the SR OS node use this certificate; if multiple CERT profiles use the certificate, the names are concatenated with the separation character “/”.
9.3.1.2. RPC CanGenerateCSR
The RPC CanGenerateCSR message can be used to determine if the gRPC server (SR OS node) can generate a Certificate Signing Request (CSR). It is a simple request and response operation as shown in Figure 26.
Figure 26: RPC CanGenerateCSR Message Flow
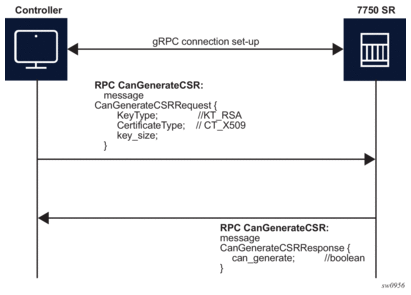
The SR OS only supports RSA keys and X509 certificates, so it only responds positively if those values are filled in the respective fields. The key size must be between 512 and 8192. In all other cases, the SR OS responds negatively to the CanGenerateCSRRequest message.
9.3.1.3. RPC Rotate
RPC Rotate allows the controller to rotate an active certificate on the server. After the rotation is completed, a new certificate can be used without affecting existing TLS connections.
The following two cases are supported for a certificate rotation:
The SR OS supports both possibilities, although it is assumed that in most cases the CSR is generated on SR OS node.
The following steps apply to both scenarios:
- Generate the CSR
- Sign the CSR by the Certificate Authority (CA)
- Load the new certificate on the server
- Verify the new certificate by creating a new connection
- Finalize by confirming that the new certificate is being used
After the RPC Rotate is completed, all new connections use new keys.
Figure 27: RPC Rotate Message Flow (CSRs Generated on the SR OS Node)
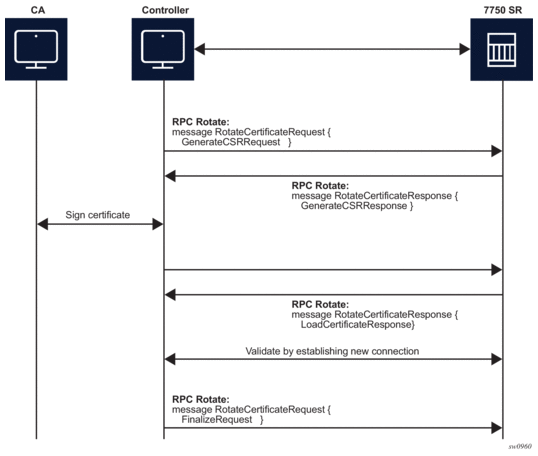
Figure 28: RPC Rotate Message Flow (no CSRs Generated on the SR OS Node)
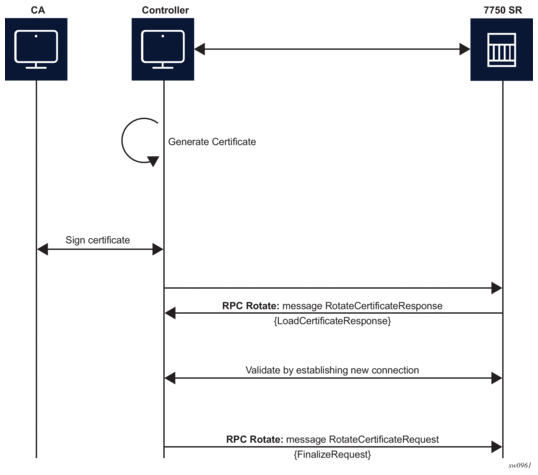
From the perspective of the interaction of the controller and the server (SR OS) two stages are the most important:
- message exchange for the CSR generation
- message exchange to load the new certificates on the server
Figure 29 shows a detailed content of the messages that are exchanged for CSR generation. The SR OS accepts requests only for the X509 certificate type, RSA key type, and a minimum key length of 512 bits.
Figure 29: GenerateCSR Message Flow
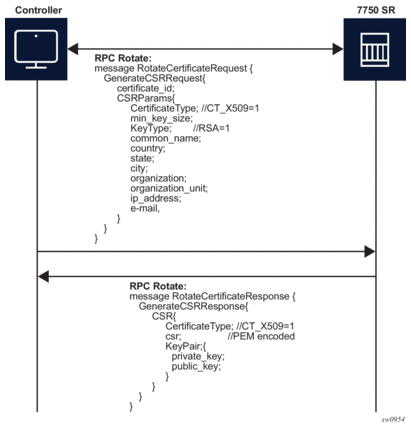
For RPC Rotate, the certificate_id points to an existing certificate on the node. All the other parameters in the GenerateCSRRequest message are not checked by the SR OS software explicitly. They are used by the internal API to generate the CSR and that result is transparently passed to the controller.
After the CA signs the certificates, the files are loaded to the server using LoadCSRRequest and LoadCSRResponse messages that are exchanged as shown in Figure 30. If this message exchange is used in the context of RPC Rotate, the certificate_id should not be present in LoadCSRRequest message. When the SR OS receives the message, it performs all the necessary steps to load this certificate, including storing the certificate and key files on the disk.
Figure 30: LoadCSRRequest/Response Message Flow
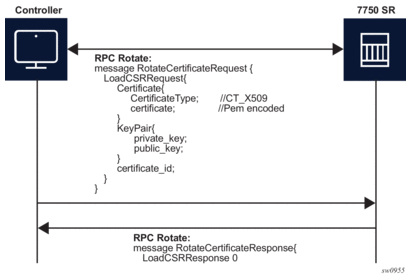
The controller is responsible for verifying the connection with the new certificate (Step 4 in Figure 27 and Figure 28); SR OS considers this as an optional step.
After the whole RPC is successfully closed, the system can use the new certificate to start new TLS connections.
9.3.1.4. RPC Install
The controller can use RPC Install to install a new certificate on the server. After the certificate is installed, the server must be configured (assign a certificate and key files in the CERT profile) before the new certificate can be used.
The following two possible cases are supported for installing a certificate:
The SR OS supports both possibilities, although it is assumed that in most cases the CSR is generated on SR OS node.
Both scenarios have multiple steps:
- Generate the CSR
- Sign the CSR by the Certificate Authority (CA)
- Load the new certificate on the server
Figure 31: RPC Install Message Flow (CSRs Generated on the SR OS Node)
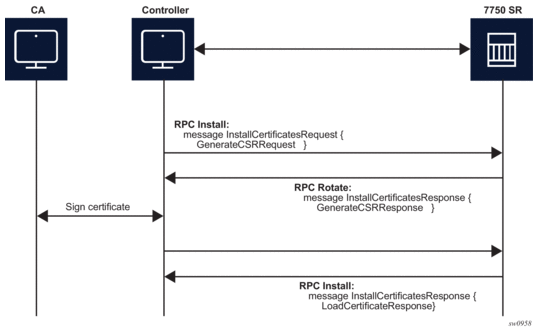
Figure 32: RPC Install Message Flow (no CSRs Generated on the SR OS Node)
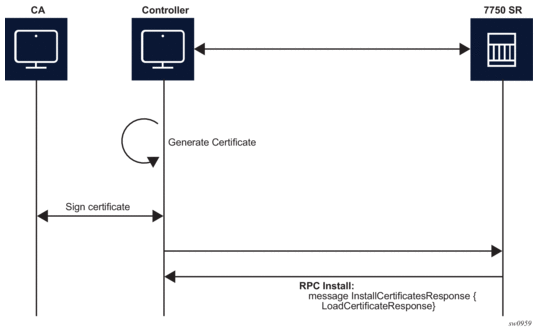
The messages that are exchanged during phases 1 and 3 are the same as shown in Figure 29 and Figure 30. The only difference, in the case of RPC Install, is that, a new certificate_id is used.
After new certificates are installed, the system must be configured before it can be used. Configuration is supported using the following methods:
- an existing gRPC session
- a CLI session, SNMP, and/or NETCONF
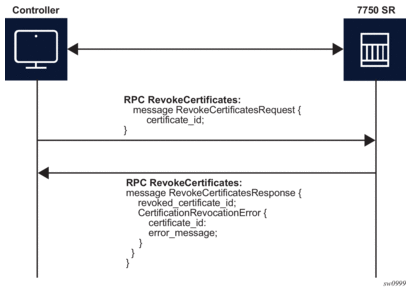
9.3.1.5. RPC RevokeCertificates
The purpose of the RPC RevokeCertificates is to render the existing certificate unusable by any client. In cases where the certificate being revoked by the client does not exist on a SR OS, the corresponding RPC silently succeeds. The message flow is shown in Figure 33.
Figure 33: RPC RevokeCertificates Message Flow