Multicast packets that traverse an NGE domain can be categorized into two main scenarios:
Scenario 1
Multicast packets that ingress the router on an interface that is outside the NGE domain. These packets can egress a variety of interfaces that are either inside or outside the NGE domain.
Scenario 2
Multicast packets that ingress the router on an interface that is inside the NGE domain. These packets can egress a variety of interfaces that are either inside or outside the NGE domain. This scenario has two cases:
Scenario 2a
The ingress multicast packet is not yet NGE-encrypted.
Scenario 2b
The ingress multicast packet is NGE-encrypted.
Figure: Processing multicast packets shows these scenarios.
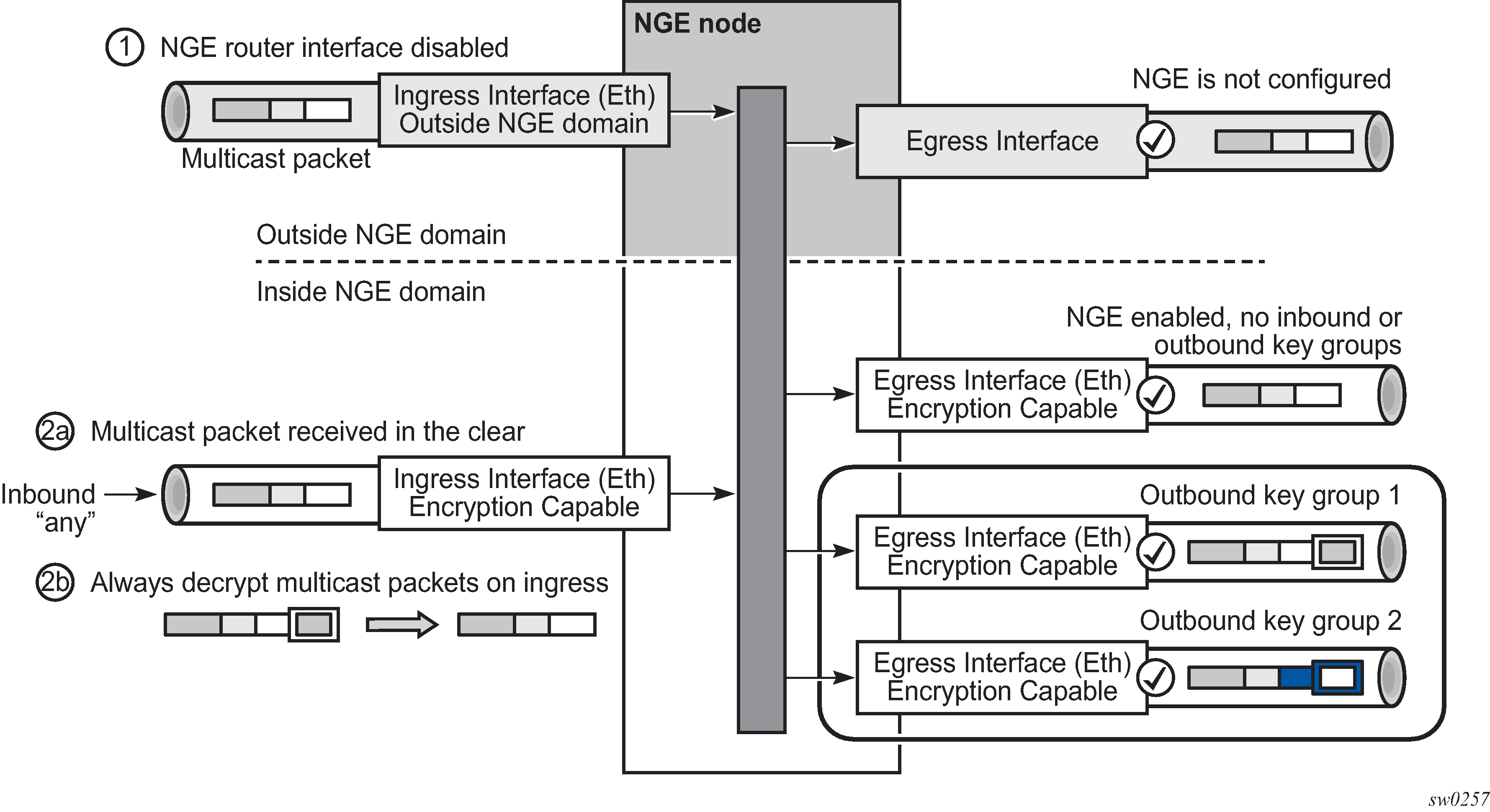
Multicast packets received from outside the NGE domain (Scenario 1) are processed similarly to multicast packets received from inside the NGE domain (Scenarios 2a and 2b).
The processing rule is that multicast packets are always forwarded as clear text over the fabric. This means that for Scenario 2b, when a multicast packet is received on an encryption-capable interface and is NGE-encrypted, the packet is always decrypted first so that it can be processed in the same way as packets in Scenarios 1 and 2a.
On egress, the following scenarios apply:
Egressing an interface outside the NGE domain
Packets are processed in the same way as any multicast packets forwarded out a non-NGE interface.
Egressing an NGE router interface and no inbound or outbound key group is configured
The router forwards these packets out from the egress interface without encrypting them because there is no outbound key group configured. This behavior also applies to unicast packets in the same scenario.
egressing an NGE router interface with the outbound key group configured — the router encrypts the multicast packet using the SPI keys of the outgoing SA configured in the key group. This behavior also applies to unicast packets in the same scenario.