3. MPLS and RSVP-TE
This chapter provides information required to configure Multiprotocol Label Switching (MPLS) and Resource Reservation Protocol for Traffic Engineering (RSVP-TE) for the 7705 SAR. For information on dynamic LSPs with LDP, refer to the chapter Label Distribution Protocol.
Topics in this chapter include:
3.1. Overview
The 7705 SAR provides MPLS technology using static LSPs, RSVP-TE for traffic-engineered signaled routing of LSPs and LDP for non-traffic-engineered signaled routing of LSPs. A network operator may choose to use any combination of static LSPs, RSVP-TE, and LDP to establish paths for services. RSVP-TE and LDP are considered to be Layer 2.5 protocols.
The 7705 SAR can be used as an ingress and egress Label Edge Router (iLER and eLER), and as a transit router. A transit router is also referred to as a Label Switch Router (LSR).
OSPF and IS-IS are the interior gateway protocols with traffic engineering extensions (IGP-TE) available to the 7705 SAR. These are the Layer 3 protocols. Typically, one or the other of these gateway protocols will be in use in the network. Whichever protocol is the chosen gateway protocol, it must be working in order for LDP or RSVP-TE to function. These Layer 3 protocols identify the next hop, which is information needed by the Layer 2.5 protocols (LDP or RSVP-TE) in order to assign labels.
In addition, the 7705 SAR provides link and node redundancy protection through LSP redundancy and Fast Reroute (FRR) features.
The LSP redundancy and FRR features have the ability to take shared risk link groups (SRLGs) into consideration when the Constrained Shortest Path First (CSPF) algorithm is used to determine an alternate LSP. The selection of a route is determined by the IGP-TE protocol. The added constraints imposed by SRLGs and CSPF will ensure that the redundant route selected will be unique from the principal route (route being protected); that is, it will use physical equipment that is different from the equipment that carries the principal route. CSPF will constrain the alternate route to be the shortest possible alternative route. There may be more than one alternative route.
3.2. MPLS
Multiprotocol Label Switching (MPLS) is a label switching technology that provides the ability to set up connection-oriented paths over a connectionless IP network. MPLS facilitates network traffic flow and provides a mechanism to engineer network traffic patterns independently from routing tables. MPLS sets up a specific path for a sequence of packets. The packets are identified by a label inserted into each packet.
MPLS is independent of any routing protocol but is considered multiprotocol because it works with protocols such as IP, ATM, Ethernet, and circuit emulation.
This section contains the following topics:
3.2.1. Traffic Engineering for MPLS
Without traffic engineering (TE), routers route traffic according to the Shortest Path First (SPF) algorithm, disregarding congestion or packet types.
With traffic engineering, network traffic is routed efficiently to maximize throughput and minimize delay. Traffic engineering facilitates traffic flows to be mapped to the destination through a less-congested path than the one selected by the SPF algorithm.
MPLS directs a flow of IP packets along a label switched path (LSP). LSPs are simplex, meaning that the traffic flows in one direction (unidirectional) from an ingress router to an egress router. Two LSPs are required for duplex (bidirectional) traffic. Each LSP carries traffic in a specific direction, forwarding packets from one router to the next across the MPLS domain.
When an ingress router receives a packet, it adds an MPLS header to the packet and forwards it to the next hop in the LSP. The labeled packet is forwarded along the LSP path (from next hop to next hop) until it reaches the destination point. The MPLS header is removed and the packet is forwarded based on Layer 3 information such as the IP destination address. The physical path of the LSP is not constrained to the shortest path that the IGP would choose using SPF to reach the destination IP address.
3.2.1.1. TE Metric and IGP Metric
When the TE metric is selected for an LSP, the shortest path computation will select an LSP path based on the TE metric constraints instead of the IGP metric (for OSPF and IS-IS), which is the default metric. The user configures the TE metric under the router>mpls>interface context and the IGP metric under the router>ospf>area> interface context (for OSPF) and the router>isis>if>level context (for IS-IS). Both the TE and IGP metrics are advertised by OSPF and IS-IS for each link in the network.
The TE metric is part of the traffic engineering extensions of the IGP protocols. For more information on the OSPF and IS-IS routing protocols, refer to the 7705 SAR Routing Protocols Guide.
Typically, the TE metric is used to allow Constrained Shortest Path First (CSPF) to represent a dual TE topology for the purpose of computing LSP paths, where one TE topology is based on the RSVP-TE database and the other is based on the IGP-TE database.
An LSP dedicated to real-time and delay-sensitive user and control traffic has its path computed by CSPF using the TE metric. The user configures the TE metric to represent the amount of delay, or combined delay and jitter, of the link. In this case, the shortest path satisfying the constraints of the LSP path will effectively represent the shortest-delay path.
An LSP dedicated to non-delay-sensitive user and control traffic has its path computed by CSPF using the IGP metric. The IGP metric could represent the link bandwidth or some other value as required.
When the use of the TE metric is enabled for an LSP, the CSPF process will first eliminate all links in the network topology that do not meet the constraints specified for the LSP path; the constraints include bandwidth, admin-groups, and hop limit. CSPF will then run the SPF algorithm on the remaining links. The shortest path among all the SPF paths will be selected based on the TE metric instead of the IGP metric. The TE metric is only used in CSPF computations for MPLS paths and not in the regular SPF computation for IP reachability.
Operational metrics of LSPs that use the TE metric in CSPF path calculations can be overridden with the user-configured administrative LSP metric.
3.2.2. MPLS Label Stack
Routers that support MPLS are known as Label Edge Routers (LERs) and Label Switch Routers (LSRs). MPLS requires a set of procedures to enhance network layer packets with label stacks, which turns them into labeled packets. In order to initiate, transmit, or terminate a labeled packet on a particular data link, an LER or LSR must support the encoding technique which, when given a label stack and a network layer packet, produces a labeled packet.
In MPLS, packets can carry not just one label, but a set of labels in a stack. An LSR can swap the label at the top of the stack, pop the stack (that is, remove the top label), or swap the label and push one or more labels onto the stack. The processing of a labeled packet is completely independent of the level of hierarchy. The processing is always based on the top label, without regard for the possibility that other labels may have been above it in the past or that other labels may be below it at present.
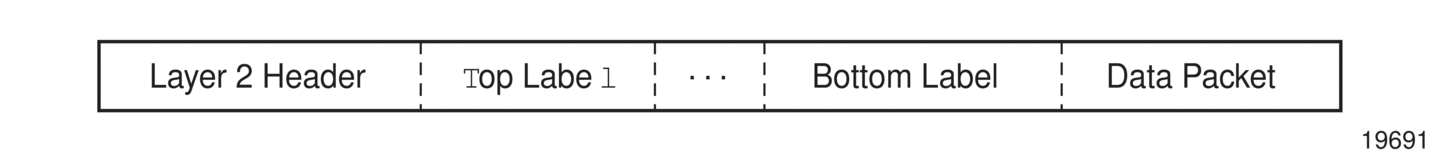
As described in RFC 3032, MPLS Label Stack Encoding, the label stack is represented as a sequence of “label stack entries”. Each label stack entry is represented by 4 octets. Figure 1 shows the structure of a label and Table 2 describes the fields. Figure 2 shows the label placement in a packet.
Figure 1: Label Structure

Table 2: Packet/Label Field Description
Field | Description |
Label | This 20-bit field carries the actual value (unstructured) of the label. |
Exp | This 3-bit field is reserved for experimental use. It is currently used for Class of Service (CoS). |
S | This bit is set to 1 for the last entry (bottom) in the label stack and 0 for all other label stack entries. |
TTL | This 8-bit field is used to encode a time-to-live value. |
A stack can carry several labels, organized in a last in/first out order. The top of the label stack appears first in the packet and the bottom of the stack appears last (Figure 2).
Figure 2: Label Packet Placement
The label value at the top of the stack is looked up when a labeled packet is received. A successful lookup reveals:
- the next hop where the packet is to be forwarded
- the operation to be performed on the label stack before forwarding
In addition, the lookup may reveal outgoing data link encapsulation and other information needed to properly forward the packet.
An empty label stack can be thought of as an unlabeled packet. An empty label stack has zero (0) depth. The label at the bottom of the stack is referred to as the Level 1 label. The label above it (if it exists) is the Level 2 label, and so on. The label at the top of the stack is referred to as the Level m label.
3.2.2.1. Label Values
The 7705 SAR uses RSVP-TE and LDP protocols for label forwarding, For packet-based services such as VLL, the 7705 SAR uses T-LDP for signaling PW labels between peer nodes.
Packets traveling along an LSP are identified by the packet label, which is the 20-bit, unsigned integer (see Label Edge and Label Switch Routers). The range is 0 through 1 048 575. Label values 0 to 15 are reserved and are defined below:
- A value of 0 represents the IPv4 Explicit NULL label. This label value is legal only at the bottom of the label stack if the label stack is immediately followed by an IPv4 header, in which case the packet forwarding is based on the IPv4 header. If the IPv4 Explicit NULL label is not at the bottom of the label stack, then the packet forwarding is based on the subsequent label.
- A value of 1 represents the router alert label. This label value is legal anywhere in the label stack except at the bottom. When a received packet contains this label value at the top of the label stack, it is delivered to a local software module for processing. The actual packet forwarding is determined by the label beneath it in the stack. However, if the packet is further forwarded, the router alert label should be pushed back onto the label stack before forwarding. The use of this label is analogous to the use of the router alert option in IP packets. Since this label cannot be at the bottom of the stack, it is not associated with a particular network layer protocol.
- A value of 3 represents the Implicit NULL label. An LER advertises this when it is requesting penultimate hop popping (PHP) and expecting unlabeled packets. The label value 3 should never appear in the label stack.
- A value of 7 represents the entropy label indicator (ELI). The ELI is a special-purpose MPLS label that indicates that the entropy label (EL) follows it in the stack.
- Values 4 through 6 and 8 through 15 are reserved for future use.
Table 3 lists the label ranges available for use by ingress labels (pop labels).
Table 3: Ingress Label Values (Pop Labels)
Label Values | Description |
16 through 31 | Reserved for future use |
32 through 1023 | Available for static outer LSP tunnel label assignment |
1024 through 2047 | Reserved for future use |
2048 through 18 431 1 | Statically assigned for services (inner pseudowire label) |
32 768 through 131 071 | Dynamically assigned for both MPLS and services |
131 072 through 1 048 575 | Reserved for future use |
- In addition, users can define part of the dynamic label range from 18 432 to 131 071 to be the range of labels for the segment routing global block (SRGB).
Note:
Table 4 lists the label ranges available for use by egress labels (push labels).
Table 4: Egress Label Values (Push Labels)
Label Values | Description |
16 through 1 048 575 | Can be used for static LSP tunnel and static PW labels |
16 through 1 048 575 | Can be dynamically assigned for both MPLS tunnel labels and PW labels |
3.2.3. MPLS Entropy Labels
This section contains information on the following topics:
3.2.3.1. Overview of Entropy Labels
The 7705 SAR supports MPLS entropy labels on RSVP-TE and SR-TE LSPs, as per RFC 6790. The entropy label provides greater granularity for load balancing on an LSR where load balancing is typically based on the MPLS label stack.
The ability of a node to receive and process an entropy label for an LSP is signaled using capability signaling (referred to as entropy label capability (ELC)). Entropy labels are supported on RSVP-TE and SR-TE tunnels.
Inserting an entropy label adds two labels in the MPLS label stack: the entropy label itself and the entropy label indicator (ELI).
The entropy label is inserted directly below the tunnel label and closest to the service payload that has advertised entropy label capability (which may be above the bottom of the stack). The value of the entropy label is calculated at the iLER and is based on a hash of the packet payload header content and other system parameters at ingress. For more information on hashing inputs, see the “Per-Flow Hashing” section in the 7705 SAR Interface Configuration Guide.
The ELI is inserted by the iLER. The ELI is a special-purpose MPLS label (value = 7) that indicates that the entropy label is the next label in the stack.
Entropy label capability is advertised at the tunnel level by the far-end node (eLER). This capability can be advertised for an RSVP-TE FEC or an SR-TE tunnel on IS-IS or OSPF. Capability signaling is not supported for point-to-multipoint LSPs, BGP tunnels, or LDP FECs. An LSR used for RSVP-TE and SR-TE tunnels will pass the entropy label capability signal from the downstream LSP segment to upstream peers. However, earlier releases that do not support entropy label functionality will pass the capability flag transparently, without altering the value.
The insertion of an entropy label by the upstream LER on a tunnel enabled for entropy label capability is enabled on a per-service basis. The entropy label is only inserted if the downstream peer has signaled entropy label support. The upstream LER only inserts a single entropy label, even if multiple LSP labels exist in a label stack.
The 7705 SAR supports the entropy label feature for the following services:
- Cpipe, Epipe, and Ipipe access to spoke SDP
- Cpipe, Epipe, and Ipipe spoke SDP to spoke SDP (vc-switching)
- VPLS SAP to VPLS spoke SDP or mesh SDP
- VPLS spoke SDP to VPLS spoke SDP
- VPRN for RSVP-TE
- R-VPLS
- IGP shortcut
- IS-IS for SR-TE
- OSPF for SR-TE
Entropy label capability on RSVP-TE LSPs is enabled on the eLER using the config>router>rsvp>entropy-label-capability command.
At the iLER, the insertion of the entropy label into the label stack is enabled using the entropy-label command under the service, mesh SDP, or spoke SDP context or under the config>router>isis (or ospf)>segment-routing context for SR-TE LSPs.
The entropy label requires the insertion of two additional labels in the label stack. In some cases, this may result in an unsupported label stack depth or large changes in the label stack depth during the lifetime of an LSP (for example, due to switching from a primary path with entropy label capability enabled to a secondary path for which the far end has not signaled entropy label capability).
The entropy-label command under the config>router>mpls and config>router>mpls>lsp contexts provides local control at the head end of an LSP over whether the entropy label is inserted on an LSP by overriding the entropy label capability signaled from the far-end LER, and control over how the additional label stack depth is accounted for. This allows the user to avoid entropy label insertion where there is a risk of the label stack depth becoming too great.
For entropy labels that are supported on LDP tunnels with remote-LFA protection (that is, for rsvp-shortcut), only loop-free alternate protect (lfa-protect) and LFA (lfa-only) are allowed.
Support of entropy labels over RSVP-TE and SR-TE tunnels are the only valid options, except when the 7705 SAR is the LER node with BGP labeled unicast (BGP-LU) tunnels. A 7705 SAR in an LER role can push and pop an entropy label for Epipe and VPLS services with a BGP-LU tunnel riding over an RSVP-TE LSP. Conversely, a 7705 SAR does not support being in an ABR or ASBR role with BGP-LU. Table 5 lists entropy label support on the 7705 SAR.
Table 5: Summary of Entropy Label Support
Service | RSVP-TE | SR-TE |
Epipe | Yes | Yes |
Ipipe | Yes | Yes |
Cpipe | Yes | Yes |
Apipe, Fpipe, Hpipe | No | No |
VPRN (MP-BGP) | Yes | Yes |
VPRN (Layer 3 spoke SDP) | Yes | Yes |
IES (Layer 3 spoke SDP) | Yes | Yes |
VPLS SDP (spoke/mesh SDP) | Yes | Yes |
LDP over IGP shortcut (RSVP) | Yes | N/A |
IGP shortcut (SR) | N/A | No |
LDP FRR over RSVP | Yes | N/A |
LDP stitching over SR (SR to LDP) | N/A | Yes 1 |
LDP stitching over SR (LDP to SR) | No | No |
BGP LU | Yes 2 | Yes 2 |
SR | No | Yes |
EVPN VPLS | Yes | Yes |
EVPN Epipe | Yes | Yes |
R-VPLS | Yes | Yes |
IGP shortcut | Yes | No |
SR FRR over TI-LFA or R-LFA | N/A | Yes |
Static route with tunnel next hop | Yes | Yes |
- On the SR segment because the SR head end injects the entropy label.
- For services that support entropy label.
Notes:
3.2.3.2. Inserting and Processing the Entropy Label
This section contains inserting and processing information on the following node types:
3.2.3.2.1. Ingress LER
The procedures at the iLER are as specified in section 4.2 of RFC 6790. In general, the router inserts an entropy label into the label stack if the downstream node for the LSP tunnel has signaled support for entropy label and the entropy label is enabled for the particular service.
RFC 6790 specifies that the iLER can insert several entropy labels in the label stack where the LSP hierarchy exists, one for each LSP in the hierarchy. However, this could result in unreasonably large label stacks. Therefore, when there are multiple LSPs in a hierarchy (for example, LDP over RSVP-TE), the router only inserts a single EL/ELI pair within the innermost LSP label closest to the service payload that has advertised entropy label capability.
The entropy label functionality is not available on first generation (Gen-1) adapter cards.
The router inserts an entropy label on a tunnel that is entropy label-capable when the service has entropy label enabled, even if an implicit or explicit NULL label has been signaled by the downstream LSR or LER. This ensures consistent behavior and ensures that the entropy label value as determined by the iLER is maintained where a tunnel with an implicit NULL label is stitched at a downstream LSR.
3.2.3.2.2. LSR
If an LSR is configured for load balancing and an entropy label is found in the label stack, the LSR will take the entropy label into account in the hashing algorithm as follows:
- label-only: the entropy label is used as input to the hash routine and the rest of the label stack is ignored.
- label-ip: the entropy label and the IP packet are used as input to the hash routine and the rest of the label stack is ignored.
The entropy label functionality is not available on first generation (Gen-1) adapter cards.
If penultimate hop popping (PHP) has been requested by a next-hop LER, the LSR will retain any entropy label found immediately below the tunnel label that is to be popped. The system will retain and use the entropy label information as input to the local hash routine if an applicable LSR load-balancing mode has been configured.
For more information on LSR load balancing, see the “LSR Hashing” section in the 7705 SAR Interface Configuration Guide.
3.2.3.2.3. Egress LER
At an eLER, if an ELI and entropy label are detected in the label stack, both the ELI and entropy label are popped and the packet processed as normal. This occurs whether or not the system has signaled entropy label capability.
If an ELI is popped that has the bottom of stack (BoS) bit set, the system will discard the packet.
3.2.3.3. Entropy Label on OAM Packets
Service OAM packets also include an entropy label and ELI if entropy label capability is signaled for the corresponding tunnel and entropy label is enabled for the service. The EL/ELI pair is inserted at the same level in the label stack as it is in user data packets; that is, within the innermost LSP label context closest to the service payload that has advertised entropy label capability. The EL/ELI pair will therefore always reside at a different level in the label stack from special-purpose labels related to the service payload (for example, the router alert label).
OAM packets at the LSP level, such as LSP ping and LSP trace, do not have the EL/ELI pair inserted.
3.2.3.4. Segment Routing Entropy Label and IPSec, ESPI Hashing, and NGE
Segment routing with entropy label can be used with IPSec and NGE services and with ESPI hashing, as listed below:
- IPSec and segment routing entropy label
- IPSec over BGP 3107 over segment routing with entropy label
- IPSec over static route over segment routing with entropy label
- VLL over GRE over IPSec over BGP 3107 over segment routing with entropy label
- VLL over GRE over IPSec over static route over segment routing with entropy label
- ESPI hashing GRT/VPRN
- NGE
- VLL, VPLS, and VPRN NGE interaction with entropy label
3.2.3.5. Entropy Label Configuration
Figure 3 illustrates the use of entropy labels at the service level.
The iLER has entropy label enabled under an applicable service context and the eLER has entropy label capability enabled. The iLER inserts the ELI and the EL into the label stack. The entropy label value is based on the service ID for point-to-point Layer 2 services.
At the LSR, if hashing is enabled, the LSR recognizes the ELI and uses the entropy label value as the hash result. If the entropy-label command had been disabled at the iLER, the LSR would not find the ELI and would default to hashing based on the label stack, if applicable.
Figure 3: Entropy Label and Load Balancing
At the ingress LER:
config>service>cpipe>spoke-sdp>entropy-label
config>service>epipe>spoke-sdp>entropy-label
config>service>ipipe>spoke-sdp>entropy-label
config>service>vpls>spoke-sdp>entropy-label
config>service>vpls>mesh-sdp>entropy-label
config>service>vprn>entropy-label
config>service>vprn>interface>spoke-sdp>entropy-label
config>router>isis>segment-routing>entropy-label
config>router>ospf>segment-routing>entropy-label
At the egress LER:
config>router>entropy-label
config>router>rsvp>entropy-label-capability
config>router>mpls>lsp>entropy-label
config>router>isis>entropy-label>override-tunnel-elc
config>router>ospf>entropy-label>override-tunnel-elc
The per-service-hashing command and the l4-load-balancing, teid-load-balancing, and spi-load-balancing commands are mutually exclusive.
For IP traffic, use the l4-load-balancing command. For IP traffic with mobile payload, use the teid-load-balancing and/or the spi-load-balancing command.
3.2.4. Label Edge and Label Switch Routers
A 7705 SAR performs different functions based on its position in an LSP—ingress, egress, or transit—as described in the following list:
- ingress Label Edge Router (iLER) — The router at the beginning of an LSP is the iLER. The ingress router encapsulates packets with an MPLS header and forwards the packets to the next router along the path. An LSP can only have one ingress router.
- Label Switching Router (LSR) — An LSR can be any intermediate router in the LSP between the ingress and egress routers, swapping the incoming label with the outgoing MPLS label and forwarding the MPLS packets it receives to the next router in the LSP. An LSP can have 0 to 253 transit routers.
- egress Label Edge Router (eLER) — The router at the end of an LSP is the eLER. The egress router strips the MPLS encapsulation, which changes it from an MPLS packet to a data packet, and then forwards the packet to its final destination using information in the forwarding table. An LSP can have only one egress router. The ingress and egress routers in an LSP cannot be the same router.
A router in a network can act as an ingress, egress, or transit router for one or more LSPs, depending on the network design.
Constrained-path LSPs are signaled and are confined to one Interior Gateway Protocol (IGP) area. These LSPs cannot cross an autonomous system (AS) boundary.
Static LSPs can cross AS boundaries. The intermediate hops are manually configured so that the LSP has no dependence on the IGP topology or a local forwarding table.
3.2.5. LSP Types
The following LSP types are supported:
- static LSPs — a static LSP specifies a static path. All routers that the LSP traverses must be configured manually with labels. No RSVP-TE or LDP signaling is required. Static LSPs are discussed in this chapter.
- signaled LSPs — LSPs are set up using the RSVP-TE or LDP signaling protocol. The signaling protocol allows labels to be assigned from an ingress router to the egress router. Signaling is triggered by the ingress routers. Configuration is required only on the ingress router and is not required on intermediate routers. Signaling also facilitates path selection. RSVP-TE is discussed in this chapter, and LDP is discussed in Label Distribution Protocol.There are two types of signaled LSP:
- explicit-path LSPs — MPLS uses RSVP-TE to set up explicit-path LSPs. The hops within the LSP are configured manually. The intermediate hops must be configured as either strict or loose, meaning that the LSP must take either a direct path from the previous hop router to this router (strict) or can traverse other routers (loose). Thus, you can control how the path is set up. Explicit-path LSPs are similar to static LSPs but require less configuration. See RSVP and RSVP-TE. An explicit path that has not specified any hops will follow the IGP route.
- constrained-path LSPs — for constrained-path LSPs, the intermediate hops of the LSP are dynamically assigned. A constrained-path LSP relies on the Constrained Shortest Path First (CSPF) routing algorithm to find a path that satisfies the constraints for the LSP. In turn, CSPF relies on the topology database provided by an extended IGP such as OSPF or IS-IS.Once the path is found by CSPF, RSVP-TE uses the path to request the LSP setup. CSPF calculates the shortest path based on the constraints provided, such as bandwidth, class of service, and specified hops.
If Fast Reroute (FRR) is configured, the ingress router signals the downstream routers so that each downstream router can preconfigure a detour route for the LSP that will be used if there is a failure on the original LSP. If a downstream router does not support FRR, the request is ignored and the router continues to support the original LSP. This can cause some of the detour routes to fail, but the original LSP is not impacted. For more information on FRR, see RSVP-TE Fast Reroute (FRR).
No bandwidth is reserved for the reroute path. If the user enters a value in the bandwidth parameter in the config>router>mpls>lsp>fast-reroute context, it will have no effect on establishing the backup LSP. The following warning message is displayed:
“The fast reroute bandwidth command is not supported in this release.”
3.3. RSVP and RSVP-TE
The Resource Reservation Protocol (RSVP) is a network control protocol used by a host to request specific qualities of service from the network for particular application data streams or flows. RSVP is also used by routers to deliver quality of service (QoS) requests to all nodes along the paths of the flows and to establish and maintain operational state to provide the requested service. In general, RSVP requests result in resources reserved in each node along the data path.
The Resource Reservation Protocol for Traffic Engineering (RSVP-TE) is an extended version of RSVP for MPLS. RSVP-TE uses traffic engineering extensions to support automatic signaling of LSPs. MPLS uses RSVP-TE to set up traffic-engineered LSPs. See RSVP-TE Extensions for MPLS for more information.
3.3.1. RSVP-TE Overview
RSVP-TE requests resources for simplex (unidirectional) flows. Therefore, RSVP-TE treats a sender as logically distinct from a receiver, although the same application process may act as both a sender and a receiver at the same time. Duplex flows require two LSPs, to carry traffic in each direction.
RSVP-TE is a signaling protocol, not a routing protocol. RSVP-TE operates with unicast and multicast routing protocols. Routing protocols determine where packets are forwarded. RSVP-TE consults local routing tables to relay RSVP-TE messages.
RSVP-TE uses two message types to set up LSPs, PATH and RESV. Figure 4 depicts the process to establish an LSP.
- The sender (the ingress LER (iLER)) sends PATH messages toward the receiver, (the egress LER (eLER)) to indicate the forwarding equivalence class (FEC) for which label bindings are desired. PATH messages are used to signal and request the label bindings required to establish the LSP from ingress to egress. Each router along the path observes the traffic type.
- PATH messages facilitate the routers along the path to make the necessary bandwidth reservations and distribute the label binding to the router upstream.
- The eLER sends label binding information in the RESV messages in response to PATH messages received.
- The LSP is considered operational when the iLER receives the label binding information.
Figure 4: Establishing LSPs
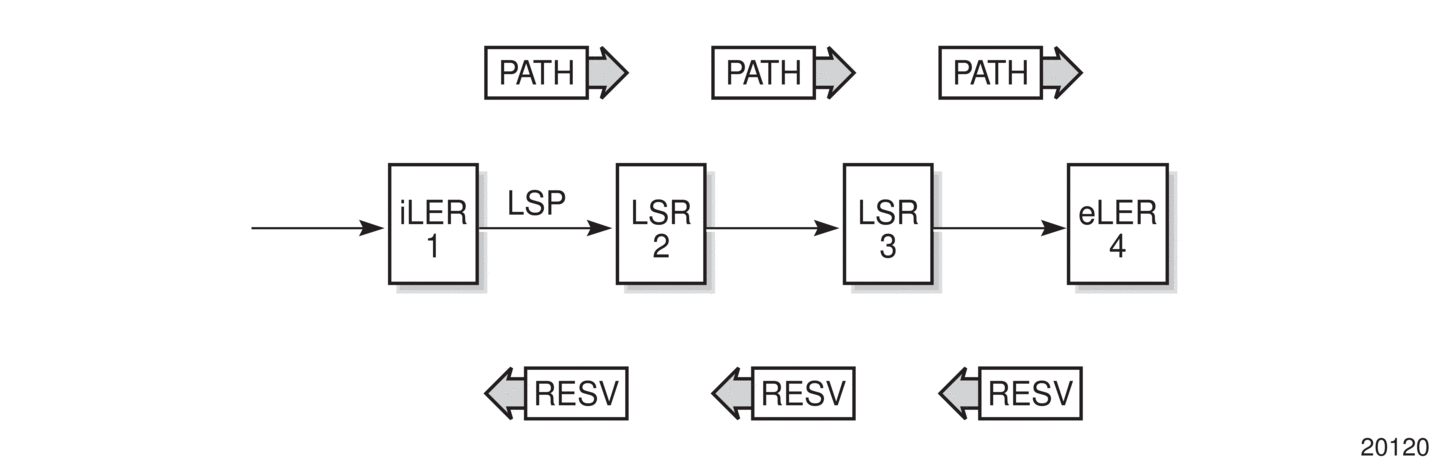
Figure 5 displays an example of an LSP path set up using RSVP-TE. The ingress label edge router (iLER 1) transmits an RSVP-TE PATH message (path: 30.30.30.1) downstream to the egress label edge router (eLER 4). The PATH message contains a label request object that requests intermediate LSRs and the eLER to provide a label binding for this path.
Figure 5: LSP Using RSVP-TE Path Setup
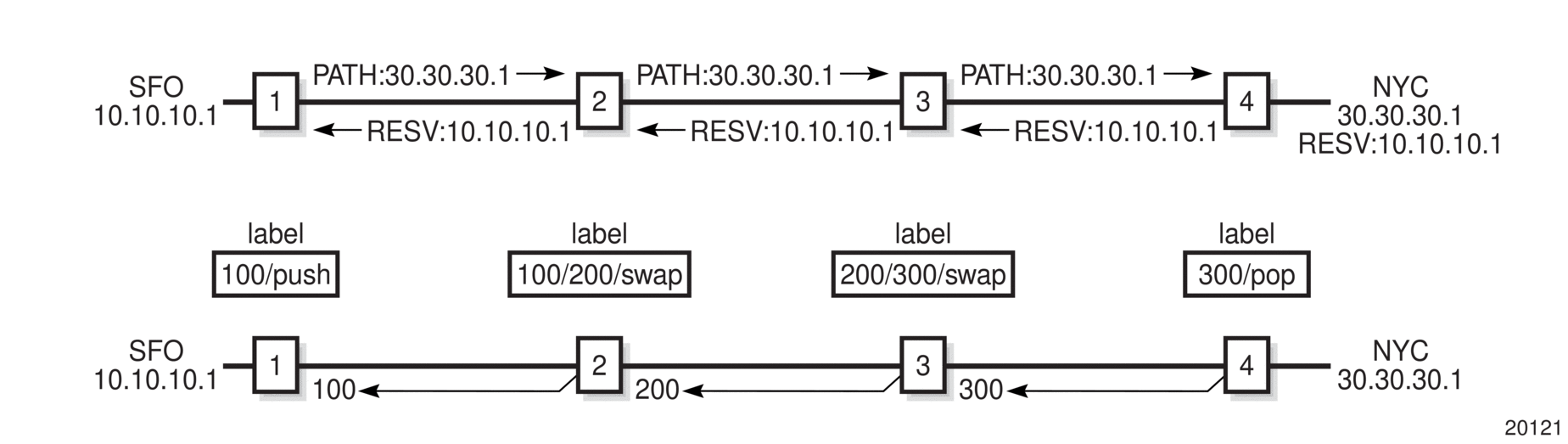
In addition to the label request object, an RSVP-TE PATH message can also contain a number of optional objects:
- explicit route object (ERO) — when the ERO is present, the RSVP-TE PATH message is forced to follow the path specified by the ERO (independent of the IGP shortest path)
- record route object (RRO) — allows the iLER to receive a listing of the LSRs that the LSP tunnel actually traverses
- session attribute object — controls the path setup priority, holding priority, and local rerouting features
Upon receiving a PATH message containing a label request object, the eLER transmits an RESV message that contains a label object. The label object contains the label binding that the downstream LSR communicates to its upstream neighbor. The RESV message is sent upstream towards the iLER, in a direction opposite to that followed by the PATH message. Each LSR that processes the RESV message carrying a label object uses the received label for outgoing traffic associated with the specific LSP. When the RESV message arrives at the ingress LSR, the LSP is established.
3.3.1.1. Using RSVP-TE for MPLS
Hosts and routers that support both MPLS and RSVP-TE can associate labels with RSVP-TE flows. When MPLS and RSVP-TE are combined, the definition of a flow can be made more flexible. Once an LSP is established, the traffic through the path is defined by the label applied at the ingress node of the LSP. The mapping of label to traffic can be accomplished using a variety of criteria. The set of packets that are assigned the same label value by a specific node are considered to belong to the same Forwarding Equivalence Class (FEC) that defines the RSVP-TE flow.
For use with MPLS, RSVP-TE already has the resource reservation component built in, making it ideal to reserve resources for LSPs.
3.3.1.2. RSVP-TE Extensions for MPLS
The RSVP-TE extensions enable MPLS to support the creation of explicitly routed LSPs, with or without resource reservation. Several of the features enabled by these extensions were implemented to meet the requirements for traffic engineering over MPLS, which enables the creation of traffic trunks with specific characteristics. None of the TE extensions result in backward compatibility problems with traditional RSVP implementations.
To run properly, the traffic engineering capabilities of RSVP-TE require an underlying TE-enabled IGP routing protocol. The 7705 SAR supports OSPF and IS-IS with TE extensions.
Routing protocols make it possible to advertise the constraints imposed over various links in the network. For example, in order for the nodes in a network to choose the best link for signaling a tunnel, the capacity of a particular link and the amount of reservable capacity must be advertised by the IGP. RSVP-TE makes use of these constraints to request the setup of a path or LSP that traverses only those links that are part of an administrative group (admin groups are described in the following list). Thus, both RSVP-TE and the IGP-TE (that is, OSPF-TE or IS-IS-TE for the 7705 SAR) must be enabled and running simultaneously.
The following TE capabilities are supported:
- hop limit — the hop limit is the maximum number of LSRs that a given LSP can traverse, including the ingress and the egress LERs. Typically, the hop limit is used to control the maximum delay time for mission-critical traffic such as voice traffic.The hop limit applies to the primary LSP, any backup LSPs, and LSPs configured to be used in Fast Reroute (FRR) situations.
- admin groups — administrative groups provide a way to define which LSR nodes should be included or excluded while signaling an LSP. For example, it might be desirable to avoid some nodes or links that are known to be used heavily from being included in the path of an LSP, or to include a specific LSR node to ensure that a newly signaled RSVP-TE tunnel traverses that LSR node.Administrative groups apply to both primary and secondary LSPs. They are defined under the config>router>if-attribute context, and are applied at the MPLS interface level, as well as at the LSP and the primary and secondary LSP levels through include and exclude commands.
- bandwidth — the bandwidth capability (supported by RSVP-TE), is similar to the Connection Admission Control (CAC) function in ATM. During the establishment phase of RSVP-TE, the LSP PATH message contains the bandwidth reservation request. If the requested capacity is available, the RESV message confirms the reservation request. The amount of reserved bandwidth stated in the request is deducted from the amount of reservable bandwidth for each link over which the LSP traverses.The bandwidth capability applies to both primary and secondary LSPs, and LSPs configured to be used in Fast Reroute (FRR) situations.
3.3.1.3. Hello Protocol
The Hello protocol detects the loss of a neighbor node (node failure detection) or the reset of a neighbor’s RSVP-TE state information. In standard RSVP, neighbor monitoring occurs as part of the RSVP soft-state model. The reservation state is maintained as cached information that is first installed and then periodically refreshed by the ingress and egress LERs. If the state is not refreshed within a specified time interval, the LSR discards the state because it assumes that either the neighbor node has been lost or its RSVP-TE state information has been reset.
The Hello protocol extension is composed of a Hello message, a Hello request object and a Hello ACK object. Hello processing between two neighbors supports independent selection of failure detection intervals. Each neighbor can automatically issue Hello request objects. Each Hello request object is answered by a Hello ACK object.
3.3.1.4. Authentication
Protocol authentication protects against malicious attacks on the communications between routing protocol neighbors. These attacks could either disrupt communications or inject incorrect routing information into the systems routing table. The use of authentication keys can help to protect routing protocols from these types of attacks.
All RSVP-TE protocol exchanges can be authenticated. This guarantees that only trusted routers can participate in autonomous system routing.
Authentication must be explicitly configured and can be done using two separate mechanisms:
- configuration of an explicit authentication key and algorithm using the authentication-key command
- configuration of an authentication keychain using the auth-keychain command
Either the authentication-key command or the auth-keychain command can be used by RSVP-TE, but both cannot be supported at the same time. If both commands are configured, the auth-keychain configuration will be applied and the authentication-key command will be ignored.
By default, authentication is not enabled on an interface.
3.3.1.4.1. Authentication Key
When enabled on an RSVP-TE interface with the authentication-key command, authentication of RSVP messages operates in both directions of the interface. A node maintains a security association with its neighbors for each authentication key. The following items are stored in the context of this security association:
- the HMAC-MD5 authentication algorithm
- the key used with the authentication algorithm
- the lifetime of the key. A key is a user-generated key using third-party software or hardware. The value is entered as a static string into the CLI configuration of the RSVP interface. The key will continue to be valid until it is removed from that RSVP interface.
- the source address of the sending system
- the latest sending sequence number used with this key identifier
The RSVP sender transmits an authenticating digest of the RSVP message, computed using the shared authentication key and a keyed hash algorithm. The message digest is included in an Integrity object that also contains a Flags field, a Key Identifier field, and a Sequence Number field. The RSVP sender complies with the procedures for RSVP message generation in RFC 2747, RSVP Cryptographic Authentication.
An RSVP receiver uses the key together with the authentication algorithm to process received RSVP messages.
If a point of local repair (PLR) node switches the path of the LSP to a bypass LSP, it does not send the integrity object in the RSVP messages over the bypass tunnel. If an integrity object is received from the merge point (MP) node, then the message is discarded since there is no security association with the next-next-hop MP node.
The 7705 SAR MD5 implementation does not support the authentication challenge procedures in RFC 2747.
3.3.1.4.2. Authentication Keychains
The keychain mechanism allows for the creation of keys used to authenticate RSVP-TE communications. Each keychain entry defines the authentication attributes to be used in authenticating RSVP-TE messages from remote peers or neighbors; the entry must include at least one key entry to be valid. The keychain mechanism also allows authentication keys to be changed without affecting the state of the RSVP-TE adjacencies and supports stronger authentication algorithms than plain text and MD5.
Keychains are configured in the config>system>security>keychain context. For more information about configuring keychains, refer to the 7705 SAR System Management Guide, “TCP Enhanced Authentication and Keychain Authentication”.
The keychain is then associated with an RSVP-TE interface with the auth-keychain command.
For a key entry to be valid, it must include a valid key, the current system clock value must be within the begin and end time of the key entry, and the algorithm specified must be supported by RSVP-TE.
RSVP-TE supports the following authentication algorithms:
- HMAC-MD5
- HMAC-SHA-1-96
- HMAC-SHA-1
- HMAC-SHA-256
Keychain errors are handled as follows.
- If a keychain exists but there are no active key entries with an authentication type that matches the type supported by RSVP-TE, inbound RSVP-TE packets will not be authenticated and will be discarded and no outbound RSVP-TE packets will be sent.
- If a keychain exists but the last key entry has expired, a log entry will be raised indicating that all keychain entries have expired.RSVP-TE requires that the protocol continue to authenticate inbound and outbound traffic using the last valid authentication key.
3.3.1.5. Non-Router ID Addresses as Destinations and Hops
The address of a configured loopback interface, other than the router ID, can be used as the destination of an RSVP LSP. For a constrained-path LSP, CSPF searches for the best path that matches the constraints across all areas or levels of the IGP where this address is reachable. If the address is the router ID of the destination node, then CSPF selects the best path across all areas or levels of the IGP for that router ID, regardless of which area or level the router ID is reachable for as an interface.
The address of a loopback interface other than the router ID can also be configured as a hop in the LSP path hop definition. If the hop is “strict” and corresponds to the router ID of the node, the CSPF path may use any TE-enabled link to the downstream node based on best cost. If the hop is “strict” and does not correspond to the router ID of the node, CSPF will fail.
3.3.2. RSVP LSP and LDP FEC Statistics
RSVP LSP and LDP FEC statistics allow operators to monitor traffic being forwarded between any two PE routers and for all services using an RSVP or LDP SDP. If the LSP is used as a shortcut to transport BGP LU, VPRN traffic over MP-BGP or IGP prefixes, statistics are collected for these IP packets being forwarded.
The following statistics are collected for each RSVP LSP or LDP FEC:
- per forwarding class forwarded in-profile packet count
- per forwarding class forwarded in-profile byte count
- per forwarding class forwarded out-of-profile packet count
- per forwarding class forwarded out-of-profile byte count
For an RSVP LSP, these counters are available for the egress data path at the ingress LER and for the ingress data path at the egress LER.
For an LDP FEC, these counters are available for the egress data path at the ingress LER and LSR. Because an ingress LER is also potentially an LSR for an LDP FEC, combined egress data path statistics are provided whenever applicable.
OAM packets that are forwarded using LSP encapsulation, such as LSP ping and LSP trace, are also included in the above counters.
Dropped packets and bytes for an RSVP LSP or LDP FEC are not counted on the ingress LER.
Octet counters are for the entire frame and include the label stack and Layer 2 header and padding, similar to existing MPLS interface counters. For that reason, ingress and egress octet counters for an RSVP LSP may differ slightly if the type of interface or encapsulation is different (POS, Ethernet null, or Ethernet dot1q).
RSVP LSP and LDP FEC statistics counters can be retrieved by:
- using the CLI show command for the RSVP LSP or the LDP FEC
- using the CLI monitor command applied to a specific RSVP LSP or LDP FEC
- using an SNMPv3 interface to query the MIB
- accessing an accounting file if statistics collection is enabled with the default or a user-specified accounting policy for the RSVP LSP or LDP FEC
RSVP LSP and LDP FEC statistics counters are not saved to an accounting file unless statistics collection is enabled and the specific RSVP LSP or LDP FEC statistics collection record is included in the default accounting policy or in a user-defined accounting policy using the following commands:
- RSVP LSP ingress data path countersconfig>router>mpls>ingress-statistics>lsp>collect-statsconfig>router>mpls>ingress-statistics>lsp>accounting-policy policy-id
- RSVP LSP egress data path countersconfig>router>mpls>lsp>egress-statistics>collect-statsconfig>router>mpls>lsp>egress-statistics>accounting-policy policy-id
- LDP FEC egress data path countersconfig>router>ldp>egress-statistics>fec-prefix>collect-statsconfig>router>ldp>egress-statistics>fec-prefix>accounting-policy policy-id
3.3.2.1. Configuring RSVP LSP Statistics at Ingress LER
At the ingress LER, statistics are configured in the egress data path of an originating LSP with the config>router>mpls>lsp>egress-statistics command in the LSP configuration at the head-end node. Statistics collection in the egress data path is enabled after the user executes the no shutdown command in the egress-statistics context. By default, this function is in a shutdown state.
Statistics cannot be configured if the LSP name contains a colon (:), which is used as a field separator by the ingress LER for encoding the LSP and path names into the RSVP Session Name field in the Session_Attribute object.
The no form of the egress-statistics command disables statistics collection in the egress data path and removes the accounting policy association from the RSVP LSP. Users can choose to disable statistics in the egress data path while keeping the accounting policy association of the RSVP LSP with the config>router>mpls>lsp>egress-statistics shutdown command.
The same set of counters are updated for packets forwarded over any path of the LSP. In the steady state, counters are updated for packets forwarded over the active path of the LSP. The active path can be the primary path, one of the secondary paths, the FRR detour path, or the FRR bypass path when the head-end node is also the PLR.
The LSP counters are maintained over the lifetime of the LSP as long as statistics are enabled. The user can clear the counters with the clear>router>mpls>lsp-egress-stats [lsp-name] command.
LSP statistics are not collected on a dynamic or static bypass tunnel. LSP egress statistics are also not collected if the head-end node is also the penultimate-popping hop (PHP) node for a single-hop LSP using an implicit null label. However, if any label is pushed onto the label stack, for example, the Layer 2 or Layer 3 service label, the egress statistics are counted for the LSP even if the transport MPLS label is not present.
When a hierarchy of LSPs is in use, statistics collection on the outermost label corresponding to the tunneling LSP and on the inner labels, corresponding to the tunneled LSPs, are mutually exclusive. The outermost label takes precedence. Consequently, when the user enables statistics collection on an RSVP LSP that is also used for tunneling LDP FECs with the LDP over RSVP shortcut, statistics will be collected on the RSVP LSP only. No statistics are collected for an LDP FEC tunneled over this RSVP LSP even if the user enabled statistics collection on the FEC. When the user disables statistics collection on the RSVP LSP, statistics collection, if enabled, will be performed on the tunneled LDP FEC.
LSP statistics are not collected on static LSPs. Auto-LSP templates do not support LSP statistics collection.
3.3.2.2. Configuring RSVP LSP Statistics at Egress LER
At the egress LER, statistics are configured in the ingress data path of a terminating LSP by entering the LSP name, along with the ingress LER system interface address, with the config>router>mpls>ingress-statistics>lsp lsp-name sender ip-address command. Statistics collection is enabled in the ingress data path after the user executes the no shutdown command in the ingress-statistics context. By default, this function is in a shutdown state.
The LSP name must correspond to the name configured by the user at the ingress LER. Statistics cannot be configured if the LSP name contains a colon (:), which is used as a field separator by the ingress LER for encoding the LSP and path names into the RSVP Session Name field in the Session_Attribute object.
The no form of the ingress-statistics command disables statistics collection in the ingress data path and removes the accounting policy association from the RSVP LSP. Users can choose to disable statistics in the ingress data path while keeping the accounting policy association of the RSVP LSP with the config>router>mpls>ingress-statistics>lsp>shutdown command.
The same set of counters are updated for packets received over any path of the LSP. In the steady state, the counters are updated for packets received over the active path of the LSP. The active path can be the primary path, one of the secondary paths, the FRR detour path, or the FRR bypass path when the tail-end node is also the MP.
The LSP counters are maintained over the lifetime of the LSP as long as statistics are enabled. The user can clear the counters with the clear>router>mpls>lsp-ingress-stats ip-address lsp lsp-name command.
When a hierarchy of LSPs is in use, statistics collection on the outermost label corresponding to the tunneling LSP and on the inner labels, corresponding to the tunneled LSPs, are mutually exclusive. The outermost label takes precedence.
Because ingress data path statistics are not supported for an LDP FEC, there are no statistics collected for an LDP FEC, however if the LDP FEC is tunneled over an RSVP shortcut LSP that has LSP ingress statistics configured, the statistics are collected for the RSVP LSP
The user can enable statistics collection on a manual bypass LSP terminating on the egress LER. However, all LSPs whose primary path is protected by the manual bypass will not collect statistics when they activate forwarding over the manual bypass. If the user disables statistics collection on the manual bypass LSP, statistics collection, if enabled, is continued on the protected LSP when the bypass LSP is activated.
A flag in the output of the show command for the LSP statistics will indicate if there were no path state blocks (PSBs) that matched the specified LSP name at any given point in time. This could be due to the absence of the RSVP session or to the presence of a session type that is not supported; for example, the LSP name matched a point-to-multipoint LSP. The counters will show all zero values, which could otherwise be confused with an LSP with a valid matched PSB that is not receiving packets.
3.3.2.3. Configuring LDP FEC Statistics
At the ingress LER and LSR, statistics collection is configured in the egress data path of an LDP FEC by specifying the FEC prefix with the config>router>ldp>egress-statistics>fec-prefix command. Statistics collection is enabled in the egress data path after the user executes the no shutdown command under the egress-statistics context. By default, this function is in a shutdown state.
The no form of the egress-statistics command disables statistics collection in the egress data path and removes the accounting policy association from the LDP FEC. Users can choose to disable statistics in the egress data path while keeping the accounting policy association of the LDP FEC with the config>router>ldp>egress-statistics>fec-prefix>shutdown command.
Statistics collection applies to prefix FECs imported from both LDP neighbors and T-LDP neighbors.
The egress data path counters are updated for both originating and transit packets. Originating packets may be service packets or IP user and control packets forwarded either as BGP LU over LDP FEC or as VPRN traffic (MP-BGP) over LDP FEC or simply over LDP FEC IGP shortcut. Transit packets of the FEC are label-switched on this node.
When ECMP is enabled and multiple paths exist for a FEC, the same set of counters is updated for each packet forwarded over any of the ECMP links for as long as this FEC is active.
The LDP FEC counters are maintained over the lifetime of the FEC as long as statistics are enabled. The user can clear the counters with the clear>router>ldp>fec-egress-statistics command.
For more information about LDP FEC statistics commands, see LDP Command Reference.
3.4. RSVP-TE Signaling
RSVP-TE-based signaling provides a means to establish tunnels dynamically.
RSVP-TE uses the Downstream on Demand (DOD) label distribution mode, sending PATH messages from the ingress LER node to the egress LER and RESV messages in the reverse direction. DOD label distribution is a router’s response to an explicit request from another router for label binding information. The DOD mode is in contrast to LDP on the 7705 SAR, which uses the Downstream Unsolicited (DU) label distribution mode for both PWs and LSPs. A router in DU mode will distribute label bindings to another router that has not explicitly requested the label bindings.
RSVP-TE signaling is supported when the 7705 SAR is deployed as an LER and as an LSR. When used as an LER, the 7705 SAR uses RSVP-TE signaling to set up constrained paths because only the LER knows all the constraints imposed on the LSP. When used as an LSR, the 7705 SAR uses RSVP-TE to interpret the RSVP-TE messages (including all the constraints).
With RSVP-TE, users can choose which services and PWs may use a particular LSP. One-to-one or many-to-one scenarios for binding PWs to RSVP-TE LSPs is supported, which is similar to binding PWs to static LSPs. Furthermore, each RSVP-TE LSP can be configured with its own set of attributes and constraints.
3.4.1. General Attributes of RSVP-TE
The following general attributes of RSVP-TE on the 7705 SAR are supported:
3.4.1.1. Bidirectional Forwarding Detection
Bidirectional Forwarding Detection (BFD) is supported on the 7705 SAR. In the case of BFD for RSVP-TE, an RSVP-TE enabled link is registered with the BFD state machine, and if a failure occurs the RSVP-TE interface is taken out of service. The BFD implementation on the 7705 SAR works on a hop-by-hop basis, and if BFD detects a link failure, only the two directly connected MPLS nodes are aware of that failure. If the node that detects the link failure is an LSR node, it generates PATH-ERR messages to the originators (the LER nodes) of the failing LSPs. If FRR is configured, the detecting node takes corrective action itself. See LSP Redundancy and RSVP-TE Fast Reroute (FRR) for more information on these topics.
3.4.1.1.1. RSVP-TE over Broadcast Interface with BFD
The 7705 SAR supports per-neighbor tracking when RSVP-TE is used over a broadcast interface in conjunction with BFD. Per-neighbor tracking enables RSVP-TE to distinguish neighbors from one another when the outgoing interface is a broadcast interface that is connected to multiple neighbors over a broadcast domain. If a BFD session toward a specific neighbor on the broadcast domain goes down, the session failure triggers consecutive actions (for example, an FRR switchover) only for the LSPs of the affected neighbor.
3.4.1.2. Timers
The following timers are implemented to ensure the successful operation of RSVP-TE:
- bypass-resignal-timer — the bypass resignal timer defines the time between the global reoptimization of all dynamic bypass RSVP-TE LSPs. For more information, see Bypass Resignal Timer.
- hold-timer — the hold timer defines the amount of time before an LSP is brought up and is in service, which provides protection against unreliable nodes and links
- resignal-timer — the resignal timer is used in conjunction with the route optimization process, especially after a reroute has occurred. If the newly computed path for an LSP has a better metric than the currently recorded hop list, an attempt is made to resignal that LSP, and if the attempt is successful, a make-before-break switchover occurs. If the attempt to resignal an LSP fails, the LSP continues to use the existing path and another resignal attempt is made the next time the timer expires.When the resignal timer expires, a trap and syslog message are generated.
- retry-timer — the retry timer defines a period of time before a resignal attempt is made after an LSP failure. This delay time protects network resources against excessive signaling overhead.
3.4.1.3. LSP Resignal Limit
When an LSP fails, an LER node tries to resignal it. The following limit can be configured:
- retry-limit — the retry limit defines the number of resignaling attempts in order to conserve the resources of the nodes in the network. There could be a serious loss of capacity due to a link failure where an infinite number of retries generate unnecessary message overhead.
3.4.1.4. RSVP-TE Message Pacing
RSVP-TE message pacing provides a means to limit the overwhelming number of RSVP-TE signaling messages that can occur in large MPLS networks during node failures. RSVP-TE message pacing allows the messages to be sent in timed intervals.
To protect nodes from receiving too many messages, the following message pacing parameters can be configured:
- msg-pacing — message pacing can be enabled or disabled
- max-burst — maximum burst defines the number of RSVP-TE messages that can be sent in the specified period of time
- period — period defines the interval of time used in conjunction with the max-burst parameter to send message pacing RSVP-TE messages
Message pacing needs to be enabled on all the nodes in a network to ensure the efficient operation of tier-1 nodes. Message pacing affects the number of RSVP-TE messages that a particular node can generate, not the number of messages it can receive. Thus, each node must be paced at a rate that allows the most loaded MPLS nodes to keep up with the number of messages they receive.
| Note: Typically, a tier-1 node is an aggregator of tier-2 node transmissions, which is an aggregator of tier-3 node transmissions. Tier-1 nodes are often installed at an MTSO, while tier-3 nodes are often installed at cell sites. |
3.4.1.5. RSVP-TE Overhead Refresh Reduction
RFC 2961, RSVP Refresh Overhead Reduction Extensions, defines enhancements to the RSVP-TE signaling protocol that reduce refresh overhead, which are in addition to the message pacing function.
These extensions are:
- RSVP-TE message bundling — RSVP-TE message bundling reduces the total number of RSVP-TE messages by aggregating the status information of multiple LSPs into a single RSVP-TE PDU. The 7705 SAR supports the receipt and processing of bundled RSVP-TE messages but not the transmission of bundled messages as specified in RFC 2961, section 3.3.
- reliable message delivery — reliable message delivery extends RSVP-TE to support MESSAGE_ACK. Each RSVP-TE PDU has a unique message-id for sequence tracking purposes. When an RSVP-TE message arrives, the recipient acknowledges the reception of the specific message-id (this is similar to TCP ACK messages). Lost PDUs can be detected and re-sent with this method, which helps reduce the refresh rate because there are two endpoints tracking the received/lost messages.
- summary refresh — the summary refresh capability uses a single message-id list to replace many individual refresh messages and sends negative ACKs (NACKs) for any message-id that cannot be matched (verified). The summary refresh capability reduces the number of message exchanges and message processing between peers. It does not reduce the amount of soft state stored in the node. The term soft state refers to the control state in hosts and routers that will expire if not refreshed within a specified amount of time (see RFC 2205 for information on soft state).
These capabilities can be enabled on a per-RSVP-TE interface basis and are referred to collectively as “refresh overhead reduction extensions”. When refresh-reduction is enabled on a 7705 SAR RSVP-TE interface, the node indicates this to its peer by setting a refresh-reduction-capable bit in the flags field of the common RSVP-TE header. If both peers of an RSVP-TE interface set this bit, all three of the capabilities listed above can be used. The node monitors the setting of this bit in received RSVP-TE messages from the peer on the interface. If the bit is cleared, the node stops sending summary refresh messages. If a peer did not set the refresh-reduction-capable bit, a 7705 SAR node does not attempt to send summary refresh messages.
Also, reliable delivery of RSVP-TE messages over the RSVP-TE interface can be enabled using the reliable-delivery option.
3.4.1.6. RSVP-TE Reservation Styles
LSPs can be signaled with explicit reservation styles for the reservation of resources, such as bandwidth. A reservation style describes a set of attributes for a reservation, including the sharing attributes and sender selection attributes. The style information is part of the LSP configuration. The 7705 SAR supports two reservation styles:
- fixed filter (FF) — the fixed filter (FF) reservation style specifies an explicit list of senders and a distinct reservation for each of them. Each sender has a dedicated reservation that is not shared with other senders. Each sender is identified by an IP address and a local identification number, the LSP ID. Because each sender has its own reservation, a unique label and a separate LSP can be constructed for each sender-receiver pair. For traditional RSVP applications, the FF reservation style is ideal for a video distribution application in which each channel (or source) requires a separate pipe for each of the individual video streams.
- shared explicit (SE) — the shared explicit (SE) reservation style creates a single reservation over a link that is shared by an explicit list of senders. Because each sender is explicitly listed in the RESV message, different labels can be assigned to different sender-receiver pairs, thereby creating separate LSPs.
If the FRR option is enabled for the LSP and the facility FRR method is selected at the head-end node, only the SE reservation style is allowed. If a 7705 SAR PLR node receives a PATH message with fast reroute requested with facility method and the FF reservation style, it will reject the reservation. The one-to-one backup method supports both FF and SE styles.
3.4.1.7. Implicit Null Label
The implicit null label option enables an eLER to receive MPLS packets from the previous-hop LSR without the outer LSP label.
The implicit null label is included in RESV messages sent by the eLER to the previous-hop LSR. When the implicit null label is signaled to the LSR, it pops the outer label before sending the MPLS packet to the eLER; this is known as penultimate hop popping.
The implicit null label option can be enabled for all RSVP-TE interfaces and for all RSVP-TE LSPs for which the router is the eLER by using the implicit-null-label command in the config>router>rsvp context.
RSVP-TE must be shut down before this command can be used.
The implicit null label option can also be enabled or disabled on a specific RSVP-TE interface, overriding the RSVP-TE level configuration, by using the implicit-null-label {enable | disable} command in the config>router>rsvp>interface context.
The implicit null label is enabled for all LSPs for which the router is the eLER and for which the PATH message is received from the previous-hop LSR over the RSVP-TE interface.
With facility backup, if the eLER is also the merge point (MP) node, the incoming interface for the PATH refresh message over the bypass tunnel dictates whether the packet will use the implicit null label. Similarly, with one-to-one backup, if the eLER is also the detour merge point (DMP) node, the incoming interface for the PATH refresh message over the detour LSP dictates whether the packet will use the implicit null label.
The RSVP-TE interface must be shut down before this command can be used.
3.4.1.8. RSVP-TE Entropy Labels
The 7705 SAR supports entropy labels as described in MPLS Entropy Labels.
3.5. LSP Redundancy
Each primary LSP can be protected by up to two secondary LSPs. When the LER detects a primary LSP failure, it signals its secondary LSPs, if any have been configured, and automatically switches to the first one that is available. LSP redundancy supports shared risk link groups (SRLG). See Shared Risk Link Groups for more information on SRLG.
LSP redundancy differs from the Fast Reroute (FRR) feature in that LSP redundancy is controlled by the LER that initiated the LSP, whereas FRR uses the node that detects the failure to take recovery action. This means that LSP redundancy takes longer to reroute traffic than FRR because failure messages need to traverse multiple hops to reach the LER and activate LSP redundancy, whereas an FRR-configured node responds immediately to bypass the failed node or link. See RSVP-TE Fast Reroute (FRR) for more information on FRR.
The following parameters can be configured for primary and secondary LSPs:
- bandwidth — the amount of bandwidth needed for the secondary LSP can be reserved and can be any value; it does not need to be identical to the value reserved by the primary LSP. Bandwidth reservation can be set to 0, which is equivalent to reserving no bandwidth.
- inclusion and exclusion of nodes — by including or excluding certain nodes, you can ensure that the primary and secondary LSPs do not traverse the same nodes and therefore ensure successful recovery. Each secondary LSP can have its own list of included and excluded nodes.
- hop limit — the hop limit is the maximum number of LSRs that a secondary LSP can traverse, including the ingress and egress LERs.
- standby (secondary LSPs only) — when a secondary LSP is configured for standby mode, it is signaled immediately and is ready to take over traffic the moment the LER learns of a primary LSP failure. This mode is also called hot-standby mode.When a secondary LSP is not in standby mode, then it is only signaled when the primary LSP fails. If there is more than one secondary LSP, they are all signaled at the same time (upon detection of a primary LSP failure) and the first one to come up is used.If a path-preference priority value is configured for standby secondary LSP paths, the standby secondary LSP configured with the highest path priority becomes the active LSP when the primary LSP fails.
3.5.1. Make-Before-Break (MBB) Procedures for LSP and Path Parameter Configuration Changes
The Make-Before-Break (MBB) procedure allows an LSP to switch from an existing working path to a new path without interrupting service. The MBB procedure does this by first signaling the new path when it is operationally up, having the ingress LER move the traffic to the new path, and then allowing the ingress LER to tear down the original path.
The MBB procedure is invoked during the following operations:
- timer-based and manual resignal of an LSP path
- Fast Reroute (FRR) global revertive procedures
- Traffic Engineering (TE) graceful shutdown procedures
- update of the secondary path due to an update to the primary path SRLG
- LSP primary or secondary path name change
- LSP or path configuration parameter change
MBB procedure coverage has been extended to most of the other LSP-level and path-level parameters as follows:
- including or excluding admin groups at the LSP and path levels
- enabling or disabling the LSP-level CSPF option
- enabling or disabling LSP-level use-te-metric parameters when the CSPF option is enabled
- enabling or disabling the LSP-level hop-limit option in the fast-reroute context
- enabling the LSP-level least-fill option
- enabling or disabling the LSP-level adspec option
- changing between node-protect and no node-protect (link-protect) values in the LSP-level fast-reroute option
- changing the LSP-level and path-level hop-limit parameter values
- enabling or disabling primary or secondary path record or record-label options
The MBB procedure is not supported on a manual bypass LSP.
3.5.2. Automatic Creation of RSVP-TE LSPs
Automatic creation of RSVP-TE LSPs enables the automated creation of point-to-point RSVP-TE LSPs within a single IGP IS-IS level or OSPF area that can subsequently be used by services and/or IGP shortcuts. The feature is divided into two modes: creation of an RSVP-TE LSP mesh, and creation of single-hop RSVP-TE LSPs.
When creating an RSVP-TE LSP mesh, the mesh can be full or partial, the extent of which is governed by a prefix list containing the system addresses of all nodes that should form part of the mesh. When using single-hop RSVP-TE LSPs, point-to-point LSPs are established to all directly connected neighbors.
The use of automatically created RSVP-TE LSPs avoids manual configuration of RSVP-TE LSP meshes. Even when provisioning tools are used to automatically provision these LSPs, automatic creation of a mesh still provides a benefit by avoiding increased configuration file sizes.
3.5.3. Automatic Creation of RSVP-TE LSP Mesh (Auto-LSP)
This feature enables the automatic creation of an RSVP-TE point-to-point LSP to a destination node whose router ID matches a prefix in the specified peer prefix policy. This LSP type is referred to as an auto-created LSP mesh. To start the process of automatically creating an RSVP-TE LSP mesh, the user must create a route policy referencing a prefix list. This prefix list contains the system addresses of all nodes that are required to be in the mesh, and can be entered as a series of /32 addresses, or simply as a range.
After the route policy is created, the user must create an LSP template containing the common parameters that are used to establish all point-to-point LSPs within the mesh. The template must be created with the keyword mesh-p2p:
config>router>mpls>lsp-template template-name mesh-p2p
Upon creation of the template, CSPF is automatically enabled and cannot be disabled. The template must also reference a default path before it can be placed in a no shutdown state.
Next, the user must associate the LSP template with the previously defined route policy, and this is accomplished using the auto-lsp lsp-template command:
config>router>mpls>auto-lsp lsp-template template-name policy peer-prefix-policy
Once the auto-lsp lsp-template command is entered, the system starts the process of establishing the point-to-point LSPs. The prefixes defined in the prefix list are checked, and if a prefix corresponds to a router ID that is present in the Traffic Engineering (TE) database, the system instantiates a CSPF-computed primary path to that prefix using the parameters specified in the LSP template.
Multiple templates can be associated with the same or different peer prefix policies. Each application of an LSP template with a given prefix in the prefix list results in the instantiation of a single CSPF-computed LSP primary path using the LSP template parameters, as long as the prefix corresponds to a router ID for a node in the TE database. Auto LSP does not support the automatic signaling of a secondary path for an LSP. If the signaling of multiple LSPs to the same destination node is required, a separate LSP template must be associated with a prefix list that contains the same destination node address. Each instantiated LSP will have a unique LSP ID and a unique tunnel ID.
The auto-created LSP is installed in the Tunnel Table Manager (TTM) and is available to applications such as resolution of BGP label routes, and resolution of BGP, IGP, and static routes. The auto-created LSP can also be used for auto-binding by a VPRN service. The auto-created LSP cannot be used as a provisioned SDP for explicit binding by services.
The auto-created LSP mesh can be signaled over both numbered and unnumbered RSVP-TE interfaces.
Up to five peer prefix policies can be associated with an LSP template. Every time the user executes the auto-lsp command with the same or different prefix policy associations or changes the prefix policy associated with an LSP template, the system re-evaluates the prefix policy. The outcome of the re-evaluation indicates to MPLS whether an existing LSP must be torn down or a new LSP must be signaled to a destination address that is already in the TE database.
If a /32 prefix is added to or removed from a prefix list associated with an LSP template, or if a prefix range is expanded or narrowed, the prefix policy re-evaluation is performed. Whether the prefix list contains one or more specific /32 addresses or a range of addresses, MPLS requires an external trigger to instantiate an LSP to a node whose address matches an entry in the prefix list. The external trigger is when the router with a router ID matching an address in the prefix list appears in the TE database. The TE database provides the trigger to MPLS.
The user must perform a no shutdown of the template before it takes effect. When a template is in use, the user must shut down the template before changing any parameters except for those LSP parameters for which the change can be handled with the Make-Before-Break (MBB) procedures (see Make-Before-Break (MBB) Procedures for LSP and Path Parameter Configuration Changes). When the template is shut down and parameters are added, removed, or modified, the existing instances of the LSP using this template are torn down and resignaled.
MBB procedures for manual and timer-based resignaling of the LSP, and for TE graceful shutdown, are supported.
The tools>perform>router>mpls>update-path command is not supported for mesh LSPs.
The one-to-one option under the fast-reroute command is also not supported.
If the TE database loses the router ID while the LSP is up, it will perform an update to the MPLS that states that the router ID is no longer in the TE database. This occurs whether the bypass backup path is activated or not. This will cause MPLS to tear down all mesh LSPs to this router ID. However, if the destination router is not a neighbor of the ingress LER and the user shuts down the IGP instance on the destination router, the router ID corresponding to the IGP instance will only be deleted from the TE database on the ingress LER after the LSA/LSP times out. If the user brings the IGP instance back up before the LSA/LSP times out, the ingress LER will delete and reinstall the same router ID at the receipt of the updated LSA/LSP. The RSVP-TE LSPs destined for this router ID will be deleted and re-established. All other failure conditions will cause the LSP to activate the bypass backup LSP or to go down without being deleted.
3.5.3.1. Multi-Area and Multi-Instance Support
A router that does not have TE links within a given IGP area or level will not have its router ID discovered in the TE database by other routers in this area or level. In other words, an auto-created LSP mesh cannot be signaled to a router that does not participate in the area or level of the ingress LER.
A mesh LSP can be signaled using TE links that belong to the same IGP area even if the router ID of the ingress and egress routers are interfaces reachable in a different area. In this case, the LSP is considered to be an intra-area LSP.
If multiple instances of IS-IS are configured on a router, each with its own router ID, the TE database on other routers will be able to discover TE links advertised by each instance. In this case, an instance of an LSP can be signaled to each router ID with a CSPF path computed using TE links within each instance.
If multiple instances of IS-IS are configured on a destination router, each with the same router ID, a single instance of LSP will be signaled from other routers. If the user shuts down one IGP instance, this will have no impact as long as the other IGP instances remain up. The LSP will remain up and will forward traffic using the same TE links. The same behavior exists with a provisioned LSP.
3.5.3.2. Mesh LSP Name Encoding
When the ingress LER signals the path of an auto-created mesh LSP, it includes the name of the LSP and the path name in the Session Name field of the Session Attribute object in the PATH message. The encoding is as follows:
Session Name: <lsp-name::path-name>, where the lsp-name component is encoded as follows:
TemplateName-DestIpv4Address-TunnelId
where DestIpv4Address is the address of the destination of the auto-created LSP.
3.5.4. Automatic Creation of an RSVP-TE Single-Hop LSP
If the one-hop option is specified instead of a prefix policy, the auto-lsp command enables the automatic signaling of single-hop, point-to-point LSPs using the specified template to all directly connected neighbors. This LSP type is referred to as auto-created single-hop LSPs of type one-hop. Unlike the automatically created RSVP-TE LSP mesh, the automatically created single-hop RSVP-TE LSPs have no requirement for a prefix list to be referenced.
The first requirement is to create an LSP template containing the common parameters used to establish each single-hop LSP. The template must be created with the keyword one-hop-p2p:
config>router>mpls>lsp-template template-name one-hop-p2p
Upon creation of the template, CSPF is automatically enabled (and cannot be disabled), and the hop-limit is set to a value of two. The hop-limit defines the number of nodes the LSP may traverse, and since these are single-hop LSPs to adjacent neighbors, a limit of two is sufficient. The template must also reference a default path before it can be placed in the no shutdown state.
The next requirement is to trigger the creation of single-hop LSPs using the auto-lsp lsp-template command:
config>router>mpls>auto-lsp lsp-template template-name one-hop
The LSP and path parameters and options supported in an LSP template of type one-hop-p2p are the same as those in the LSP template of type mesh-p2p. The show command for auto-lsp will display the actual outgoing interface address in the “from” field.
The auto-created single-hop LSP can be signaled over both numbered and unnumbered RSVP-TE interfaces.
When the one-hop command is executed, the TE database keeps track of each TE link to a directly connected IGP neighbor whose router ID is discovered. MPLS then signals an LSP with a destination address matching the router ID of the neighbor and with a strict hop consisting of the address of the interface used by the TE link. The auto-lsp command with the one-hop option results in one or more LSPs signaled to the IGP neighbor.
Only the router ID of the first IGP instance of the neighbor that advertises a TE link causes the LSP to be signaled. If another IGP instance with a different router ID advertises the same TE link, no action is taken and the existing LSP is kept up. If the router ID originally used disappears from the TE database, the LSP is kept up and is now associated with the other router ID.
The state of a single-hop LSP that is signaled displays the following behavior.
- If the interface used by the TE link goes down or BFD times out and the RSVP-TE interface is registered with BFD, the LSP path moves to the bypass backup LSP if the primary path is associated with one.
- If the association of the TE link with a router ID is removed from the TE database while the single-hop LSP is up, the single-hop LSP is torn down whether the bypass backup path is activated or not. This occurs if the interface used by the TE link is deleted or if the interface is shut down in the context of RSVP-TE.
- If the TE database loses the router ID while the LSP is up, it will perform two separate updates to MPLS, whether the bypass backup path is activated or not. The first one updates the loss of the TE link association, which will cause the single-hop LSP to be torn down. The other update states that the router ID is no longer in the TE database, which will cause MPLS to tear down all mesh LSPs to this router ID. A shutdown at the neighbor of the IGP instance that advertised the router ID will cause the router ID to be removed from the ingress LER node immediately after the last IGP adjacency is lost and not be subject to time-out as it is for a non-directly connected destination router.
All other feature behavior and limitations are the same as for an auto-created LSP mesh.
3.5.5. Automatic ABR Selection for Inter-area LSPs
Inter-area RSVP point-to-point LSPs support automatic area border router (ABR) selection at the ingress LER. The ABR does not need to be included as a loose hop in the LSP path definition.
CSPF can now compute all segments of a multi-segment, inter-area LSP path in one operation. Previously, MPLS made separate requests to CSPF for each segment.
For LSP path establishment, the explicit route object (ERO) in the PATH message is expanded on ABRs where the next hop is a loose hop in the LSP path definition. For ERO expansion to operate, the cspf-on-loose-hop command must be enabled under the mpls context on the ABR to allow the ABR to perform a CSPF calculation. If CSPF calculations are not performed, CSPF for the LSP path fails at the head-end node as TE information for links in another area are not available.
Figure 6 illustrates the role of each node in the signaling of an inter-area LSP with automatic ABR selection.
Figure 6: Automatic ABR Selection for Inter-Area LSP
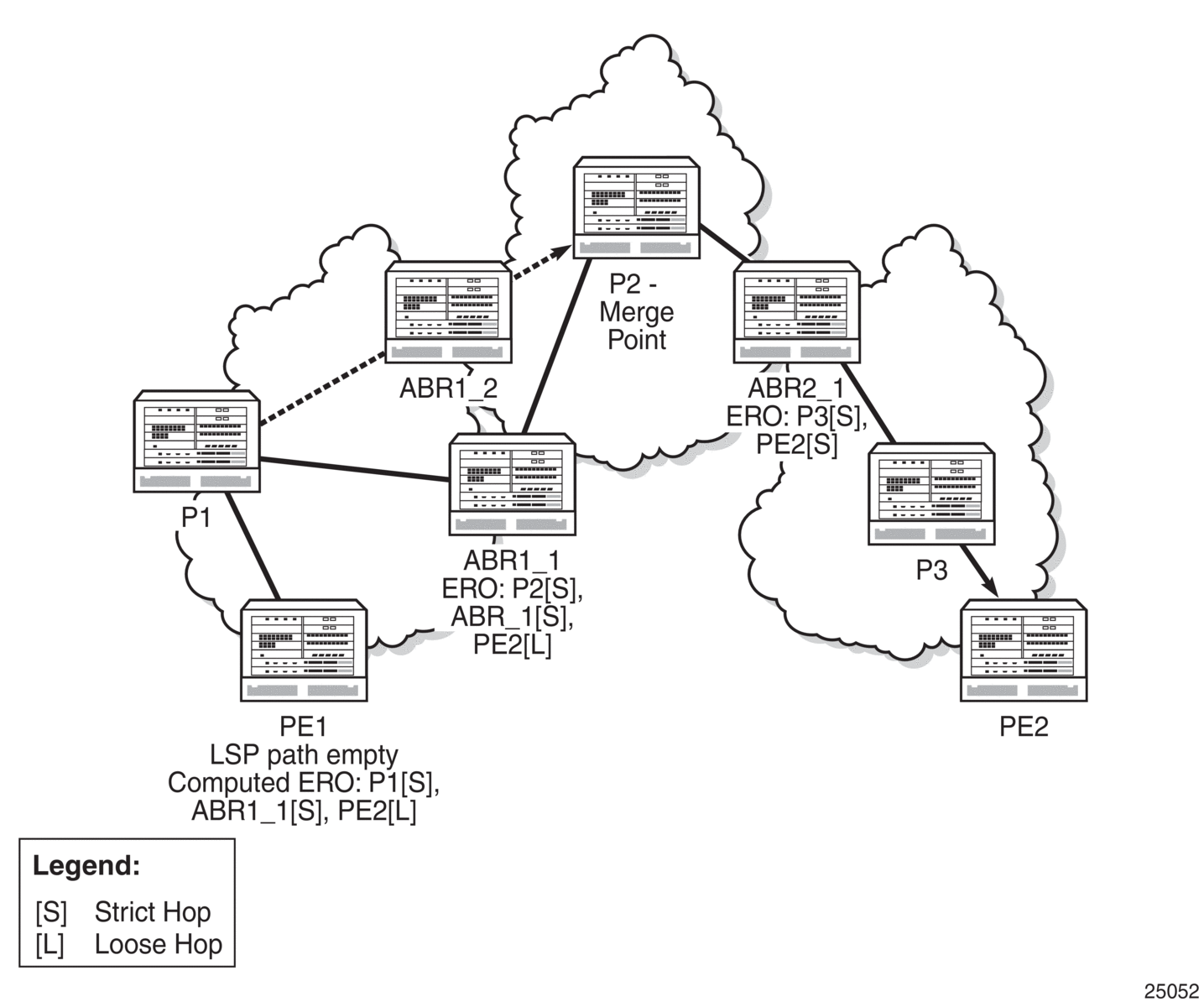
CSPF for an inter-area LSP operates as follows:
- CSPF in the ingress LER node determines that an LSP is inter-area by performing a route lookup with the destination address of a point-to-point LSP, such as the address in the “to” field of the LSP configuration. If there is no intra-area route to the destination address, the LSP is considered to be inter-area.
- When the path of the LSP is empty, CPSF computes a single-segment, intra-area path to an ABR that advertised a prefix matching the destination address of the LSP.
- If the path of the LSP contains one or more hops, CSPF computes a multi-segment, intra-area path including the hops that are in the area of the ingress LER node.
- If all hops are in the area of the ingress LER, the calculated path ends on an ABR that advertised a prefix matching the destination address of the LSP.
- When there are one or more hops that are not in the area of the ingress LER, the calculated path ends on an ABR that advertised a prefix matching the first-hop address that is not in the area of the ingress LER.
- Note the following special case of a multi-segment, inter-area LSP. If CSPF hits a hop that can be reached via an intra-area path but that resides on an ABR, CSPF only calculates a path up to that ABR. This is because there is a better chance to reach the destination of the LSP by first signaling the LSP up to that ABR and continuing the path calculation from there on by having the ABR expand the remaining hops in the ERO.
- If there is more than one ABR that advertised a prefix, CSPF calculates a path for all ABRs. Only the shortest path is withheld. If more than one path is the shortest path, CSPF picks a path randomly or based on the least-fill criterion if least-fill is enabled. If more than one ABR satisfies the least-fill criterion, CSPF also picks one path randomly.
- The path for an intra-area LSP cannot exit and re-enter the local area of the ingress LER. This behavior was possible in prior implementations when the user specified a loose hop outside the local area or when the only available path was via TE links outside the local area.
3.5.5.1. Rerouting of Inter-area LSPs
In prior implementations, an inter-area LSP path would have been rerouted if a failure or a topology change occurred in the local area or in a remote area while the ABR loose hop in the path definition was still up. If the transit/inter-area (exit) ABR failed or was put into node TE graceful shutdown, or if IS-IS went into overload mode, the LSP path would remain down at the ingress LER.
With automatic ABR selection, the ingress LER can reroute an inter-area LSP primary path via a different ABR in the following situations:
- When the local exit ABR fails, there are two cases to consider:
- If the primary path is not protected at the ABR, and is therefore torn down by the previous hop in the path, then the ingress LER retries the LSP primary path via the ABR that currently has the best path for the destination prefix of the LSP.
- If the primary path is protected at the ABR with a manual or dynamic bypass LSP, the ingress LER will receive a PathErr message with a notification of protection becoming active downstream and a RESV message with a Local-Protection-In-Use flag set. At the receipt of the first of these two messages, the ingress LER performs a Global Revertive MBB procedure to optimize the LSP primary path via the ABR that currently has the best path for the destination prefix of the LSP.
- When the local exit ABR node goes into IS-IS overload or is put into node TE graceful shutdown, the ingress LER performs an MBB procedure to optimize the LSP primary path via the ABR that currently has the best path for the destination prefix of the LSP. The MBB is performed at the receipt of the PathErr message for the node TE shutdown, or at the next timer or manual optimization of the LSP path if the IS-IS overload bit is received.
3.5.5.2. Behavior of MPLS Options in Inter-area LSPs
The automatic ABR selection for an inter-area LSP does not change the prior implementation of inter-area LSP behavior for many of the LSP-level and path-level options. However, there are a number of enhancements introduced by the automatic ABR selection feature.
- Features such as path bandwidth reservation and admin-groups continue to operate within the scope of all areas since they rely on propagating the parameter information in the PATH message across the area boundary.
- The TE graceful shutdown feature continues to support MBB of the LSP path to avoid the link or node that originated the PathErr message as long as the link or node is in the local area of the ingress LER. If the PathErr originated in a remote area, the ingress LER is not able to avoid the link or node when it performs the MBB since it computes the path to the local exit ABR only. However, there is an exception to this. An enhancement has been added to cause the upstream ABRs in the current path of the LSP to record the link or node to avoid and use the record in subsequent ERO expansions. This means that if the ingress LER computes a new MBB path that goes through the same exit ABR as the current path, and all ABRs upstream of the node or link that originated the PathErr message are also selected in the new MBB path when the ERO is expanded, then the new path will also avoid this link or node.
- MBB support has been expanded to avoid the ABR when the node is put into TE graceful shutdown.
- The use-te-metric option in CSPF cannot be propagated across the area boundary and thus operates within the scope of the local area of the ingress LER. This is a new behavior.
- The srlg option on the bypass LSP continues to operate locally at each PLR within each area. The PLR protecting the ABR checks the SRLG constraint for the path of the bypass within the local area.
- The srlg option on the secondary path is allowed to operate within the scope of the local area of the ingress LER with the automatic ABR selection feature.
- The least-fill option support with an inter-area LSP is introduced with the automatic ABR selection feature. When this option is enabled, CSPF applies the least-fill criterion to select the path segment to the exit ABR in the local area.
- The PLR must indicate to CSPF that a request to a one-to-one detour LSP path must remain within the local area. If the destination for the detour, which is the same as that of the LSP, is outside of the area, CSPF must return no path.
- With the automatic ABR selection feature, timer-based resignaling of the inter-area LSP path is supported and the path is resignaled if the cost of the path segment to the local exit ABR changes. The cost shown for the inter-area LSP at the ingress LER is the cost of the path segments to the ABR.
3.5.5.3. Inter-area LSP Support of OSPF Virtual Links
The OSPF virtual link extends area 0 for a router that is not connected to area 0 (OSPF backbone area). All prefixes in area 0 appear to be reachable via an intra-area path. However, the prefixes are not reachable since the path crosses the transit area through which the virtual link is set up to reach the area 0 remote nodes.
The TE database in a router learns all of the remote TE links in area 0 from the ABR connected to the transit area, but an intra-area LSP path using these TE links cannot be signaled within area 0 since none of these links are directly connected to this node.
The inter-area LSP feature can identify when the destination of an LSP is reachable via a virtual link. In that case, CSPF automatically computes and signals an inter-area LSP via the ABRs that are connected to the transit area.
However, when the ingress LER for the LSP is the ABR connected to the transit area, and the destination of the LSP is the address corresponding to another ABR router-id in that same transit area, CSPF computes and signals an intra-area LSP using the transit area TE links, even when the destination router-id is only part of area 0.
3.5.6. ABR FRR Protection for Inter-area LSP
For protection of the ABR, the upstream node of the ABR acts as a PLR, and the next-hop node to the protected domain border router is the merge point (MP). Both manual and dynamic bypass are available to protect the ABR.
Manual bypass protection only works when a proper completely strict path is provisioned that avoids the ABR.
Dynamic bypass protection provides for the automatic computation, signaling, and association with the primary path of an inter-area point-to-point LSP to provide ABR protection. Figure 7 illustrates the role of each node in ABR protection using a dynamic bypass LSP.
Figure 7: ABR Protection Using Dynamic Bypass LSP
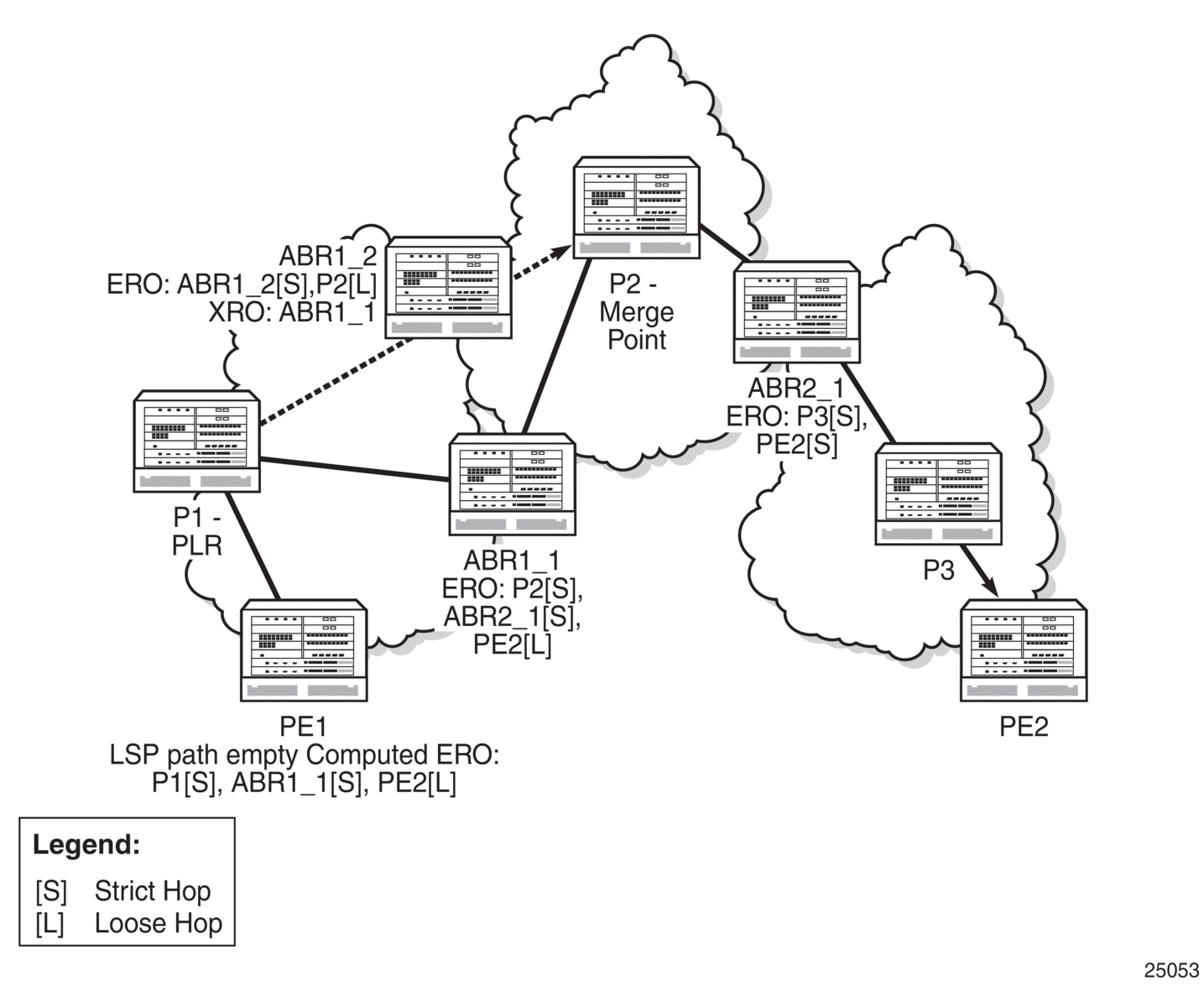
In order for a PLR within the local area of the ingress LER to provide ABR protection, it must dynamically signal a bypass LSP and associate it with the primary path of the inter-area LSP using the following procedures.
- The PLR must inspect the RRO node-id of the LSP primary path to determine the address of the node immediately downstream of the ABR in the other area.
- The PLR signals an inter-area bypass LSP with a destination address set to the address downstream of the ABR and with the exclude route object (XRO) set to exclude the node-id of the protected ABR.
- The request to CSPF is for a path to the merge point (that is, the next-next-hop in the RRO received in the RESV message for the primary path) along with the constraint to exclude the protected ABR and the include/exclude admin groups of the primary path. If CSPF returns a path that can only go to an intermediate hop, then the PLR signals the dynamic bypass and automatically includes the XRO with the address of the protected ABR and propagates the admin-group constraints of the primary path into the Session Attribute object of the bypass LSP. Otherwise, the PLR signals the dynamic bypass directly to the merge point node with no XRO in the PATH message.
- If a node-protect dynamic bypass cannot be found or signaled, the PLR attempts a link-protect dynamic bypass LSP. As with the existing implementation of dynamic bypass within the same area, the PLR attempts in the background to signal a node-protect bypass at the receipt of every third RESV refresh message for the primary path.
- Refresh reduction over dynamic bypass only works if the RRO node-id also contains the interface address. Otherwise, the neighbor is not created once the bypass is activated by the PLR. The Path state then times out after three refreshes following the activation of the bypass backup LSP.
A one-to-one detour backup LSP cannot be used at the PLR for the protection of the ABR. As a result, a 7705 SAR, acting as a PLR, will not signal a one-to-one detour LSP for ABR protection. In addition, an ABR will reject a PATH message, received from a third party implementation, with a detour object and with the ERO having the next hop loose. This is performed whether the cspf-on-loose option is enabled or not on the 7705 SAR. In other words, the 7705 SAR, working as a transit ABR for the detour path, rejects the signaling of an inter-area detour backup LSP.
3.6. Preference Option for Standby Secondary LSP Paths
The path-preference command allows priority values to be assigned to standby secondary LSP paths. This command can only be used for secondary LSP paths that have been configured in standby mode.
When the primary LSP becomes inactive, the standby secondary LSP with the highest path priority (lowest path-preference value) is chosen from the qualifying standby secondary LSPs to become the active LSP. This functionality allows a user to choose a path for one of the standby secondary LSPs that may, for example, be over a more reliable link or over a link with a lower latency.
If multiple standby secondary LSP paths have the same priority value, the system selects the path with the lowest uptime.
3.7. RSVP-TE Fast Reroute (FRR)
FRR is a mechanism to protect against RSVP-TE signaled LSP failures by reacting to these failures as soon as possible. FRR is set up from the iLER, which signals the transit routers to precompute their backup LSPs. FRR creates a precomputed backup LSP from each node in the LSP path. If a link or LSP between two routers fails, traffic is rerouted immediately onto the precomputed backup LSP.
| Note: In order for FRR to work, CSPF must be enabled. |
The 7705 SAR supports FRR facility backup and one-to-one backup.
Facility backup mode allows FRR to be enabled on an aggregate basis and protects a whole node or a whole link, regardless of the number of LSPs using that link. In other words, facility backup mode creates a common bypass tunnel to protect all LSP-paths traversing a common facility path. It provides flexibility, faster provisioning, and faster convergence times compared with one-to-one backup or LSP redundancy. One-to-one backup allows FRR to be enabled on a per-LSP basis.
With both methods, MPLS switches build many possible detour routes on the nodes between the ingress and egress nodes of an LSP. The facility backup method creates a detour route between two nodes, called a bypass tunnel, which is a single tunnel that follows the primary LSP path except where the link or node has failed. Traffic then switches to the bypass tunnel. The bypass tunnel merges with the original LSP path at the merge point (MP) as soon as possible. The one-to-one backup method creates a detour route, called a detour LSP, for each LSP that needs to be rerouted. Unlike the bypass tunnel, the detour LSP takes the best path to the termination point, and does not merge with the original LSP as soon as possible. The detour LSPs of a one-to-one backup LSP can merge at a detour merge point (DMP), which can either be at the termination point or at a point along the primary LSP.
One of the major differences between facility and one-to-one backup is the scalability offered by the protection method. In facility backup mode, all LSPs of the same type are rerouted over the bypass tunnel. Hence they are all protected against the failure of a node or link in the network. In facility backup mode, each LSR along the path verifies that it has a bypass tunnel available to meet its requirements; otherwise, if it can, it signals a new bypass tunnel based on the requirements. If a new LSP is configured for FRR facility backup, the existing backup tunnels are scanned and if any one of them can be used for recovery, it is preferred. If there are no common links, then a new bypass tunnel will be signaled, assuming that the LSP requirements can be met. One-to-one backup mode uses similar reroute and protection methods except a detour route is applied on a per-LSP basis.
The 7705 SAR uses CSPF to calculate the explicit route and dynamically signal the FRR LSP.
With facility backup mode, routers check the contents of the Record Route Object (RRO) in the received RESV message to determine the bypass tunnel endpoint in the FRR facility. For link protection, the router uses the RRO to check the IP address of the next-hop router attached to the far end of the link along with the label allocation information and to build the bypass tunnel. This label is preserved until the LSP is merged at the MP. For node protection, the router uses the RRO to determine the next-next-hop router and the label it is expecting. The collection of RRO information is enabled through the record and record-label options.
If, after this process, another LSP requests FRR using the facility backup method, the router checks and compares its session object to the existing session objects and if there is a match, the router binds that LSP to the same bypass tunnel. If there is no match, another bypass is created.
3.7.1. FRR Terminology
Table 6 provides definitions of terms used for FRR.
Table 6: FRR Terminology
Term | Definition |
Backup path | The LSP that is responsible for backing up a protected LSP. A backup path can be a backup tunnel (facility backup) or a detour LSP (one-to-one backup). |
Backup tunnel | The LSP that is used to back up one of the many LSPs in FRR facility (many-to-one) backup |
Bypass tunnel | An LSP that is used to protect a set of LSPs passing over a common facility in FRR facility backup. A bypass tunnel can be configured manually or dynamically (see Dynamic and Manual Bypass LSPs). |
CSPF | Constraint-based shortest path first |
Detour route | Any alternate route that protects the primary path, such as a secondary path, FRR bypass tunnel, or FRR detour LSP. The term “detour route” should not be confused with the term “detour LSP”. Detour route is a general term that refers to any alternate route, while detour LSP is a specific term that applies to one-to-one backup. |
Detour LSP | The LSP that is used to reroute traffic around a failure in FRR one-to-one backup. The term “detour LSP” should not be confused with the term “detour route”. Detour route is a general term that refers to any alternate route, while detour LSP is a specific term that applies to one-to-one backup. |
DMP | Detour merge point In the case of one-to-one backup, this is an LSR where multiple detours converge. Only one detour is signaled beyond that LSR. |
Disjoint | See SRLG disjoint |
Facility backup | A local repair method in which a single bypass tunnel is used to protect one or more LSPs that traverse the PLR, the resource being protected, and the Merge Point (in that order). Facility backup is distinct from a one-to-one backup tunnel, which has one backup path per protected path. |
MP | Merge point The LSR where one or more backup tunnels rejoin the path of the protected LSP downstream of the potential failure. The same LSR may be both an MP and a PLR simultaneously. |
NHOP bypass tunnel | Next-hop bypass tunnel A backup tunnel that bypasses a single link of the protected LSP |
NNHOP bypass tunnel | Next-next-hop bypass tunnel A backup tunnel that bypasses a single node of the protected LSP |
One-to-one backup | A local repair method in which a backup LSP is separately created for each protected LSP at a PLR |
PLR | Point of local repair The head-end router of a backup tunnel or a detour LSP, where the term local repair refers to techniques used to repair an LSP tunnel quickly when a node or link along an LSP path fails |
Primary path | An LSP that uses the routers specified by the path defined by the primary path-name command |
Protected LSP | An LSP is protected at a given hop if it has one or more associated backup tunnels originating at that hop |
Reroutable LSP | Any LSP for which the head-end router requests local protection |
Secondary path | An LSP that protects a primary path that uses LSP redundancy protection rather than FRR protection |
SRLG disjoint | A path is considered to be SRLG disjoint from a given link or node if the path does not use any links or nodes that belong to the same SRLG as the given link or node |
3.7.2. Bypass Resignal Timer
When the bypass resignal timer is enabled, MPLS makes a request to CSPF for the best path for each dynamic bypass LSP originated on the node. The constraints of the first associated LSP primary path that originally triggered the signaling of the bypass LSP must be satisfied. In order to do this, MPLS saves the original Path State Block (PSB) of the LSP primary path, even if the path is torn down.
If CSPF returns no path or returns a new path that is equal in cost to the current path, the PSB associations are not updated. If CSPF returns a new path with a different cost from the current one, MPLS signals it.
When the new path is successfully signaled, MPLS evaluates each PSB of each PLR (that is, each unique avoid-node or avoid-link constraint) associated with the older bypass LSP path to check whether the corresponding LSP primary path constraints are still satisfied by the new bypass LSP path. If the constraints are satisfied, the PSB association is moved to the new bypass LSP.
If the constraints are not satisfied, the PSB remains associated with the older bypass LSP and will be checked at the next background PSB re-evaluation or at the next timed or manual bypass reoptimization. Additionally, if the older bypass LSP is SRLG disjoint with a primary path that has the non-strict SRLG condition and the new bypass LSP is not SRLG disjoint, the PSB association is not moved.
If a PLR associated with a bypass LSP is active, the corresponding PSBs remain associated with the older bypass LSP until the global revertive make-before-break (MBB) operation tears down all corresponding primary paths, which also causes the older bypass LSP to be torn down.
When the bypass resignal timer is configured, a PSB re-evaluation task is initiated that runs in the background of each RSVP-TE session to determine whether an existing manual or dynamic bypass is more optimal for that session. If the PSB re-evaluation task finds a more optimal bypass, it moves the PSB association to it. If the PLR for this session is active, no action is taken and the PSB is re-examined at the next re-evaluation.
The periodic bypass reoptimization feature evaluates only the PSBs of the PLRs associated with that bypass LSP and only against the new bypass LSP path. The background re-evaluation task will, however, audit all PSBs on the system against all existing manual and dynamic bypass LSPs. PSBs that have not been moved by the dynamic or manual re-optimization of a bypass LSP, due to the PSB constraints not being met by the new signaled bypass LSP path, will be re-evaluated by the background task against all existing manual and dynamic bypass LSPs.
The background re-evaluation task also checks for PSBs that have requested a node-protect bypass LSP but are currently associated with a link-protect bypass LSP, as well as PSBs that have requested FRR protection and have no association. The background task is in addition to the attempt made when an RESV message is received on the protected LSP path, which ensures the association is completed faster.
This feature is not supported with inter-area dynamic bypass LSPs.
3.7.3. FRR Behavior
The FRR MPLS facility backup method and one-to-one backup method are configured on the ingress LER (iLER) by using the fast-reroute command.
The behavior of an LSP at an iLER with both FRR and a standby LSP path configured is as follows.
- When a downstream detour route (alternative path) becomes active at a Point of Local Repair (PLR):The iLER switches to the standby LSP path as soon as it is notified of the reroute. If the primary LSP path is subsequently repaired at the PLR, the LSP switches back to the primary path. If the standby path goes down, the LSP is switched back to the primary path, even though the primary path is still on the detour route at the PLR.
- If the primary path goes down at the iLER while the LSP is on the standby path, the detour route at the iLER is torn down and, for one-to-one backup detour routes, a “path tear” is sent for the detour route. In other words, the detour route at the iLER does not protect the standby LSP. If and when the primary LSP is again successfully resignaled, the iLER detour route will be restarted.
- When the primary LSP fails at the iLER:The LSP switches to the detour route. If the primary path undergoes a global revertive recovery, the LSP switches back to the primary path. If the LSP is on the detour route and the detour route fails, the LSP is switched to the standby path.
- Administrative groups are not taken into account when creating the detour routes for LSPs.
3.7.4. Dynamic and Manual Bypass LSPs
Users can disable dynamic bypass creation on a per-node basis using the config>router>mpls>dynamic-bypass command. Disabling dynamic bypass means that manual bypass is enabled. Dynamic bypass is enabled by default.
Dynamic bypass tunnels are implemented as per RFC 4090, Fast Reroute Extensions to RSVP-TE for LSP Tunnels. When an LSP is signaled and the Local Protection flag in the Session_attribute object is set, or the FRR object in the PATH message indicates that facility backup is desired, the PLR establishes a bypass tunnel to provide node and link protection. If there exists a bypass LSP that merges with the protected LSP at a downstream node, and if this LSP satisfies the constraints in the FRR object, then this bypass tunnel is selected and used. The frr-object command specifies whether facility backup is signaled in the FRR object.
The manual bypass feature allows an LSP to be preconfigured from a Point of Local Repair (PLR) that will be used exclusively for bypass protection. When a PATH message for a new LSP requests bypass protection, the node first checks for a manual bypass tunnel that satisfies the path constraints. If one is found, it is selected and used. If no manual bypass tunnel is found, the 7705 SAR dynamically signals a bypass LSP in the default behavior. To configure a manual bypass LSP, use the bypass-only option in the config>router>mpls>lsp lsp-name [bypass-only] command.
When a PLR activates a bypass backup LSP and subsequently receives a RESV refresh message for the original primary LSP path reservation over the restored interface, the PLR does not generate a ResvErr packet downstream. In addition, the MP node, once it becomes active, does not propagate a downstream ResvErr message received packet for the original primary LSP path reservation.
Refer to Configuring Manual Bypass Tunnels for configuration information.
3.7.4.1. Bypass LSP Selection Rules for the PLR
Figure 8 shows an example of a network used to illustrate the LSP selection rules for a PLR bypass scenario.
Figure 8: Bypass Tunnel Node Example
The PLR uses the following rules to select a bypass LSP from among multiple bypass LSPs (manually and dynamically created) when establishing the primary LSP path or when searching for a bypass for a protected LSP that does not have an association with a bypass tunnel.
- The MPLS/RSVP-TE task in the PLR node checks for an existing manual bypass tunnel that satisfies the constraints. If the PATH message for the primary LSP path indicated that node protection is desired, which is the default LSP FRR setting at the head-end node, then the MPLS/RSVP-TE task searches for a node-protect bypass LSP. If the PATH message for the primary LSP path indicated that link protection is desired, then it searches for a link-protect bypass LSP.
- If multiple manual bypass LSPs satisfying the path constraints exist, the PLR will prefer a manual bypass LSP terminating closer to the PLR over a manual bypass LSP terminating further away. If multiple manual bypass LSPs satisfying the path constraints terminate on the same downstream node, the PLR selects the one with the lowest IGP path cost, or if there is a tie, it picks the first one available.
- If none of the manual bypass LSPs satisfy the constraints and dynamic bypass tunnels have not been disabled on the PLR node, then the MPLS/RSVP-TE task in the PLR node checks to determine if any of the already established dynamic bypass LSPs of the requested type satisfy the constraints.
- If none of the dynamic bypass LSPs satisfy the constraints, then the MPLS/RSVP-TE task will ask CSPF to check if a new dynamic bypass of the requested type, node-protect or link-protect, can be established.
- If the PATH message for the primary LSP path indicated node protection is desired, and no manual bypass was found after Step 1, and/or no dynamic bypass LSP was found after three attempts to perform Step 3, the MPLS/RSVP-TE task will repeat Steps 1 to 3 looking for a suitable link-protect bypass LSP. If none are found, the primary LSP will have no protection and the PLR node must clear the Local Protection Available flag in the IPv4 address sub-object of the RRO, starting in the next RESV refresh message it sends upstream.
- If the PATH message for the primary LSP path indicated link protection is desired, and no manual bypass was found after Step 1, and/or no dynamic bypass LSP was found after performing Step 3, the primary LSP will have no protection and the PLR node must clear the Local Protection Available flag in the IPv4 address sub-object of the RRO, starting in the next RESV refresh message it sends upstream. The PLR will not search for a node-protect bypass LSP in this case.
- If the PLR node successfully makes an association, it must set the Local Protection Available flag in the IPv4 address sub-object of the RRO, starting in the next RESV refresh message it sends upstream.
- For all primary LSPs that requested FRR protection but are not currently associated with a bypass tunnel, the PLR node—upon reception of an RESV refresh message on the primary LSP path—repeats Steps 1 to 7.
If the user disables dynamic bypass tunnels on a node while dynamic bypass tunnels are activated and passing traffic, traffic loss will occur on the protected LSP. Furthermore, if no manual bypass tunnel exists that satisfies the constraints of the protected LSP, the LSP will remain without protection.
If the user configures a bypass tunnel on Node B (Figure 8) and dynamic bypass tunnels have been disabled, LSPs that had been previously signaled and that were not associated with any manual bypass tunnel (for example, none existed) will be associated with the manual bypass tunnel, if it is suitable. The node checks for the availability of a suitable bypass tunnel for each of the outstanding LSPs every time an RESV message is received for these LSPs.
If the user configures a bypass tunnel on Node B and dynamic bypass tunnels have not been disabled, LSPs that had been previously signaled over dynamic bypass tunnels will not automatically be switched to the manual bypass tunnel, even if the manual bypass tunnel is a more optimized path. The user must perform a make-before-break switchover at the head end of these LSPs. The make-before-break process is enabled using the adaptive option.
If the manual bypass tunnel goes into the down state on Node B and dynamic bypass tunnels have been disabled, Node B (PLR) will clear the “protection available” flag in the RRO IPv4 sub-object in the next RESV refresh message for each affected LSP. It will then try to associate each of these LSPs with one of the manual bypass tunnels that are still up. If it finds one, it will make the association and set the “protection available” flag in the next RESV refresh message for each of these LSPs. If it cannot find one, it will keep checking for one every time an RESV message is received for each of the remaining LSPs. When the manual bypass tunnel is back up, the LSPs that did not find a match are associated back with this tunnel and the protection available flag is set starting in the next RESV refresh message.
If the manual bypass tunnel goes into the down state on Node B and dynamic bypass tunnels have not been disabled, Node B will automatically signal a dynamic bypass tunnel to protect the LSPs if a suitable one does not exist. Similarly, if an LSP is signaled while the manual bypass tunnel is in the down state, the node will only signal a dynamic bypass tunnel if the user has not disabled dynamic tunnels. When the manual bypass tunnel is back up, the node will not switch the protected LSPs from the dynamic bypass tunnel to the manual bypass tunnel.
3.7.4.2. FRR Node Protection (Facility Backup)
The MPLS Fast Reroute (FRR) functionality enables PLRs to be aware of the lack of node protection and lets them regularly probe for a node bypass via the node-protect command.
When enabled, the node-protect command provides node protection for the specified LSP. If node protection cannot be provided, link protection is attempted. If link protection cannot be provided, no protection is provided. When disabled via the no form of the command, link protection is attempted, and if link protection cannot be provided, no protection is provided.
For example, assume the following for the LSP scenario in Figure 9.
- LSP_1 is between PE_1 and PE_2 (via P1 and P2), and has CSPF, FRR facility backup, and FRR node protection enabled.
- P1 protects P2 with bypass nodes P1 - P3 - P4 - PE_4 - PE_3.
- If P4 fails, P1 tries to establish the bypass node three times.
- When the bypass node creation fails (there is no bypass route), P1 will protect link P1-P2.
- P1 protects the link to P2 through P1 - P5 - P2.
- P4 returns online.
Figure 9: FRR Node-Protection Example
LSP_1 had requested node protection, but due to lack of an available path it could only obtain link protection. Therefore, every 60 s, the PLR for LSP_1 will search for a new path that might be able to provide node protection. When P4 is back online and such a path is available, a new bypass tunnel will be signaled and LSP_1 will be associated with this new bypass tunnel.
3.7.5. Admin Group Support on Facility Bypass Backup LSPs
Admin group support on facility bypass backup LSPs provides for the inclusion of the LSP primary path admin-group constraints in the computation of an FRR facility bypass backup LSP to protect the primary LSP path. Admin group constraints are honored by all nodes in the LSP path both for primary and FRR backup LSPs.
This feature is supported on primary paths of an RSVP point-to-point LSP in both intra-area and inter-area TE where applicable.
This feature is not supported on one-to-one detour backup LSPs.
3.7.6. FRR Over Unnumbered Interfaces
When the PLR is the ingress LER node and the outgoing interface of the bypass LSP is unnumbered, the user must assign a borrowed IP address to the interface that is different from the system interface; otherwise, the bypass LSP will not come up.
In addition, the PLR node includes the IF_ID RSVP_HOP object (C-Type = 3) in the PATH message if the outgoing interface of the bypass LSP is unnumbered. If the outgoing interface of the bypass LSP is numbered, the PLR node includes the IPv4 RSVP_HOP object (C-Type = 1).
When the MP node receives the PATH message over the bypass LSP, it creates the merge-point context for the protected LSP and associates it with the existing state if any of the following is satisfied:
- the C-Type value of the RSVP_HOP object has changed
- the C-Type is the value for the IF_ID RSVP_HOP object (C-Type = 3) and it has not changed, but the IF_ID TLV is different
- the IPv4 Next/Previous Hop Address field in the RSVP_HOP object has changed, regardless of the C-Type value
This behavior at the PLR and MP nodes is the same for both link protection and node protection FRR.
| Note: If node protection FRR is enabled but the MP does not support an unnumbered interface, the PATH message is rejected at the MP and the path is torn down. |
See RSVP-TE Support for Unnumbered Interfaces for information on unnumbered interfaces.
3.8. Shared Risk Link Groups
A shared risk link group (SRLG) represents a set of interfaces (or links) that share the same risk of failing because they may be subjected to the same resource failures or defects. Two examples where the same risk of failure exists are fiber links that share the same conduit, and multiple wavelengths that share the same fiber.
SRLGs are supported by both LSP redundancy protection and FRR protection. SRLGs allow the user to prepare a detour route that is disjoint from the primary LSP path. See Disjoint and Non-disjoint Paths.
The SRLG feature ensures that a primary and secondary LSP path, or a bypass tunnel or detour LSP path, do not share SRLGs. That is, they do not share the same sets of links that are considered to have a similar (or identical) chance of failure.
To use SRLGs, the user first creates an SRLG by assigning one or more routers to the SRLG. Then, the user links the SRLG to an MPLS interface and enables the SRLG feature on the LSP path. SRLGs cannot be assigned to the system interface.
3.8.1. SRLGs for Secondary LSP Paths
SRLGs for secondary LSP paths apply when LSP redundancy protection is used.
When setting up the secondary path, enable the srlg option on the secondary path to ensure that CSPF includes the SRLG constraint in its route calculation. To make an accurate computation, CSPF requires that the primary LSP be established and in the up state (because the head-end LER needs the most current explicit route object (ERO) for the primary path, and the most current ERO is built during primary path CSPF computation). The ERO includes the list of SRLGs.
At the establishment of a secondary path with the SRLG constraint, the MPLS/RSVP-TE task queries CSPF again, which provides the list of SRLGs to be avoided. CSPF prunes all links having interfaces that belong to the same SRLGs as the interfaces included in the ERO of the primary path. If CSPF finds an eligible path, the secondary path is set up. If CSPF does not find an eligible path, MPLS/RSVP-TE keeps retrying the requests to CSPF.
3.8.2. SRLGs for FRR LSP Paths
When setting up the FRR bypass or detour LSP, enable the srlg-frr option on FRR to ensure that CSPF includes the SRLG constraint in its route calculation. CSPF prunes all links that are in the SRLG being used by the primary LSP during the calculation of the FRR path. If one or more paths are found, CSPF sets up the FRR bypass or detour LSP based on the best cost and signals the FRR LSP.
If there is no path found based on the above calculation and the srlg-frr command has the strict option set, then the FRR LSP is not set up and the MPLS/RSVP-TE task keeps trying to set up a path. If the strict option is not set, then the FRR LSP is set up based on the other TE constraints (that is, excluding the SRLG constraint).
3.8.3. Disjoint and Non-disjoint Paths
A path is considered to be SRLG disjoint from a given link (or node) if the path does not use any links (or nodes) that belong to the same SRLG as the given link (or node). Eligible disjoint paths are found by CSPF when the SRLG constraint is included in the CSPF route calculation (referred to as the strict SRLG condition).
When LSP redundancy is used, the secondary LSP is always signaled with a strict SRLG condition.
When FRR is used, the FRR bypass or detour LSP may have a strict or non-strict SRLG condition. If the strict option is used with the srlg-frr command, then the bypass LSP must be on the list of eligible paths found by the CSPF calculation that included the SRLG constraint. If the strict option is not used, then it is possible for the bypass or detour LSP to be non-disjoint. The non-disjoint case is supported only if the SRLG is not strict.
At the PLR, if an FRR tunnel is needed to protect a primary LSP, the priority order for selecting that FRR tunnel is as follows:
- Manual bypass disjoint
- Manual bypass non-disjoint (eligible only if srlg-frr is non-strict)
- Dynamic bypass disjoint
- Dynamic bypass non-disjoint (eligible only if srlg-frr is non-strict)
A bypass or a detour LSP path is not guaranteed to be SRLG disjoint from the primary path. This is because only the SRLG constraint of the outgoing interface at the PLR that the primary path is using is considered in the CSPF calculation.
3.8.4. Enabling Disjoint Backup Paths
A typical application of the SRLG feature is to provide automatic setup of secondary LSPs or FRR bypass or detour LSPs, in order to minimize the probability that they share the same failure risks with the primary LSP path (see Figure 10 and Figure 11).
Figure 10 illustrates SRLG when LSP redundancy is used, where SRLG_1 contains the interfaces that define links A-B, B-C, and C-D. The primary path uses these links to connect node A to node D. In the event of a failure along the primary path, the secondary path cannot use any of the links in SRLG_1 and takes the path from node A to nodes E, F, G, H, J, and D.
Figure 11 illustrates SRLG when FRR bypass is used, where SRLG_1 is the same as in Figure 10. Since FRR bypass is used, the following possible reroutes may occur, depending on where the failure occurs:
- if node B fails, the bypass is from node A to nodes E, F, G, H, and C
- if node C fails, the bypass is from node B to nodes F, G, H, J, and D
- if link C-D fails, the bypass is from node C to nodes H, J, and D
The SRLG feature is supported on OSPF and IS-IS interfaces for which RSVP-TE is enabled.
The following steps describe how to enable SRLG disjoint backup paths for LSP redundancy and FRR.
LSP Redundancy for Primary/Secondary (standby) SRLG Disjoint Configuration
- Create an SRLG-group (similar to creating an admin group).
- Link the SRLG-group to MPLS interfaces.
- Configure primary and secondary LSP paths, and enable SRLG on the secondary LSP path. The SRLG secondary LSP paths will always perform a strict CSPF query.The setting of the srlg-frr command is irrelevant in this case (see the srlg-frr command).
FRR Bypass Tunnel or Detour LSP SRLG Disjoint Configuration
- Create an SRLG-group (similar to creating an admin group).
- Link the SRLG-group to MPLS interfaces.
- Enable the strict option on the srlg-frr command, which is a system-wide command that forces the CSPF calculation for every LSP path to take any configured SRLG memberships into account.
- Configure primary FRR (facility backup or one-to-one backup) LSP paths. Each PLR will create a bypass or detour LSP that will only avoid the SRLG memberships configured on the primary LSP path egress interface. For one-to-one backup, detour-detour merging is out of the control of the PLR. The PLR will not ensure that the FRR detour will be prohibited from merging with a colliding detour LSP. For facility backup, given that there are several bypass types to bind to, the priority rules shown in Disjoint and Non-disjoint Paths are used.
Manually configured bypasses that do not use CSPF are not considered as possible backup paths.
Figure 10: Disjoint Primary and Secondary LSPs
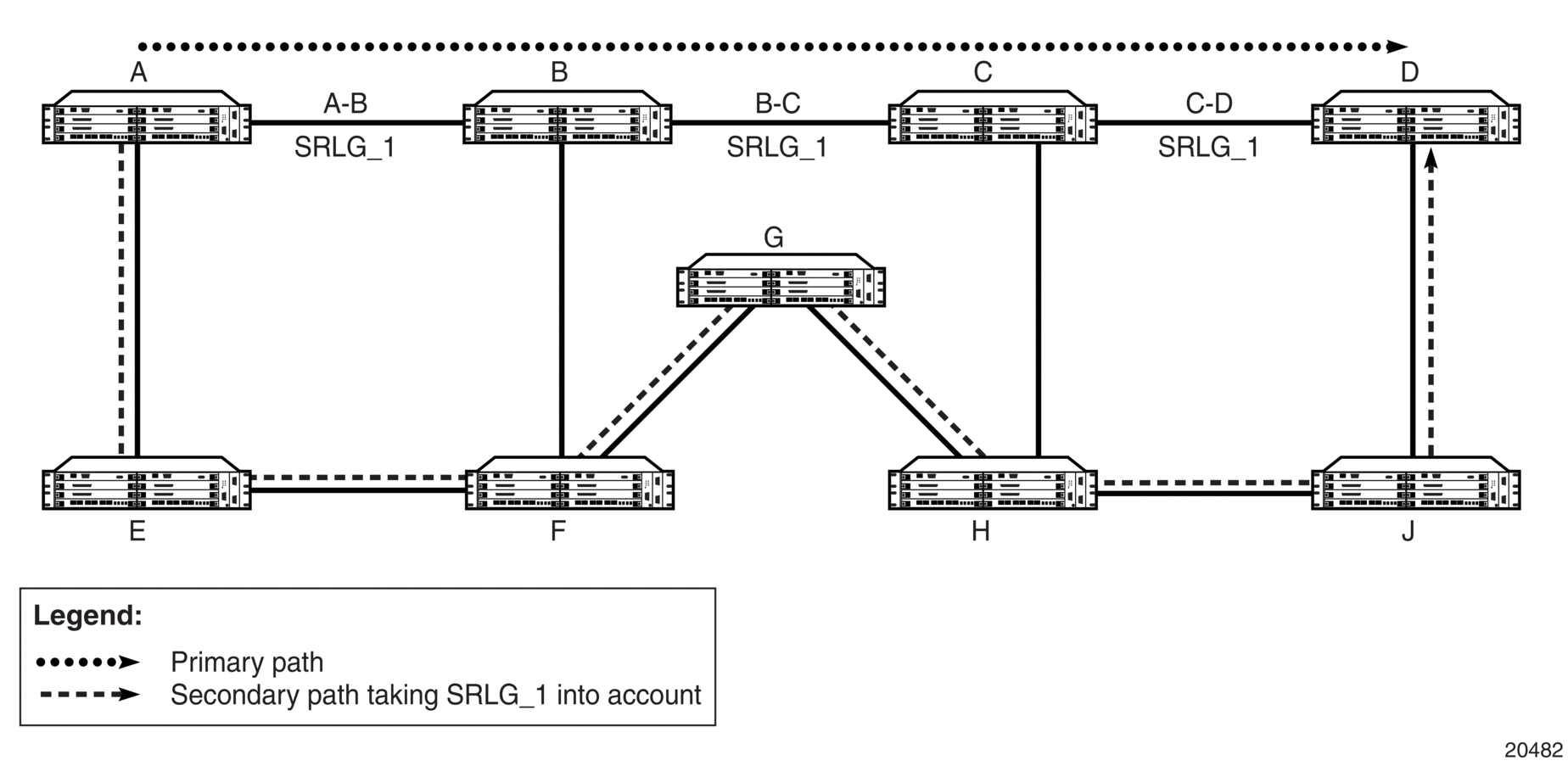
Figure 11: Disjoint FRR Bypass LSPs
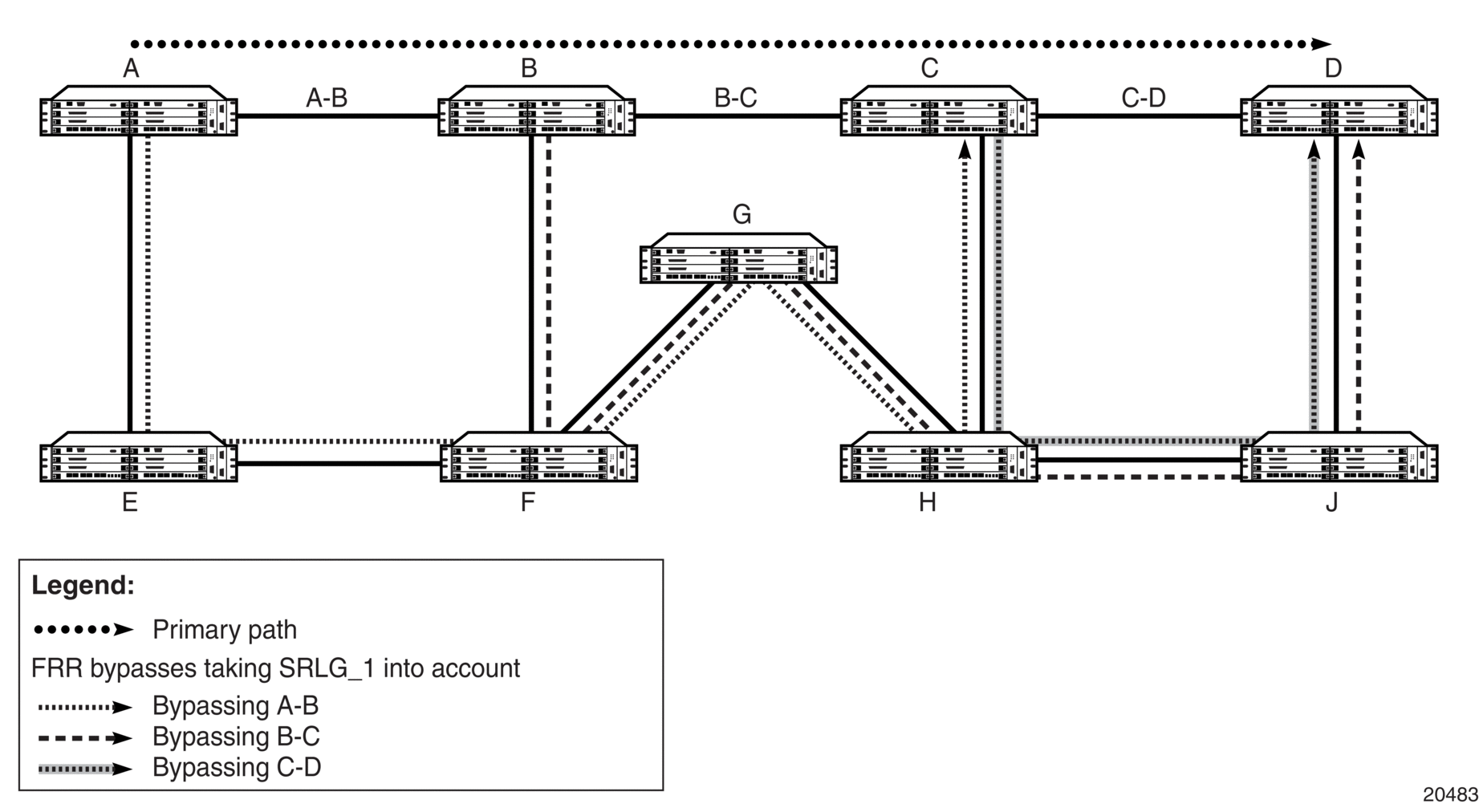
3.9. RSVP-TE Graceful Shutdown
RSVP-TE graceful shutdown provides a method to reroute transit LSPs in a bulk fashion away from a node prior to maintenance of that node. A PathErr message with the error code “Local Maintenance on TE Link required Flag” (if the affected network element is a link) or the error code “Local node maintenance required” (if the affected network element is the node) is sent before the links or node are taken out of service.
When an LER receives the message, it performs a make-before-break on the LSP path to move the LSPs away from the links/nodes whose IP addresses are indicated in the PathErr message and reroute them. Affected link/node resources are flagged in the TE database so that other routers will signal LSPs using the affected resources only as a last resort.
Graceful shutdown can be enabled on a per-interface basis or on all interfaces on the node if the whole node must be taken out of service.
3.10. RSVP-TE Support for Unnumbered Interfaces
Unnumbered interfaces are point-to-point interfaces that are not explicitly configured with a dedicated IP address and subnet; instead, they borrow (or link to) an IP address from another interface on the system (the system IP address, another loopback interface, or any other numbered interface) and use it as the source IP address for packets originating from the interface. For more information on support for unnumbered interfaces, refer to the 7705 SAR Router Configuration Guide, “Unnumbered Interfaces”.
Unnumbered IP interfaces can be used via RSVP-TE for signaling traffic engineering (TE) LSPs.
Supporting RSVP-TE over unnumbered interfaces requires the ability to:
- carry TE information over unnumbered links in IS-IS-TE or OSPF-TE extensions
- specify unnumbered interfaces in RSVP-TE signaling
An unnumbered IP interface is identified uniquely on a router in the network by the tuple (router ID, ifindex). An LSR at each end of the link assigns a system-wide unique interface index to the unnumbered interface. IS-IS, OSPF, MPLS (RSVP-TE, LDP), and OAM use this tuple to advertise the link information, signal LSPs over the interface, or send and respond to an MPLS echo request message over an unnumbered interface.
The borrowed IP address for an unnumbered interface is configured using the following CLI command, with the default value set to the system interface address: config>router>interface>unnumbered {ip-int-name | ip-address}.
| Note: The borrowed IP address is used exclusively as the source address for IP packets that originate from the interface. For FRR, this address must be configured to an address different from the system interface in order for the FRR bypass LSP to come up at the ingress LER. See RSVP-TE Fast Reroute (FRR) for information on FRR. |
To support unnumbered TE links in IS-IS, a new sub-TLV of the extended IS reachability TLV is added, which encodes the link local identifiers and link remote identifiers as defined in RFC 5307, IS-IS Extensions in Support of Generalized Multi-Protocol Label Switching (GMPLS).
To support unnumbered TE links in OSPF, a new sub-TLV of the Link TLV is added, which encodes the link local identifiers and link remote identifiers as defined in RFC 4203, OSPF Extensions in Support of Generalized Multi-Protocol Label Switching (GMPLS).
To support unnumbered TE links in RSVP-TE, a new sub-object of the Explicit Route Object (ERO) is added to specify unnumbered links and a new sub-object of the Route Record Object (RRO) is added to record that the LSP traversed an unnumbered link, as per RFC 3477, Signalling Unnumbered Links in Resource ReSerVation Protocol - Traffic Engineering (RSVP-TE). As well, a new IF_ID RSVP_HOP object with a C-Type of 3 is added as per section 8.1.1 of RFC 3473, Generalized Multi-Protocol Label Switching (GMPLS) Signaling Resource ReserVation Protocol-Traffic Engineering (RSVP-TE) Extensions. The IPv4 Next/Previous Hop Address field in the object is set to the borrowed IP interface address.
The unnumbered IP interface address is advertised by IS-IS-TE or OSPF-TE, and CSPF can include it in the computation of a path for a point-to-point LSP. However, this feature does not support defining an unnumbered interface as a hop in the path definition of an LSP.
A router creates an RSVP neighbor over an unnumbered interface using the tuple (router ID, ifindex). The router ID of the router that advertised an unnumbered interface index is obtained from the TE database. Therefore, if traffic engineering is disabled in IS-IS or OSPF, a non-CSPF LSP that has its next hop over an unnumbered interface will not come up at the ingress LER because the router ID of the neighbor that has the next hop of the PATH message cannot be looked up. The LSP path will remain operationally down with the error “noRouteToDestination”. If a PATH message is received at the LSR for which traffic engineering was disabled and the next hop for the LSP is over an unnumbered interface, a PathErr message is sent back to the ingress LER with the error code of 24 “Routing Problem” and an error value of 5 “No route available toward destination”.
All MPLS (RSVP-TE and LDP) features supported for numbered IP interfaces are supported for unnumbered interfaces, with the following exceptions:
- configuration of a router ID with a value other than system interface
- signaling of an LSP with an ERO based on a loose or strict hop using an unnumbered TE link in the path hop definition
- signaling of a one-to-one detour LSP over an unnumbered interface
- RSVP Hello messages and all Hello-related capabilities, such as Graceful-Restart Helper
- RSVP refresh reduction on an unnumbered interface
The unnumbered interface feature also extends the support of LSP ping and LSP traceroute to point-to-point LSPs that have unnumbered TE links in their path.
3.11. PCEP Support for RSVP-TE LSPs
The Path Computation Element Communication Protocol (PCEP) is one of several protocols used for communication between a wide area network (WAN) software-defined network (SDN) controller and network elements.
The 7705 SAR operates as a PCE Client (PCC) only, supporting PCC capabilities for RSVP-TE LSPs.
The following MPLS-level and LSP-level CLI commands are used to configure RSVP-TE LSPs in a router acting as a PCC. See MPLS and RSVP-TE Command Reference for command descriptions. See the PCEP Support for RSVP-TE LSPs section in the PCEP chapter for information on using these commands.
- config>router>mpls>pce-report rsvp-te {enable | disable}
- config>router>mpls>lsp>path-profile profile-id [path-group group-id]pce-computationpce-controlpce-report {enable | disable | inherit}
- config>router>mpls>lsp-template>pce-report {enable | disable | inherit}
3.12. Segment Routing with Traffic Engineering (SR-TE)
Segment routing adds the ability to perform shortest path routing and source routing using the concept of abstract segments to IS-IS and OSPF routing protocols. A segment can represent a local prefix of a node, a specific adjacency of the node (interface/next hop), a service context, or a specific explicit path over the network. For each segment, the IGP advertises an identifier referred to as a Segment ID (SID).
When segment routing is used together with the MPLS data plane, the SID is a standard MPLS label. A router forwarding a packet using segment routing will therefore push one or more MPLS labels.
Segment routing using MPLS labels can be used in both shortest path routing applications (refer to the 7705 SAR Routing Protocols Guide for information) and in traffic engineering (TE) applications, as described in this section.
The following are the objectives and applications of segment routing:
- ability for a node to specify a unicast shortest-route or source-routed forwarding path with the same mechanism; IGP can be reused to minimize the number of control plane protocols
- ability to use IGP-based MPLS tunnels without the addition of any other signaling protocol
- ability to tunnel services from ingress PE to egress PE with or without an explicit path and without requiring forwarding plane or control plane state in intermediate nodes
- ability to use Layer 3 spoke SDP interfaces to support multicast for segment routing. Refer to the 7705 SAR Routing Protocols Guide, “Multicast for Segment Routing”.
- FRR: ability to expand coverage of basic LFA to any topology with the use of a source-routed backup path; precomputation and setup of backup path without additional signaling
- support for LFA policies with shared-risk constraints, admin-groups, and link/node protection
- support for SR-TE entropy labels
- support for TE that includes loose/strict options, distributed and centralized TE, path disjointness, ECMP awareness, and limited or no per-service state on midpoint and tail-end routers
- support for fine-grained flow steering and service chaining via a centralized stateful Path Computation Element (PCE) such as the one provided by the Nokia Network Services Platform (NSP)
3.12.1. SR-TE Support
The following MPLS commands and modes are supported:
- global [router] MPLS-level commands and modes:interface, lsp, path, shutdown
- LSP-level commands and modes:bfd, bgp-transport-tunnel, exclude, hop-limit, include, metric, primary, retry-limit, retry-timer, shutdown, to, from, vprn-auto-bind
- primary path-level commands and modes:bandwidth, bfd, exclude, hop-limit, include, shutdown
- secondary path-level commands and modes:bandwidth, bfd, exclude, hop-limit, include, path-preference, shutdown, standby
The following MPLS commands and modes are not supported:
- global MPLS-level commands and modes not applicable to SR-TE LSPs (configuration is ignored):admin-group-frr, auto-lsp, bypass-resignal-timer, cspf-on-loose-hop, dynamic-bypass, frr-object, hold-timer, least-fill-min-thd, least-fill-reoptim-thd, logger-event-bundling, lsp-template, srlg-frr, static-lsp, static-lsp-fast-retry
- LSP-level commands and modes not supported with SR-TE LSPs (configuration is blocked):adaptive, adspec, fast-reroute, least-fill, propagate-admin-group, rsvp-resv-style
- LSP-level commands and modes not supported with SR-TE LSPs (configuration is ignored):cspf, igp-shortcut
- primary path-level commands and modes not supported with SR-TE LSPs (configuration is blocked):adaptive, record, record-label
- secondary path-level commands and modes not supported with SR-TE LSPs (configuration is blocked):adaptive, record, record-label
The user can associate an empty path or a path with strict or loose explicit hops with the primary paths of the SR-TE LSP using the hop, primary, and secondary CLI commands.
A hop that corresponds to an adjacency SID must be identified with its far-end host IP address (next hop) on the subnet. If the local-end host IP address is provided, this hop is ignored because this router can have multiple adjacencies (next hops) on the same subnet.
A hop that corresponds to a node SID is identified by the prefix address.
Details of processing the user-configured path hops are provided in SR-TE LSP Instantiation.
3.12.2. SR-TE LSP Instantiation
When an SR-TE LSP is configured on the router, its path can be computed by the router or by an external TE controller referred to as a PCE. This feature works with the Nokia stateful PCE that is part of the Network Services Platform (NSP).The 7705 SAR supports three different modes of operation configurable on a per- SR-TE LSP basis.
- When the path of the LSP is computed by the router acting as a PCE client (PCC), the LSP is referred to as PCC-initiated and PCC-controlled.A PCC-initiated and controlled SR-TE LSP has the following characteristics:
- can contain strict or loose hops, or a combination of both
- does not support CSPF, and local path computation takes the form of hop-to-label translation
- has the capability to report an SR-TE LSP to synchronize the LSP database of a stateful PCE server using the pce-report option, but the LSP path cannot be updated by the PCE. The control of the LSP is maintained by the PCC.
- When the path of the LSP is computed by the PCE at the request of the PCC, it is referred to as PCC-initiated and PCE-computed.A PCC-initiated and PCE-computed SR-TE LSP supports the passive stateful mode, which enables the pce-computation option for the SR-TE LSP so that the PCE can perform path computation at the request of the PCC only. The PCC retains control.The capability exists to report an SR-TE LSP to synchronize the LSP database of a stateful PCE server using the pce-report option.
- When the path of the LSP is computed and updated by the PCE following a delegation from the PCC, it is referred to as PCC-initiated and PCE-controlled.A PCC-initiated and PCE-controlled SR-TE LSP allows active stateful mode, which enables the pce-control option for the SR-TE LSP so that the PCE can perform path computation and updates following a network event without the explicit request from the PCC. The PCC delegates full control.
The user can configure the path computation requests only (PCE-computed) or both path computation requests and path updates (PCE-controlled) to the PCE for a specific LSP using the pce-computation and pce-control commands.
The pce-computation option sends the path computation request to the PCE instead of the local CSPF. When this option is enabled, the PCE acts in passive stateful mode for this LSP. In other words, the PCE can perform path computations for the LSP only at the request of the router. This is used in cases where the operator wants to use the PCE specific path computation algorithm instead of the local router CSPF algorithm.
The default value is no pce-computation. Enabling pce-computation requires that the cspf option also be enabled; otherwise, the command is rejected. If the cspf option is disabled for an LSP, the pce-computation option will also be automatically disabled.
Enabling cspf without enabling pce-computation for an SR-TE LSP means that, internally, the router still performs label translation as if cspf was disabled, because there is no support of CSPF for an SR-TE LSP on the router.
The pce-control option allows the router to delegate full control of the LSP to the PCE (PCE-controlled). Enabling this option means that the PCE is acting in active stateful mode for this LSP and the PCE can reroute the path following a failure or to reoptimize the path and update the router without requiring a request from the router.
Note:
|
In all cases, the PCC LSP database is synchronized with the PCE LSP database using the PCEP path computation state report (PCRpt) message for LSPs that have the pce-report command enabled.
The global MPLS- level pce-report command can be used to enable or disable PCE reporting for all SR-TE LSPs for the purpose of LSP database synchronization. This configuration is inherited by all LSPs of a particular type. The PCE reports both CSPF and non-CSPF LSPs. The default value is disabled (no pce-report). This default value controls the introduction of the PCE into an existing network and allows the operator to decide if all LSP types need to be reported.
The LSP-level pce-report command overrides the global configuration for PCE reporting for an LSP. The default value is to inherit the global MPLS-level value. The inherit value reconfigures the LSP to inherit the global configuration for that LSP type.
| Note: If PCE reporting is disabled for the LSP, either due to inheritance or due to LSP-level configuration, enabling the pce-control option for the LSP has no effect. To help troubleshoot this situation, operational values of both the pce-report and pce-control are added to the output of the LSP show commands. |
For more information about configuring PCC-initiated and PCC-controlled LSPs, see Configuring PCC-controlled, PCE-computed, and PCE-controlled SR-TE LSPs.
3.12.2.1. PCC-initiated and PCC-controlled LSPs
For PCC-initiated and PCC-controlled LSPs, the user configures the LSP name, primary path name, and optional secondary path name with the path information in the referenced path name, entering a full or partial explicit path with all or some hops to the destination of the LSP. Each hop is specified as an address of a node or an address of the next hop of a TE link.
To configure the primary path or secondary path to always use a specific link whenever it is up, the strict hop must be entered as an address corresponding to the next hop of an adjacency SID. If the strict hop corresponds to a loopback address, it is translated to an adjacency SID as explained below and therefore there is no guarantee that the same TE link is picked.
To use an SR-TE path that consists of unprotected adjacency SIDs, each hop of the path must be configured as a strict hop with the address matching the next hop of the adjacency SID and protection on each of these adjacencies must be disabled as explained in SR-TE LSP Path Computation.
MPLS assigns a tunnel ID to the SR-TE LSP and a path ID to each new instantiation of the primary path, as for an RSVP-TE LSP. These IDs represent the MBB path of the same SR-TE LSP, which must coexist during the update of the primary path.
| Note: The concept of MBB is not exactly accurate in the context of an SR-TE LSP because there is no signaling involved and therefore the new path information immediately overrides the older one. |
The router retains full control of the path of the LSP. CSPF is not supported; therefore, the full or partially explicit path is instantiated as is and no other constraint (such as SRLG, admin-group, hop-count, or bandwidth) is checked. Only the LSP path label stack size is checked by MPLS against the maximum value configured for the LSP after the TE database (TE-DB) hop-to-label translation returns the label stack. See SR-TE LSP Path Computation for more information about this check.
The ingress LER performs the following steps to resolve the user-entered path before programming it in the data path:
- MPLS passes the path information to the TE-DB, which converts the list of hops into a label stack by scanning the TE-DB for adjacency and node SID information that belongs to the router or link identified by each hop address. If the conversion is successful, the TE-DB will return the actual selected hop SIDs plus labels as well as the configured path hop addresses that were used as the input for this conversion.Details of this step are as follows:
- A loose hop with an address matching any interface (loopback or not) of a router (identified by router ID) is always translated to a node SID. If the prefix matching the hop address has a node SID in the TE-DB, it will be selected by preference. If not, the node SID of any loopback interface of the same router that owns the hop address is selected. In the latter case, the lowest IP address of that router that has a /32 prefix-SID is selected.
- A strict hop with an address matching any interface (loopback or not) of a router (identified by router ID) is always translated to an adjacency SID. If the hop address matches the host address reachable in a local subnet from the previous hop, the adjacency SID of that adjacency is selected. If the hop address matches a loopback interface, it is translated to the adjacency SID of any link from the previous hop that terminates on the router owning the loopback. The adjacency SID label of the selected link is used.In both cases, it is possible to have multiple matching previous hops if the interface is a LAN interface. If there are multiple hops, the adjacency SID with the lowest interface address is selected.
- All IGP instances are scanned from the lowest to the highest instance ID, beginning with IS-IS instances and then the OSPF instance; not only the IGP instance that resolved the prefix of the destination address of the LSP in the RTM is used. For the first instance where all specified path hop addresses can be translated, the label stack is selected. The hop-to-SID/label translation tool does not support paths that cross area boundaries. All SID/labels of a given path are therefore taken from the same IGP area and instance.

Note: For the hop-to-label translation to operate, the user must enable TE on the network links by adding the network interfaces to MPLS and RSVP. In addition, the user must enable the traffic-engineering option on all participating router IGP instances. If a router has the database-export option enabled in the participating IGP instances to populate the TE-DB with the learned IGP link-state information, then enabling of the traffic-engineering option is not required. For consistency, it is recommended that the traffic-engineering option always be enabled.
- The ingress LER validates the first hop of the path to determine the outgoing interface and next hop to forward the packet to, and programs the data path according to the following conditions.
- If the first hop corresponds to an adjacency SID (host address of next hop on the link’s subnet), the adjacency SID label is not pushed. In other words, the ingress LER treats forwarding to a local interface as a push of an implicit null label.
- If the first hop is a node SID of a downstream router, the node SID label is pushed.
In both cases, the SR-TE LSP tracks and uses the SR shortest path tunnel of the SID of the first hop. - If the router is configured as a PCC and has a PCEP session to a PCE, the router sends a PCRpt message to update the PCE with the Up state and the RRO object for each LSP that has the pce-report option enabled. The PE router does not set the delegation control flag to keep LSP control. The state of the LSP is now synchronized between the router and the PCE.
3.12.2.1.1. Guidelines for Using PCC-initiated and PCC-controlled LSPs
The 7705 SAR does not support CSPF path computation for an SR-TE LSP and uses hop-to-label translation to compute the path. The ingress LER does not monitor network events that affect the reachability of the adjacency SID or node SID used in the label stack of the LSP; therefore, the label stack is not updated to reflect changes in the path except when seamless BFD is used to detect path failures. As a result, it is recommended that this type of SR-TE LSP be used in the following configurations only:
- empty path
- path with a single node SID loose hop
- path of an LSP to a directly connected router (single-hop LSP) with an adjacency SID or a node SID loose or strict hop
- strict path with hops of adjacencies explicitly configured in the path and seamless BFD used to monitor the LSP
In addition, the user can configure an SR-TE LSP with a single loose hop, using the anycast SID concept to provide LSR node protection within a particular plane of the network TE topology. This is illustrated in Figure 12. The user configures all LSRs in a plane with the same loopback interface address, which must be different from that of the system interface and the router ID of the router, and assigns them the same node SID index value. All routers must use the same SRGB.
Figure 12: Multi-plane TE with Node Protection
The user then configures an SR-TE LSP on an LER to a destination and adds to its path a loose hop matching the anycast loopback address. The SR-TE LSP to any destination will hop over the closest of the LSRs owning the anycast SID because the resolution of the node SID for that anycast loopback address uses the closest router. If that router fails, the resolution is updated to the next closest router owning the anycast SID without changing the label stack of the SR-TE LSP.
3.12.2.2. PCC-initiated and PCE-computed/controlled LSP
In the PCC-initiated and PCE-computed/controlled LSP mode of operation, the ingress LER uses PCEP to communicate with a PCE-based external TE controller (also referred to as the PCE). The router instantiates a PCEP session to the PCE. The router is referred to as the PCE client (PCC).
When the user enables the pce-computation option for one or more SR-TE LSPs, the PCE performs path computations at the request of the PCC, which is referred to as passive stateful mode. If the user enables the pce-control option for an LSP, the PCE can also perform both path computation and periodic reoptimization of the LSP path without an explicit request from the PCC. This is referred to as active stateful mode.
For the PCC to communicate with a PCE about the management of the path of an SR-TE LSP, the router implements the extensions to PCEP in support of segment routing (see PCEP for more information).This feature works with the Nokia stateful PCE, which is part of the network services platform (NSP).
The following steps describe configuring a PCC-initiated SR-TE LSP when passive or active control is given to the PCE.
- The SR-TE LSP configuration is created on the PE router using the CLI or NSP NFM-P.The configuration dictates which PCE stateful mode is desired: active (pce-control option enabled) or passive (pce-computation enabled and pce-control disabled).
- The PCC assigns a unique PLSP-ID to the LSP. The PLSP-ID uniquely identifies the LSP on a PCEP session and must remain constant during its lifetime. The PCC on the router tracks the association of {PLSP-ID, SRP-ID} to {tunnel-ID, path-ID} and uses the latter to communicate with MPLS about a specific path of the LSP.
- The PE router does not validate the entered path. While the PCC can include the IRO objects for any loose or strict hop in the configured LSP path in the path computation request (PCReq) message to the PCE, the PCE ignores the IRO objects and computes the path with the other constraints.
- The PE router sends a PCReq message to the PCE to request a path for the LSP and includes the LSP parameters in the METRIC object, the LSPA object, and the BANDWIDTH object. It also includes the LSP object with the assigned PLSP-ID. At this point, the PCC does not delegate control of the LSP to the PCE.
- The PCE computes a new path, reserves the bandwidth, and returns the path in a path computation reply (PCRep) message with the computed ERO in the ERO object. It also includes the LSP object with the unique PLSP-ID, the METRIC object with the computed metric value if any, and the BANDWIDTH object.

Note: In order for the PCE to use the SRLG path diversity and admin-group constraints in the path computation, the user must configure the SRLG and admin-group membership against the MPLS interface and verify that the traffic-engineering option is enabled in the IGP. This causes the IGP to flood the link SRLG and admin-group membership in its participating area and for the PCE to learn it in its TE database.
- The PE router updates the CSM and the data path with the new path.Up to this step, the PCC and PCE are using passive stateful PCE procedures. The next steps synchronize the LSP database of the PCC and PCE for both PCE-computed and PCE-controlled LSPs. They also initiate the active PCE stateful procedures for the PCE-controlled LSP only.
- The PE router sends a PCRpt message to update the PCE with the Up state and the RRO as confirmation, including the LSP object with the unique PLSP-ID. For a PCE-controlled LSP, the PE router also sets a delegation control flag to delegate control to the PCE. The state of the LSP is now synchronized between the router and the PCE.
- Following a network event or reoptimization, the PCE computes a new path for a PCE-controlled LSP and returns it in a path computation update (PCUpd) message with the new ERO. It includes the LSP object with the same unique PLSP-ID assigned by the PCC and the stateful request parameter (SRP) object with a unique SRP-ID number to track error and state messages specific to this new path.
- The PE router updates the CSM and the data path with the new path.
- The PE router sends a new PCRpt message to update the PCE with the Up state and the RRO as confirmation. The state of the LSP is now synchronized between the router and the PCE.
- If the user makes any configuration change to the PCE-computed or PCE-controlled LSP, MPLS requests the PCC to revoke delegation in a PCRpt message (PCE-controlled only), and then MPLS and the PCC follow the above steps to convey the changed constraint to the PCE, which will result in a new path programmed into the data path, the LSP databases of the PCC and PCE to be synchronized, and the delegation to be returned to the PCE.For SR-TE LSPs, MBB is not supported. Therefore, the PCC first tears down the LSP and sends a PCRpt message to the PCE with the remove flag set to 1 before following this configuration change procedure.
| Note: The above procedures are followed when the user performs a no shutdown on a PCE-controlled or PCE-computed LSP. The starting point is an administratively down LSP with no active paths. |
The following steps are for an LSP with an active path.
- If the user enabled the pce-computation option on a PCC-controlled LSP that has an active path, no action is performed until the next time the router needs a path for the LSP following a network event or an LSP parameter change. At that point, the procedures above are followed.
- If the user enabled the pce-control option on a PCC-controlled or PCE-computed LSP that has an active path, the PCC will issue a PCRpt message to the PCE with the Up state and the RRO of the active path. The PCC will set the delegation control flag to delegate control to the PCE. The PCE will keep the active path of the LSP and will not update until the next network event or reoptimization. At that point, the procedures above are followed.
The PCE supports the computation of disjoint paths for two different LSPs originating or terminating on the same or different PE routers. To indicate this constraint to the PCE, the user must configure the PCE path profile ID and path group ID that the LSP belongs to. These parameters are passed transparently by the PCC to the PCE and are therefore opaque data to the router. The user can configure the path profile and path group using the path-profile profile-id [path-group group-id] command.
The association of the optional path group ID is to allow the PCE to determine which profile ID this path group ID must be used with. One path group ID is allowed per profile ID. The user can, however, enter the same path group ID with multiple profile IDs by executing this command multiple times. A maximum of five entries of path-profile [path-group] can be associated with the same LSP. More details of the operation of the PCE path profile are provided in the PCEP chapter.
3.12.3. SR-TE LSP Path Computation
For PCC-controlled SR-TE LSPs, CSPF is not supported on the router. Whether the cspf option is enabled or disabled for an SR-TE LSP, MPLS makes a request to the TE-DB to get the label corresponding to each hop entered by the user in the primary path of the SR-TE LSP. See PCC-initiated and PCC-controlled LSPs for details of the hop-to-label translation.
The user can configure the path computation request of a CSPF-enabled SR-TE LSP to be forwarded to a PCE instead of the local router CSPF by enabling the pce-computation option, as explained in SR-TE LSP Instantiation. The user can further delegate the reoptimization of the LSP to the PCE by enabling the pce-control option. In both cases, the PCE is responsible for determining the label required for each returned explicit hop and includes this in the SR-ERO.
In all cases, the user can configure the maximum number of labels that the ingress LER can push for a particular SR-TE LSP by using the max-sr-labels command.
This command is used to set a limit on the maximum label stack size of the SR-TE LSP primary path to allow room to insert additional transport, service, and other labels when packets are forwarded in a particular context.
The max-sr-labels label-stack-size value should be set to account for the desired maximum label stack of the primary path of the SR-TE LSP. Its range is 1 to 11 and the default value is 6.
The value in additional-frr-labels labels should be set to account for additional labels inserted by remote LFA or Topology Independent LFA (TI-LFA) for the backup next hop of the SR-TE LSP. Its range is 0 to 4 labels with a default value of 1.
The sum of both label values represents the worst-case transport of SR label stack size for this SR-TE LSP and is populated by MPLS in the TTM such that services and shortcut applications can check it to decide if a service can be bound or a route can be resolved to this SR-TE LSP. More details of the label stack size check and requirements in various services and shortcut applications are provided in Service and Shortcut Application SR-TE Label Stack Check.
The maximum label stack supported by the router is discussed in Data Path Support. The maximum label stack is always signaled by the PCC in the PCEP Open object as part of the SR-PCE-CAPABILITY TLV. It is referred to as the Maximum Stack Depth (MSD).
In addition, the per-LSP value for the max-sr-labels label-stack-size option, if configured, is signaled by the PCC to the PCE in the SID Depth value in a METRIC object for both a PCE-computed LSP and a PCE-controlled LSP. The PCE will compute and provide the full explicit path with TE links specified. If there is no path with the number of hops lower than the MSD value or the SID Depth value (if signaled), a reply with no path will be returned to the PCC.
For a PCC-controlled LSP, if the label stack returned by the TE-DB hop-to-label translation exceeds the per-LSP maximum SR label stack size, the LSP is brought down.
3.12.3.1. Service and Shortcut Application SR-TE Label Stack Check
Each service and shortcut application on the router performs a check of the resulting net label stack after pushing all the labels required for forwarding the packet in that context. The MPLS module populates each SR-TE LSP in the TTM with the maximum transport label stack size, which consists of the sum of the values in max-sr-labels label-stack-size and additional-frr-labels labels.
Each service or shortcut application then adds the additional, context-specific labels, such as service label and NGE label, required to forward the packet in that context, and checks that the resulting net label stack size does not exceed the maximum label stack supported by the router.
If the check succeeds, the service is bound or the prefix is resolved to the SR-TE LSP. If the check fails, the service will not bind to this SR-TE LSP. Instead, the service will either find another SR-TE LSP or another tunnel of a different type to bind to, if the user configured the use of other tunnel types. Otherwise, the service will go down.
When the service uses an SDP with one or more SR-TE LSPs (up to eight), the spoke SDP bound to this SDP will remain operationally down as long as at least one SR-TE LSP fails the check. In this case, the spoke SDP flag “labelStackLimitExceeded” will be displayed in the show output of the service. As well, the prefix will not get resolved to the SR-TE LSP and will either be resolved to another SR-TE LSP or another tunnel type or become unresolved.
The value of additional-frr-labels labels is checked against the maximum value across all IGP instances of the parameter frr-overhead. The frr-overhead parameter value is computed within an IGP instance as shown in Table 7. For more information on FRR overhead, refer to the “Segment Routing in Shortest Path Forwarding” section in the 7705 SAR Routing Protocols Guide.
Table 7: Parameter Values for frr-overhead
Condition | Parameter Value |
segment-routing is disabled in the IGP instance | 0 |
segment-routing is enabled but remote-lfa is disabled and ti-lfa is disabled | 0 |
segment-routing is enabled and remote-lfa is enabled but ti-lfa is disabled | 1 |
segment-routing is enabled and ti-lfa is enabled, regardless of whether remote-lfa is enabled or disabled | ti-lfa max-sr-frr-labels label |
When the user configures or changes the configuration of additional-frr-labels, MPLS ensures that the new value accommodates the frr-overhead parameter value across all IGP instances.
For example:
- The user configures the config>router>isis>loopfree-alternate remote-lfa command.
- The user creates a new SR-TE LSP or changes the configuration of an existing SR-TE LSP as follows: mpls>lsp>max-sr-labels 10 additional-frr-labels 0.
- Performing a no shutdown of the new LSP or changing the existing LSP configuration will be blocked because the IS-IS instance enabled remote LFA, which requires one additional label on top of the 10 SR labels of the primary path of the SR-TE LSP.
If the check is successful, MPLS adds max-sr-labels and additional-frr-labels and checks that the sum is lower than or equal to the maximum label stack supported by the router. MPLS then populates the value of {max-sr-labels + additional-frr-labels}, along with tunnel information in the TTM, and also passes max-sr-labels to the PCEP module.
Conversely, if the user tries a configuration change that results in a change to the computed frr-overhead, the IGP will check that all SR-TE LSPs can properly account for the overhead; otherwise, the change is rejected. On the IGP, enabling remote-lfa may cause the frr-overhead value to change.
For example:
- An MPLS LSP is administratively enabled and has mpls>lsp>max-sr-labels 10 additional-frr-overhead 0 configured.
- The current configuration in IS-IS or OSPFv2 has the loopfree-alternate command disabled.
- The user attempts to configure loopfree-alternate remote-lfa for IS-IS or OSPFv2. This changes frr-overhead to 1.This configuration change would be blocked.
When the user configures the ti-lfa command, the max-sr-frr-labels value parameter is used to limit the search for the LFA backup next hop, as follows:
- 0 — the IGP LFA SPF restricts the search to the TI-LFA backup next hop that does not require a repair tunnel, meaning that the P node and Q node are the same and match a neighbor. This is also the case when both P and Q nodes match the advertising router for a prefix. For information on P nodes and Q nodes, refer to draft-francois-rtgwg-segment-routing-ti-lfa-04 (Topology Independent Fast Reroute using Segment Routing).
- 1 to 3 — the IGP LFA SPF widens the search to include a repair tunnel to a P node that is connected to the Q nodes with zero to two hops for a total of three labels maximum: one node SID-to-P node and two adjacency SIDs from the P node to the Q node. If the P node is a neighbor of the computing node, its node SID is compressed, meaning that up to three adjacency SIDs can separate the P and Q nodes.
- 2 (default) — this corresponds to a repair tunnel to a non-adjacent P node that is adjacent to the Q node. If the P node is a neighbor of the computing node, the node SID of the P node is compressed and the default value of two labels corresponds to two adjacency SIDs between the P and Q nodes.
When the user attempts to change the max-sr-frr-labels parameter to a value that results in a change to the computed FRR overhead, the IGP checks that all SR-TE LSPs can properly account for the overhead based on the configuration of the LSP max-sr-labels and additional-frr-labels values; otherwise, the change is rejected.
The FRR overhead is computed by the IGP and its value is shown in Table 7.
The above LFA commands allow the user to enable the base LFA feature with the loopfree-alternate command, and to optionally add remote LFA with the remote-lfa option and TI-LFA with the ti-lfa option. For more information, refer to the “Segment Routing in Shortest Path Forwarding” section in the 7705 SAR Routing Protocols Guide.
3.12.4. SR-TE LSP Protection
Each path is locally protected along the network using LFA or remote-LFA next hop whenever possible. The protection of a node SID reuses the LFA and remote LFA features introduced with segment routing shortest path tunnels; the protection of an adjacency SID has been added to the 7705 SAR in the specific context of an SR-TE LSP to augment the protection level. The user must enable the loopfree-alternate [remote-lfa] option in IS-IS or OSPF.
An SR-TE LSP has state at the ingress LER only. The LSR has state for the node SID and adjacency SID, whose labels are programmed in the label stack of the received packet and which represent the part of the ERO of the SR-TE LSP on this router and downstream of this router. In order to provide protection for an SR-TE LSP, each LSR node must attempt to program a link-protect or node-protect LFA next hop in the ILM record of a node SID or an adjacency SID, and the LER node must do the same in the LTN record of the SR-TE LSP. The following are details of the behavior.
- If the ILM record is for a node SID of a downstream router that is not directly connected, the ILM of this node SID points to the backup NHLFE computed by the LFA SPF and programmed by the SR module for this node SID. Depending on the topology and LFA policy used, this can be a link-protect or node-protect LFA next hop.This behavior is already supported in the SR shortest path tunnel feature at both the LER and LSR. Therefore, an SR-TE LSP that transits at an LSR and that matches the ILM of a downstream node SID automatically takes advantage of this protection when enabled. If required, node SID protection can be disabled under the IGP instance by excluding the prefix of the node SID from the LFA.
- If the ILM is for a node SID of a directly connected router, the LFA SPF only provides link protection. The ILM or LTN record of this node SID points to the backup NHLFE of this LFA next hop. An SR-TE LSP that transits at an LSR and that matches the ILM of a neighboring node SID automatically takes advantage of this protection when enabled.

Note: Only link protection is possible in this case because packets matching this ILM record can either terminate on the neighboring router owning the node SID or can be forwarded to different next hops of the neighboring router, that is, to different next next-hops of the LSR providing the protection. The LSR providing the connection does not have context to distinguish among all possible SR-TE LSPs and therefore can only protect the link to the neighboring router.
- If the ILM or LTN record is for an adjacency SID, it is treated as in the case of a node SID of a directly connected router.When protecting an adjacency SID, the PLR first tries to select a parallel link to the node SID of the directly connected neighbor. That is the case when the node SID is reachable over parallel links. The selection is based on lowest interface ID. If no parallel links exist, regular LFA/remote LFA algorithms are applied to find a loopfree path to reach the node SID of the neighbor via other neighbors.The ILM or LTN for the adjacency SID must point to this backup NHLFE and will benefit from FRR link protection. As a result, an SR-TE LSP that transits at an LSR and matches the ILM of a local adjacency SID automatically takes advantage of this protection when enabled.
- At the ingress LER, the LTN record points to the SR-TE LSP NHLFE, which points to the NHLFE of the SR shortest path tunnel to the node SID or adjacency SID of the first hop in the ERO of the SR-TE LSP.The FRR link or node protection at the ingress LER is inherited directly from the SR shortest path tunnel.
If an adjacency to a neighbor fails, the IGP withdraws the advertisement of the link TLV information as well as its adjacency SID sub-TLV. However, the LTN or ILM record of the adjacency SID must be kept in the data path for a sufficient period of time to allow the ingress LER to compute a new path after the IGP converges. If the adjacency is restored before the timer expires, the timer is aborted as soon as the new ILM or LTN records are updated with the new primary and backup NHLFE information. By default, the ILM/LTN and NHLFE information is kept for a period of 15 seconds.
The adjacency SID hold timer is configured using the adj-sid-hold command and activated when the adjacency to the neighbor fails due to the following conditions:
- the network IP interface went down due to a link or port failure or due to the user performing a shutdown of the port
- the user shuts down the network IP interface in the config>router or config>router>ospf/isis context
The adjacency SID hold timer is not activated if the user deletes an interface in the config>router>ospf/isis context.
Note:
|
While protection is enabled globally for all node SIDs and local adjacency SIDs when the user enables the loopfree-alternate option in IS-IS or OSPF at the LER and LSR, there are applications where the user wants traffic to never divert from the strict hop computed by CSPF for an SR-TE LSP. In that case, the user can disable protection for all adjacency SIDs formed over a particular network IP interface using the sid-protection command.
The protection state of an adjacency SID is advertised in the B-FLAG of the IS-IS or OSPF Adjacency SID sub-TLV. No mechanism exists in PCEP for the PCC to signal to the PCE the constraint to use only adjacency SIDs, which are not protected. The path profile ID is configured in the PCE with the no-protection constraint.
3.12.5. Seamless BFD for SR-TE LSPs
The 7705 SAR supports seamless BFD (S-BFD). Unlike LSP BFD, S-BFD does not rely on the traditional BFD session bootstrapping process or session state at the tail end of a session. Instead, when S-BFD is initialized the system selects a set of discriminators for the reflector or initiator function.
One S-BFD reflector is configured per system in the config>bfd>seamless-bfd context. A mapping between reflector discriminators and their IP addresses is configured on the initiator in the config>router>bfd>seamless-bfd context.
For information on seamless BFD, refer to the 7705 SAR Router Configuration Guide, “Seamless BFD”.
This section describes the application of S-BFD to SR-TE LSPs and the LSP configuration required for this feature.
S-BFD is supported in the following SR-TE contexts:
- PCC-initiated:
- SR-TE LSP level
- SR-TE primary path
- SR-TE secondary and standby paths
3.12.5.1. Configuration of S-BFD on SR-TE LSPs
For PCC-initiated or PCC-controlled LSPs, the head end of an S-BFD session is configured under the SR-TE LSP context, the SR-TE primary path context, or the SR-TE secondary path context by using the following commands:
- config>router>mpls>lsp lsp-name sr-te>bfd
- config>router>mpls>lsp lsp-name sr-te>primary>bfd
- config>router>mpls>lsp lsp-name sr-te>secondary>bfd
The remote discriminator value is determined by passing the to address of the LSP to BFD, which then matches it to a mapping table of peer IP addresses to reflector remote discriminators. If there is no match for the to address of the LSP, a BFD session is not established on the LSP or path.
| Note: A remote peer IP address-to-discriminator mapping must exist prior to bringing an LSP administratively up. |
The referenced BFD template must specify parameters that are consistent with an S-BFD session; for example, the endpoint type must be np.
S-BFD can be configured at the LSP level, as follows:
When S-BFD is configured at the LSP level, separate S-BFD sessions with the same configuration are enabled on all primary, secondary, and standby paths of the LSP.
Alternatively, S-BFD can be configured on the primary path or secondary path of the LSP, as follows:
The wait-for-up-timer command is only available if the configured failure action is failover-or-down. For more information, see Support for BFD Failure Action with SR-TE LSPs.
3.12.5.2. Support for BFD Failure Action with SR-TE LSPs
S-BFD provides a mechanism to check the data path forwarding for an SR-TE LSP. If an S-BFD session fails, the LSP can be brought operationally down when the failure-action command is configured with the failover-or-down option. When the failure-action command is configured with the none option, an S-BDF failure will only raise a trap. The failure-action command is available in the following context:
The failure-action command is configured at the LSP level. It can be configured whether S-BFD is applied at the LSP level or the individual path level. The failure-action command can be configured even if the BFD template is not yet configured.
For LSPs configured with a primary path and a secondary or a standby path and a failure action of failover-or-down, the following points apply.
- The path is held in an operationally down state when its S-BFD session is down.
- If all paths are operationally down, the SR-TE LSP is taken operationally down and a trap is generated.
- If S-BFD is enabled at the LSP or active path level, a switchover from the active path to an available path is triggered if the S-BFD session fails on the active path (primary or standby).
- If S-BFD is not enabled on the active path and this path is shut down, a switchover is triggered.
- If S-BFD is enabled on the candidate standby or secondary path, this path is only selected if S-BFD is up.
- An inactive standby path configured with S-BFD is only available to become active if it is not operationally down; that is, its S-BFD session is up and all other criteria for it to become operational are true. The path is held in an inactive state if the S-BFD session is down.
- The system does not revert to the primary path or start a reversion timer when the primary path is either administratively down or operationally down, because the S-BFD session is not up or down for any other reason.
For LSPs configured with only one path and a failure action of failover-or-down, the following points apply.
- The path is held in an operationally down state when its S-BFD session is down.
- If the path is operationally down, the LSP is taken operationally down and a trap is generated.

Note: S-BFD and other OAM packets can still be sent on an operationally down SR-TE LSP.
For LSPs configured with one or more paths and a failure action of none, a BFD trap is raised when the LSP goes down. The path state does not change.
3.12.5.2.1. SR-TE LSP State Changes and Failure Actions Based on S-BFD
When a path is first configured with S-BFD, it is held operationally down until BFD comes up (subject to the BFD wait time).
The BFD wait-for-up-timer is started when BFD is first enabled on a path or when an existing S-BFD session transitions from up to down. If this timer expires before S-BFD is up, the path is torn down and the LSP retry timer is started.
In the S-BFD up-to-down case, if there is only one path, the LSP is torn down when S-BFD fails and then deprogrammed when the wait-for-up-timer expires.
If all the paths of an LSP are operationally down due to S-BFD, the LSP is taken operationally down and the BFD wait-for-up-timer is started for each path. If one or more paths do not have S-BFD configured or are otherwise not down, the LSP is not taken operationally down.
When an existing S-BFD session fails on a path and the failure action is failover-or-down, the configured failure action is activated, the path is put into the operationally down state, and a trap is raised. The state and reason code are displayed with the show>router>bfd>seamless-bfd command.
3.12.5.3. S-BFD Operational Considerations
A minimum control packet timer transmit interval of 10 ms can be configured. To maximize the reliability of S-BFD connectivity checking in scaled scenarios with short timers, situations where BFD may go down due to normal changes of the next hop of an LSP path at the head end must be avoided. It is therefore recommended that LFA not be configured at the head-end LER when using S-BFD with sub-second timers. When LFA is not configured, protection of the SR-TE LSP is still provided end-to-end by the combination of S-BFD connectivity checking and primary or secondary path protection.
Similar to LDP and RSVP functionality, S-BFD uses a single path for a loose hop; multiple S-BFD sessions for each of the ECMP paths or spraying of S-BFD packets across the paths is not supported. S-BFD is not down until all the ECMP paths of the loose hop go down.
| Note: With very short control packet timer values in scaled scenarios, S-BFD may bounce if the next hop that the path is currently using goes down. This is because it takes time for BFD to be updated to use another next hop in the ECMP set. |
3.12.6. Static Route Resolution Using SR-TE LSPs
Static route packets can be forwarded to an indirect next hop over an SR-TE LSP programmed in the TTM with the following static route tunnel binding command:
3.12.7. BGP Label Route Resolution Using SR-TE LSPs
An SR-TE LSP programmed in the TTM can be used for resolving the next hop of a BGP IPv4 label route with the following BGP transport tunnel command:
3.12.8. Service Packet Forwarding Using SR-TE LSPs
An SDP sub-type of the MPLS encapsulation type allows service binding of up to eight SR-TE LSPs programmed in the TTM by MPLS. The following example shows how to bind an SR-TE LSP to an MPLS SDP:
The destination address of all LSPs must match the SDP far-end address. Service data packets are sprayed over the set of LSPs in the SDP using the same procedures as for tunnel selection in ECMP. In all cases, the SDP can only spray packets over a maximum of eight next hops. Each SR-TE LSP can, however, have up to eight next hops at the ingress LER when the first segment is a node SID-based SR tunnel. The SDP selects one next hop from each SR-TE LSP until the maximum number of eight next hops for the SDP is reached.
The tunnel-far-end option is not supported. In addition, the mixed-lsp-mode option does not support the sr-te tunnel type.
The signaling protocol for the service labels for an SDP using an SR-TE LSP can be configured to static (off), T-LDP (tldp), or BGP (bgp).
An SR-TE LSP can be used in VPRN auto-bind with the following commands:
Both VPN-IPv4 and VPN-IPv6 (6VPE) are supported in a VPRN service using segment routing transport tunnels with the auto-bind-tunnel command.
This auto-bind-tunnel command is also supported with BGP EVPN service, as shown below:
The following service contexts are supported with SR-TE LSPs:
- VLL, VPLS, IES/VPRN spoke-SDP and interface, and R-VPLS
- Epipe and VPLS services under BGP EVPN
- intra-AS BGP VPRN for VPN-IPv4 and VPN-IPv6 prefixes with both auto-bind and explicit SDP
- inter-AS option C for VPN-IPv4 and VPN-IPv6 VPRN prefix resolution
- multicast over IES/VPRN spoke interface with spoke-SDP over an SR-TE LSP
3.12.9. Data Path Support
The support of SR-TE in the data path requires that the ingress LER push a label stack where each label represents a hop, a TE link, or a node, in the ERO for the LSP path computed by the router or the PCE. However, only the label and the outgoing interface to the first strict or loose hop in the ERO factor into the forwarding decision of the ingress LER. In other words, the SR-TE LSP only needs to track the reachability of the first strict or loose hop.
The first strict or loose hop of the SR-TE LSP is represented as an NHFLE to the SR shortest path tunnel. The rest of the SR-TE label stack can have a larger size and is modeled as another NHLFE referred to as a “super NHLFE”.
Therefore, an SR-TE LSP is modeled in the ingress LER data path as a hierarchical LSP with the super NHLFE tunneled over the NHLFE of the SR shortest path tunnel to the first strict or loose hop in the SR-TE LSP path ERO.
Some characteristics of this design are as follows.
- The design saves on NHLFE usage. When many SR TE LSPs are going to the same first hop, they will be using the same SR shortest path tunnel and will consume one super NHLFE each, but they will be pointing to a single NHLFE, or set of NHLFEs, when ECMP exists for the first strict or loose hop, of the first-hop SR tunnel.The ingress LER does not need to program a separate backup super NHLFE. Instead, the single super NHLFE will automatically begin forwarding packets over the LFA backup path of the SR tunnel to the first hop as soon as it is activated.
- There is an exception to the above model in the case where the user configured an empty path SR-TE LSP that uses the router’s hop-to-label translation. In this case, the SR-TE LSP will use the NHLFE of the node SID of the destination router. The super NHLFE is null in this case.
- If the first segment is a node SID tunnel and multiple next hops exist, ECMP spraying is supported at the ingress LER.
- If the first-hop SR tunnel, node SID, or adjacency SID goes down, the SR module informs MPLS that the outer tunnel is down and MPLS brings the SR-TE LSP down and requests the SR to delete the SR-TE LSP in the IOM.
The data path behavior at the LSR and egress LER for an SR-TE LSP is similar to that of the shortest path tunnel because there is no tunnel state in these nodes. The forwarding of the packet is based on processing the incoming label stack consisting of a node SID and/or adjacency SID label. If the ILM is for a node SID and multiple next hops exist, ECMP spraying is supported at the LSR.
The link-protect LFA backup next hop for an adjacency SID can be programmed at the ingress LER and LSR nodes (as explained in SR-TE LSP Protection).
A maximum of 12 labels, including all transport (including entropy), service, NGE, and OAM labels, can be pushed. The label stack size for the SR-TE LSP can be 1 to 11 labels, with a default value of 6.
The label stack size manipulation includes the following LER and LSR roles:
- LER role:
- push up to 12 labels depending on the service type
- pop up to 8 labels
- LSR role:
- pop up to 5 labels and swap 1 label for a total of 6 labels
- LSR hash of a packet with up to 10 labels
An example of the label stack pushed by the ingress LER and by an LSR acting as a PLR is illustrated in Figure 13.
Figure 13: SR-TE LSP Label Stack Programming
On node A, the user configures an SR-TE LSP to node D with a list of explicit strict hops mapping to the adjacency SID of links A-B, B-C, and C-D.
Ingress LER A programs a super NHLFE consisting of the label for the adjacency over link C-D and points it to the already programmed NHLFE of the SR tunnel of its local adjacency over link A-B. The latter NHLFE has the top label and also the outgoing interface to send the packet to.
| Note: The SR-TE LSP does not consume a separate backup super NHLFE; it only points the single super NHLFE to the NHLFE of the SR shortest path tunnel it is riding. When the latter activates its backup NHLFE, the SR-TE LSP will automatically forward over it. |
LSR Node B already programmed the primary NHLFE for the adjacency SID over link C-D and has the ILM with label 1001 point to it. In addition, node B will preprogram the link-protect LFA backup next hop for link B-C and point the same ILM to it.
| Note: There is no super NHLFE at node B because it only deals with the programming of the ILM and primary and backup NHLFE of its adjacency SIDs and its local and remote node SIDs. |
VPRN service in node A forwards a packet to the VPN-IPv4 prefix X advertised by BGP peer D. Figure 13 shows the resulting data path at each node for the primary path and for the FRR backup path at LSR B.
3.12.9.1. SR-TE LSP Metric and MTU Settings
The MPLS module assigns an SR-TE LSP the maximum LSP metric value of 16 777 215 when the local router provides the hop-to-label translation for its path. For an SR-TE LSP that uses PCE for path computation (pce-computation option enabled) by the PCE and/or has its control delegated to the PCE (pce-control enabled), the latter will return the computed LSP IGP or TE metric in the PCReq and PCUpd messages. In both cases, the user can override the returned value by configuring an admin metric using the command config>router>mpls>lsp>metric.
The MTU setting of an SR-TE LSP is derived from the MTU of the outgoing SR shortest path tunnel it is using, adjusted with the size of the super NHLFE label stack size.
The following are the details of this calculation:
SR_Tunnel_MTU = MIN {Cfg_SR_MTU, IGP_Tunnel_MTU – (1+ frr-overhead)×4}
where:
- Cfg_SR_MTU is the MTU configured by the user for all SR tunnels within a particular IGP instance using config>router>ospf/isis>segment-routing>tunnel-mtu. If no value was configured by the user, the SR tunnel MTU will be fully determined by the IGP interface calculation. This calculation is performed by the IGP and passed to the SR module each time it changes due to an updated resolution of the node SID.
- IGP_Tunnel_MTU is the minimum of the IS-IS or OSPF interface MTU among all the ECMP paths or among the primary and LFA backup paths of this SR tunnel.
- frr-overhead is set to 1 if segment-routing and remote-lfa options are enabled in the IGP instance; otherwise, it is set to 0.
This calculation is performed by the IGP and passed to the SR module each time it changes due to an updated resolution of the node SID.
The 7705 SAR also provides the MTU for the adjacency SID tunnel because it is needed in an SR-TE LSP if the first hop in the ERO is an adjacency SID. In that case, the calculation for SR_Tunnel_MTU, initially introduced for a node SID tunnel, is applied to get the MTU of the adjacency SID tunnel.
The MTU of the SR-TE LSP is derived as follows:
SRTE_LSP_MTU = SR_Tunnel_MTU – numLabels×4
where:
- SR_Tunnel_MTU is the MTU SR tunnel shortest path that the SR-TE LSP is using. The 7705 SAR also provides the MTU for the adjacency SID tunnel because it is needed in an SR-TE LSP if the first hop in the ERO is an adjacency SID. In that case, the calculation for SR_Tunnel_MTU (given above), initially introduced for a node SID tunnel, is applied to get the MTU of the adjacency SID tunnel.
- numLabels is the number of labels found in the super NHLFE of the SR-TE LSP. At LER, the super NHLFE is pointing to the SR tunnel NHLFE, which has a primary and a backup NHLFE.
This calculation is performed by the SR module and is updated each time the SR-TE LSP path changes or the SR tunnel it is using is updated.
3.12.10. SR-TE Entropy Labels
The 7705 SAR supports SR-TE entropy labels as described in MPLS Entropy Labels.
3.13. Weighted ECMP by RSVP-TE or SR-TE LSPs
ECMP over MPLS LSPs for VPRN services and IES or VPRN Layer 3 spoke SDP interfaces implements packet spraying across multiple RSVP-TE or for SR-TE LSPs within the same ECMP set.
ECMP RSVP-TE or SR-TE packet spraying consists of hashing the relevant fields in the header of a labeled packet and selecting the next-hop tunnel based on the modulo operation of the output of the hash and the number of ECMP tunnels. The maximum number of ECMP tunnels selected from the Tunnel Table Manager (TTM) matches the value of the user-configured ecmp command. Only LSPs with the same lowest LSP metric can be part of the ECMP set. If the number of these LSPs is higher than the value configured with the ecmp command, the LSPs with the lowest tunnel IDs are selected first. The ecmp command context for setting the maximum number of tunnels that can be used for auto-bind tunnel resolution is config>router>ecmp max-ecmp-routes.
| Note: The 7705 SAR supports a maximum of eight ECMP routes (max-ecmp-routes), which is the maximum value that an LSP can bear after normalization. |
With the weighted ECMP functionality, the load-balancing weight of the LSP is normalized by the system and then used to bias the amount of traffic forwarded over each LSP.
The weight of the LSP is configured using the config>router>mpls>lsp>load-balancing-weight weight and config>router>mpls>lsp-template>load-balancing-weight weight commands.
| Note: SR-TE LSP templates are currently not supported. |
Weighted ECMP for IVPN services with auto-bind is enabled using the config>service>vprn>auto-bind-tunnel>weighted-ecmp command. This command is applicable if the auto-bind tunnel is configured for RSVP or SR-TE using the config>service>vprn>auto-bind-tunnel>resolution-filter>rsvp/sr-te command.
If weighted ECMP is enabled, a path is selected based on the output of the configured hashing algorithm. Packet paths are then mapped to LSPs for the service in proportion to the configured load-balancing weight of the LSP. The hash is based on the system load-balancing configuration. Weighted ECMP is disabled by default.
If an LSP in the ECMP set has no load-balancing weight configured, and the ECMP is set to a specific next hop, regular ECMP spraying is used.
The config>service>vprn>auto-bind-tunnel>ecmp max-ecmp-routes command configures the number of tunnels that can be used for auto-bind tunnel resolution.
Weighted ECMP for IES or VPRN Layer 3 spoke SDP interfaces is enabled using the config>service>sdp>weighted-ecmp command. This command is applicable when the SDP has RSVP-TE LSPs configured using the config>service>sdp>lsp command or SR-TE LSPs configured using the config>service>sdp>sr-te-lsp command.
When weighted ECMP is enabled on an SDP, a path is selected based on the configured hash. Paths are then load-balanced across the LSPs used by the SDP according to the normalized LSP load-balancing weight configured using the load-balancing-weight command. This means that consecutive packets of a particular service use the same LSP, but the overall load handled by LSPs to the SDP far end is balanced according to the load-balancing weight if all services using the SDP send the same bandwidth and there are more services using the SDP than there are LSPs for the SDP.
If an LSP in the ECMP set has no load-balancing weight configured, ECMP is applied to packets based on the output of the hash for the service ID.
3.14. MPLS Service Usage
The 7705 SAR routers enable service providers to deliver virtual private networks (VPNs) and Internet access using Generic Routing Encapsulation (GRE), IP, and/or MPLS tunnels, with Ethernet and/or SONET/SDH interfaces.
3.14.1. Service Destination Points
A service destination point (SDP) acts as a logical way of directing traffic from one 7705 SAR router to another through a unidirectional (one-way) service tunnel. The SDP terminates at the far-end 7705 SAR router, which directs packets to the correct service egress service access point (SAP) on that device. All services mapped to an SDP use the GRE, IP, or MPLS transport encapsulation type.
For information about service transport tunnels, refer to the 7705 SAR Services Guide. Service transport tunnels can support up to eight forwarding classes and can be used by multiple services.
3.15. MPLS and RSVP-TE Configuration Process Overview
Figure 14 displays the process to configure MPLS and RSVP-TE parameters.
Figure 14: MPLS and RSVP-TE Configuration and Implementation Flow
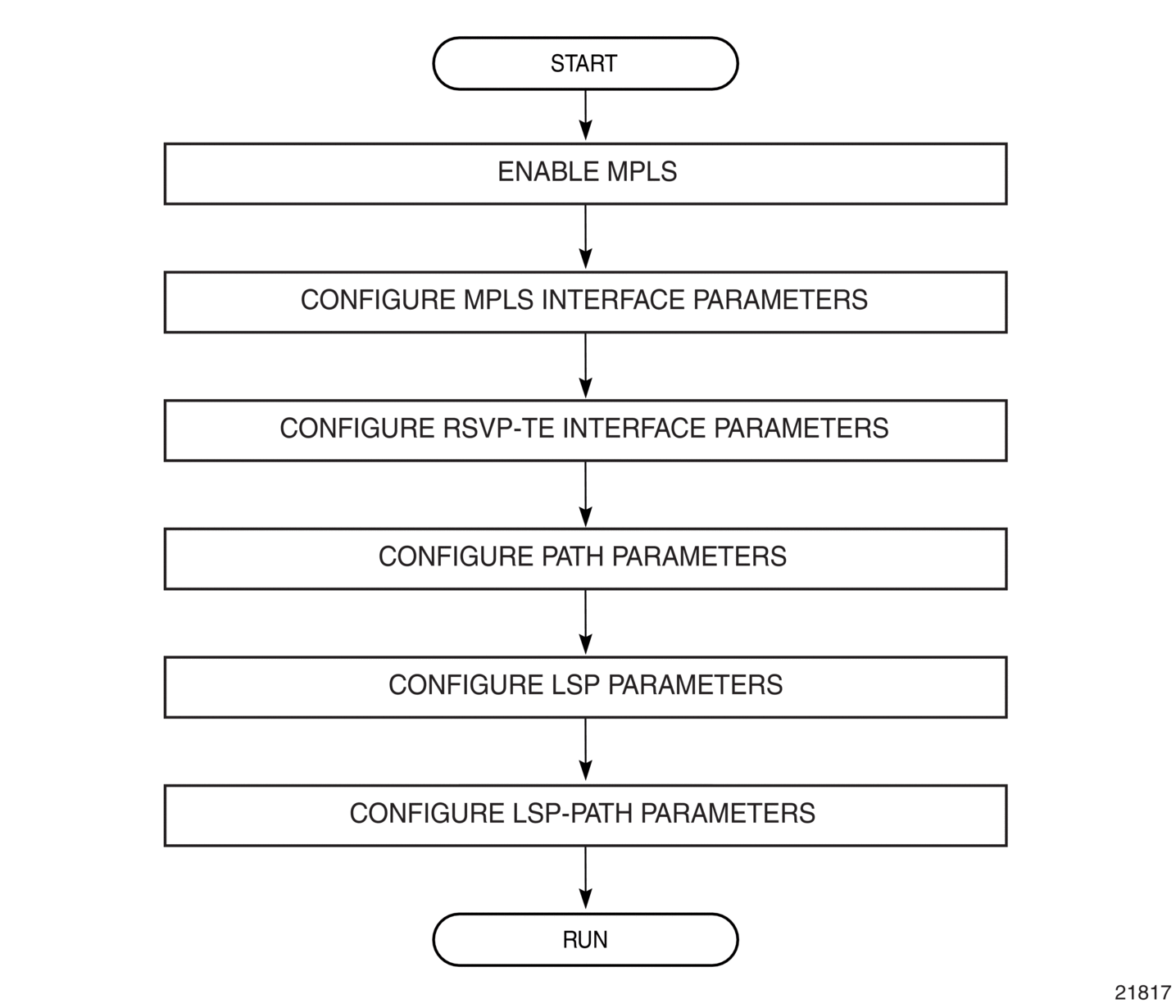
3.16. Configuration Notes
Network and system interfaces must be configured in the config>router>interface context before they can be specified in MPLS. Refer to the 7705 SAR Router Configuration Guide for interface configuration information.
This section describes MPLS and RSVP-TE guidelines and caveats.
- Interfaces must already be configured in the config>router>interface context before they can be specified in MPLS and RSVP.
- A router interface must be specified in the config>router>mpls context in order to apply it or modify parameters in the config>router>rsvp context.
- A system interface must be configured and specified in the config>router>mpls context.
- Paths must be created before they can be applied to an LSP.
- CSPF must be enabled in order for administrative groups and SRLGs to be relevant.
3.16.1. Reference Sources
For information on supported IETF drafts and standards, as well as standard and proprietary MIBs, refer to Standards and Protocol Support.