Figure: Policy structure shows the relationship between the AA system components used to identify applications and configure AA-related capabilities. Each ID-related component is defined as follows:
protocol signatures
application filters
applications
application groups
charging groups
flow attributes
Figure: Policy structure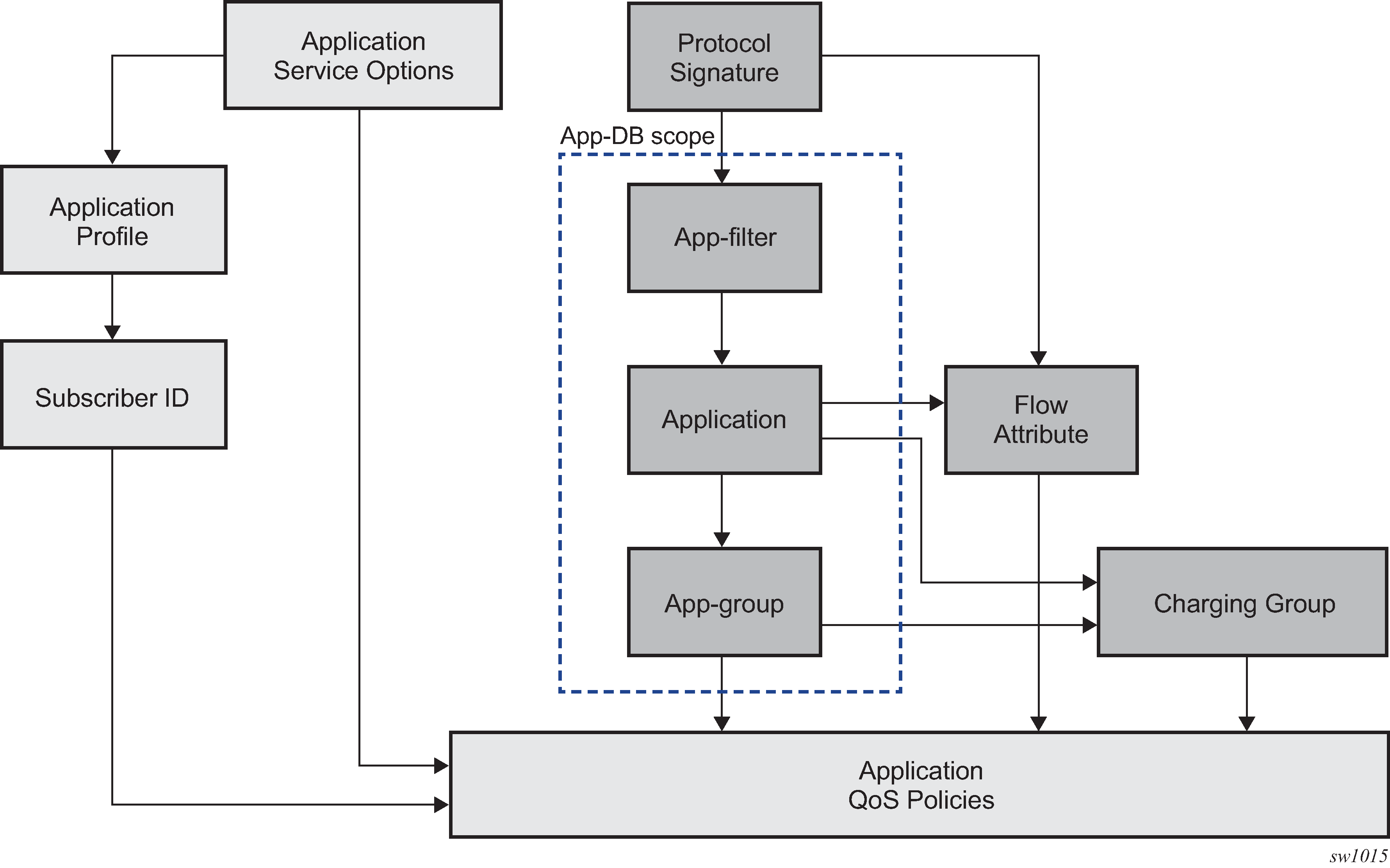
Table: AA classification elements provides an overview of how those various components are used in AA to recognize types of flows and sessions.
| Term | Definition | Examples |
|---|---|---|
Protocol Signature |
Nokia’s proprietary component of AA flow identification provided as part of AA S/W load to identify protocols used by clients. Where a protocol is defined as an agreed upon format for transmitting data between two devices. |
Tftp, iMap, msn-msgr, RTP, emule, http_video, bittorrent, SIP. Nokia’s protocol signatures do not rely on IP port numbers to identify a TCP/UDP port based protocols and applications to avoid eliminate false-positives but allow operators to define application filters if a port-based identification is deemed adequate (see an example below). |
Application Filter |
Operator configurable, optional component of AA flow identification that uses any combination of protocol signatures, server IP address and port, flow set-up direction, configurable expressions (for example an HTTP string match) to identify user’s traffic. |
http_video + IP address of partner’s video server or http_video + an HTTP string to identify partner’s video content TCP or UDP + TCP/UDP port number to identify a TCP or UDP based protocol or application. |
Application |
Operator configurable, optional component of AA flow identification that allows defining any specific forms of traffic to and from end user clients by combining application filter entries |
Google Talk, POP3, YouTube, iTunes, Shoutcast. |
Application Charging Group |
Operator configurable, optional component of AA flow identification that allows grouping of similar end use applications using operator defined names and groups. |
IM, Mail, Multimedia, P2P, Tunneling, Web, Other. |
Clients |
End user programs that generate user traffic for applications and protocols, and that are used in a process of AA flow identification verification. |
The list of clients is constantly evolving as new clients or versions are introduced in the marketplace. The following example illustrates clients that may be used to generate Application traffic matching BitTorrent application defined using BitTorrent and DHT protocol signatures: Limewire, BitTorrent, Azureus, Ktorrent, Transmission, Utorrent. |
Flow attributes |
Nokia-provided algorithms based on machine learning, which assign flow attribute confidence levels to all traffic flows, whether encrypted or not. The attribute results may be used for analytics or control purposes. |
video, audio, download, upload, abr_service, encrypted, esni, real_time_communication |