7. Event and Accounting Logs
7.1. Logging Overview
The two primary types of logging supported in the OS are event logging and accounting logs.
Event logging controls the generation, dissemination and recording of system events for monitoring status and troubleshooting faults within the system. The OS groups events into four major categories or event sources.
- Security events — Events that pertain to attempts to breach system security.
- Change events — Events that pertain to the configuration and operation of the node.
- Main events — Events that pertain to applications that are not assigned to other event categories/sources.
- Debug events — Events that pertain to trace or other debugging information.
Events within the OS and have the following characteristics:
- A time stamp in UTC or local time.
- The generating application.
- A unique event ID within the application.
- A router name (also called a vrtr-name) identifying the associated routing context (for example, Base or vprn1000).
- A subject identifying the affected object for the event (e.g. interface name or port identifier).
- A short text description.
Event control assigns the severity for each application event and whether the event should be generated or suppressed. The severity numbers and severity names supported in the OS conform to ITU standards M.3100 X.733 & X.21 and are listed in Table 34.
Table 34: Event Severity Levels
Severity Number | Severity Name |
1 | cleared |
2 | indeterminate (info) |
3 | critical |
4 | major |
5 | minor |
6 | warning |
Events that are suppressed by event control will not generate any event log entries. Event control maintains a count of the number of events generated (logged) and dropped (suppressed) for each application event. The severity of an application event can be configured in event control.
An event log within the OS associates the event sources with logging destinations. Examples of logging destinations include the console session, a specific telnet or SSH session, memory logs, file destinations, SNMP trap groups and syslog destinations. A log filter policy can be associated with the event log to control which events will be logged in the event log based on combinations of application, severity, event ID range, router name (vrtr-name), and the subject of the event.
The OS accounting logs collect comprehensive accounting statistics to support a variety of billing models. The routers collect accounting data on services and network ports on a per-service class basis. In addition to gathering information critical for service billing, accounting records can be analyzed to provide insight about customer service trends for potential service revenue opportunities. Accounting statistics on network ports can be used to track link utilization and network traffic pattern trends. This information is valuable for traffic engineering and capacity planning within the network core.
Accounting statistics are collected according to the parameters defined within the context of an accounting policy. Accounting policies are applied to customer Service Access Points (SAPs) and network ports. Accounting statistics are collected by counters for individual service queues defined on the customer’s SAP or by the counters within forwarding class (FC) queues defined on the network ports.
The type of record defined within the accounting policy determines where a policy is applied, what statistics are collected and time interval at which to collect statistics.
The supported destination for an accounting log is a compact flash system device. Accounting data is stored within a standard directory structure on the device in compressed XML format. It is recommended that accounting logs be configured on the cf1: or cf2: devices only. Accounting log files are not recommended on the cf3: device (cf3: is intended to be used primarily for software images and configuration related files).
7.1.1. Logging Using the Management VPRN
When a management VPRN is configured, all authentication, authorization, and accounting servers, DNS server, or syslog servers are reachable using this management VPRN. The user can configure a syslog server within the management VPRN, log all SR OS events, and direct the logs to this syslog server. The command config>log>services-all-events service id enables the logging of all events under the management VPRN specified by the service ID. Within the specified VPRN, the command config>service>vprn>log>log-id>from directs the logs from the specified event sources (main, change, security, or debug-trace) to be saved at the log ID destination specified by the config>service>vprn>log>log-id>to command.
7.2. Log Destinations
Both event logs and accounting logs use a common mechanism for referencing a log destination. Routers support the following log destinations:
Only a single log destination can be associated with an event log or with an accounting log. An event log can be associated with multiple event sources, but it can only have a single log destination.
A file destination is the only type of log destination that can be configured for an accounting log.
7.2.1. Console
Sending events to a console destination means the message will be sent to the system console The console device can be used as an event log destination.
7.2.2. Session
A session destination is a temporary log destination which directs entries to the active telnet or SSH session for the duration of the session. When the session is terminated, for example, when the user logs out, the “to session” configuration is removed. Event logs configured with a session destination are stored in the configuration file but the “to session” part is not stored. Event logs can direct log entries to the session destination.
7.2.3. CLI Logs
A CLI log is a log that outputs log events to a CLI session. An operator can subscribe to a CLI log from within a CLI session using the tools perform log subscribe-to log-id command. The events are sent to the CLI session for the duration of that CLI session (or until an unsubscribe-from command is issued).
7.2.4. Memory Logs
A memory log is a circular buffer. When the log is full, the oldest entry in the log is replaced with the new entry. When a memory log is created, the specific number of entries it can hold can be specified, otherwise it will assume a default size. An event log can send entries to a memory log destination.
7.2.5. Log Files
Log files can be used by both event logs and accounting logs and are stored on the compact flash devices in the file system. I
A log file is identified with a single log file ID, but a log file will generally be composed of a number individual files in the file system. A log file is configured with a rollover parameter, expressed in minutes, which represents the length of time an individual log file should be written to before a new file is created for the relevant log file ID. The rollover time is checked only when an update to the log is performed. Thus, complying to this rule is subject to the incoming rate of the data being logged. For example, if the rate is very low, the actual rollover time may be longer than the configured value.
The retention time for a log file specifies the amount of time the file should be retained on the system based on the creation date and time of the file.
When a log file is created, only the compact flash device for the log file is specified. Log files are created in specific subdirectories with standardized names depending on the type of information stored in the log file.
Event log files are always created in the \log directory on the specified compact flash device. The naming convention for event log files is:
log eeff-timestamp
where:
ee is the event log ID
ff is the log file destination ID
timestamp is the timestamp when the file is created in the form of yyyymmdd-hhmmss where:
yyyy is the four-digit year (for example, 2007)
mm is the two digit number representing the month (for example, 12 for December)
dd is the two digit number representing the day of the month (for example, 03 for the 3rd of the month)
hh is the two digit hour in a 24-hour clock (for example, 04 for 4 a.m.)
mm is the two digit minute (for example, 30 for 30 minutes past the hour)
ss is the two digit second (for example, 14 for 14)
Accounting log files are created in the \act-collect directory on a compact flash device (specifically cf1 or cf2). The naming convention for accounting log files is nearly the same as for log files except the prefix act is used instead of the prefix log. The naming convention for accounting logs is:
act aaff-timestamp.xml.gz
where:
aa is the accounting policy ID
ff is the log file destination ID
timestamp is the timestamp when the file is created in the form of yyyymmdd-hhmmss where:
yyyy is the four-digit year (for example, 2007)
mm is the two digit number representing the month (for example, 12 for December)
dd is the two digit number representing the day of the month (for example, 03 for the 3rd of the month)
hh is the two digit hour in a 24-hour clock (for example, 04 for 4 a.m.)
mm is the two digit minute (for example, 30 for 30 minutes past the hour)
ss is the two digit second (for example, 14 for 14 seconds)
Accounting logs are .xml files created in a compressed format and have a .gz extension.
The \act-collect directory is where active accounting logs are written. When an accounting log is rolled over, the active file is closed and archived in the \act directory before a new active accounting log file created in \act-collect.
When creating a new log file on a Compact Flash disk card, the system will check the amount of free disk space and that amount must be greater than or equal to the lesser of 5.2 MB or 10% of the Compact Flash disk capacity.
7.2.6. SNMP Trap Group
An event log can be configured to send events to SNMP trap receivers by specifying an SNMP trap group destination.
An SNMP trap group can have multiple trap targets. Each trap target can have different operational parameters.
A trap destination has the following properties:
- The IP address of the trap receiver.
- The UDP port used to send the SNMP trap.
- SNMP version (v1, v2c, or v3) used to format the SNMP notification.
- SNMP community name for SNMPv1 and SNMPv2c receivers.
- Security name and level for SNMPv3 trap receivers.
For SNMP traps that will be sent out-of-band through the Management Ethernet port on the SF/CPM, the source IP address of the trap is the IP interface address defined on the Management Ethernet port. For SNMP traps that will be sent in-band, the source IP address of the trap is the system IP address of the router.
Each trap target destination of a trap group receives the identical sequence of events as defined by the log ID and the associated sources and log filter applied.
7.2.7. Syslog
7.2.7.1. Syslog Implementation Overview
An event log can be configured to send events to one syslog destination. Syslog destinations have the following properties:
- Syslog server IP address
- UDP port or TLS profile used to send the syslog message
- Syslog Facility Code (0 to 23) (default 23 - local 7)
- Syslog Severity Threshold (0 to 7); sends events exceeding the configured level
Because syslog uses eight severity levels whereas the router uses six internal severity levels, the severity levels are mapped to syslog severities. The following table describes the severity level mappings to syslog severities.
Table 35: Router to Syslog Severity Level Mappings
SR OS Event Severity | Syslog Severity Numerical Code | Syslog Severity Name | Syslog Severity Definition |
— | 0 | emergency | System is unusable |
critical (3) | 1 | alert | Action must be taken immediately |
major (4) | 2 | critical | Critical conditions |
minor (5) | 3 | error | Error conditions |
warning (6) | 4 | warning | Warning conditions |
— | 5 | notice | Normal but significant condition |
cleared (1) indeterminate (2) | 6 | info | Informational messages |
— | 7 | debug | Debug-level messages |
The general format of an SR OS syslog message is as follows (see RFC 3164, The BSD Syslog Protocol):
<PRI> <HEADER><MSG>
| Note: The “<” and “>” are informational delimiters to make reading and understanding the format easier and they do not appear in the actual syslog message except as part of the PRI. |
where:
- <PRI> (the “<” and “>” are included in the syslog message) is the configured facility*8+severity (as described in the 7450 ESS, 7750 SR, 7950 XRS, and VSR System Management Guide and RFC 3164).
- <HEADER> is "MMM DD HH:MM:SS <source IP addr>" (without the quotes). There are always 2 characters for the day (DD). Single digit days are preceded with a space character.
- <MSG> is <log-prefix>: <seq> <vrtr-name> <application>-<severity>-<Event Name>-<Event ID> [<subject>]: <message>\n
- <log-prefix> is an optional 32 characters of text (default = 'TMNX') as configured in the log-prefix command.
- <seq> is the log event sequence number (always preceded by a colon and a space char)
- <vrtr-name> is vprn1, vprn2, … | Base | management | vpls-management
- <subject> may be empty resulting in []:
- \n is the standard ASCII new line character (hex 0A)
Examples (from different nodes)
default log-prefix (TMNX):
no log-prefix:
log-prefix "test":
7.2.7.2. Syslog over TLS for Log Events
Syslog messages containing log events can be optionally sent over TLS instead of UDP. TLS support for log event syslog messages is based on RFC 5425, which provides security for syslog through the use of encryption and authentication.To enable the use of TLS for syslog log events, configure a TLS profile against the syslog profile, as shown in the following example:
Syslog over TLS packets are sent with a fixed TCP source port of 6514.
TLS is supported for the following log event syslogs:
- system syslogs (configure log syslog), which can send syslog messages as follows:
- in-band (for example, out a port on an IMM)
- out-of-band (out a CPM Ethernet port in the management router instance)
The configure log route-preference command configuration determines where the TLS connection is established for the base system syslogs. - service VPRN syslogs (configure service vprn log syslog)
7.2.8. NETCONF
A NETCONF log is a log that outputs log events to a NETCONF session as notifications. A NETCONF client can subscribe to a NETCONF log using the configured netconf-stream stream-name for the log in a subscription request. See NETCONF Notifications for more details.
7.3. Event Logs
Event logs are the means of recording system generated events for later analysis. Events are messages generated by the system by applications or processes within the router.
Figure 16 depicts a function block diagram of event logging.
Figure 16: Event Logging Block Diagram
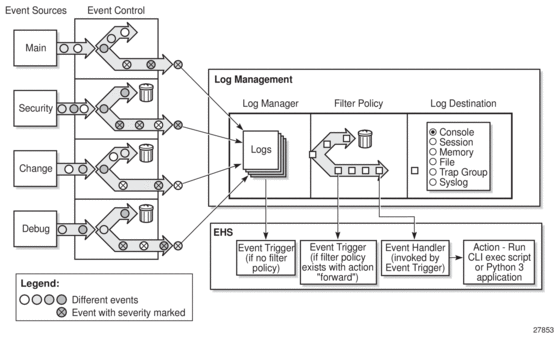
7.3.1. Event Sources
In Figure 16, the event sources are the main categories of events that feed the log manager.
- Security — The security event source is all events that affect attempts to breach system security such as failed login attempts, attempts to access MIB tables to which the user is not granted access or attempts to enter a branch of the CLI to which access has not been granted. Security events are generated by the SECURITY application and the authenticationFailure event in the SNMP application.
- Change — The change activity event source is all events that directly affect the configuration or operation of the node. Change events are generated by the USER application. The Change event stream also includes the tmnxConfigModify (#2006), tmnxConfigCreate (#2007), tmnxConfigDelete (#2008) and tmnxStateChange (#2009) change events from the SYSTEM application, as well as the various xxxConfigChange events from the MGMT_CORE application.
- Debug — The debug event source is the debugging configuration that has been enabled on the system. Debug events are generated when debug is enabled for various protocols under the debug branch of the CLI (for example, debug system ntp).
- Main — The main event source receives events from all other applications within the router.
Examples of applications within the system include IP, MPLS, OSPF, CLI, services, and so on. The following example displays a partial sample of the show log applications command output which displays all applications.
7.3.2. Event Control
Event control pre-processes the events generated by applications before the event is passed into the main event stream. Event control assigns a severity to application events and can either forward the event to the main event source or suppress the event. Suppressed events are counted in event control, but these events will not generate log entries as it never reaches the log manager.
Simple event throttling is another method of event control and is configured similarly to the generation and suppression options. See Simple Logger Event Throttling.
Events are assigned a default severity level in the system, but the application event severities can be changed by the user.
Application events contain an event number and description that explains why the event is generated. The event number is unique within an application, but the number can be duplicated in other applications.
The following example, generated by querying event control for application generated events, displays a partial list of event numbers and names.
7.3.3. Log Manager and Event Logs
Events that are forwarded by event control are sent to the log manager. The log manager manages the event logs in the system and the relationships between the log sources, event logs and log destinations, and log filter policies.
An event log has the following properties:
- A unique log ID — The log ID is a short, numeric identifier for the event log. A maximum of 30 logs can be configured at a time.
- One or more log sources — The source stream or streams to be sent to log destinations can be specified. The source must be identified before the destination can be specified. The events can be from the main event stream, events in the security event stream, or events in the user activity stream.
- One event log destination — A log can only have a single destination (for example, syslog or memory).
- An optional event filter policy — An event filter policy defines whether to forward or drop an event or trap-based on match criteria.
7.3.4. Event Filter Policies
The log manager uses event filter policies to allow fine control over which events are forwarded or dropped based on various criteria. Like other filter policies in the SR OS, filter policies have a default action. The default actions are either:
- Forward
- Drop
Filter policies also include a number of filter policy entries that are identified with an entry ID and define specific match criteria and a forward or drop action for the match criteria.
Each entry contains a combination of matching criteria that define the application, message, event number, router, severity, and subject conditions. The entry’s action determines how the packets should be treated if they have met the match criteria.
Entries are evaluated in order from the lowest to the highest entry ID. The first matching event is subject to the forward or drop action for that entry.
Valid operators are displayed in Table 36:
Table 36: Valid Filter Policy Operators
Operator | Description |
eq | equal to |
neq | not equal to |
lt | less than |
lte | less than or equal to |
gt | greater than |
gte | greater than or equal to |
A match criteria entry can include combinations of:
- Equal to or not equal to a given system application.
- Equal to or not equal to an event message string or regular expression match.
- Equal to, not equal to, less than, less than or equal to, greater than or greater than or equal to an event number within the application.
- Equal to, not equal to, less than, less than or equal to, greater than or greater than or equal to a severity level.
- Equal to or not equal to a router name string or regular expression match.
- Equal to or not equal to an event subject string or regular expression match.
7.3.5. Event Log Entries
Log entries that are forwarded to a destination are formatted in a way appropriate for the specific destination whether it be recorded to a file or sent as an SNMP trap, but log event entries have common elements or properties. All application generated events have the following properties:
- A time stamp in UTC or local time.
- The generating application.
- A unique event ID within the application.
- A router name identifying the router instance that generated the event.
- A subject identifying the affected object.
- A short text description.
The general format for an event in an event log with either a memory, console or file destination is as follows.
The following is an event log example:
The specific elements that compose the general format are described in Table 37.
Table 37: Log Entry Field Descriptions
Label | Description |
nnnn | The log entry sequence number. |
<time> | YYYY/MM/DD HH:MM:SS.SSS |
YYYY/MM/DD | The UTC date stamp for the log entry. YYYY — Year MM — Month DD — Date |
HH:MM:SS.SSS | The UTC time stamp for the event. HH — Hours (24 hour format) MM — Minutes SS.SSS — Seconds |
TZONE | The timezone (for example, UTC, EDT) as configured by configure log log-id x time-format. |
<severity> | The severity level of the event. CLEARED — A cleared event (severity number 1). INFO — An indeterminate/informational severity event (severity level 2). CRITICAL — A critical severity event (severity level 3). MAJOR — A major severity event (severity level 4). MINOR — A minor severity event (severity level 5). WARNING — A warning severity event (severity 6). |
<application> | The application generating the log message. |
<event-id> | The application’s event ID number for the event. |
<vrtr-name> | The router name (vrtr-name, for example, vprn101 or Base), in a format used by the logging system, representing the router instance that generated the event. |
<subject> | The subject/affected object for the event. |
<message> | A text description of the event. |
7.3.6. Simple Logger Event Throttling
Simple event throttling provides a mechanism to protect event receivers from being overloaded when a scenario causes many events to be generated in a very short period of time. A throttling rate, # events/# seconds, can be configured. Specific event types can be configured to be throttled. Once the throttling event limit is exceeded in a throttling interval, any further events of that type cause the dropped events counter to be incremented. Dropped events counts are displayed by the show>log>event-control context. Events are dropped before being sent to one of the logger event collector tasks. There is no record of the details of the dropped events and therefore no way to retrieve event history data lost by this throttling method.
A particular event type can be generated by multiple managed objects within the system. At the point this throttling method is applied the logger application has no information about the managed object that generated the event and cannot distinguish between events generated by object “A” from events generated by object “B”. If the events have the same event-id, they are throttled regardless of the managed object that generated them. It also does not know which events may eventually be logged to destination log-id <n> from events that will be logged to destination log-id <m>.
Throttle rate applies commonly to all event types. It is not configurable for a specific event-type.
A timer task checks for events dropped by throttling when the throttle interval expires. If any events have been dropped, a TIMETRA-SYSTEM-MIB::tmnxTrapDropped notification is sent.
7.3.7. Default System Log
Log 99 is a pre-configured memory-based log which logs events from the main event source (not security, debug, and so on). Log 99 exists by default.
The following example displays the log 99 configuration.
7.3.8. Event Handling System
The Event Handling System (EHS) is a framework that allows operator-defined behavior to be configured on the router. EHS adds user-controlled programmatic exception handling by allowing the execution of either a CLI script or a Python 3 application when a log event (the “trigger”) is detected. Various fields in the log event provide regexp style expression matching, which allows flexibility for the trigger definition.
EHS handler objects are used to tie together the following:
- trigger events (typically log events that match a configurable criteria)
- a set of actions to perform (enabled using CLI scripts and Python applications)
EHS, along with CRON, may execute SR OS CLI scripts or Python 3 applications to perform operator-defined functions as a result of receiving a trigger event. The Python programming language provides an extensive framework for automation activities for triggered or scheduled events, including model-driven transactional configuration and state manipulation. See the Python chapter for more information.
The use of Python applications from EHS is supported only in model-driven configuration mode.
Figure 17 shows the relationships among the different configurable objects used by EHS (and CRON).
Figure 17: EHS Object Relationships
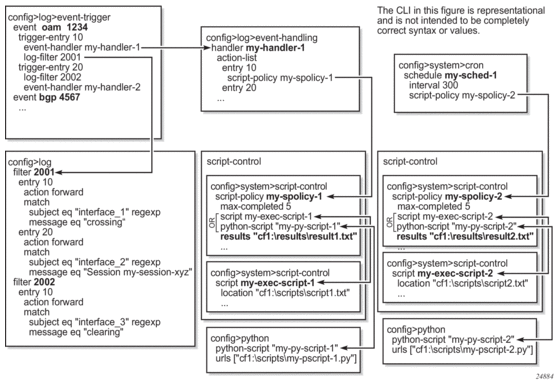
7.3.8.1. EHS Configuration and Variables
Complex rules can be configured to match log events as the trigger for EHS.
When a log event is generated in SR OS, it is subject to discard using suppression and throttling (config>log>event-control) before it is evaluated as a trigger for EHS, according to the following.
- EHS does not trigger on log events that are suppressed through config>log>event-control.
- EHS does not trigger on log events that are throttled by the logger.
EHS is triggered on log events that are dropped by user-configured log filters assigned to individual logs (config>log>filter). The EHS event trigger logic occurs before the distribution of log event streams into individual logs.
Varbinds are variable bindings that represent the variable number of values included in a log event.
The common parameters and varbinds for a triggering log event are passed into the triggered EHS CLI script or Python application and can be used within that script or application as passed-in (dynamic) variables. Passed-in (dynamic) variables are split into the following groups:
- Group oneCommon event parameters, as follows:
- appid — name of the application that generated the event
- eventid — event ID of the application
- severity — severity level of the event
- subject — subject or affected object of the event
- gentime — formatted time the even was generated (in UTC)
- timestamp — timestamp when the event was generated, in seconds (available within a Python application only)
- Group twoVariable parameters (varbinds), depending on the event. These are provided in different ways, depending on whether a CLI script or a Python application is triggered.
Note:
|
7.3.8.2. Triggering a CLI Script from EHS
When using the classic CLI, an EHS script has the ability to define local (static) variables and uses basic .if or .set syntax inside the script. The use of variables with .if or .set commands within an EHS script adds more logic to the EHS scripting and allows the reuse of a single EHS script for more than one trigger or action.
Both passed-in and local variables can be used within an EHS script, either as part of the CLI commands or as part of the .if or .set commands.
The following applies to both CLI commands and .if or .set commands (where X represents a variable).
- Using $X, without using single or double quotes, replaces the variable X with its string or integer value.
- Using “X”, with double quotes, means the actual string X.
- Using “$X”, with double quotes, replaces the variable X with its string or integer value.
- Using ‘X’, with single quotes does not replace the variable X with its value but means the actual string $X.
The following interpretation of single and double quotes applies.
- All characters within single quotes are interpreted as string characters.
- All characters within double quotes are interpreted as string characters except for $, which replaces the variable with its value (for example, shell expansion inside a string).
7.3.8.2.1. Examples of EHS Syntax Supported in Classic CLI
This section describes the supported EHS syntax for the classic CLI.
| Note: These scenarios use pseudo syntax. |
- .if $string_variable==string_value_or_string_variable {CLI_commands_set1.} else {CLI_commands_set2.} endif
- .if ($string_variable==string_value_or_string_variable) {CLI_commands_set1.} else {CLI_commands_set2.} endif
- .if $integer_variable==integer_value_or_integer_variable {CLI_commands_set1.} else {CLI_commands_set2.} endif
- .if ($integer_variable==integer_value_or_integer_variable) {CLI_commands_set1.} else {CLI_commands_set2.} endif
- .if $string_variable!=string_value_or_string_variable {CLI_commands_set1.} else {CLI_commands_set2.} endif
- .if ($string_variable!=string_value_or_string_variable) {CLI_commands_set1.} else {CLI_commands_set2.} endif
- .if $integer_variable!=integer_value_or_integer_variable {CLI_commands_set1.} else {CLI_commands_set2.} endif
- .if ($integer_variable!=integer_value_or_integer_variable) {CLI_commands_set1.} else {CLI_commands_set2.} endif
- .set $string_variable = string_value_or_string_variable
- .set ($string_variable = string_value_or_string_variable)
- .set $integer_variable = integer_value_or_integer_variable
- .set ($integer_variable = integer_value_or_integer_variable)
where:
- CLI_commands_set1 is a set of one or more CLI commands
- CLI_commands_set2 is a set of one or more CLI commands
- string_variable is a local (static) string variable
- string_value_or_string_variable is a string value/variable
- integer_variable is a local (static) integer variable
- integer_value_or_integer_variable is an integer value/variable
Note:
|
7.3.8.2.2. Valid Examples of EHS Syntax in Classic CLI
This section provides a list of valid examples to trigger log events using EHS syntax in classic CLI.
- configure service epipe $serviceIDwhere $serviceID is either a local (static) integer variable or passed-in (dynamic) integer variable
- echo srcAddr is $srcAddrwhere $srcAddr is a passed-in (dynamic) string variable
- .set $ipAddr = "10.0.0.1"where $ipAddr is a local (static) string variable
- .set $ipAddr = $srcAddrwhere $srcAddr is a passed-in (dynamic) string variable$ipAddr is a local (static) string variable.
- .set ($customerID = 50)where $customerID is a local (static) integer variable
- .set ($totalPackets = $numIngrPackets + $numEgrPackets)where $totalPackets, $numIngrPackets, $numEgrPackets are local (static) integer variables
- .set ($portDescription = $portName + $portLocation)where $portDescription, $portName, $portLocation are local (static) string variables
- if ($srcAddr == "CONSOLE") {CLI_commands_set1.else {CLI_commands_set2.} endifwhere $srcAddr is a passed-in (dynamic) string variableCLI_commands_set1 is a set of one or more CLI commandsCLI_commands_set2 is a set of one or more CLI commands
- .if ($customerId == 10) {CLI_commands_set1.else {CLI_commands_set2.} endifwhere $customerID is a passed-in (dynamic) integer variable CLI_commands_set1 is a set of one or more CLI commandsCLI_commands_set2 is a set of one or more CLI commands
- .if ($numIngrPackets == $numEgrPackets) {CLI_commands_set1.else {CLI_commands_set2.} endifwhere $numIngrPackets and $numEgrPackets are local (static) integer variablesCLI_commands_set1 is a set of one or more CLI commandsCLI_commands_set2 is a set of one or more CLI commands
7.3.8.2.3. Invalid Examples for EHS Syntax in Classic CLI
This section provides a list of invalid variable use in EHS syntax in classic CLI.
- .set $srcAddr = "10.0.0.1"where $srcAddr is a passed-in (dynamic) string variableReason: passed-in variables are read only inside an EHS script.
- .set ($ipAddr = $numIngrPackets + $numEgrPackets)where $ipAddr is a local (static) string variable$numIngrPackets and $numEgrPackets are local (static) integer variablesReason: variable types do not match, cannot assign a string to an integer.
- .set ($numIngrPackets = $ipAddr + $numEgrPackets)where $ipAddr is a local (static) string variable$numIngrPackets and $numEgrPackets are local (static) integer variablesReason: variable types do not match, cannot concatenate a string to an integer.
- .set $ipAddr = "10.0.0.1"100where $ipAddr is a local (static) string variableReason: when double quotes are used, they have to surround the entire string.
- .if ($totalPackets == "10.1.1.1") {.} endifwhere $totalPackets is a local (static) integer variablesReason: cannot compare an integer variable to a string value.
- .if ($ipAddr == 10) {.} endifwhere $ipAddr is a local (static) string variableReason: cannot compare a string variable to an integer value.
- .if ($totalPackets == $ipAddr) {where $totalPackets is a local (static) integer variables$ipAddr is a local (static) string variableReason: cannot compare an integer variable to a string variable.
7.3.8.3. Triggering a Python Application from EHS
When using model-driven configuration mode and the MD-CLI, EHS can trigger a Python application that is executed inside a Python interpreter running on SR OS. See the Python chapter for more information.
Python applications are not supported in classic configuration mode or mixed configuration mode.
When developing an EHS Python application, the event attributes are passed to the application using the get_event function in the pysros.ehs module.
To import this module, the Python application developer must add the following statement to the application:
Use the get_event function call to obtain the event that triggered the Python application to run. The following example catches the event and returns a Python object into the event variable:
When using an EHS Python application, the operator can use the Python programming language to create applications, as required. See the Python chapter for information about displaying model-driven state or configuration information, performing transactional configuration of SR OS, or executing CLI commands in Python.
Common event parameters (group one) are available in Python from the object created using the get_event function, as shown in the following table (the functions assume that the EHS event object is called event).
Table 38: Python get_event Common Parameters
Function call | Description | Example Output | Python Return Type |
event.appid | The name of the application that generated the event | SYSTEM | String |
event.eventid | The event ID number of the application | 2068 | Integer |
event.severity | The severity level of the event | minor | String |
event.subject | The subject or affected object of the event | EHS script | String |
event.gentime | The formatted time the event was generated in UTC | The timestamp in ISO 8601 format (consistent with state date/time leaves) that the event was generated. For example, 2021-03-08T11:52:06.0-05:00 | String |
event.timestamp | The timestamp that the event was generated (in seconds) | 1632165026.921208 | Float |
The variable parameters (group two) are available in Python in the eventparameters attribute of the event object, as shown in the following table. They are presented as a Python dictionary (unordered).
Table 39: Variable Parameters Available in Python
Function call | Description | Example Output | Python Return Type |
event.eventparameters | The event specific variable parameters | <EventParams> When calling keys() on this object the example output is: ('tmnxEhsHandlerName', 'tmnxEhsHEntryId', 'tmnxEhsHEntryScriptPlcyOwner', 'tmnxEhsHEntryScriptPlcyName', 'smLaunchOwner', 'smLaunchName', 'smLaunchScriptOwner', 'smLaunchScriptName', 'smLaunchError', 'tmnxSmLaunchExtAuthType', 'smRunIndex', 'tmnxSmRunExtAuthType', 'tmnxSmRunExtUserName') | Dict |
In addition to the variables, the format_msg() function is provided to output the formatted log string from the event as it would appear in the output of the show log command. The following is an example usage.
The following shows an example output of the format_msg() function.
7.3.8.4. EHS Debounce
EHS debounce (also called dampening) is the ability to trigger an action (for example an EHS script), if an event happens (N) times within a specific time window (S).
N = [2..15]
S = [1..604800]
Note:
|
For example:
When linkDown occurs N times in S seconds, an EHS script is triggered to shut down the port.
7.3.8.5. Executing EHS or CRON CLI Scripts or Python Applications
The execution of EHS or CRON scripts depends on the CLI engine associated with the configuration mode. The EHS or CRON script execution engine is based on the primary CLI engine set by the configure system management-interface cli cli-engine CLI command.
For example, if cli-engine is configured to classic-cli, the script executes in the classic CLI infrastructure and disregards the configuration mode, even if it is model-driven.
The following is the default behavior of the EHS or CRON scripts, depending on the configuration mode.
- Classic CLI configuration modeEHS or CRON scripts execute in the classic CLI environment and an error occurs if any model-driven CLI commands exist. Python applications are not supported and the system returns an error.
- Model-driven configuration modeEHS or CRON scripts execute in the MD-CLI environment and an error occurs if any classic CLI commands exist. Python applications are fully supported and utilize the SR OS model-driven interfaces and the pySROS libraries to obtain and manipulate state and configuration data, as well as pySROS API calls to execute MD-CLI commands.
- Mixed configuration modeEHS or CRON scripts execute in the classic CLI environment and an error occurs if any model-driven CLI commands exist. Python applications are not supported and the system returns an error.
EHS or CRON scripts that contain MD-CLI commands can be used in the MD-CLI as follows:
- scripts can be configured
- scripts can be created, edited, and results read through FTP
- scripts can be triggered and executed
- scripts generate an error if there are any non MD-CLI commands or .if or .set syntax in the script
User authorization for EHS or CRON scripts and Python applications can be configured in either the classic CLI or the MD-CLI as follows:
- classic CLIconfig>system>security>cli-script>authorization>event-handler>cli-user user-name
- MD-CLIconfigure system security cli-script authorization event-handler cli-user user-name
When a user is not specified, an EHS or CRON script bypasses authorization and can execute all commands.
In all configuration modes, a script policy can be disabled (using the configure system script-control script-policy policy-name admin-state disable MD-CLI command or the configure system script-control script-policy policy-name shutdown classic CLI command) even if history exists. When the script policy is disabled, the following applies.
- Newly triggered EHS or CRON scripts or Python applications are not allowed to execute or queue.
- In-progress EHS or CRON scripts or Python applications are allowed to continue.
- Already queued EHS or CRON scripts or Python applications are allowed to execute.
By default, a script policy is configured to allow an EHS or CRON script to override datastore locks from any model-driven interface (MD-CLI, NETCONF, and so on) in mixed and model-driven modes. A script policy can be configured to not allow EHS or CRON scripts to override datastore locks (using the configure system script-control script-policy policy-name lock-override false MD-CLI command or the configure system script-control script-policy policy-name no lock-override classic CLI command).
7.4. Customizing Syslog Messages Using Python 2
| Note: This section refers to the integrated Python 2 interpreter in SR OS, and the extensive features of Python 3 with the pySROS libraries are not available for syslog message customization. |
Log events in SR OS can be customized by a Python script before they are sent to a syslog server. Log events that are subject to Python processing are selected via log filters, which allows only a preferred subset of log messages to be customized. The following figure shows the interaction between the Logger and the Python engine.
Figure 18: Interaction between the Logger and the Python Engine
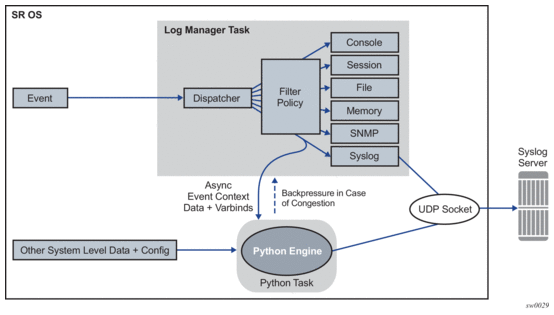
7.4.1. Python Engine for Syslog
This section discusses syslog-specific aspects of Python processing. Refer to the “Python Script Support for ESM” section of the 7450 ESS, 7750 SR, and VSR Triple Play Service Delivery Architecture Guide for an introduction to Python.
When an event is dispatched to the log manager in SR OS, the log manager asynchronously passes the event context data and varbinds to the Python engine, that is, the logger task is not waiting for feedback from Python. Varbinds are variable bindings that represent the variable number of values that are included in the event. Each varbind consists of a triplet (OID, type, value). Along with other system-level variables, the Python engine constructs a syslog message and sends it to the syslog destination. During this process, the operator can modify the format of the syslog message or leave it intact, as if it was generated by the syslog process within the log manager.
The tasks of the Python engine in a syslog context are as follows:
- assembles custom syslog messages (including PRI, HEADER and MSG fields) based on the received event context data, varbinds specific to the event, system-level data, and the configuration parameters (syslog server IP address, syslog facility, log-prefix and the destination UDP port)
- reformats timestamps in a syslog message
- sends the original or modified message to the syslog server
- drops the message
7.4.1.1. Python Syslog APIs
Python APIs are used to assemble a syslog message which, in SR OS, has the format described in section Syslog.
Table 40 describes Python information that can be used to manipulate syslog messages.
Table 40: Manipulating Python Syslog Messages
Imported Nokia (ALC) Modules | Access Rights | Comments |
event (from alc import event) | — | The method used to retrieve generic event information. |
syslog (from alc import syslog) | — | The method used to retrieve syslog-specific parameters. |
system (from alc import system) | — | The method used to retrieve system-specific information. Currently, the only parameter retrieved is the system name. |
Events use the following format as they are written into memory, file, console, and system: nnnn <time> <severity>:<application> # <event_id> <router-name> <subject> <message> The event-related information received in the context data from the log manager is retrieved via the following Python methods: | ||
event.sequence | RO | The sequence number of the event (nnnn). |
event.timestamp | RO | The timestamp of the event. (YYYY/MM/DD HH:MM:SS.SS). |
event.routerName | RO | The router name, for example, BASE, VPRN1, and so on. |
event.application | RO | The application generating the event, for example, NA. |
event.severity | RO | The severity of the event. This is configurable in SR OS (CLEARED [1], INFO [2], CRITICAL [3], MAJOR [4], MINOR [5], WARNING [6]). |
event.eventId | RO | The event ID, for example, 2012. |
event.eventName | RO | The event Name, for example, tmnxNatPlBloclAllocationLsn. |
event.subject | RO | An optional field, for example, [NAT]. |
event.message | RO | The event-specific message, for example, "{2} Map 192.168.20.29 [2001-2005] MDA 1/2 -- 276824064 classic-lsn-sub %3 vprn1 10.10.10.101 at 2015/08/31 09:20:15". |
Syslog Methods | ||
syslog.hostName | RO | The IP address of the SR OS node sending the syslog message. This is used in the Syslog HEADER. |
syslog.logPrefix | RO | The log prefix which is configurable and optional, for example, TMNX: |
syslog.severityToPRI(event.severity) | — | The Python method used to derive the PRI field in syslog header based on event severity and a configurable syslog facility. |
syslog.severityToName(event.severity) | — | An SR OS event severity to syslog severity name. For more information, see the Syslog section. |
syslog.timestampToUnix(timestamp) | — | The Python method that takes a timestamp in the format if YYYY/MM/DD HH:MM:SS and converts it into a UNIX-based format (seconds since Jan 01 1970 – UTC). |
syslog.set(newSyslogPdu) | — | The Python method used to send the syslog message in the newSyslogPdu. This variable must be constructed manually via string manipulation. In the absence of the command, the SR OS assembles the default syslog message (as if Python was not configured) and sends it to the syslog server, assuming that the message is not explicitly dropped. |
syslog.drop() | — | The Python method used to drop a syslog message. This method must be called before the syslog.set<newSyslogPdu method. |
System Methods | ||
system.name | RO | The Python method used to retrieve the system name |
For example, assume that the syslog format is:
Then the following is an example of the syslogPdu constructed via Python:
7.4.1.2. Timestamp Format Manipulation
Certain logging environments require customized formatting of the timestamp. Nokia provides a timestamp conversion method in the alu.syslog Python module to convert a timestamp from the format YYYY/MM/DD hh:mm:ss into a UNIX-based timestamp format (seconds since Jan 01 1970 – UTC).
For example, an operator can use the following Python method to convert a timestamp from the YYYY/MM/DD hh:mm:ss.ss or YYYY/MM/DD hh:mm:ss (no centiseconds) format into either the UNIX timestamp format or the MMM DD hh:mm:ss format.
The timeFormatConversion method can accept the event.timestamp value in the format:
and return a new timestamp in the format determined by the format parameter:
This method accepts the input format in either of the two forms YYYY/MM/DD HH:MM:SS.SS or YYYY/MM/DD HH:MM:SS and simply ignores the centisecond part in the former form.
7.4.2. Python Processing Efficiency
Python retrieves event-related variables from the log manager, as opposed to retrieving pre-assembled syslog messages. This eliminates the need for string parsing of the syslog message to manipulate it constituent parts increasing the speed of Python processing.
To further improve processing performance, Nokia recommends performing string manipulation via the Python native string method, when possible.
7.4.3. Python Backpressure
A Python task assembles syslog messages based on the context information received from the logger and sends them to the syslog server independent of the logger. If the Python task is congested due to a high volume of received data, the backpressure should be sent to the ISA so that the ISA stops allocating NAT resources. This behavior matches the current behavior in which NAT resources allocation is blocked if that logger is congested.
7.4.4. Event Selection for Python Processing
Events destined for Python processing are configured through a log ID that references a Python policy. The selection of the events are performed via a filter associated with this log ID. The remainder of the events destined to the same syslog server can bypass Python processing by redirecting them to a different log ID. The following example clarifies this point:
- Creating the Python policyA:dut-a# configure python python-policy PyForLogEvents create*A:dut-a>config>python>py-policy$[no] description - Configure the description of this policy[no] dhcp - Configure scripts to handle dhcp messages jritter[no] dhcp6 - Configure scripts to handle dhcp6 messages[no] diameter - Configure scripts to handle diameter messages[no] gtpv1-c - Configure scripts to handle GTPv1-C messages[no] gtpv2-c - Configure scripts to handle GTPv2-C messages[no] pppoe - Configure scripts to handle PPPoE messages[no] radius - Configure scripts to handle RADIUS messages[no] vsd - Configure scripts to handle VSD messages[no] syslog - Configure a script to handle outgoing syslog messages*A:dut-a>config>python>py-policy$ syslog- syslog script <name>- no syslog<name> :[32 chars max]The detailed Python policy description is explained in the “Python Script Support for ESM” section in the 7450 ESS, 7750 SR, and VSR Triple Play Service Delivery Architecture Guide.
- Log filters identify the events that are subject to Python processingA:dut-a>config>log# info----------------------------------------------filter 6default-action dropentry 1action forwardmatchapplication eq "nat"number eq 2012exitexitexitfilter 7default-action forwardentry 1action dropmatchapplication eq "nat"number eq 2012exitexitexit
- Syslog destinationsyslog 1address 192.168.1.1exit
- Applying Python syslog policy to selected events via filter 6:log-id 33 Note: Process log events with id of 2012 with Python beforesending them to syslog server.filter 6from mainto syslog 1python-policy "PyForLogEvents"no shutdownexitlog-id 34 Note: Log events that are not processed by Python.filter 7from mainto syslog 1no shutdownexit
In the example above, the configuration-only event 2012 from application "nat" will be sent to log-id 33. All other events are forwarded to the same syslog destination via log-id 34, without any modification. As a result, all events (modified via log-id 33 and unmodified via log-id 34) are sent to the syslog 1 destination.
This configuration may cause reordering of syslog messages at the syslog 1 destination due to slight delay of messages processed by Python.
7.5. Accounting Logs
Before an accounting policy can be created a target log file must be created to collect the accounting records. The files are stored in system memory on compact flash (cf1: or cf2:) in a compressed (tar) XML format and can be retrieved using FTP or SCP.
A file ID can only be assigned to either one event log ID or one accounting log.
7.5.1. Accounting Records
An accounting policy must define a record name and collection interval. Only one record name can be configured per accounting policy. Also, a record name can only be used in one accounting policy.
The record name, sub-record types, and default collection period for service and network accounting policies are shown in Table 41. Table 43 (fields per policer stat-mode are given in the stat-mode command descriptions in the 7450 ESS, 7750 SR, 7950 XRS, and VSR Quality of Service Guide), Table 44, and Table 45 provide field descriptions.
Table 41: Accounting Record Name and Collection Periods
Record Name | Sub-Record Types | Accounting Object | Platform | Default Collection Period (minutes) |
service-ingress-octets | sio | SAP | All | 5 |
service-egress-octets | seo | SAP | All | 5 |
service-ingress-packets | sip | SAP | All | 5 |
service-egress-packets | sep | SAP | All | 5 |
network-ingress-octets | nio | Network port | All | 15 |
network-egress-octets | neo | Network port | All | 15 |
network-egress-packets | nep | Network port | All | 15 |
network-ingress-packets | nio | Network port | All | 15 |
compact-service-ingress-octets | ctSio | SAP | All | 5 |
combined-service-ingress | cmSipo | SAP | All | 5 |
combined-network-ing-egr-octets | cmNio & cmNeo | Network port | All | 15 |
combined-service-ing-egr-octets | cmSio & cmSeo | SAP | All | 5 |
complete-network-ingr-egr | cpNipo & cpNepo | Network port | All | 15 |
complete-service-ingress-egress | cpSipo & cpSepo | SAP | All | 5 |
combined-sdp-ingress-egress | cmSdpipo and cmSdpepo | SDP and SDP binding | All | 5 |
complete-sdp-ingress-egress | cmSdpipo, cmSdpepo, cpSdpipo and cpSdpepo | SDP and SDP binding | All | 5 |
complete-subscriber-ingress-egress | cpSBipo & cpSBepo | Subscriber profile | 7750 SR | 5 |
aa-protocol | aaProt | AA ISA Group | 7750 SR | 15 |
aa-application | aaApp | AA ISA Group | 7750 SR | 15 |
aa-app-group | aaAppGrp | AA ISA Group | 7750 SR | 15 |
aa-subscriber-protocol | aaSubProt | Special study AA subscriber | 7750 SR | 15 |
aa-subscriber-application | aaSubApp | Special study AA subscriber | 7750 SR | 15 |
custom-record-aa-sub | aaSubCustom | AA subscriber | All | 15 |
combined-mpls-lsp-egress | mplsLspEgr | LSP | All | 5 |
combined-mpls-lsp-ingress | mplsLspIn | LSP | All | 5 |
saa | saa png trc hop | SAA or SAA test | All | 5 |
complete-ethernet-port | enet | Ethernet port | All | 15 |
When creating accounting policies, one service accounting policy and one network accounting policy can be defined as default. If statistics collection is enabled on a SAP or network port and no accounting policy is applied, then the respective default policy is used. If no default policy is defined, then no statistics are collected unless a specifically defined accounting policy is applied.
Each accounting record name is composed of one or more sub-records which is in turn composed of multiple fields.
Refer to the Application Assurance Statistics Fields Generated per Record table in the 7450 ESS, 7750 SR, and VSR Multiservice Integrated Service Adapter and Extended Services Appliance Guide for fields names for Application Assurance records.
The availability of the records listed in Table 42 depends on the specific platform functionality and user configuration.
Table 42: Accounting Record Name Details
Record Name | Sub-Record | Field | Field Description |
Service-ingress-octets (sio) 1 | sio | svc | SvcId |
sap | SapId | ||
qid | QueueId | ||
hoo | OfferedHiPrioOctets | ||
hod | DroppedHiPrioOctets | ||
loo | LowOctetsOffered | ||
lod | LowOctetsDropped | ||
uco | UncoloredOctetsOffered | ||
iof | InProfileOctetsForwarded | ||
oof | OutOfProfileOctetsForwarded | ||
Service-egress-octets (seo) 1 | seo | svc | SvcId |
sap | SapId | ||
qid | QueueId | ||
iof | InProfileOctetsForwarded | ||
iod | InProfileOctetsDropped | ||
oof | OutOfProfileOctetsForwarded | ||
ood | OutOfProfileOctetsDropped | ||
sip | svc | SvcId | |
sap | SapId | ||
qid | QueueId | ||
hpo | HighPktsOffered | ||
hpd | HighPktsDropped | ||
lpo | LowPktsOffered | ||
lpd | LowPktsDropped | ||
ucp | UncoloredPacketsOffered | ||
ipf | InProfilePktsForwarded | ||
opf | OutOfProfilePktsForwarded | ||
sep | svc | SvcId | |
sap | SapId | ||
qid | QueueId | ||
ipf | InProfilePktsForwarded | ||
ipd | InProfilePktsDropped | ||
opf | OutOfProfilePktsForwarded | ||
opd | OutOfProfilePktsDropped | ||
Network-ingress-octets (nio) | nio | port | PortId |
qid | QueueId | ||
iof | InProfileOctetsForwarded | ||
iod | InProfileOctetsDropped | ||
oof | OutOfProfileOctetsForwarded | ||
ood | OutOfProfileOctetsDropped | ||
Network-egress-octets (neo) | neo | port | PortId |
qid | QueueId | ||
iof | InProfileOctetsForwarded | ||
iod | InProfileOctetsDropped | ||
oof | OutOfProfileOctetsForwarded | ||
ood | OutOfProfileOctetsDropped | ||
Network-ingress-packets (nip) | nip | port | PortId |
qid | QueueId | ||
ipf | InProfilePktsForwarded | ||
ipd | InProfilePktsDropped | ||
opf | OutOfProfilePktsForwarded | ||
opd | OutOfProfilePktsDropped | ||
Network Egress Packets (nep) | nep | port | PortId |
qid | QueueId | ||
ipf | InProfilePktsForwarded | ||
ipd | InProfilePktsDropped | ||
opf | OutOfProfilePktsForwarded | ||
opd | OutOfProfilePktsDropped | ||
Compact-service-ingress-octets (ctSio) | ctSio | svc | SvcId |
sap | SapId | ||
qid | QueueId | ||
hoo | OfferedHiPrioOctets | ||
hod | DroppedHiPrioOctets | ||
loo | LowOctetsOffered | ||
lod | LowOctetsDropped | ||
uco | UncoloredOctetsOffered | ||
Combined-service-ingress (cmSipo) | cmSipo | svc | SvcId |
sap | SapId | ||
qid | QueueId | ||
hpo | HighPktsOffered | ||
hpd | HighPktsDropped | ||
lpo | LowPktsOffered | ||
lpd | LowPktsDropped | ||
ucp | UncoloredPacketsOffered | ||
hoo | OfferedHiPrioOctets | ||
hod | DroppedHiPrioOctets | ||
loo | LowOctetsOffered | ||
lod | LowOctetsDropped | ||
uco | UncoloredOctetsOffered | ||
ipf | InProfilePktsForwarded | ||
opf | OutOfProfilePktsForwarded | ||
iof | InProfileOctetsForwarded | ||
oof | OutOfProfileOctetsForwarded | ||
Combined-network-ing-egr-octets (cmNio & cmNeo) | cmNio | port | PortId |
qid | QueueId | ||
iof | InProfileOctetsForwarded | ||
iod | InProfileOctetsDropped | ||
oof | OutOfProfileOctetsForwarded | ||
ood | OutOfProfileOctetsDropped | ||
cmNeo | port | PortId | |
qid | QueueId | ||
iof | InProfileOctetsForwarded | ||
iod | InProfileOctetsDropped | ||
oof | OutOfProfileOctetsForwarded | ||
ood | OutOfProfileOctetsDropped | ||
Combined-service-ingr-egr-octets (cmSio & CmSeo) | cmSio | svc | SvcId |
sap | SapId | ||
qid | QueueId | ||
hoo | OfferedHiPrioOctets | ||
hod | DroppedHiPrioOctets | ||
loo | LowOctetsOffered | ||
lod | LowOctetsDropped | ||
uco | UncoloredOctetsOffered | ||
iof | InProfileOctetsForwarded | ||
oof | OutOfProfileOctetsForwarded | ||
cmSeo | svc | SvcId | |
sap | SapId | ||
qid | QueueId | ||
iof | InProfileOctetsForwarded | ||
iod | InProfileOctetsDropped | ||
oof | OutOfProfileOctetsForwarded | ||
ood | OutOfProfileOctetsDropped | ||
Complete-network-ingr-egr (cpNipo & cpNepo) | cpNipo | port | PortId |
qid | QueueId | ||
ipf | InProfilePktsForwarded | ||
ipd | InProfilePktsDropped | ||
opf | OutOfProfilePktsForwarded | ||
opd | OutOfProfilePktsDropped | ||
iof | InProfileOctetsForwarded | ||
iod | InProfileOctetsDropped | ||
oof | OutOfProfileOctetsForwarded | ||
ood | OutOfProfileOctetsDropped | ||
cpNepo | port | PortId | |
qid | QueueId | ||
ipf | InProfilePktsForwarded | ||
ipd | InProfilePktsDropped | ||
opf | OutOfProfilePktsForwarded | ||
opd | OutOfProfilePktsDropped | ||
iof | InProfileOctetsForwarded | ||
iod | InProfileOctetsDropped | ||
oof | OutOfProfileOctetsForwarded | ||
ood | OutOfProfileOctetsDropped | ||
Complete-service-ingress-egress (cpSipo & cpSepo) | cpSipo | svc | SvcId |
sap | SapId | ||
qid | QueueId | ||
hpo | HighPktsOffered | ||
hpd | HighPktsDropped | ||
lpo | LowPktsOffered | ||
lpd | LowPktsDropped | ||
ucp | UncoloredPacketsOffered | ||
hoo | OfferedHiPrioOctets | ||
hod | DroppedHiPrioOctets | ||
loo | LowOctetsOffered | ||
lod | LowOctetsDropped | ||
uco | UncoloredOctetsOffered | ||
apo | AllPacketsOffered | ||
aoo | AllOctetsOffered | ||
apd | AllPacketsDropped | ||
aod | AllOctetsDropped | ||
apf | AllPacketsForwarded | ||
aof | AllOctetsForwarded | ||
ipd | InProfilePktsDropped | ||
iod | InProfileOctetsDropped | ||
opd | OutOfProfilePktsDropped | ||
ood | OutOfProfileOctetsDropped | ||
hpf | HighPriorityPacketsForwarded | ||
hof | HighPriorityOctetsForwarded | ||
Complete-service-ingress-egress (cpSipo & cpSepo) (Continued) | cpSipo (Continued) | lpf | LowPriorityPacketsForwarded |
lof | LowPriorityOctesForwarded | ||
ipf | InProfilePktsForwarded | ||
opf | OutOfProfilePktsForwarded | ||
iof | InProfileOctetsForwarded | ||
oof | OutOfProfileOctetsForwarded | ||
cpSepo | svc | SvcId | |
sap | SapId | ||
qid | QueueId | ||
ipf | InProfilePktsForwarded | ||
ipd | InProfilePktsDropped | ||
opf | OutOfProfilePktsForwarded | ||
opd | OutOfProfilePktsDropped | ||
iof | InProfileOctetsForwarded | ||
iod | InProfileOctetsDropped | ||
oof | OutOfProfileOctetsForwarded | ||
ood | OutOfProfileOctetsDropped | ||
Complete-sdp-ingress-egress (cpSdpipo & cpSdpepo) | cpSdpipo | sdp | SdpID |
tpf | TotalPacketsForwarded | ||
tpd | TotalPacketsDropped | ||
tof | TotalOctetsForwarded | ||
tod | TotalOctetsDropped | ||
cpSdpepo | sdp | SdpID | |
tpd | TotalPacketsDropped | ||
tod | TotalOctetsDropped | ||
Combined-sdp-ingress-egress (cmSdpipo & cmSdpepo) | cmSdpipo | svc | SvcID |
sdp | SdpID | ||
tpf | TotalPacketsForwarded | ||
tpd | TotalPacketsDropped | ||
tof | TotalOctetsForwarded | ||
tod | TotalOctetsDropped | ||
cmSdpepo | svc | SvcID | |
sdp | SdpID | ||
tpf | TotalPacketsForwarded | ||
tof | TotalOctetsForwarded | ||
Complete-sdp-ingress-egress (cmSdpipo & cmsdpepo) (cpSdpip & cpSdpepo) | cmSdpipo | svc | SvcID |
sdp | SdpID | ||
tpf | TotalPacketsForwarded | ||
tpd | TotalPacketsDropped | ||
tof | TotalOctetsForwarded | ||
tod | TotalOctetsDropped | ||
cmSdpepo | svc | SvcID | |
sdp | SdpID | ||
tpf | TotalPacketsForwarded | ||
tof | TotalOctetsForwarded | ||
cpSdpipo | sdp | SdpID | |
tpf | TotalPacketsForwarded | ||
tpd | TotalPacketsDropped | ||
tof | TotalOctetsForwarded | ||
tod | TotalOctetsDropped | ||
cpSdpepo | sdp | SdpID | |
tpf | TotalPacketsForwarded | ||
tof | TotalOctetsForwarded | ||
Complete-subscriber-ingress-egress (cpSBipo & cpSBepo) | SubscriberInformation | subId | SubscriberId |
subProfile | SubscriberProfile | ||
Sla- Information | svc | SvcId | |
sap | SapId | ||
slaProfile | SlaProfile | ||
spiSharing | SPI sharing type and identifier | ||
Complete-subscriber-ingress-egress (cpSBipo & cpSBepo) (Continued) | cpSBipo | qid | QueueId |
hpo | HighPktsOffered | ||
hpd | HighPktsDropped | ||
lpo | LowPktsOffered | ||
lpd | LowPktsDropped | ||
ucp | UncolouredPacketsOffered | ||
hoo | OfferedHiPrioOctets | ||
hod | DroppedHiPrioOctets | ||
loo | LowOctetsOffered | ||
lod | LowOctetsDropped | ||
apo | AllPktsOffered | ||
aoo | AllOctetsOffered | ||
uco | UncolouredOctetsOffered | ||
ipf | InProfilePktsForwarded | ||
opf | OutOfProfilePktsForwarded | ||
iof | InProfileOctetsForwarded | ||
oof | OutOfProfileOctetsForwarded | ||
v4pf | IPv4PktsForwarded | ||
v6pf | IPv6PktsForwarded | ||
v4pd | IPv4PktsDropped | ||
v6pd | IPv6PktsDropped | ||
v4of | IPv4OctetsForwarded | ||
v6of | IPv6OctetsForwarded | ||
v4od | IPv4OctetsDropped | ||
v6od | IPv6OctetsDropped | ||
Complete-subscriber-ingress-egress (cpSBipo & cpSBepo) (Continued) | cpSBepo | qid | QueueId |
ipf | InProfilePktsForwarded | ||
ipd | InProfilePktsDropped | ||
opf | OutOfProfilePktsForwarded | ||
opd | OutOfProfilePktsDropped | ||
iof | InProfileOctetsForwarded | ||
iod | InProfileOctetsDropped | ||
oof | OutOfProfileOctetsForwarded | ||
ood | OutOfProfileOctetsDropped | ||
v4pf | IPv4PktsForwarded | ||
v6pf | IPv6PktsForwarded | ||
v4pd | IPv4PktsDropped | ||
v6pd | IPv6PktsDropped | ||
v4of | IPv4OctetsForwarded | ||
v6of | IPv6OctetsForwarded | ||
v4od | IPv4OctetsDropped | ||
v6od | IPv6OctetsDropped | ||
saa | saa | tmd | TestMode |
own | OwnerName | ||
tst | TestName | ||
png | PingRun subrecord | ||
rid | RunIndex | ||
trr | TestRunResult | ||
mnr | MinRtt | ||
mxr | MaxRtt | ||
avr | AverageRtt | ||
rss | RttSumOfSquares | ||
pbr | ProbeResponses | ||
spb | SentProbes | ||
mnt | MinOutTt | ||
mxt | MaxOutTt | ||
avt | AverageOutTt | ||
tss | OutTtSumOfSquares | ||
mni | MinInTt | ||
mxi | MaxInTt | ||
avi | AverageInTt | ||
iss | InTtSumOfSqrs | ||
ojt | OutJitter | ||
ijt | InJitter | ||
rjt | RtJitter | ||
prt | ProbeTimeouts | ||
prf | ProbeFailures | ||
saa (Continued) | trc | rid | RunIndex |
trr | TestRunResult | ||
lgp | LastGoodProbe | ||
hop | hop | TraceHop | |
hid | HopIndex | ||
mnr | MinRtt | ||
mxr | MaxRtt | ||
avr | AverageRtt | ||
rss | RttSumOfSquares | ||
pbr | ProbeResponses | ||
spb | SentProbes | ||
mnt | MinOutTt | ||
mxt | MaxOutTt | ||
avt | AverageOutTt | ||
tss | OutTtSumOfSquares | ||
mni | MinInTt | ||
mxi | MaxInTt | ||
avi | AverageInTt | ||
iss | InTtSumOfSqrs | ||
ojt | OutJitter | ||
ijt | InJitter | ||
rjt | RtJitter | ||
prt | ProbeTimeouts | ||
prf | ProbeFailures | ||
tat | TraceAddressType | ||
tav | TraceAddressValue | ||
Complete-ethernet-port (enet) | enet | port | PortId |
to | EtherStatsOctets | ||
tp | EtherStatsPkts | ||
de | EtherStatsDropEvents | ||
tbcp | EtherStatsBroadcastPkts | ||
mcp | EtherStatsMulticastPkts | ||
cae | EtherStatsCRCAlignErrors | ||
up | EtherStatsUndersizePkts | ||
op | EtherStatsOversizePkts | ||
fgm | EtherStatsFragments | ||
jab | EtherStatsJabbers | ||
col | EtherStatsCollisions | ||
p64o | EtherStatsPkts64Octets | ||
p127o | EtherStatsPkts65to127Octets | ||
p255o | EtherStatsPkts128to255Octets | ||
p511o | EtherStatsPkts256to511Octets | ||
p1023o | EtherStatsPkts512to1023Octets | ||
p1518o | EtherStatsPkts1024to1518Octets | ||
po1518o | EtherStatsPktsOver1518Octets | ||
ae | Dot3StatsAlignmentErrors | ||
fe | Dot3StatsFCSErrors | ||
scf | Dot3StatsSingleCollisionFrames | ||
mcf | Dot3StatsMultipleCollisionFrames | ||
sqe | Dot3StatsSQETestErrors | ||
dt | Dot3StatsDeferredTransmissions | ||
Complete-ethernet-port (enet) (Continued) | enet (Continued) | lcc | Dot3StatsLateCollisions |
exc | Dot3StatsExcessiveCollisions | ||
imt | Dot3StatsInternalMacTransmitErrors | ||
cse | Dot3StatsCarrierSenseErrors | ||
ftl | Dot3StatsFrameTooLongs | ||
imre | Dot3StatsInternalMacReceiveErrors | ||
se | Dot3StatsSymbolErrors | ||
ipf | Dot3InPauseFrames | ||
opf | Dot3OutPauseFrames |
- The number of octets in an ATM sap excludes the Header Error Control (HEC) byte, thus meaning each packet/cell has only 52 bytes instead of the usual 53.
- For a SAP in AAL5 SDU mode, packet counters refer to the number of SDU. For a SAP in N-to-1 cell mode, packet counters refer to the number of cells.
Notes:
Table 43, Table 44, and Table 45 provide field descriptions.
Table 43: Policer Stats Field Descriptions
Field | Field Description |
pid | PolicerId |
statmode | PolicerStatMode |
aod | AllOctetsDropped |
aof | AllOctetsForwarded |
aoo | AllOctetsOffered |
apd | AllPacketsDropped |
apf | AllPacketsForwarded |
apo | AllPacketsOffered |
c1od | ConnectionOneOctetsDropped ** |
c1of | ConnectionOneOctetsForwarded ** |
c1oo | ConnectionOneOctetsOffered ** |
c1pd | ConnectionOnePacketsDropped ** |
c1pf | ConnectionOnePacketsForwarded ** |
c1po | ConnectionOnePacketsOffered ** |
c2od | ConnectionTwoOctetsDropped ** |
c2of | ConnectionTwoOctetsForwarded ** |
c2oo | ConnectionTwoOctetsOffered ** |
c2pd | ConnectionTwoPacketsDropped ** |
c2pf | ConnectionTwoPacketsForwarded ** |
c2po | ConnectionTwoPacketsOffered ** |
hod | HighPriorityOctetsDropped |
hof | HighPriorityOctetsForwarded |
hoo | HighPriorityOctetsOffered |
hpd | HighPriorityPacketsDropped |
hpf | HighPriorityPacketsForwarded |
hpo | HighPriorityPacketsOffered |
iod | InProfileOctetsDropped |
iof | InProfileOctetsForwarded |
ioo | InProfileOctetsOffered |
ipd | InProfilePacketsDropped |
ipf | InProfilePacketsForwarded |
ipo | InProfilePacketsOffered |
lod | LowPriorityOctetsDropped |
lof | LowPriorityOctetsForwarded |
loo | LowPriorityOctetsOffered |
lpd | LowPriorityPacketsDropped |
lpf | LowPriorityPacketsForwarded |
lpo | LowPriorityPacketsOffered |
opd | OutOfProfilePacketsDropped |
opf | OutOfProfilePacketsForwarded |
opo | OutOfProfilePacketsOffered |
ood | OutOfProfileOctetsDropped |
oof | OutOfProfileOctetsForwarded |
ooo | OutOfProfileOctetsOffered |
xpd | ExceedProfilePktsDropped |
xpf | ExceedProfilePktsForwarded |
xpo | ExceedProfilePktsOffered |
xod | ExceedProfileOctetsDropped |
xof | ExceedProfileOctetsForwarded |
xoo | ExceedProfileOctetsOffered |
ppd | InplusProfilePacketsDropped |
ppf | InplusProfilePacketsForwarded |
ppo | InplusProfilePacketsOffered |
pod | InplusProfileOctetsDropped |
pof | InplusProfileOctetsForwarded |
poo | InplusProfileOctetsOffered |
uco | UncoloredOctetsOffered |
ucp | UncoloredPacketsOffered |
v4po | IPv4PktsOffered * |
v4oo | IPv4OctetsOffered * |
v6po | IPv6PktsOffered * |
v6oo | IPv6OctetsOffered * |
v4pf | IPv4PktsForwarded * |
v6pf | IPv6PktsForwarded * |
v4pd | IPv4PktsDropped * |
v6pd | IPv6PktsDropped * |
v4of | IPv4OctetsForwarded * |
v6of | IPv6OctetsForwarded * |
v4od | IPv4OctetsDropped * |
v6od | IPv6OctetsDropped * |
* Enhanced Subscriber Management (ESM) only.
** Enhanced Subscriber Management (ESM) connection bonding only.
Table 44: Queue Group Record Types
Record Name | Description |
qgone | PortQueueGroupOctetsNetworkEgress |
qgosi | PortQueueGroupOctetsServiceIngress |
qgose | PortQueueGroupOctetsServiceEgress |
qgpne | PortQueueGroupPacketsNetworkEgress |
qgpsi | PortQueueGroupPacketsServiceIngress |
qgpse | PortQueueGroupPacketsServiceEgress |
fpqgosi | ForwardingPlaneQueueGroupOctetsServiceIngress |
fpqgoni | ForwardingPlaneQueueGroupOctetsNetworkIngress |
fpqgpsi | ForwardingPlaneQueueGroupPacketsServiceIngress |
fpqgpni | ForwardingPlaneQueueGroupPacketsNetworkIngress |
Table 45: Queue Group Record Type Fields
Field | Field Description |
data port | Port (used for port based Queue Groups) |
member-port | LAGMemberPort (used for port based Queue Groups) |
data slot | Slot (used for Forwarding Plane based Queue Groups) |
forwarding-plane | ForwardingPlane (used for Forwarding Plane based Queue Groups) |
queue-group | QueueGroupName |
instance | QueueGroupInstance |
qid | QueueId |
pid | PolicerId |
statmode | PolicerStatMode |
aod...ucp | same as above |
7.5.2. Accounting Files
When a policy has been created and applied to a service or network port, the accounting file is stored on the compact flash in a compressed XML file format. The router creates two directories on the compact flash to store the files. The following output displays a directory named act-collect that holds accounting files that are open and actively collecting statistics. The directory named act stores the files that have been closed and are awaiting retrieval.
Accounting files always have the prefix act followed by the accounting policy ID, log ID and timestamp. The accounting log file naming and log file destination properties like rollover and retention are discussed in more detail in Log Files.
7.5.3. Design Considerations for Accounting Policies
The router has ample resources to support large scale accounting policy deployments. When preparing for an accounting policy deployment, verify that data collection, file rollover, and file retention intervals are properly tuned for the amount of statistics to be collected.
If the accounting policy collection interval is too brief there may be insufficient time to store the data from all the services within the specified interval. If that is the case, some records may be lost or incomplete. Interval time, record types, and number of services using an accounting policy are all factors that should be considered when implementing accounting policies.
The rollover and retention intervals on the log files and the frequency of file retrieval must also be considered when designing accounting policy deployments. The amount of data stored depends on the type of record collected, the number of services that are collecting statistics, and the collection interval that is used. For example, with a 1Gb CF and using the default collection interval, the system is expected to hold 48 hours’ worth of billing information.
7.5.4. Reporting and Time-Based Accounting
SR OS on the 7750 SR platform has support for volume accounting and time-based accounting concepts, and provides an extra level of intelligence at the network element level in order to provide service models such as “prepaid access” in a scalable manner. This means that the network element gathers and stores per-subscriber accounting information and compares it with “pre-defined” quotas. Once a quota is exceeded, the pre-defined action (such as re-direction to a web portal or disconnect) is applied.
7.5.5. Overhead Reduction in Accounting: Custom Record
Custom records can be used to decrease accounting messaging overhead as follows:
7.5.5.1. User Configurable Records
Users can define a collection of fields that make up a record. These records can be assigned to an accounting policy. These are user-defined records rather than being limited to pre-defined record types. The operator can select queues and policers and the counters within these queues and policers that need to be collected. Refer to the predefined records containing a given field for XML field name of a custom record field.
7.5.5.2. Changed Statistics Only
A record is only generated if a significant change has occurred to the fields being written in a given the record. This capability applies to both ingress and egress records regardless on the method of delivery (such as RADIUS and XML). The capability also applies to Application Assurance records; however without an ability to specify different significant change values and per-field scope (for example, all fields of a custom record are collected if any activity was reported against any of the statistics that are part of the custom record).
7.5.5.3. Configurable Accounting Records
7.5.5.3.1. XML Accounting Files for Service and ESM-Based Accounting
The custom-record command in the config>log>accounting-policy context provides the flexibility to reduce the volume of data generated by allowing network operators to specify the record needed for collection. This can eliminate queues and policers, or selected counters within these queues and policers, that are not relevant for billing.
ESM-based accounting applies to the 7750 SR only.
Record headers including information such as service-ID, SAP-ID, and so on, will always be generated.
7.5.5.3.2. XML Accounting Files for Policer Counters
Policer counters can be collected using custom records with the record within the accounting policy configured to be either custom-record-service or custom-record-subscriber. The policer identifier for which counters are collected must be configured under custom-record, specifying the required ingress (i-counters) and egress (e-counters) counters to be collected. A similar configuration is available for a reference policer (ref-policer) to define a reference counter used together with the significant-change command.
The counters collected are dependent on the stat-mode of the related policer, as this determines which statistics are collected by the system for the policer.
The ingress policer counters collected for each combination of XML accounting record name and policer stat-mode are given in Table 46.
The egress policer counters collected for each combination of XML accounting record name and policer stat-mode are given in Table 47.
Table 46: Custom Record Policer Ingress Counter Mapping
Policer i-counters CLI Name | Policer stat-mode | Custom Record Counter | Custom Record Field |
in-profile-octets-discarded-count | minimal | — | — |
offered-limited-capped-cir offered-limited-profile-cir offered-priority-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir | In-Profile Octets Dropped | iod | |
offered-priority-no-cir | High-Priority Octets Dropped | hod | |
v4-v6 | V4 Octets Dropped | v4od | |
in-profile-octets-forwarded-count | minimal | — | — |
offered-limited-capped-cir offered-limited-profile-cir offered-priority-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir | In-Profile Octets Forwarded | iof | |
offered-priority-no-cir | High-Priority Octets Forwarded | hof | |
v4-v6 | V4 Octets Forwarded | v4of | |
in-profile-octets-offered-count | minimal offered-limited-profile-cir offered-total-cir | — | — |
offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir | In-Profile Octets Offered | ioo | |
offered-priority-cir offered-priority-no-cir | High-Priority Octets Offered | hoo | |
v4-v6 | V4 Octets Offered | v4oo | |
in-profile-packets-discarded-count | minimal | — | — |
offered-limited-capped-cir offered-limited-profile-cir offered-priority-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir | In-Profile Packets Dropped | ipd | |
offered-priority-no-cir | High-Priority Packets Dropped | hpd | |
v4-v6 | V4 Packets Dropped | v4pd | |
in-profile-packets-forwarded-count | minimal | — | — |
offered-limited-capped-cir offered-limited-profile-cir offered-priority-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir | In-Profile Packets Forwarded | ipf | |
offered-priority-no-cir | High-Priority Packets Forwarded | hpf | |
v4-v6 | V4 Packets Forwarded | v4pf | |
in-profile-packets-offered-count | minimal offered-limited-profile-cir offered-total-cir | — | — |
offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir | In-Profile Packets Offered | ipo | |
offered-priority-cir offered-priority-no-cir | High-Priority Packets Offered | hpo | |
v4-v6 | V4 Packets Offered | v4po | |
out-profile-octets-discarded-count | minimal | All Octets Dropped | aod |
offered-limited-capped-cir offered-limited-profile-cir offered-priority-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir | Out-of-Profile Octets Dropped | ood | |
offered-priority-no-cir | Low-Priority Octets Dropped | lod | |
v4-v6 | V6 Octets Dropped | v6od | |
out-profile-octets-forwarded-count | minimal | All Octets Forwarded | aof |
offered-limited-capped-cir offered-limited-profile-cir offered-priority-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir | Out-of-Profile Octets Forwarded | oof | |
offered-priority-no-cir | Low-Priority Octets Forwarded | lof | |
v4-v6 | V6 Octets Forwarded | v6of | |
out-profile-octets-offered-count | minimal offered-total-cir | All Octets Offered | aoo |
offered-limited-capped-cir | — | — | |
offered-limited-profile-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir | Out-of-Profile Octets Offered | ooo | |
offered-priority-cir offered-priority-no-cir | Low-Priority Octets Offered | loo | |
v4-v6 | V6 Octets Offered | v6oo | |
out-profile-packets-discarded-count | minimal | All Packets Dropped | apd |
offered-limited-capped-cir offered-limited-profile-cir offered-priority-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir | Out-of-Profile Packets Dropped | opd | |
offered-priority-no-cir | Low-Priority Packets Dropped | lpd | |
v4-v6 | V6 Packets Dropped | v6pd | |
out-profile-packets-forwarded-count | minimal | All Packets Forwarded | apf |
offered-limited-capped-cir offered-limited-profile-cir offered-priority-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir | Out-of-Profile Packets Forwarded | opf | |
offered-priority-no-cir | Low-Priority Packets Forwarded | lpf | |
v4-v6 | V6 Packets Forwarded | v6pf | |
out-profile-packets-offered-count | minimal offered-total-cir | All Packets Offered | apo |
offered-limited-capped-cir | n/a | n/a | |
offered-limited-profile-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir | Out-of-Profile Packets Offered | opo | |
offered-priority-cir offered-priority-no-cir | Low-Priority Packets Offered | lpo | |
v4-v6 | V6 Packets Offered | v6po | |
uncoloured-octets-offered-count | minimal offered-priority-cir offered-priority-no-cir offered-profile-no-cir offered-total-cir v4-v6 | — | — |
offered-limited-capped-cir offered-limited-profile-cir offered-profile-capped-cir offered-profile-cir | Uncoloured Octets Offered | uco | |
uncoloured-packets-offered-count | minimal offered-priority-cir offered-priority-no-cir offered-profile-no-cir offered-total-cir v4-v6 | — | — |
offered-limited-capped-cir offered-limited-profile-cir offered-profile-capped-cir offered-profile-cir | Uncoloured Packets Offered | ucp |
Table 47: Custom Record Policer Egress Counter Mapping
Policer e-counters CLI Name | Policer stat-mode | Custom Record Counter | Custom Record Field |
exceed-profile-octets-discarded-count | bonding minimal offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir v4-v6 | n/a | n/a |
offered-four-profile-no-cir offered-total-cir-exceed offered-total-cir-four-profile | Exceed-Profile Octets Dropped | xod | |
exceed-profile-octets-forwarded-count | bonding minimal offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir v4-v6 | — | — |
offered-four-profile-no-cir offered-total-cir-exceed offered-total-cir-four-profile | Exceed-Profile Octets Forwarded | xof | |
exceed-profile-octets-offered-count | bonding minimal offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed offered-total-cir-four-profile v4-v6 | — | — |
offered-four-profile-no-cir | Exceed-Profile Octets Offered | xoo | |
exceed-profile-packets-discarded-count | bonding minimal offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir v4-v6 | — | — |
offered-four-profile-no-cir offered-total-cir-exceed offered-total-cir-four-profile | Exceed-Profile Packets Dropped | xpd | |
exceed-profile-packets-forwarded-count | bonding minimal offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir v4-v6 | — | — |
offered-four-profile-no-cir offered-total-cir-exceed offered-total-cir-four-profile | Exceed-Profile Packets Forwarded | xpf | |
exceed-profile-packets-offered-count | bonding minimal offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed offered-total-cir-four-profile v4-v6 | — | — |
offered-four-profile-no-cir | Exceed-Profile Packets Offered | xpo | |
in-plus-profile-octets-discarded-count | bonding minimal offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed v4-v6 | — | — |
offered-four-profile-no-cir offered-total-cir-four-profile | In-Plus-Profile Octets Dropped | pod | |
in-plus-profile-octets-forwarded-count | bonding minimal offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed v4-v6 | — | — |
offered-four-profile-no-cir offered-total-cir-four-profile | In-Plus-Profile Octets Forwarded | pof | |
in-plus-profile-octets-offered-count | bonding minimal offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed offered-total-cir-four-profile v4-v6 | — | — |
offered-four-profile-no-cir | In-Plus-Profile Octets Offered | poo | |
in-plus-profile-packets-discarded-count | bonding minimal offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed v4-v6 | — | — |
offered-four-profile-no-cir offered-total-cir-four-profile | In-Plus-Profile Packets Dropped | ppd | |
in-plus-profile-packets-forwarded-count | bonding minimal offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed v4-v6 | — | — |
offered-four-profile-no-cir offered-total-cir-four-profile | In-Plus-Profile Packets Forwarded | ppf | |
in-plus-profile-packets-offered-count | bonding minimal offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed offered-total-cir-four-profile v4-v6 | — | — |
offered-four-profile-no-cir | In-Plus-Profile Packets Offered | ppo | |
in-profile-octets-discarded-count | bonding | Connection 1 Octets Dropped | c1od |
minimal | — | — | |
offered-four-profile-no-cir offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed offered-total-cir-four-profile | In-Profile Octets Dropped | iod | |
v4-v6 | V4 Octets Dropped | v4od | |
in-profile-octets-forwarded-count | bonding | Connection 1 Octets Forwarded | c1of |
minimal | — | — | |
offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed offered-four-profile-no-cir offered-total-cir-four-profile | In-Profile Octets Forwarded | iof | |
v4-v6 | V4 Octets Forwarded | v4of | |
in-profile-octets-offered-count | bonding | Connection 1 Octets Offered | c1oo |
minimal offered-total-cir offered-total-cir-exceed offered-total-cir-four-profile | — | — | |
offered-four-profile-no-cir offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir | In-Profile Octets Offered | ioo | |
v4-v6 | V4 Octets Offered | v4oo | |
in-profile-packets-discarded-count | bonding | Connection 1 Packets Dropped | c1pd |
minimal | — | — | |
offered-four-profile-no-cir offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed offered-total-cir-four-profile | In-Profile Packets Dropped | ipd | |
v4-v6 | V4 Packets Dropped | v4pd | |
in-profile-packets-forwarded-count | bonding | Connection 1 Packets Forwarded | c1pf |
minimal | — | — | |
offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed offered-four-profile-no-cir offered-total-cir-four-profile | In-Profile Packets Forwarded | ipf | |
v4-v6 | V4 Packets Forwarded | v4pf | |
in-profile-packets-offered-count | bonding | Connection 1 Packets Offered | c1po |
minimal offered-total-cir offered-total-cir-exceed offered-total-cir-four-profile | — | — | |
offered-four-profile-no-cir offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir | In-Profile Packets Offered | ipo | |
v4-v6 | V4 Packets Offered | v4po | |
out-profile-octets-discarded-count | bonding | Connection 2 Octets Dropped | c2od |
minimal | All Octets Dropped | aod | |
offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed offered-four-profile-no-cir offered-total-cir-four-profile | Out-of-Profile Octets Dropped | ood | |
v4-v6 | V6 Octets Dropped | v6od | |
out-profile-octets-forwarded-count | bonding | Connection 2 Octets Forwarded | c2of |
minimal | All Octets Forwarded | aof | |
offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed offered-four-profile-no-cir offered-total-cir-four-profile | Out-of-Profile Octets Forwarded | oof | |
v4-v6 | V6 Octets Forwarded | v6of | |
out-profile-octets-offered-count | bonding | Connection 2 Octets Offered | c2oo |
minimal offered-total-cir offered-total-cir-exceed offered-total-cir-four-profile | All Octets Offered | aoo | |
offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-four-profile-no-cir | Out-of-Profile Octets Offered | ooo | |
v4-v6 | V6 Octets Offered | v6oo | |
out-profile-packets-discarded-count | bonding | Connection 2 Packets Dropped | c2pd |
minimal | All Packets Dropped | apd | |
offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed offered-four-profile-no-cir offered-total-cir-four-profile | Out-of-Profile Packets Dropped | opd | |
v4-v6 | V6 Packets Dropped | v6pd | |
out-profile-packets-forwarded-count | bonding | Connection 2 Packets Forwarded | c2pf |
minimal | All Packets Forwarded | apf | |
offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed offered-four-profile-no-cir offered-total-cir-four-profile | Out-of-Profile Packets Forwarded | opf | |
v4-v6 | V6 Packets Forwarded | v6pf | |
out-profile-packets-offered-count | bonding | Connection 2 Packets Offered | c2po |
minimal offered-total-cir offered-total-cir-exceed offered-total-cir-four-profile | All Packets Offered | apo | |
offered-limited-capped-cir offered-profile-capped-cir offered-profile-cir offered-profile-no-cir offered-four-profile-no-cir | Out-of-Profile Packets Offered | opo | |
v4-v6 | V6 Packets Offered | v6po | |
uncoloured-octets-offered-count | bonding minimal offered-four-profile-no-cir offered-limited-capped-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed offered-total-cir-four-profile v4-v6 | — | — |
offered-profile-capped-cir offered-profile-cir | Uncoloured Octets Offered | uco | |
uncoloured-packets-offered-count | bonding minimal offered-four-profile-no-cir offered-limited-capped-cir offered-profile-no-cir offered-total-cir offered-total-cir-exceed offered-total-cir-four-profile v4-v6 | — | — |
offered-profile-capped-cir offered-profile-cir | Uncoloured Packets Offered | ucp |
7.5.5.3.3. RADIUS Accounting in Networks Using ESM
The custom-record command in the config>subscr-mgmt>radius-accounting-policy context provide the flexibility to include individual counters in RADIUS accounting messages. See the CLI tree for commands and syntax. This functionality applies to the 7750 SR only.
7.5.5.4. Significant Change Only Reporting
Another way to decrease accounting messaging related to overhead is to include only “active” objects in a periodical reporting. An “active object” in this context is an object which has seen a “significant” change in corresponding counters. A significant change is defined in terms of a cumulative value (the sum of all reference counters).
This concept is applicable to all methods used for gathering accounting information, such as an XML file and RADIUS, as well as to all applications using accounting, such as service-acct, ESM-acct, and Application Assurance.
Accounting records are reported at the periodical intervals. This periodic reporting is extended with an internal filter which omits periodical updates for objects whose counter change experienced lower changes than a defined (configurable) threshold.
Specific to RADIUS accounting the significant-change command does not affect ACCT-STOP messages. ACCT-STOP messages will be always sent, regardless the amount of change of the corresponding host.
For Application Assurance records, a significant change of 1 in any field of a customized record (send a record if any field changed) is supported. When configured, if any statistic field records activity, an accounting record containing all fields will be collected.
7.5.6. Immediate Completion of Records
7.5.6.1. Record Completion for XML Accounting
For ESM RADIUS accounting, an accounting stop message is sent when:
- A subscriber/subscriber-host is deleted.
- An SLA profile instance is changed.
A similar concept is also used for XML accounting. In case the accounted object is deleted or changed, the latest information will be written in the XML file with a “final” tag indication in the record header. This functionality applies to the 7750 SR only.
7.5.7. AA Accounting per Forwarding Class
This feature allows the operator to report on protocol/application/app-group volume usage per forwarding class by adding a bitmap information representing the observed FC in the XML accounting files. In case the accounted object is deleted or changed, the latest information will be written in the XML file with a “final” tag indication in the record header.
7.6. Configuration Notes
This section describes logging configuration restrictions.
- A file or filter cannot be deleted if it has been applied to a log.
- File IDs, syslog IDs, or SNMP trap groups must be configured before they can be applied to a log ID.
- A file ID can only be assigned to either one log ID or one accounting policy.
- Accounting policies must be configured in the config>log context before they can be applied to a service SAP or service interface, or applied to a network port.
- The snmp-trap-id must be the same as the log-id.