The selection of the NAT pool and the outside routing context is performed through the NAT policy. Multiple NAT policies can be used within an inside routing context. This feature effectively allows selective mapping of the incoming traffic within an inside routing context to different NAT pools (with different mapping properties, such as port-block size, subscriber-limit per pool, address-range, port-forwarding-range, deterministic vs non-deterministic behavior, port-block watermarks, and so on) and to different outside routing contexts. NAT policies can be configured:
via filters as part of the action nat command
via routing with the destination-prefix command within the inside routing context
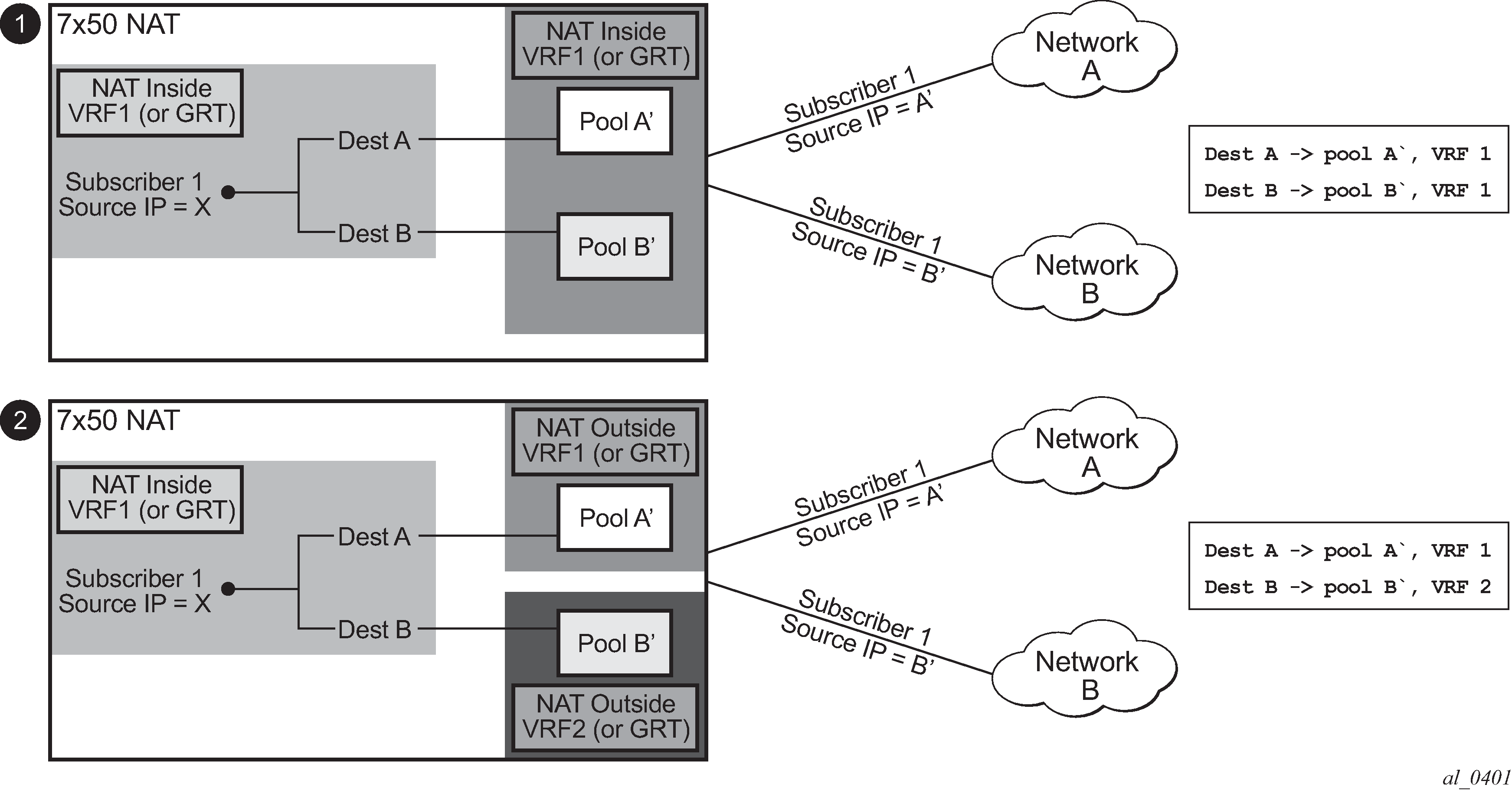
The concept of the NAT pool selection mechanism based on the destination of the traffic via routing is shown in Figure: Pool selection based on traffic destination.
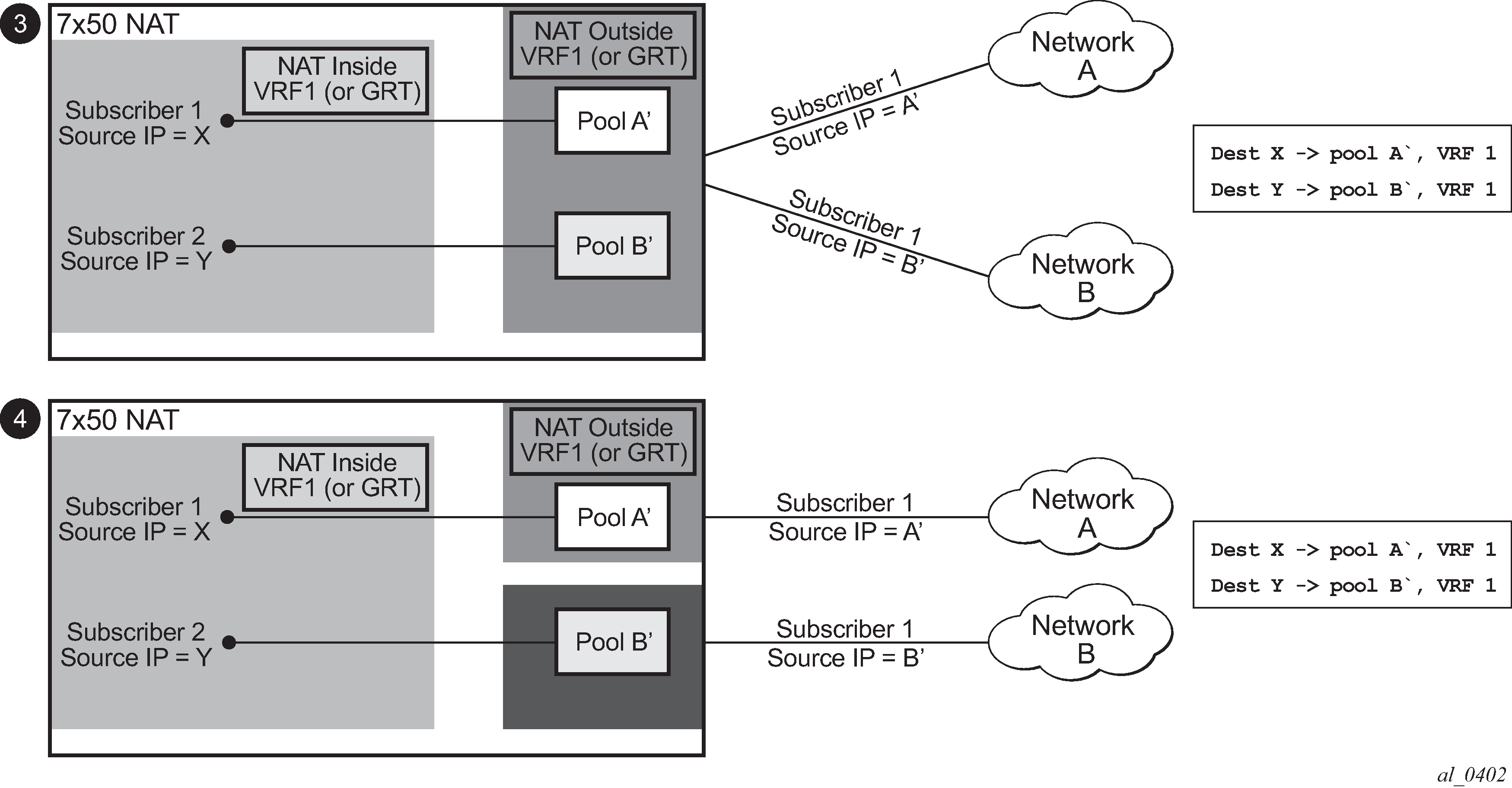
Diversion of the traffic to NAT based on the source of the traffic is shown in Figure: NAT pool selection based on the inside source IP address.
Only filter-based diversion solution is supported for this case. The filter-based solution can be extended to a 5 tuple matching criteria.
The following considerations must be taken into account when deploying multiple NAT policies per inside routing context:
The inside IP address can be mapped into multiple outside IP addresses based on the traffic destination. The relationship between the inside IP and the outside IP is 1:N.
In case where the source IP address is selected as a matching criteria for a NAT policy (or pool) selection, the inside IP address always stays mapped to the same outside IP address (relationship between the inside IP and outside IP address is, in this case, 1:1)
Static Port Forwards (SPF); each SPF can be created only in one pool. This means that the pool (or NAT policy) must be an input parameter for SPF creation.