This section describes the Nokia router acting as a Broadband Subscriber Aggregator (BSA).
In the TPSDA solutions, the Nokia 5750 Subscriber Services Controller (SSC) serves as the policy manager, DHCP and RADIUS server.
In this application, one of the required functions can be to authenticate users trying to gain access to the network. While sometimes the DHCP server (an SSC) can perform authentication, in most cases a RADIUS server (an SSC) is used to check the customer's credentials.
See the DHCP Management section for information about DHCP and DHCP Snooping.
For information about the RADIUS server selection algorithm, see the 7450 ESS, 7750 SR, 7950 XRS, and VSR System Management Guide.
If authentication is enabled, the router temporarily holds any received DHCP discover message and sends an access-request message to a configured RADIUS server containing the client's MAC address or circuit-ID (from the Option 82 field) as the username. If access is granted by the RADIUS server, the router then forwards or relays the DHCP discover message to the DHCP server and allows an IP address to be assigned. If the RADIUS authentication request is denied, the DHCP message is dropped and an event is generated.
A typical initial DHCP scenario (after client bootup) is shown in Figure: Initial DHCP scenario.
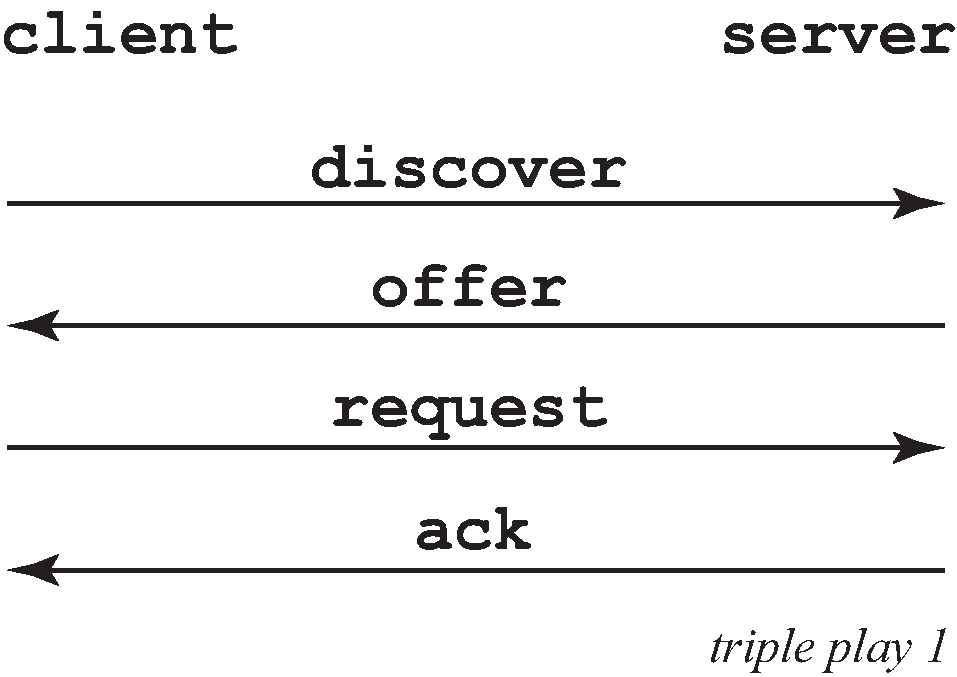
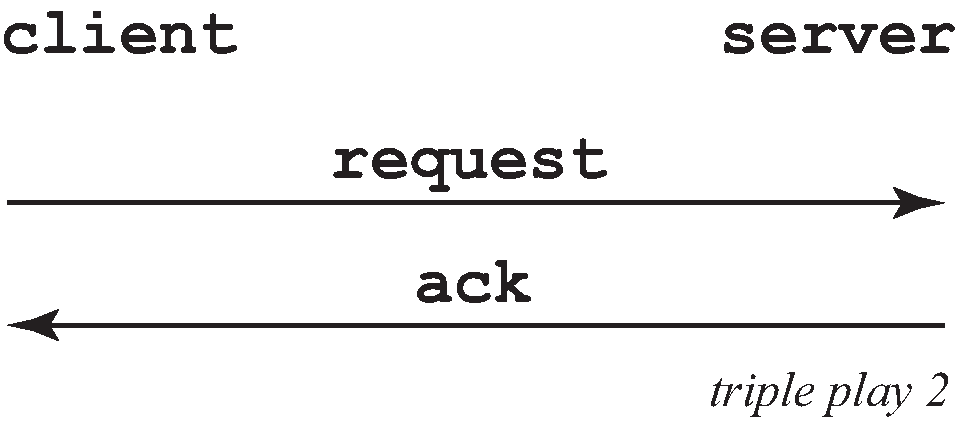
But, when the client already knows its IP address (when an existing lease is being renewed), it can skip straight to the request/ack phase, as shown in Figure: DHCP scenario with known IP address.
In the first scenario, the DHCP discover triggers an authentication message to RADIUS and the DHCP request also triggers RADIUS authentication. The previous reply is cached for 10 seconds, the second DHCP packet does not result in a RADIUS request.
In the second scenario, the DHCP request triggers an authentication message to RADIUS.
If the optional subscriber management authentication policy re-authentication command is enabled, DHCP authentication is performed at every DHCP lease renew request. Only dynamic DHCP sessions are subject to remote authentication. Statically provisioned hosts are not authenticated.