The distributed RADIUS proxy acts just like the regular RADIUS proxy but runs on an ISA and is designed for high scale and high performance. It can handle a high number of RADIUS transactions; therefore it is able to keep up with EAP authentications that consists of many RADIUS transactions (EAP-PEAP) and all the accounting messages sent by an Access Point for a specific UE. The distributed RADIUS proxy is designed to handle the scale and performance of Distributed Subscriber Management (DSM) but can also be used as a performance improvement for Enhanced Subscriber Management (ESM). All common server-selection mechanisms are supported (direct, round-robin, hash-based) and both IPv4 and IPv6 RADIUS clients can communicate with the proxy. Important difference with the CPM based proxy is no IPv6 support toward the RADIUS server.
The distributed proxy also supports caching an access-accept to aid authentication of Layer 3 setup (DHCP/SLAAC/DHCPv6). After UE creation the cache supports tracking of both accounting and authentication messages. Contrary to the CPM-based RADIUS proxy the key used in the cache is always the calling-station-id attribute and it is expected to contain the UE MAC address, as specified in RFC 3580, IEEE 802.1X Remote Authentication Dial In User Service (RADIUS) Usage Guidelines. Accounting-on and accounting-off messages are not supported. The RADIUS proxy cache works with both ESM and DSM UEs.
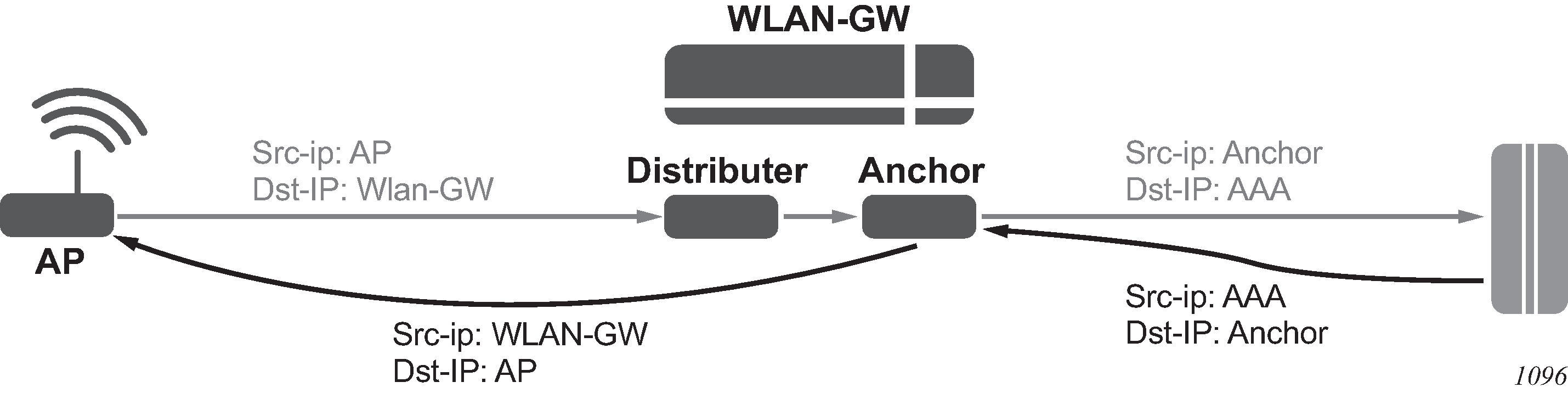
For caching to work, the distributed proxy makes sure that all packets are routed via the anchor ISA tied to the UE. An AP sends a RADIUS packet to the RADIUS proxy IP address shared by all ISAs, the WLAN-GW forwards the packet to a distributor ISA based on the source IP address of the radius packet. That ISA then looks for the calling-station-id and forwards the packet to the correct anchor-isa to handle proxy functionality and caching. If no calling-station-id is found (such as acct-on/acct-off), the packet is always forwarded to a fixed ISA that is chosen at startup. The chosen ISA forwards the packet with a per-ISA IP as source-ip, this source-ip is assigned at startup from the range configured under config>aaa>isa-radius-policy policy-name. From server to client the packet is sent back to that IP address and therefore immediately arrives at the correct anchor ISA, which subsequently forwards the packet straight to the AP without an additional ISA pass through.
The following is a distributed proxy configuration example.
#------------------------------------------------------
/configure service vprn 50 radius-proxy
----------------------------------------------
server "distributed_radius_proxy" purpose accounting authentication wlan-gw-group 1 create
cache
key packet-type request attribute-type 31
timeout min 5
no track-accounting
track-authentication accept
track-delete-hold-time 0
no shutdown
exit
default-accounting-server-policy "wlangw_isa_radius"
default-authentication-server-policy "wlangw_isa_radius"
no description
no load-balance-key
no python-policy
secret "BLoAGDmsLt/Rs9LLU5/lESjjqZa/ssWnEIMJNvgBwmo" hash2
send-accounting-response
wlan-gw
address 10.1.10.1
ipv6-address 2001:db8::0
exit
no shutdown
exit
----------------------------------------------
/configure aaa isa-radius-policy "wlangw_isa_radius"
----------------------------------------------
password "rNPEv/V0j095N0Qy4rnekTVbF89OIlVj" hash2
servers
router "Base"
source-address-range 10.100.100.4
server 1 create
authentication
ip-address 10.100.100.2
secret "rNPEv/V0j095N0Qy4rnekPU0fmH2TwEl" hash2
no shutdown
exit
exit
----------------------------------------------