7.2. Configuring Triple Play Security with CLI
7.2.1. Common Configuration Tasks
7.2.1.1. Configuring Anti-Spoofing Filters
Anti-spoofing filters are used to prevent malicious subscribers from sending IP packets with a forged IP or MAC address, and thus mis-directing traffic. The anti-spoofing filter is populated from the DHCP lease state table, and DHCP snooping must be enabled on the SAP.
There are three types of filters (MAC, IP, and IP+MAC). One type is allowed per SAP.
The following displays an IES service interface configuration with anti-spoofing.
7.2.1.2. Configuring Triple Play Security Features
7.2.1.2.1. Configuring MAC Pinning
The following example displays a partial BSA configuration with MAC pinning enabled on a SAP.
7.2.1.2.2. Configuring MAC Protection
7.2.1.2.2.1. Preventing Access By Residential Subscribers Using Protected (Gateway) MAC Addresses
The first step is to create a list of MAC addresses to be protected. The second step is to prevent access using these source addresses inside an SHG or a SAP.
The following example displays a partial BSA configuration with some protected MAC addresses on any SAP created inside the SHG.
7.2.1.2.2.2. Restricting Access By Residential Subscribers To a Small List Of Upstream MAC Addresses
The first step is to create a list of MAC addresses to be protected. The second step is to restrict access to these addresses only from an SHG or a SAP (if the MAC address of an upstream server is not known, it can be discovered using, for example, the CPE ping OAM tool).
The following example displays a partial BSA configuration with restricted access to some MAC addresses from a specified SAP (an unrestricted access from any other SAP within the VPLS).
7.2.1.2.3. Configuring VPLS Redirect Policy
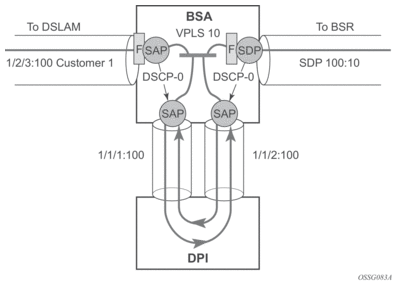
Figure 48 displays an IP filter entry configuration for VPLS redirect policy.
Figure 48: VPLS Redirect Policy Example
Information about defining and applying IP and MAC filters is described in the 7450 ESS, 7750 SR, 7950 XRS, and VSR Router Configuration Guide.
7.2.1.2.3.1. Creating the Filter
The following displays a redirect filter entry:
7.2.1.2.3.2. Applying the Filter to a VPLS Service
The following displays how the redirection filter configured above is assigned to the ingress SAP from the DSLAM, and the ingress SDP from the BSR:
7.2.1.3. Configuring ARP Handling
7.2.1.3.1. Configuring Proxy ARP
The implementation of proxy ARP with support for local proxy ARP allows the 7450 ESS or 7750 SR to respond to ARP requests in the subnet assigned to an IES or VPRN interface.
Configuring this command allows multiple customers to share the same IP subnet.
The following example displays an IES proxy ARP configuration:
7.2.1.3.2. Configuring Local Proxy ARP
When local proxy ARP is enabled on an IP interface, the 7450 ESS or 7750 SR responds to all ARP requests for IP addresses belonging to the subnet with its own MAC address, and forwards all traffic between hosts in that subnet. Local proxy ARP is disabled by default.
| Note: When local-proxy-arp is enabled under a IES or VPRN service, all ICMP redirects on the ports associated with the service are automatically blocked. This prevents users from learning each other's MAC address (from ICMP redirects). |
The following example displays a local proxy ARP IES configuration:
7.2.1.3.3. Configuring ARP Reply Agent in a VPLS Service
When ARP reply agent is enabled, the 7450 ESS or 7750 SR responds to ARP requests from the network, with information from the DHCP lease state table.
In the upstream direction (toward the network), the ARP reply agent intercepts ARP requests on subscriber SAPs, and checks them against the DHCP lease state table. The purpose is to prevent a malicious subscriber spoofing ARP request or ARP reply messages and thus populating the upstream router's ARP table with incorrect entries.
The following example displays a partial BSA configuration with ARP Reply Agent enabled on a SAP:
7.2.1.3.4. Configuring Remote Proxy ARP
The following example displays the IES configuration to enable remote proxy ARP:
7.2.1.3.5. Configuring Automatic ARP Table Population in an IES or VPRN Interface
The following example displays the IES DHCP configuration to enable automatic population of the ARP table using snooped DHCP information on an IES or VPRN (VPRN is supported on the 7750 SR only) interface:
7.2.1.3.6. Configuring CPU Protection
CPU Protection can be used to protect the SR OS in subscriber management scenarios. Refer to the 7450 ESS, 7750 SR, 7950 XRS, and VSR System Management Guide for information about CPU Protection operation and configuration.
7.2.1.4. Configuring Web Portal Redirect
The generic CLI structure for defining and applying IP and MAC filters is described in the 7450 ESS, 7750 SR, 7950 XRS, and VSR Router Configuration Guide.
The following example displays an IP filter entry configuration for web-portal redirect:
- Filter entry 10 in the example output allows the customer to access DNS to get the IP address of the original website they are trying to view.
- Entry 20 allows HTTP packets destined to the captive portal itself to be forwarded.

Note: The actual IP address (a.b.c.d) must be entered, not the DNS name (“www.myportal.com”). The IP address can be easily resolved from the 7450 ESS or 7750 SR CLI using the ping command.
- Entry 30 (which is the last option that does not drop the customer packets) checks for HTTP protocol and then starts the redirection process:
- The 7450 ESS or 7750 SR intercepts the HTTP GET from the subscriber and respond with an HTTP 302 (temporarily moved) with the URL configured in the filter entry. This URL can contain some variables, notably the customer IP and MAC addresses to allow the portal to create an entry for the customer. The original requested URL is also included to redirect the client site back to the original requested site when the process is done.
- The client then closes the connection with the original IP address and open a connection to the redirected server. Entry 20 allows this connection.
The following displays how the redirection filter configured above is assigned to an ingress SAP: