NGE nodes support Layer 3 encryption on router interfaces for IPv4 traffic. NGE is not supported on dual-stack IPv4/IPv6 or IPv6-only interfaces. See the 7450 ESS, 7750 SR, 7950 XRS, and VSR Services Overview Guide for more information about platforms that support NGE.
NGE is enabled on a router interface by configuring the group-encryption command on the router interface. The interface is considered part of the NGE domain, and any received packets that are NGE-encrypted are decrypted if the key group is configured on the node. To encrypt packets egressing the interface, the outbound key group must be configured on the interface. All IP packets, such as self-generated traffic or packets forwarded from router interfaces that are not inside the NGE domain, are encrypted when egressing the interface. There are some exceptions to this general behavior, as described in the sections below; for example, GRE-MPLS and MPLSoUDP packets are not encrypted when router interface encryption is enabled.
The outbound and inbound key groups configured on the router interface determine which keys are used to encrypt and decrypt traffic. See the 7450 ESS, 7750 SR, 7950 XRS, and VSR Services Overview Guide for more information about configuring key groups.
To perform encryption, router interface encryption reuses the IPsec transport mode packet format as shown in Figure: Router Interface Encryption Packet Format (IPsec Transport Mode).
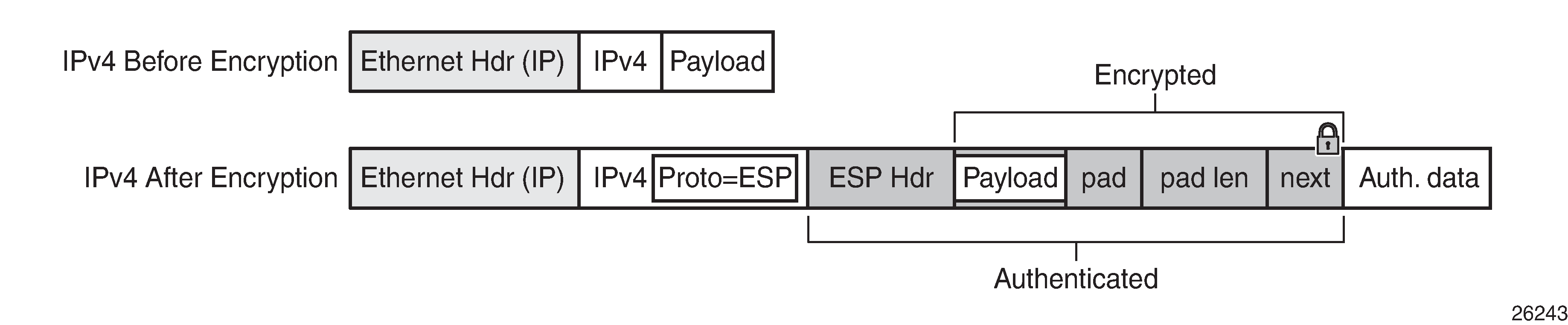
The protocol field in the IP header of an NGE packet is always set to ‟ESP”. Within an NGE domain, the SPI that is included in the ESP header is always an SPI for the key group configured on the router interface. Other fields in the IP header, such as the source and destination addresses, are not altered by NGE router interface encryption. Packets are routed through the NGE domain and decrypted when the packet leaves the NGE domain.
The group keys used on an NGE-enabled router interface provide encryption of broadcast and multicast packets within the GRT. For example, OSPF uses a broadcast address to establish adjacencies, which can be encrypted by NGE without the need to establish point-to-point encryption tunnels. Similarly, multicast packets are also encrypted without point-to-point encryption tunnels.