Local configuration elements have precedence over configuration group inheritance.
In the following example, the configuration group "isis-1" contains the configuration element
level-capability 1, which is not inherited because a corresponding local
configuration element exists.
(ex)[/configure]
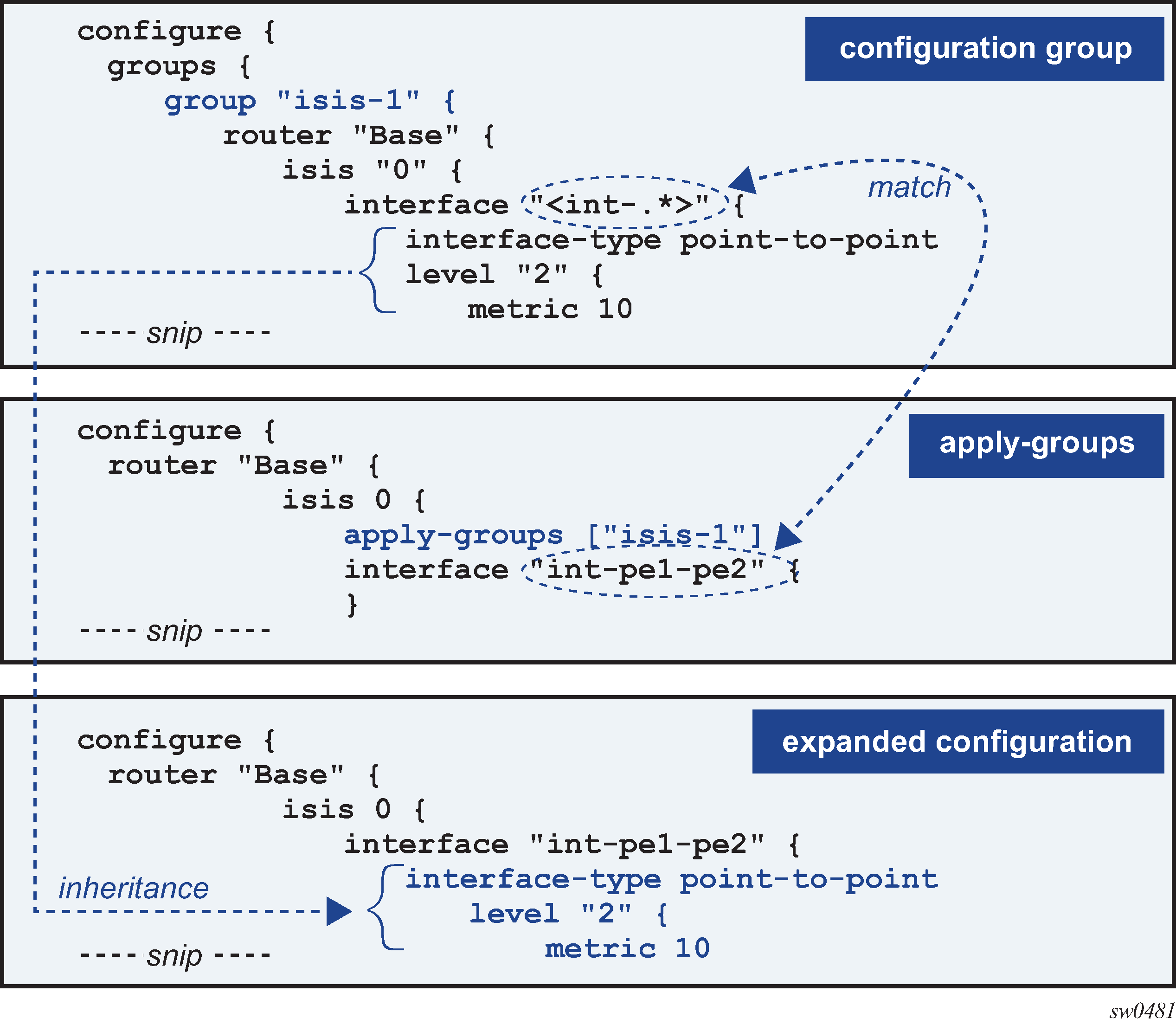
A:admin@node-2# info
groups {
group "isis-1" {
router "Base" {
isis "0" {
level-capability 1
interface "<int-.*>" {
interface-type point-to-point
level "2" {
metric 10
}
}
}
}
}
}
---snip---
router "Base" {
isis 0 {
apply-groups ["isis-1"]
admin-state enable
level-capability 2
area-address [49.0001.0001]
interface "int-pe1-pe2" {
}
}
}
The resulting expanded configuration after inheritance is shown as follows:
(ex)[/configure]
A:admin@node-2# info inheritance
router "Base" {
isis 0 {
apply-groups ["isis-1"]
admin-state enable
level-capability 2
area-address [49.0001.0001]
interface "int-pe1-pe2" {
## inherited: from group "isis-1"
interface-type point-to-point
level 2 {
## inherited: from group "isis-1"
metric 10
}
}
}
}
Up to eight configuration groups can be applied to a configuration branch. The configuration order determines the inheritance precedence:
In the following example, both configuration groups "isis-1" and "isis-2" set an interface
level 2
metric. Because configuration group "isis-2" is listed first in the
apply-groups, its configuration elements have precedence. The
interface-type configuration element is inherited from group "isis-1"
because a corresponding configuration element is not present in group "isis-2" nor
is it locally configured.
(ex)[/configure]
A:admin@node-2# info
groups {
group "isis-1" {
router "Base" {
isis "0" {
level-capability 1
interface "<int-.*>" {
interface-type point-to-point
level "2" {
metric 10
}
}
}
}
}
group "isis-2" {
router "Base" {
isis "0" {
interface "<int-.*>" {
level "2" {
metric 20
}
}
}
}
}
}
---snip---
router "Base" {
isis 0 {
apply-groups ["isis-2" "isis-1"]
admin-state enable
level-capability 2
area-address [49.0001.0001]
interface "int-pe1-pe2" {
}
}
}
The resulting expanded configuration after inheritance is shown as follows:
(ex)[/configure]
A:admin@node-2# info inheritance
router "Base" {
isis 0 {
apply-groups ["isis-2" "isis-1"]
admin-state enable
level-capability 2
area-address [49.0001.0001]
interface "int-pe1-pe2" {
## inherited: from group "isis-1"
interface-type point-to-point
level 2 {
## inherited: from group "isis-2"
metric 20
}
}
}
}
Configuration groups can be applied at different hierarchical branches. The hierarchy determines the inheritance precedence.
Configuration elements in groups applied at a lower-level branch have precedence over configuration elements in groups applied at a higher-level branch.
In the following example, all configuration groups set an interface level 2 metric.
Because configuration group "isis-3" is applied at the lowest level, its
configuration elements have precedence. The interface-type configuration
element is also inherited from group "isis-3" for the same reason. As described
earlier, the level-capability configuration element from group "isis-1" has
lower precedence than the local configured value. The wide-metric-only
configuration element from group "isis-3" is not inherited because the group is
applied at the interface branch and only configuration elements at that level or
lower can be inherited.
(ex)[/configure]
A:admin@node-2# info
groups {
group "isis-1" {
router "Base" {
isis "0" {
level-capability 1
interface "<int-.*>" {
interface-type point-to-point
level "2" {
metric 10
}
}
}
}
}
group "isis-2" {
router "Base" {
isis "0" {
interface "<int-.*>" {
level "2" {
metric 20
}
}
}
}
}
group "isis-3" {
router "Base" {
isis "0" {
interface "<int-.*>" {
interface-type point-to-point
level "2" {
metric 30
}
}
level "2" {
wide-metrics-only true
}
}
}
}
}
---snip---
router "Base" {
isis 0 {
apply-groups ["isis-2" "isis-1"]
admin-state enable
level-capability 2
area-address [49.0001.0001]
interface "int-pe1-pe2" {
apply-groups ["isis-3"]
}
}
}
The resulting expanded configuration after inheritance is shown as follows:
(ex)[/configure]
A:admin@node-2# info inheritance
router "Base" {
isis 0 {
apply-groups ["isis-2" "isis-1"]
admin-state enable
level-capability 2
area-address [49.0001.0001]
interface "int-pe1-pe2" {
apply-groups ["isis-3"]
## inherited: from group "isis-3"
interface-type point-to-point
level 2 {
## inherited: from group "isis-3"
metric 30
}
}
}
}
Inheritance rules for leaf-lists are the same as for a single leaf, whether the list is a
system-ordered leaf list (for example, configure router interface
interface-name
if-attribute admin-group value) or a user-ordered leaf list (for
example, configure router bgp export policyvalue). The entire
leaf-list is inherited, and it is not possible to add values to an existing
leaf-list through configuration group inheritance.
Inheritance rules for user-ordered lists (for example, configure policy-options
policy-statement
name
named-entry
entry-name) are:
list order is ignored for user-ordered list entry matching
unmatched list entries in the configuration group definition and its descendant configuration elements are inherited in the locally-configured user-ordered list. Newly-created list entries are appended at the end in the order they appear in the configuration group definition.
descendant configuration elements of matched user-ordered list entries are candidates for inheritance