MACsec uses SAs for encryption of packets. SA is a security relationship that provides security guarantees for frames transmitted from one member of a CA to the others. Each SA contains a single secret key (SAK) where the cryptographic operations used to encrypt the datapath PDUs.
SAK is the secret key used by an SA to encrypt the channel.
When enabled, MACsec uses a static CAK security mode. Two security keys, a connectivity association key (CAK) that secures control plane traffic and a randomly-generated secure association key (SAK) that secures data plane traffic are used to secure the point-to-point or point-to-multipoint Ethernet link. Both keys are regularly exchanged between both devices on each end of the Ethernet link to ensure link security.
Figure 1 illustrates MACsec generating the CAK.
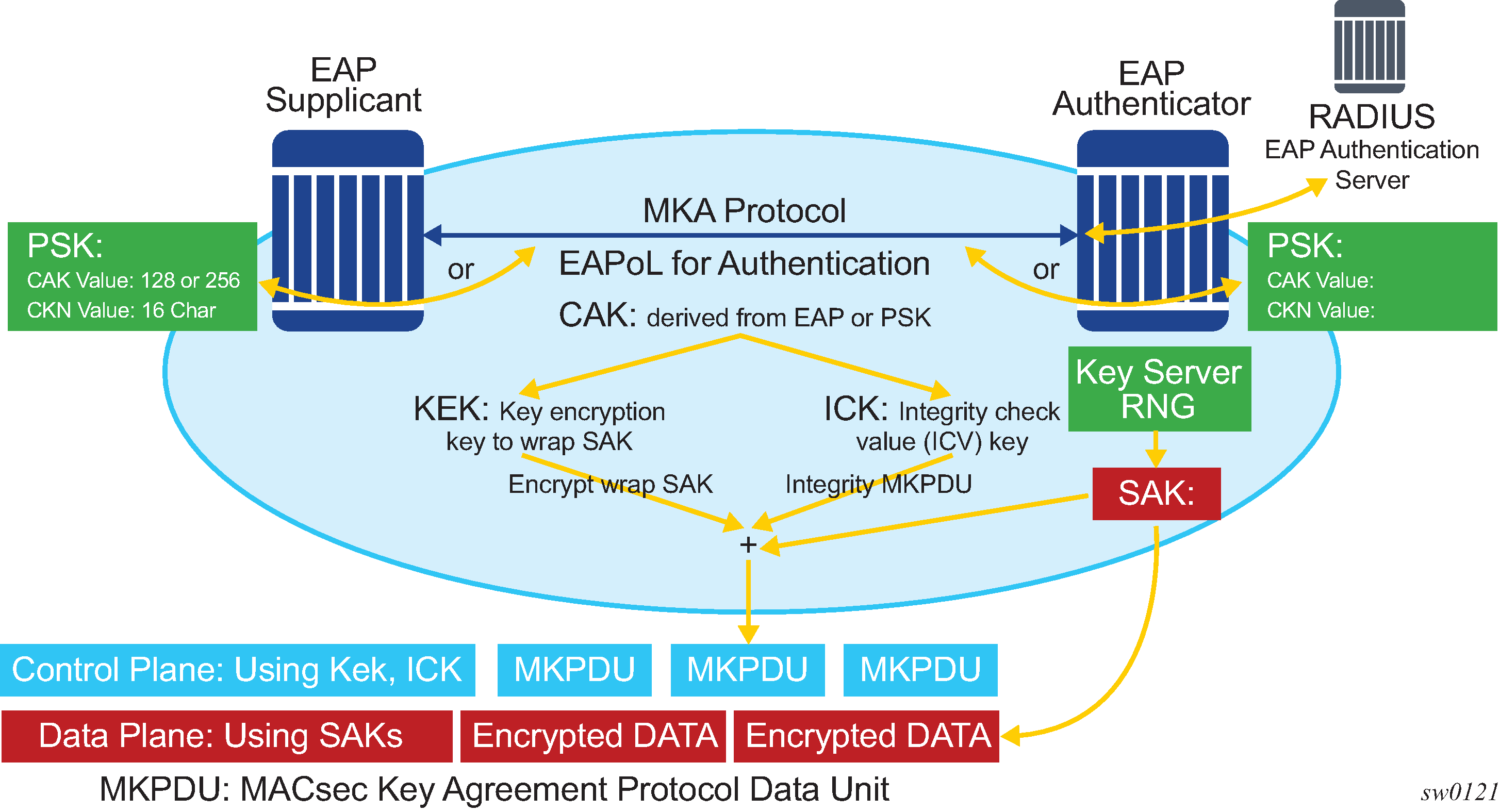
The node initially needs to secure the control planecontrol plane communication to distribute the SAKs between two or more members of a CA domain.
The securing of control plane is done via CAK. To generate the CAK, there are two main methods:
EAPoL (SR OS does not support EAPoL)
pre shared key (CAK and CKN values are configured manually via CLI). The following CAK and CKN rules apply.
CAK is a 32 hexadecimal characters for 128-bit key and 64 hexadecimal characters for 256-bit key depending on which algorithm is used for control planecontrol plane encryption (for example, aes-128-cmac or aes-256-cmac).
CKN is a 32 octets char (64 hex) and it is the connectivity association key name which identifies the CAK. This allows each of the MKA participants to select which CAK to use to process a received MKPDU. MKA places no restriction on the format of the CKN, except that it must comprise an integral number of octets, between 1 and 32 (inclusive), and that all potential members of the CA use the same CKN.
CKN and CAK must match on peers to create a MACsec Secure CA.
Figure 2 illustrates the MACsec control plane authentication and encryption.
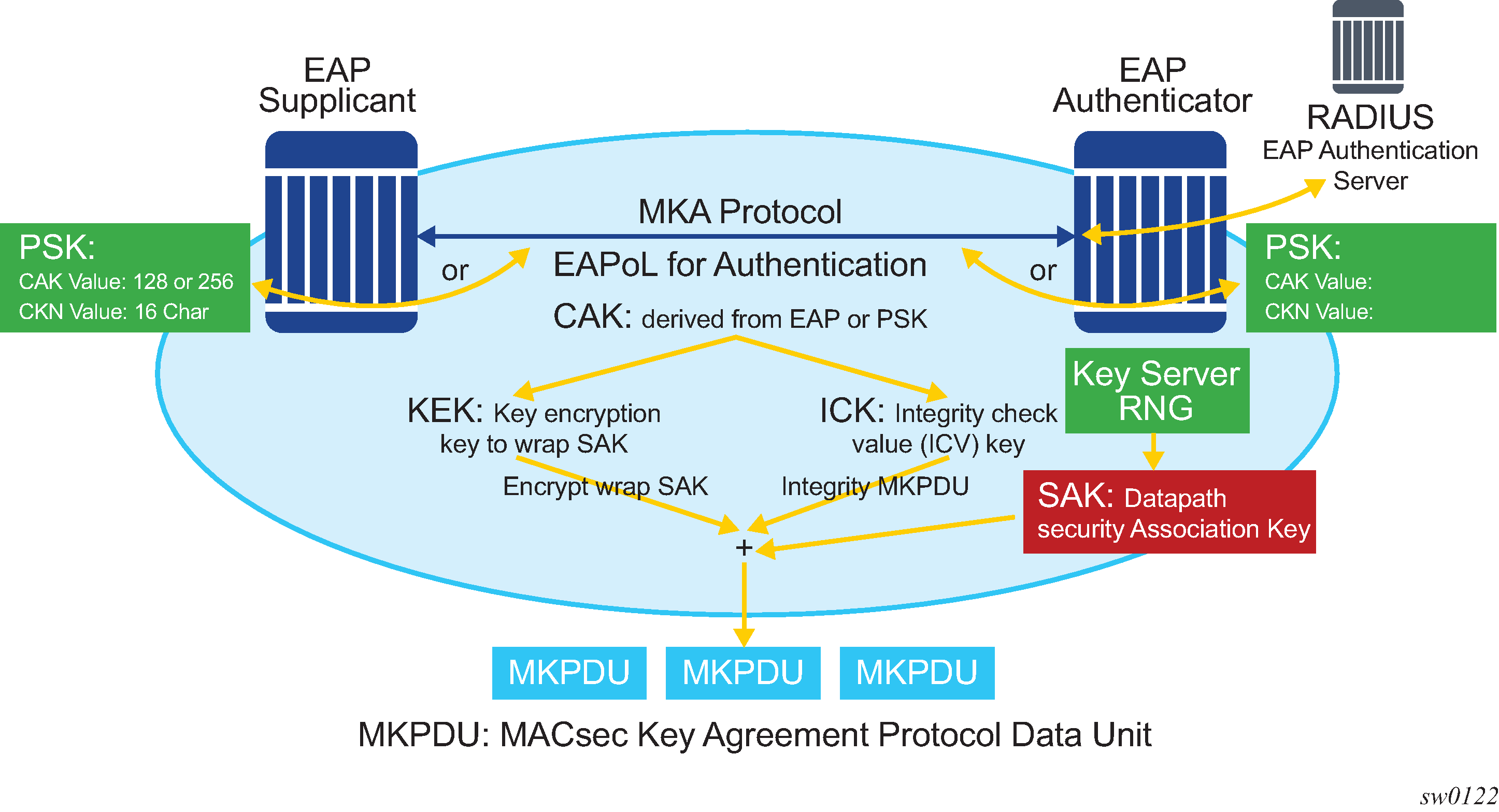
After the CAK is generated, it can obtain two other keys. These keys are:
Key Encryption Key (KEK) — used to wrap and encrypt the SAKs
Integrity Connection Value (ICV) Key (ICK) — used to for integrity check of each MKPDU send between two CA
The key server then creates a SAK, that is shared with the CAs of the security domain, and that SAK secures all data traffic traversing the link. The key server continues to periodically create and share a randomly-created SAK over the point-to-point link for as long as MACsec is enabled.
The SAK is encrypted via the AES-CMAC, the KEK as encryption key, and ICK as integration key.