The SR OS supports EAP authentication for a IKEv2 remote-access tunnel, in which case, the system acts as an authenticator between an IPsec client and a RADIUS server. It transparently forwards EAP messages between the IKEv2 session and RADIUS session. Thus, the actual EAP authentication occurs between the client and the RADIUS server.
Figure: Typical call flow of EAP authentication shows a typical call flow of EAP authentication.
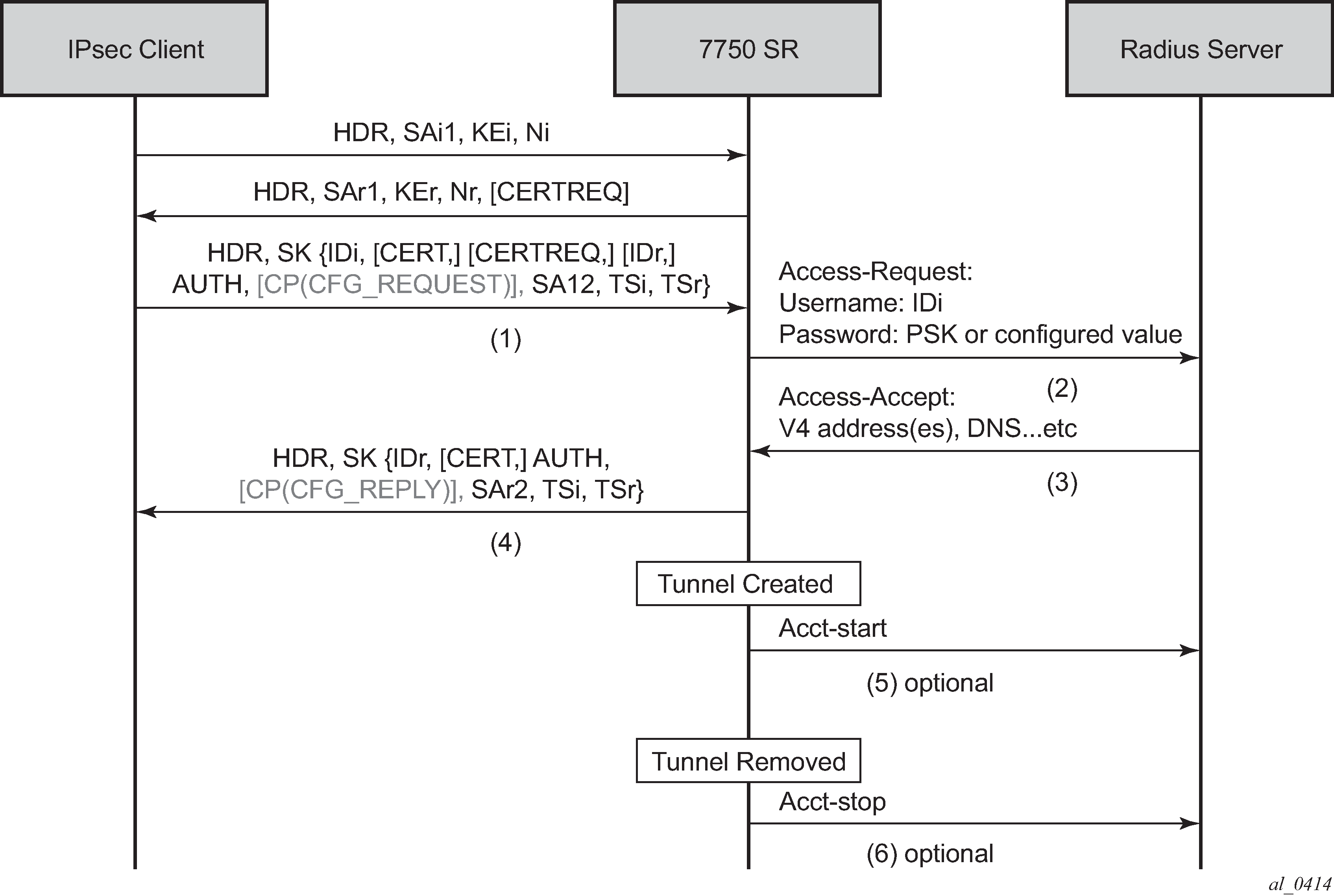
EAP authentication is enabled by configuring authentication eap. When enabled, after the received IKE_AUTH request from the client, the system sends an EAP-Response/ID with IDi as the value in the access-request to AAA. AAA returns a method request and the system starts passing through between the client and AAA. (as shown in Figure: Typical call flow of EAP authentication).
The generation of the AUTH payload in the IKE_AUTH response sent by the SR OS (message 4 in flow shown above) is dependent on the own-auth-method configuration:
- psk
- The AUTH payload is present and generated by using PSK.
- cert
- The AUTH payload is present and generated by the configured public and private key pairs as it does in certificate authentication. Any needed certificates are also sent.
- eap-only
- Neither AUTH nor CERT payload is present.
The RADIUS attributes in authentication and accounting packets are similar as psk-radius and cert-radius with following differences:
RADIUS attributes support EAP-Message/Message-Authenticator/State attributes.
RADIUS attributes support Access-Challenge packet.
RADIUS attributes support MS-MPPE-Send-Key/ MS-MPPE-Recv-Key in access-accept. These two attributes are required for all EAP methods that generate MSK.
The system provides a method to support EAP and other authentication methods on the same ipsec-gw policy. This is enabled by configuring auto-eap-radius or auto-eap as the auth-method in the ike-policy.
With auto-eap-radius:
If there is no AUTH payload in an IKE_AUTH request, then the system uses EAP to authenticate the client and also uses own-auth-method to generate the AUTH payload.
If there is an AUTH payload in the IKE_AUTH request, the system uses auto-eap-own-method to generate the AUTH payload.
If the auto-eap-method is psk, then the system proceeds as auth-method: psk-radius.
If the auto-eap-method is cert, then the system proceeds as auth-method: cert-radius.
If auto-eap-method is psk-or-cert, then:
If the Auth Method field of the AUTH payload is PSK, then the system proceeds as auth-method:psk-radius.
If the Auth Method field of the AUTH payload is RSA or DSS, then the system proceeds as auth-method:cert-radius.
With auto-eap:
If there is no AUTH payload in IKE_AUTH request, then the system uses EAP to authenticate the client and also uses own-auth-method to generate AUTH payload.
If there is an AUTH payload in the IKE_AUTH request:
If the auto-eap-method is psk, then the system proceeds as auth-method: psk.
If the auto-eap-method is cert, then the system proceeds as auth-method: cert.
If the auto-eap-method is psk-or-cert, then:
-
If the Auth Method field of the AUTH payload is PSK, then the system proceeds as auth-method psk.
-
If the Auth Method field of the AUTH payload is RSA or DSS, then the system proceeds as auth-method cert-auth.
-
The system uses auto-eap-own-method to generate the AUTH payload.