CPU protection provides a granular method to control which ETH-CFM packets are processed. As indicated in CPU protection extensions for ETH-CFM, a unique rate can be applied to ETH-CFM packets classifying on specific MD-level and a specific OpCode and applied to both ingress (down MEP and ingress MIP) and egress (up MEP and egress MIP) extraction. This function is to protect the CPU on extraction when a Management Point (MP) is configured.
It is also important to protect the ETH-CFM architecture deployed in the service provider network. This protection scheme varies from CPU protection. This model is used to prevent ETH-CFM frames at the service provider MD-levels from gaining access to the network even when extraction is not in place. ETH-CFM squelching drops all ETH-CFM packets at or below the configured MD-level. The ETH-CFM squelch feature is supported at ingress only.
Figure: ETH-CFM hierarchical model shows a typical ETH-CFM hierarchical model with a subscriber ME (6), test ME (5), EVC ME (4) and an operator ME (2). This model provides the necessary transparency at each level of the architecture. For security reasons, it may be necessary to prevent errant levels from entering the service provider network at the UNI, ENNI, or other untrusted interconnection points. Configuring squelching at level four on both UNI-N interconnection ensures that ETH-CFM packets matching the SAP or binding delimited configuration will silently discard ETH-CFM packets at ingress.
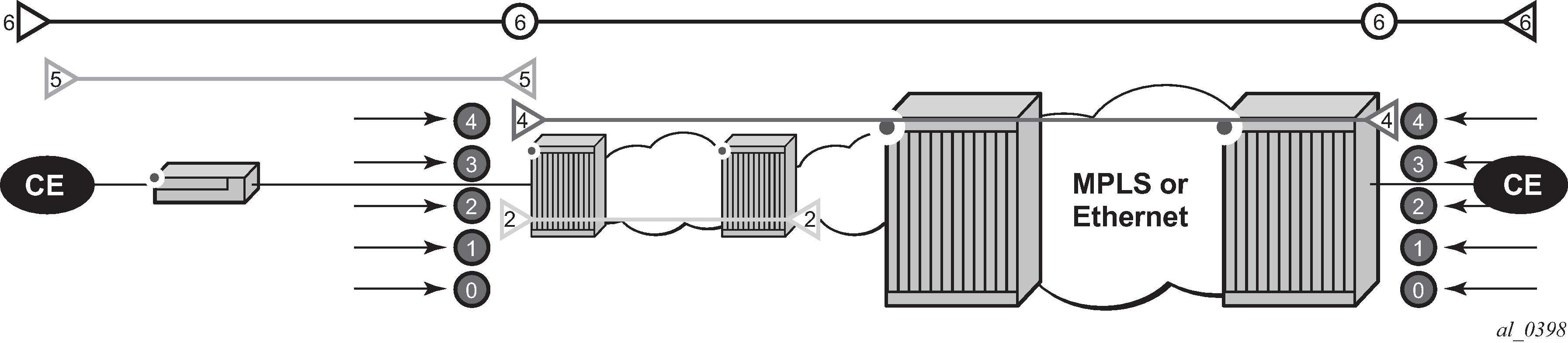
Squelching configuration uses a single MD-level (0 to 7) to silently drop all ETH-CFM packets matching the SAP or binding delimited configuration at or below the specified MD-level. In Figure: ETH-CFM hierarchical model, a squelch level is configured at MD-level 4. This means the configuration will silently discard MD-levels 0,1,2,3 and 4, assuming there is a SAP or binding match.
The operator is able to configure down MEPs and ingress MIPs that conflict with the squelched levels. This means that any existing MEP or MIP processing ingress CFM packets on a SAP or binding where a squelching policy is configured will be interrupted as soon as this command is entered into the configuration. These MPs are not able to receive any ingress ETH-CFM frames because squelching is processed before ETH-CFM extraction.
CPU protection extensions for ETH-CFM are still required in the model above because the subscriber ME (6) and the test ME (5) are entering the network across an untrusted connection, the UNI. ETH-CFM squelching and CPU protection for ETH-CFM can be configured on the same SAP or binding. Squelching is processed followed by CPU protection for ETH-CFM.
MPs configured to support primary VLANs are not subjected to the squelch function. Primary VLAN-based MPs, supported only on Ethernet SAPs, are extractions that take into consideration an additional VLAN beyond the SAP configuration.
The difference in the two protection mechanisms is shown in the Table: CPU protection and squelching. CPU protection is used to control access to the CPU resources when processing is required. Squelching is required when the operator is protecting the ETH-CFM architecture from external sources.
| Description | CPU protection extension for ETH-CFM | ETH-CFM squelching |
|---|---|---|
Ingress filtering |
Yes |
Yes |
Egress filtering |
Yes |
— |
Granularity |
Specified level and OpCode |
Level (at and below) |
Rate |
Configurable rate (includes 0=drop all) |
Silent drop |
Primary VLAN support |
Rate shared with SAP delineation |
Not exposed to squelch |
Extraction |
Requires MEP or MIP to extract |
No MEP or MIP required |
As well as including the squelching information under the show service service-id all, display output the squelch-ingress-level key also appears in the output of the sap-using and sdp-using show commands.
show service sap-using squelch-ingress-levels
===============================================================================
ETH-CFM Squelching
===============================================================================
PortId SvcId Squelch Level
-------------------------------------------------------------------------------
6/1/1:100.* 1 0 1 2 3 4 5 6 7
lag-1:100.* 1 0 1 2 3 4
6/1/1:200.* 2 0 1 2
lag-1:200.* 2 0 1 2 3 4 5
-------------------------------------------------------------------------------
Number of SAPs: 4
-------------------------------------------------------------------------------
===============================================================================
show service sdp-using squelch-ingress-levels
================================================================================
ETH-CFM Squelching
================================================================================
SdpId SvcId Type Far End Squelch Level
-------------------------------------------------------------------------------
12345:4000000000 2147483650 Spok 10.1.1.1 0 1 2 3 4
===============================================================================