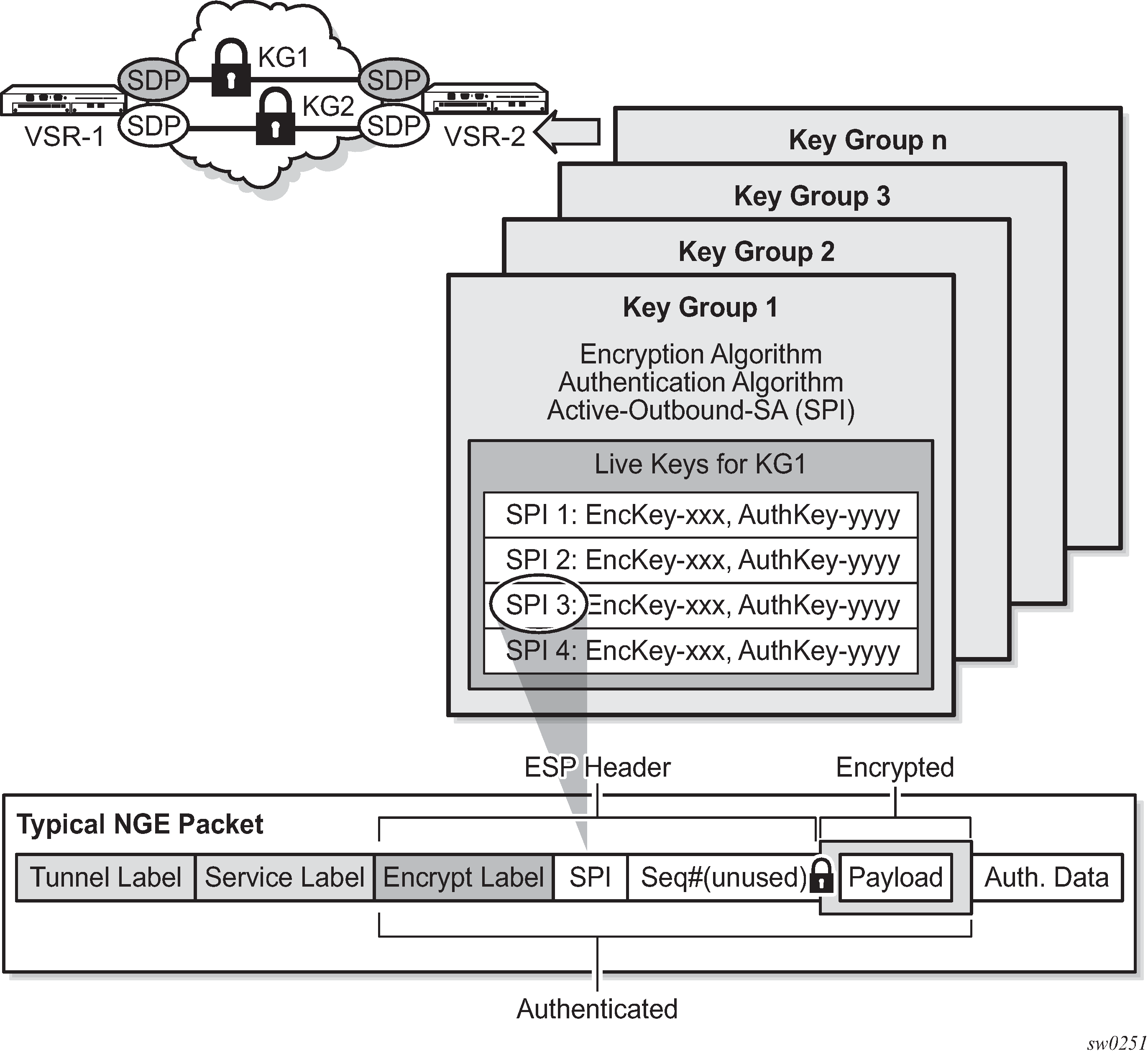
Users can partition the network based on security requirements by organizing encryption keys into distinct key groups. A key group contains the following elements:
an encryption algorithm (see Key group algorithms)
an authentication algorithm (see Key group algorithms)
a list of security associations (SAs) (see Security associations)
an active outbound SA (see Active outbound SA)
Figure: Key groups and a typical NGE packet illustrates the use of key groups (KGs), SAs, and security parameter indexes (SPIs). The VSR-1 and VSR-2 both have the same set of key groups configured. One path uses key group 1 (KG1) and the other uses key group 2 (KG2). Each key group contains the elements listed above. KG1 has four live keys, SPI_1 through SPI_4, and SPI_3 is the active outbound SA. The active outbound SA is identified by its SPI, and this SPI is embedded in the NGE packet.
Each SA listed in a key group, indexed by an SPI, specifies a single key for encryption and a single key for authentication. Packets transmitted or received that reference a particular SPI use the keys in the SA for that SPI when performing encryption and authentication.
Before enabling encryption, key groups must be configured on the node. Only after a key group is configured can it be assigned to an SDP or VPRN services.