This section discusses the Nokia routers acting as a Broadband Subscriber Aggregator (BSA) with Layer 2 aggregation toward a Broadband Subscriber Router (BSR).
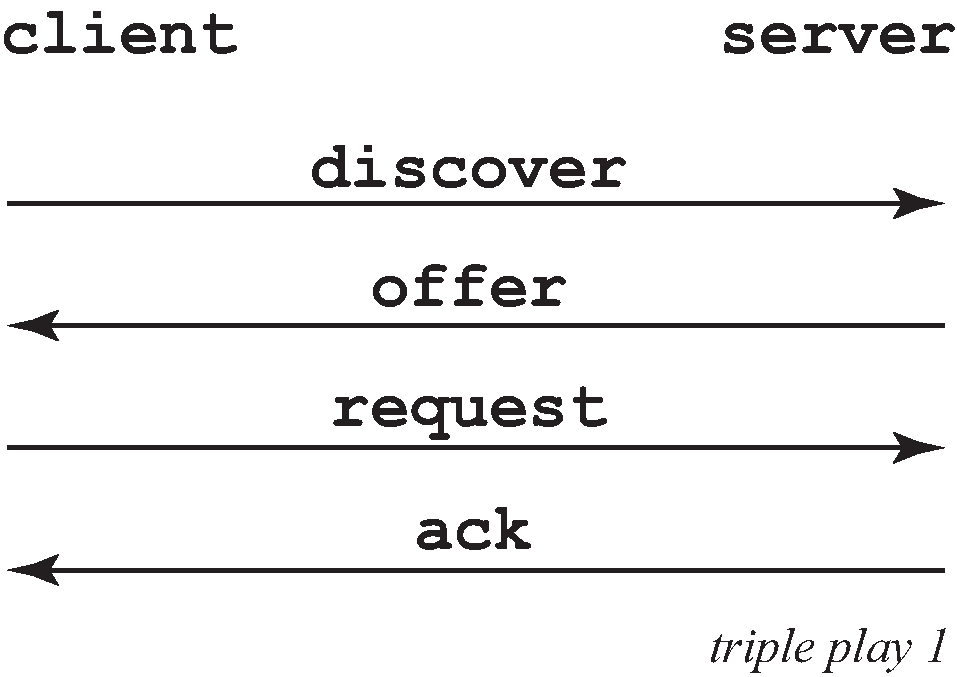
A typical initial DHCP scenario is shown in Figure: Initial DHCP scenario.
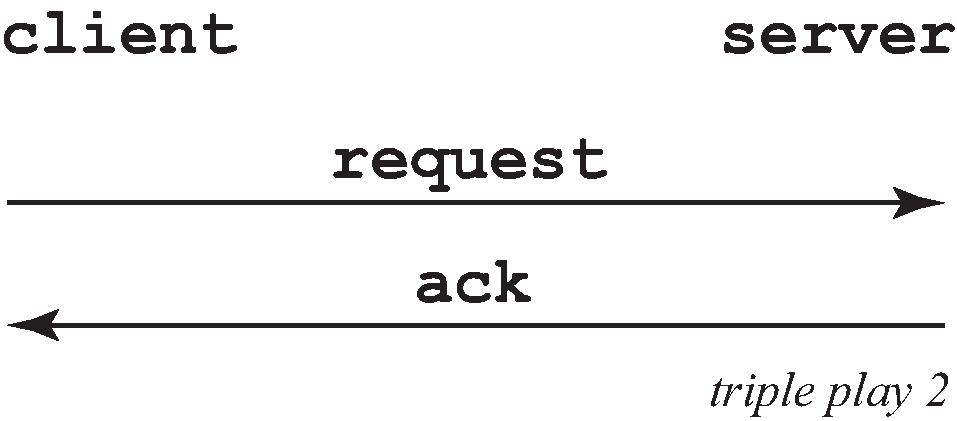
But, when the client already knows its IP address, it can skip the discover, as shown in Figure: DHCP scenario with known IP address.
The BSA can copy packets designated to the standard UDP port for DHCP (port 67) to its control plane for inspection, this process is called DHCP snooping.
DHCP snooping can be performed in two directions:
From the client to the DHCP server (Discover or Request messages):
to insert Option 82 information (when the system is not configured to do DHCP Relay), see Subscriber identification using Option 82 field.
to forward DHCP requests to a RADIUS server first, and not send them to the DHCP server unless the RADIUS server confirms positive identification.
For these applications, DHCP snooping must be enabled on the SAP toward the subscriber.
From the DHCP server (ACK messages):
to remove the Option 82 field toward the client
to build a dynamic DHCP lease state table for security purposes, see section DHCP lease state table
to perform Enhanced Subscriber Management, see Triple Play Enhances Subscriber Management
For these applications, DHCP snooping must be enabled on both the SAP and SDP toward the network and the SAP toward the subscriber.
A major application for DHCP response snooping in the context of Triple Play is security: A malicious user A could send an IP packet (for example, requesting a big video stream) with as source the IP address of user B. Any return packets would be sent to B, and therefore potentially jam the connection to B.
As the snooped information is coming straight from the operator's DHCP server, it is considered reliable. The BSA and BSR can use the snooped information to build anti-spoofing filters, populate the ARP table, send ARP replies, and so on.