3. IP Router Configuration
This chapter provides information about configuring basic router parameters.
Topics in this chapter include:
3.1. Configuring IP Router Parameters
In order to provision services on a 7705 SAR, IP parameters must be configured on the node. Logical IP routing interfaces must be configured to associate entities, such as a port or the system, with IP addresses.
A special type of IP interface is the system interface. Configuration of the system interface is the first step in the provisioning process. When configured, the system IP address can be advertised via peering or signaling protocols.
A system interface must have a unique IP address with a 32-bit subnet mask (for IPv4) or 128-bit prefix length (for IPv6). The system interface is used as the router identifier by higher-level protocols such as OSPF, IS-IS, and BGP, unless overwritten by an explicit router ID.
The following router parameters can be configured:
3.1.1. Interfaces
The 7705 SAR routers use different types of interfaces for various functions. Interfaces must be configured with parameters such as the address or port. An interface that is assigned to a port is a network interface. The system interface is a logical entity and is not assigned to a physical port.
The 7705 SAR supports IES and VPRN interfaces. IES is used to provide direct forwarding of IP traffic between CE devices and to facilitate the transport of in-band management traffic over ATM links. VPRN provides a Layer 3 virtual private network service to end customers.
3.1.1.1. Network Interface
A network interface (a logical IP routing interface) can be configured on a network-facing physical or logical port, and is used for connectivity purposes. Each network interface can have only one IP address. The connections are point-to-point; for example, a network port on an Ethernet interface cannot be connected to a LAN but must be connected to a network interface on another router.
Secondary IP address assignment, which is used to connect the same interface to more than one subnet, is not supported.
Network ports are used to transport Ethernet, ATM, and TDM services by means of pseudowires.
IP address assignment is not supported on access (customer-facing) ports except for services such as IES or VPRN.
On the 2-port 10GigE (Ethernet) Adapter card/module, the network interface can only be created on the v-port (not the ring ports).
The 7705 SAR can be used as an LER (label edge router) or LSR (label switch router).
OSPF, RIP, IS-IS, and BGP are supported as dynamic routing protocols, and static routes to next-hop addresses are also supported.
Some network Ethernet ports support network egress per-VLAN shapers on a per-network-interface basis. Refer to the “Per-VLAN Network Egress Shapers” section in the 7705 SAR Quality of Service Guide for details.
3.1.1.1.1. Ethernet Ports and Multiple ARP Entries
Multiple far-end MAC addresses can be associated with an Ethernet network port on the Ethernet Adapter card. These IP-to-MAC mappings are stored in the ARP table.
With multiple far-end MAC addresses supported in the ARP table, an Ethernet port can work with multiple network devices located in the same LAN segment. The 7705 SAR provides dynamic addressing by the ARP protocol as soon as MAC address resolution is needed for a given IP address. As devices are added to or removed from the network, the router updates the ARP table, adding new dynamic addresses and aging out those that are not in use.
Using the ARP table, the 7705 SAR inserts the appropriate far-end MAC address into the egress packet after the forwarding decision has been made based on the routing tables.
There is no limit to the number of MAC addresses per port or per adapter card. If the number of ARP entries reaches the system limit and a new MAC address that is not already in the ARP table becomes available, at least one MAC address must be flushed from the ARP table with the command clear>router>arp.
3.1.1.1.2. Dynamic ARP and Static MAC entry
The MAC address of the far end can be learned dynamically or be statically configured.
ARP is the common way to dynamically resolve the MAC address of next-hop IP hosts and is the primary way to resolve IP-to-MAC associations. ARP packets are sent as soon as a MAC address resolution is needed for a given IP address.
Static configuration of MAC addresses for next-hop routers is also supported. Static configuration provides a higher level of security against IP hijacking attacks.
Note:
|
3.1.1.1.3. Configurable ARP Retry Timer
A timer is available to configure a shorter retry interval when an ARP request fails. An ARP request may fail for a number of reasons, such as network connectivity issues. By default, the 7705 SAR waits 5000 ms before retrying an ARP request. The configurable retry timer makes it possible to shorten the retry interval to between 100 and 30 000 ms.
| Note: The ARP retry default value of 5000 ms is intended to protect CPU cycles on the 7705 SAR, especially when it has a large number of interfaces. Configuring the ARP retry timer to a value shorter than the default should be done only on mission-critical links, such as uplinks or aggregate spoke SDPs transporting mobile traffic; otherwise, the retry interval should be left at the default value. |
The configurable ARP retry timer is supported on VPRN and IES service interfaces, as well on the router interface.
3.1.1.1.4. Proxy ARP
Proxy ARP is a technique by which a router on one network responds to ARP requests intended for another node that is physically located on another network. The router effectively pretends to be the destination node by sending an ARP response to the originating node that associates the router’s MAC address with the destination node’s IP address (acts as a proxy for the destination node). The router then takes responsibility for routing traffic to the real destination.
Proxy ARP simplifies networking schemes because it enables nodes on a subnet to reach remote subnets without the need to configure routing or a default gateway.
The 7705 SAR supports both proxy ARP and local proxy ARP. Local proxy ARP is similar to proxy ARP except that it is used within a subnet; the router responds to all requests for IP addresses within the subnet and forwards all traffic between the hosts in the subnet. Local proxy ARP is used on subnets where hosts are prevented from communicating directly.
Typically, routers support proxy ARP only for directly attached networks. The 7705 SAR supports proxy ARP for all known networks in the routing instance where the virtual interface proxy ARP is configured.
Proxy ARP is supported on:
- the global routing table
- IES service interfaces
- VPRN service interfaces
A typical application for proxy ARP is when hosts in a private subnet need to communicate to host/servers via the public Internet; for example, when using network address translation (NAT). Source NAT can be used for creating connections from inside (private network) to outside (public network). If an arriving IP packet on the 7705 SAR matches the NAT policy rules, an internal mapping is created between the private source IP address/source port and a public source IP address/source port. The public IP address and port are configured in the NAT pool policy.
Proxy ARP is therefore required for Source NAT when the NAT pool uses a range of IP public addresses. The NAT pool public IP address can either be in a different subnet than the public interface or in the same subnet as the public interface. Proxy ARP can be used to respond to ARP requests for an IP address in these NAT pools.
| Note: Only remote proxy ARP is applicable for NAT. |
In order to support NAT and other edge-like environments, proxy ARP supports policies that allow the provider to:
- configure prefix lists that determine for which target networks proxy ARP will be attempted
- configure prefix lists that determine for which source hosts proxy ARP will be attempted
As an example, when a source NAT pool is configured with a dynamic IP pool with the address range 1.1.1.2 to 1.1.1.254 on the public interface 1.1.1.1, proxy ARP can be used to resolve the ARP request of the NAT pool hosts with the local interface (1.1.1.1) MAC address (remote proxy ARP).
As another example, if a NAT pool of addresses in the range 2.2.2.1 to 2.2.2.100 is configured on the public Layer 3 interface 128.251.10.59, then by enabling remote proxy ARP, the 7705 SAR will respond to ARP requests from hosts 2.2.2.1 to 2.2.2.100. In addition, a route policy with a prefix list can be created and used as a proxy ARP policy for finer granularity of the IP range for which proxy ARP is being used.
For detailed information on NAT, see NAT Security.
3.1.1.1.5. ETH-CFM Support
Ethernet Connectivity Fault Management (ETH-CFM) is defined in the IEEE 802.1ag and ITU Y.1731 standards. ETH-CFM specifies protocols, procedures, and managed objects to support fault management (including discovery and verification of the path), detection, and isolation of a connectivity fault in an Ethernet network.
ETH-CFM requires the configuration of specific entities at the global level and at the Ethernet service level and/or network interface level. Maintenance domains (MDs) and maintenance associations (MAs) are configured at the global level. Maintenance association endpoints (MEPs) are configured at the service level and network interface level.
MEPs that are not service-based are referred to as facility MEPs. A facility MEP is a Down MEP that detects failure conditions for an Ethernet transport network using ETH-CCM and, where appropriate, propagates alarm conditions so that the Epipe services that share this common transport are aware of the failure. The 7705 SAR supports facility MEPs on network interfaces.
Facility MEPs are created in the same way as service MEPs, by configuring the ETH-CFM domain and association. However, the association used to build the facility MEP does not include a bridge identifier, as the facility MEP is not bound to a service. The CLI ensures that a bridge identifier is not configured when the association is applied to a facility MEP.
The following applies to facility MEPs on network interfaces:
- the MEP must be a Down MEP
- the port must be in network mode
- the port must be configured for null or dot1q encapsulation
- the MEP supports all fault management functionality, with the exception of alarm indication signaling (AIS)
- the MEP supports all performance monitoring functionality including synthetic loss measurement (SLM)
- the MEP supports throughput measurement via loopback messaging at wire speed
- received CFM messages are processed only when the VLAN ID, the MAC destination address, and the MEP level matches those of the MEP
Network interface facility MEPs are supported on all network Ethernet ports on the 7705 SAR adapter cards and chassis.
For detailed information on ETH-CFM entities and on ETH-CFM support for services, refer to the 7705 SAR Services Guide, “ETH-CFM (802.1ag and Y.1731)”. For information on running Ethernet OAM tests, refer to the 7705 SAR OAM and Diagnostics Guide, “ETH-CFM (802.1ag and Y.1731)”.
3.1.1.2. System Interface
The system interface is associated with the node, not a specific interface. It is used during the configuration of the following entities:
- LSP creation (next hop) — when configuring MPLS paths and LSPs
- the addresses on a target router — to set up an LDP, OSPF, or BGP session between neighbors and to configure SDPs (the system interface is the service tunnel endpoint)
The system interface is also referred to as the loopback interface. It is used as the router identifier if a router ID has not been explicitly configured. Additional loopback interfaces can be configured; however, the system interface is a special loopback interface.
The system interface is used to preserve connectivity (when alternate routes exist) and to decouple physical connectivity and reachability. If an interface carrying peering traffic fails, and there are alternative links to the same peer system interface, peering could be either unaffected or re-established over the alternate links. The system interface IP address is also used for MPLS and pseudowire/VLL signaling (via targeted LDP).
3.1.1.3. Unnumbered Interfaces
Unnumbered interfaces are point-to-point interfaces that are not explicitly configured with a dedicated IP address and subnet; instead, they borrow (or link to) an IP address from another interface on the system (the system IP address, another loopback interface, or any other numbered interface) and use it as the source IP address for packets originating from the interface.
The benefits of using unnumbered interfaces are:
- ISP backhaul can be enabled with a single IP address allocated to the CE nodes (network interface address is coupled with the system IP address)
- nodes can be added to or deleted from a network without address changes—unnumbered interfaces are linked to a centralized IP address and therefore do not require any address change if the nodes are relocated. After a topology change, the ARP table is updated to ensure reachability and the upper layer protocols re-establish the peering sessions.
Unnumbered interfaces are supported on:
- network interfaces
- IES interfaces
- VPRN interfaces
Only IPv4 addresses are supported.
Unnumbered interfaces are supported for the IS-IS and OSPF routing protocols and for MPLS (RSVP-TE and LDP). Refer to the 7705 SAR Routing Protocols Guide, “Unnumbered Interfaces” in the OSPF and IS-IS sections, for more information on IS-IS and OSPF unnumbered interface support. Refer to the 7705 SAR MPLS Guide, “RSVP-TE Support for Unnumbered Interfaces” and “LDP Support for Unnumbered Interfaces”, for more information on MPLS unnumbered support.
This feature is supported via both dynamic and static ARP.
The following ports on the 7705 SAR adapter cards, modules, and fixed platforms support IP unnumbered interfaces:
- any datapath Ethernet port with null, dot1q, or qinq encapsulation (with the exception of the 10GigE port on the 2-port 10GigE (Ethernet) Adapter card)
- v-port on the 2-port 10GigE (Ethernet) Adapter card
- MWA ports on the Packet Microwave Adapter card
- any T1/E1 port (access or network) with ppp encapsulation
- any DS3/E3 port (network) with ppp encapsulation
- any OC3/STM1 port (network) with ppp-auto encapsulation (POS)
| Note: Unnumbered interfaces do not support PIM routing or IGMP listener capabilities. |
3.1.1.4. Creating an IP Address Range
An IP address range can be reserved for IES or VPRN services by using the config>router>service-prefix command. When a service interface is configured, the IP address must be in the range specified in the service-prefix command. If the service-prefix command is not configured, then no limitation exists.
Addresses in the range of a defined service-prefix can be allocated to a network port unless the exclusive parameter is specified. Then, the address range is exclusively reserved for services.
When defining a range that is a superset of a previously defined service prefix, the new superset definition will replace the original configuration. For example, if a service prefix exists for 10.10.10.0/24, and a new service prefix is configured as 10.10.0.0/16, then the old address (10.10.10.0/24) will be replaced with the new address (10.10.0.0/16).
When defining a range that is a subset of a previously defined service prefix, the subset will replace the existing superset providing that the addresses used by services are not affected. For example, if a service prefix exists for 10.10.0.0/16, and a new service prefix is configured as 10.10.10.0/24, then the 10.10.0.0/16 entry will be unreserved as long as there no services configured that are using the 10.10.x.x addresses other than 10.10.10.x.
3.1.2. IP Addresses
IP addresses are assigned to system interfaces and to network-facing physical or logical ports. The IP addresses are in the form <ip-address/prefix-length> or <ip-address/subnet mask>.
IP version 4 (IPv4) addresses are supported on all interfaces except the CWDM/OADM module. On the 2-port 10GigE (Ethernet) Adapter card and 2-port 10GigE (Ethernet) module, an IPv4 network address is assigned to the v-port only.
IP version 6 (IPv6) addresses are supported on:
- access ports (IES only); for a complete list of cards and ports that support IES IPv6 SAPs, refer to the 7705 SAR Services Guide, “IES for Customer Traffic”
- network ports (null or dot1q encapsulation) on:
- 2-port 10GigE (Ethernet) Adapter card (v-port only)
- 8-port Ethernet Adapter card, version 2
- 6-port Ethernet 10Gbps Adapter card
- 8-port Gigabit Ethernet Adapter card
- 10-port 1GigE/1-port 10GigE X-Adapter card
- Packet Microwave Adapter card
- Ethernet ports on the 7705 SAR-M (all variants)
- Ethernet ports on the 7705 SAR-A (both variants)
- Ethernet ports on the 7705 SAR-Ax
- 7705 SAR-W
- Ethernet ports on the 7705 SAR-Wx
- 7705 SAR-H
- Ethernet ports on the 7705 SAR-Hc
- Ethernet ports on the 7705 SAR-X
- Ethernet management port
- DSL module
- GPON module
- 2-port 10GigE (Ethernet) module (v-port only) when the module is installed in the 7705 SAR-M (variants with module slots)
- 4-port SAR-H Fast Ethernet module when the module is installed in the 7705 SAR-H
- 6-port SAR-M Ethernet module when the module is installed in the 7705 SAR-M (variants with module slots)
- network ports on the 4-port OC3/STM1 Clear Channel Adapter card (POS encapsulation)
The 7705 SAR supports IPv6 dual stack on Ethernet ports and the management port. IPv6 dual stack is also supported on DSL module ports and GPON module ports when the module is installed in the 7705 SAR-M (variants with module slots). Dual stack allows both IPv4 and IPv6 to run simultaneously on the interface.
Network IP addresses can be assigned manually, or assigned dynamically using DHCP when the 7705 SAR is acting as a DHCP client. System IP addresses can be assigned manually, or assigned dynamically using DHCP when the 7705 SAR is acting as a DHCP client and the DHCP server-facing interface is unnumbered. See Unnumbered Interfaces for more information.
3.1.3. Internet Protocol Versions
The 7705 SAR supports IP version 4 (IPv4 – RFC 791, Internet Protocol) and IP version 6 (IPv6 – RFC 2460, Internet Protocol, Version 6 Specification). The 7705 SAR can forward IPv6 packets over static routes for network forwarding, IES services, and node management.
IPv6 is a newer version of IP, designed as a successor to IPv4. Some of the differences between IPv4 and IPv6 are:
- expanded addressing capabilities — IPv6 increases the IP address size from 32 bits (IPv4) to 128 bits, to support more levels of addressing hierarchy, a much greater number of addressable nodes, and simplified autoconfiguration of addresses
- header format simplification — some IPv4 header fields have been dropped or made optional to reduce the processing cost of packet handling and to limit the bandwidth cost of the IPv6 header
- improved support for extensions and options — changes in the way IP header options are encoded allows for more efficient forwarding, less stringent limits on the length of options, and greater flexibility for introducing new options in the future
- flow labeling capability — the capability to enable the labeling of packets belonging to particular traffic flows for which the sender requests special handling, such as non-default quality of service (QoS) or real-time service, was added in IPv6
- authentication and privacy capabilities — extensions to support authentication, data integrity, and (optional) data confidentiality are specified for IPv6
3.1.3.1. IPv6 Address Format
IPv6 uses a 128-bit address, as opposed to the IPv4 32-bit address. Unlike IPv4 addresses, which use the dotted-decimal format, with each octet assigned a decimal value from 0 to 255, IPv6 addresses use the colon-hexadecimal format X:X:X:X:X:X:X:X, where each X is a 16-bit section of the 128-bit address. In its full notation, an IPv6 address appears as shown in the following example:
2001:0db8:0a0b:12f0:0000:0000:0000:0001
| Note: On the 7705 SAR, any function that displays an IPv6 address or prefix reflects the rules specified in RFC 5952, A Recommendation for IPv6 Address Text Representation. Specifically, hexadecimal letters in IPv6 addresses are represented in lowercase, and the correct compression of all leading zeros is displayed. |
As per RFC 5952, the above IPv6 address appears as:
2001:db8:a0b:12f0::1
Leading zeros must be omitted from each block in the address. A series of zeros can be replaced with a double colon. The double colon can only be used once in an address.
The IPv6 prefix is the part of the IPv6 address that represents the network identifier. The network identifier appears at the beginning of the IP address and is made up of the network address and subnet address. The IPv6 prefix length, which begins with a forward slash (/), specifies the number of bits in the network identifier; this is similar to the subnet mask in IPv4 addresses. For example, the address 1080:6809:8086:6502::1/64 means that the first 64 bits of the address represent the network identifier; the remaining 64 bits represent the node identifier.
The following adapter cards support the full IPv6 subnet range for IPv6 static routes and interface IP addresses:
- 6-port Ethernet 10Gbps Adapter card
- 8-port Gigabit Ethernet Adapter card, version 2 and version 3
- 2-port 10GigE (Ethernet) Adapter card (on the v-port)
- 10-port 1GigE/1-port 10GigE X-Adapter card
For these cards, the supported route range for statically provisioned or dynamically learned routes is from /1 to /128. Supported interface IP address prefixes are from /4 to /127, and /128 on system or loopback interfaces.
For all other cards, modules, and ports (including the v-port on the 2-port 10GigE (Ethernet) module), the supported range for statically provisioned or dynamically learned routes is from /1 to /64 or is /128 (indicating a host route). Supported interface IP address prefixes are from /4 to /64, and /128 on system or loopback interfaces.
3.1.3.2. IPv6 Headers
The IPv6 header format is shown in Figure 1. Table 2 describes the fields.
Figure 1: IPv6 Header Format
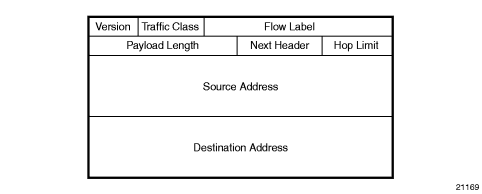
Table 2: IPv6 Header Field Descriptions
Field | Description |
Version | 4-bit IP version number (v6) |
Traffic Class | 8-bit value that enables a source to identify the delivery classification of its packets |
Flow Label | 20-bit flow label that can be used by a source to label packets for which the source requests special handling by IPv6 routers; for example, non-default QoS or real-time service A flow contains a series of packets that travel between a particular source and particular destination |
Payload Length | The length of the payload (16-bit unsigned integer), which is the rest of the packet following the IPv6 header, in octets Any extension headers that are present in the packet are considered to be part of the payload; therefore, the payload always begins immediately after the Destination Address |
Next Header | 8-bit selector that identifies the type of header immediately following the IPv6 header. The Next Header uses the same values as the IPv4 protocol field for some protocols; for example, the values for TCP and UDP are the same for both IPv4 and IPv6. The Next Header values differ from IPv4 when IPv6 extension headers are identified or when IPv6 unique protocols, such as ICMPv6, are identified. |
Hop Limit | 8-bit unsigned integer that is decremented by 1 by each node that forwards the packet. If the hop limit is decremented to 0, the packet is discarded and the node sends the ICMPv6 message “Hop Limit Exceeded in transit” back to the sender. |
Source Address | 128-bit address of the originator of the packet |
Destination Address | 128-bit address of the intended recipient of the packet |
| Note: Type 0 IPv6 routing headers have been deprecated on the 7705 SAR (per RFC 5095). |
3.1.3.3. Neighbor Discovery
IPv6 provides autoconfiguration of addresses, where equipment connecting to an IPv6 network can autoconfigure a usable address. There are two types of address autoconfiguration: stateless and stateful. Stateless autoconfiguration requires no manual configuration of hosts, minimal configuration of routers, and no servers. The host generates its own addresses using locally available information and information advertised by routers, such as the 7705 SAR. Stateless autoconfiguration is a feature of the neighbor discovery protocol.
Stateful autoconfiguration involves hosts obtaining interface addresses and/or configuration information from a server. For more information on stateful configuration, see DHCP Relay and DHCPv6 Relay.
Stateless autoconfiguration uses two neighbor discovery messages: router solicitation and router advertisement. The host sends router solicitation messages to find routers, and the routers send router advertisement messages to indicate their presence. The host sends the router solicitation message to all routers, requesting the IPv6 prefix as well as the IPv6 address of the routers. Each router responds with a router advertisement message indicating their IPv6 prefix and IPv6 address.
Neighbor discovery performs Layer 2 neighbor address resolution similar to ARP in IPv4. In addition, the neighbor discovery protocol performs a neighbor reachability function, where a “stale” neighbor entry is probed for reachability using a unicast neighbor solicitation message. This function ensures that link-layer address changes will be discovered reliably in addition to confirming the presence of the IPv6 neighbor.
Neighbor discovery is implemented within ICMPv6.
3.1.4. Router ID
The router ID is a 32-bit IP address (IPv4) that uniquely identifies the router within an autonomous system (see Autonomous Systems).
IS-IS and BGP use the router ID as their system ID.
OSPF routers use the router IDs of the neighbor routers to establish adjacencies. Neighbor IDs are learned when Hello packets are received from the neighbor.
Before configuring OSPF parameters, ensure that the router ID is derived by one of the following methods:
- define the value using the config>router>router-id ip-address command
- define the system interface using the config>router>interface ip-int-name command (used if the router ID is not specified with the config>router>router-id ip-address command), or, if the 7705 SAR is acting as a DHCP client, allow the system interface to be defined dynamically by configuring the DHCP server-facing interface as unnumbered.A system interface (also referred to as the loopback address) must have an IP address with a 32-bit subnet mask. The system interface is assigned during the primary router configuration process when the interface is created in the logical IP interface context.
- if you do not specify a router ID, the last 4 bytes of the MAC address are used
- the router ID can be derived on the protocol level; for example, BGP
3.1.5. Autonomous Systems
Networks can be grouped into areas. An area is a collection of network segments within an autonomous system (AS) that have been administratively assigned to the same group. An area’s topology is concealed from the rest of the AS, which results in a significant reduction in routing traffic.
Routing in the AS takes place on two levels, depending on whether the source and destination of a packet reside in the same area (intra-area routing) or different areas (inter-area routing). In intra-area routing, the packet is routed solely on information obtained within the area; no routing information obtained from outside the area can be used. This protects intra-area routing from the injection of bad routing information.
Routers that belong to more than one area are called area border routers. All routers in an AS do not have an identical topological database. An area border router has a separate topological database for each area it is connected to. Two routers, which are not area border routers, belonging to the same area, have identical area topological databases.
Autonomous systems share routing information, such as routes to each destination and information about the route or AS path, with other ASs using BGP. Routing tables contain lists of next hops, reachable addresses, and associated path cost metrics to each router. BGP uses the information and path attributes to compile a network topology.
| Note: Within the router context, the 7705 SAR supports EBGP and IBGP. Within the VPRN context, the 7705 SAR supports EBGP but does not support IBGP. For information on configuring BGP within the router context, refer to the 7705 SAR Routing Protocols Guide, “BGP”. For information on configuring BGP within the VPRN context, refer to the 7705 SAR Services Guide, “VPRN Services”. |
3.1.6. DHCP and DHCPv6
DHCP is a configuration protocol used to communicate network information and configuration parameters from a DHCP server to a DHCP-aware client. DHCP is based on the BOOTP protocol, with additional configuration options and the added capability of allocating dynamic network addresses. DHCP-capable devices are also capable of handling BOOTP messages.
A DHCP client is an IP-capable device (typically a computer or base station) that uses DHCP to obtain configuration parameters such as a network address. A DHCP server is an Internet host or router that returns configuration parameters to DHCP clients. A DHCP/BOOTP Relay agent is a host or router that passes DHCP messages between clients and servers.
DHCPv6 is not based on, and does not use, the BOOTP protocol.
Home computers in a residential high-speed Internet application typically use the DHCP protocol to have their IP address assigned by their Internet service provider.
The 7705 SAR can act as a DHCP client, a DHCP or DHCPv6 Relay agent, or a local DHCP or DHCPv6 server.
When used as a CPE device, the 7705 SAR can act as a DHCP client to learn the IP address of the network interface. Dynamic IP address allocation is supported on both network and system interfaces.
OSPF, IS-IS, or RIP is used to advertise the system IP address over the network interface to the next-hop router. Static routing cannot be used because the network interface IP address is dynamic and can change during normal operation.
For DHCP, the DHCP protocol requires the client to transmit a request packet with a destination broadcast address of 255.255.255.255 that is processed by the DHCP server.
For DHCPv6, the DHCP protocol requires the client to transmit a request packet with a destination multicast address of ff02::1:2 (all DHCP servers and relay agents on the local network segment) that is processed by the DHCP server.
Since IP routers do not forward broadcast or multicast packets, this would suggest that the DHCP client and server must reside on the same network segment. However, for various reasons, it is sometimes impractical to have the server and client reside in the same IP network.
When the 7705 SAR is acting as a DHCP Relay agent, it processes these DHCP broadcast or multicast packets and relays them to a preconfigured DHCP server. Therefore, DHCP clients and servers do not need to reside on the same network segment.
When the 7705 SAR is acting as a local DHCP server, it processes these DHCP broadcast or multicast packets and allocates IP addresses for the DHCP client as needed.
The 7705 SAR supports a maximum of 16 servers per node on the 7705 SAR-A, 7705 SAR-Ax, 7705 SAR-H, 7705 SAR-Hc, 7705 SAR-M, 7705 SAR-W, 7705 SAR-Wx, and 7705 SAR-X. The 7705 SAR supports a maximum of 62 servers per node on the 7705 SAR-8 with a CSMv2 and on the 7705 SAR-18. Any Layer 3 interface configured using the global routing table or Layer 3 services supports up to 8 servers.
3.1.6.1. DHCP Relay and DHCPv6 Relay
The 7705 SAR provides DHCP/BOOTP Relay agent services and DHCPv6 Relay agent services for DHCP clients. DHCP is used for IPv4 network addresses and DHCPv6 is used for IPv6 network addresses. Both DHCP and DHCPv6 are known as stateful protocols because they use dedicated servers to maintain parameter information.
In the stateful autoconfiguration model, hosts obtain interface addresses and/or configuration information and parameters from a server. The server maintains a database that keeps track of which addresses have been assigned to which hosts.
The 7705 SAR supports DHCP Relay on the base router, and on access IP interfaces associated with IES and VPRN. Each DHCP instance supports up to 8 DHCP servers.
The 7705 SAR supports DHCPv6 Relay on access IP interfaces associated with IES and VPRN. Each DHCPv6 instance supports up to 8 DHCPv6 servers. For more information on DHCPv6 Relay, refer to the 7705 SAR Services Guide, “DHCPv6 Relay”.
3.1.6.1.1. DHCP Relay Agent Options
DHCP options are codes that the 7705 SAR inserts in packets being forwarded from a DHCP client to a DHCP server. Some options have additional information stored in suboptions.
The 7705 SAR supports Option 60 and Option 61 as specified in RFC 2132. Option 60 is the vendor class identifier, which can contain information such as the client’s hardware configuration. Option 61 is the client identifier.
The 7705 SAR supports the Relay Agent Information Option 82 as specified in RFC 3046. The following suboptions are supported for the base router:
- action
- circuit ID
- copy-82
- remote ID
3.1.6.2. Local DHCP and DHCPv6 Server
The 7705 SAR supports local DHCP server functionality on the base router and on access IP interfaces associated with VPRN, by dynamically assigning IPv4 or IPv6 addresses to access devices that request them. This standards-based, full DHCP server implementation allows a service provider the option to decentralize IP address management into the network. The 7705 SAR can support public and private addressing in the same router, including overlapped private addressing in the form of VPRNs in the same router.
The 7705 SAR acts as a DHCP server or a DHCPv6 server.
An administrator creates pools of addresses that are available for assigned hosts. Locally attached hosts can obtain an address directly from the server. Routed hosts receive addresses through a relay point in the customer’s network.
When a DHCP server receives a DHCP message from a DHCP Relay agent, the server looks for a subnet to use for assigning an IP address. If configured with the use-pool-from-client command, the server searches Option 82 information for a pool name. If a pool name is found, an available address from any subnet of the pool is offered to the client. If configured with the use-gi-address command, the server uses the gateway IP address (GIADDR) supplied by the Relay agent to find a matching subnet. If a subnet is found, an address from the subnet is offered to the client. If no pool or subnet is found, then no IP address is offered to the client.
When a DHCPv6 server receives a DHCP message from a DHCPv6 Relay agent, the server looks for a subnet to use for assigning an IP address. If configured with the use-pool-from-client command, the server searches Option 17 information for a pool name. If a pool name is found, an available address from any subnet of the pool is offered to the client. If configured with the use-link-address command, the server uses the address supplied by the Relay agent to find a matching subnet prefix. If a prefix is found, an address from the subnet is offered to the client. If no pool or prefix is found, then no IP address is offered to the client.
IPv4 and IPv6 address assignments are temporary and expire when the configured lease time is up. The server can reassign addresses after the lease expires.
If both the no use-pool-from-client command and the no use-gi-address command or no use-link-address command are specified, the server does not act.
3.1.6.2.1. DHCP and DHCPv6 Server Options
Options and identification strings can be configured on several levels.
DHCP servers support the following options, as defined in RFC 2132:
- Option 1—Subnet Mask
- Option 3—Default Routers
- Option 6—DNS Name Servers
- Option 12—Host Name
- Option 15—Domain Name
- Option 44—Netbios Name Server
- Option 46—Netbios Node Type Option
- Option 50—IP Address
- Option 51—IP Address Lease Time
- Option 53—DHCP Message Type
- Option 54—DHCP Server IP Address
- Option 55—Parameter Request List
- Option 58—Renew (T1) Timer
- Option 59—Renew (T2) Timer
- Option 60—Class Identifier
- Option 61—Client Identifier
DHCP servers also support Suboption 13 Relay Agent Information Option 82 as specified in RFC 3046, to enable the use of a pool indicated by the DHCP client.
DHCPv6 servers support the following options, as defined in RFC 3315:
- Option 1—OPTION_CLIENTID
- Option 2—OPTION_SERVERID
- Option 3—OPTION_IA_NA
- Option 4—OPTION_IA_TA
- Option 5—OPTION_IAADDR
- Option 6—OPTION_ORO
- Option 7—OPTION_PREFERENCE
- Option 8—OPTION_ELAPSED_TIME
- Option 9—OPTION_RELAY_MSG
- Option 11—OPTION_AUTH
- Option 12—OPTION_UNICAST
- Option 13—OPTION_STATUS_CODE
- Option 14—OPTION_RAPID_COMMIT
- Option 15—OPTION_USER_CLASS
- Option 16—OPTION_VENDOR_CLASS
- Option 17—OPTION_VENDOR_OPTS
- Option 18—OPTION_INTERFACE_ID
- Option 19—OPTION_RECONF_MSG
- Option 20—OPTION_RECONF_ACCEPT
These options are copied into the DHCP reply message, but if the same option is defined several times, the following order of priority is used:
- subnet options
- pool options
- options from the DHCP client request
A local DHCP server must be bound to a specified interface by referencing the server from that interface. The DHCP server will then be addressable by the IP address of that interface. A normal interface or a loopback interface can be used.
A DHCP client is defined by the MAC address and the circuit identifier. This implies that for a certain combination of MAC and circuit identifier, only one IP address can be returned; if more than one request is made, the same address will be returned.
3.1.7. ICMP and ICMPv6
Internet Control Message Protocol (ICMP) is part of the Internet Protocol Suite as defined in RFC 792, Internet Control Message Protocol, for IPv4 and RFC 4443, Internet Control Message Protocol (ICMPv6) for the Internet Protocol Version 6 (IPv6) Specification. The neighbor discovery capability of ICMPv6 is specified in RFC 4861, Neighbor Discovery for IP Version 6 (IPv6).
ICMP messages are typically generated in response to errors in IP datagrams or for diagnostic or routing purposes. The ICMP ping utility for IPv4 and IPv6 and the ICMP traceroute utility for IPv4 are described in the 7705 SAR OAM and Diagnostics Guide, “ICMP Diagnostics”.
The 7705 SAR supports the ICMP capabilities described in Table 3.
Table 3: ICMP Capabilities for IPv4
ICMP Message | Description |
Address mask reply | Used to reply to an address mask request with an appropriate subnet mask |
Time exceeded (TTL expired) | Generated by a router to inform the source of a packet that was discarded due to the time to live (TTL) field reaching zero Used by the traceroute utility to obtain a list of hosts that the packets traversed from source to destination |
Destination unreachable | Generated by a router to inform the source host that the destination is unreachable for a specified reason |
Echo request/Echo reply | Used by the ping utility to test whether a host is reachable across an IP network and to measure the roundtrip time for packets sent from the local host to a destination node |
The 7705 SAR supports the ICMPv6 capabilities described in Table 4.
Table 4: ICMPv6 Capabilities for IPv6
ICMPv6 Message | Description |
Destination unreachable | Generated by a router to inform the source host that the destination is unreachable for a specified reason, other than congestion |
Packet too big | Generated by a router in response to a packet that it cannot forward because the packet is larger than the MTU of the outgoing link. |
Time exceeded | Generated by a router to inform the source of a packet that was discarded because the hop limit was exceeded in transit |
Parameter problem | Generated by a router to inform the source of a packet that the packet was discarded due to a problem with a field in the IPv6 header or extension header that prevented it from processing the packet |
Echo request/Echo reply | Used by the ping utility to test whether a host is reachable across an IP network and to measure the roundtrip time for packets sent from the local host to a destination node |
Neighbor Discovery ICMPv6 Messages | |
Router solicitation | Sent by a host, when an interface is enabled, to request routers to generate router advertisements immediately rather than at their next scheduled time |
Router advertisement | Sent by a router to advertise its presence as well as link and Internet parameters, periodically or in response to a router solicitation message |
Neighbor solicitation | Sent by a node to determine the link-layer address of a neighbor or to verify that a neighbor is still reachable |
Neighbor advertisement | Sent by a node in response to a neighbor solicitation message Nodes can also send unsolicited neighbor advertisements to announce a link-layer address change |
3.1.8. Static Routes, Dynamic Routes, and ECMP
Static routes to next-hop addresses are supported on the 7705 SAR. Dynamic routing using the OSPF, RIP, IS-IS, or BGP protocols is also supported.
If the 7705 SAR chassis is equipped with two Control and Switching modules (CSMs) for redundancy, non-stop services are supported. Therefore, if the active CSM experiences an activity switch, all static route entries are maintained.
Equal-Cost Multipath Protocol (ECMP) refers to the distribution of packets over two or more egress links that share the same routing cost. ECMP is supported on static routes and dynamic (OSPF, IS-IS, and BGP) routes. The 7705 SAR supports ECMP for both LDP and IP traffic.
ECMP for LDP can be used to distribute MPLS traffic across the links in order to balance the traffic load. ECMP for LDP load-balances traffic across all equal-cost links based on the output of the hashing algorithm using the allowed inputs, based on the service type. For detailed information, refer to the 7705 SAR Interface Configuration Guide, “LAG and ECMP Hashing”. Refer also to the 7705 SAR MPLS Guide, “ECMP Support for LDP”, for more information.
For IP-routed traffic, as shown in Table 15 in the 7705 SAR Interface Configuration Guide, “LAG and ECMP Hashing”, the 7705 SAR load-balances the traffic over multiple equal-cost links with a hashing algorithm that uses header fields from incoming packets to calculate which link to use. By adding additional fields to the algorithm, the randomness of the results can be increased to ensure a more even distribution of packets across available links. ECMP for IP allows load balancing to be configured across all IP interfaces at the system level or interface level on the network side. Configuration at the interface level overrides the system-level settings for the specific interface. IP ECMP is supported on all 7705 SAR adapter cards and platforms.
| Note: For VPLS, hashing is done on both the service ID and VPLS ID. For VLLs, hashing in done on the service ID. For Layer 3 spoke-SDP termination in IES and VPRN services, hashing is done on the service ID. |
Interfaces on the system can have any mixture of load-balancing configurations, including having load balancing disabled. Router updates often cause interface load- balancing configuration changes. The 7705 SAR will automatically continue processing packets using the new interface configuration.
ECMP is configured on the interface but is agnostic to the underlying SAP, spoke SDP, or VPLS binding. ECMP configuration is maintained even if the binding type changes.
If multiple routes are learned with an identical preference using the same protocol, the lowest-cost route is used. If multiple routes are learned with an identical preference using the same protocol and the costs (metrics) are equal, the decision of which route to use is determined by the configuration of ECMP.
Preferences are set on static routes in the config>router>static-route context. Preferences are set on OSPF routes in the config>router>ospf context, on RIP routes in the config>router>rip context, on IS-IS routes in the config>router>isis> level context, and on BGP routes in the config>router>bgp context (refer to the 7705 SAR Routing Protocols Guide for OSPF, IS-IS, and BGP configuration).
3.1.8.1. Enabling ECMP
The ECMP decision is performed at the ingress point on the node; therefore, ECMP must always be enabled on the ingress interface.
To enable LDP and GRT IP ECMP, the config>router>ecmp command is used.
To enable IP ECMP on a per-IP, next-hop basis (far-end PE) under the IP-VPRN context, the config>service>vprn>ecmp command is used.
For LDP ECMP, the lsr-load-balancing command under the system context enables optional LSR load balancing for the node. The lsr-load-balancing command under the router interface context overrides the system configuration for the specified interface.
For IP ECMP, the l4-load-balancing command under the system context enables optional Layer 4 load balancing for the node. The l4-load-balancing command under the router interface context, IES service interface context, or VPRN service interface context overrides the system configuration for the specified interface.
For IP ECMP, the teid-load-balancing command can be configured under the router interface context, IES interface context, and VPRN interface context.
For both LDP and IP ECMP, the system-ip-load-balancing command can be configured under the system context.
For information on the load-balancing commands, see Router Interface Commands, the 7705 SAR Basic System Configuration Guide, “System Information and General Commands”, and the 7705 SAR Services Guide, “VLL Services Command Reference”, “VPLS Command Reference”, “IES Command Reference”, and “VPRN Services Command Reference”.
3.1.9. IGP-LDP and Static Route-LDP Synchronization
With LDP, FECs learned from an interface do not necessarily link to that interface state. As long as the router that advertised the labels is reachable, the learned labels are stored in the incoming label map (ILM) table.
Although this feature gives LDP a lot of flexibility, it can also cause problems. For example, when an interface comes back up from a failure or from a shutdown state, the static routes bound to that interface are installed immediately. However, the LDP adjacency to the next hop might not be up, which means that the LDP SDP remains down. In this case, the MPLS traffic will be blackholed until the LDP adjacency comes up.
The same issue is also applicable to dynamic routes (OSPF and IS-IS).
To resolve this issue, the LDP synchronization timer enables synchronization of IGP or static routes to the LDP state.
With IGP, when a link is restored after a failure, IGP sets the link cost to infinity and advertises it. The value advertised in OSPF is 0xFFFF (65535). The value advertised in IS-IS regular metric is 0x3F (63) and in IS-IS wide-metric is 0xFFFFFE (16777214).
After IGP advertises the link cost, the LDP hello adjacency is brought up with the neighbor. The LDP synchronization timer is started by IGP from the time the LDP session to the neighbor is up over the interface. This synchronization timer allows time for the label-FEC bindings to be exchanged.
When the LDP synchronization timer expires, the link cost is restored and is readvertised. IGP will announce a new best next-hop and LDP will use it if the label binding for the neighbor’s FEC is available.
The above behavior is similar for static routes. If the static route is enabled for ldp-sync, the route is not enabled immediately after the interface to the next hop comes up. Routes are suppressed until the LDP adjacency with the neighbor comes up and the synchronization timer expires. The timer does not start until the LDP adjacency with the neighbor node is fully established. For static routes, the ldp-sync-timer function requires LDP to use the interface address, not the system address, as its transport address.
3.1.10. Bidirectional Forwarding Detection (BFD)
BFD is a simple protocol for detecting failures in a network. BFD uses a “hello” mechanism that sends control messages periodically to the far end and receives periodic control messages from the far end. BFD is implemented for IGP and BGP protocols, including static routes, in asynchronous mode only, meaning that neither end responds to control messages; rather, the messages are sent in the time period configured at each end.
Due to the lightweight nature of BFD, it can detect failures faster than other detection protocols, making it ideal for use in applications such as mobile transport.
If the configured number of consecutive BFD missed messages is reached, the route to the peer is declared not active. For centralized and line card BFD sessions, failure detection is propagated to all impacted upper layer protocols within a few milliseconds. Upper layer protocols act on failure information as soon as it is made available by BFD.
The v-port on the 2-port 10GigE (Ethernet) Adapter card and on the 2-port 10GigE (Ethernet) module is linked to the ring ports through the add/drop port, therefore its operational status—always operationally up—is not dependent on the status of the ring ports. Hence a ring port failure will not necessarily trigger an action at the v-port. To ensure that there is fast detection of any Layer 2 failure and that protocols on the v-port will react to the failure, you must run health-check tests or OAM tests with the peer or peers at the far end. For example, BFD must be configured between the v-port and the far-end IP interface. The use of health-check tests to the far-end interface will trigger upper layer protection mechanisms on the v-port, where the behavior will be comparable to an intermediate Layer 2 transport network failure on any other Ethernet port.
For IPv4, BFD is supported on static routes, OSPF, IS-IS, BGP, PIM, RSVP-TE, L-LDP, and T-LDP. For IPv6, BFD is supported on static routes, IPv6 interfaces, and OSPFv3. The 7705 SAR also supports centralized BFD on Layer 3 spoke SDP interfaces. This capability allows BFD on Layer 3 spoke SDP interfaces to ride over the applicable tunnel and the configured spoke SDP to the far-end node where the spoke SDP is terminated. It offers a fast way to detect failures on Layer 3 interfaces riding over spoke SDPs; for example, service traffic running over an LSP tunnel.
Note:
|
3.1.11. IP Fast Reroute (FRR)
IP Fast Reroute (FRR) protects against link or node failures in an IP network by precalculating a backup route to use when the primary next hop is not available. Both routes are populated in the RTM.
Without FRR, when a link or node failure occurs in a routed network, there is a period of disruption to the delivery of traffic until the network reconverges. Packets may be dropped or looped during this time, which can last hundreds of milliseconds.
IP FRR uses a Loop-Free Alternate (LFA) backup next hop to forward in-transit IP packets as soon as the primary next-hop failure is detected and the backup is invoked. This means that a node resumes forwarding IP packets to a destination prefix without waiting for the routing convergence. Convergence times should be similar to RSVP-TE FRR, in the tens of milliseconds.
When any of the following occurs, the backup LFA is enabled:
- an OSPF or IS-IS interface goes operationally down, due to either a physical failure or a local administrative shutdown
- a BFD session to a next hop times out when BFD is enabled on the interface
Refer to RFC 5286, Basic Specification for IP Fast Reroute: Loop-Free Alternates, for more information on LFAs.
IP FRR is supported on IPv4 and IPv6 OSPF and IS-IS prefixes and on VPN-IPv4 OSPF prefixes forwarded in the base router instance. IP FRR also provides an LFA backup next hop for the destination prefix of a GRE tunnel used in an SDP or in VPRN auto-bind.
3.1.11.1. ECMP vs FRR
If ECMP is enabled, which provides multiple primary next hops for a prefix, IP FRR is not used. That is, the LFA next hops are not populated in the RTM and the ECMP paths are used instead.
3.1.11.2. IGP Shortcuts (RSVP-TE Tunnels)
IGP shortcuts are an MPLS functionality where LSPs are treated like physical links within IGPs; that is, LSPs can be used for next-hop reachability. If an RSVP-TE LSP is used as a shortcut by OSPF or IS-IS, it is included in the SPF calculation as a point-to-point link for both primary and LFA next hops. It can also be advertised to neighbors so that the neighboring nodes can also use the links to reach a destination via the advertised next hop.
IGP shortcuts can be used to simplify remote LFA support and simplify the number of LSPs required in a ring topology.
When both IGP shortcuts and LFA are enabled under OSPF or IS-IS, and IP FRR is also enabled, the following applies:
- a prefix that is resolved to a direct primary next hop can be backed up by a tunneled LFA next hop
- a prefix that is resolved to a tunneled primary next hop will not have an LFA next hop; it relies on RSVP-TE FRR for protection
3.1.11.3. IP FRR Configuration
To configure IP FRR, LFA calculation by the SPF algorithm must first be enabled under the OSPF, OSPFv3, or IS-IS protocol level with the command:
config>router>ospf>loopfree-alternate
or
config>router>ospf3>loopfree-alternate
or
config>router>isis>loopfree-alternate
LFA can also be enabled on an OSPF or OSPFv3 instance within a VPRN service with the command:
config>service>vprn>ospf>loopfree-alternate
or
config>service>vprn>ospf3>loopfree-alternate
Next, IP FRR must be enabled to use the LFA next hop with the command config>router>ip-fast-reroute.
If IGP shortcuts are used, they must be enabled under the OSPF or IS-IS routing protocol. As well, they must be enabled under the MPLS LSP context, using the command config>router>mpls>lsp>igp-shortcut.
For information on LFA and IGP shortcut support for OSPF and IS-IS, refer to the 7705 SAR Routing Protocols Guide, “LDP and IP Fast Reroute for OSPF Prefixes” and “LDP and IP Fast Reroute for IS-IS Prefixes”.
The 7705 SAR supports both IP FRR and LDP FRR; for information on LDP FRR, refer to the 7705 SAR MPLS Guide, “LDP Fast Reroute (FRR)”.
3.2. Configuring Security Parameters
The 7705 SAR supports a number of mechanisms for node security, including Access Control Lists (ACLs), Network Address Translation (NAT), and stateful, zone-based firewalls. For information about ACLs, see Configuring Filter Policies. For more details about NAT, see NAT Security.
Firewalls extend ACL filtering by ensuring that pass-through IP traffic between an inside (trusted private) network and an outside (untrusted public) network does not pose a security risk.
NAT and firewall security configurations are based on zones that use policies that determine how traffic will be handled. Profiles are applied to security policies in order to customize the characteristics of the firewall to exact customer requirements and appropriate end-user-specific settings or requirements.To enable NAT or firewall functionality, security policy, application group, host group, and profile parameters must be configured under the config>security context in the CLI, and a security zone must be configured under one or more of the following contexts:
- config>router>zone
- config>service>vprn>zone
- config>service>ies>zone
Figure 2 shows the relationship between the configurable elements for firewall and NAT security.
Figure 2: Firewall and NAT Security Configuration for the 7705 SAR
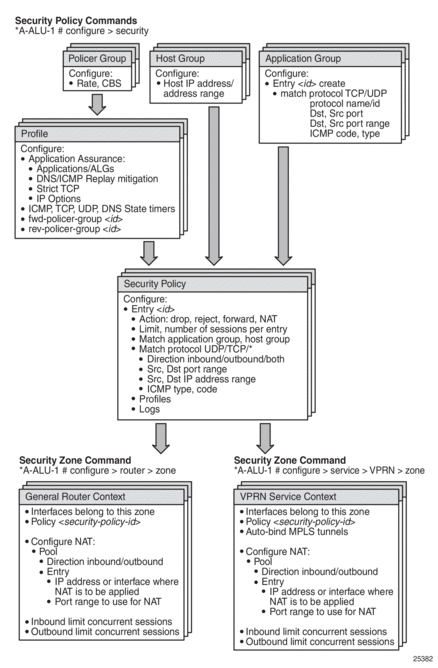
This section describes the following topics:
3.2.1. Supported Hardware
NAT and firewall security functionality is supported on the following cards and platforms:
- on the 7705 SAR-8 (with CSMv2) and the 7705 SAR-18:
- 8-port Gigabit Ethernet Adapter card, version 3
- 2-port 10GigE (Ethernet) Adapter card
- Packet Microwave Adapter card
- 10-port 1GigE/1-port 10GigE X-Adapter card, version 2 (7705 SAR-18 only)
- on the 7705 SAR-8 Shelf V2 (with CSMv2) and the 7705 SAR-18:
- 6-port Ethernet 10Gbps Adapter card
- 7705 SAR-Ax
- 7705 SAR-H
- 7705 SAR-Hc
- 7705 SAR-Wx
- 7705 SAR-X
3.2.2. Security Zone Configuration
NAT and firewall security configuration is based on zones. Zones segment a network, making it easier to control and organize traffic. A zone consists of a group of Layer 3 interfaces with common criteria, bundled together. Security policies, which define a set of rules that determine how NAT or a firewall should direct traffic, can be applied to the entire zone or multiple zones.
A security zone can be created within the base router context and/or within the IES or VPRN service context. Interfaces are assigned to the zone once the zone is created. Table 5 lists the supported interfaces that can be added to zones in each CLI context for NAT or firewall.
Table 5: Security Zone Interfaces per Context
CLI Context | Interface Type | NAT | Firewall |
Router | Layer 3 | ✓ | ✓ |
VPRN | SAP | ✓ | ✓ |
Spoke-SDP termination | ✓ | ✓ | |
IPSec private | ✓ | ✓ | |
Routed VPLS | ✓ | ✓ | |
MP-BGP | ✓ | ✓ | |
IES | SAP | ✓ | ✓ |
Spoke-SDP termination | ✓ | ✓ | |
IPSec public | ✓ | ||
Routed VPLS | ✓ | ✓ |
A zone is created by adding at least one Layer 3 interface to the zone configuration. Multiple zones can be created within each service or within the router context. Layer 3 interfaces from different services cannot be grouped into a single common zone.
A zone configured within the router context is typically used to provide security functionality between an outside (insecure) network such as an ISP network or Layer 2/Layer 3 leased line network, and an inside (secure) network such as a corporate LAN or a small cell wireless network.
Figure 3 shows a 7705 SAR connected to an insecure network (the public Internet), via the GRT. A firewall configured on the 7705 SAR protects the private access network from any connection that is not part of the 7705 SAR security policy.
Figure 3: Firewall Protection of a Private Access Network

For information about creating a security zone in a VPRN, refer to the Services Guide, “Security Zones and VPRN”.
Security policies can be configured based on traffic entering (inbound) the zone, leaving (outbound) the zone, or both inbound and outbound. A zone can be configured so that all traffic inbound to the zone has NAT and/or firewall applied to it based on the security policy configured for that zone. Likewise, a zone can be configured so that all traffic leaving the zone has NAT and/or firewall applied to it. A zone can be configured so that all traffic both inbound and outbound has firewall applied to it.
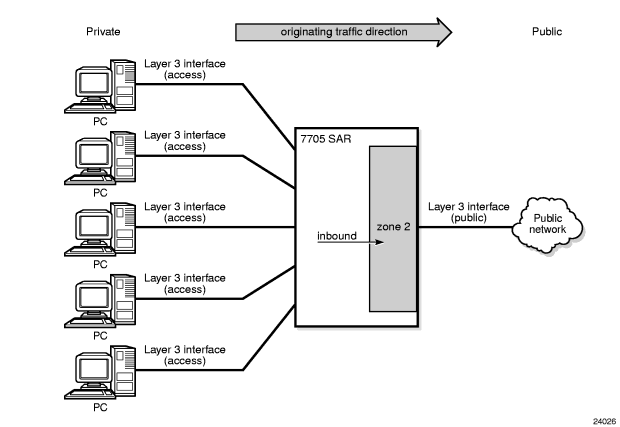
An example of inbound zone direction is shown in Figure 4. All traffic entering zone 2 has NAT applied to it based on the configured NAT policy assigned to zone 2.
Figure 4: Zone Direction (Inbound)
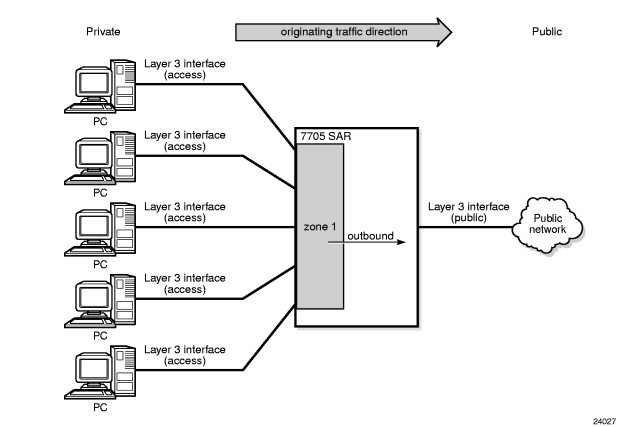
An example of outbound zone direction is shown in Figure 5. All traffic leaving zone 1 has NAT applied to it based on the configured NAT policy assigned to zone 1.
Figure 5: Zone Direction (Outbound)
3.2.3. Security Session Creation
A firewall or NAT security session is established by extracting packets to the CSM and matching them against the rules configured in a security policy. Packet extraction is based on zone configuration. If a packet is inbound to or outbound from a security zone, the packet will be extracted to the CSM and examined by the firewall/NAT engine on the CSM.
If the extracted packet matches the criteria defined in the security policy, a connection session is set up using lookup criteria that are specific to the packet type and an accompanying action. For example, an IP packet uses a 6-tuple lookup of source IP address, destination IP address, source port, destination port, protocol, and VRF (where VRF 0 is the base routing table).
Depending on the match criteria and action, a copy of the session is downloaded to the datapath. For example, a session is not downloaded to the datapath if the action in the security policy is configured as reject. When the session is downloaded to the datapath, there is no further extraction to the CSM for examination; any subsequent packet matching the 6-tuple of the session occurs on the datapath session.
Some connection sessions are set up using more criteria in the lookup than 6-tuple while other sessions are set up using a 4-tuple lookup. Table 6 lists the session type and session tuple signature.
Table 6: Security Session Type and Session Tuple Signature
Session Type | Session Tuple Signature |
IP | VRF, source IP address, destination IP address, and protocol |
UDP/TCP/SCTP | VRF, source IP address, destination IP address, source port, destination port, and protocol |
ICMP | VRF, source IP address, destination IP address, and ICMP request ID |
DNS | VRF, source IP address, destination IP address, source port, destination port, protocol, and DNS transaction ID |
Some connection sessions require CSM extraction of every packet; for example, a connection that requires strict TCP. For this type of CSM connection, the TCP session state and sequence number must be examined for every packet on that connection. The connection session is not downloaded to the datapath and all security processing occurs only on the CSM. The throughput rate of these CSM firewall sessions is lower than that of datapath firewall sessions. Datapath sessions can process traffic at approximately the line rate. Any connection session that uses strict TCP is not hot-redundant and will time out after an activity switch.
Both CSM and datapath sessions are stateful as they can both read into TCP/UDP states and close the session based on the timers configured for that session.
On the 7705 SAR-8 and 7705 SAR-18, security sessions survive a CSM redundancy switch; however, security sessions configured with strict TCP do not.
Zones can be configured to have session limits on a per-direction basis, in order to limit potential attacks.
3.2.3.1. Directionally Aware Security Behavior
A security session can be directionally aware. For example, a firewall security policy entry can be configured to allow packets with source IP address X and source port Y that are traveling from the private network to the public network to traverse the firewall. This means that any traffic arriving from the outside network on IP address X and port Y is denied entry to the inside network. However, a host in the private network can create a session from inside to outside for IP address X and port Y. Once this inside-to-outside session is created, traffic with IP address X and port Y traveling in the reverse direction (from outside to inside) is now allowed.
Similarly with NAT, a source NAT policy entry can be created to apply NAT on all arriving packets with source IP address X and source port Y to an outside source IP address A and source port B. When the first packet with IP address X and port Y arrives, NAT creates an inside-to-outside session and punches a hole through the firewall for that specific IP address and port number, thus allowing all packets to be transmitted from the inside network to the outside network.
3.2.3.2. TCP MSS Configuration and Adjustment
Typically, the MTU in a private LAN is larger than the MTU of a public network; the MTU of a private LAN is usually 1500 bytes whereas the MTU of a public network is usually less than 1500 bytes. In addition, packets destined to the public network may have an additional header, such as a transport tunnel, appended to the original packet. These two factors can cause the TCP/IP packet to become fragmented when entering the public network. Fragmentation is not desirable for TCP applications where the server needs a lot of processing power to reassemble the fragmented packets.
To avoid fragmentation, the maximum segment size (MSS) of application data in a TCP connection can be adjusted. Applications use the MSS to calculate the maximum number of data bytes (not including the header) that can be transmitted in a single packet. By lowering the MSS value, an outgoing packet's MTU can be made smaller than the public network MTU, ensuring that the packets entering the public network will not be fragmented.
The 7705 SAR supports TCP MSS adjustment. When acting as a CE router, the 7705 SAR can insert or modify the MSS value in the header of a TCP SYN or SYN-ACK packet. The sending and receiving CE routers set their MSS based on the outgoing interface MTU. The routers exchange TCP SYN or SYN-ACK packets during TCP session negotiation, engaging in a three-way handshake to compare and then select the lowest MSS value.
On the 7705 SAR, MSS configuration and adjustment is supported on the following cards and platforms:
- on the 7705 SAR-8 (with CSMv2) and the 7705 SAR-18:
- 8-port Gigabit Ethernet Adapter card, version 3
- 2-port 10GigE (Ethernet) Adapter card
- Packet Microwave Adapter card
- 10-port 1GigE/1-port 10GigE X-Adapter card, version 2 (7705 SAR-18 only)
- on the 7705 SAR-8 Shelf V2 (with CSMv2) and the 7705 SAR-18:
- 6-port Ethernet 10Gbps Adapter card
- 7705 SAR-Ax
- 7705 SAR-H
- 7705 SAR-Hc
- 7705 SAR-W
- 7705 SAR-Wx
When the tcp-mss command is configured, the 7705 SAR can adjust the MSS field in the TCP SYN packet or SYN-ACK packet, or insert the MSS field in the SYN packet if the field is not present.
The command is supported in the general router, VPRN service, and IES CLI contexts; Table 7 lists the supported interface types for each context. The tcp-mss command is not supported for TCP packets arriving on or leaving from MP-BGP tunnels in a VPRN.
Table 7: MSS Configuration Interfaces per Context
CLI Context | Interface Type |
Router | Layer 3 |
VPRN | SAP |
Spoke-SDP termination | |
IPSec private | |
IES | SAP |
Spoke-SDP termination |
When the tcp-mss command is configured on an interface, TCP packets with a SYN or SYN-ACK flag will have the MSS value is adjusted or inserted, as follows.
- If the TCP session has no defined MSS, the 7705 SAR inserts the field in the TCP packet.
- If the MSS value of the TCP session arriving from an access interface is greater than the MSS value configured on the 7705 SAR interface, the TCP session MSS is overwritten with the lower value.
- If the MSS value of the TCP session arriving from an access interface is less than the MSS value configured on the 7705 SAR interface, the TCP session MSS does not change.
The command can be configured on an ingress interface, an egress interface, or both. When configured on both interfaces, the smallest MSS value is used.
If the interface configured with tcp-mss is part of a firewall zone, the MSS packet extraction occurs as part of the firewall processing extraction. If the security session does not have a 5-tuple signature, the TCP SYN or SYN-ACK packets are extracted to the CSM via control queues. If the security session has a 5-tuple signature or if there is no security session configured for the interface, the TCP SYN or SYN-ACK packets are extracted to the CSM via datapath queues. The SYN and SYN-ACK packets that are extracted to the CSM are counted as control or datapath queue statistics.
Fragmented packets are not monitored for TCP MSS adjustment.
TCP MSS configuration and adjustment is supported for both IPv4 and IPv6 interfaces. Because the tcp-mss value is configured separately for each interface, it is possible to configure and enforce a different MSS value for IPv4 and IPv6.
3.2.4. Application Groups
An application group is a grouping of common criteria, such as the TCP/UDP port or ICMP code/type, used for a specific application. An application group is assigned to a security policy and application group criteria are matched in the policy. For further security, an application group can be configured with security profile parameters such as timeouts, fragmentation rules, and application assurance rules. Configuring an application group simplifies the configuration and management of firewall policies. An application group can be configured on the NSP NFM-P and downloaded to all routers at a particular network layer (either access or core) that require the same matching criteria.
3.2.5. Host Groups
A host group is a grouping of host IP addresses that can be added to a security policy. Configuring a host group simplifies the configuration of a security policy. Typically, service providers have a preassigned set of IP addresses that are allowed in the network. By creating a host group, a range of IP addresses or a single source/destination IP address is configured once and assigned to every edge router. The host group is added to the security policy as matching criteria.
3.2.6. Security Policy Policing
A private network can be infiltrated when an open port through the firewall is scanned and a DoS attack is initiated. The attack can use large amounts of bandwidth, starving existing connections of bandwidth and preventing other connections traversing through the firewall from using any bandwidth. To address this, a policer group can be configured against a profile and assigned to an entry within a security policy. All connections set up against that particular entry on the same adapter card or port are subjected to a policer rate and CBS buffer size. If the aggregate for one or more sessions using the policer group is exceeded, packets received beyond the policed rate are dropped and a log event is issued.
3.2.7. Security Profiles
Security profiles define security characteristics on the router, such as timers for different states of a TCP/UDP connection, application assurance parameter definitions, and whether to allow fragmented packets in a network. Security profiles can vary from subscriber to subscriber and are assigned to security policies, which are then applied to zones at the time the zone is created.
| Note: Security profile 1 is the default profile and cannot be modified. By default, this profile is assigned to any security policy that does not have a profile. |
3.2.7.1. Profile Timers
Timers are used to time out a NAT or firewall session and drop it. The 7705 SAR supports configurable timers for different connections. Timers can be idle or strict. Idle timers are activated by the lack of traffic. Strict timers are used for protocol state changes and are not affected by the presence of traffic. The supported timers are described in Table 8.
Table 8: Security Profile Timers
Timer | Description | Timer Type | CLI Command |
ICMP request | Specifies the timeout for an ICMP session Default timeout: 1 min Minimum timeout: 1 min Maximum timeout: 5 min | Strict | icmp-request |
Idle timeout | Specifies the timeout for a security session for IP packets that are not ICMP, TCP, or UDP Default timeout: 600 s Minimum timeout: 1 s Maximum timeout: 10800 s | Idle | other-sessions |
TCP established | Specifies the timeout for a TCP session in the established state Default timeout: 2 h, 4 min Minimum timeout: 1 min Maximum timeout: 24 h | Idle | tcp-established |
TCP SYN | Specifies the timeout applied to a TCP session in the SYN state Default timeout: 15 s Minimum timeout: 6 s Maximum timeout: 24 h | Strict | tcp-syn |
TCP time wait | Specifies the timeout applied to a TCP session in a time-wait state Default timeout: n/a Minimum timeout: n/a Maximum timeout: 4 min | Strict | tcp-time-wait |
TCP transitory | Specifies the idle timeout applied to a TCP session in a transitory state Default timeout: 4 min Minimum timeout: 1 min Maximum timeout: 24 h | Strict | tcp-transitory |
UDP | Specifies the UDP mapping timeout Default timeout: 5 min Minimum timeout: 1 min Maximum timeout: 24 h | Idle | udp |
UDP DNS | Specifies the timeout applied to a UDP session with destination port 53 Default timeout: 15 s Minimum timeout: 15 s Maximum timeout: 24 h | Idle | udp-dns |
UDP initial | Specifies the timeout applied to a UDP session in its initial state Default timeout: 15 s Minimum timeout: 10 s Maximum timeout: 5 min | Strict | udp-initial |
3.2.7.2. Application Assurance Parameters
The following application assurance parameters can be defined in a security profile:
- DNS
- ICMP
- IP options
- strict TCP
3.2.7.2.1. DNS
Each DNS session request received on the 7705 SAR should have only a single response. When the reply-only command is configured in the config>security> profile>aa>dns CLI context, the firewall discards any additional responses, which can help prevent a DNS replay attack. The firewall will permit a single request and a single reply; any other DNS packets with the same DNS request ID that are received on that session will be dropped. See Table 6 for the match criteria for a DNS session.
3.2.7.2.2. ICMP
ICMP replay attacks can be prevented using two mechanisms:
- limiting the number of ICMP requests and the number of replies to ICMP requests with the request-limit command
- limiting the number of ICMP type 3 replies to ICMP or IP sessions with the limit-type3 command
For each ICMP request received, the 7705 SAR creates an ICMP session based on the ICMP packet identifier field and source and destination IP addresses. The 7705 SAR restricts the number of packets for that session based on the limit configured in the request-limit command. Any request received beyond the configured limit for that session is blocked. For example, if the ICMP request limit is set to 2, only two ping requests and replies can be transmitted from that ICMP session, while the ICMP session has not timed out. This ensures that an external attacker cannot replay the ICMP reply packet repeatedly to the source of the ICMP request.
| Note: It is recommended that the ICMP session timeout be set to equal the latency or delay of the network so that the session times out very quickly, and also that the timer type be set to strict so that the ICMP session times out strictly within the timer value. |
The 7705 SAR can limit the number of ICMP type 3 replies for ICMP and IP sessions. For every packet arriving at the firewall, the 7705 SAR creates a 6-tuple session. For regular IP packets, these sessions are uniquely identified using the 6-tuple. For ICMP packets, these sessions are identified using the source IP address, the destination IP address, and the ICMP identifier field. If these packets are discarded after traversing the firewall (for example, because the destination is unreachable or fragmentation is not allowed), an ICMP type 3 packet is generated and sent back to the originator.
The ICMP type 3 packet usually has at least the first 8 octets of the original datagram in the payload of its packet. When the ICMP type 3 packet arrives at the 7705 SAR, the 7705 SAR examines the packet and its payload to find the original packet that triggered the error and tries to find the corresponding session for that packet. If it does, it counts the ICMP type 3 packet against the session. The 7705 SAR allows only 15 ICMP type 3 packets through for each original packet. If the 7705 SAR does not find the session corresponding to the packet that triggered the error, it discards the ICMP type 3 packet.
3.2.7.2.3. IP Options
Traffic on the 7705 SAR can be firewalled based on the IP options in the IP packet header. When IP option names or bit mask values are configured in a security profile using the config>security>profile>aa>ip>options command, only packets with the specified IP options are allowed through the firewall.
If the command is configured with the permit-any option (the default), the firewall does not examine the packet IP options and allows all packets through.
Table 9 lists the names and bit mask values of supported IP options. For more information, see the IANA website at: http://www.iana.org/assignments/ip-parameters/ip-parameters.xhtml
Table 9: Supported IP Options
IP Option Number | IP Option Value | IP Option Name | Bit Mask Value |
0 | 0 | EOOL – End of Options List | 0x00000001 |
1 | 1 | NOP – No Operation | 0x00000002 |
2 | 130 | SEC – Security | 0x00000004 |
3 | 131 | LSR – Loose Source Route | 0x00000008 |
4 | 68 | TS – Time Stamp | 0x00000010 |
5 | 133 | E-ESC – Extended Security | 0x00000020 |
6 | 134 | CIPSO – Commercial Security | 0x00000040 |
7 | 7 | RR – Record Route | 0x00000080 |
8 | 136 | SID – Stream ID | 0x00000100 |
9 | 137 | SSR – Strict Source Route | 0x00000200 |
10 | 10 | ZSU – Experimental Measurement | 0x00000400 |
11 | 11 | MTUP – MTU Probe | 0x00000800 |
12 | 12 | MTUR – MTU Reply | 0x00001000 |
13 | 205 | FINN – Experimental Flow Control | 0x00002000 |
14 | 142 | VISA – Experimental Access Control | 0x00004000 |
15 | 15 | Encode | 0x00008000 |
16 | 144 | IMITD – IMI Traffic Descriptor | 0x00010000 |
17 | 145 | EIP – Extended Internet Protocol | 0x00020000 |
18 | 82 | TR – Traceroute | 0x00040000 |
19 | 147 | ADDEXT – Address Extension | 0x00080000 |
20 | 148 | RTRALT – Router Alert | 0x00100000 |
21 | 149 | SDB – Selective Directed Broadcast | 0x00200000 |
22 | 150 | Unassigned | 0x00400000 |
23 | 151 | DPS – Dynamic Packet State | 0x00800000 |
24 | 152 | UMP – Upstream Multicast Packet | 0x01000000 |
25 | 25 | QS – Quick-Start | 0x02000000 |
30 | 30 | EXP – RFC3692-style experiment | 0x40000000 |
30 | 94 | EXP – RFC3692-style experiment | 0x40000000 |
30 | 158 | EXP – RFC3692-style experiment | 0x40000000 |
30 | 222 | EXP – RFC3692-style experiment | 0x40000000 |
3.2.7.2.4. Strict TCP
A security profile on the 7705 SAR can be configured with strict TCP in order to monitor a TCP connection. With strict TCP configured, the 7705 SAR extracts all packets for that session to the CSM for further examination as defined by RFC 793. This parameter should be used under particular circumstances, such as a suspected DoS attack.
3.2.7.3. Application Level Gateway
When a 7705 SAR security profile is configured with Application Level Gateway (ALG), the firewall/NAT engine intercepts all upstream traffic destined for TCP port 21 (the FTP control channel), UDP port 69 (the TFTP port), or some other destination port configured to support ALG. All traffic matching the policy is extracted to the CSM for examination.
If the examined traffic is found to be an FTP control channel, the corresponding data channel is programmed to the datapath. When an FTP client sends the port command in the FTP control channel, the firewall/NAT ALG intercepts this command, creates a new mapping in the firewall/NAT table, and opens the data port based on the client port command. Firewalls configured in either passive or active mode must have ALG configured in order to allow the FTP datapath through the firewall. A temporary match rule for the FTP data port is placed on top of the security policy, and TCP timer configuration is inherited from ALG policy control timers. In short, the temporary data session inherits all the control session policy/profile configuration.
Trivial File Transfer Protocol (TFTP) is a simple File Transfer Protocol, which is implemented on top of the UDP/IP protocol and uses port 69. TFTP was designed to be small and easy to implement; therefore, it does not have most of the advanced features offered by more robust file transfer protocols such as FTP. TFTP requests from a client are always destined for UDP port 69 on the server. The server responds by sending an ACK and/or the data on a random port. The 7705 SAR firewall and the ALG are able to detect this random port and create a temporary rule to open the UDP port in the firewall.
The ALG security profile parameter can be configured as auto, ftp, or tftp.
When the parameter is configured as auto (the default), FTP or TFTP ALG is enabled on TCP port 21 (the default port for FTP) or UDP port 69 (the default port for TFTP). The firewall will enforce use of the ALG on the FTP or TFTP session for port translation, if NAT is being used, and for pin-hole operations.
When the parameter is configured as ftp, FTP ALG is enabled on any TCP port being used for FTP. For example, if a security session has been configured for a DNAT mapping where the destination port is not TCP port 21, configuring the ALG security parameter as ftp allows the FTP ALG to be enabled on TCP ports or TCP port ranges so that the session can be treated as FTP and so that the ALG can perform the correct translation and pin-hole functions as required by FTP.
When the parameter is configured as tftp, TFTP ALG is enabled on any UDP port being used for TFTP.
Unlike auto ALG, where only the default FTP and TFTP ports are inspected for a potential ALG session, FTP ALG and TFTP ALG inspect all packets that match their policy’s matching criteria. It is recommended that a specific destination port or port range be matched so that entire port ranges are not left open for potential attackers.
The following example shows a recommended configuration for incoming (DNAT) and outgoing FTP control.
3.2.7.4. Fragmentation Handling
Security functionality on the 7705 SAR can process TCP/UDP packet fragments; however, the fragment containing the header must arrive first. If this condition is not met, the following actions occur.
- The firewall drops all fragmented packets arriving on the 7705 SAR until the fragment that contains the TCP/UDP header arrives.
- For bidirectional forwarding, packets arriving from the opposite direction are discarded because no session was created for the forward direction.
- For any TCP/UDP packets traversing from a public network to a private network and destined for a local IP address on the 7705 SAR, fragmented packets that do not contain the TCP/UDP header are extracted to the CSM for processing and an ICMP error message is sent to the sender.
- For destination NAT (port forwarding) packets traversing from a public network to a private network and destined for a local IP address on the 7705 SAR, fragmented packets that do not contain the TCP/UDP header are extracted to the CSM for processing and an ICMP error message is sent to the sender.
On the 7705 SAR-8 and 7705 SAR-18, in addition to the condition requiring the fragment containing the header to arrive first, all fragments of a given packet must arrive on the same adapter card for processing.
If packets for an application such as DNS or ICMP are fragmented and the first fragment does not contain the information needed to make a firewall decision, the packet is discarded.
A security profile configured with strict TCP requires that all packets, including packet fragments, are extracted to the CSM for processing. The CSM checks for repeated packet fragments and discards them, and also checks the fragment offset to ensure that all fragments correspond to the correct offset.
3.2.8. Security Policies
Security policies define the rules within a zone that a packet must match in order for a defined action to be applied. Policies can vary from subscriber to subscriber and are applied to zones at the time the zone is created. The 7705 SAR supports the matching criteria and policy actions described in Table 10.
A security policy performs NAT when the policy entry is configured with the action to perform NAT and is configured with the destination IP address and port address parameters. NAT policies are all of type NPAT, meaning that they use both a network address translation and port address translation mechanism. Within a NAT policy, if the defined action is NAT, the packet has NAT applied to it based on the configured NAT pool IP address and ports.
| Note: A security policy is a template that can be applied to multiple zones. |
Table 10: Security Policy Attributes and Packet Matching Criteria
Attribute | Description | CLI Command |
Action | Specifies how a packet is handled if a criterion is matched. If the zone finds a match for all the specified criteria, then it performs the specified actions on the packet. If there is no match, the packet is dropped. The supported policy actions are:
| action |
Packet flow direction | Specifies whether the policy matching criteria are applied to packets that are inbound to a zone, outbound from a zone, or to both inbound and outbound packets. The supported directions are zone-inbound, zone-outbound, or both. The both option does not apply to NAT. | direction |
Match (protocol ID) | Specifies a protocol ID that the protocol specification of the packet must match | match |
Source IP | Specifies an explicit source IP address for the match criteria of the rule. Packets being processed by a zone are evaluated for a match to the specified source IP address. | src-ip |
Destination IP | Specifies an explicit destination IP address for the match criterion of the rule. Packets destined for the specified IP address are evaluated for a match. | dst-ip |
Source Port | Specifies a source port to match in the IP packets when the match attribute is specified as protocol ID | src-port |
Destination Port | Specifies a destination port to match in the IP packets when the match attribute is specified as protocol ID | dst-port |
ICMP Code | Specifies the ICMP code when the protocol ID specified for the match attribute of the rule is set to ICMP | icmp-code |
ICMP Type | Specifies the ICMP type when the protocol ID specified for the match attribute of the rule is set to ICMP | icmp-type |
Profile | Specifies the profile ID applied to the policy | profile |
Concurrent Sessions | Specifies the number of concurrent sessions that can be created using a single rule or zone | concurrent-sessions |
3.2.9. Security Session Resource Alarms
The system monitors the overall session resource utilization. An alarm state is declared if the utilization exceeds the user-configurable high-water mark (session-high-wmark). The alarm condition is only cleared when the utilization has dropped below the user-configurable low-water mark (session-low-wmark).
If the thresholds are not configured, an alarm is raised if utilization reaches 100% and is cleared when utilization drops to 0%.
Session resource utilization alarms are described in Table 11.
Table 11: Session Resource Utilization Alarms
Event | Description | SNMP Notification |
All security session resources have been exhausted | This event is generated if all session resources have been exhausted (utilization reaches 100%) | aluSecSessionsExhausted |
Security session resource alarm detected | This event is generated when a resource alarm state is detected. The alarm state is detected when either the high-water mark is crossed (if configured) or all session resources have been exhausted. | aluSecSessionHiWtrMrkCrossed |
Security session resource alarm cleared | This event is generated when a security session resource alarm state is cleared. This alarm state is cleared when either the low-water mark is crossed (if configured) or all sessions have been cleared. | aluSecSessionLoWtrMrkCrossed |
Security session resource alarm threshold modified | This event is generated when the high or low thresholds for the alarm state are modified. | aluSecSessionWtrMrkModified |
3.2.10. Security Logging
An essential component of security functionality is the ability to log events in order to have a view of the types of traffic and connections that are attempting to traverse a network. Events can be logged for each entry of a security policy or for a zone. Use the config>security>logging command to configure a logging profile, and then specify the log event or event type in the profile using the event-control command. For each event or event type, configure an action (one of suppress, throttle, or off) to determine how the event should be handled in the logging profile. To enable logging, the logging command must be configured in the security policy.
In addition to logging events per zone or per rule, the following can be logged:
- the permitted inbound or outbound security sessions that are destined for or traversing the 7705 SAR
- firewall administrative logs such as the number of policies or rules that have been created or deleted
- the dropped or rejected packets or sessions that are destined for or traversing the 7705 SAR
The 7705 SAR supports logging of the following firewall event types:
Table 12: Firewall Packet Events
Event | Description |
TcpInvalidHeader | The full TCP Header is not provided in the TCP segment. |
DnsInvalidHeader | The format or content of the DNS packet is not valid. For example, the packet is a DNS answer from client to name server. |
DnsUnmatchedAnswer | A DNS answer has been received without a preceding DNS query that matches the query ID. |
IcmpUnmatchedReply | An ICMP response has been received without a preceding ICMP request that matches the ICMP request ID. |
TcpInvalidFlagCombination | The TCP header contains flag combinations that are not valid and the packet may have been generated to probe the network or disrupt traffic. |
TcpRst | A TCP RST has been generated with no matching session. |
PolicyErrorFrag | The packet is a fragment and has been dropped; for example, because the first fragment received does not contain the entire protocol header, the reassembly time has expired, the limit on the number of non-adjacent fragments has been exceeded, or the fragment overlaps an existing fragment of this packet. |
FragDropAction | The fragment packet has been rejected as the result of a problem with an earlier fragment of this packet. |
DuplicateFrag | The fragment duplicates another fragment of this fragmented packet. |
LandAttack | Source and destination IP addresses and UDP/TCP/SCTP ports all have the same value. This is an attack packet. |
Table 13: Firewall Zone Events
Event | Description |
NoRuleMatched | The packet is associated with a zone (source or destination) but does not match any rule in that zone. |
SessionLimitReached | The configured limit of sessions for this IP protocol has been reached and this session cannot be established. |
Table 14: Firewall Policy Events
Event | Description |
Matched | A non-NAT rule has been matched in the creation of a session for this packet. |
MatchedNAT | A NAT rule has been matched in the creation of a session for this packet. |
ActionReject | A rule has been matched for this packet with the action to reject. The packet has been dropped and no session has been created. |
MaxConcurrentUsesReached | A rule has been matched by this packet whose limit of concurrently active sessions has been exceeded. The rule has been skipped and an attempt to match a succeeding rule has been made. If no succeeding rule matches this packet, the packet is dropped and no session established. |
FragsNotAccepted | The packet is fragmented and the matched rule does not allow fragments. The packet will be dropped and no session will be created. |
TcpSynReqdtoEstablish | An invalid combination of TCP flags was encountered on a non-existent TCP session, so the packet was dropped. |
Table 15: Firewall Session Events
Event | Description |
InvalidIcmpT3 | An ICMP packet type 3 packet is invalid. This may be due to policy configuration. |
PktLimitReached | A security session has not been created because the zone-based session limits have been reached. |
ProhibitedIpOption | A packet with invalid or malformed IP options was encountered so it was dropped. |
RuleActionDrop | Due to policy configuration, a drop session exists for the packet flow and all packets are discarded for the duration of the session. |
SessionBegin | A new session has been created. The session may be a PASS or a DROP session and will continue to exist until the inter-packet interval configured for the session has been exceeded. Events such as a TCP full-close or TCP RST can also trigger the termination of the session. |
SessionEnd | A session has terminated. This is either as the result of an operator action or the natural expiration of the session when the inter-packet interval has been exceeded. |
SessionBeginEnd | The packet has been passed but the session allows only one packet and has been terminated. This can be accomplished by configuring an inter-packet interval of zero. Such sessions are sometimes used by an operator to pass ICMP type 3 notifications that do not match an existing session. |
Table 16: Firewall Application Events
Event | Description |
Summary | If TCP events have been discarded as a result of event-rate throttling, this event will identify the types of events that have been discarded. |
HandshakeMissing | The TCP connection did not start with a SYN, SYN_ACK sequence. |
HandshakeCtlInvalid | RST or ACK on SYN packet or data flags on dataless TCP SYN. |
HandshakeDataUnexpected | The SYN packet has data in non-T/TCP handshake. |
OptError | One or more TCP options are corrupted. |
OptBadLen | A TCP option has an incorrect length. |
OptTTcpForbidden | T/TCP options are present but not permitted. |
OptNonStdForbidden | Experimental TCP options are present but not permitted. |
OptTStampMissing | TCP timestamps have been negotiated but the timestamp option is not present. |
OptTStampUnexpected | The TCP timestamp is present but has not been negotiated. |
TStampTooOld | The TCP timestamp value is too old. |
TStampEchoInvalid | The echoed TCP timestamp is greater than expected. |
ScaleUnexpected | The TCP scale option is present but has not been negotiated. |
SeqNumOutside | The TCP sequence number is outside the window. |
AckNumOutside | The TCP acknowledgment number is outside the window. |
AckNumNotZero | There is no TCP ACK flag but the ACK number is not zero. |
AckNumStale | An old TCP ACK flag is being used for a reused connection. |
AckUnexpected | The TCP ACK flag is present but the connection has not yet synchronized. |
AckMissing | The TCP ACK flag is expected but not present |
FlagsSynRst | The TCP SYN and RST flags are both set. |
SynUnexpected | The TCP SYN flag is present after the handshake completed. |
SynMissing | The TCP SYN flag is not present but the connection has not yet synchronized. |
FinUnexpected | There is a duplicate TCP FIN in this direction. |
InvCksum | There is an invalid TCP checksum. |
ConnReused | A TCP packet has been received on a closed connection |
RstSeqNumUnexpected | The TCP RST sequence number is out of order. |
TTL | The TCP TTL has been changed inappropriately. |
NotFullHeader | The complete TCP header was not present. |
FlagsSynFin | The TCP SYN and FIN flags are both set. Likely a probe or an attack. |
SplitHandshake | The TCP SYN with no ACK was received when TCP SYN/ACK expected. |
Table 17: Firewall ALG Events
Event | Description |
CmdIncomplete | The ALG control session contained an incomplete command. |
DynamicRuleInserted | A rule has been inserted into the rule list for a zone to permit a data session to be established. |
DynamicRuleInsertedPASV | A rule has been inserted into the rule list for a zone to permit a data session to be established (PASV mode). |
CannotInsertDynamicRule | This is an unusual event. |
CannotInsertDynamicRulePASV | This is an unusual event. |
BadCmdSyntax | The ALG control session contained an invalid command. The packet will be dropped. |
BadPortCmdSyntax | The FTP control session contained an invalid TCP port specification. The packet will be dropped. |
BadPasvCmdSyntax | The FTP control session contained an invalid PASV specification. The packet will be dropped. |
BadAddrSyntax | The FTP control session contained an invalid IP address specification. The packet will be dropped. |
TftpDynRuleInsertEr | This is an unusual event. |
TftpDynRuleInserted | A rule has been inserted into the rule list for a zone to permit a TFTP data session to be established. |
3.2.11. Firewall Debugging
If a security session is suspected of having a problem, it can be investigated with the firewall debugging capability. Use the debug>security>capture command to capture and isolate for inspection packets that are being processed by the firewall. Depending on the configured destination, packets are sent to a log or the console. The contents of the log can be viewed using the show>security>capture command. To configure the capture capability, a zone identifier must be specified and the start command must be issued; however, every time a start command is issued, the contents of the log are cleared. The extraction rate for the capture capability is 25 packets/s. By default, the packet-capture process is continuous and packets are never dropped. However, when the log reaches 1024 packets, the oldest entry in the log is overwritten with a new one. Configuring the optional count packets parameter in the start command specifies the number of packets that will be captured before the oldest entry in the log is overwritten with a new one.
| Note: It is recommended that the debug>security>capture>start>count packets option be used rather than continuous capture. |
To stop the capture process, use the debug>security>capture>stop command. To view the configured packet-capture parameters, use the show>debug command.
3.2.12. NAT Security
Network Address Translation (NAT) is used by mobile backhaul, enterprise, and SI (Strategic Industries) providers to provide expandability and security for private networks. Tier 1 providers can potentially run out of private IPv4 addresses, making it difficult to expand their existing networks. To address this issue, NAT can be used. NAT can hide multiple private IP addresses behind a single public IP address and therefore makes it possible to scale IP solutions in mobile backhaul, enterprise, and SI networks.
For example, when applying NAT to a typical metrocell deployment, the cell site network is divided into two separate segments, a private domain and a public domain. Private domain network IP addressing needs to be hidden from the public domain. NAT makes all metrocells accessible via a single IP address visible in the public domain. The IPSec tunnels generated from metrocells are uniquely identified using IPSec NAT traversal (NAT-T).
Besides conserving available IPv4 addresses, NAT can also be used as a security feature to hide the real IP addresses of hosts, securely providing private LAN users access to public addresses.
This section describes security functionality specific to NAT, and covers the following topics:
3.2.12.1. NAT Zones
With source NAT, a traffic session can only be initiated from a private domain to a public domain. Unless a session is created, packets from the public domain cannot be forwarded to the private domain. All arriving packets from the private domain, which are routed towards a public interface, are checked to determine if they traverse a NAT zone. If so, the packets are examined against the NAT policy rules. If there is a match between the policy and the packet, NAT is applied to the packet. Source NAT changes the source IP address and the source port of the packet, based on the configured NAT pool.
Zones can be segmented as small as a single interface or as large as the maximum number of interfaces supported by the 7705 SAR. For example, in metrocell applications, all the SAPs on the access point used to aggregate the metrocell can be placed in a single zone (zone 2) and the uplink public interface can be placed in another zone (zone 1). All traffic routed between the two zones uses NAT rules based on the NAT policies created for zone 1 and zone 2.
An example of the above zone configuration is shown in Figure 6.
Note:
|
Figure 6: Zone Configuration in a Mobile Backhaul Network
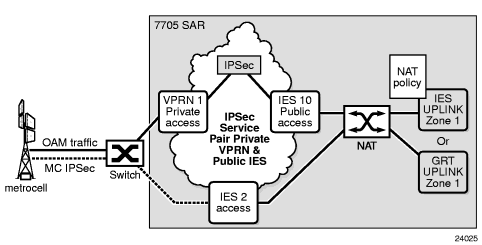
In Figure 6, the OAM traffic from the metrocell is not encrypted. The OAM traffic is aggregated into a single VPRN service and IPSec functionality encrypts the OAM traffic. The encrypted traffic enters IES 10 with an IPSec header that has a routable IP destination address (typically to a security gateway) in addition to the encrypted payload. The far-end destination IP address can be reached through IES uplink zone 1 or GRT uplink zone 1. Since the traffic from IES 10 to the uplink zone crosses a zone boundary, the zone policy is applied to the uplink interface, and NAT is applied to the packet. The source IP address in the packet is replaced with the IP address of the uplink interface.
Similarly, in Figure 6, traffic from the metrocell (indicated by the dashed line), is encrypted by the metrocell with a valid IP header that contains a destination IP address (typically to a security gateway). The far-end destination is reachable through IES uplink zone 1 or GRT uplink zone 1. The packet has NAT applied to it because the packet must cross a zone boundary. The source IP address of the metrocell packet that enters IES 2 is replaced with the source IP address of IES uplink zone 1 as it exits the 7705 SAR. In addition, the source UDP/TCP port may also be replaced depending on the NAT policy configured for the zone.
In both of the cases described above, NAT is applied to the IP traffic according to NAT zone policy rules configured for IES uplink zone 1 or GRT uplink zone 1.
When using NAT in conjunction with IPSec, all IPSec tunnels must be configured (enabled) with NAT traversal (NAT-T) functionality. Enabling NAT-T on IPSec causes an insertion of the UDP port below the IPSec IP header. This UDP port can be used by NAT to uniquely identify each IPSec tunnel.
With static destination NAT, when packets from a public domain arrive at a zone, their source and destination IP addresses are evaluated to determine from which interface within the zone the packet will egress.
3.2.12.2. Dynamic Source NAT
Source NAT can be used to create sessions from inside a private network to an outside (public) network. If an arriving IP packet on the 7705 SAR matches the NAT policy rules, an internal mapping is created between the inside (private) source IP address/source port and an outside (public) source IP address/source port. The public IP address and port are configured in the NAT pool policy.
NAT automatically creates a reverse mapping for arriving traffic from the public domain to the private domain for the same connection. This reverse mapping is based on an outside destination IP address and destination port to an inside destination IP address and destination port.
The configurable outside NAT pool for the source IP address and source port can be either a range of addresses and ports or a unique IP address and port.
The 7705 SAR also supports a single public IP address so that all inside source IP addresses can be mapped to a single outside IP address and a range of ports. In this case, the interface name can be assigned to the NAT pool configuration. For ease of configuration, any local interfaces on the 7705 SAR can be assigned to the NAT pool (for example, local Layer 3 interfaces, loopback interfaces).
By assigning the Layer 3 interface name, the NAT pool inherits the IP address of that specific interface. For a DHCP client, the NAT pool IP address can change based on the IP address assigned to the interface by the DHCP server. If the interface IP address changes, all associated NAT sessions are cleared and re-established.
3.2.12.3. Local Traffic and NAT
Source NAT does not support self-generated traffic such as OSPF, BGP, or LDP.
Only packets transiting the 7705 SAR node have NAT applied to them. Any packet arriving on the 7705 SAR with a local IP address will be checked against active NAT sessions on the datapath (6-tuple lookup), and if there is no match, the packet is sent to the CSM for processing as local traffic.
3.2.12.4. Port Forwarding (Static Destination NAT)
Port forwarding consists of mapping an outside destination port to an inside destination IP address and port. For example, a packet arriving from outside on port X and using a UDP protocol (from any IP address) is mapped to an inside destination port and destination IP address.
A typical use of port forwarding is shown in Figure 7. Each inside application is uniquely accessible via an outside port. For example, the surveillance camera behind the 7705 SAR can be reached via the UDP protocol and port 50. Any packet from any IP address arriving on destination port 50 is mapped to an internal destination IP address of 192.168.1.3 and destination port 50.
| Caution: Using port forwarding for well-known ports can disrupt in-band local management traffic. |
Figure 7: Static Port Forwarding with NAT

Static port forwarding can provide accessibility to applications behind a single IP address. Each application can be uniquely accessed via the public IP address and the destination port for that application.
Matching criteria for port forwarding includes local interface IP address, source IP address, and source UDP/TCP port.
3.3. Using the 7705 SAR as Residential or Business CPE
The 7705 SAR can be used as a residential or business CPE device for the purposes of ISP backhaul. With GPON, DSL, or cable-based residential or business backhaul services, specifically, ISPs typically terminate subscribers on a broadband network gateway to assign IP addresses, and to enforce authentication, authorization, and accounting before the customer traffic is routed for Internet access. By making use of the 7705 SAR as a CPE device, ISP backhaul infrastructure can be used to connect an eNodeB, such as a voice-free metrocell, to a network. The 7705 SAR continues to support a wide array of services, including IP-VPN, Ethernet, TDM, PWs, and VPLS services, over this backhaul by making use of GRE or IP tunnels. An example of a network using a 7705 SAR as a CPE device is shown in Figure 8.
Figure 8: Network Using 7705 SAR as a CPE Device
Residential or business CPE functionality is available through the use of:
- unnumbered interfacesIn normal operation, the 7705 SAR requires at least two IP addresses: a system IP address and an uplink interface IP address. However, ISPs typically assign a single IP address per connection for residential or business backhaul services, due to cost or architectural issues. Configuring the 7705 SAR to use unnumbered interfaces alleviates this issue.See Unnumbered Interfaces for more information.
- dynamic assignment of system IP addresses through DHCPA 7705 SAR using unnumbered interfaces does not have a configured uplink interface IP address, as the uplink interface identifier is tied to the system IP address. In residential and business backhaul, the system IP address must be assigned dynamically. The system IP address can be assigned dynamically using DHCP when the 7705 SAR is acting as a DHCP client and the DHCP server-facing interface is unnumbered.
- automatic provisioning of a default gatewayAs part of a DHCP OFFER message, the ISP also offers a default gateway IP address to the client. The 7705 SAR, as the client, must set up a default route pointing to the default gateway once the gateway IP is offered via Option 3. The default gateway points to the network interface, which, as the DHCP server-facing interface, is unnumbered.
3.4. Router Configuration Process Overview
Figure 9 displays the process to configure basic router parameters.
Figure 9: IP Router Configuration Flow
3.5. Configuration Notes
The following information describes router configuration guidelines and caveats.
- A system interface and associated IP address must be specified.
- Boot options file (BOF) parameters must be configured prior to configuring router parameters.
3.5.1. Reference Sources
For information on supported IETF drafts and standards, as well as standard and proprietary MIBs, refer to Standards and Protocol Support.