gRPC communication between the client and server must be authenticated and encrypted. There are two types of authentication:
Authentication via session credentials
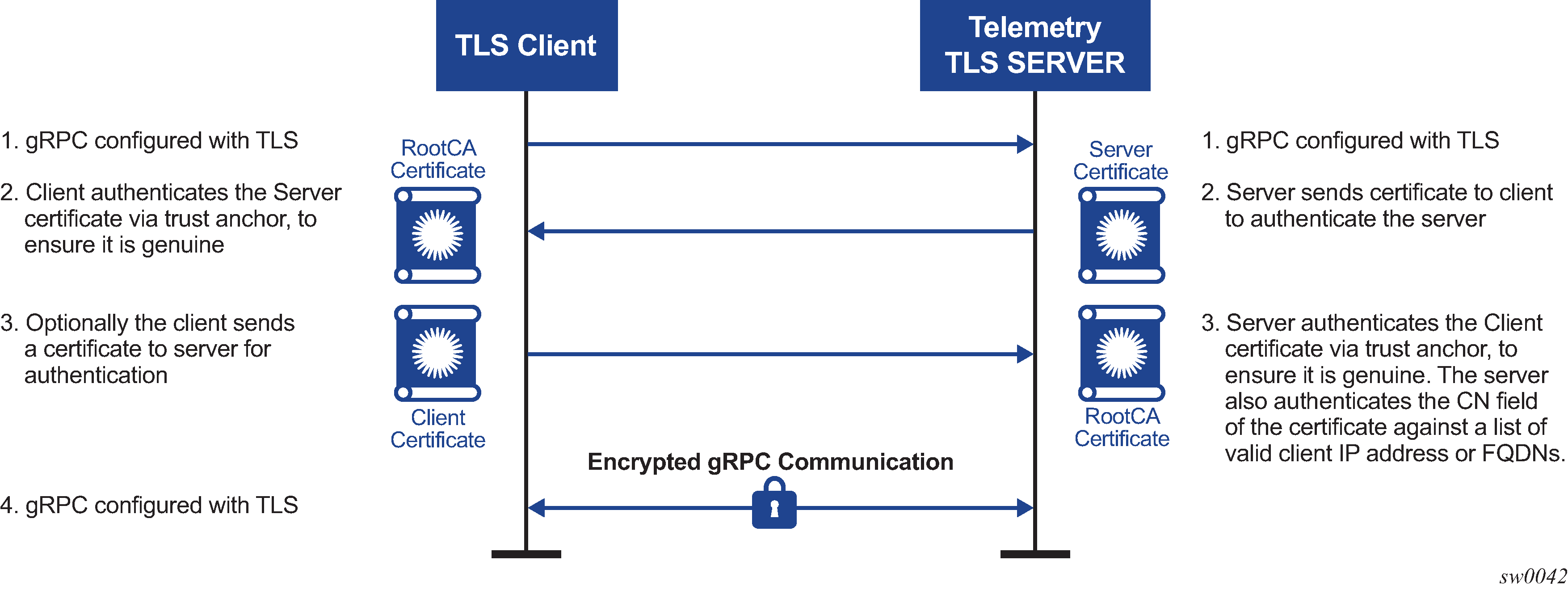
Session credentials operate similarly to device authentication, ensuring that the device is allowed in the network and is authorized by the provider. This type of authentication is performed using PKI and X.509.3 certificates. gRPC uses TLS for session authentication.
SR OS supports TLS servers for gRPC.
Authentication using channel credentials
Channel credentials use a username and password that are entered at the gRPC client terminal to authenticate gRPC packets using an AAA method.
Session authentication provides proof that the client and server are authorized devices and that they belong to the provider. After authentication, the session becomes encrypted using TLS, and gRPC PDUs are transmitted between the client and server.
Figure: Session authentication using TLS shows a basic session authentication using TLS.
Channel credentials use username and password authentication. Each gRPC channel packet can contain a username and a password. Authentication is done through standard SR OS authentication order and mechanisms. All current authentication methods, including local and AAA servers, are applicable to gRPC channels. In addition, all authentication orders currently used by Telnet or SSH are compatible with gNMI Call authentication.
Figure: gNMI call authentication using SR OS shows a basic gNMI Call authentication using SR OS.
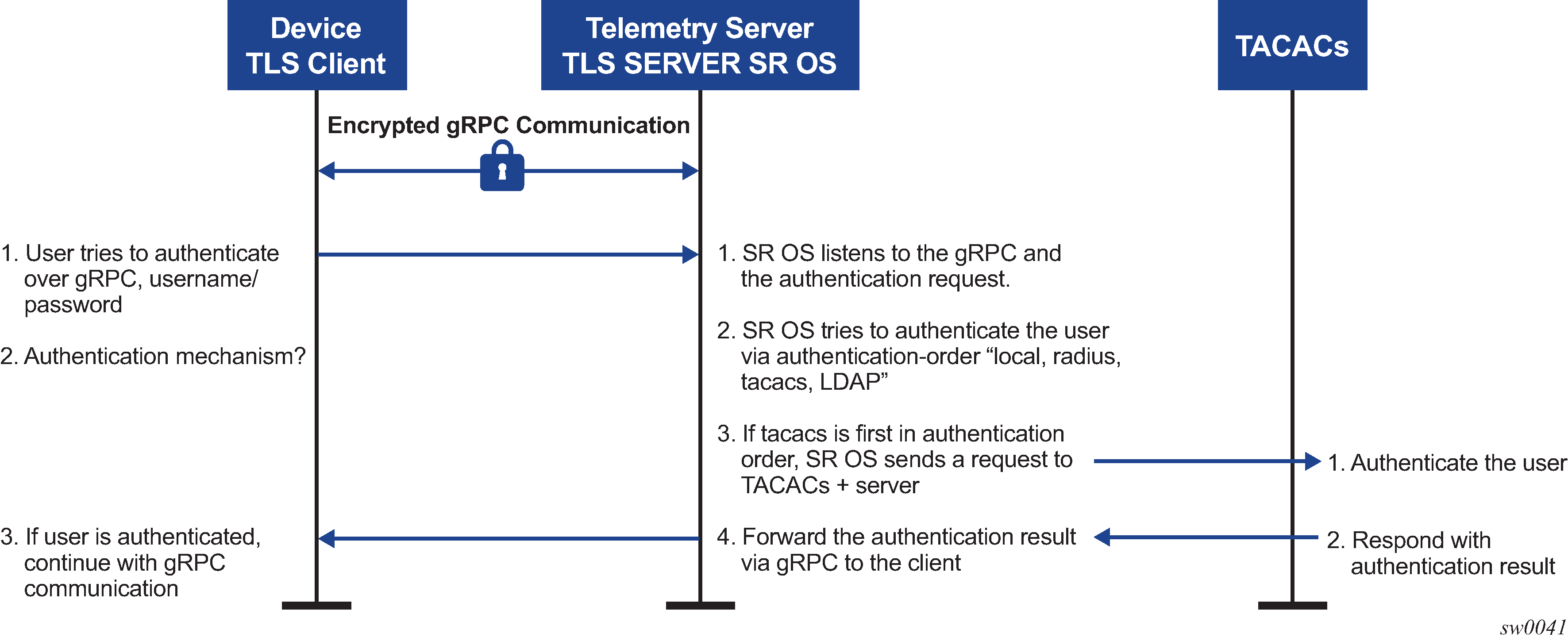
The gRPC channel packets contain the username and password in clear text, and are only encrypted using TLS. If a TLS server profile is assigned to the gRPC session, all PDUs between the server and client are encrypted. If TLS becomes operationally down, no gRPC PDUs are transmitted in clear text.
SR OS relies on existing authentication mechanisms for gRPC channels, including:
AAA servers and local authentication orders configured using the config>system>security>password>authentication-order command
password complexity rules
requiring the user to be configured as part of gRPC access by using the config>system>security>user>access>grpc command
disconnecting the gRPC session by using the admin>disconnect gNMI command
Note: The gRPC is not affected by the password aging.
Security profiles can authorize bulk get, set, and subscribe gRPC commands that are received by the server. Profiles can be configured to allow or deny specific gRPC commands; for example, a profile for one user can authorize get and set commands, while a profile for another user can authorize get commands only.