Secure Neighbor Discovery (SeND) in conjunction with Cryptographically Generated Addresses (CGAs) allows operators to secure IPv6 neighbor discovery between nodes on a common Layer 2 network segment.
When SeND is enabled on an interface, CGAs must be enabled and static GUA/LLA IPv6 addressing is not supported. In this case, the router generates a CGA from the configured prefix (GUA, LLA) and use that address for all communication. The router validates NS/ND messages from other nodes on the network segment, and only install them in the neighbor cache if they pass validation.
Several potential use-cases for SeND exist to secure the network from deliberate or accidental tampering during neighbor discovery, SeND can prevent hijacking of in-use IPv6 addressing or man-in-the-middle attacks, but also to validate whether a node is permitted to participate in neighbor discovery, or validate which routers are permitted to act as default gateways.
SeND affects the following areas of neighbor discovery:
Neighbor solicitation (solicited-node multicast address; target address)
Neighbor advertisement (solicited; unsolicited)
Router solicitation
Router advertisement
Redirect messages
Figure: Neighbor discovery with and without SeND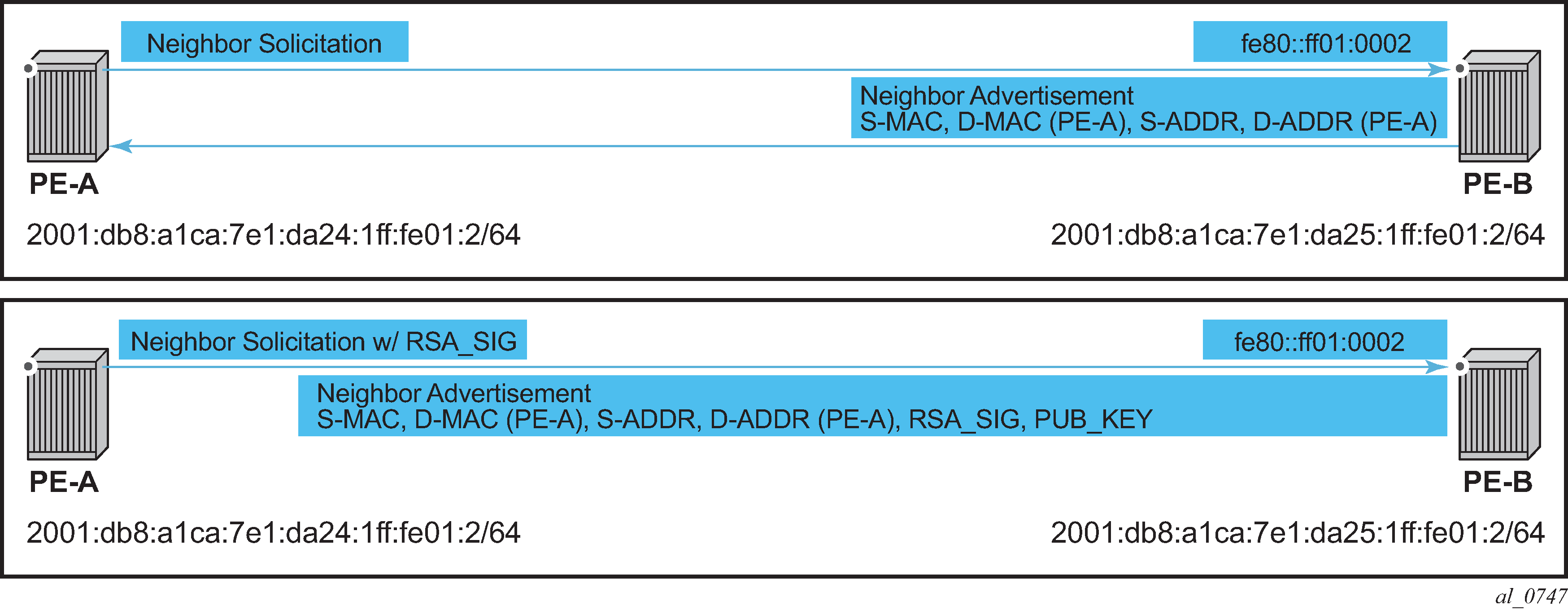
When SeND is enabled on a node, basic neighbor discovery messaging is changed as shown in Figure: Neighbor discovery with and without SeND. In the example, PE-A needs to find the MAC address of PE-B.
PE-A sends an NS message to the solicited node multicast address for PE-B's address with the CGA option, RSA signature option, timestamp option, and nonce option.
PE-B processes the NS message and, because it is configured for SeND operation, processes the NS. PE-B validates the source address of the packet to ensure it is a valid CGA, then validate the cryptographic signature embedded in the NS message.
PE-B generates an NA message, which is sent back to PE-A with the solicited bit, router bit set. The source address is that of PE-B, while the destination address is that of PE-A from the NS message. The timestamp is generated from PE-B, while the nonce is copied from PE-A's NS message.
PE-A receives the NA and completes similar checks as PE-B did.
If all steps process correctly, both nodes install each other’s addresses into their neighbor cache database.