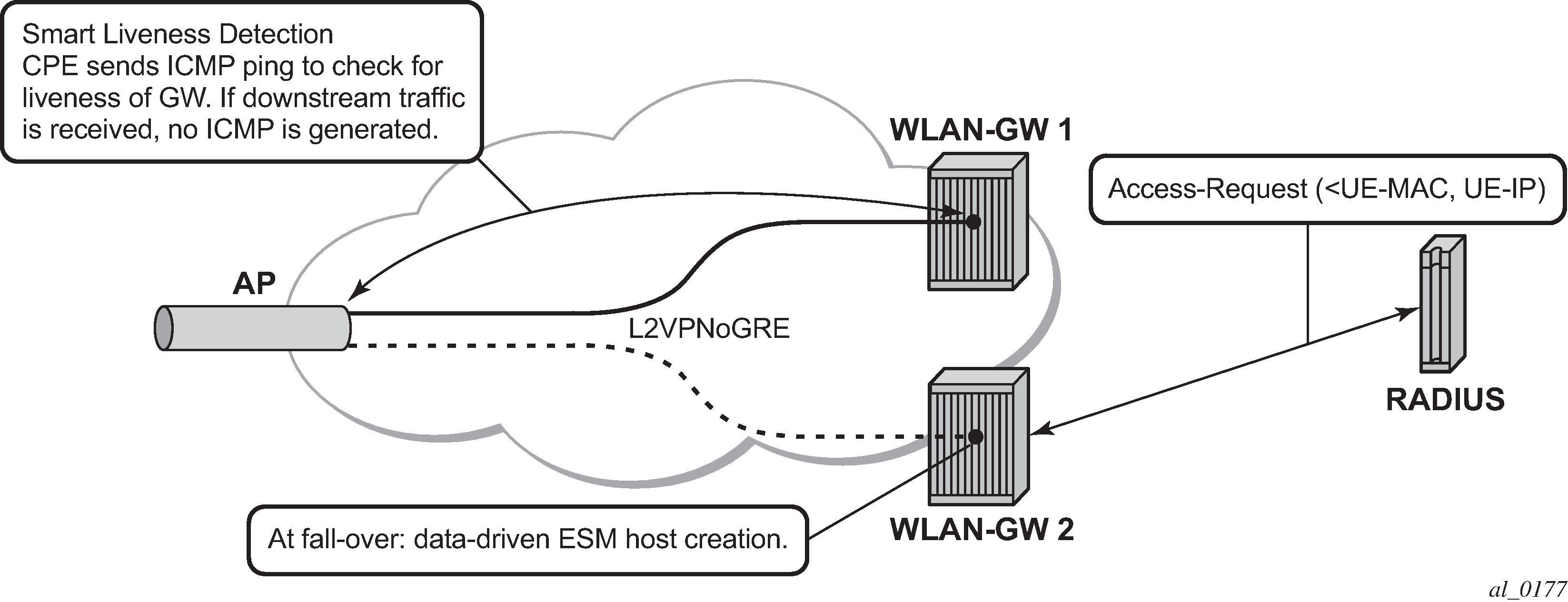
With data-triggered-ue-creation configured under wlan-gw group interface or per VLAN range (such as, per one or more SSIDs), the first UDP or TCP packet received on WLAN-GW ISA from an unknown subscriber (with no prior state, such as an unknown MAC address) triggers RADIUS authentication from the ISA. The authentication is based on configured isa-radius-policy (under the aaa context). If RADIUS authentication succeeds, then ESM host is created from the CPM. The ESM host can get deleted based on idle-timeout. Data-triggered authentication and subscriber creation enables stateless inter WLAN-GW redundancy, as shown in Figure: N:1 WLAN-GW redundancy based on data-triggered authentication and subscriber creation. If the AP is configured with a backup WLAN-GW address (or FQDN), it can tunnel subscriber traffic to the backup WLAN-GW, when it detects failure of the primary WLAN-GW (based on periodic liveness detection). With ‟data-triggered-ue-creation” configured, the first data packet results in authentication and ESM host creation on the backup WLAN-GW. If the subscriber had obtained an IP address via DHCP with L2-aware NAT on the primary WLAN-GW, it can retain it with L2 aware NAT on the backup WLAN-GW. The NAT outside pool for the subscriber changes on the backup WLAN-GW based on local configuration. For a subscriber that needs to be anchored on GGSN/PGW (as indicated via RADIUS access-accept), RADIUS server returns the IP address of PGW/GGSN where the UE was anchored before the switch-over. GTP tunnel is then signaled with ‟handover indication” set. The PGW/GGSN must return the requested IP address of the UE, which is the address with which the UE originated data packet that triggered authentication.
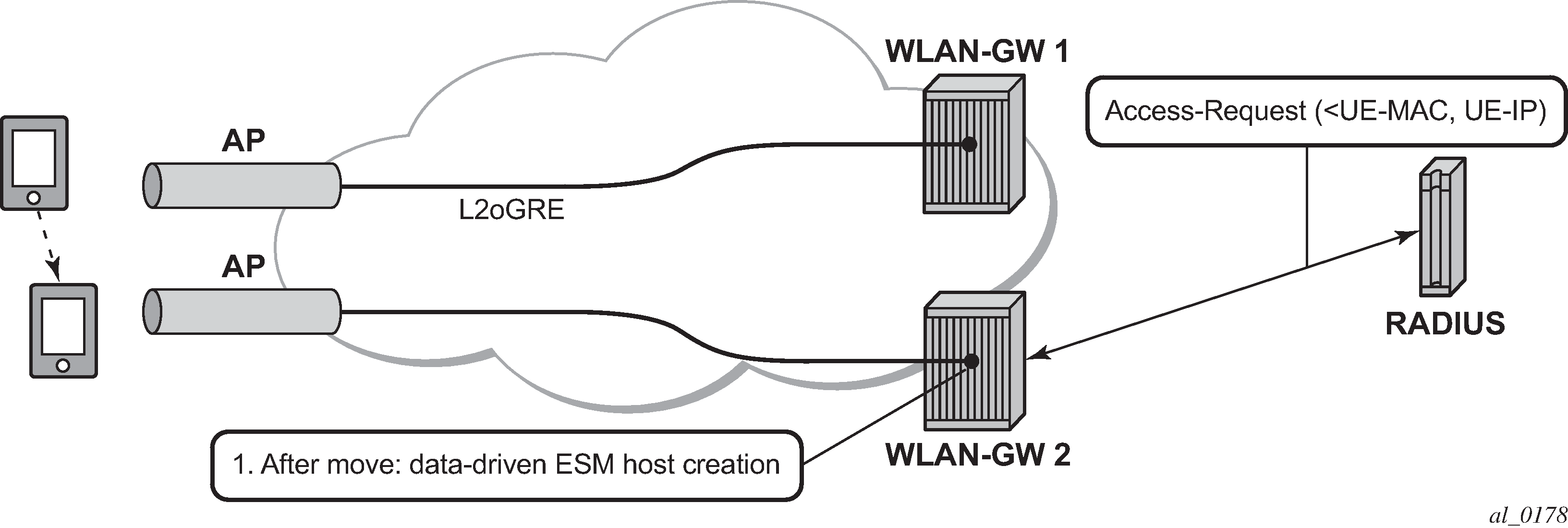
The same data-triggered authentication and subscriber creation is also used to support inter WLAN-GW mobility, such as when a UE moves form one AP to another AP such that the new AP is anchored on a different WLAN-GW. This is shown in Figure: N:1 WLAN-GW redundancy based on data-triggered authentication and subscriber creation.
The following output displays the configuration for migrant user support and ‟data-triggered” subscriber creation.
Migrant user NAT configuration
#------------------------------------------------------
NAT configuration for migrant and authenticated users
#------------------------------------------------------
service
vprn 300 customer 1 create
nat
inside
l2-aware
address 10.20.12/16
exit
exit
outside
pool "migrant_outside_pool" nat-group 1 type wlan-gw-anchor create
address-range 10.22.0.0 10.22.0.255 create
exit
no shutdown
exit
pool "wifi_outside_pool" nat-group 1 type l2-aware create
address-range 10.0.0.0 10.0.0.255 create
exit
no shutdown
exit
exit
exit
exit
nat
nat-policy "migrant_nat_300" create
pool "migrant_outside_pool" router 300
timeouts
tcp-established min 1
exit
exit
nat-policy "wifi_nat_300" create
pool "wifi_outside_pool" router 300
exit
exit
#--------------------------------------------------------------------------------
echo "AAA Configuration" - ISA-RADIUS-Policy for authentication from WLAN-GW ISA
#--------------------------------------------------------------------------------
aaa
isa-radius-policy "wifi_isa_radius" create
description "Default authentication policy for migrant users"
password "i2KzVe9XPxgy4KN2UEIf6jKeMT3X4mT6JcUmnnPZIrw" hash2
servers
router "Base"
source-address-range 10.100.100.4
server 1 create
authentication
coa
ip-address 10.100.100.2
secret "ABIQRobhHXzq13ycwqS74FSrj.OdTwh5IdjhRB.yAF." hash2
no shutdown
exit
exit
exit
radius-server-policy "radius_server_policy" create
servers
router "Base"
server 1 name "radius_server"
exit
exit
exit
#--------------------------------------------------
echo "Subscriber-mgmt Configuration" - Redirect Policy
#--------------------------------------------------
subscriber-mgmt
http-redirect-policy "migrant_redirect" create
url "portal.ipdtest.nokia.com:8081/start/?mac=$MAC&url=$URL&ip=$IP"
portal-hold-time 10
forward-entries
dst-ip 10.8.8.1 protocol tcp dst-port 8081
dst-ip 10.8.8.7 protocol tcp dst-port 8007
dst-ip 10.8.8.8 protocol udp dst-port 53
exit
exit
exit
service
#----------------------------------------------------------------
echo "migrant user configuration under wlan-gw group interface”
#---------------------------------------------------------------
vprn 300 customer 1 create
subscriber-interface "ies-4-20.10.1.1" create
address 10.20.12/16
group-interface "grp-vprn_ue-2/1/2:51" wlangw create
sap-parameters
sub-sla-mgmt
def-sla-profile "slaprof_1"
def-sub-profile "subprof_1"
sub-ident-policy "identprof"
exit
exit
dhcp
proxy-server
emulated-server 10.20.12.12
no shutdown
exit
trusted
lease-populate 32767
user-db "radius_ludb"
no shutdown
exit
host-connectivity-verify interval 1000
wlan-gw
gw-addresses
address 10.1.1.4
exit
mobility
hold-time 0
trigger data iapp
exit
router 50
wlan-gw-group 1
vlan-tag-ranges
range start 100 end 100
authentication
authentication-policy "wifi_isa_radius"
exit
data-triggered-ue-creation
dhcp
l2-aware-ip-address 10.1.1.2
primary-dns 10.1.1.1
secondary-dns 10.1.1.1
no shutdown
exit
nat-policy "migrant_nat_4"
exit
exit
no shutdown
exit
exit
exit
exit