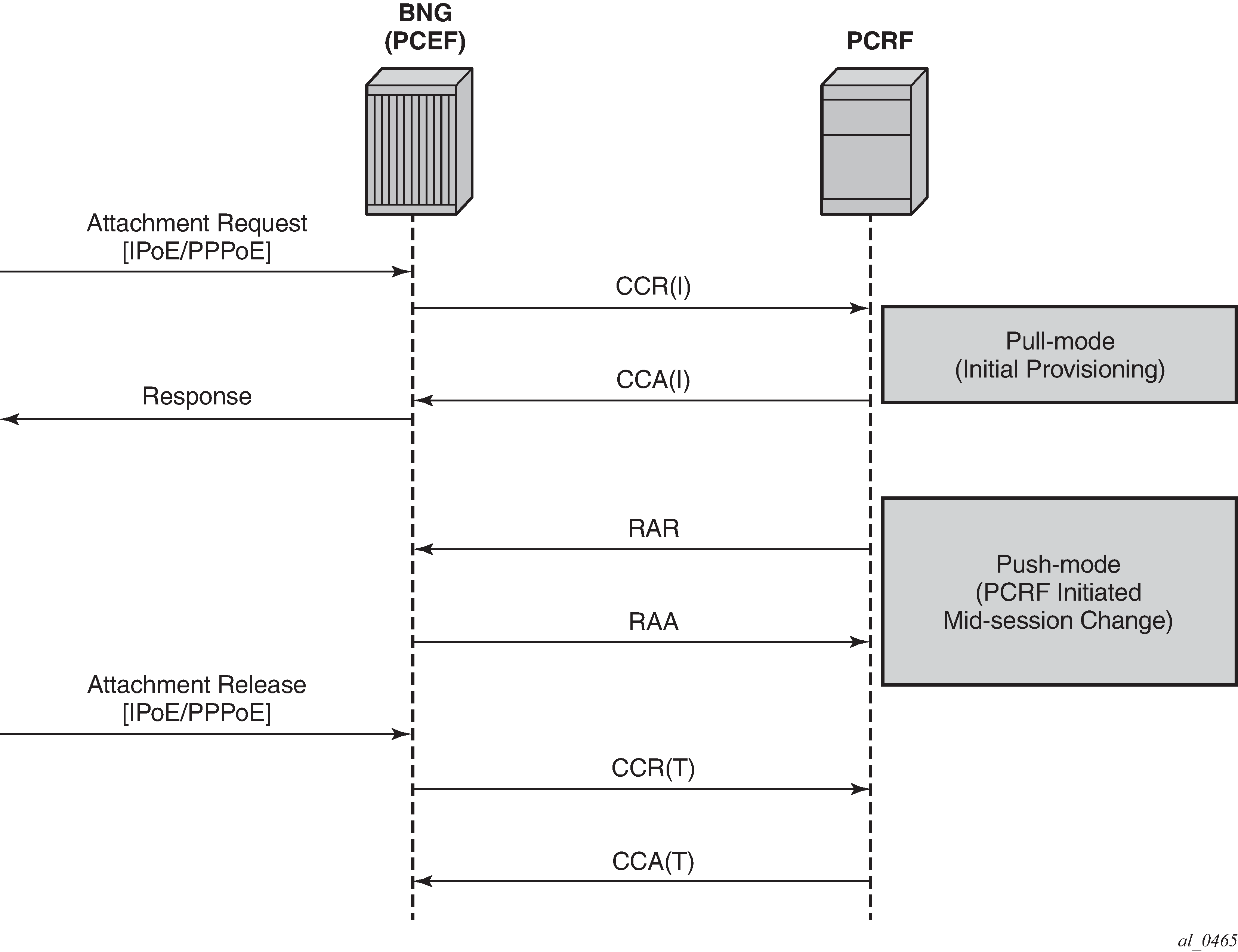
Subscriber and AA policies on the node (PCEF with integrated TDF) is assigned through the Gx protocol from the policy server (PCRF).
There are two modes of operation:
Pull mode
The policy creation or modification is solicited by the node.
Push mode
The policy change is unsolicited by the node.
In the pull mode, during the host creation process, a user is authenticated by the AAA server. This process is independent from PCRF. After the user is authenticated and the IP address is allocated to it, the node sends a request for policies to the PCRF via CCR-I messages (initialization request message). This communication occurs via the Gx interface. The subscriber-host must be uniquely identified in this request toward the PCRF. This sub-identification over the Gx interface could be by means of IP address, username, SAP ID, and so on.
Based on the user identification, PCRF submits policies to the node. Those policies can range from subscriber strings (sub/sla-profiles/AA-profiles) to QoS and filter-related parameters.
In the push mode, the PCRF initiates the mid-session policy change through the Re-Authentication Request (RAR) message (Figure: Policy assignment models).
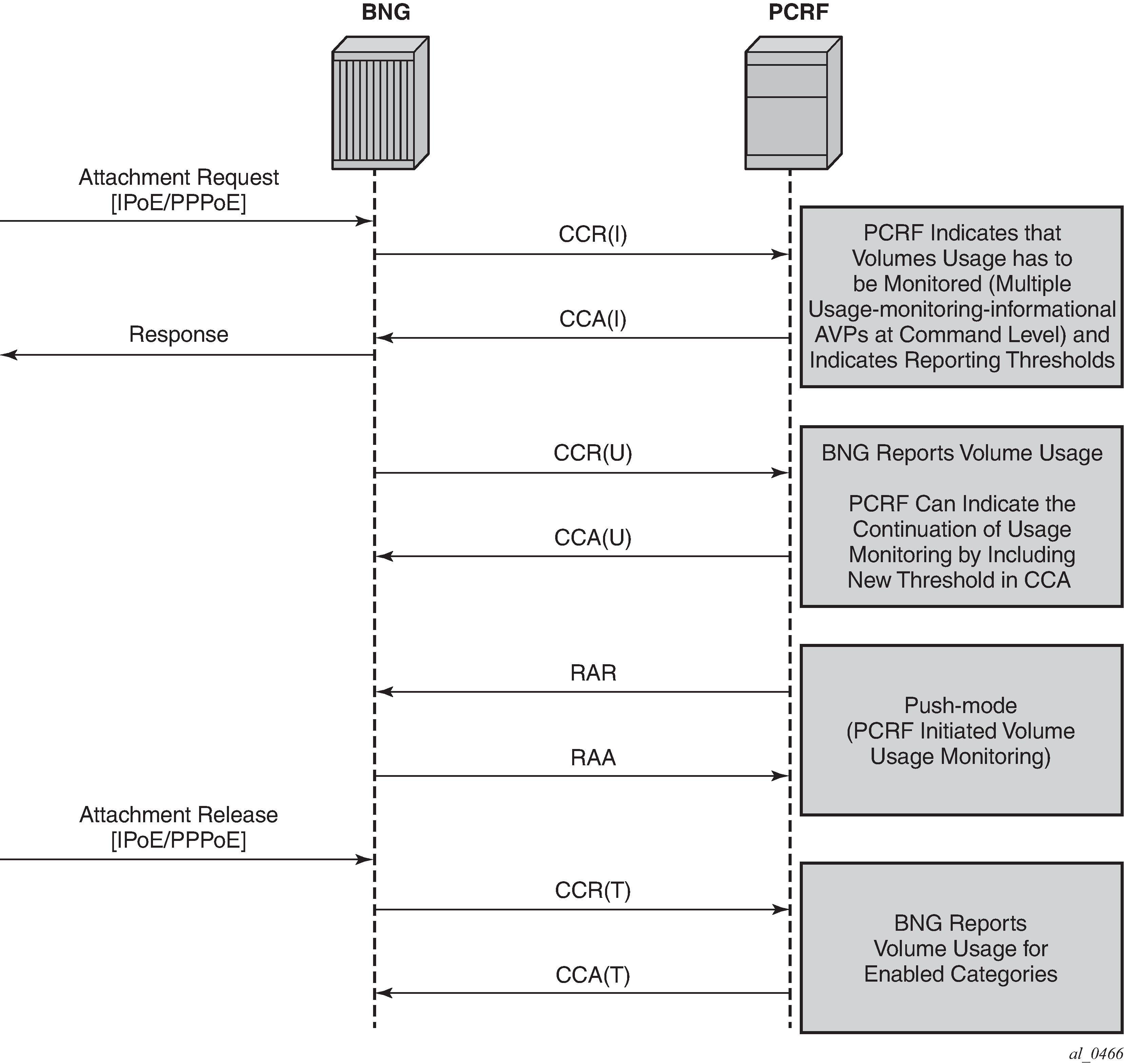
If that Usage-Monitoring is requested, the PCRF submitted policy changes are triggered by the Credit Control Request (Update) messages. This is based on ESM or AA Usage Monitoring. After the specified usage threshold is reached on the session-level, credit-category level, pcc rule level or application level on the node, the Usage-Monitoring is reported from the node to the PCRF in the CCR-U message. See the 7450 ESS, 7750 SR, and VSR Multiservice Integrated Service Adapter and Extended Services Appliance Guide for details on AA based Usage-Monitoring (Figure: On-demand usage reporting).
Alternatively, PCRF can request usage reporting on-demand via the rar command.