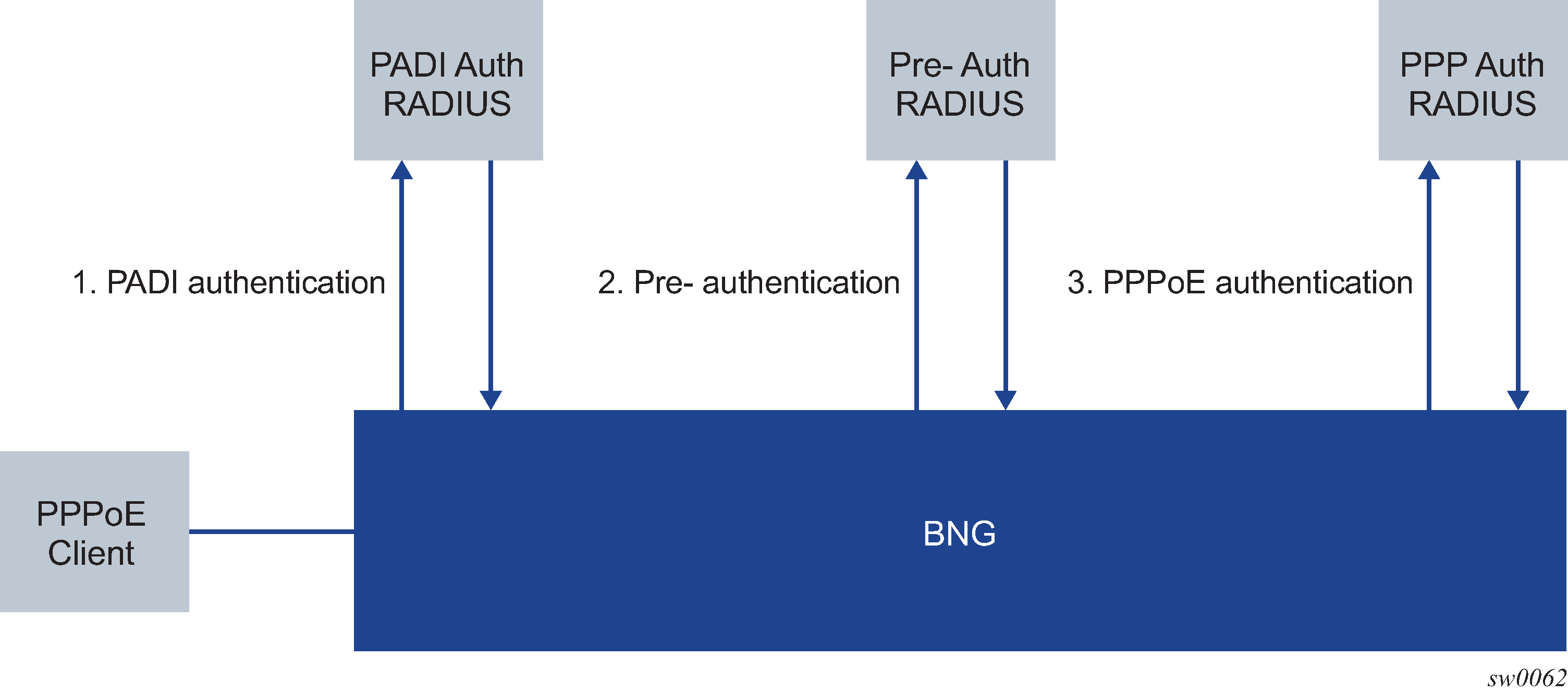
The PADI Authentication Policy feature enables PADI authentication that retrieves MSAP parameters before pre-authentication and PPPoE authentication.
With this feature, authentication occurs in the following manner.
PADI authentication and MSAP authorization:
A capture SAP receives a PPPoE PADI packet.
A check verifies that the LUDB is configured as pppoe-user-db on the capture SAP.
The LUDB must be configured on the capture SAP. Without the LUDB specified, the existing functionality is performed for MSAP creation.
The LUDB host entry is matched to the entry that has the PADI authentication policy.
RADIUS authentication and MSAP authorization occurs.
An MSAP is created if the authentication policy is not configured for PAP/CHAP.
(Optional) LLID pre-authentication:
Look up the LLID pre-authentication policy under the LUDB host entry.
Perform RADIUS pre-authentication to obtain an LLID.
LCP authentication and L2TP tunnel authorization:
Trigger RADIUS authentication defined by the authentication policy configured in the LUDB host entry in the previous step.
Create the MSAP, finish the LCP authentication with the PPP client, and establish an L2TP tunnel/session.
Figure: Triple authentication with MSAP authentication policy shows triple authentication with MSAP authentication policy.
The CLI command config>subscr-mgmt>loc-user-db>ppp>host>padi-auth-policy configures a PADI authentication policy used for PADI authentication with MSAP authorization as shown in the CLI example below:
configure
subscriber-mgmt
local-user-db ‟ludb-1” create
ppp
host ‟default” create
padi-auth-policy ‟padi_auth”