If the auth-method parameter in the ike-policy is configured as psk-radius or cert-radius, then the system authenticates the client via PSK or certificate accordingly as like a LAN-to-LAN tunnel. The difference being that in the case of psk-radius or cert-radius, the system also performs a RADIUS authentication or authorization and optionally send RADIUS accounting messages.
Figure: Call flow for psk-radius/cert-radius displays a typical call flow for psk-radius and cert-radius.
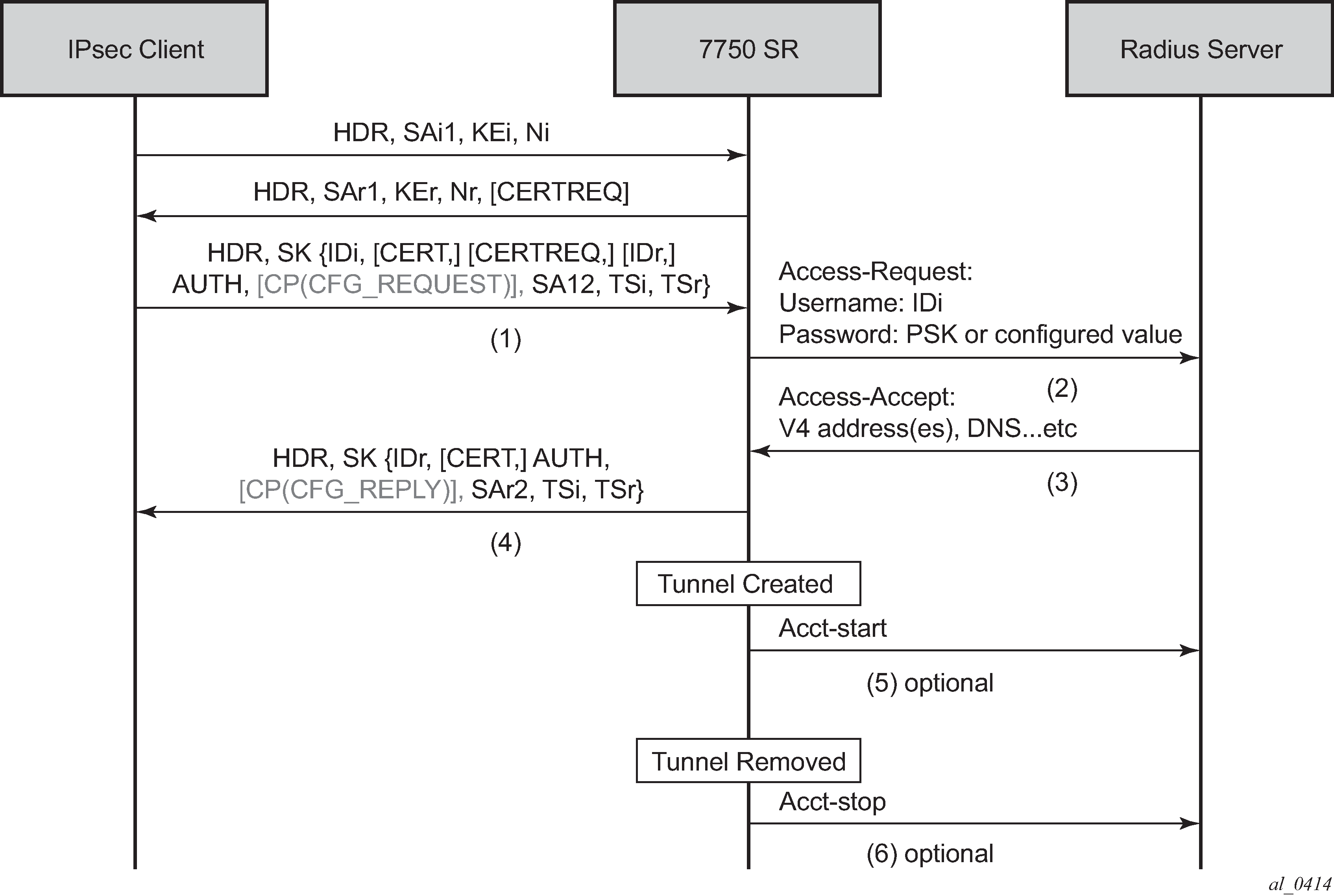
The Access-Request includes the following attributes:
Username is IDi.
User-Password is one of following value’s hash according to section 5.2 of RFC 2865, Remote Authentication Dial In User Service (RADIUS):
client’s PSK if the psk-radius is configured (see the CLI)
otherwise, a CLI configured key via the password command in the radius-authentication-policy; if password is not configured in this case, then system does not include the User-Password attribute in access-request.
Acct-Session-Id represents the IPsec tunnel session.
The format is: local_gw_ip-remote_ip:remote_port-time_stamp.
For example: 172.16.100.1-192.168.5.100:500-1365016423.
Other RADIUS attributes (dependent on the config>ipsec>radius-auth-policy> include-radius-attribute configuration) are as follows:
Called-Station-Id (local tunnel address)
Calling-station-Id (remote tunnel address:port number)
Nas-Identifier (the system name)
Nas-Ip-Address (the system IP)
Nas-port-id (the public tunnel SAP ID)
If the RADIUS authentication is successful, then the RADIUS server sends an access-accept message back; otherwise, an access-reject message is sent back.
The following are supported attributes in access-accept:
Alc-IPsec-Serv-Id
Alc-IPsec-Interface
Framed-IP-Address
Framed-IP-Netmask
Alc-Primary-Dns
Alc-Secondary-Dns
Alc-IPsec-Tunnel-Template-Id
Alc-IPsec-SA-Lifetime
Alc-IPsec-SA-PFS-Group
Alc-IPsec-SA-Encr-Algorithm
Alc-IPsec-SA-Auth-Algorithm
Alc-IPsec-SA-Replay-Window
After the tunnel is successfully created, the system could optionally (depending on the configuration of the radius-accounting-policy under the ipsec-gw context), send an accounting-start packet to the RADIUS server, and also send an accounting-stop when the tunnel is removed. The user can also enable the interim-update option in the radius-accounting-policy.
The following are some attributes included in the acct-start/stop and interim-update:
Acct-status-type
Acct-session-id (the same as in the access-request)
Username
The following attributes are dependent on the radius-acct-policy>include-radius-attribute configuration:
Frame-ip-address: the assigned internal address
Calling-station-id
Called-station-id
Nas-Port-Id
Nas-Ip-Addr
Nas-Identifier
Acct-Session-Time (tunnel session time, only in acct-stop packet)
For a complete list of supported attributes, see the 7450 ESS, 7750 SR, and VSR RADIUS Attributes Reference Guide.
The system also supports RADIUS disconnect messages to remove an established tunnel, If accept-coa (existing command) is enabled in the radius-server configuration, then the system accepts the disconnect-request message (RFC 5176, Dynamic Authorization Extensions to Remote Authentication Dial In User Service (RADIUS)), and tear down the specified remote-access tunnel.
config>router>radius-server>server#
[no] accept-coa
For security reasons, the system only accepts a disconnect-request when accept-coa is configured and the disconnect-request comes from the corresponding server.
The target tunnel is identified by one of following methods:
Acct-Session-Id
Nas-Port-Id + Framed-Ip-Addr(Framed-Ipv6-Prefix) + Alc-IPsec-Serv-Id
User-Name
See the 7450 ESS, 7750 SR, and VSR RADIUS Attributes Reference Guide for more details about disconnect message support.
By default, the system only returns what the client has requested in the CFG_REQUEST payload. However, this behavior can be overridden by configuring relay-unsolicited-cfg-attribute in the ike-policy. With this configuration, the configured attributes returned from the source (such as the RADIUS server) are returned to the client regardless if the client has requested it in the CFG_REQUEST payload.