Static steering to LSN44 is based on the destination-prefix command with a statically-configured routing prefix in an inside routing context (VPRN or GRT). This static route points to an ISA or VM-ISA. In transit from the inside routing context to the outside routing context, frames must be redirected through an ISA or VM-ESA where NAT is performed.
If there are multiple ISA or VM-ESAs in a NAT group, an internal LAG per NAT group is used with member ports connected to each ISA or VM-ESA. Upstream traffic is load-balanced between the ISAs or VM-ESAs based on the source IP addresses or prefixes.
The CLI configuration used for static steering to LSN44 is shown in Figure: Basic CLI for NAT where a NAT policy containing a pool name and the outside routing context acts as a bond between the inside routing context and the outside routing context. A destination-prefix without an explicitly configured NAT policy uses a default NAT policy. As shown in Figure: Basic CLI for NAT, the prefix 192.168.1.0/24 is mapped to nat-policy cgn2.
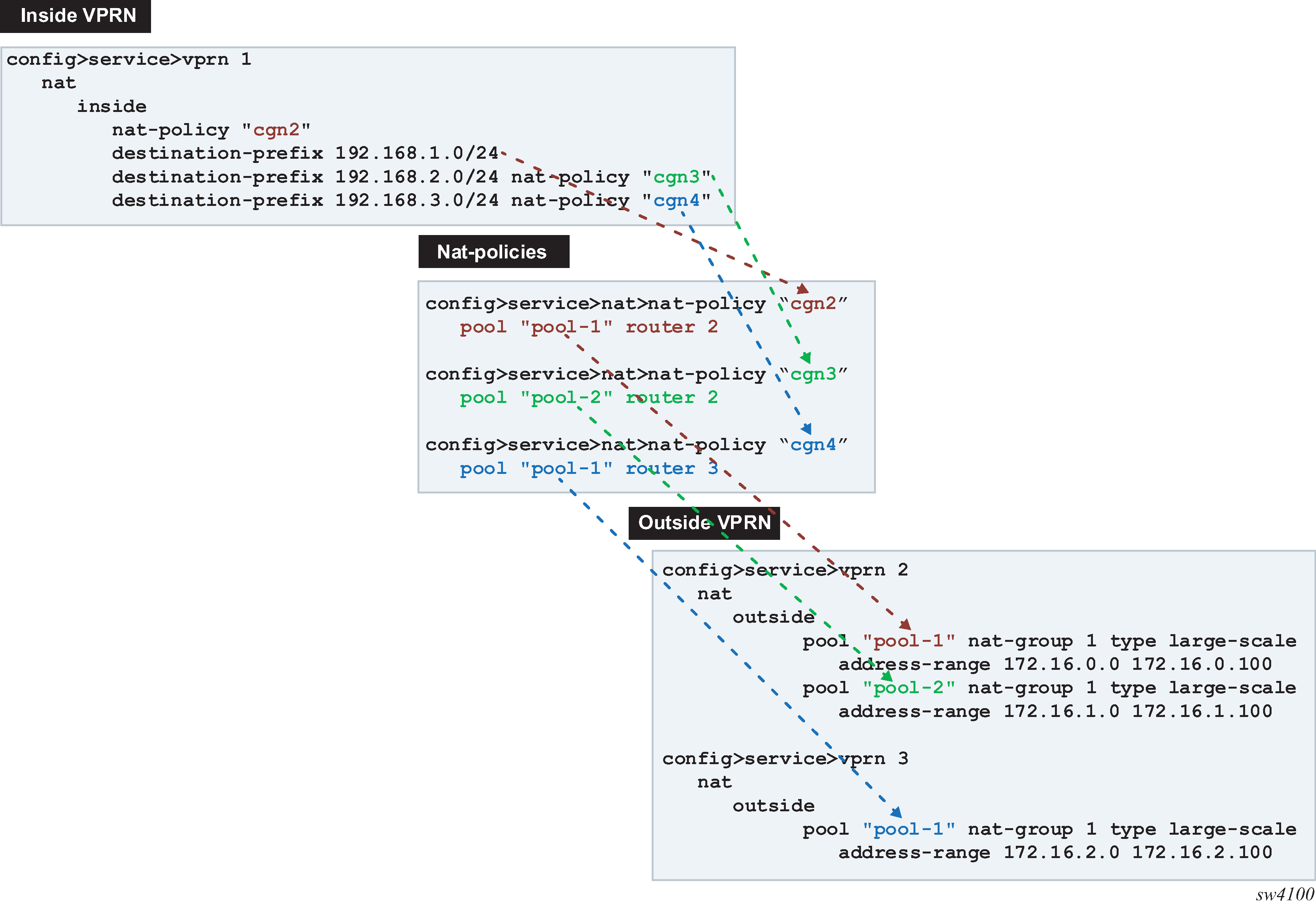
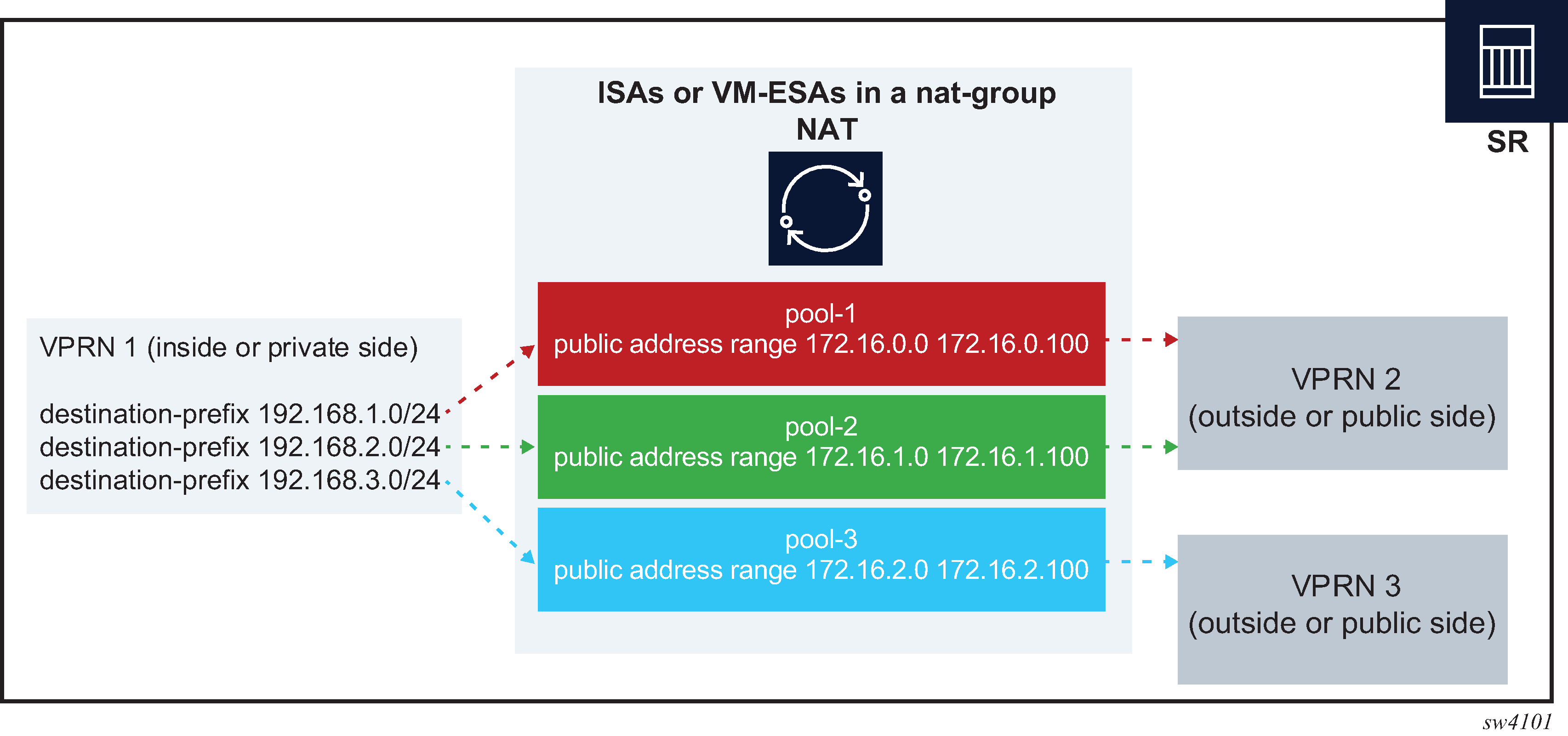
Figure: Logical representation of NAT routing through SR displays the logical configuration.
In the routing table, the ISA or VM-ESA next hops for NAT destination prefixes are shown as NAT inside semantics and the listed static routes belong to protocol NAT, as shown in the following example:
show router 1 route-table
===============================================================================
Route Table (Service: 1)
===============================================================================
Dest Prefix[Flags] Type Proto Age Pref
Next Hop[Interface Name] Metric
-------------------------------------------------------------------------------
192.168.1.0/24 Remote NAT 05d15h21m 0
NAT inside 0
192.168.2.0/24 Remote NAT 05d15h21m 0
NAT inside 0
192.168.3.0/24 Remote NAT 05d15h21m 0
NAT inside 0
When forwarding in the downstream direction (in the public to private direction), the outside address ranges (NAT pool ranges 172.16.x.x, as shown in the following example) are subdivided (micronetted) and distributed on a more granular level across the ISAs and VM-ESAs in the same NAT group. The micronetting is necessary so that traffic can be distributed across ISAs or VM-ESAs. The micronets are visible in the routing table and their next hops point to the corresponding ISA or VM-ESA. Micronets are used to attract traffic toward the ISAs or VM-ESAs in the downstream direction. An example of the route table on the outside (public side) is shown in the following output:
show router 3 route-table
===============================================================================
Route Table (Router: Base)
===============================================================================
Dest Prefix[Flags] Type Proto Age Pref
Next Hop[Interface Name] Metric
-------------------------------------------------------------------------------
172.16.2.0/28 Remote NAT 05d15h32m 0
NAT outside to mda 1/2 0
172.16.2.16/28 Remote NAT 05d15h32m 0
NAT outside to mda 2/2 0
172.16.2.32/28 Remote NAT 05d15h32m 0
NAT outside to mda 1/2 0
172.16.2.48/28 Remote NAT 05d15h32m 0
NAT outside to mda 2/2 0
172.16.2.64/28 Remote NAT 05d15h32m 0
NAT outside to mda 1/2 0
172.16.2.80/28 Remote NAT 05d15h32m 0
NAT outside to mda 2/2 0
172.16.2.96/31 Remote NAT 05d15h32m 0
NAT outside to mda 1/2 0
172.16.2.98/31 Remote NAT 05d15h32m 0
NAT outside to mda 2/2 0
172.16.2.100/32 Remote NAT 05d15h32m 0
NAT outside to mda 1/2 0