AA provides a URL filtering mechanism, as an alternative to ICAP, that is used to provide content filtering. Similar to the ICAP-based solution, web-service URL classification can be used to restrict opt-in users from accessing specific (configurable) URL categories. But in contrast to the ICAP-based solution, the decision is made by the AA. There is no involvement by an external element. Nokia has partnered with a leading URL categorization service provider to help provide the categorization; however, Nokia provides the end-to-end service. The operator does not need to integrate with any third party server; all communication between the AA and the URL categorization database is transparent to the operator.
The URL categorization database contains tens of millions of URLs and is constantly being updated. Along with the categorization of new URLs, the database is also updated with malicious URLs. Operators are therefore able to offer protection against phishing and spam, and other similar sites.
Apart from enabling the operator to restrict content to opt-in users, web-service URL classification provides access to the Internet Watch Foundation (IWF) List. The IWF List contains websites which host the physical or sexual abuse of children. Using the Web-service URL classification, operators can restrict access to those sites. The IWF list is updated in real-time, so the list is always up-to-date.
Using the web-service URL classification, operators can offer the following:
- parental control
- typically offered as an opt-in service; restricts users from accessing URLs categorized as, for example, drugs, gambling, violence, and weapons
- security and threat protection
- blocks URLs categorized as compromised or phishing/fraud
- IWF
- blocks sites belonging to the IWF list (mandated by law in several countries)
The URL categorization database is hosted on the Cloud. The DNS service ensures that the AA always connects to the fastest server, ensuring minimum latency. In addition, AA implements a cache containing URLs and their categories. The vast majority of categorization requests are served by the cache and do not affect the user experience.
Figure: AA URL categorization displays a high level diagram of URL categorization in AA.
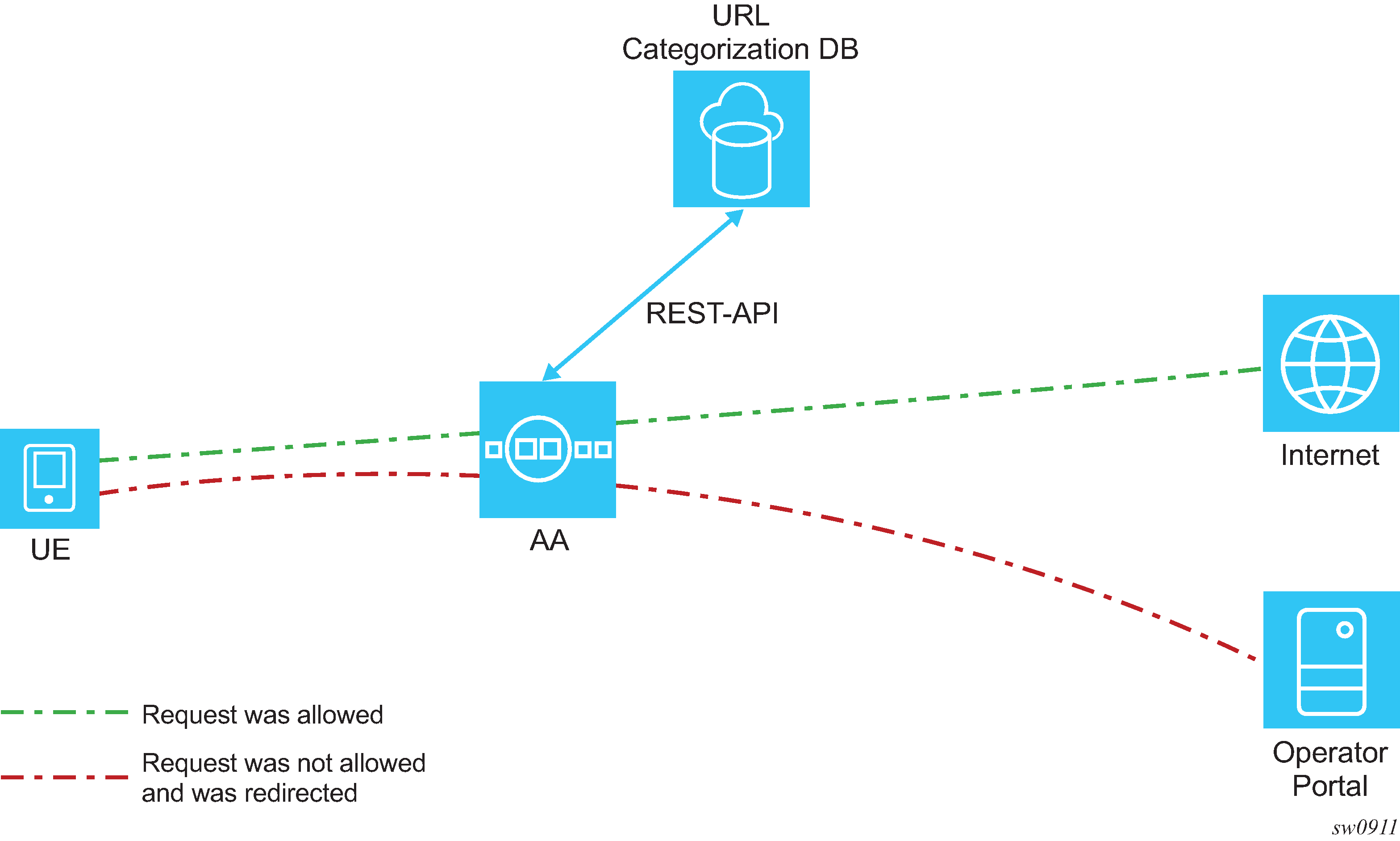
For every HTTP, HTTPS, HTTP2c, or QUIC request an opt-in user makes, AA first checks if the category of the requested URL is available in the cache. If available, AA checks if that category is allowed for the subscriber and acts accordingly.
If the request is not present in the cache, AA makes a Rest-API call to the URL categorization database and asks for the URL’s category. After the AA receives the response, the AA decides whether the request should be allowed or redirected.
The AA removes user-identifiable data before sending the URL to the categorization database. As an example, if the user requests ‟http://www.service.com/request.php?client=123”, the AA sends the following URL for categorization: ‟http://www.service.com/request.php”.
When the response from the URL categorization database arrives after the web server’s reply, the AA is always a restrictive filter; that is, AA always blocks the traffic in a way similar to the ICAP-based solution. This ensures that operators are never in breach of contract and a late URL categorization response does not result in a website displayed to the user.
The operator can define up to eight profiles containing categories. Using ASOs, a profile is mapped to a user and defines which URL categories are not allowed for that user.
The operator can manually set the category of a hostname to one of the supported categories. This is used in cases where the Categorization database has categorized a hostname as "Unknown" and operator either knows the category or a hostname has been misclassified. In either case, the operator must contact Nokia and request reclassification of the hostname.
Table: Example URL category profile shows three example profiles with different levels of restriction. The high-level profile example is the most restrictive profile. The medium-level profile is less restrictive and contains moderate category blocking. The low-level profile contains only a few URL categories to block.
| High | Medium | Low |
|---|---|---|
IWF List |
IWF List |
IWF List |
Phishing/Fraud |
Phishing/Fraud |
Phishing/Fraud |
Spyware and Malicious Sites |
Spyware and Malicious Sites |
Spyware and Malicious Sites |
Illegal Drugs |
Illegal Drugs |
— |
Violence |
Violence |
— |
Weapons |
Weapons |
— |
Nudity |
— |
— |
Alcohol |
— |
— |
Criminal Skills/Hacking |
— |
— |
Hate Speech |
— |
— |
Profiles can be modified at any time. Profiles can be dynamically mapped to users using PCRF/AAA.
Web-service URL Filtering is supported both for HTTP (using the entire URL) and HTTPS (using the hostname only) traffic.
A detailed configuration example is available in the Configuring web-service URL classification section.