Figure: TLS handshake shows the TLS handshake.
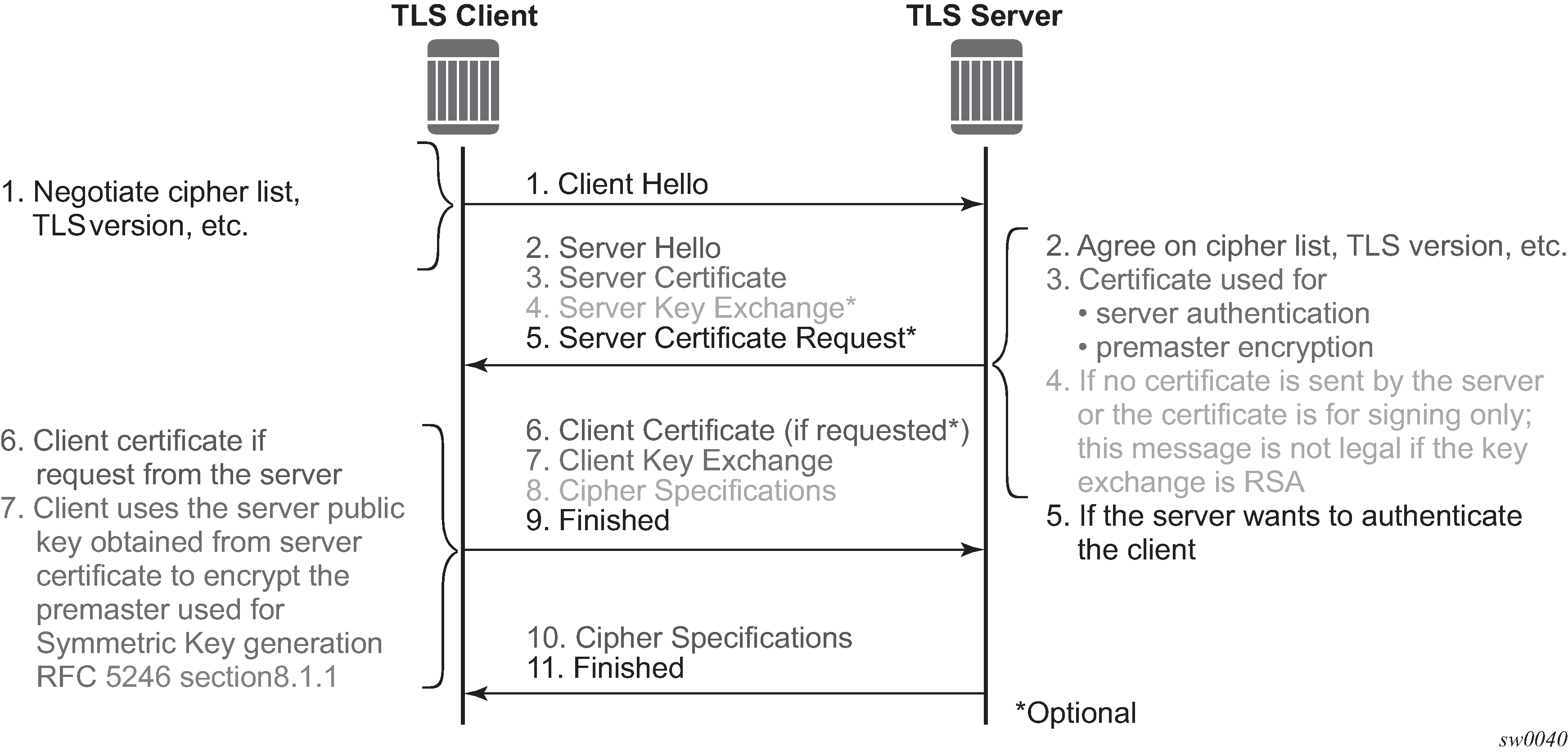
Table: TLS handshake step descriptions describes the steps in the TLS handshake.
| Step | Description |
|---|---|
1 |
The TLS handshake begins with the client Hello message. This message includes the cipher list that the client wants to use and negotiate, among other information. |
2 |
The TLS server sends back a server Hello message, along with the first common cipher found on both the client cipher list and the server cipher list. This agreed cipher is used for data encryption. |
3 |
The TLS server continues by sending a server certificate message, where the server provides a certificate to the client so that the client can authenticate the server identity. The public key of this certificate (RSA key) can also be used for encryption of the symmetric key seed that is used by the client and server to create the symmetric encryption key. This occurs only if the PKI is using RSA for asymmetric encryption. |
4 |
Server key exchange is not supported by SR OS. SR OS only uses RSA keys; Diffie-Hellman key exchange is not supported. |
5 |
The server can optionally be configured to request a certificate from the client to authenticate the client. |
6 |
If the server has requested a certificate, the client should provide a certificate using a client certificate message. If the client does not provide a certificate, the server drops the TLS session. |
7 |
The client uses the server public RSA key that was included in the server certificate to encrypt a seed used for creating the symmetric key. This seed is used by the client and server to create the identical symmetric key for encrypting and decrypting the data plane traffic. |
8 |
The client sends a cipher spec to switch encryption to this symmetric key. |
9 |
The client successfully finishes the handshake. |
10 |
The server sends a cipher spec to switch encryption to this symmetric key. |
11 |
The server successfully finishes the handshake. |
After a successful handshake, TLS is operationally up, and applications can then use it for application encryption.