Wireless network operators rely on the GPRS Tunneling Protocol (GTP) for the delivery of mobile data services across the access network. GTP is not designed to be secure and is exposing the mobile access network to risk from both its own subscribers and its partners' networks attacks.
While roaming is essential to mobile operators, it comes with its own additional unique security risks when providing connectivity to roaming partners’ networks and the end customers.
Figure: S5/S8/Gn/Gp AA firewall deployment shows the S5/S8/Gn/Gp AA Firewall deployment.
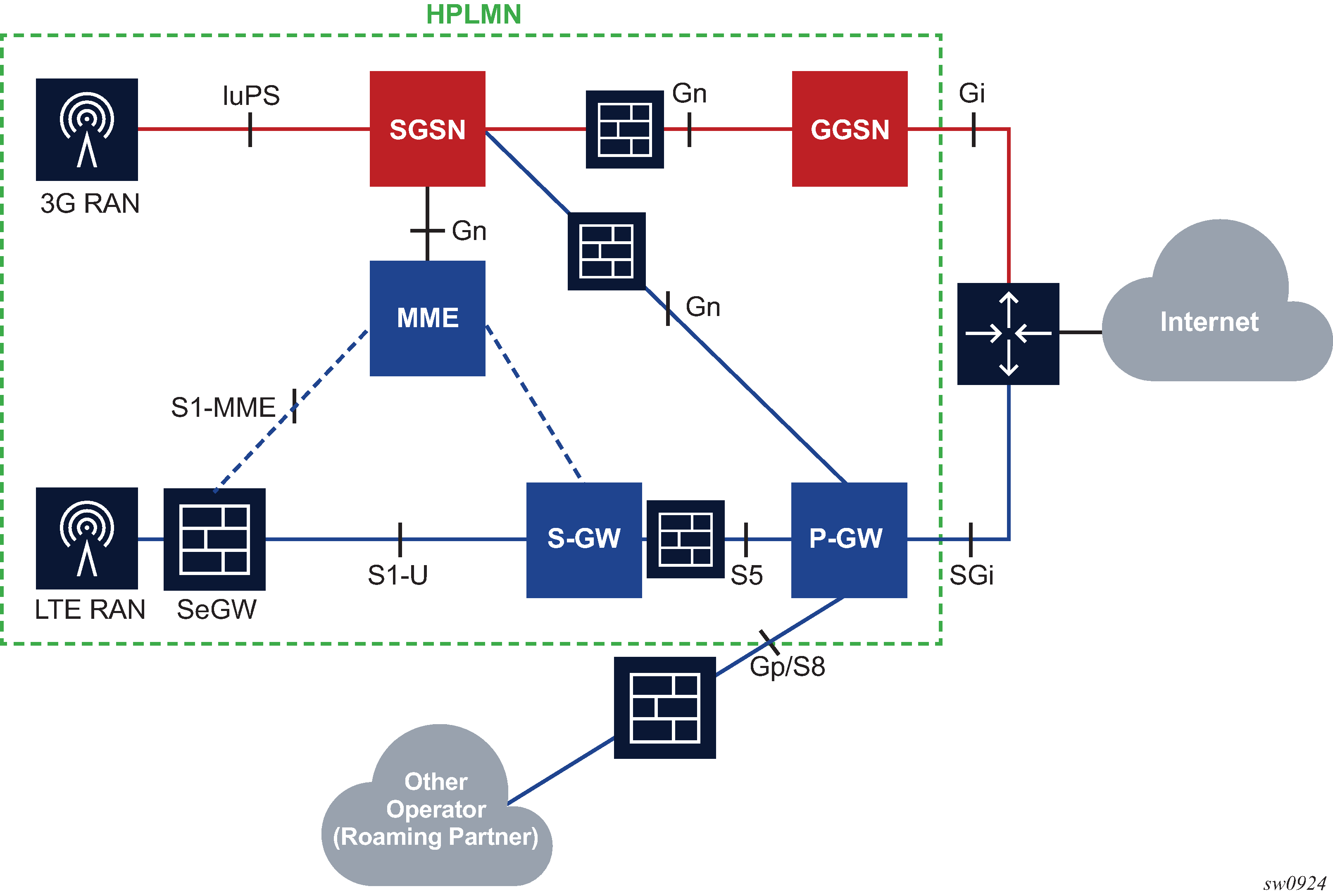
AA is deployed as a GTP firewall on S8/Gp (or S5/Gn) interfaces either as part of the 7750 SR router in the form of the AA-ISA hardware module or as a separate Virtual SR (VSR) appliance. The AA firewall provides network security features, such as:
GTP protocol validation (checks for anomaly attacks that involve malformed, corrupt, or spoofed traffic):
header length checks
IE length validation
invalid reserved field validation
reserved information elements validation
missing mandatory information elements validation
out of state message/information elements validation (GTPv1-c only)
sequence number validation
TEID validation (blocks GTP tunnel creations that have not been signaled correctly)
GGSN/PGW and SGSN/SGW redirection protection
GTP-in-GTP check
handover control to prevent session hijacking
source address—UE – anti-spoofing protection
protection against unauthorized Public Land Mobile Network (PLMN) access and unauthorized APN access by filtering based on APN, International Mobile Station Identity (IMSI) prefix, GTP src IP address prefix list
protection against unsupported GTP message types by filtering messages based on message type and message length
protection against flooding attacks:
GTP traffic bandwidth policing (limits the GTP bandwidth from a roaming partner’s SGSN or SGW)
GTP tunnel limiting (limits the number of concurrent GTP tunnels and the setup rate of these tunnels from a roaming partner’s SGSN or SGW)
protection against IP fragmentation-based attacks by using drop rules for IP fragmentation of GTP messages
AA FW supports GTPv1 and GTPv2.