The IEEE 802.1x standard defines three participants in an authentication conversation (see Figure: 802.1x Architecture):
the supplicant — the end-user device that requests access to the network
the authenticator — controls access to the network. Both the supplicant and the authenticator are referred to as Port Authentication Entities (PAEs).
the authentication server — performs the actual processing of the user information
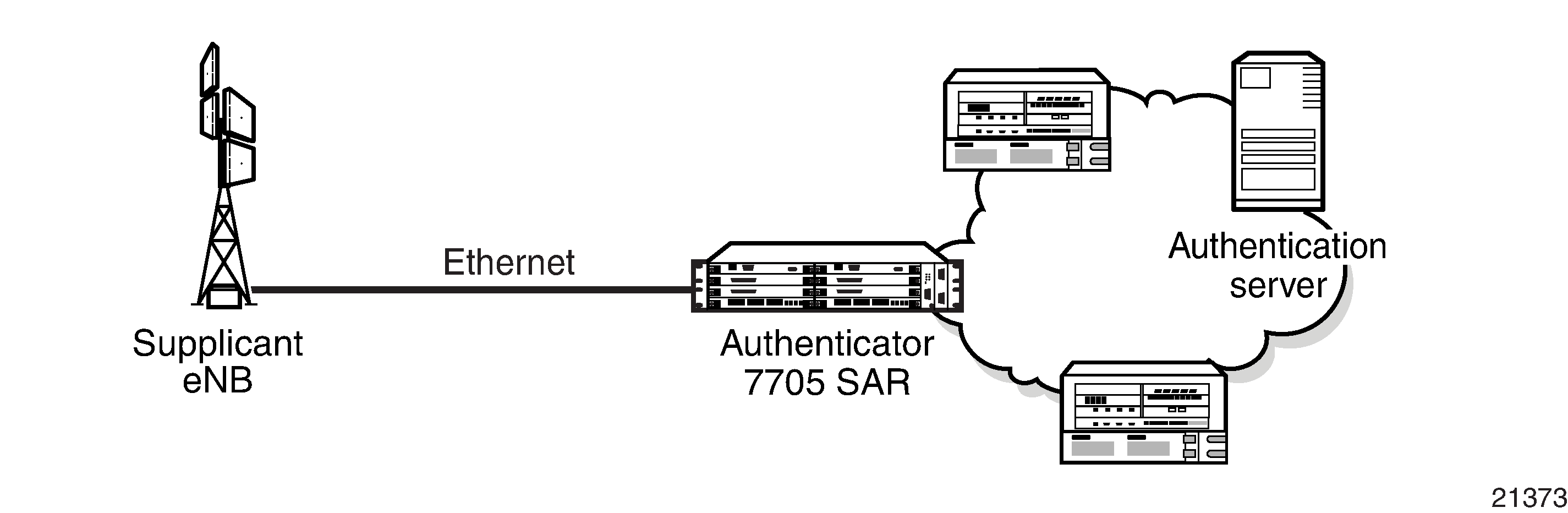
The authentication exchange is carried out between the supplicant and the authentication server; the authenticator acts only as a bridge. The communication between the supplicant and the authenticator is done using EAPOL. The communication between the authenticator and the authentication server is done using the RADIUS protocol. The authenticator is therefore a RADIUS client, and the authentication server is a RADIUS server.
Figure: Authentication Scenario shows an example of the messages transmitted during an authenticator-initiated One Time Password (OTP) authentication process.
OTP is one of many authentication mechanisms that are available for use between the supplicant and the authentication server. These authentication mechanisms (protocols) are transparent to the 7705 SAR.
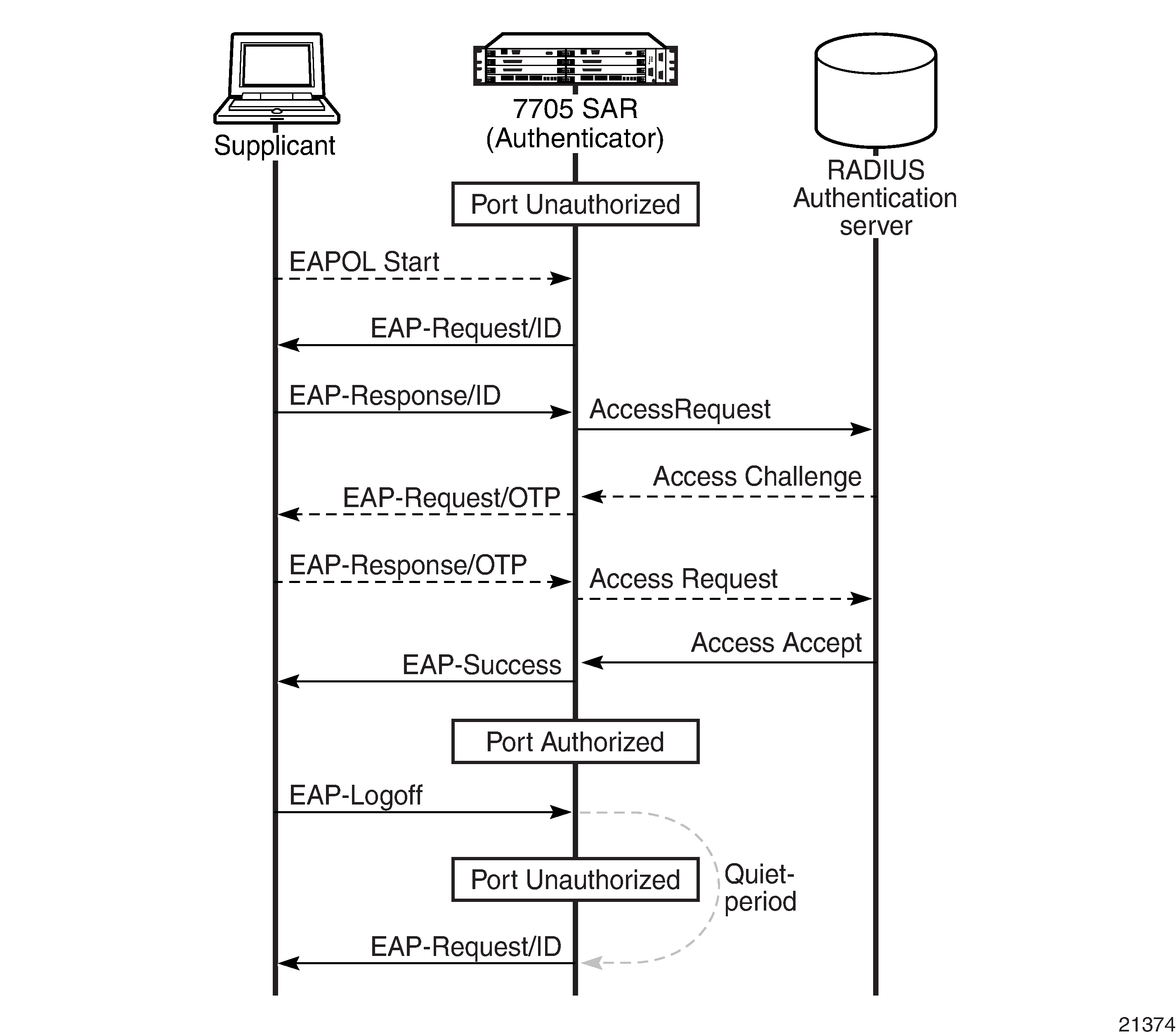
The authenticator initiates the procedure when the Ethernet port becomes operationally up by sending a special PDU called an EAP-Request/ID to the supplicant. The supplicant can also initiate the exchange by sending an EAPOL-start PDU if it does not receive the EAP-Request/ID frame during boot-up. The supplicant responds to the EAP-Request/ID with an EAP-Response/ID frame containing its identity (typically username + password).
After receiving the EAP-Response/ID frame, the authenticator encapsulates the identity information into a RADIUS Access Request packet, and sends it off to the configured RADIUS server. The RADIUS Access Request packet contains the following attributes:
User-Name – the name of the supplicant to be authenticated
Calling-Station-Id – the MAC address of the supplicant
NAS-IP-Address – the IP address of the device acting as the authenticator
NAS-Port – the physical port number of the device acting as the authenticator
State – allows state information to be maintained between the authenticator and the RADIUS server
EAP-Message – used to encapsulate EAP packets for transmission from the authenticator to the RADIUS server
Message-Authenticator – used to authenticate and protect the integrity of Access Request messages in order to prevent spoofing attacks
The RADIUS server checks the supplied credentials using an authentication algorithm to verify the supplicant’s identity. If approved, the RADIUS server returns an Access Accept message to the authenticator. The authenticator notifies the supplicant with an EAP-Success message and puts the port in the authorized state.
If the supplicant sends an EAP-Logoff message, the authenticator puts the supplicant in an unauthorized state and continues searching for supplicants to authenticate.
After sending an EAP-Failure message, the authenticator puts the supplicant in an unauthorized state, waits for the number of seconds defined by the quiet-period timer, then continues searching for supplicants to authenticate.
The 7705 SAR conforms to the relevant sections of the 802.1X-2001 implementation.