The SR OS supports the node-protect extensions to the TI-LFA algorithm as described in draft-bashandy-rtgwg-segment-routing-ti-lfa-05.
Figure 1 shows a simple topology to illustrate the operation of the node-protect in the TI-LFA Algorithm.
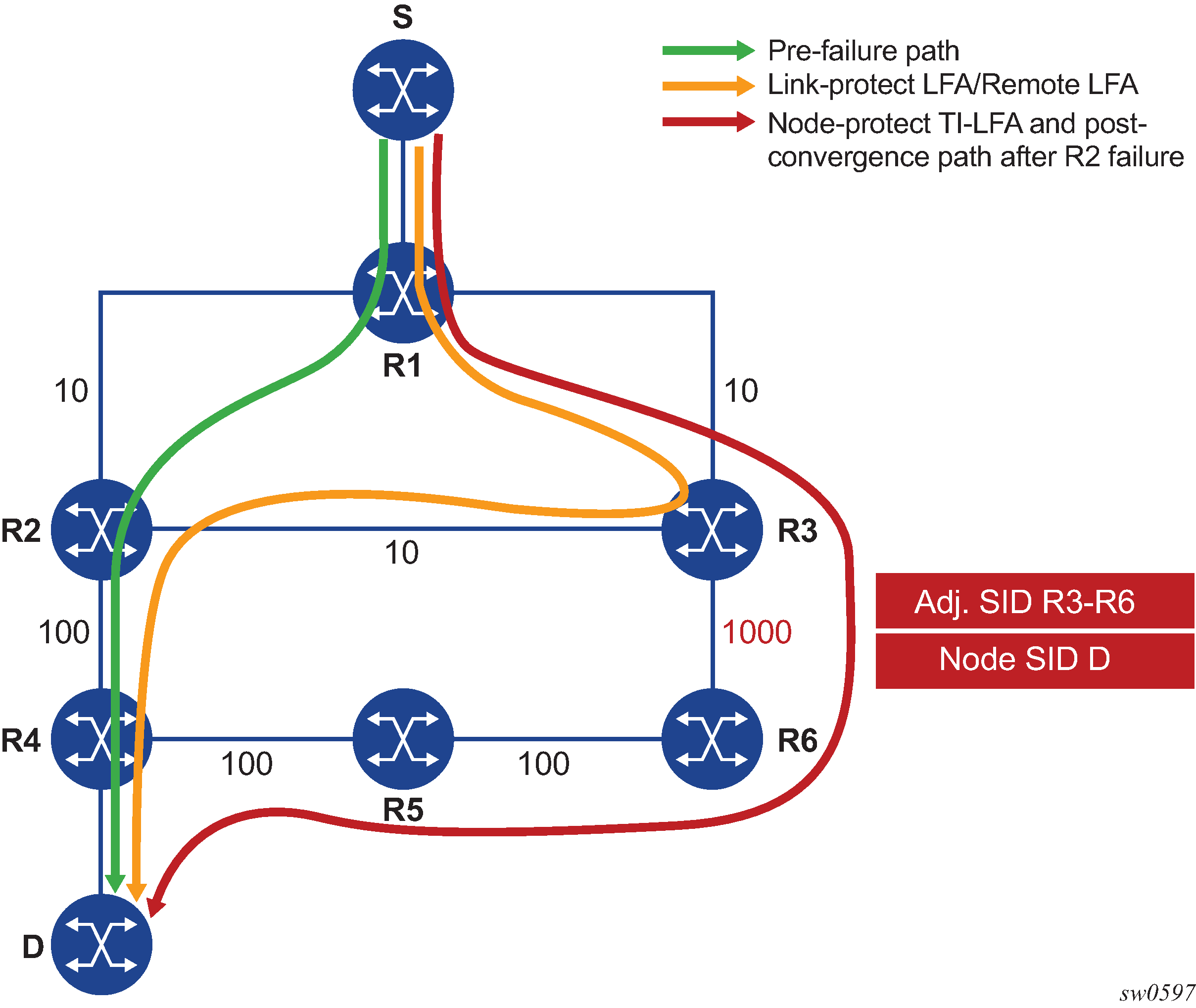
The first change is that the algorithm has to protect a node instead of a link.
The following topology computations pertain to Figure 1:
For each destination prefix D, R1 programs the TI-LFA repair tunnel (max-sr-frr-labels=1):
-
For prefixes other than those owned by node R2 and R3, R1 programs a node-protect repair tunnel to the P-Q pair R3-R6 by pushing the SID of adjacency R3-R6 on top of the SID for destination D and programming a next-hop of R3.
-
For prefixes owned by node R2, R1 runs the link-protect TI-LFA algorithm and programs a simple link-protect repair tunnel which consists of a backup next-hop of R3 and pushing no additional label on top of the SID for the destination prefix.
-
Prefixes owned by node R3 are not impacted by the failure of R2 since their primary next-hop is R3.