The system keeps track of the number of PPPoE sessions active on a specific SAP and assign a per SAP session index to each such that always the lowest free index is assigned to the next active PPPoE session. When PAP/CHAP RADIUS authentication is used, the PPPoE SAP session index can be sent to, and received from, the RADIUS server using the following VSA:
ATTRIBUTE Alc-SAP-Session-Index 180 integer
This is supported for all PPPoE sessions, including those using LAC and LNS, but is not supported in a dual-homing topology. It should only be used in a subscriber per VLAN model as the session index is per SAP.
The SAP session index allows PPPoE sessions to have their own set of queues for QoS and accounting purposes when using the same SLA profile name as that received from a RADIUS server. An example of this with multiple levels of HQoS egress scheduling is shown in Figure: Egress QoS per PPPoE session. Alternatively, this can be achieved by configuring per-session SPI sharing in the SLA profile as described in SLA Profile Instance Sharing.
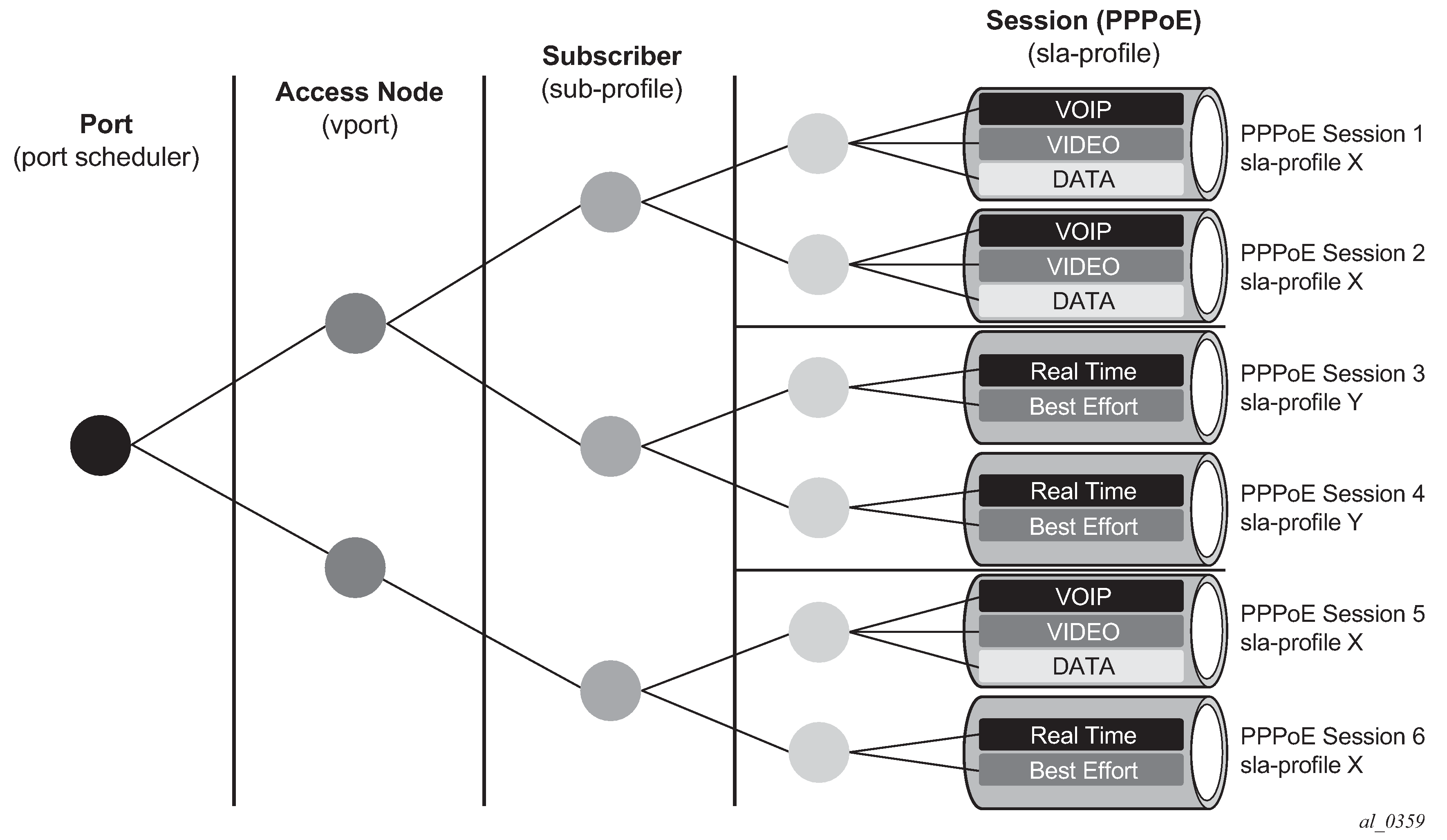
This requires a set of identical SLA profiles to be configured which only differ by an index being, for example, appended to their name. The SAP session index must be sent to RADIUS in the Access-Request message, which is achieved by configuring the RADIUS authentication policy to include it as follows:
Example:
configure subscriber-mgmt authentication-policy name
include-radius-attribute
[no] sap-session-index
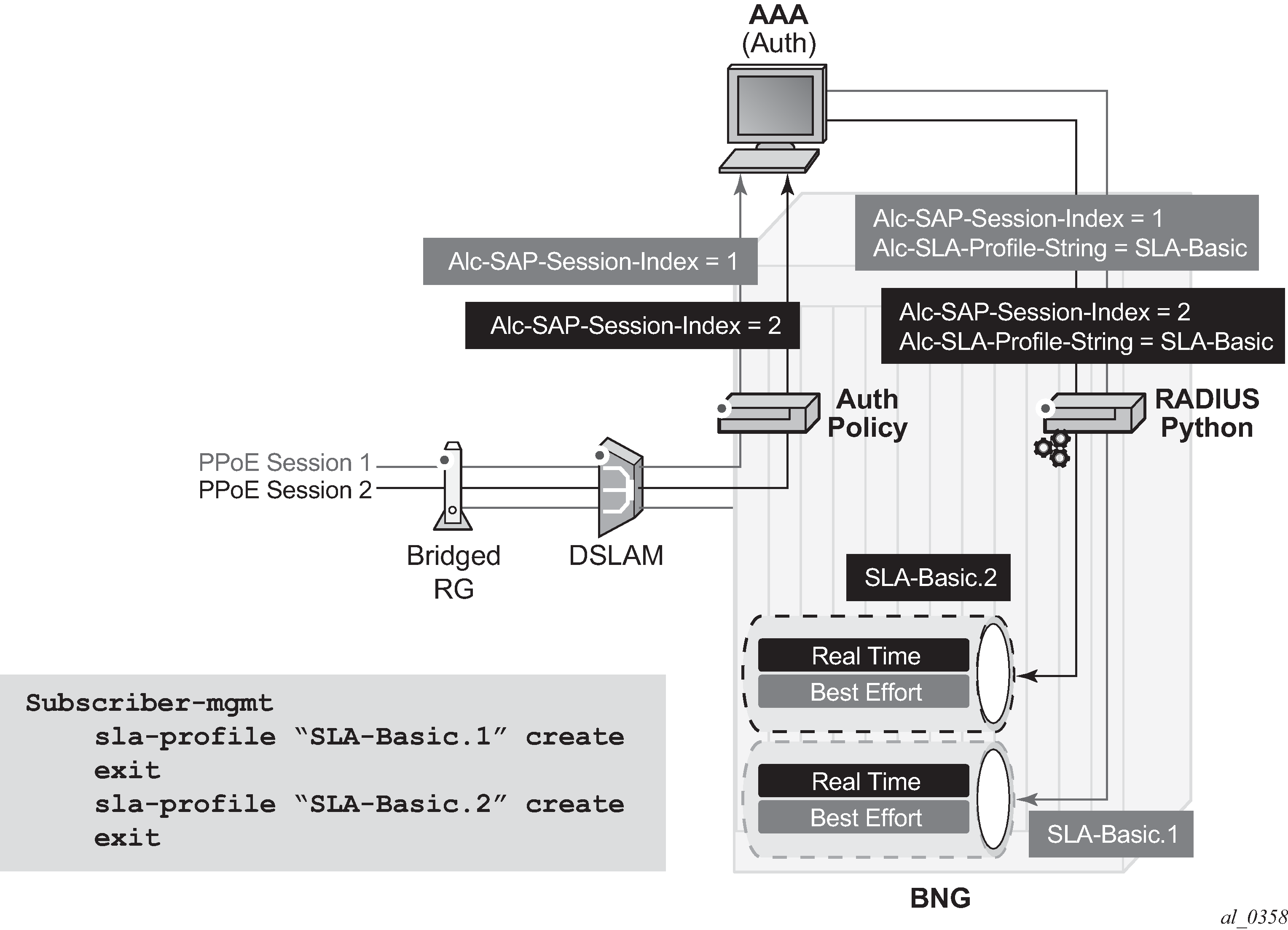
The RADIUS server must then reflect the SAP session index back to the system in the RADIUS Access-Accept message together with the SLA profile name.
A Python script processes the RADIUS Access-Accept message to append the SAP session index to the SLA profile name to create the unique SLA profile name, in this example with the format:
sla-profile sla-profile-name.suffix
The exact format (for example, the separator used) is not fixed and merely needs to match the pre-provisioned SLA profiles, while not exceeding 16 characters. This ensures that each PPPoE session is provided its own SLA profile and consequently its own set of queues.
This processing is shown in Figure: Per PPPoE session SLA profile selection.
Below is an example Python script for this purpose:
import alc
import struct
from alc import radius
from alc import sub_svc
PROXY_STATE = 33
ALU = 6527
SLA_PROF_STR = 13
SAP_SESSION_INDEX = 180
##################################
## QoS for Multiple PPPoE Sessions
# This script checks if a sap-session-
index (sid) is included in the authentication
# accept. If present, the sla-profile-string (sla) is adapted to "sla.sid"
if alc.radius.attributes.isVSASet(ALU,SLA_PROF_STR):
sla = alc.radius.attributes.getVSA(ALU,SLA_PROF_STR)
if alc.radius.attributes.isVSASet(ALU,SAP_SESSION_INDEX):
ssi = alc.radius.attributes.getVSA(ALU,SAP_SESSION_INDEX)
suffix = "" .join(["%x" % ord(x) for x in ssi])
alc.radius.attributes.setVSA(ALU,SLA_PROF_STR,sla + '.' + "%d" %
int(suffix,16))
To use a CoA to change the SLA profile used, the new SLA profile name must be constructed with the same suffix (in this example) as that used for the current SLA profile. This is necessary to ensure unique use of a specifically provisioned SLA profile. This mandates that the SAP session index is included in the CoA information. Two options are proposed to achieve this:
The CoA can specify a new SLA profile name and include the SAP session index. A Python script would then process the CoA and construct the new SLA profile name to be used by appending the suffix in the same way as was done with the RADIUS Access-Accept.
The CoA could be using a RADIUS proxy which may make the first option unattractive. An alternative solution would be to use a Python script to append the suffix to the acct-session-id in all messages sent so that the suffix can be identified when a CoA is received that uses the acct-session-id(+suffix) for session identification. This would need to be performed for all messages sent that include the acct-session-id. CoAs would reference the session using the acct-session-id+suffix. A Python script would be required to remove the suffix and append it to the new SLA profile name. All messages received with the acct-session-id+suffix would be processed by the Python script to remove the suffix before sending the acct-session-id to the system.
To ensure that the acct-session-id sent in RADIUS accounting messages is updated with the suffix, the user must configure include-radius-attribute sla-profile in the RADIUS accounting policy to be applied. The Python script needs to remove the suffix from the SLA profile and add it to the acct-session-id for all messages sent. Clearly, the acct-session-id used by any external server would then be different to that seen on the system.