This chapter describes authentication, authorization, and accounting (AAA) used to monitor and control network access on routers. Network security is based on a multi-step process. The first step, authentication, validates a user’s credentials. The second step, authorization, allows the user to access and execute commands at various command levels based on profiles assigned to the user.
The third step, accounting, keeps track of the activity of users who have accessed the network. The type of accounting information recorded can include a history of the commands executed, the amount of time spent in the session, the services accessed, and the data transfer size during the session. The accounting data can be used for trend analysis, billing, and auditing purposes.
Configure routers to use local, Remote Authentication Dial In User Service (RADIUS), Lightweight Directory Access Protocol (LDAP), or Terminal Access Controller Access Control System Plus (TACACS+) security to validate users who attempt to access the router by console, Telnet, SSH, NETCONF, FTP, and more. Select the authentication order, which determines the authentication method to try first, second, third, or fourth.
The router supports the following security features:
-
local security can be implemented for authentication and authorization
-
LDAP can be implemented for authentication in the Base routing instance
-
RADIUS can be used for authentication, authorization, and accounting in the Base routing instance or a VPRN
-
TACACS+ can be used for authentication, authorization, and accounting in the Base routing instance or a VPRN
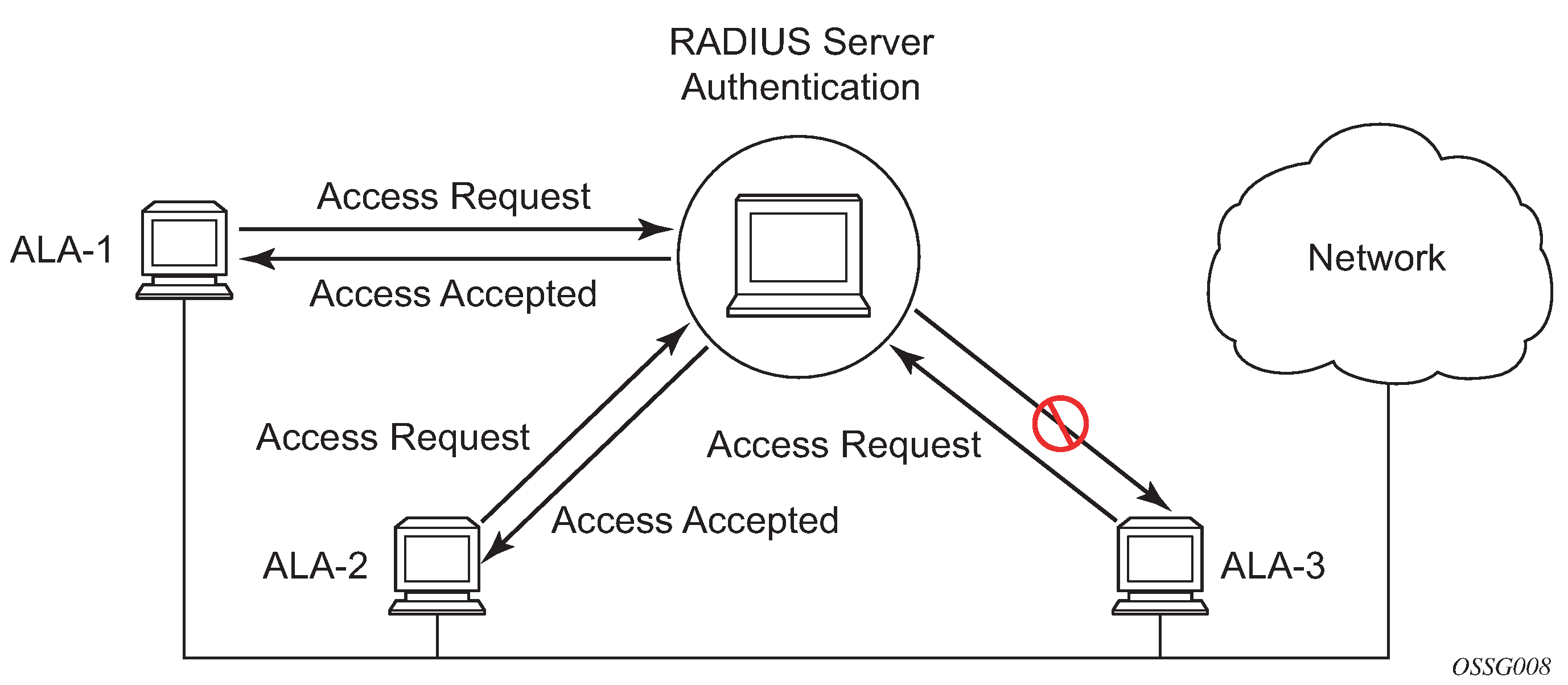
The following figure depicts end user access-requests sent to a RADIUS server. After validating the usernames and passwords, the RADIUS server returns an access-accept message to the users on ALA-1 and ALA-2. The username and password from ALA-3 could not be authenticated; therefore, access was denied.